Introduction
The modern Internet is all about media. Suppose you look at any list of the most popular apps. All of them are somehow connected to media: TikTok featuring short videos, Instagram showing you photos, or YouTube, where you can watch films, podcasts and listen to music.
In a digital forensic investigation or an incident response case, an examiner may need to analyze thousands, if not millions of images, videos, and audio files to find just one or even a dozen artifacts that need attention.
The volume of data modern devices may store, makes it nearly impossible to go through all the pictures and videos without automation. One needs a tool to facilitate an automated search for various artifacts and the info hidden inside.
This article describes Belkasoft's approach to media file forensics implemented in Belkasoft X, our flagship mobile, computer, and cloud forensics tool.
Audio file forensics
Mobile and computer device users may share audio files in different ways, including voice mail—whether via a regular phone call or a call made in various communication apps such as WhatsApp, Telegram, Facebook Messenger, or Skype.
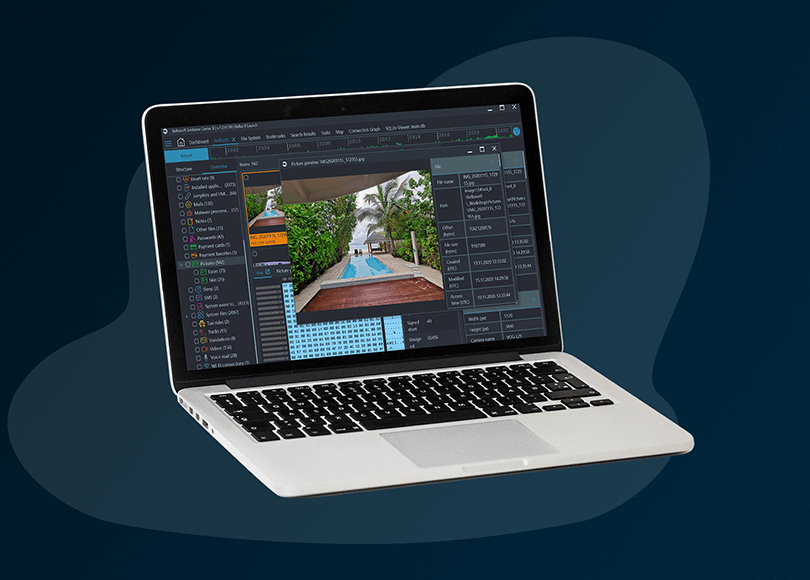
Belkasoft X can analyze more than 1,500 different apps for computer and mobile devices, including those which allow the sharing of audio files and making calls The results related to audio files are shown under the Audio node of the Overview tab on the Artifacts window:
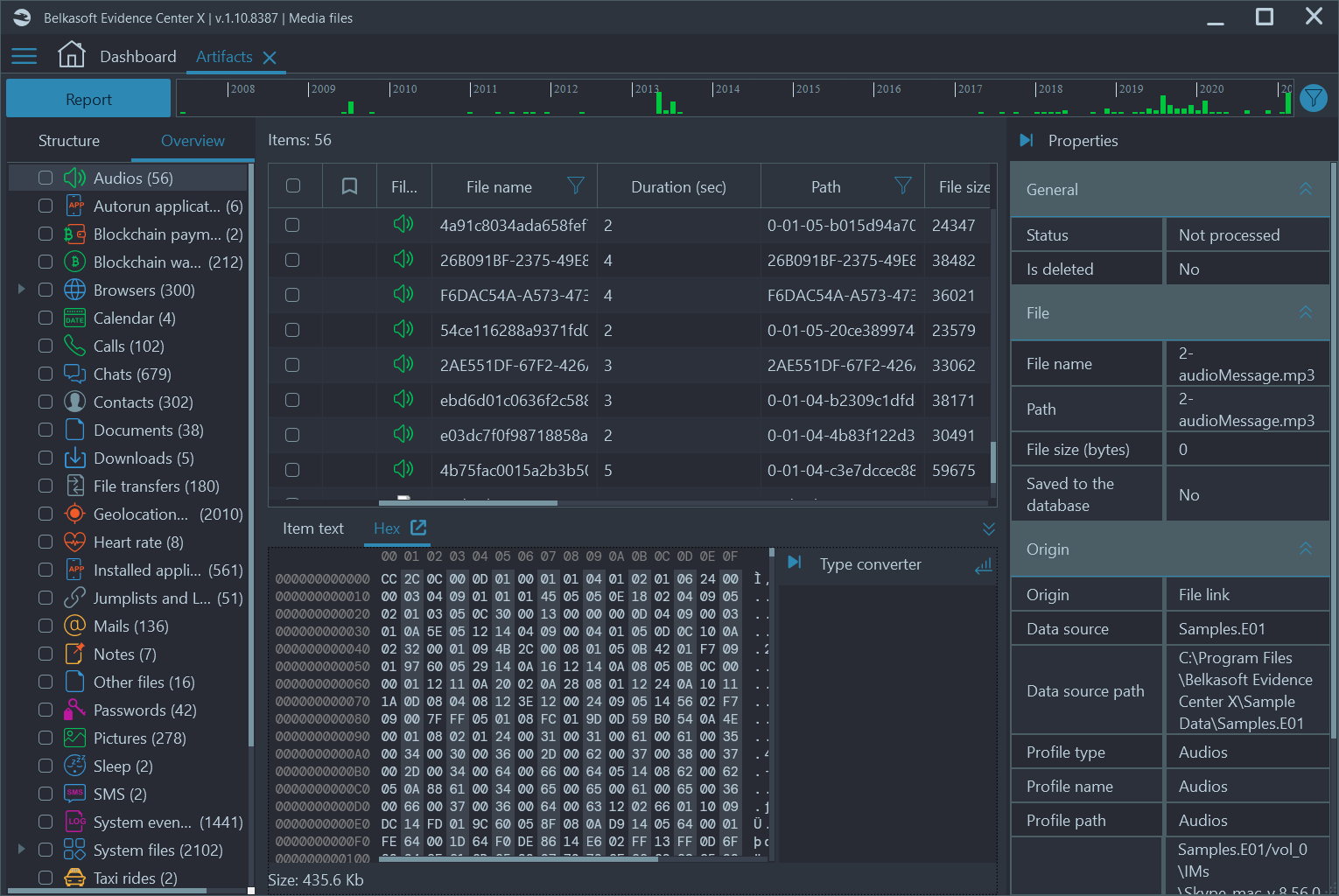
Figure 1: Audio files found by Belkasoft X on devices added to a case
On most occasions, such files are temporarily stored on a device and can be already deleted (automatically by an app) at the moment of the examination. An app typically stores only a link to that temporary file location. The audio file is already unable to replay it unless you connect to the Internet again and redownload the file (what is not legally allowed in most cases for a criminal case).
