Evidence Center is an all-in-one digital
forensic solution by Belkasoft—leading forensic software manufacturer. Why do
you need this product in your investigator's toolset?
1. Belkasoft Evidence Center (BEC) supports both computer and mobile forensics
Whether you have a laptop or an iPhone device, desktop computer or Android tablet,
the same BEC software can help you to understand what information is kept inside.
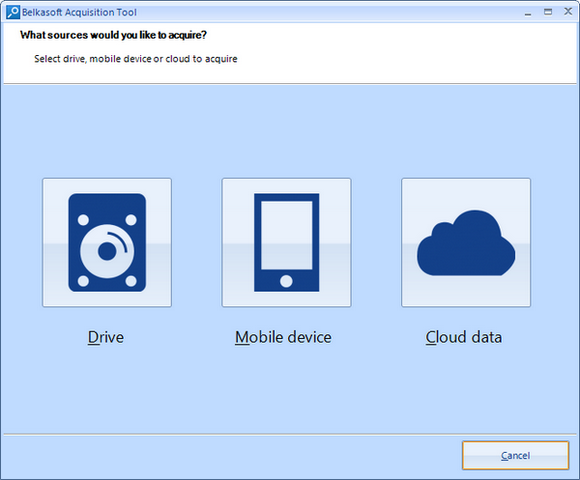
BEC helps you to acquire and analyze computers, mobiles, clouds and RAM
"My Agency has been using Belkasoft Evidence Center for 2 years now.
The software is a powerful robust Forensic tool with all the built in features
needed for a thorough examination for computers and cell phone images. I
highly recommend this great tool in any Forensic examiners arsenal of tools."
David Shelton, Chief Forensic Examiner at Advanced Technology Investigations,
LLC in Greensboro, NC USA
2. BEC recovers all available data
Doesn't matter if data is still kept in files or deleted, hidden in unallocated
or slack space, the product can easily reveal it by searching inside existing files,
carving using file or record signatures, analyzing Volume Shadow Copy and many other
forensically important areas (such as, for example, SQLite freelists).
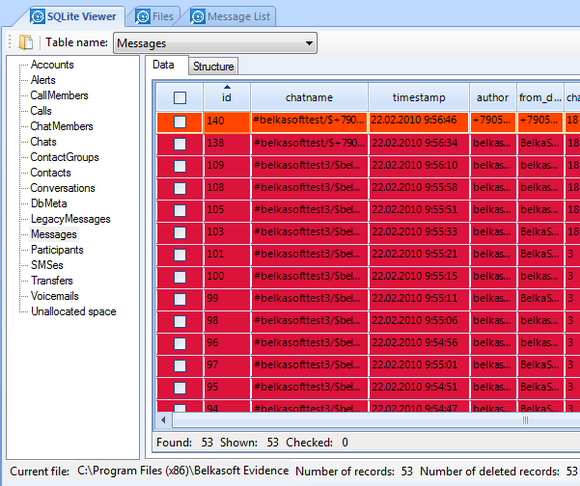
BEC recovers deleted SQLite records from a seemingly empty Skype database with
the help of SQLite freelist analysis
3. BEC supports all stages of your investigation
Starting from the acquisition phase, where the product helps you to copy a hard
drive, create a smart mobile device dump, capture RAM memory and even download Google
Drive or iCloud, to creation of reports in numerous formats, the product eases all
routine operations of your investigation.
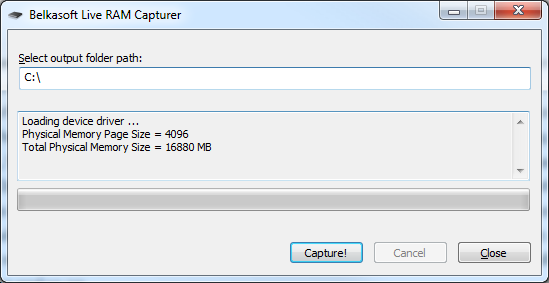
RAM Capturer, which is a part of BEC package, robustly dumps a running computer
RAM memory in kernel mode. The memory dump can then be analyzed in BEC for things
like social network communications, chats, in-private browsing and so on
4. BEC can extract more than 800 types of artifacts out of the box
Automatic extraction of application data, which we call "Low hanging digital
fruits analysis", can be enough to solve the vast majority of cases, where you are
investigating internet communications, documents or, say it, photos. The product
knows all popular (and even less known) apps, such as WhatsApp, WeChat, Snapchat,
Skype, major browsers and mail apps such as Outlook, office formats such as MS Word
or Open Office Spreadsheet, so you do not have to know data formats, file locations,
signatures for carving files or individual records, encryption schema, and so on.
