Introduction
Built-in encryption, in many of its facets, became a standard within the last few years. Thanks to the use of Solid State Drives (SSD) as primary storage for computers, quick flash memory and processors on mobiles, there is no more performance penalty on the use of encrypted storage. We witnessed the transition from encryption, which had to be explicitly enabled (as it noticeably hurt device performance and responsiveness), to 'built-in' encryption as hardware and software performance improved. Today, how many users know that their iPhone or Android has all their data encrypted, even though they did not opt-in for it?
The broad use of encryption presents new, unique challenges for a digital forensic examiner or a corporate incident responder. Modern encryption is reliable and strong; all 'childhood' flaws that previously enabled one to easily brute-force a password, are now fixed. In fact, some encryption can be reliable enough to assure it takes billions of years to guess a reasonably strong password—unless we have quantum computing capabilities. Thus, we have to develop techniques and methodologies to address file-based and whole device encryption, in our investigations.
In this article, we highlight what decryption support an investigator or a responder has available to them within Belkasoft Evidence Center X, the flagship software product for digital forensics and cyber incident investigations by Belkasoft.
Encryption types
There are roughly two types of encryptions: file-based encryption (FBE) and whole disk encryption (WDE), or full disk encryption (FDE). WDE may be volume or partition-based. Full-volume encryption (FVE) is a form of WDE where only a single partition of a file system is encrypted. For WDE, possibly the most famous technology is called BitLocker, which is built-in to the latest versions of Windows.
To provide a little more background, a good example of FBE is any file on an iPhone. Another good example is an encrypted zip file, which is quite common for sharing sensitive or private information.
How to detect file encryption within Belkasoft X
Equipped with Belkasoft X, an investigator can detect both types of encryptions described above, FBE and WDE.
The software comes with a built-in detection of file-based encryption. To enable search functionality for encrypted files, select the 'Search for encrypted files and volumes' on the Encryption page of Advanced analysis options of the 'Add data source' window (shown below):
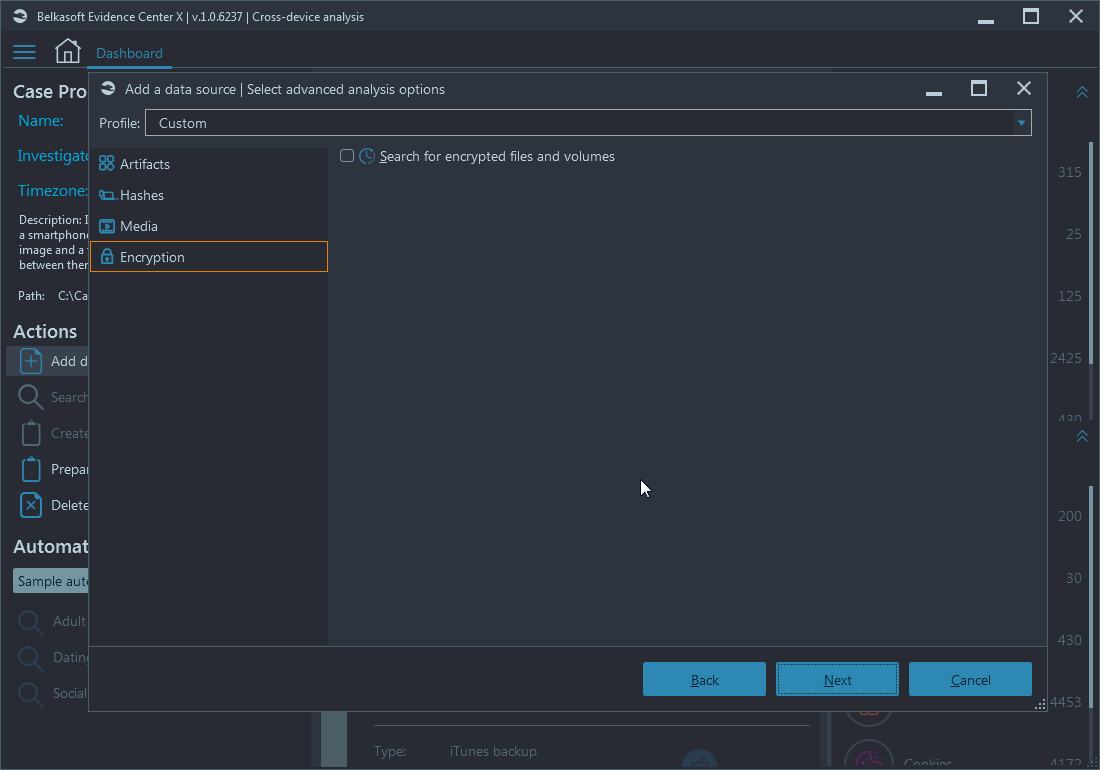 Figure 1: Belkasoft X Advanced Analysis options—Encryption
Figure 1: Belkasoft X Advanced Analysis options—Encryption
Note: Search for encryption is a time-consuming operation, so if you are in rush or encrypted files are not your primary focus, you may want to unselect this option for the first pass of analysis. You can always schedule encryption detection for a later time.