Even if the file does not exist on a device anymore, Belkasoft would still show the audio file under Audios and notify you that it is not available for replay.
Files that are still stored on a device, can be played with a built-in player by simply double-clicking on the artifact of interest. You can also open it in a default app by right-clicking and selecting Open checked files with the default application in a default viewer.
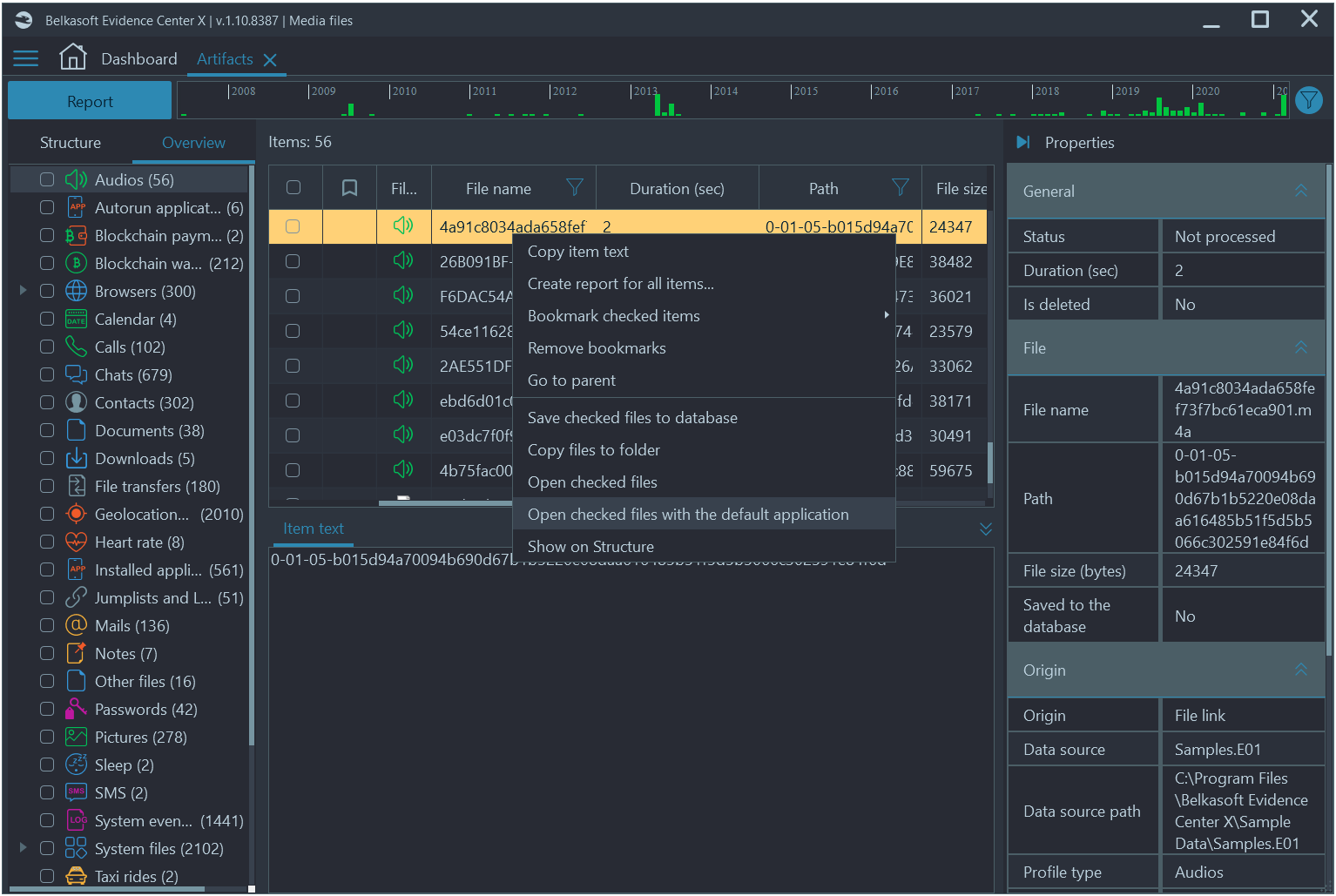
Figure 2: Opening audio files in Belkasoft X
Image file forensics
There are multiple types of data you might be interested in photos and other image files. Among them:
- Device information
- Date and timestamps
- Location data
- Content classification, including faces, nudity, scanned texts, guns, drugs, car license plates, tattoos, stamps, violence, money, etc.
- Steganography
- And more
Belkasoft X displays image files extracted from various data sources under the Pictures node of the Overview tab on the Artifacts window. These pictures can be extracted from files existing on a device; carved from unallocated and slack space; recovered from file system snapshots; found inside other artifacts (e.g., email attachments, documents, chats), and so on.
The software allows multiple basic operations on pictures such as preview and full screen review, sorting by size, creation time, and name ascending or descending, inspecting basic properties such as dimensions, picture type, JPEG metadata, and so on.
