John McAfee was a founder of one of the original antivirus software programs in the world. It has been a decade since the infamous John McAfee was plastering televisions with news of him fleeing the country of Belize. He was being named a person of interest in the murder of his neighbor, while living in Ambergris Caye.
McAfee and his neighbor, Gregory Faull, had an on-going feud over McAfee’s dogs escaping his yard. A day after their latest disagreement, Faull was found dead from a 9mm gunshot wound and McAfee was nowhere to be found. McAfee fled Belize and headed for Guatemala with his girlfriend and a journalism crew from Vice Magazine. McAfee would remain in hiding for quite some time. While avoiding authorities he turned to taunting the Belize police and the world with social media posts and blogs. He even went so far as to disguise himself as a Guatemalan trinket peddler to evade capture from the police.
All seemed to be going smoothly for McAfee, that is until Vice Magazine posted a picture of McAfee and their editor-in-chief at the time, Rocco Castoro posing together. The picture had been taken with an iPhone 4s at 18:25:26Z on December 3rd, 2012. In addition to the time, we also know the approximate location of where the photo was taken—15 39.49N and 88 59.53W.
But how could someone determine detailed location information along with date and time from a simple picture posted on social media? Behold the power of the Exchangeable Image File Format (EXIF) which is a standard that defines additional information related to an image or other media captured by a digital camera. This additional information is stored in the form of Metadata (i.e. data about data).
EXIF digital image files often use JPEG compression. Below is a listing of some of the common data types can expect to see within image metadata:
- Date and time information
- Camera settings, such as:
- Camera make and model
- Rotation
- Aperture
- Shutter speed
- Focal length
- Metering mode
- ISO speed
- and more (depending on the type of camera)
- Thumbnail
- Descriptions
- Copyright Info
- and more
Before diving too much deeper into the story that ultimately led to McAfee taking his own life in a Barcelona prison, let us next explore another example of how EXIF eventually brought down a member of an An0nymous offshoot (CabinCr3w), known as W0rmer.
Higinio O Ochoa III, who holds a Twitter account with the name W0rmer was following the group An0nymous for quite some time and began sympathizing with their beliefs. Eventually, W0rmer was adopted into An0nOps chat groups, (hacktivists for social justice) which is where we will begin our story.
W0rmer, while sitting in an An0nOps chat, noticed a female come into the chat and begin asking for assistance on a problem that she was seeing with the abuse of dogs. She wanted the group's help to expose the abuse and abusive people. We would later learn that a simple inappropriate joke would ultimately lead to W0rmer’s capture, but more on that in a bit.
Upon seeing the new female, W0rmer made a crude reference to her breasts saying, “_____ or get the $%&* out." To his surprise, she actually forwarded him pictures of her in a bikini, which W0rmerlater adopted and used in his posts to taunt police. W0rmer also fell in love with the girl (eventually marrying her) and noticed that the pictures she was sending contained useful metadata. He could use this metadata to get the location of her house in Australia, which she later confirmed as being accurate. W0rmer of course knew these EXIF photos contained metadata and planned to use them later for his hacktivist activities. He had a method of cleaning the metadata from the photos to make them safe for his use.
W0rmer was executing his plan for social justice by hacking into police department websites within the United States, as he was tired of seeing police officers beating civilians and, in his eyes, abusing their power. He obtained lists of police department websites from other members in the AnonOps chat sites, where he would scan these websites searching for vulnerabilities. When he would find a vulnerability, he would take control of the site and leak database information full of police officer information into Pastebin. When he posted these databases, he would also include pictures of the girl in the bikini holding a sign that said something like “PwND by w0rmer & CabinCr3w. Unfortunately for W0rmer, he accidentally made the mistake of using a non-scrubbed photo that still included metadata, which ultimately led the FBI directly to his girlfriend and eventually straight to w0rmer.
How Belkasoft can help examiners find the smoking gun with EXIF in their cases
Belkasoft X, Belkasoft’s flagship DFIR product does an outstanding job of scraping EXIF from photographs and presents the data in a very clean and easy to use interface. As an examiner you can even filter only for pictures that contain GPS coordinates. You can also plot these coordinates on a built-in map inside Belkasoft X or even plot coordinates straight to a satellite image within Google Earth.
Additionally, you can export these artifacts into the Keyhole Markup Language (KML) format, an XML notation for expressing geographic annotation and visualization within two-dimensional maps and three-dimensional Earth browsers, developed for use within Google Earth, to display these artifacts in the format designed for the program.
