Articles

Case Study: From Hidden Databases to Key Evidence with Belkasoft's SQLite Viewer
In this case involving a pyramid scheme, key evidence was found in a hidden SMS database on the victim's iPhone. The investigator used Belkasoft X's SQLite viewer to uncover a critical text message exchange between the suspect and the victim, which was missed by other digital forensic tools.

Remote Mobile Acquisition with Belkasoft R

BelkaX-101: 4-Day Onsite Belkasoft Certified Examiner Course

Preventing Data Leaks: Offline-First DFIR with Belkasoft X

BelkaX-101: 3-Day Onsite Belkasoft Certified Examiner Course in Tbilisi

RAM Forensics: Tools, Techniques, and Best Practices

Belkasoft Customer Survey 2025

iOS Telegram Forensics. Part II: Artifacts, Secret Chats, Cache, Deleted Messages

Incident Response Workflow Template

Digital Forensics Playbook for Enterprise Forensics

BelkaGPT and BelkaGPT Hub: AI That Actually Works for DFIR

Navigating the Deluge: eDiscovery with RSMF and Belkasoft X

Empowering Non-Forensic Experts with Intuitive Tools to Bridge the DFIR Talent Gap
BelkaGPT: Effective Artificial Intelligence in DFIR [ON-DEMAND COURSE]

Remote Acquisition with Belkasoft R

Belkasoft CTF 7: Write-up

Photo Forensics: Analyzing the Full Picture

AI in Digital Forensics: Ethical Considerations

Effective Evidence Sharing with Belkasoft Evidence Reader

Automating Digital Forensic Workflows with Belkasoft X

Carving in DFIR: Data Recovery and Detection of Anti-Forensic Measures

Navigating the Future: Top 6 Trends Shaping Modern DFIR in 2025

Building a Timeline: A Case for Belkasoft X

Skype Forensics Postmortem: Why DFIR Specialists Should Still Care

Windows Event Log Forensics: Techniques, Tools, and Use Cases

Unlocking Android Devices with Brute-Force

Belkasoft On-Demand Training Courses

Windows Registry Forensics: Analysis Techniques

Automating Forensic Workflows: Increased Performance with No Increase in Budget

Windows Registry: Structure, Forensic Challenges, and Acquisition

Windows Forensics: Analyzing Prefetch Files with Belkasoft X

Lessons Learned from the Silk Road Investigation

Email Forensics with Belkasoft X

Windows Browser Forensics with Belkasoft X

How to Become a Digital Forensic Investigator

Mobile Forensics Cheatsheet: iOS and Android System Artifacts

Document Forensics with Belkasoft X: Best Practices and Tips

Belkasoft Customer Survey 2024

Go Deeper. Are your forensic tools showing you all the data in your investigations?

BelkaDay Asia Conference 2024: Get Recordings

Windows Forensics with Belkasoft [ON-DEMAND COURSE]

Case Study: From Hidden Databases to Key Evidence with Belkasoft X's SQLite Viewer

Trusting AI in DFIR: Where It Shines and Fails

Belkasoft Research: Inside the Battle against Child Sexual Abuse Material (CSAM)
iOS Telegram Forensics. Part I: Acquisition and Database Analysis

How to Investigate Telegram Crime without Arresting the Company’s CEO
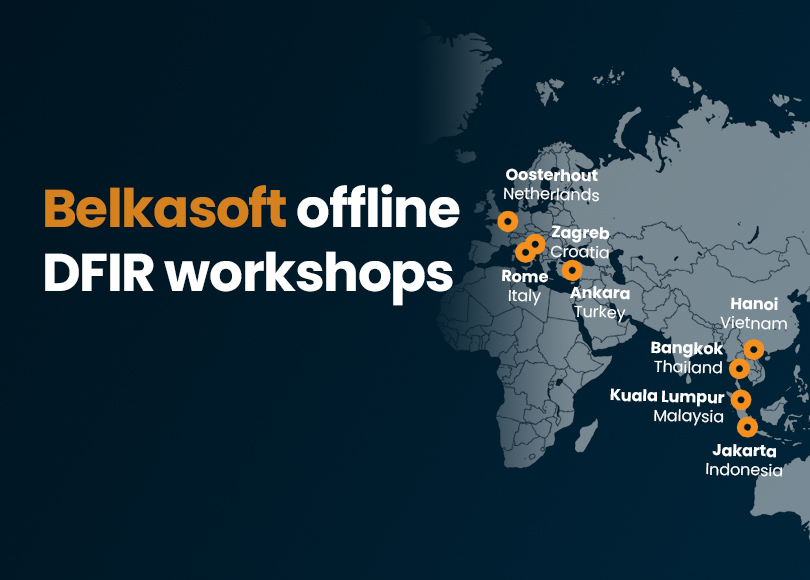
On-Site Digital Forensics Training and Workshops with Belkasoft

