Computer forensic techniques allow investigators to collect evidence from various digital devices. Tools and techniques exist allowing discovery of evidence that is difficult to get, including destroyed, locked, or obfuscated data. At the same time, criminals routinely make attempts to counter forensic efforts by wiping data, deleting files, faking or clearing logs, histories and other traces of performed activities. Anti-forensic efforts are not limited to just that. In this whitepaper, we will have a brief overview of common anti-forensic techniques frequently used by suspects who are not specialists in high-tech, and ways to counter them during the investigation.
What this paper does not discuss is the suspects' use of advanced tools dedicated to countering forensic efforts. Instead, we will talk about the most common anti-forensic techniques. In this paper, we will move from easy to moderately difficult anti-forensic techniques, explaining who might be using these methods and how to counter them.
What Is Anti-Forensics?
Anti-forensics is a set of precautionary measures a user can perform in order to hide traces of his activity, making investigations on digital media more complicated and time-consuming, and potentially rendering evidence of illegal activities difficult or impossible to obtain. Detecting anti-forensic techniques in use is not always easy and not always possible, as destroying certain types of evidence may leave no traces anywhere in the system. However, since average users have little to average hi-tech knowledge, anti-forensic attempts they perform may be generally ineffective or obviously visible to the expert.
Moving or Renaming Files
Moving or renaming files that may hold evidence against suspects is a form of simple, almost naive anti-forensics. By moving certain files (such as those used by instant messengers for keeping conversation histories), renaming or changing extensions (e.g. renaming an encrypted ZIP archive containing illegal images into something like c:\Windows\System32\drivers\rtvienna32.dat), suspects hope to confuse experts and delay investigations.
Indeed, locating moved or renamed files presents an obstacle to investigators who rely on nothing but their skills and expertise to locate evidence. However, modern computer forensic tools such as Belkasoft Evidence Center automatically analyze media with different techniques, like evidence search or carving.
The carving technique performs is a bit-precise sequential scan of the media for various artifacts. With carving, file names or locations become irrelevant as carving does not rely entirely on the file system, reading low-level data directly from the media instead.
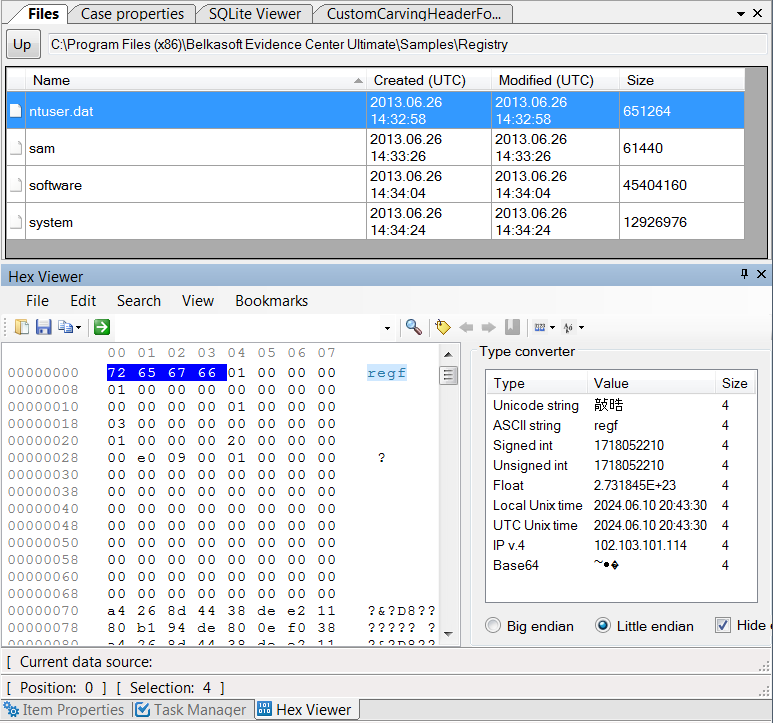
Carving can locate evidence by looking for signatures, which are sequences of bytes characteristic of certain types of data. In our example, the “c:\Windows\System32\drivers\rtvienna32.dat” file will be located during the carving process and identified as a ZIP archive not based on the name of the file, but because the actual data stream contains information associated with ZIP archives. Similarly, Skype databases, JPEG images, documents, and dozens of other types of evidence can be reliably detected by carving the disk or disk image.