Once the analysis completes, you will find all the files, which Belkasoft X detected as encrypted, under the Encrypted files node of the 'Artifacts' window:
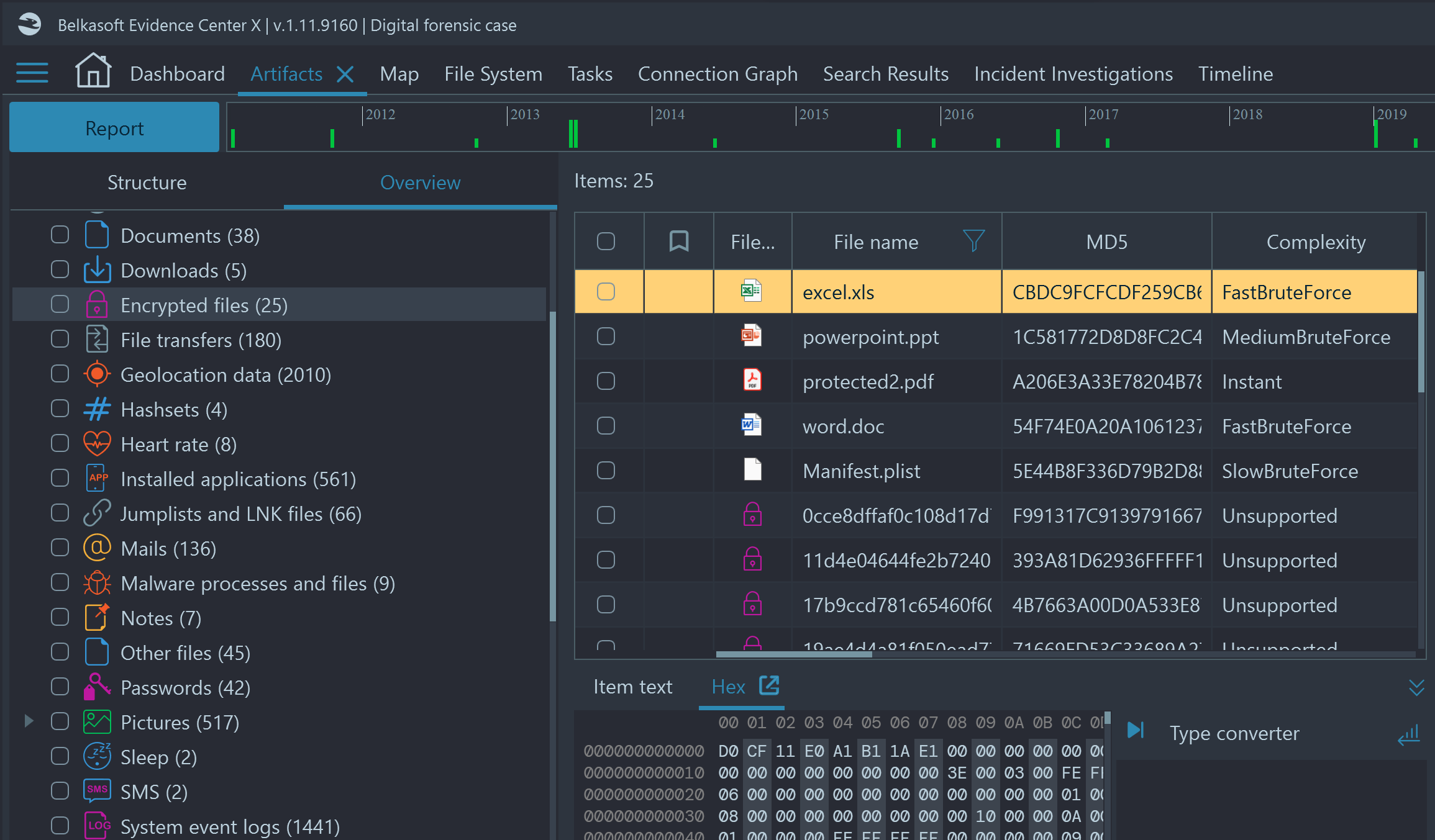 Figure 2: Belkasoft X Artifacts windows—Detected encrypted files
Figure 2: Belkasoft X Artifacts windows—Detected encrypted files
This view will show you the following details:
- File name.