A number of filters exist; among the most useful are filters by time, camera model, manufacturer, and existence or absence of location metadata. For example, you can review all photos taken with a GPS-enabled device and place them on a built-in Map using the latter one.
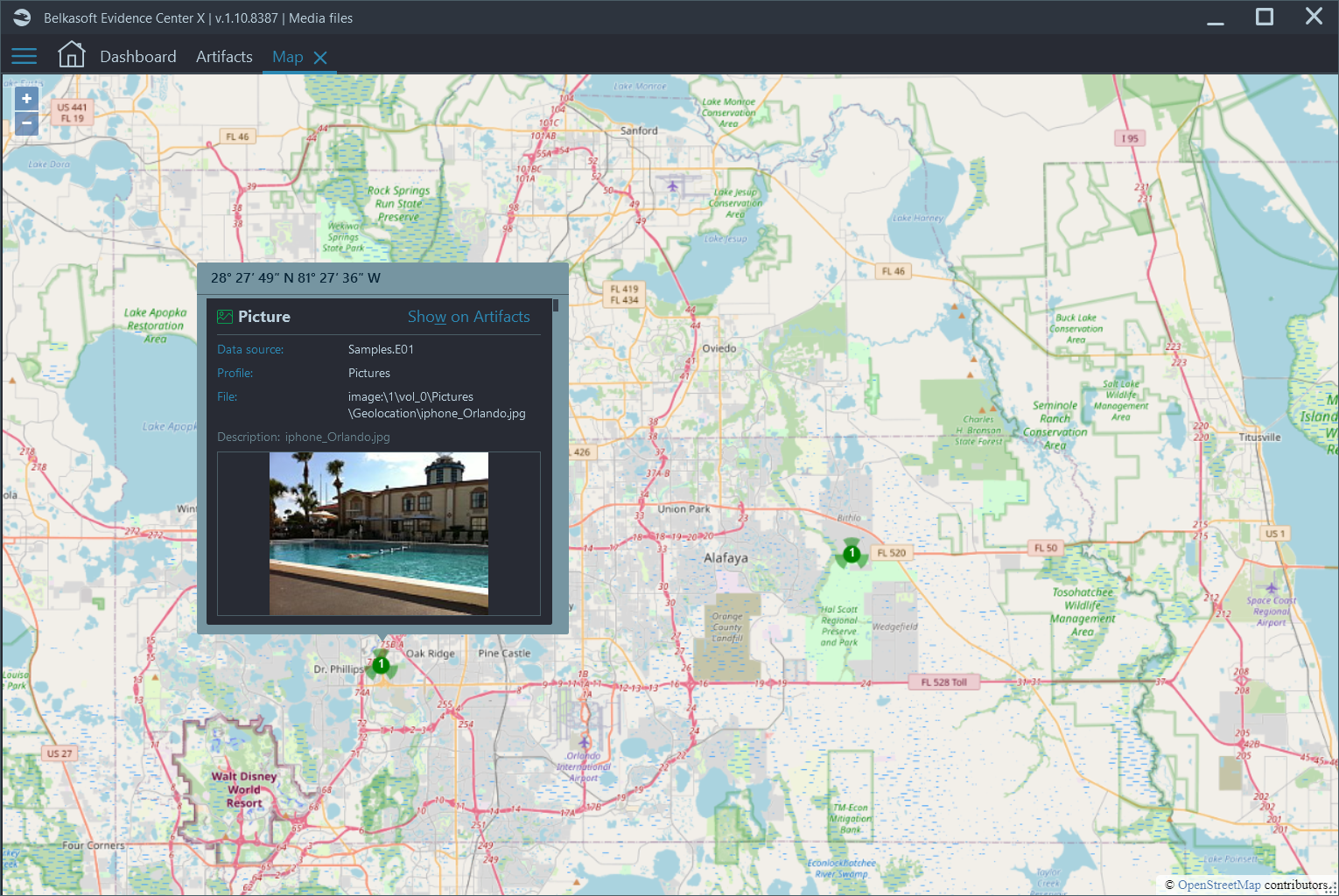
Figure 3: On the Map window, you can see selected photos with location metadata. A hint shown on hover visualizes important info on artifacts shown in a cluster of points
Another helpful filter enables you to review pictures based on the method by which they were found. For example, you can ask the product to show you only pictures received or sent as email attachments. Or list those embedded in a document such as Microsoft Word, Excel, PowerPoint, OpenOffice file, macOS document, or PDF file. Alternatively, you can choose to only see carved pictures or only pictures stored as a regular file.