Ready to start carving the disk, memory card or forensic disk image? If you are using Belkasoft Evidence Center, you can follow these step-by-step instructions with screenshots: https://belkasoft.com/bec/Carving.asp
Moreover, in the latest version of Belkasoft Evidence Center you will find a new carving mode, which allows you to carve only selected partitions of the drive, making the process easier, faster, and more convenient for investigators:
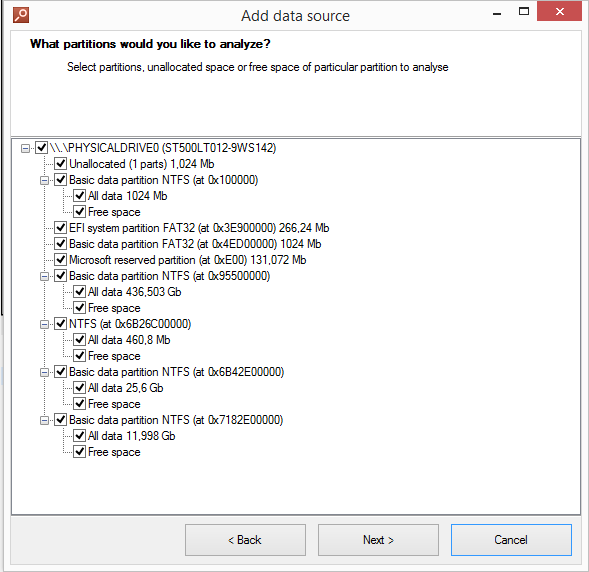
Deleting Evidence or Using Privacy Protection and Disk Cleaning Tools
Another type of naive anti-forensics is using freeware or commercial disk cleaners or privacy protection tools. Most, if not all such tools are not designed specifically for anti-forensics, providing more peace of mind to their users than actually countering forensic efforts. Traditionally, such tools have been created to protect the privacy of the user as opposed to purposely destroying evidence. Most privacy protection tools and many disk sanitizers are effective against casual observers, but leave many traces behind that can be easily discovered during an investigation.
Many disk cleaners will clean up the following:
- Cache and history for popular Web browsers
- Chat logs produced with Skype and some other popular instant messengers
- Provide “secure delete” option to wipe files
- Clean some (but almost never all) of the following: jumplists, thumbnails, registry items, Skype chatsync, etc.
In our experience, we have never encountered a single disk cleaner/privacy protection tool that would consistently destroy every piece of evidence an investigator would be looking for. Some of the things that were able to discover after running a bunch of disk cleaning tools were:
- Deleted digital pictures, but did not clean thumbnails cache
- Deleted documents, but did not clean Windows jumplists
- Deleted but did not wipe data such as browsing cache and history
- Deleted main Skype database but did not touch chatsync
- Failed to delete files that were currently opened (e.g. deleted files from the browser cache but could not delete the index database)
- Deleted files but left corresponding Registry entries intact
By using forensic tools, investigators can counter many of these measures. Let us briefly look at what can be done to locate evidence after it has been cleaned by the user manually or using one of the privacy protection tools.
Deleted Pictures
Windows OS is designed in such a way that it has many hidden and little known places that keep remnants or traces of evidence. One of these places is the Thumbnail cache. If a suspect used a privacy protection tool or securely wiped one or more pictures and denies their existence, it’s not the end. Let’s have a look into the Thumbnail cache.
Windows keeps thumbnail-sized copies of many file formats including pictures, PDF files, compatible RAW (digital negative) formats, presentations and documents stored on the computer in thumbnail cache. Files in JPEG, GIF, DOC/DOCX, XLS/XLSX, PDF, and dozens of other formats will leave traces in the form of small preview images long after the original file is deleted. If a certain format is not supported by Windows, third-party extensions are available and often installed with corresponding applications.
The system keeps file thumbnails even if the original image has been deleted. This gives investigators a chance to find a smaller version of the picture of interest in Windows Thumbnails. Thumbnails are indirect but strong pieces of evidence. It is worth mentioning that if Windows (or the suspect) deletes a thumbnail item, experts can attempt to recover it with file carving.
When analyzing the computer for evidence, digital forensic tools implement a complex approach including a combination of techniques to recover deleted data or discover external metadata that belongs to deleted files. When looking for deleted pictures, the tool will normally carve the disk that used to contain images. In some cases, the data can be recovered from unallocated space with carving. If, however, there are seemingly no traces of deleted pictures anywhere on the disk, it is worth looking in the system Thumbnail cache.
Different versions of Windows keep thumbnails in different places. Windows XP and earlier create a hidden file named Thumbs.db in the same folder where the pictures are stored. When deleting the entire folder with pictures, Thumbs.db would typically also get deleted.
In addition to Thumbs.db, Windows XP Media Center maintains a video thumbnail cache file named ehthumbs.db.