- Hash values, including message-digest algorithm (MD5) and the Secure Hash Algorithm (both SHA1 and SHA256).
Note: SHA256 is the hash function and mining algorithm of the Bitcoin protocol. - Complexity to decrypt, which can be instant, fast, medium or slow brute-force. While the instant, fast and medium methods are likely to finish in a reasonable time without additional information (such as key dictionaries which are explained below), the 'slow brute-force' decryption algorithm is likely to take billions of years to complete even with modern technology.
- Protection features, for example ‘open password’, which means that if a file is password protected, it may only be accessed with the correct password. Additional permission restrictions may also apply (e.g. printing or copying not allowed).
- Recovery options, which display various hints to improve your chance of success. Some examples are 'Rainbow table attack', 'Hardware acceleration possible' (meaning that using a GPU farm may help significantly) or 'File patching required'.
- File-open password, which is empty unless you run the brute-force function of Belkasoft X.
- Other columns include: file system date and times, is deleted, full path etc.
Supported file types
Belkasoft X recognizes hundreds of encrypted file types.
Among them are (click to expand):
- 1Password for Mac
- 1Password for Windows (incl. OPVault, Online)
- Acrobat 3.0
- Acrobat 4.0
- Acrobat 5.0
- Acrobat 6.0
- Acrobat 7.0
- Acrobat 8.0
- Acrobat 9.0
- Acrobat 10.0
- Acrobat 11.0
- Acrobat Revisions 3-4
- Android 4.3-4.4
- Apple iTunes Backup / iOS 4.x-9.x
- Apple iTunes Backup / iOS 10.x
- Symantec ACT! 2.0
- Symantec ACT! 3.0
- Symantec ACT! 4.0
- Symantec ACT! 2000
- ACT! by Sage 2005
- ACT! by Sage 2006
- ACT! by Sage 2007
- ACT! by Sage 2008
- ACT! by Sage 2009
- BestCrypt 6.0
- BestCrypt 7.0
- BestCrypt 8.0
- Bitcoin Wallet: Blockchain.info, Blockchain.com
- Bitcoin Wallet: Bitcoin Core
- Bitcoin Wallet: Electrum
- Dashcoin Wallet: Dash Core
- Dashlane