Let’s take a look at what EXIF data can look like inside of Belkasoft X:
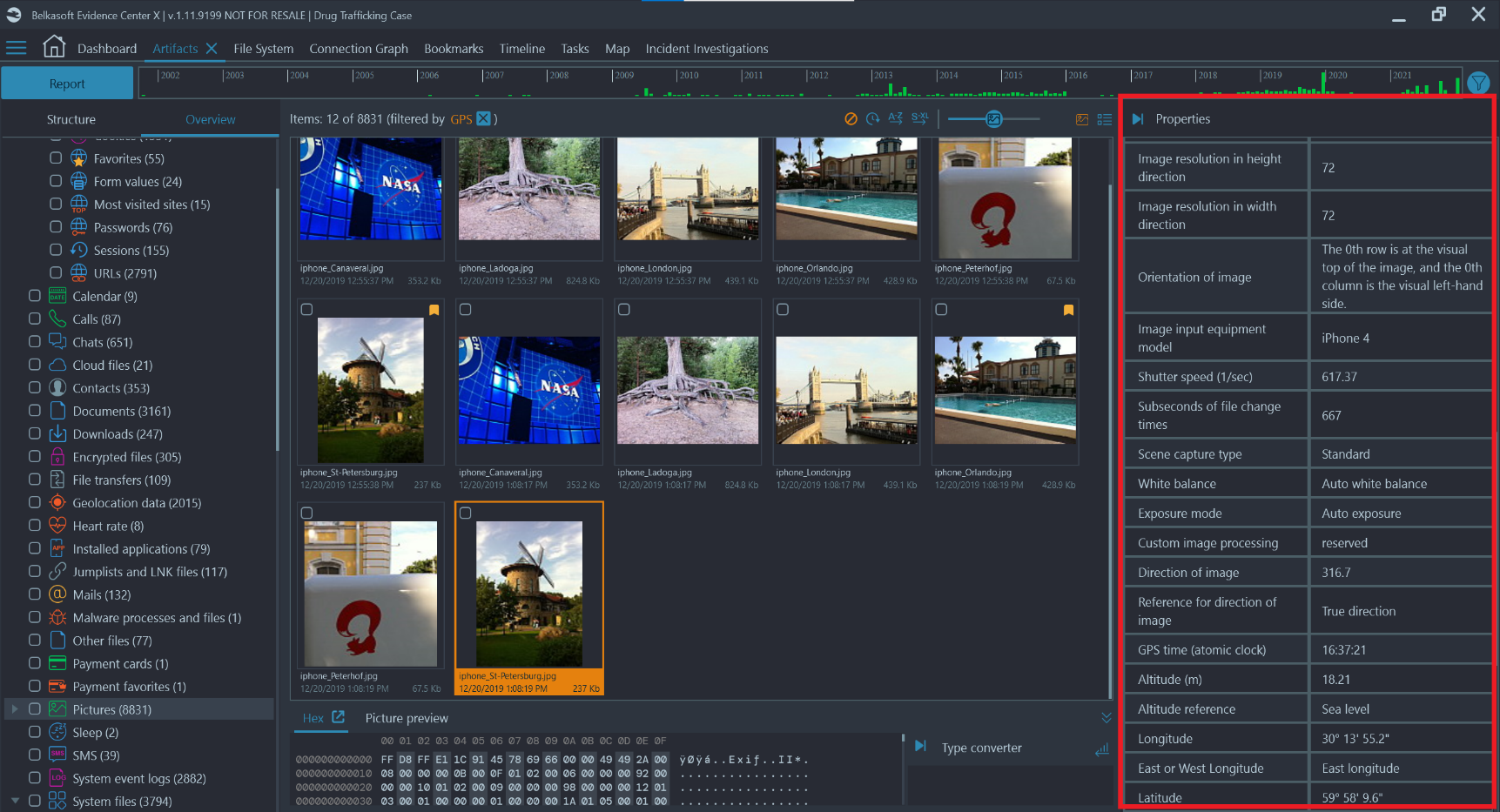
What is shown above, is only a small snippet of the available EXIF data and information about the single photograph that is selected. There are many other great features that Belkasoft offers for the analysis of photographs and other media, such as:
- Face Detection and Facial Groupings
- Skin Detection
- Pornography Detection
- Gun Detection
- Text Detection (OCR in 50 different languages!)
- Hex Viewer for low-level analysis
- and more!
We would love to hear your story of solving a crime or a corporate incident utilizing EXIF and would like to share it with the community! Please send your story to sales@belkasoft.com
Thank you for reading! If you enjoyed the use of EXIF in digital forensics and would like to see more, please take a look at a few of our latest articles.
