Most would agree that the golden age of mobile forensics is over. There is no longer an easy way to get through the passcode in new iOS devices running the latest version of iOS. Chip-off acquisition is dead for iOS devices due to full-disk encryption, while physical acquisition of Apple hardware is dead since the introduction of 64-bit devices and versions of iOS 8 that cannot be jailbroken. Blackberries were highly resistant to chip-off acquisition from the beginning, and Android is getting there quickly. In this whitepaper, we will look into the current state of mobile forensics for the different platforms and devices, analyze current trends and attempt to predict how mobile forensics will look in the years ahead.
To gather these predictions, Belkasoft analyzed state-of-the-art tools, methods and hardware offered by leading manufacturers, and interviewed experts working for manufacturers of digital forensic products. Since manufacturers often specialize in specific areas (e.g. producing equipment for breaking iPhone passcodes), we questioned multiple representatives to be able to see the whole picture. Today, we are ready to share our findings.
iOS Forensics
Since Apple uses full-disk encryption with passcode-dependent, hardware-based encryption, chip-off acquisition has not been a possibility for a long time. The following acquisition methods are available for Apple devices:
- Sending the device back to Apple. Generally available to government agencies and law enforcement. Only for iOS versions prior to iOS 8.
- Physical acquisition. A non-destructive acquisition method allowing to obtain the full image of the device via the standard Apple cord.
- Logical (backup) acquisition. Deals with offline backup files produced by the device being analyzed.
- Over-the-air acquisition. Downloads information from the iCloud.
Let us briefly review the benefits, drawbacks and current trends for each acquisition method.
Sending to Apple
Sending devices for acquisition directly to Apple used to be a viable strategy, but not anymore. With the release of iOS 8, Apple explicitly states in their Privacy Policy that the new system is so secure that even Apple themselves cannot access information inside the device if the correct passcode is not known (https://www.apple.com/privacy/government-information-requests/). Thus, modern devices running the latest version of iOS can only be acquired this way if the correct passcode is known. By June 2015, more than 80% of iOS devices were running iOS 8, so the chances of actually handling a device with an older version of iOS are becoming slim.

iOS Physical Acquisition
When it comes to physical acquisition, the technique only works for jailbroken 32-bit devices (both conditions must be met), or 32-bit devices with a known passcode that can be jailbroken by the investigator. Compared to Android, relatively few Apple users install jailbreak. Since there is currently no jailbreak for the latest version of iOS available, and all new devices are using 64-bit circuitry anyway, physical acquisition will only work in rare cases (with the exception of developing countries where older 32-bit Apple hardware still occupies a major market niche).
iOS Logical Acquisition
If a passcode is known, or there is a way of finding it out, investigators can make the device produce an offline backup via iTunes. The backup can then be analyzed, but with some restrictions:
- Device secrets (items stored in the keychain) will only be available if the backup was password-protected (and will NOT be available in backups saved without a password). Somewhat counterintuitively, if you have a device that is configured to produce backups without password protection, setting a known backup password and entering that same password in the forensic tool will enable access to more information compared to analyzing non-protected backups.
- Cached items such as downloaded mail are not available in backups.
- If the device is configured to produce password-protected backups, changing that password is not possible if the password is not known. According to Apple, “If you forgot your [backup] password, the only way to turn off backup encryption on your device is to erase your device and set up as new. Erasing removes all data from your device.” (https://support.apple.com/en-gb/HT203790). In other words, resetting the password is not an option if you do not know it already, and backups protected with an unknown password must be broken into by using forensic tools without any timeframe or success guarantee.
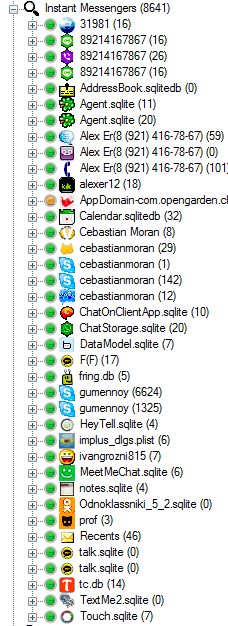
Other than that, there is a great number of forensically important items that you can find inside an iTunes backup using forensic tools. Our tool of choice Belkasoft Evidence Center. The picture below illustrates how the tool was able to extract over 8 thousand instant-messenger related artifacts from a sample iTunes backup:
Over-the-Air Acquisition (iCloud)
Finally, there is a way to acquire the content of Apple devices by downloading backups from iCloud.
iCloud is a cloud service available to Apple customers. 5 GB of cloud storage are available free of charge, and up to 50 GB can be purchased for a fee.