Windows Vista, Windows 7, 8, 8.1 and Windows 10 have all of their thumbnails stored in a single location, usually %userprofile%\AppData\Local\Microsoft\Windows\Explorer
The files are named thumbcache_xxx.db, where “xxx” is a number. Here is a brief
overview of thumbnail locations in different versions of Windows:
- Windows XP and earlier: Thumbs.db alongside pictures
- Windows XP Media Center: also ehthumbs.db for videos
- Windows Vista, Windows 7, 8, 8.1 and Windows 10: thumbcache_xxx.db (numbered by size) centrally located at %userprofile%\AppData\Local\Microsoft\Windows\Explorer
If the expert needs to find proof of existence of a certain picture, yet the image itself was deleted or accessed from a removable device (e.g. a USB flash drive that is no longer available), the thumbnails storage folder can often help locate the required evidence.
Windows thumbnail cache contains reduced versions of images that were either viewed or listed in a folder. Since Windows Vista, thumbnails are kept on the disk even if the original picture is deleted, or if the original was located on a removable drive.
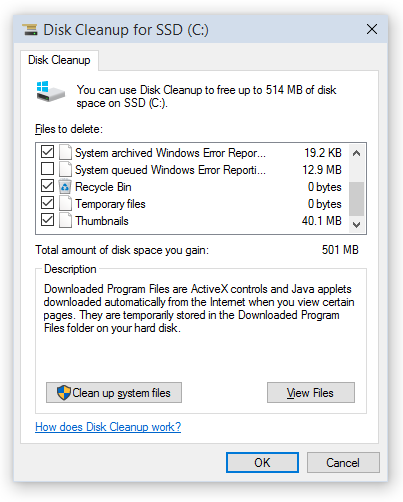
Thumbnails are relatively little known and often left out by third-party disk cleaning tools. However, Microsoft’s Disk Cleanup Wizard supplied with recent versions of Windows does clean the thumbnail cache properly. However, unlike many third-party privacy protection tools, Disk Cleanup Wizard does not run on a schedule and has to be launched manually every time the user needs to clean up their disk.
When analyzing a PC, experts have an option of locating the thumbnails manually by searching (or carving) for Thumbs.db (in Windows XP) or analyzing the content of the %userprofile%\AppData\Local\Microsoft\Windows\Explorer folder in Windows Vista, Windows 7, 8, 8.1 and Windows 10.
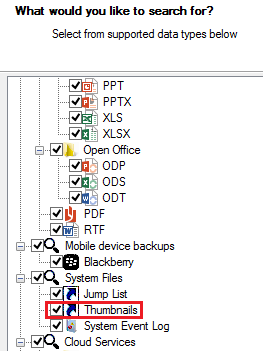
Automating thumbnail analysis is possible if using a digital forensic tool. In Belkasoft Evidence Center, thumbnails can be acquired automatically if the corresponding option is enabled when searching for evidence.
Deleted Programs and Documents
While most digital investigators know about Windows Registry, not everyone has heard about Jumplists. Jumplists contain information on documents, pictures, applications and other types of files being viewed, opened, launched or otherwise accessed by the user. Jumplists do not go anywhere even if the original file is deleted. Interestingly, jumplists are generated for files accessed from remote or external devices. Such jumplists also remain in the system even after the external device is removed, so they can be used as proof of access to a certain file that is no longer available.
Jumplists are a valuable source of information about files being used on the system. They are little known by the criminals. For this reason, they are rarely cleaned, and can trace back to the day the operating system was first installed. Jumplists can be used as definite proof of access. They contain full name and path to the file being accessed, computer name and MAC address, access date and time, and application used to open the file.
Technically speaking, jumplists are stored as little files in plain text format. They are stored at the following location:
%appdata%\microsoft\windows\recent\automaticdestinations\*
For example, they could be stored at the following path:
c:\Users\USERNAME\AppData\Roaming\microsoft\windows\recent\automaticdestinations\*
(where USERNAME is the name of the Windows account being investigated).
What is the practical use of Jumplists? Let us say the suspect denies the use of a document named “my.doc”. If the document was deleted securely with a tool such as CCleaner or if it was opened from a removable drive (e.g. a USB stick), there would be no trace in the system that the file has ever existed. However, if that file was ever opened, Windows will record information about the event in a corresponding Jumplist. The Jumplist will contain information about the name of the file, its full path, as well as the date and time of the last access. In this scenario, the investigator will get a definite proof of access to a certain file. On many systems Jumplists are available with dates going all the way back to the day the operating system was first installed.
Jumplists are also great when it comes to SSD drive analysis, allowing investigators discover files that existed on the disk before TRIM and garbage collection wiped deleted evidence.