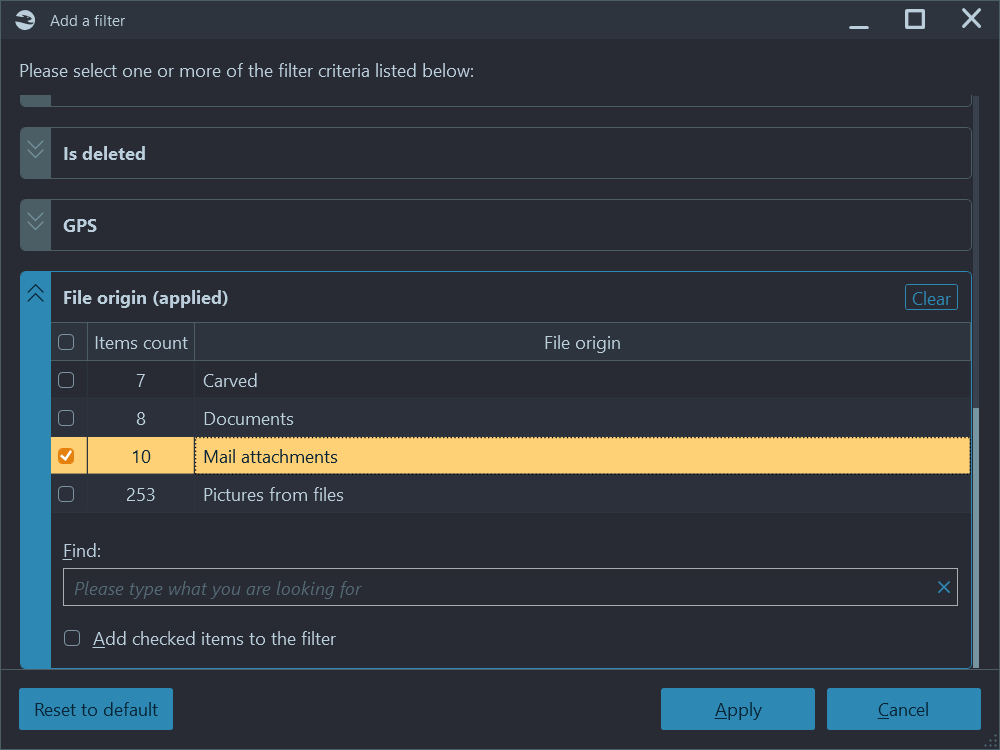
Figure 4: Origin filter helps to review photos that came as an attachment
A handy Properties tab on the right-hand pane of the Artifacts window lists all picture properties including file system ones (various timestamps, size, name, path) and metadata (device, model, location, etc.). On the bottom of the Artifacts window, you can inspect a selected picture's raw data in a built-in Hex viewer.
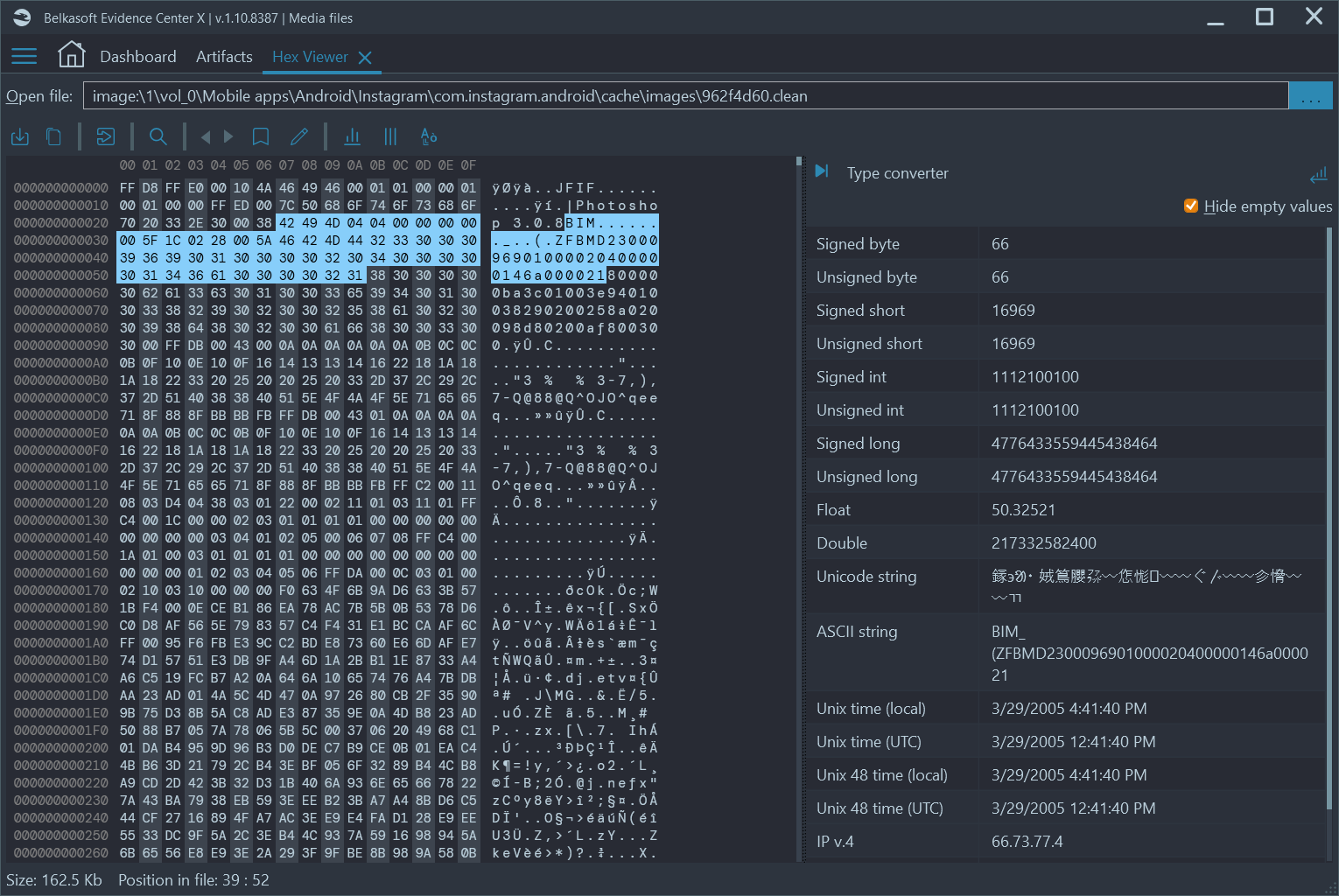
Figure 5:A built-in Hex Viewer in Belkasoft X
Belkasoft X has an essential feature of automatic picture classification. You can run this function within the process of adding a new data source or later when a basic analysis is completed. In the latter case, you should navigate to the Artifacts window, select the Pictures node under the Overview or Structure tab, right-click, and select Analyze pictures.