Android System Artifacts: Forensic Analysis of Application Usage

Challenges in Digital Forensics: The Case of the Trump Rally Shooter's Phone

Webinar: From the Field: Belkasoft X User's Guide to Effective Forensics

Case Study: Leveraging Belkasoft X for a Multi-Source Fraud Investigation

BelkaDay 2024: Digital Forensics and Cyber Incident Response Conference

Android System Artifacts: Forensic Analysis of Device Information and Usage

Belkasoft CTF 6: Interview with the Winner

Why choose Belkasoft X for digital forensics and cyber incident response?

Android WhatsApp Forensics. Part II: Analysis

Android WhatsApp Forensics. Part I: Acquisition

Android Forensics with Belkasoft [ON-DEMAND COURSE]

How to Acquire Digital Evidence with Android Screen Capturer in Belkasoft X

The Investigator’s Guide to Android Acquisition Methods. Part I: Device

Belkasoft 2023 Recap

How to Efficiently Triage Digital Evidence with Belkasoft T

Cyber Incident Response with Belkasoft X

Webinar: Digital Triage with Belkasoft T

Forensic Duel: Exploring Deleted WhatsApp Messages—iOS vs Android

Belkasoft Industry Research 2023

Telegram Forensics: Getting Started
DFIR Labs in the Cloud: The Future of Digital Forensics

Belkasoft Triage Is Now Free!

Decoding Windows Registry Artifacts with Belkasoft X: UserAssist

iCloud Advanced Data Protection: Implications for Forensic Extraction

iOS System Artifacts: Revealing Hidden Clues

Download your free e-book "Essays on Digital Forensics"

iOS WhatsApp Forensics with Belkasoft X
How to create hashset databases with Belkasoft X

Belkasoft Industry Survey 2023

iOS Forensics with Belkasoft [ON-DEMAND COURSE]

Unlocking iOS Devices with Brute-Force
How to Analyze KnowledgeC.db with Belkasoft X
Ins and Outs of Hashing and Hashset Analysis in Belkasoft X

Case Study: Belkasoft X Helps to Define CSAM Recidivism Immediately
DIY YARA vs. YARA with Belkasoft X

KnowledgeC Database Forensics: A Comprehensive Guide
What's new in Belkasoft X v.2.0
[ON-DEMAND COURSE] Maximizing DFIR Results with YARA, Sigma, and Belkasoft X
Automation with Belkasoft: Orchestrating Belkasoft X and Griffeye DI Pro

Incident Response with Belkasoft: First steps

Belkasoft X Brute-Force Webinar

Case of Casey Anthony: Extraneous Digital Evidence

Belkasoft Mobile Device Investigations Course

Walkthrough: YARA Rules in Belkasoft X
Lagging for the Win: Querying for Negative Evidence in the sms.db

SQLite Forensics with Belkasoft

Basic but significant legal issues in the Casey Anthony Case
Download your free e-book on ChatGPT in DFIR!
Walkthrough: Sigma Rules in Belkasoft X
Automation with Belkasoft X: Putting the pieces together
Automation with Belkasoft X: Installation and Licensing

Automation with Belkasoft: Export for Amped FIVE
Digital Forensic Work Automation with Belkasoft X

NIST tested Belkasoft support for SQLite data recovery

Belkasoft’s Year in Review—2022

[ON-DEMAND COURSE] SQLite Forensics with Belkasoft
Webinar: MacOS forensics. Decryption and analysis of apps images from Macs with T2