- Dell Encryption/Data Protection Recovery file
- Dogecoin Wallet
- FileMaker Pro 3.x
- FileMaker Pro 4.x
- FileMaker Pro 5.x
- FileMaker Pro 6.x
- FileMaker Pro 7.x
- FileMaker Pro 8.x
- FileMaker Pro 9.x
- FileMaker Pro 10.x
- FileMaker Pro 11.x
- FileMaker Pro 12.x
- FileMaker Pro 13.x
- FileMaker Pro 14.x
- FileMaker Pro 15.x
- FileMaker Pro 16.x
- FileMaker Pro 17.x
- FileMaker Pro 18.x
- FileMaker Pro 19.x
- Google Chrome Website
- ICQ 2000-2003
- ICQ 99a
- ICQ Lite
- iWork 2009
- iWork 2013
- iWork 2020
- KeePass
- LastPass
- Litecoin Wallet
- Lotus 1-2-3 1.1+
- Lotus Notes 4.x
- Lotus Notes 6.x
- Lotus Notes 7.x
- Lotus Notes 8.x (RC2, AES encryption)
- Lotus Organizer 1.0
- Lotus Organizer 2.0
- Lotus Organizer 3.0
- Lotus Organizer 4.0
- Lotus Organizer 5.0
- Lotus Organizer 6.0
- Lotus Word Pro 96-99
- macOS X Keychain
- macOS X User / Hash
- macOS X 10.8-10.10 User / Hash
- Microsoft Edge Website
- Mozilla Firefox Website
- MS Access 2.0
- MS Access 95
- MS Access 97
- MS Access 2000
- MS Access 2002
- MS Access 2003
- MS Access 2007
- MS Access 2010
- MS Access 2013
- MS Access 2019
- MS Access 2.0 System Database
- MS Access 97 System Database
- MS Access 2000 System Database
- MS Access VBA
- MS Backup
- MS Excel 4.0
- MS Excel 5.0
- MS Excel 95
- MS Excel 97
- MS Excel 2000
- MS Excel 2002
- MS Excel 2003
- MS Excel 2007
- MS Excel 2010
- MS Excel 2013
- MS Excel 2016
- MS Excel 2019
- MS Pocket Excel
- MS Excel VBA
- MS Internet Explorer Website
- MS Internet Explorer Webform
- MS Internet Explorer Content Advisor
- MS Mail
- MS Money 99 or earlier
- MS Money 2000-2001
- MS Money 2002
- MS Money 2003-2004
- MS Money 2005-2007
- MS OneNote 2003 Section
- MS OneNote 2007 Section
- MS OneNote 2010 Section
- MS OneNote 2013 Section
- MS OneNote 2019 Section
- MS Outlook 2000/2003/2007/2010/2013/2016/2019 Email Account
- MS Outlook 2000/2003/2007/2010/2013/2016/2019 Form Template
- MS Outlook 2000/2003/2007/2010/2013/2016/2019 Personal Storage
- MS Outlook Express Account