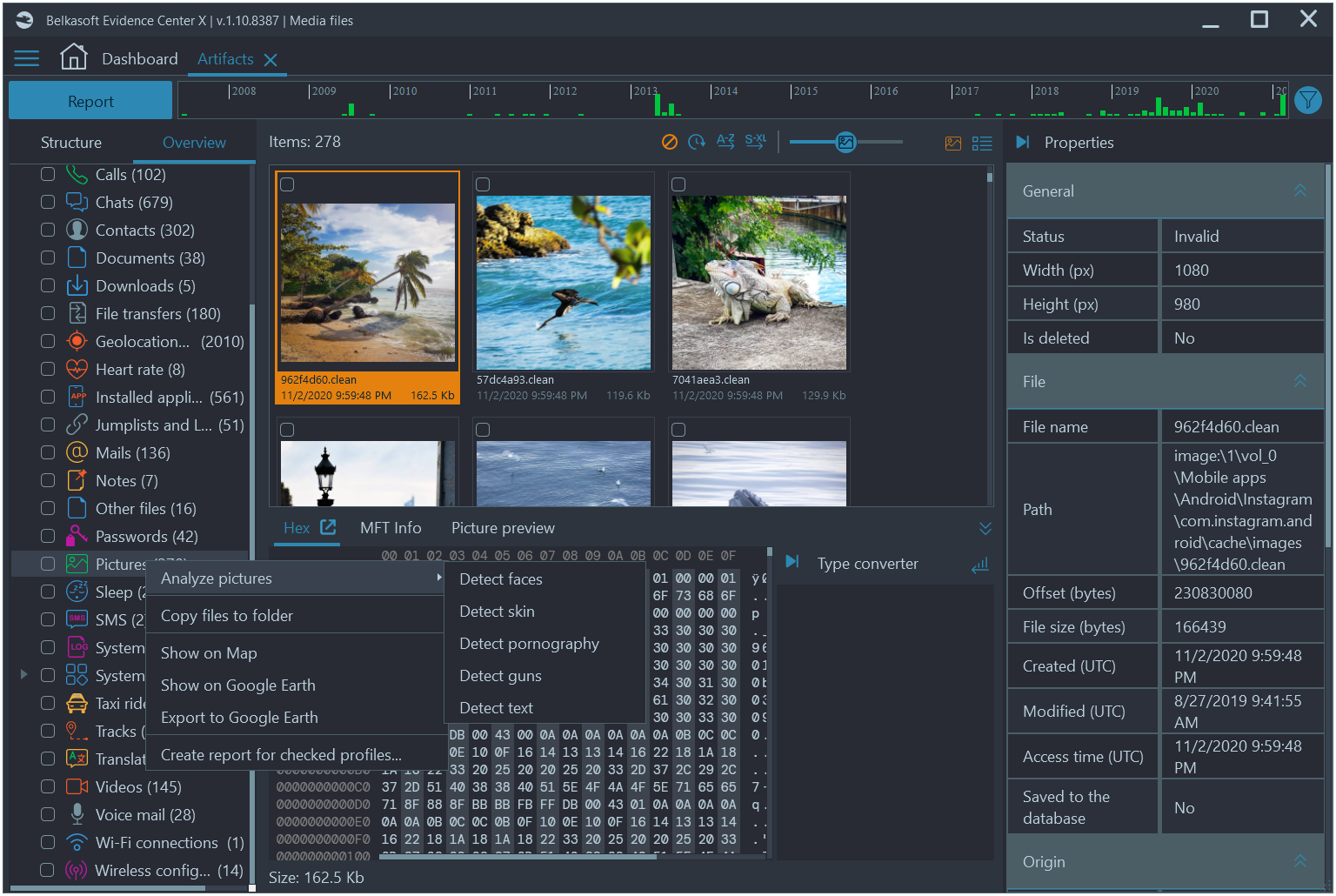
Figure 6: Picture analysis functionality in Belkasoft X
Belkasoft X currently supports the detection of the following types of content inside pictures (and video keyframes, explained below): skin tone, pornography, faces, guns, texts (including scanned books and documents, screenshots, objects with printed letters, etc). Text detection is complemented by OCR (text recognition) on one of 50 available alphabets, such as various European character sets, as well as hieroglyphics (Chinese and Japanese). Recognized texts are indexes that allow an examiner to search for text within pictures.
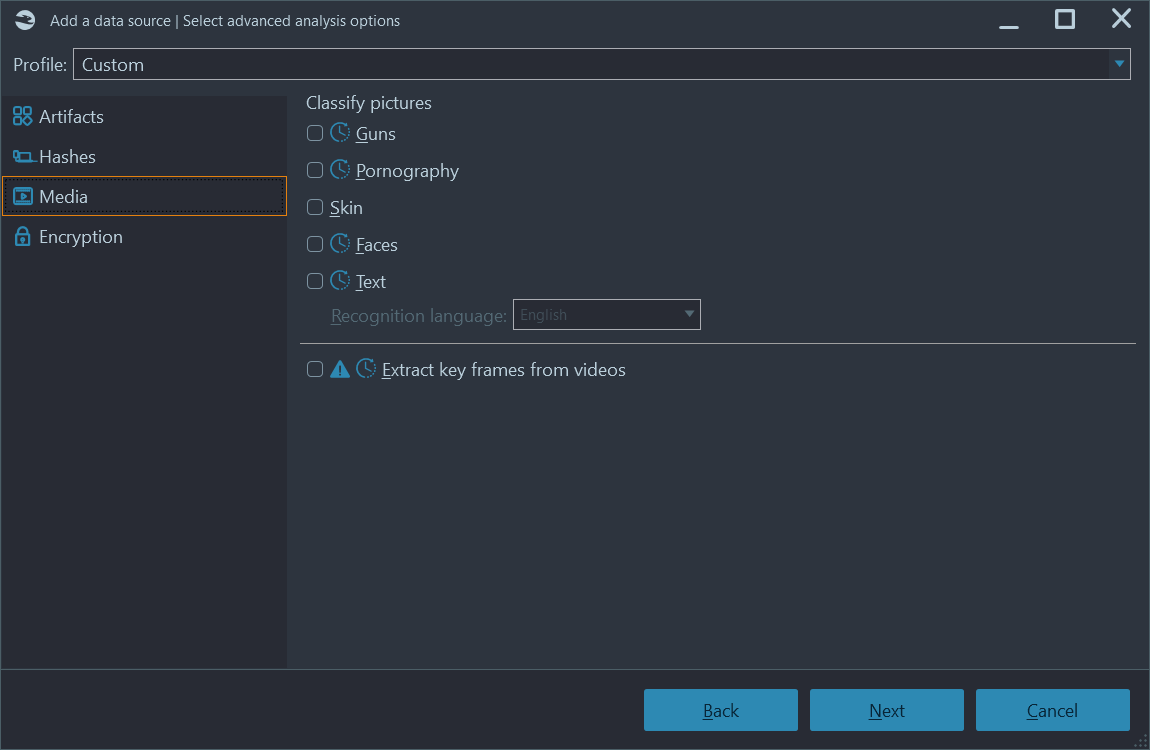
Figure 7: Advanced media analysis options in Belkasoft X
This feature can save an examiner, a lot of time, especially in corporate cases. In a company, many documents may originate from a scanner machine. Though such documents are typically stored as a PDF file, \the text inside is not searchable because a scanner just places scanned JPGs into a PDF. Opening thousands of documents like this and reviewing them manually may take an overwhelming amount of time. Belkasoft X can detect such documents and recognize the text inside, thus making it searchable like a regular Word document.