Moreover, the product will find these data in all potential places, that is, not
only in existing files, but also in Live RAM memory, pagefile or hibernation files,
virtual machines, VCS snapshots, unallocated or slack space and so on.
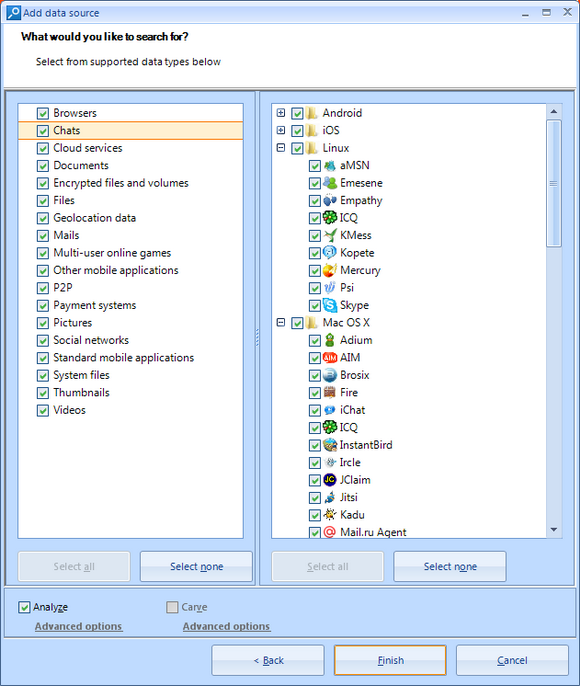
Easy to use artifact selection window allows you to choose from hundreds of different
apps to analyze
5. BEC is easy to use
Getting first results using "low hanging fruits analysis" is easy as 1-2-3. The
only few things you need to do are:
- Add a device or dump to your case (or acquire it using built-in acquisition feature)
- Select types of artifacts to look for
- Enjoy!
After the software finishes searching, all data will be
conveniently presented in different perspectives: by file system location, by
application profile and by type of data. Timeline will show you all events inside
the device sorted by time, bookmarks will help to mark important items, index-based
search will find keywords, including grep search and predefined search (e.g.
credit cards, SSN numbers, MAC or IP addresses and so on). The product interface
is so easy and intuitive that you can start using it right after the installation,
without weeks of paid training that some other products require in order to
operate effectively.
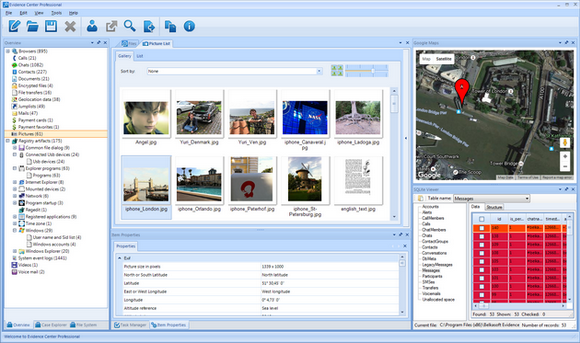
The product automatically extracts pictures from all available sources: from
files on a drive or dump, carved from unallocated/slack space, email attachments,
Windows thumbnail files, embedded in documents and so on from all available
sources: from files on a drive or dump, carved from unallocated/slack space,
email attachments, Windows thumbnail files, embedded in documents and so on
Any issue arose can be solved quickly with friendly and very responsive support
service, and product updates containing bugfixes and improvements are released
every few weeks. You can see release history at
/new
"Belkasoft Evidence Center has earned itself a fixed position in most
of our forensic workflows because it helps us to find relevant information
very fast and easily. Even when we faced challenges in our investigations
we experienced an extraordinary fast and competent support from Belkasoft
that showed us that BEC is actively developed and we always felt backed
up by the support."
