Why choose Belkasoft X for digital forensics and cyber incident response?
Belkasoft X is a versatile software tool for digital forensics and cyber incident response investigations. It is the preferred choice of forensic investigators in over 100 countries worldwide, with this number constantly growing. But what exactly makes this product so popular?
- Belkasoft X is an all-in-one tool that allows you to analyze multiple data sources acquired from different electronic devices
- The low-hanging digital forensic fruit forensics approach helps you quickly extract information from 1500+ artifact types
- The product's forensic data recovery features can help restore deleted information
- The tool supports every step of your investigations, from acquisition and analysis to building reports and sharing evidence
- Built-in tools for low-level forensic analysis let you inspect device files and examine raw data conveniently
- Straightforward workflow and automation features streamline routine tasks, saving your time and resources
In this article, we will explore each of these benefits in detail, fleshing out the powerful capabilities embedded in the product.
All-in-one tool
Belkasoft X supports computer, mobile, drone, car, and cloud forensics—all in a single product. This approach allows digital forensics specialists to collect and analyze all devices and data sources relevant to an investigation in one case and examine them comprehensively.
Belkasoft X combines multiple modules for comprehensive DFIR investigations
Effortless low-hanging fruit forensics
Belkasoft X can detect and analyze over 1500 artifact types out of the box. Its automatic application data extraction, known as "low-hanging digital forensic fruit," is often sufficient to solve most cases involving internet browsing and communication, documents, and photos. This approach also helps you quickly track malicious files or uncover lateral movement and persistence mechanisms when investigating cyber threats.
With Belkasoft X's extensive artifact inventory, you do not have to know all data formats, file locations, encryption schemas, or signatures for carving files and individual records. The product supports all popular (and even lesser-known) applications, such as WhatsApp, Facebook, Telegram, WeChat, Wickr Me, Signal, major browsers, and mail apps such as Outlook or Gmail. It automatically extracts many valuable iOS system artifacts, including knowledgeC, Android system files, various incident response-specific artifacts, and more.
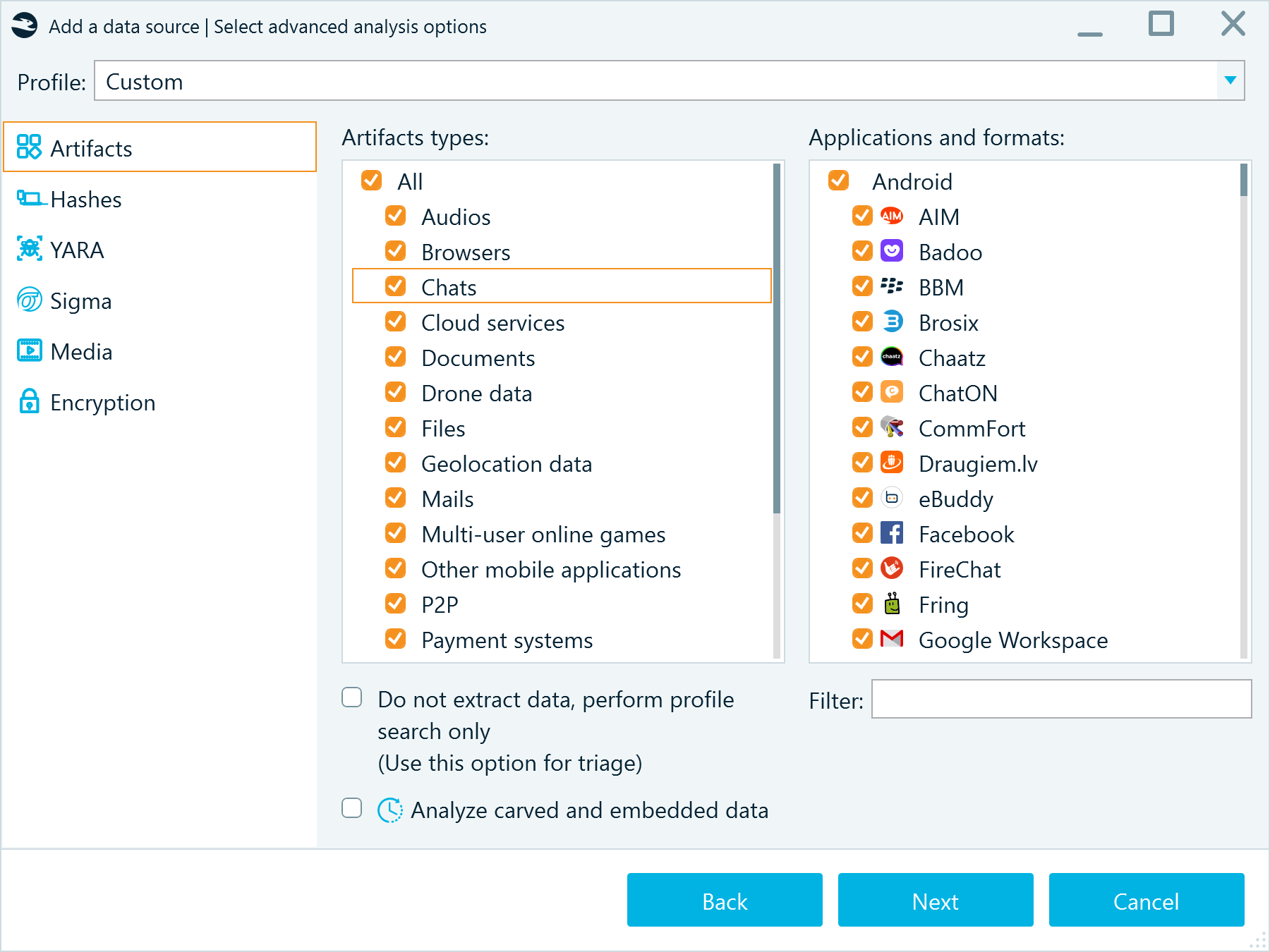
Belkasoft X allows you to select the artifact types and particular applications and formats to extract during the analysis
Moreover, when analyzing data sources, Belkasoft X searches for data in all potential locations, that is, not only in existing files but also in live RAM, pagefile, nested data sources (virtual machines, smartphone backups, and hibernation files), VCS snapshots, unallocated and slack space, and so on.