To quickly overview different types of detected pictures and inspect pictures of a given type, you can navigate to the Overview tab of the Artifacts window and click on the + icon to the left of the Pictures node. In the expanded tree, you will see all classes of pictures, and selecting any of them will show you the corresponding list. A number of useful small additions are implemented: for instance, faces are highlighted with a green square, while pornography pictures are automatically blurred (you can view the original picture by double-clicking on it, which will open the full-size picture viewer; alternatively, you can uncheck the option to blur pictures that are detected as pornography).
Video file forensics
Just like audio files and pictures, video files have a special node called Videos, on the Artifacts window of Belkasoft X. Likewise, videos can be found inside existing files, carved, extracted from email or chat attachments, located inside documents, and so on.
Belkasoft X allows a user to play video files directly inside the product, using a built-in Media player. Simply double-click to do so. You can also open a video file in a default application: right-click on a video of interest and select Open in a default viewer.
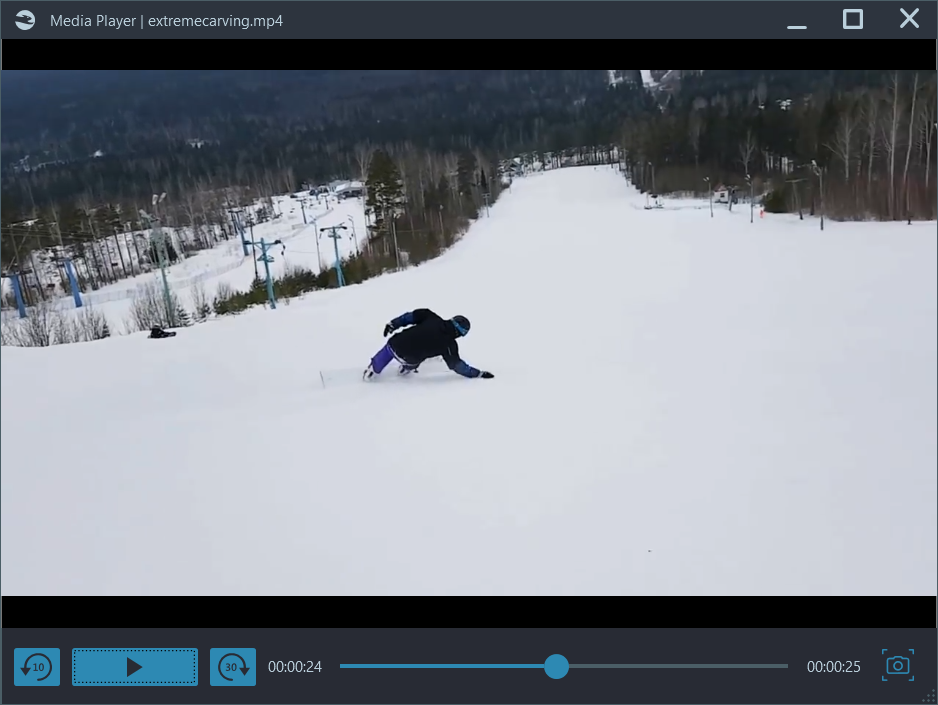
Figure 8: A built-in Media player in Belkasoft X
Note: opening a video for the first time may take a while. It must first be saved on your investigation machine to be opened in an external viewer since regular players cannot play videos from a forensic image.
Another feature that may help you save a lot of time is keyframe extraction. A keyframe is a still image extracted from a video, which significantly differs from a previous keyframe. Thus, reviewing just keyframes will give you the idea of a video file without watching it. Since a glance over still images can instantly cover some 5-10 frames, you can quickly understand whether a video contains anything that can relate to your case.