Apple designed a very convenient system for backing up devices to the cloud. Backups are incremental and occur automatically every time the device is put on a charger while locked and connected to a known Wi-Fi network (all conditions must be met). Back in 2012, about 33% of Apple customers were using iCloud. While no recent statistics are available, we can suggest that iCloud usage has increased dramatically, with the majority of Apple customers backing up their information into the cloud.
Cloud backups contain all of the same information as offline backups produced via iTunes. iCloud backups can be retrieved with forensic software (e.g. Elcomsoft Phone Breaker) if the user’s Apple ID and password are known, or if a binary authentication token from the user’s computer is available. Information can also be obtained directly from Apple by law enforcement with government request.
Android Forensics
Acquisition methods available for Android devices differ significantly.
- Sending the device to the manufacturer for data extraction. Generally available to government agencies and law enforcement for most domestic devices. May not be available for international models (e.g. no-name Chinese phones).
- Physical acquisition. A non-destructive acquisition method allowing to obtain the full image of the device via a USB cord and forensic software.
- JTAG forensics. Retrieves information via the phone’s Test Access Port.
- Chip-off acquisition. Requires the removal of memory chips. Produces raw binary dumps.
- Over-the-air acquisition. Involves downloading information from Google Account.
Sending to Manufacturer
Sending the device to its manufacturer may be a viable acquisition strategy if the device is unavailable via other means. For example, Samsung, who is the number one seller of smartphone devices in the US, has an official policy to support information extraction when serving a government request.
Notably, this approach may not be available in the case of international devices (in particular, no-name and C-brand smartphones originated from China). On the other hand, most Chinese devices are not secured in any reasonable way, and can usually be acquired via physical acquisition.
Android Fragmentation
Android is a highly fragmented platform with several hundred manufacturers and many thousand device models (source: http://opensignal.com/reports/2014/android-fragmentation/). In a report dated August 2014, OpenSignal states: “We have seen 18,769 distinct devices download our app in the past few months. In our report last year we saw 11,868”. According to the same report, “Samsung have a 43% share of the Android market”, as illustrated by the chart:

Unlike iOS, Android has multiple major versions of the OS running on the plethora of devices. The official source ( https://developer.android.com/about/dashboards/index.html?utm_source=suzunone ) demonstrates slow adoption of the latest Android 5 ‘Lollipop’ compared to blazing fast adoption of the latest iOS 8 by Apple users.

All this means that manual acquisition is probably out of the question (unless performed on a small sample of well-known models), with specialized software becoming the necessary middleman.
Notably, over-the-air acquisition (Google Account analysis) is the only method that has nothing to do with hardware fragmentation. Cloud acquisition will inevitably change as full data backups get introduced in Android M, but other than that it’s not dependent on the version of Android OS either.
Physical Acquisition of Android Devices
In this short overview, we will not go into comparing security implementation details between the different versions of Android, device manufacturers and carrier requirements. We will only give a qualitative assessment. Depending on your choice of forensic acquisition tool, the phone’s make, model, carrier, Android version, user settings, root status, lock status, whether or not the PIN code is known and whether or not the “USB debugging” option is enabled, you may or may not be able to perform physical acquisition of a particular device. (Translated to human language, the above paragraph means “you won’t know until you try”).
With all that said, a random Android device will most probably be a Samsung phone (a 43% probability). It will most probably have a locked bootloader, being protected with a 4-digit passcode, without root, and with USB debugging disabled (the user must alter certain phone settings explicitly in order to change any of the above, which is not always easy and even not always possible). Whether or not the device will be encrypted is a hit or miss (most devices are not encrypted out of the box, but enabling encryption is as easy as setting a PIN code and toggling a single setting). In other words, you will have to rely on the quality of your extraction toolkit in order to be able to perform physical acquisition of said device.
JTAG Forensics (Android)
JTAG forensics is an advanced acquisition procedure, which uses the standard JTAG port to access raw data stored in the connected device. By using specialized equipment and a matching device-specific JTAG cable, one can retrieve the entire flash memory contents from compatible devices. Notably, JTAG acquisition is often available even for locked, damaged or otherwise inaccessible devices.
It is important to realize that JTAG forensics is a low-level acquisition method that will return raw content of the memory chips. If whole-disk data encryption is present on the device (either pre-activated by the manufacturer or enabled by the user), JTAG acquisition will produce an encrypted image. In order to decrypt the raw image, one will need access to the phone’s higher-level API, which, in turn, requires supplying the correct passcode. Notably, whole-disk encryption is active out of the box on many Samsung phones, Nexus 6 and Nexus 9 devices as well as some other flagship phones sold by leading manufacturers.