Forensic data recovery
With Belkasoft X's customizable file and artifact carving functions, Volume Shadow Copy analysis, and advanced SQLite forensics features, you can recover the maximum available data from forensic images, whether the data is still in files, deleted, or hidden in unallocated or slack space.
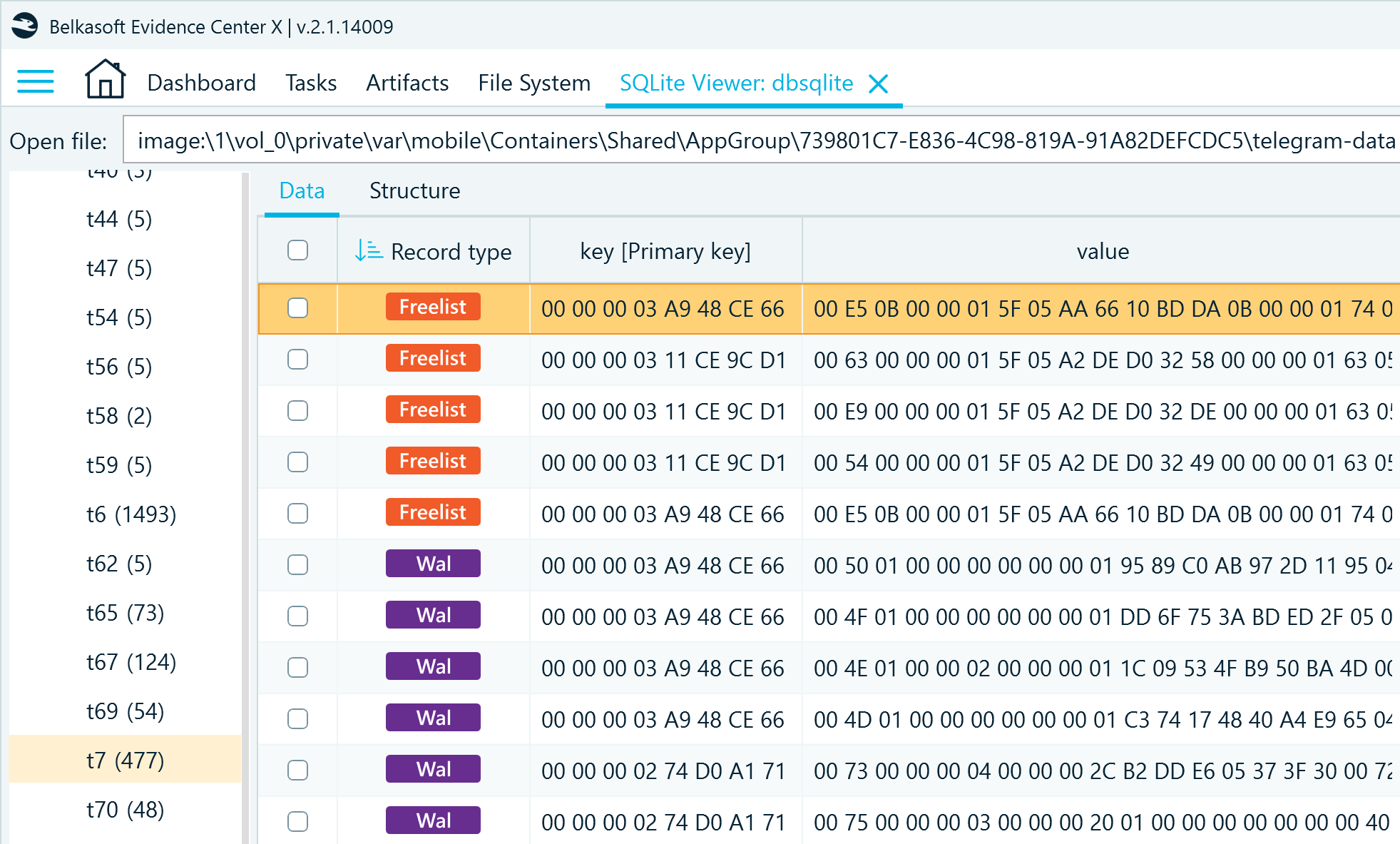
SQLite analysis helps you find freelists, write-ahead log, journal files, and SQLite unallocated space that may contain deleted and altered records
All-around support of DFIR tasks
Belkasoft X supports all stages of your investigations. During the acquisition phase, the product enables you to copy hard drives, create smart mobile device dumps, capture RAM, and download Google Drive, iCloud, and cloud-based application data.
Belkasoft X supports encrypted file search and password brute-force, helping you crack both file-based and disk-based encryption. The mobile device passcode brute-force enables you to unlock a number of iOS and Android device models when their passcodes are unknown.
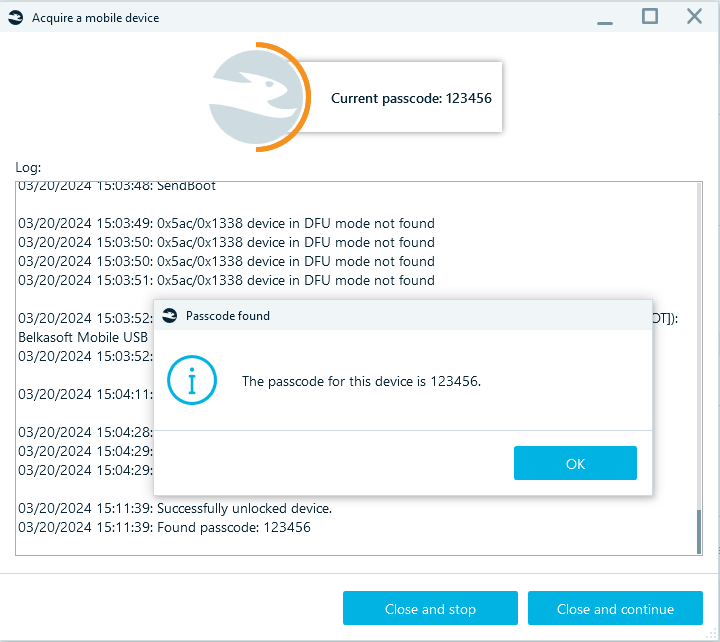
Mobile brute-force helps you bypass security restrictions and automatically guess passcodes on specific iOS and Android devices
Belkasoft X can parse physical and logical drives and drive images, memory dumps, JTAG and chip-off dumps, mobile device backups and full file system images, virtual machines, and drone data. In addition, it supports image formats created in other tools, like UFED, UFDR, GrayKey, or Berla.
The product's robust search capabilities and analysis features, such as Connection Graph, timeline, hashset analysis, and advanced picture and video analysis, streamline your examination tasks and enable rapid discovery of crucial facts. The built-in support of YARA and Sigma rules facilitates the search for traces of malware.
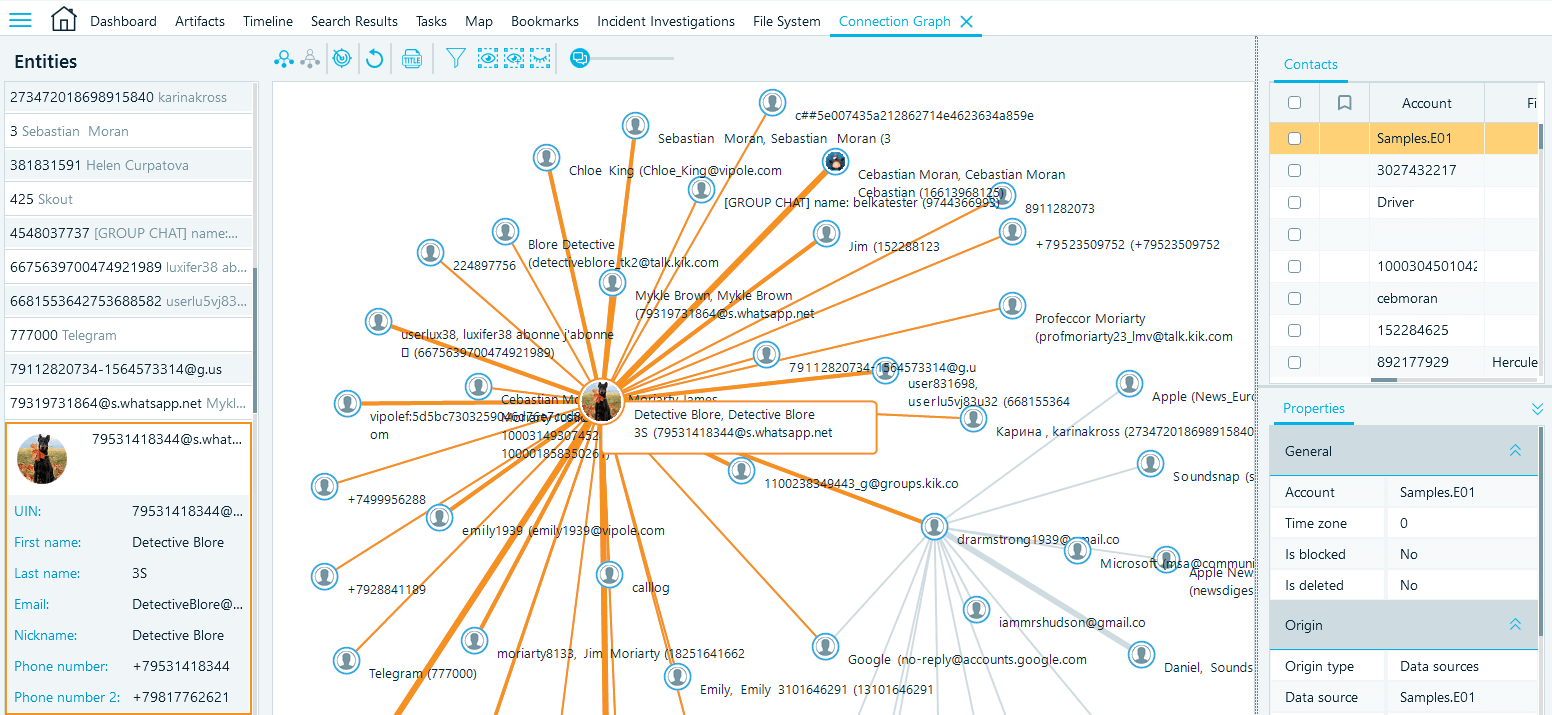
Connection Graph helps you visualize communication between individuals involved in a case
When it comes to documenting your findings, Belkasoft X provides convenient instruments for making organized bookmarks of artifacts and generating reports in various formats, including text, HTML, XML, CSV, PDF, RTF, Excel, Word, EML, KML, ProjectVIC JSON, Semantics21, and more.