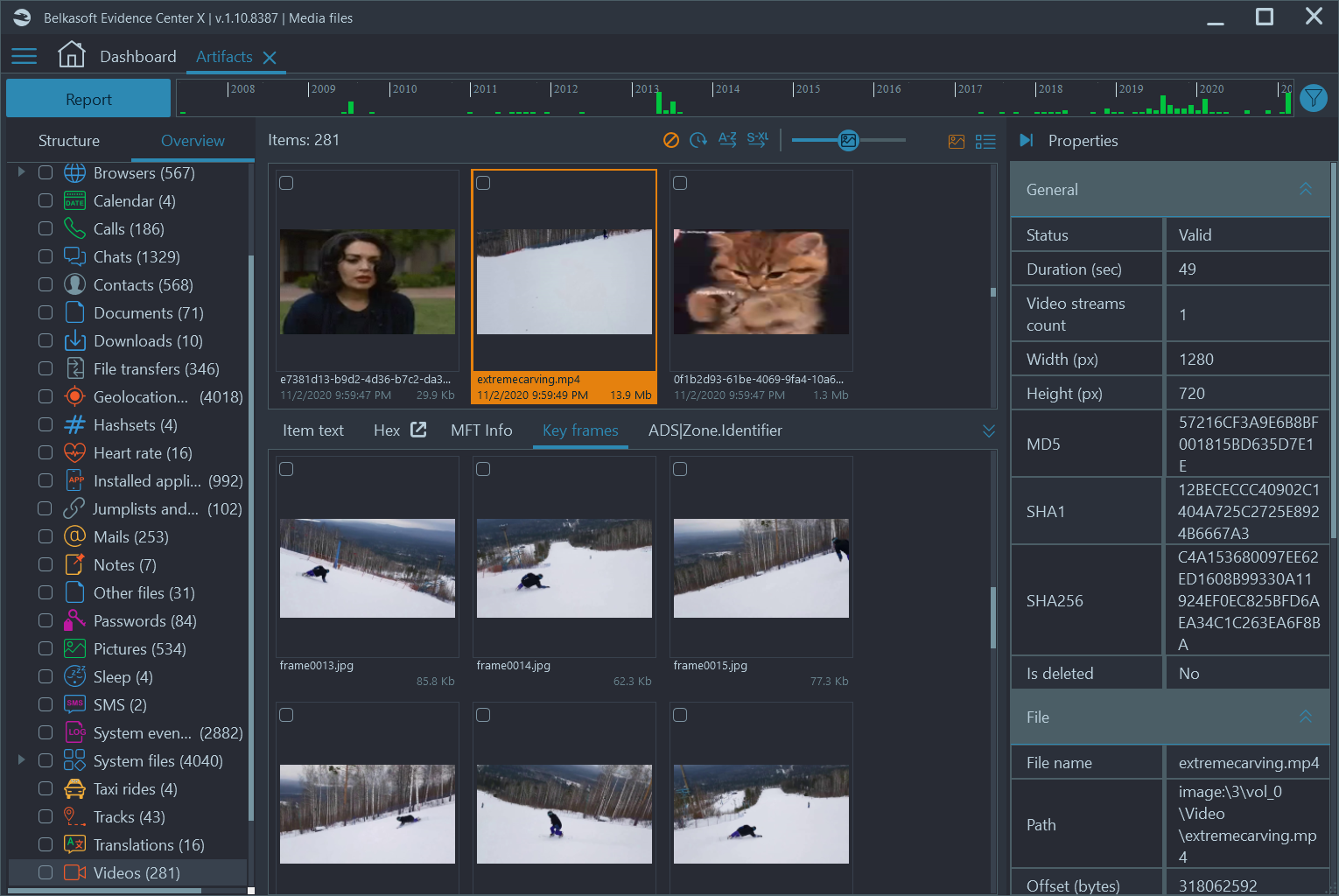
Figure 9: Keyframe analysis functionality in Belkasoft X
Moreover, you can further speed up your analysis by running the same analysis against extracted keyframes as for pictures, like face or pornography detection.
Another useful feature of Belkasoft X is multiple video streams detection. This feature allows you to find videos where illicit content is hidden inside secondary video streams. You can then play these detected videos and select which stream to review, extract keyframes from these streams, and run the same content classifications. Please find more info on this function in our article Multiple video stream detection with Belkasoft X.
Hashset analysis
Though using sets of known file hashes is not specific to media file search, it is typically used to find illegal content inside photos and videos. Belkasoft X allows an examiner to find files whose hash values, calculated in MD5, SHA1, or SHA256, match the provided hashset database. The product supports formats such as NSRL and ProjectVic. You can also implement your own hash set files, where each hash value is placed on a separate line.
Hashes can be specified at the time of adding a data source:
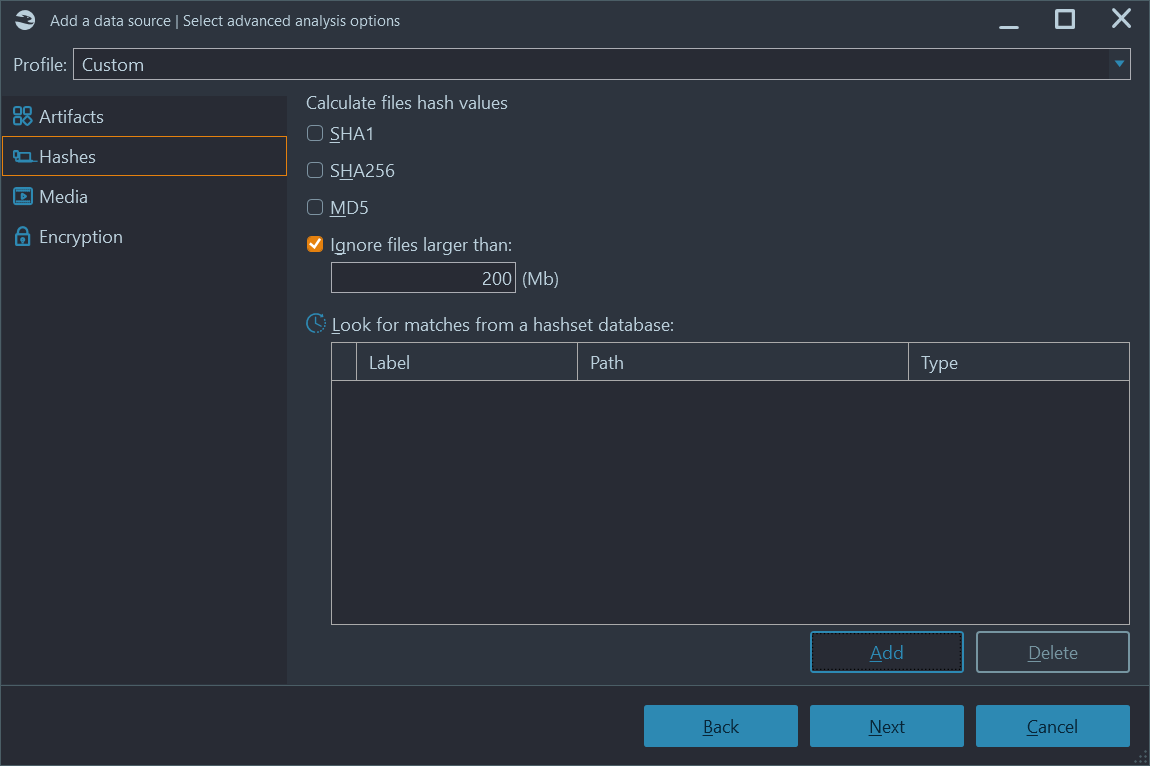
Figure 10: Hashset analysis
The matches, if any, could be found under the Hashsets node of the Overview tab on the Artifacts window.