Despite that, JTAG forensics remains a viable acquisition method for compatible Android devices. With Google’s decision to back away from encrypting new Android 5.0 devices by default ( http://arstechnica.com/gadgets/2015/03/google-quietly-backs-away-from-encrypting-new-lollipop-devices-by-default/ ), manufacturers are under no obligation to enforce whole-disk encryption in their existing devices receiving an upgrade to Android 5.0/5.1 as well as newly released phones running Lollipop out of the box. You can use JTAG forensics on compatible phones only if they are not using whole-disk encryption.
Once the acquisition is completed, we recommend using Belkasoft Evidence Center for JTAG analysis. The product will automatically extract and analyze dozens of forensically important artifacts, including contacts, call logs, geolocation data messenger chat histories, browsing history, etc. Learn more: https://belkasoft.com/jtag-analysis.
Chip-Off Acquisition
Chip-off acquisition is a highly advanced, lowest-level destructive acquisition method requiring physical de-soldering of memory chips and using specialized hardware to read off their content. Chip-off acquisition is often used as a last resort. If whole-disk encryption is not enabled, chip-off acquisition will produce the full binary image of the device complete with unallocated space.
As opposed to computer hard drives, in the world of mobile forensic the lowest-level access is not always the best thing. Granted, chip-off acquisition will produce the complete raw image of the memory chip(s) installed in the device. However, the investigator will have to deal with issues such as block address remapping, fragmentation, and encryption. In the case of Apple devices, Samsung phones and many other devices encryption is enforced out of the box and cannot be bypassed during or after chip-off acquisition even if the correct passcode is known. As a result, chip-off acquisition is limited to unencrypted devices or devices using encryption algorithms with known weaknesses.
Nandroid Backups
Examiners analyzing a rooted Android device have yet another venue for extracting the full and complete file system of the device by generating a so-called NANDroid backup. Nandroid backups can be created by booting the device into a custom recovery (by either issuing an ADB command or, of USB Debugging is not enabled, by holding the Vol- and Power keys on the device) and selecting the corresponding menu item.
The following conditions must be met in order to produce a Nandroid backup:
- Bootloader is unlocked and custom recovery (e.g. CWM or TWRP) is installed, -or-
- The device is rooted, Busybox package installed and a Nandroid backup app such as this is used
Note that a Nandroid backup app can be used to produce a full NANDroid backup even if the bootloader is locked and no custom recovery is available when Busybox package is installed and a Nandroid backup app is used on a rooted device. Root is generally not required to make or restore Nandroid backups if the operation is performed through custom recovery.
If all of the above conditions are met, the expert can boot into custom recovery and make the device dump the content of its file system onto an SD card (if supported by the device) or an OTG flash drive (again, if supported by the device). There is also a small chance to discover existing Nandroid backups in the device being analyzed.
NANDroid backups are standardized between different recoveries. NANDrpod is a de-facto standard format for storing Android system backups. Nandroid backups can be parsed and analyzed by forensic tools such as Belkasoft Evidence Center. This product supports 100+ kinds of mobile artifacts for iOS and Android. This includes both popular applications like Skype, WhatsApp, Viber, Foursquare,Kik Messenger, and less known ones like FireChat, Tango, Grindr, ooVoo, and many more.
Over-the-Air Forensics: Google Account
There are currently no full cloud backups available to Android users. Current versions of Android do not back up application data; instead, only the list of applications is generally backed up from Android devices. As a result, over-the-air forensics similar to iCloud acquisition is not available for Android devices. Apparently, this is about to change in the coming Android M. However, over-the-air forensics is far from being dead.
Google has mastered data collection. The company collects and maintains massive amounts of data from users of its services. The information is collected from all devices under the same Google ID including phones, tablets, desktop and laptop computers regardless of the operating system (if at least one service under the Google Account umbrella has been used).
Accessing such a massive amount of data is extremely tempting. With the user’s Google ID and password, forensic experts can access and analyze all information from the user’s Google Account including Gmail, Contacts, Google Drive data, synced Chrome tabs and bookmarks, passwords, registered Android devices and their location history, and a lot of other information.
Windows Phone 8 Forensics
Windows Phone 8 and 8.1 is a relatively new contender on the mobile arena. The platform enjoys a global market share of 4.2% (Q1 2015), while showing a much higher adoption rate in select markets (namely Spain, France, Germany, Italy and the UK).
The Windows Phone 8 platform does not by default use full-disk encryption on devices sold to consumers. However, Windows Phone devices used in corporate environments are always encrypted.
The Windows Phone platform is quite secure, and does not allow for logical or physical acquisition techniques. This means that traditional forensic acquisition tools such as Belkasoft, Cellebrite and XRY cannot acquire information from a locked Windows Phone by connecting via a USB cable.
At this time, two vectors of attack exist for Windows Phone devices: over-the-air acquisition of the phone backup from Microsoft Account and JTAG/chip-off extraction.
Windows Phone Cloud Forensics
The Windows Phone OS comes with the ability to create periodic backups of the content of the device to Microsoft cloud storage. These backups work similar to iOS, and contain much of the same information including application data, synced passwords, and device configuration settings.
Cloud backups can be downloaded from the user’s Microsoft Account with tools such as Elcomsoft Phone Breaker providing that their Microsoft Account login and password are known. Alternatively, the data can be requested from Microsoft with a warrant.
Windows Phone 8 JTAG and Chip-Off Extraction
Forensic acquisition of non-encrypted Windows Phones comes down to either JTAG or chip-off extraction. Since Windows Phone 8 is a Windows-based OS, it uses NTFS as a file system and has many similarities to desktop windows platform. Notably, these methods will work with most publically sold Windows Phone 8 devices.
Windows Phone: Sending to Manufacturer
Unlike Apple, Microsoft does not enforce full-disk encryption out of the box. For this reason, Windows Phone devices can be sent to their original manufacturers accompanied with a warrant to have information extracted. Since Nokia smartphones (now manufactured by Microsoft under its own name) constitute the majority of Windows Phone units, Microsoft will be the final stop for most cases involving Windows Phone acquisition.
Windows Phone Page File Analysis
A large portion of Windows Phones’ data is stored inside page files, including information from both running and background apps. However, due to a different device architecture, Windows Phone page file format differs from the one of desktop Windows, so one will need a forensic tool that specifically supports Windows Phone page file. Belkasoft Evidence Center was the first forensic product with proper WP page file parsing. Carving pagefile.sys files with Belkasoft Evidence Center will allow you to find multiple types of artifacts, such as web pages, pictures, chats, as well as registry files and many more.
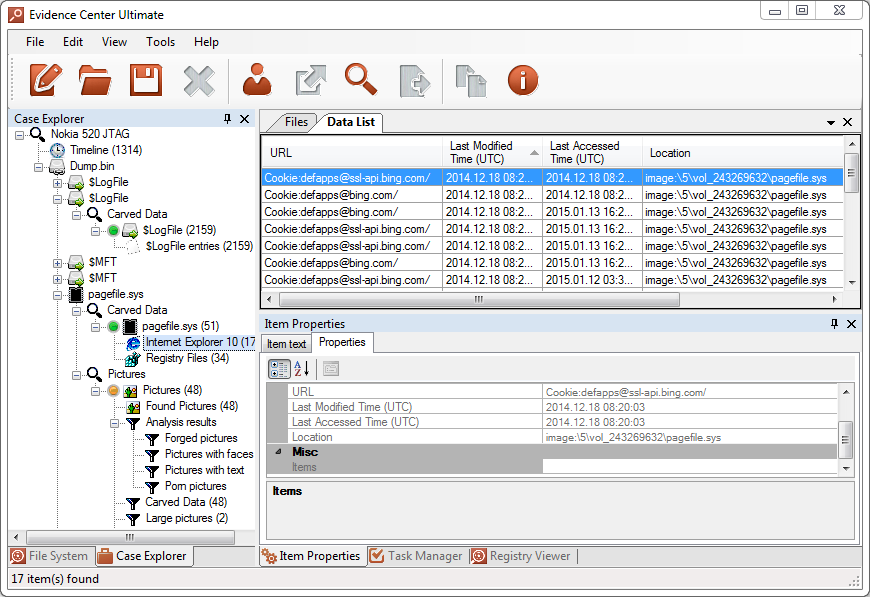
BlackBerry 10 Forensics
Once being a major player having a 43% share of the US mobile market back in 2010, the Canadian manufacturer today is a distant fourth. With only 1.5% of the US consumer market, BlackBerry devices are still commonly used in corporate environments.
From the very beginning, BlackBerries were secure. BlackBerry smartphones used full-disk encryption, making chip-off acquisition fruitless. Early-generation devices had an exploit allowing the attacker to break the encryption key offline by running an attack on a device-encrypted SD card. This is no longer the case today.
At this time, the only vector of attack on BlackBerry smartphones is accessing a BlackBerry backup file (or making the device produce a backup via BlackBerry Link), obtaining the suspect’s BlackBerry ID and password and using the login and password combination to decrypt the backup. If the backup is available, you can analyze it with forensic tools that support Blackberry backups, such as Belkasoft Evidence Center.
Breaking (or recovering) the password is not possible as information used for decrypting the backup is stored on (and is retrieved from) a BlackBerry server. However, a government request can be made to obtain the decryption keys from the company.
Mobile Forensics with Belkasoft Evidence Center
Belkasoft Evidence Center is an easy-to-use tool for both computer and mobile forensics. The tool has an extensive out-of-the-box support hundreds of mobile apps, what makes Evidence Center a keen choice to look for digital evidence inside phone backups, dumps, and images. The product supports all major forensic formats, including iTunes backups, Android backups, Blackberry backups, UFED physical and logical dumps, chip-off and JTAG dumps:

Among 100+ mobile applications that the product is able to extract data from are browsers (Safari, Chrome, Firefox, Opera), mailboxes (Gmail, Yahoo Mail), various messengers (Skype, WhatsApp, Viber, Kik), and other apps (Facebook, LinkedIn, Foursquare, QIWI wallet).

To test the product, request a free fully functional trial license at https://belkasoft.com/trial.
Conclusion
In our view, the future of iOS forensics lies with over-the-air acquisition. Since many users configure their devices to maintain cloud backups, the data can be obtained from iCloud (or requested from Apple). The alternative to this is logical acquisition via offline (iTunes) backups, which may not be available if either device passcode or backup password are not known. We consider physical acquisition to be dead for recent Apple devices used with the latest versions of iOS.
When it comes to Android, physical acquisition is quite alive, and is the first technique to attempt. If the device is not rooted, the passcode is not known, and the “USB Debugging” option is not enabled, the outlook does not look bright (but there are still possibilities such as bootloader exploits). JTAG acquisition remains a viable option for compatible devices (if whole-disk encryption is not used), while chip-off acquisition can still be used as a last resort on unencrypted devices.
Offline backups are not generally available to Android users, yet they can technically be produced with certain manufacturers (e.g. via Sony PC Companion for Xperia smartphones). There are no full cloud backups available either (the upcoming Android M is about to change that, bringing Apple-like backups to Android). However, a lot of information can be retrieved from the user’s Google Account, including synced Chrome bookmarks, passwords, list of registered devices and their geolocation information, mail (Gmail) and calendar events, and so on.
Android is slowly becoming a secure platform. More devices feature whole-disk encryption out of the box. Each version of Android is more secure than the one it replaces. Android 5 is secure enough to become an obstacle on the way of physical acquisition; many forensic tools still do not support physical acquisition of devices running Android 5 unless the correct passcode is known. Full-disk hardware encryption is about to become the norm for Android devices in near future (2-3 years). For now, physical acquisition (as well as JTAG forensics) remain viable extraction options for Android devices, slowly losing their significance as the platform becomes more secure with more devices shipped encrypted out of the box.
Google collects a lot of information about its users. This information is collected from all devices under the same Google ID including phones, tablets, desktop and laptop computers regardless of the operating system (if at least one service under the Google Account umbrella has been used). Obtaining information from the user’s Google Account can deliver lots of valuable evidence. We can certainly notice a trend here, with Android device forensics being complemented (and at a certain point replaced) by cloud-based analysis of the user’s Google Account.
The upcoming Android M will feature full device backups – just like iOS. When (or if) this materializes, forensic experts will be able to perform cloud acquisition of Android backups similar to iCloud acquisition they can do today. Android M will be released in less than a year. It will probably be a matter of at least two years before the new system takes a noticeable number in the Android OS version chart.
About the authors
Oleg Afonin is Belkasoft sales and marketing manager. He is an author, expert, and consultant in computer forensics.
Danil Nikolaev is Belkasoft sales and marketing manager, co-author, and content manager.
Yuri Gubanov is a renowned digital forensics expert. He is a frequent speaker at industry-known conferences such as CEIC, HTCIA, TechnoSecurity, FT-Day, DE-Day and others. Yuri is the Founder and CEO of Belkasoft, the manufacturer of digital forensic software empowering police departments in about 70 countries. With years of experience in digital forensics and security domain, Yuri led forensic training courses for multiple law enforcement departments in several countries. You can add Yuri Gubanov to your LinkedIn network at http://linkedin.com/in/yurigubanov.
Contacting the authors
You can contact the authors via email:
research@belkasoft.com
Follow Belkasoft on Twitter:
https://twitter.com/Belkasoft
Subscribe to the blog:
https://belkasoft.wordpress.com
Our previous article: Acquiring Windows PCs
All articles by Belkasoft
Trial version of Belkasoft Evidence Center