- MS Outlook Express Identity
- MS PowerPoint 2002
- MS PowerPoint 2003
- MS PowerPoint 2007
- MS PowerPoint 2010
- MS PowerPoint 2013
- MS PowerPoint 2019
- MS PowerPoint VBA
- MS Project 95
- MS Project 98
- MS Project 2000
- MS Project 2002
- MS Project 2003
- MS SQL 2000
- MS SQL 2005
- MS SQL 2008
- MS SQL 2012
- MS SQL 2014
- MS SQL 2016
- MS SQL 2017
- MS SQL 2019
- MS Word 1.0
- MS Word 2.0
- MS Word 3.0
- MS Word 4.0
- MS Word 5.0
- MS Word 6.0
- MS Word 95
- MS Word 97
- MS Word 2000
- MS Word 2002
- MS Word 2003
- MS Word 2007
- MS Word 2010
- MS Word 2013
- MS Word 2016
- MS Word 2019
- MS Word VBA
- MYOB earlier than 2004
- MYOB 2004
- MYOB 2005
- MYOB 2006
- MYOB 2007
- MYOB 2008
- MYOB 2009
- MYOB 2010
- Network Connection
- Norton Backup
- OpenDocument
- Opera Website
- Paradox Database
- Peachtree 2002-2006
- Peachtree 2007
- Peachtree 2008
- Peachtree 2010
- Peachtree 2013
- PGP Desktop 9.x-10.x Zip
- PGP Desktop 9.x-10.x Private Keyring
- PGP Desktop 9.x-10.x Virtual Disk
- PGP Desktop 9.x-10.x Self-Decrypting Archive
- GnuPG Private Keyring
- Quattro Pro 5-6
- Quattro Pro 7-8
- Quattro Pro 9-12, X3, X4
- QuickBooks 3.x-4.x
- QuickBooks 5.x
- QuickBooks 6.x-8.x
- QuickBooks 99
- QuickBooks 2000
- QuickBooks 2001
- QuickBooks 2002
- QuickBooks 2003
- QuickBooks 2004
- QuickBooks 2005
- QuickBooks 2006
- QuickBooks 2007
- QuickBooks 2008
- QuickBooks 2009
- QuickBooks 2010
- QuickBooks 2011
- QuickBooks 2012
- QuickBooks 2013
- QuickBooks 2014
- QuickBooks 2015
- QuickBooks 2016
- QuickBooks 2017
- QuickBooks 2018
- QuickBooks 2019
- QuickBooks 2020
- QuickBooks 2021
- QuickBooks for Mac 2012
- QuickBooks for Mac 2013
- QuickBooks for Mac 2014
- QuickBooks for Mac 2015
- QuickBooks for Mac 2016
- QuickBooks Backup
- Quicken 95/6.0
- Quicken 98
- Quicken 99
- Quicken 2000
- Quicken 2001
- Quicken 2002
- Quicken 2003
- Quicken 2004
- Quicken 2005
- Quicken 2006
- Quicken 2007
- Quicken 2008
- Quicken 2009
- Quicken 2010
- Quicken 2011
- Quicken 2012
- Quicken 2013