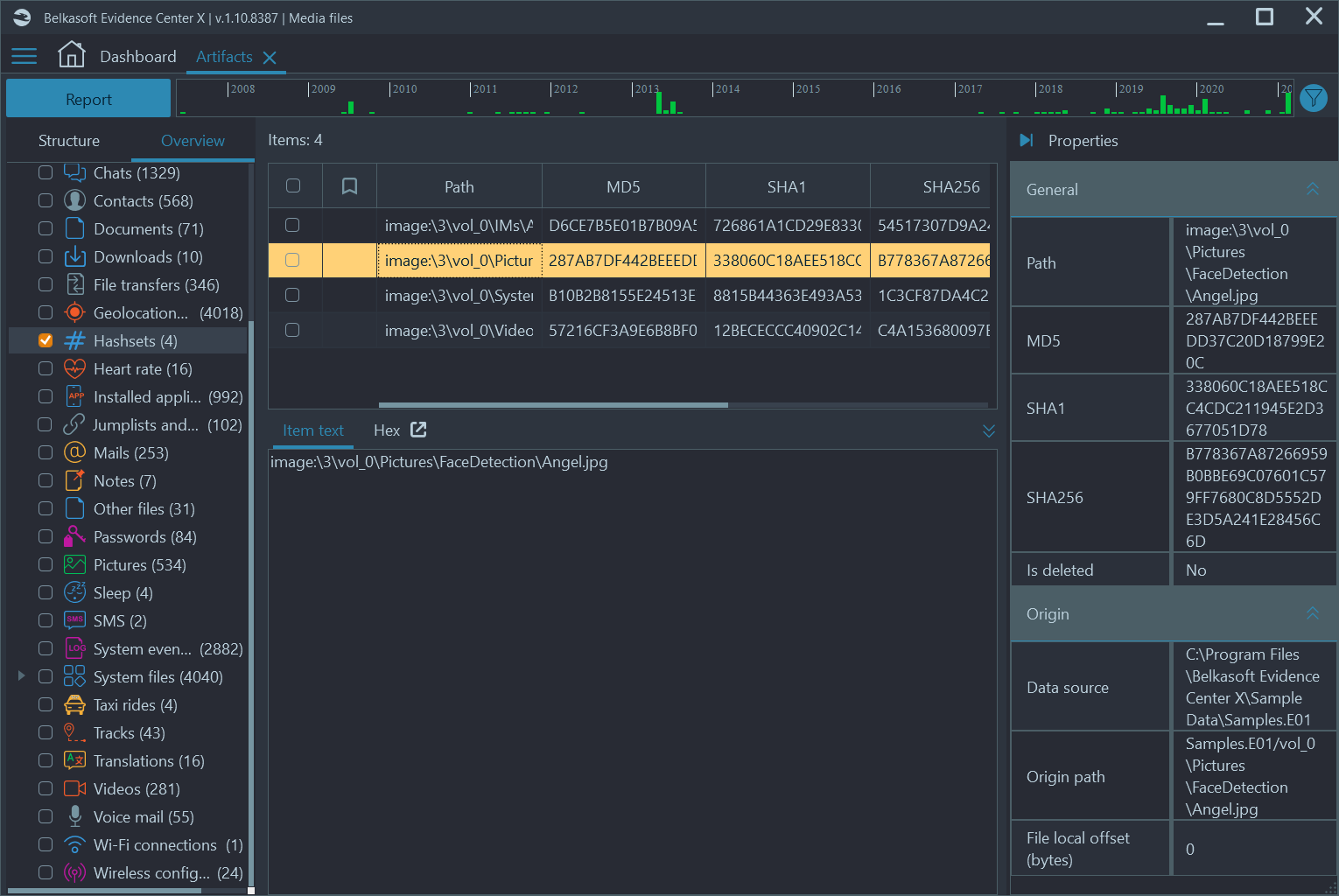
Figure 11: Hashset analysis
Conclusion
In this article, we have described how you can acquire and analyze audio files, pictures, and video files with Belkasoft X.
The product has features that allow you to detect audio files, both existing on a device and ones that are deleted, as well as to play existing audio files with a built-in media player.
Belkasoft X can also show image files extracted from various data sources, including the most complex cases like pictures carved from unallocated and slack space. With Belkasoft X, you can perform multiple operations on pictures, including filtering them by time, camera model, manufacturer, and existence, or absence of location metadata. The product allows you to detect such content inside pictures, such as skin tone, pornography, faces, guns, texts, and even language detection.
As for video files, Belkasoft X also offers a wide variety of features to perform proper analysis, including keyframe extraction and multiple video streams detection.