Heiko Rittelmeier, M.Sc. Digital Forensics, Germany
6. Advanced low-level analysis is available in BEC
While in most cases automated extraction will be enough, more complex investigations
may require manual analysis of devices in question. For such types of investigations
BEC provides powerful File System explorer, which shows all volumes and partitions
inside the device, both existing and deleted folders, VCS snapshots, existing
and deleted files. Each partition or file can be reviewed in Hex Viewer, the
window assisting you to investigate individual bytes, make automatic type conversions,
create bookmarks, run custom carving and apply various encodings.
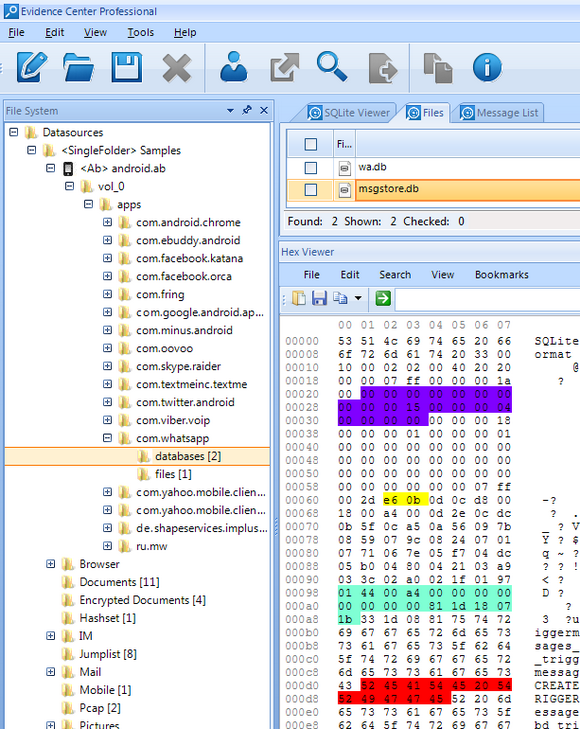
WhatsApp folder discovered inside Android backup and presented inside File
System tab of BEC. HexViewer shows binary contents of msgstore.db, some of bytes
are bookmarked and highlighted using different colors
Apart from HexViewer, there are more low-level viewers like SQLite Viewer,
Registry Viewer and Plist Viewer used for the investigation of corresponding
types of files.
7. BEC offers comprehensive analysis of your devices
The product can detect skin and faces inside pictures and videos, recognize
texts in scans, detect encryption and decrypt 300+ types of files. Powerful
Photo Forgery Detection module finds photos which were edited after the shot
was taken. Geolocation analysis will show all geo-enabled artifacts (pictures,
URLs, Uber and other mobile apps data) on Google Maps, Google Earth or export
them to KML format maps. SQLite analysis automatically reveals data in special
areas in a database, such as freelists, journal or WAL files, SQLite unallocated
and so on. Scripting allows you to extend the product to make some custom processing
like custom carving, custom search or custom reporting.
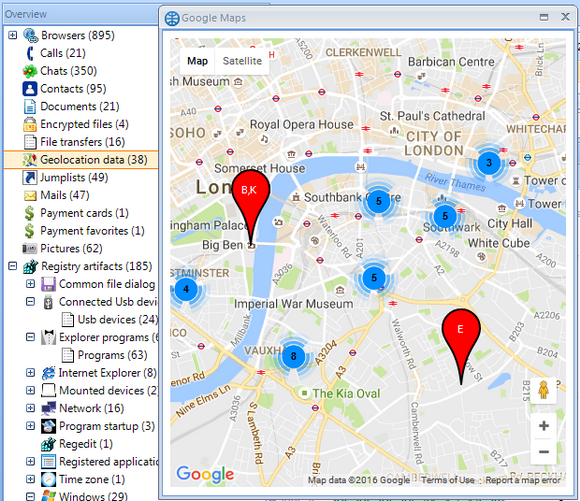
Built-in Google Maps visualize all GPS-enabled data from photos, URLs, mobile
apps like Uber and so other
Have some other products used on a daily basis? Belkasoft is integrated with
AccessData FTK and AD Lab, Guidance Software EnCase, BlueBear LACE, Passware
Kit Forensic and others; built-in export and scripting always allow you to integrate
BEC with any other third-party product.