- Quicken 2014
- RAR 2.0 Archive
- RAR 2.9-4.x (AES Encryption) Archive
- RAR 5.x Archive
- Remote Desktop Connection
- Safari Website
- Schedule+ 1.0
- Schedule+ 7.x
- Tally.ERP 9
- Unix OS User Hash
- WordPerfect 5.x
- WordPerfect 6.0
- WordPerfect 6.1
- WordPerfect 7-12, X3, X4
- WPA/WPA2
- WinZip 8.0 or earlier
- Yandex Browser Website
- Zip Archive
- 7-Zip Archive
How to detect WDE/FVE encryption with Belkasoft X
Belkasoft X can also detect WDE/FVE. Unlike file-based encryption, which you have to explicitly start, the detection of whole disk encryption happens automatically whenever you add a new data source to the case.
If any of drive partitions are detected as encrypted, you will see the drive depicted with the lock icon to the left, and a prompt to enter decryption data.
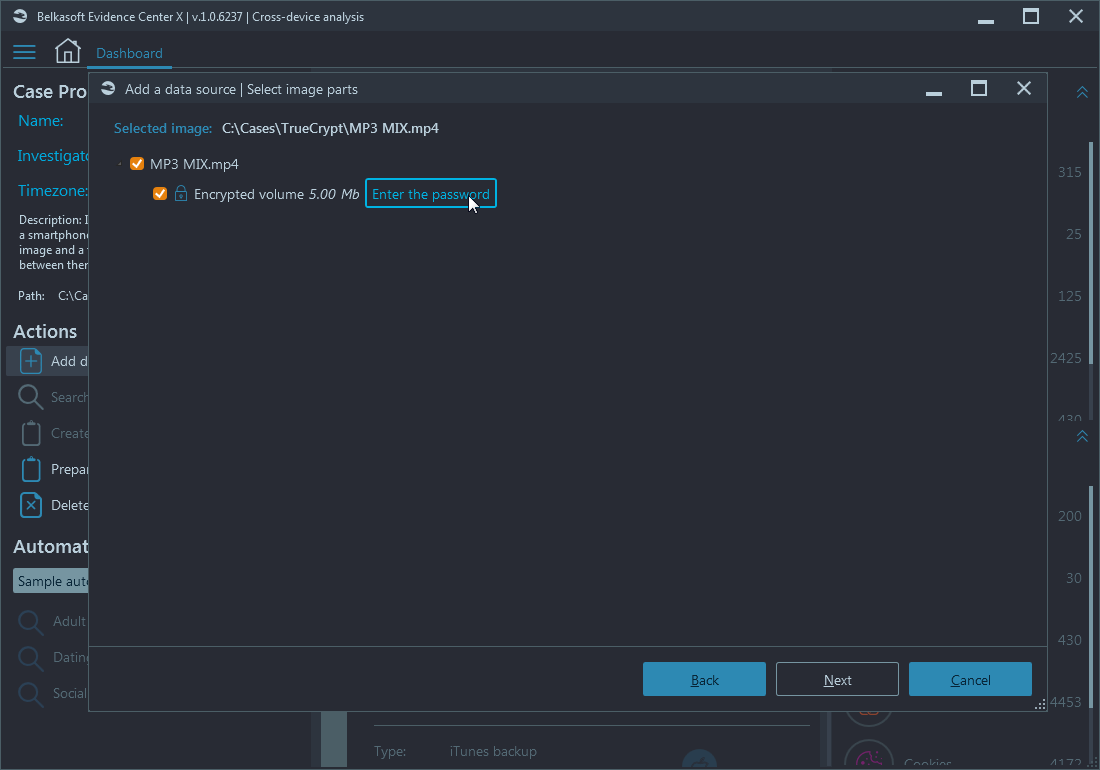 Figure 3: Belkasoft X Add a data source—Encrypted volume
Figure 3: Belkasoft X Add a data source—Encrypted volume
Click the 'Enter the password' button to open a window and enter a password, decryption key, recovery file, or unique piece of data, specific to the encryption in use:
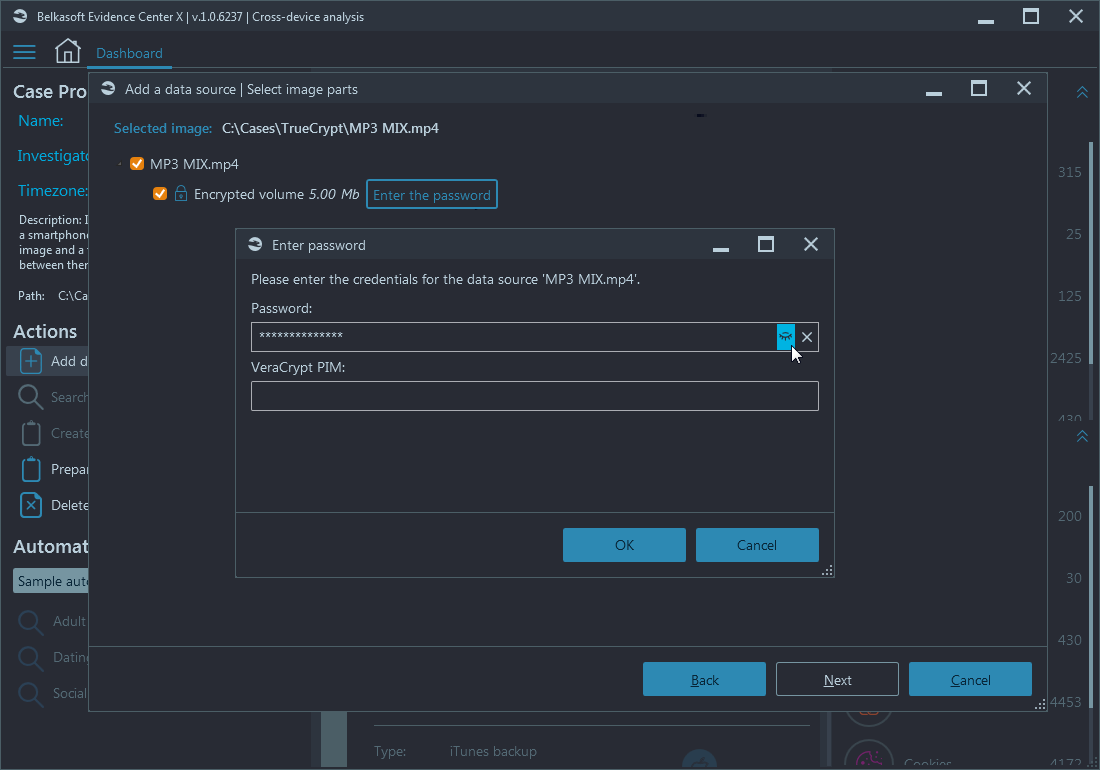 Figure 4: Belkasoft X Add a data source—Encrypted volume credentials
Figure 4: Belkasoft X Add a data source—Encrypted volume credentials
If the password or other decryption details are entered correctly, the structure of the partition will be expanded, making the partition available for the further analysis. If you do not know the correct details, you can still analyze other partitions—but not this particular partition.
Supported and Recognized WDE/FVE types
When adding a data the following types of whole disk encryption (WDE) and full volume encryption (FVE) will be recognized automatically by the Belkasoft X software:
- APFS
- BitLocker
- DriveCrypt
- FileVault2
- LUKS
- McAfee Drive Encryption
- PGP WDE
- Symantec Endpoint Encryption
- TrueCrypt
- VeraCrypt
The encryption types above may be decrypted by providing the correct decryption information.
