Full File System Extraction of iOS Devices with Belkasoft X
This February we have announced and released a valuable addition to the Belkasoft X iOS forensics toolkit—the support of iOS full file system extraction via the checkm8 BootROM exploit. The article lists all the key benefits of this new acquisition method.
In September 2019, an independent researcher axi0mX discovered and released a new iOS exploit called checkm8. The event has been announced ground-breaking, as checkm8 affects hundreds of millions of Apple devices, including iPhone, iPad, and it cannot be patched.
What does it mean? It means that the devices already in use are vulnerable. And, of course, it is an opportunity for digital forensic experts as well: support for checkm8 enables Belkasoft X to make a full file system extraction and subsequently analyze all the retrieved data.
Why is сheckm8-based full file system extraction so сool?
This February we have announced and released a valuable addition to the Belkasoft X iOS forensics toolkit—the support of iOS full file system extraction via the checkm8 BootROM exploit. So, what are the key benefits you get with this new release?
1. Unpatchable vulnerability
Apple cannot fix the checkm8 exploit with iOS updates since the vulnerability is in SecureROM, located on flash memory that cannot be reprogrammed. The only solution for Apple is to replace the chip, which means recalling every phone that has this vulnerability. It is too expensive and impractical for any vendor. That is why the checkm8-based full file system extraction will be possible with Belkasoft X for long years. And that is why checkm8 is called a game-changer.
2. Available on Windows
All public implementations of the checkm8 exploit run on macOS and Linux operating systems only. However, our method allows using this vulnerability on computers with Windows 10.

3. Forensically sound
Jailbreaking a device is a complex, unsafe, and not quite forensically sound process. You do not need to jailbreak a device to create an image of a phone memory if you have Belkasoft X. The tool does not leave any traces on a device and does not require access to the Internet.
4. Extraction from locked devices
Our new method allows you to partially acquire data from locked devices. Of course, you will not be able to acquire as much data as you can get from an unlocked device, but it is still much better than nothing.
5. Support of a vast range of iOS versions
The new approach allows you to investigate iPhones from 5S to X (and the corresponding iPad models) and running iOS versions from 12.0 to 16 beta.
6. Easy to use
All you need is a device itself and the original cable. Nothing more is required. You do not even need an Apple Developer account.
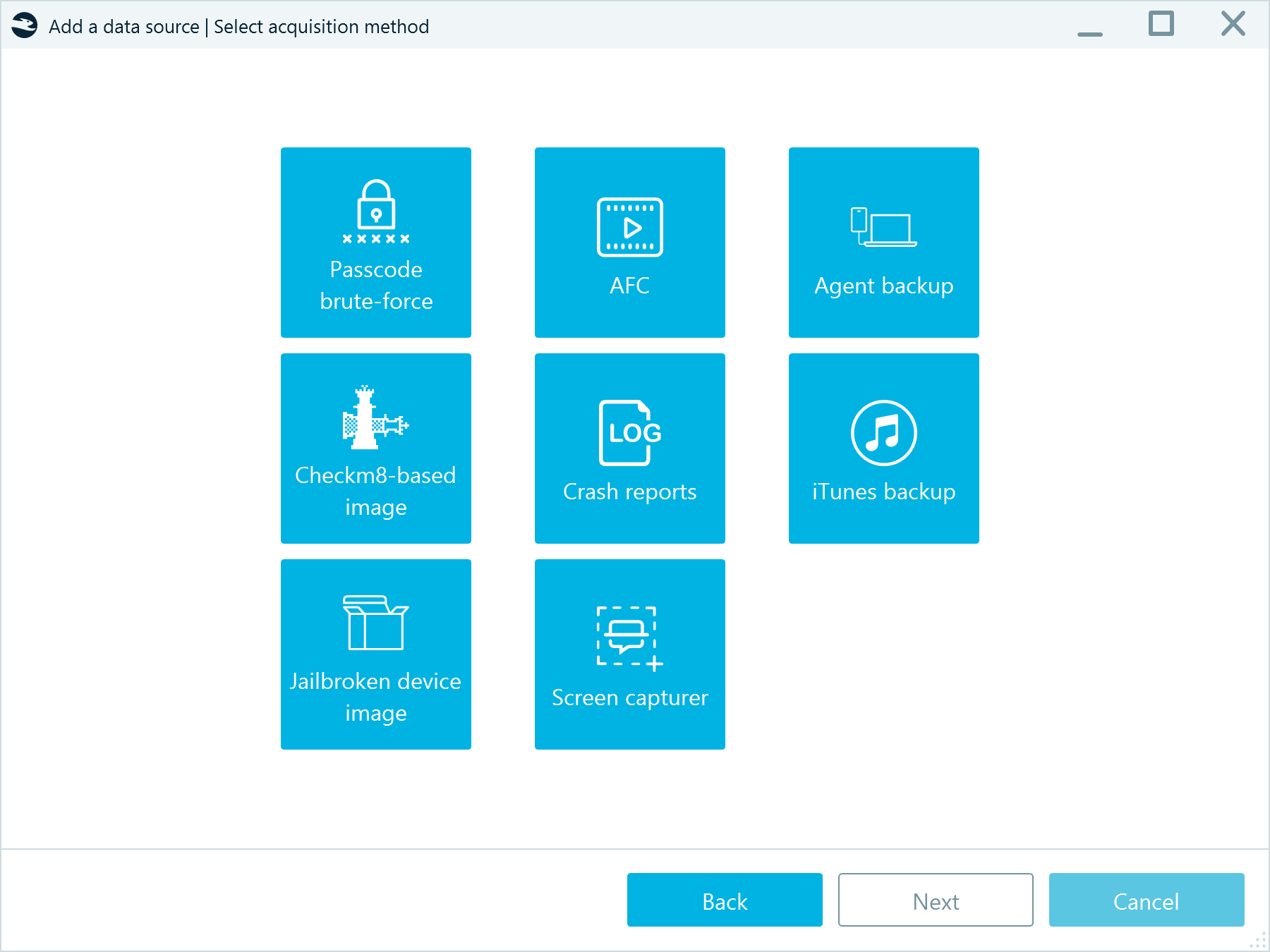
Conclusion
To sum up, checkm8 turned out to be a new and break-through feature which changed the iOS device market for long. The acquisition of iDevices is easier now than ever before.
The Belkasoft development team is constantly monitoring current digital forensics trends and turns all known device vulnerabilities into our customers’ advantage in Belkasoft X. With the benefits of the latest Belkasoft X version mentioned in this article, the investigator’s routine is simplified. Belkasoft is among the two vendors on the market who were the first to implement checkm8 support in the product, and it is important to stress, that all the features highlighted above are available at a very affordable price in comparison to our competition.