Locating Jumplists with Belkasoft Evidence Center is as easy as selecting the corresponding check box when scanning media:
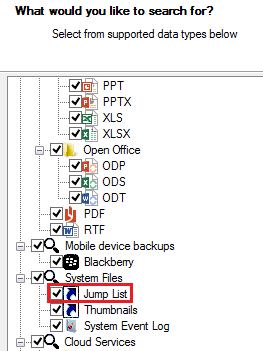
Deleted Skype Database
Cleaning chat logs is yet another example of naive anti-forensics. Since it is not possible to delete files opened by running applications, many privacy protection tools will simply delete everything except the main database. Users can manually clean their Skype histories from Skype settings.
The thing is, Skype is an old app. While employing a modern SQLite database to maintain history, Skype still keeps some internal data in a proprietary format in the “chatsync” folder. The content of that folder may reveal chunks and bits of user conversations. While the format is not officially disclosed, there are tools available that can analyze such files (e.g. Belkasoft Evidence Center). Thus, if chatsync folder exists, there are definite chances to recover Skype chats even if one have failed to recover a deleted Skype database.
Deleted SQLite Records
SQLite is a de-facto standard database used by thousands applications to keep settings, histories and other data. SQLite is used by iOS and Android apps, and employed by desktop tools such as Skype, Chrome, Firefox, and a wide range of instant messaging applications such as WhatsApp and iMessages.
Regularly cleaning browsing and conversation histories helps maintain the illusion of privacy with computer users where in fact deleted records may not immediately disappear. Instead, these records might be placed into so-called “freelist”.
Simplified analysis of SQLite databases is often concluded by opening a database file in a database viewer instead of using a proper forensic tool. The obvious drawback of using a free or commercially available database viewer for examining SQLite databases is the inherent inability of such viewers to access and display recently deleted (erased) as well as recently added (but not yet committed) records. On the other hand, forensic tools such as Belkasoft Evidence Center will look inside all available sources, often recovering records that have been deleted by the user.
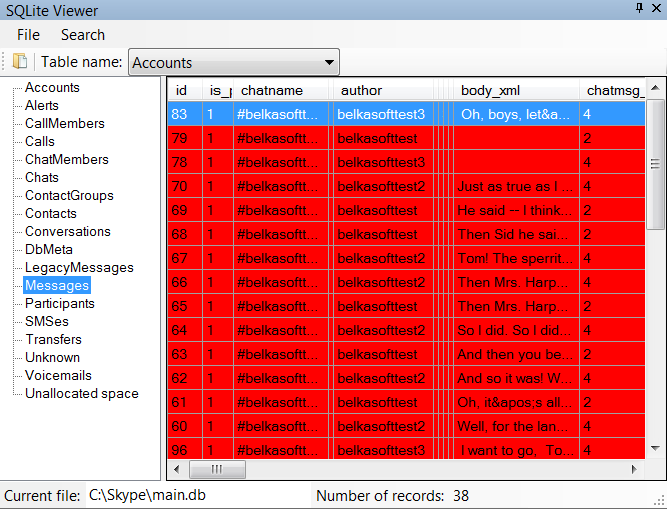
The latest version of Belkasoft Evidence Center also comes with enhanced SQLite analysis algorithms, allowing the tool to process even huge databases in a matter of seconds. Fully functional trial version of Belkasoft Evidence Center is available for evaluation at: https://belkasoft.com/trial.
More information about recovering deleted records from SQLite databases is available in the following article: "SQLite Forensics with Belkasoft X".
Stay tuned
In the first part of this whitepaper we mainly focused on describing the most common among the basic ways of applying anti-forensic measures, such as deleting or changing certain types of files manually or using privacy protection and cleaning tools, and how to deal with those if we are investigating a suspect’s machine. In the next part we will talk about some slightly more advanced anti-forensic techniques, in particular, how to deal with formatted or otherwise wiped drives as well as how to bypass encryption and anti-debugging protection while looking for digital evidence. The second part is coming next week—take a look at our other articles.About the authors
Oleg Afonin is Belkasoft sales and marketing manager. He is
an author, expert, and consultant in computer forensics.
Danil Nikolaev is Belkasoft sales and marketing manager,
co-author, and content manager.
Yuri Gubanov is a renowned digital forensics expert.
He is a frequent speaker at industry-known conferences such as CEIC, HTCIA, TechnoSecurity,
FT-Day, DE-Day and others. Yuri is the Founder and CEO of Belkasoft, the manufacturer
of digital forensic software empowering police departments in about 70 countries.
With years of experience in digital forensics and security domain, Yuri led forensic
training courses for multiple law enforcement departments in several countries.
You can add Yuri Gubanov to your LinkedIn network at
https://linkedin.com/in/yurigubanov.
Contacting the authors
You can contact the authors via email:
sales@belkasoft.com
Follow Belkasoft on Twitter: https://twitter.com/Belkasoft