Brute-forcing passwords
Belkasoft X comes equipped with a feature to brute-force (meaning 'guess via multiple tries') a password for file-based encryption. To use this feature, you must have a separate 'File Decryption module' customized specifically for Belkasoft X and decrypting a multitude of encrypted devices.
To perform 'Brute-force password' decryption, go to the 'Artifacts' window and navigate to the 'Encrypted files' node. Right-click on the node to decrypt all detected files or individually select single or multiple files in the file list. The pop-up menu will contain the 'Brute-force password' options where you will be prompted to select a brute-force method:
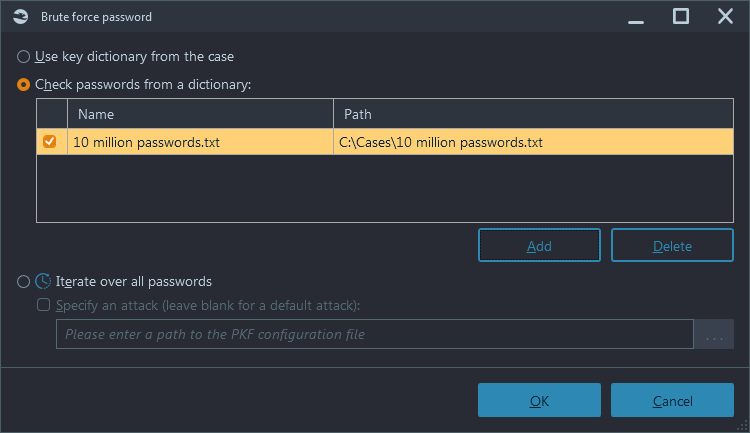
Figure 5: Belkasoft X Brute-force password window
The methods available are:
- Use key dictionary from the case
- Use external password dictionaries
- Iterate over all passwords (which match a specific type of attack)
Using a key dictionary
The first option will configure Belkasoft X decryption to attempt applying all text found in your case inside the text of artifacts previously extracted. Meaning, the decryption algorithm will use all the language from Word and Excel files, chats, pictures metadata, email and so on, and use found text as a password, one by one. This approach significantly improves your chances to identify the password. It is important to note that the more data you have analyzed from a specific user, the higher the chances of a successful brute-force attempt. Most users typically use passwords based upon their experience and language. Unless auto generated, terms like a car model, license plate number, family member names, birth dates or the like, have the best chance to appear in non-password related files and be stored as a plain text.
Using an external password dictionary
The second option allows you to attach third-party dictionaries containing some of the most popular passwords. If the password in use resides in a 'password dictionary', the brute-force process should make for an easy day.
Belkasfoft X comes equipped with a useful 10 million password starter dictionary, but you can browse and add any other dictionaries provided they put a single password per line.
Iterate over all passwords
The third and final option should only be used when all other attempts have failed to produce results. This option will attempt all passwords sequentially, e.g. "a, b, c… z," then "aa, ab, ac" and so on. As you can imagine, the number of potential passwords is incredibly huge, especially considering non-Latin characters, numbers, special symbols, hieroglyphs, etc. This means the chance of success using brute-force attempts against a long and reliable password is pretty remote. Hardware acceleration may help and decrease the number of years required for a successful brute-force attempt from billions of years to a mere 100 million.
Belkasoft X does have a limit for the character length of attempted passwords. Passwords up to a length of fourteen characters may be attempted (and for some of the most used patterns—if you leave the 'Specify an attack' field blank).
If you know that the password to a file is longer than fourteen characters, or if you have other prior knowledge as to what the password would likely be, we recommend you customize the brute-force method inside of the standalone Passware Kit Forensic tool included in the File Decryption module . You can then browse and select the customized attack file for use in the brute-force options window within Belkasoft X. This configures the brute-force password attempts according to the attack specified.