Belkasoft Customer Survey 2022

[ON-DEMAND COURSE] Remote Acquisition with Belkasoft

The riskiest cybersecurity danger for your business this fall

Sneak peek of Belkasoft X v.1.15

Internal or external: what data breach elicits the greater risk and damage?
EVEN 5 MORE Bloopers of a Digital Forensic Investigator (Part 3)

[ON-DEMAND COURSE] Corporate Investigations with Belkasoft
5 MORE Bloopers of a Digital Forensic Investigator (Part 2).
SQLite Forensics with Belkasoft X
Sneak peek of Belkasoft X v.1.14

Cyber Incident Investigations Course with Belkasoft

The importance of fully charged devices in your digital forensic investigation

Career Path—The Choice is Yours

Where in the world were John McAfee and An0nymous? A tell-tale sign from EXIF data
Sneak peek of Belkasoft X v.1.13

Encryption amidst digital forensic and cyber incident response investigations

Belkasoft Triage T v.1.2 is released!

Preventing Burnout in Digital Forensics

Stay in good physical shape: look past the screen of a digital forensic examiner

These chats are not mine! How our test engineer almost went crazy

How memory analysis helped to fight against "designer drugs"
What's new in Belkasoft X v.1.12
How even an experienced DFIR expert can catch a virus?

The case of a missing girl and the power of a memory dump

Belkasoft CTF March 2022: Write-Up

[ON-DEMAND COURSE] Mobile Forensics with Belkasoft X
Sneak peek: Belkasoft announces the upcoming release of Belkasoft X v.1.12

[INFOGRAPHICS] Mobile forensics with Belkasoft

Why RAM dumping is so important and what tool to use?
How even the best evidence can fail in court
Browser forensics and the case of Casey Anthony

Magic wand or scientific approach? Myths and realities about digital forensic software

5 Bloopers of a Digital Forensic Investigator

Preserving chain of custody in digital forensics

Where did this chat come from? The 'Origin path' concept in Belkasoft X

Сhristmas edition: Inspirational stories about digital forensics folks

Support Belkasoft at the SANS Difference Makers Awards!
iCloud acquisition and analysis with Belkasoft X

Why a term-based license is NOT good for Digital Forensics market
Mobile Forensics Software: Why Belkasoft X Should Be Your Tool of Choice
Media file forensics with Belkasoft X

Android Viber Forensics with Belkasoft X
Triaging Windows-based computers with Belkasoft T

Belkasoft Releases Belkasoft T v.1.1
Belkasoft Appoints Arvinder Garcha as VP to Lead Company's Channel Development

Digital Forensics Survey 2021: Results

iOS Signal decryption with Belkasoft X

Belkasoft is introducing a show 'BelkaTalk on DFIR'

Android Screen Capturing with Belkasoft X
How to Acquire Data from an Android Device Using the APK Downgrade Method
Belkasoft T — a new effective DFIR triage tool

Belkasoft DFIR Survey 2021: Your Personal Advisor

SANS Institute: Six Steps to Successful Mobile Validation
Investigating the Dropbox Desktop App for Windows with Belkasoft X
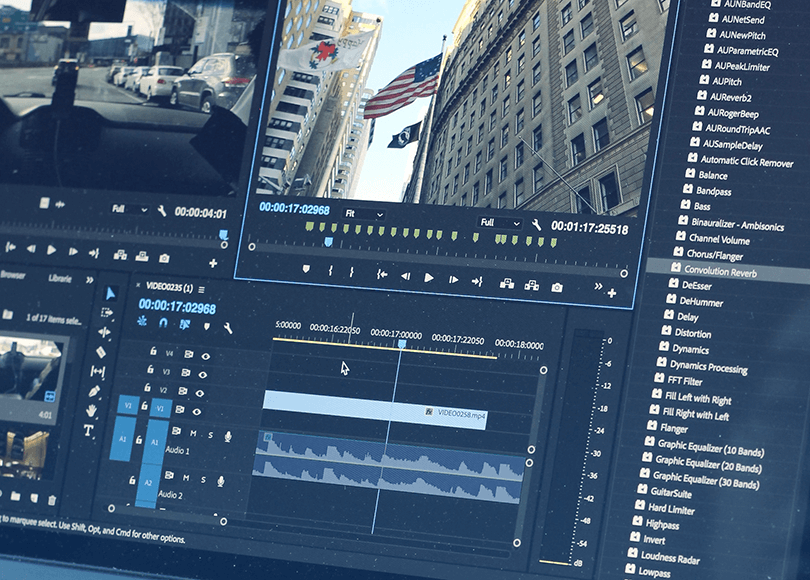
Analyzing videos with multiple video streams in digital forensics