The free Evidence Reader that comes with the tool allows you to create a portable copy of your findings and share them with fellow investigators in Belkasoft's user-friendly interface:
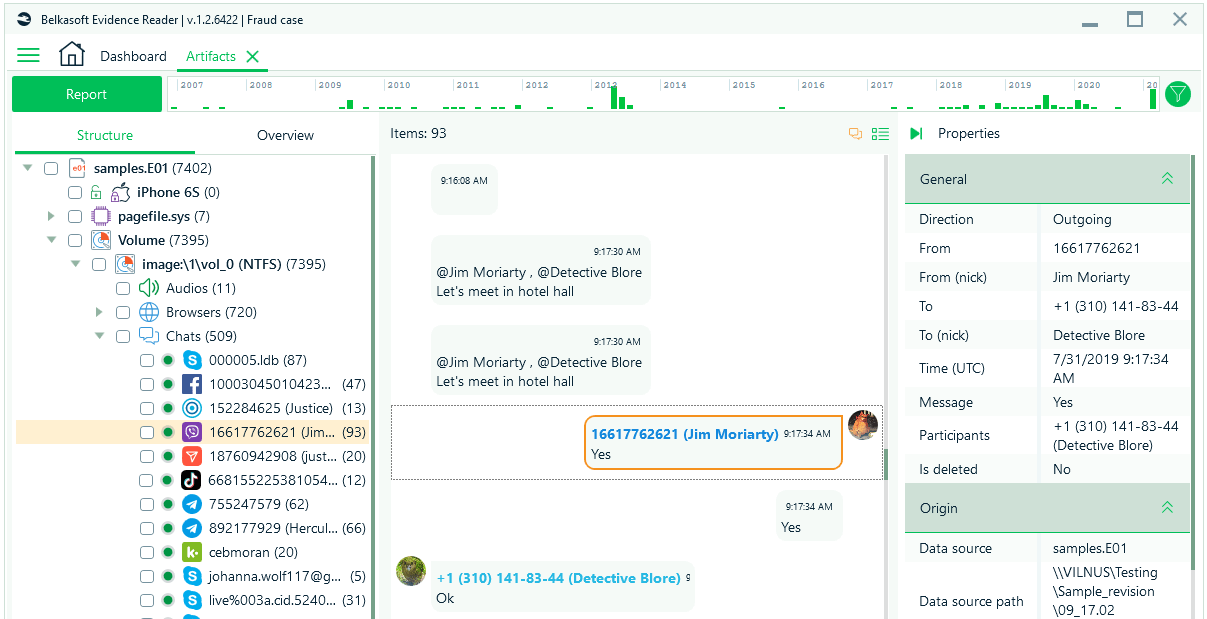
Evidence Reader can show all the exported contents of your case in read-only mode–at no charge!
Built-in tools for low-level forensic analysis
While automated extraction is usually enough, some tricky artifacts may require manual search and analysis. For such investigations, Belkasoft X provides a powerful File System Explorer that lets you view all volumes and partitions inside the device image with existing and deleted folders or files, and VCS snapshots.
When you need to dive deeper, Hex viewer enables you to investigate individual bytes, examine file partitions, convert binary values to various data types, create bookmarks, run custom carving, and apply various encodings.
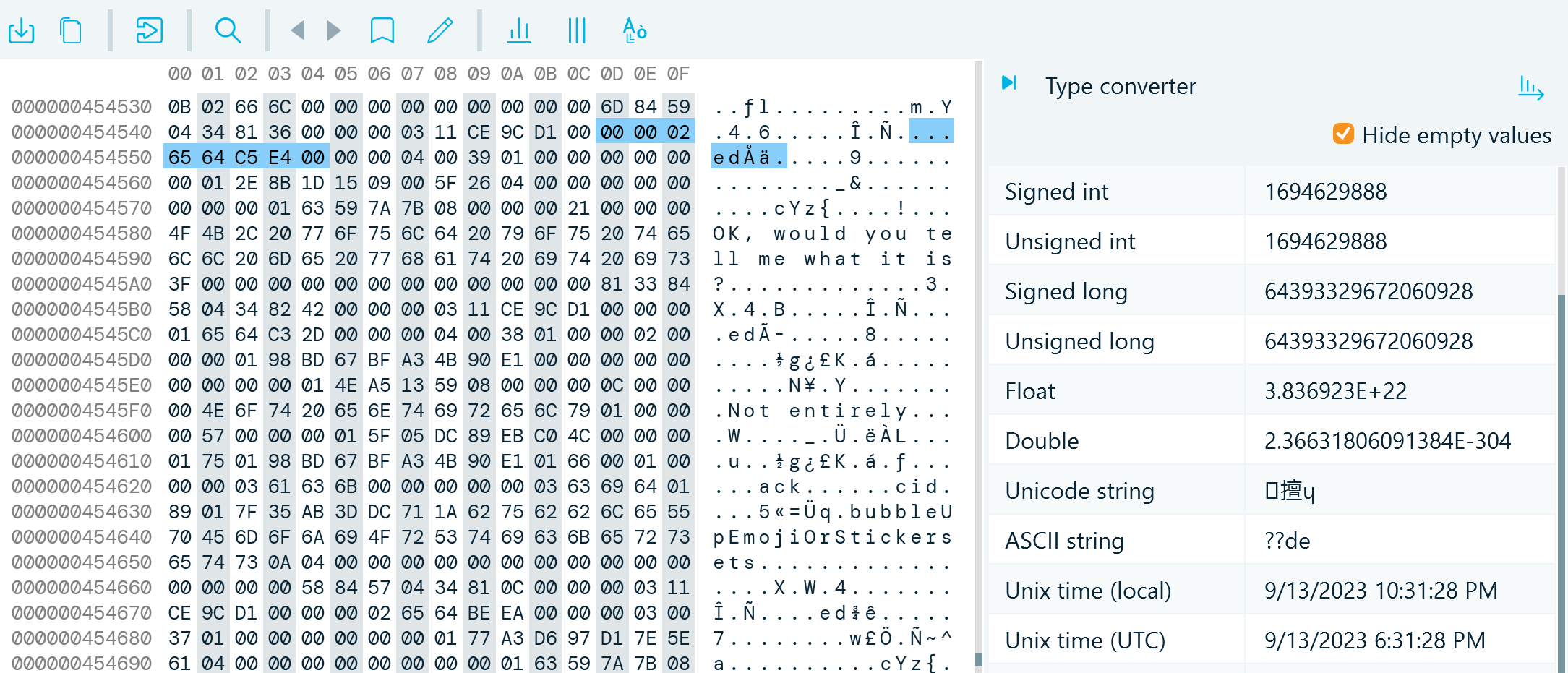
Hex viewer in Belkasoft X provides you with access to the low-level representation of data
PList, Registry, and SQLite viewers allow you to work more thoroughly with particular types of data and find additional insights that the automatic search was unable to discover.