Keyword dictionary generation
In the event built-in brute-force using the key dictionary file does not work, you can also generate a key dictionary for use with Passware Kit Forensic (or other similar third-party tools). To do so, open the Dashboard window of Belkasoft X and under 'Actions' select the 'Create key dictionary' item:
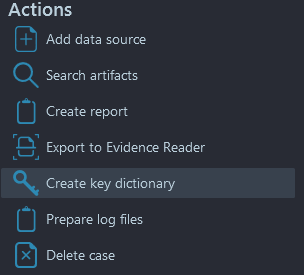
Figure 6: Belkasoft X Actions—Create key dictionary item
This creates a simple key dictionary text file containing all the text from the case, one term per line. You can then use this file as your basis for subsequent brute-force or password mutations (some are described below).
One important note, do not forget that you have to analyze your data sources prior to attempting this technique (adding data sources to the case without artifact analysis will not generate a meaningful key dictionary).
Using external password dictionaries
There are many "frequently used password" dictionaries available over the Internet. Some contain a few million of the most used passwords; others may contain as many as one billion passwords. In particular, one such dictionary is provided by Passware on their customer portal. Additionally, Belkasoft X comes equipped by default with a 'small' dictionary to help you gets started consisting of around ten million passwords for your initial brute-force attempts.
If you chose the brute-force decryption option, you may select one or even multiple dictionaries: the default dictionary option is shipped and included with the standard product installation. Other dictionaries may be added as needed. Each time you run the brute-force task, use the checkboxes to select one or multiple dictionaries for decryption:
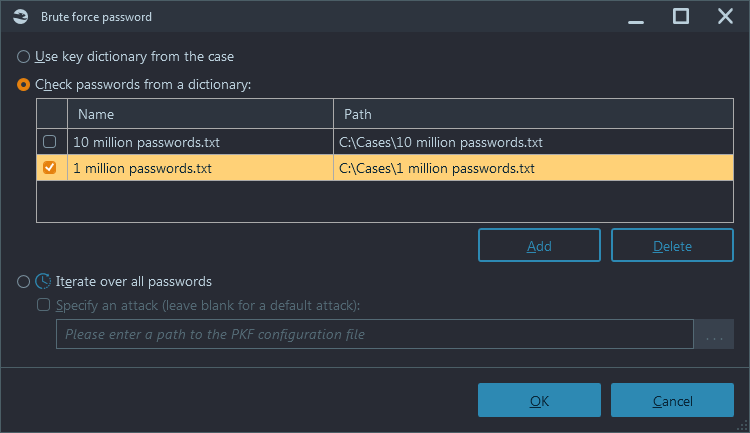
Figure 7: Belkasoft X Brute-force password—Select dictionaries
Password mutations
One popular trick some suspects may utilize with their passwords is to change a letter to a similar looking number or special character in an attempt to make their password stronger and harder to crack. An example could be 'p4ssw0rd' instead of 'password'. This password trick can be cracked using so-called 'password mutations', supported by modern decryption tools, like Passware's Kit Forensic.
Belkasoft X does not offer this feature built-in, but as with the key dictionary, you can use the same extracted language as a basis for mutations. Terms from such key dictionaries can be used for mutations and can be combined together, and so on. This is not a quick operation because there are many different possible mutations, however it is still significantly quicker than testing all potential passwords.
Conclusion
Built-in encryption is now simply a part of our lives and we will never return to the good old days when encryption was typically disabled and rarely encountered. The widespread use of encryption ushers in a new set of challenges for digital investigators and corporate incident responders, but these challenges must be met head on with new techniques and tools.
To recap, we can roughly divide encryption by file-based (FBE) and whole-disk (WDE, FDE, FVE) methods. Encrypted ZIP-files and BitLocker partitions are a good example of both.
Strong passwords and reliable modern encryption technologies make it almost impossible to decrypt files and disks; however, there is still hope for either a weak password or for capabilities like those found with Belkasoft X and its custom key dictionary generator, which extracts all language used by the suspect in your case, as a base for password brute-forcing.
Belkasoft X supports encrypted file search as well as brute-forcing a password and decryption for both file-based and disk-based encryption (for the former you have to have an optional File Decryption module; for the latter you have to have a WDE module, which comes with Belkasoft X Forensic and Corporate editions). The password or other decryption information must be known to decrypt devices that are secured with WDE. For files, it is possible to run a brute-force attack: either based on the current case language, built-in or external dictionaries of frequent passwords, a sequential brute-force of all available passwords, or a highly customized attack, created with a third-party tool.