How to analyze different types of devices and find connections between them

Find out what happened during a ransomware attack on computer

eDiscovery with Belkasoft

Dealing with Apple's USB Restricted Mode
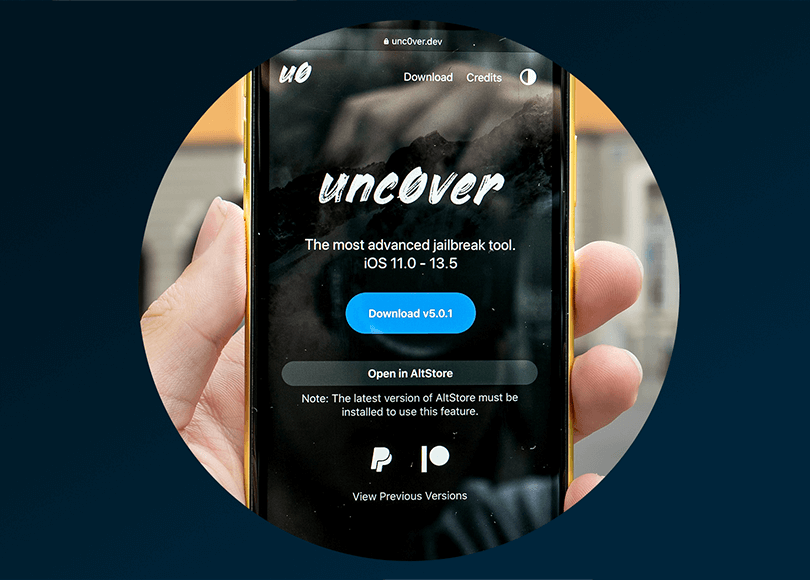
Unc0ver: What you should know about this new jailbreak for iOS devices
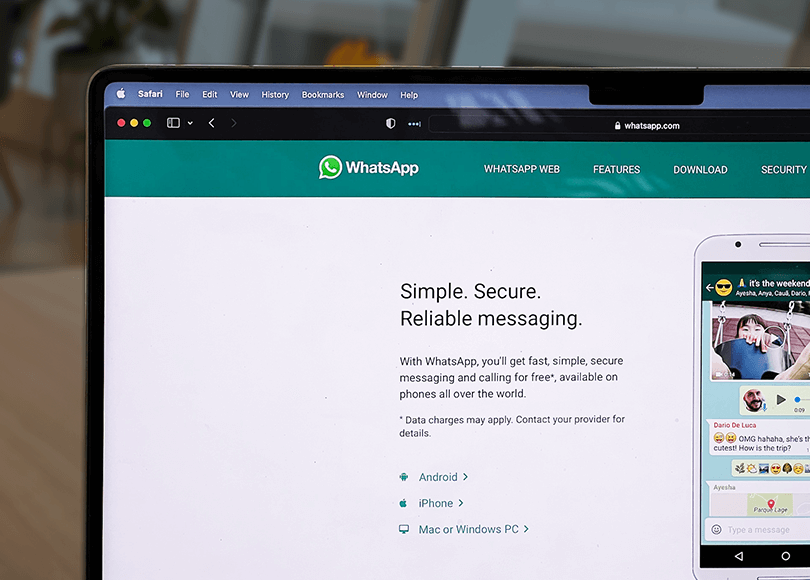
WhatsApp Forensics on Computers (Windows PCs and Macs)

Checkm8 Review

Decrypting iOS Signal App Data with Belkasoft Evidence Center

Mitigating security risks using Belkasoft Evidence Center
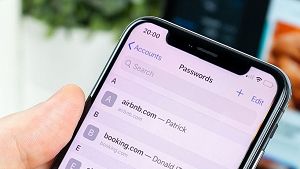
Keychain Extraction in Belkasoft Evidence Center

Checkm8 Glossary

Full File System Extraction of iOS Devices with Belkasoft X
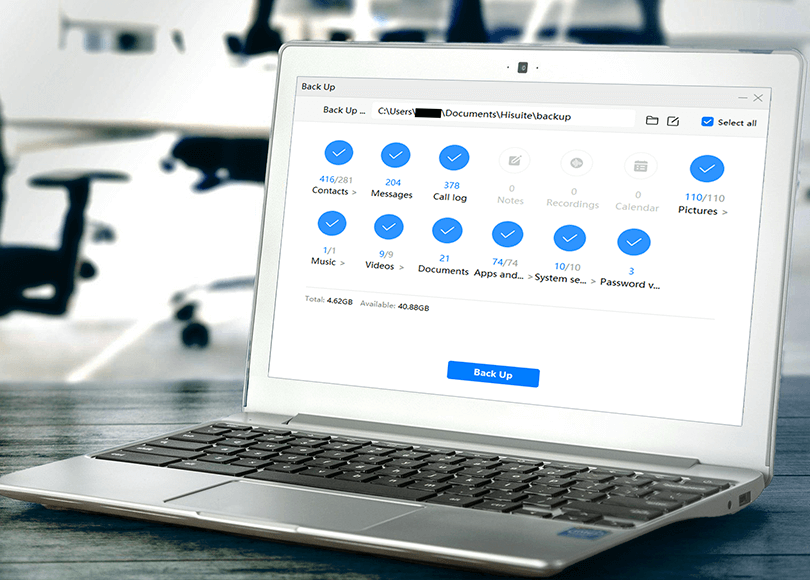
Analyzing HiSuite Backups with Belkasoft Evidence Center

Results of Customer Survey 2019: Findings and Insights

Analyzing Jump Lists with Belkasoft Evidence Center
Forensic Extraction of Data from Mobile Apple Devices with Belkasoft Products
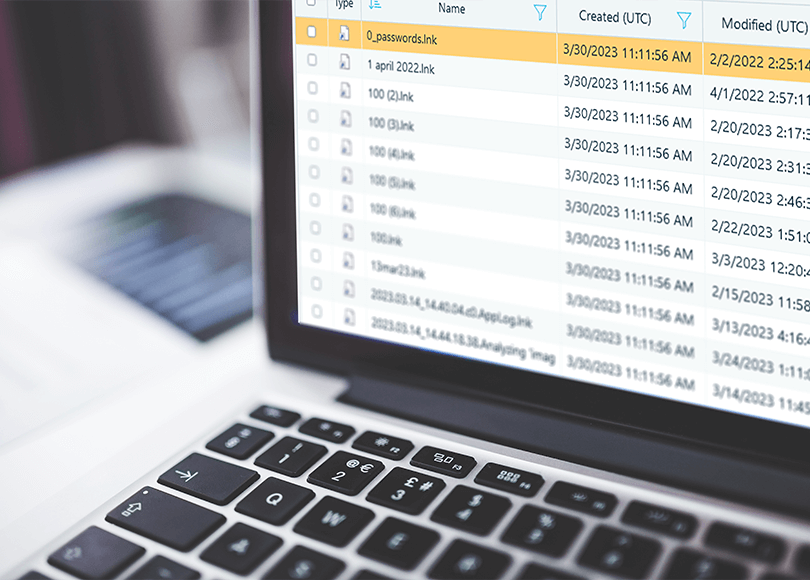
Forensic Analysis of LNK Files
Does your DFIR tool have substantial updates?
Building a Timeline: A Case for Belkasoft Evidence Center

I took Belkasoft Evidence Center for a spin around the block

Belkasoft Evidence Center: A View from Spain
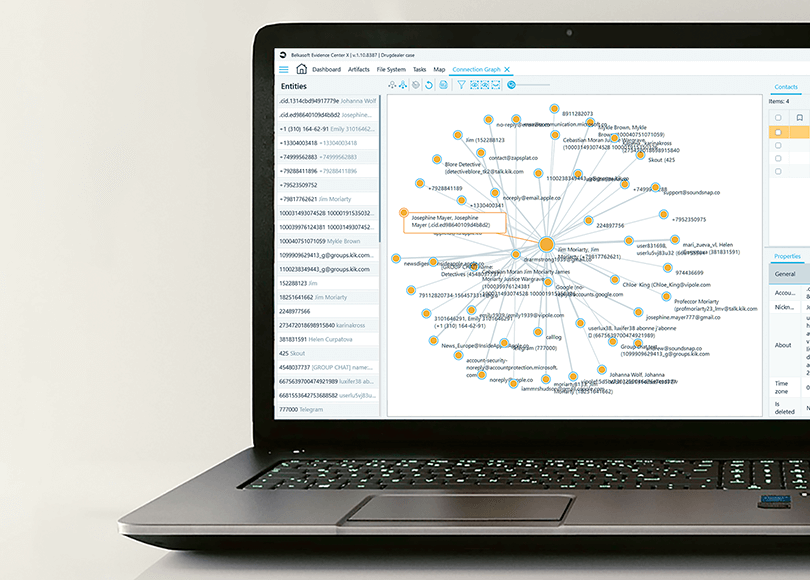
How to Use Connection Graphs by Belkasoft for Complex Cases
Walkthrough: How to Perform Remote Acquisition of Digital Devices
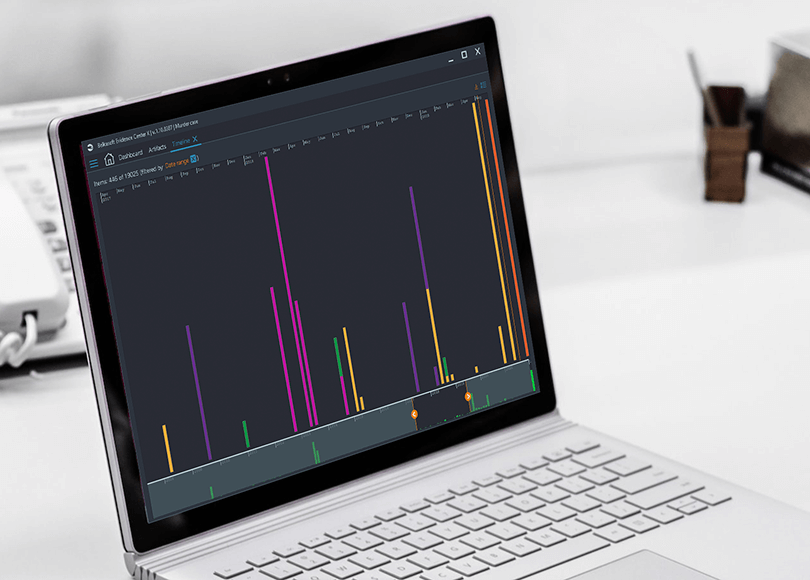
How to Analyze Windows 10 Timeline with Belkasoft Evidence Center X

How To Use Cross-Case Search With Belkasoft Evidence Center

Reasons Why You Need Belkasoft Evidence Center to Fight Workplace Bullying. Part II

5 Reasons Why Corporate Investigators Need Belkasoft to Fight Workplace Bullying. Part 1
Fast Detection of Mobile Malware and Spyware with Belkasoft

Carving and its Implementations in Digital Forensics

WeChat. The Forensic Aspects Of and Uses For Evidence from a Super-App

Comprehensive Forensic Chat Examination with Belkasoft

I Have Been Hacked

SSD and eMMC Forensics 2016—Part 3

SSD and eMMC Forensics 2016—Part 2

SSD and eMMC Forensics 2016—Part 1

BelkaScript: How to Get Most out of Digital Forensic Software

The Future of Mobile Forensics: November 2015 Follow-up

Countering Anti-Forensic Efforts - Part 2

Countering Anti-Forensic Efforts—Part 1

NAS Forensics Explained

Future of Mobile Forensics

Acquiring Windows PCs

Capturing RAM Dumps and Imaging eMMC Storage on Windows Tablets

Kik Messenger Forensics

Analyzing Windows Phone 8.1 JTAG and UFED Dumps

Forensic Analysis of SQLite Databases

SSD Forensics 2014. Recovering Evidence from SSD Drives

Recovering Destroyed SQLite Evidence, iPhone/Android Messages, Cleared Skype Logs

Detecting Altered Images

Catching the ghost: how to discover ephemeral evidence with Live RAM analysis

Why SSD Drives Destroy Court Evidence, and What Can Be Done About It