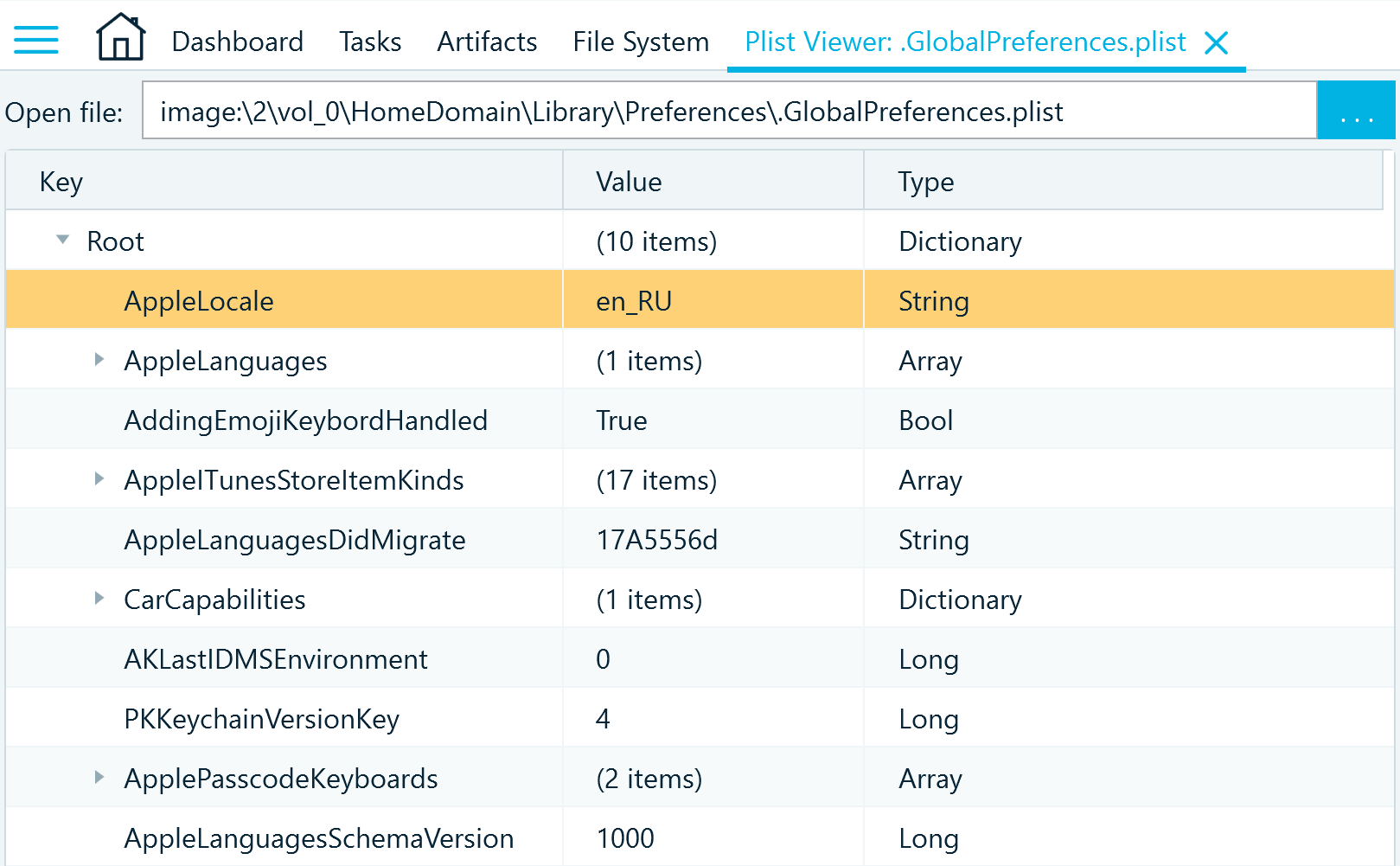
PList viewer helps you navigate the structured contents of "preference list" files
Straightforward workflow and automation
Belkasoft X offers a straightforward workflow, making it easy for users to get started with their digital forensics tasks. Achieving initial results through "low-hanging fruit analysis" is as simple as 1-2-3. Here is what you need to do:
- Add a device or dump to your case (or acquire it using the built-in acquisition features).
- Select the types of artifacts to look for.
- Enjoy reviewing the found results!
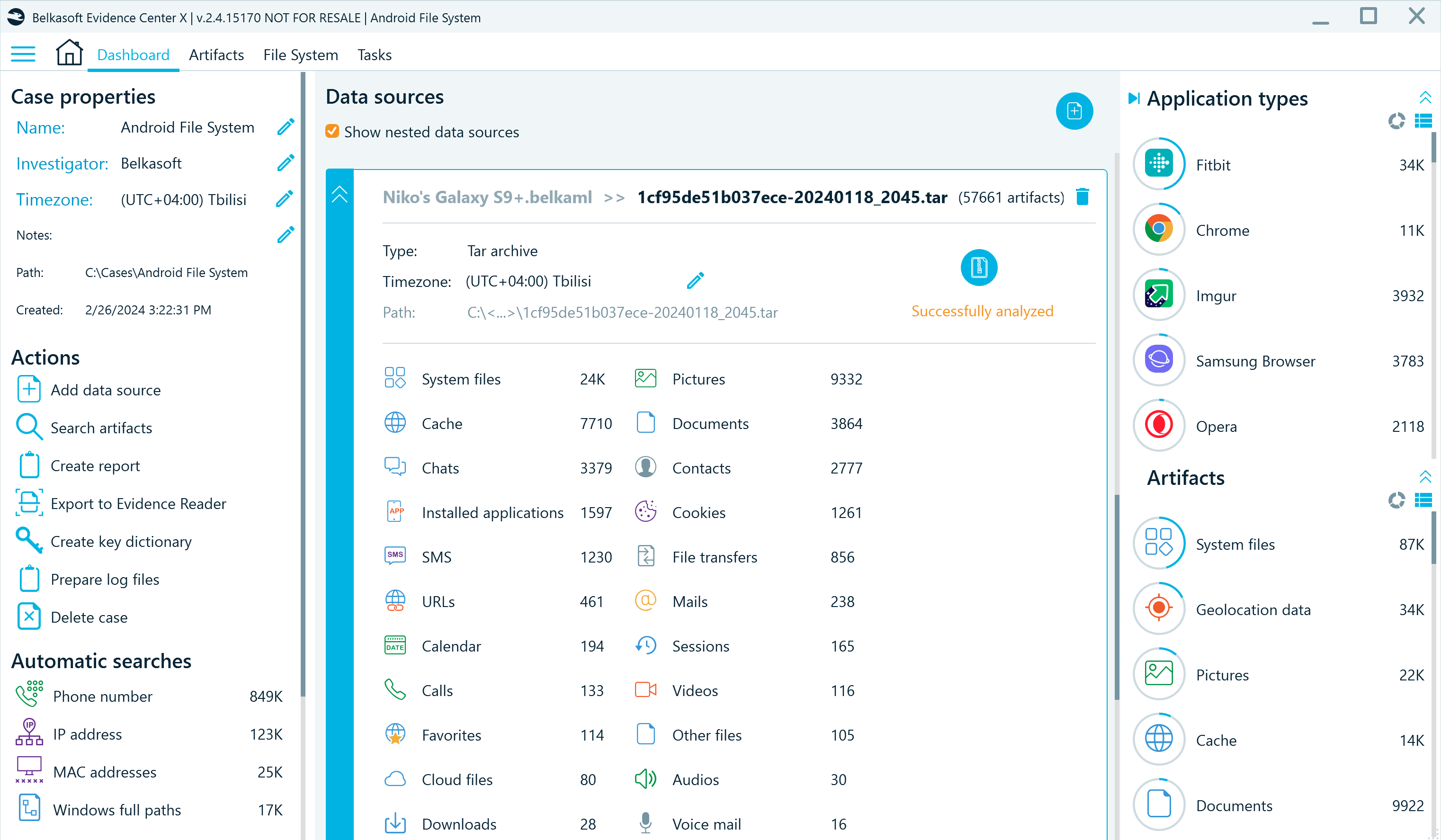
Belkasoft X's dashboard provides you with an overview of the extracted artifacts
Next, you can explore artifacts individually, run searches, delve into the source files, and, as a result, build reports of your findings. For routine investigation tasks, you can configure smart automated workflows and complete your work even faster with the Belkasoft X command line.
The product interface is so simple and intuitive that you can begin working in it right after the installation, skipping the weeks of paid training that some other products require for effective operation. It also includes guided product tours and video tutorials that help get you started with the tool's features or quickly bring new team members up to speed; however, for deeper insights, we recommend Belkasoft training.
Conclusion
Belkasoft X stands out as a versatile and comprehensive tool for digital forensics and cyber incident response. Its all-in-one capabilities, effortless low-hanging fruit analysis, and robust support for various DFIR tasks make it a preferred choice for professionals worldwide. Are you looking for a powerful yet user-friendly and cost-effective solution? Take the next step in your digital forensics journey by exploring Belkasoft X.