8. BEC is quick
Unlike many competitor products that search for and index unnecessary data,
BEC indexes and searches only data you need in a course of forensic investigation,
thus the initial extraction and analysis will complete in few hours, not days
or weeks. Sophisticated algorithms make sure that all cores and memory of your
investigation machine are used one hundred percent efficiently, enabling parallel
processing, which also significantly speeds up the analysis.
Throughout the six years of my personal experience as a forensic examiner,
I have tried many forensic tools, but I find that it's Belkasoft Evidence
Center that can help find crucial data for the investigation and verification
processes in the fastest and the most effective way."
Tamas Lakatos, Computer Forensic Expert, Hungary
9. BEC shows the entire picture
With Social Graph window you can reveal connections between various individuals
in your case. Proprietary algorithm finds most important links and allows you
to detect communities of tightly connected people.
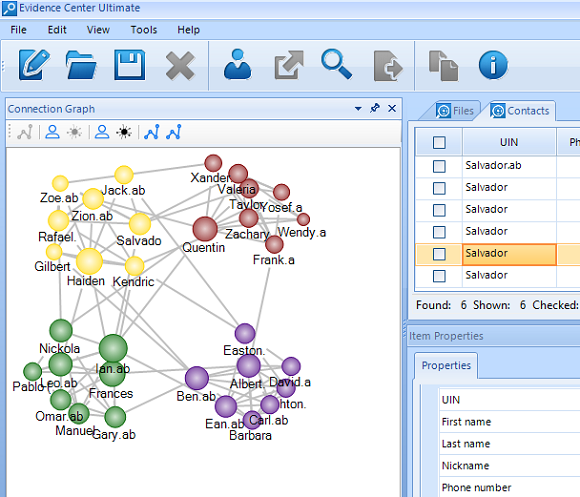
In this picture you can see 4 groups of people, found automatically by BEC
in 18-device case. Groups are marked with different colors, which mean that
people from the same "color" likely know each other very well, while they are
not closely connected to the people from other groups. Larger circles mean more
important persons, who act as "gate keepers", so it might be a good idea to
start investigation with such people.EC in 18-device case. Groups are marked
with different colors, which mean that people from the same "color" likely know
each other very well, while they are not closely connected to the people from
other groups. Larger circles mean more important persons, who act as "gate keepers",
so it might be a good idea to start investigation with such people.
10. BEC is just much more cost-effective
The product offers more features for a lower price than the competition.
Not only does it save your money at the moment of purchase, but it also helps
saving each year on decently priced renewals. Moreover, our free Evidence Reader
allows you to share part of your work with your colleagues at absolutely no
cost, thus saving you even more! Finally, Belkasoft customers have a wide variety
of discounts towards purchase of our partners' digital forensic products.
"Our company has been using software products from Belkasoft since
2011. Before that we were using 2 other forensic tools, but Belkasoft Evidence
Center has proven to be more convenient and versatile. Not only it allows
analysis of all the types of data that we look for on various devices, but
it also comes at a very fair price."
Tsvetomir Atanasov, Matrex EOOD, Bulgaria
Would like to get an independent opinion on Belkasoft Evidence Center? See
recently published review by Shafik Punja, well-known digital forensic investigator:
https://www.digitalforensicscorp.com/blog/review-of-belkasoft-evidence-center-bec/
Convinced by the reasons and eager to try Evidence Center yourself? Download
your full trial license right now at https://belkasoft.com/trial!
More details on BEC:


