Decoding Windows Registry Artifacts with Belkasoft X: UserAssist
Introduction
The Windows registry is a structured database housing configuration settings for Microsoft Windows operating system (OS) components and numerous applications. For digital forensic examiners investigating Windows machine data, it is one of the primary places to look for traces of malicious or illicit activity on the system.
The registry keeps track of OS and application settings and user-specific data. While users typically do not interact with it directly, their activities are often recorded when they run installers or applications. The HKEY_CURRENT_USER registry hive stores settings specific to the user currently logged in to the system.
One particularly valuable artifact stored under this hive is UserAssist. This part of the registry tracks information about the applications installed and running on the machine, and it can help you find evidence of their presence and execution.
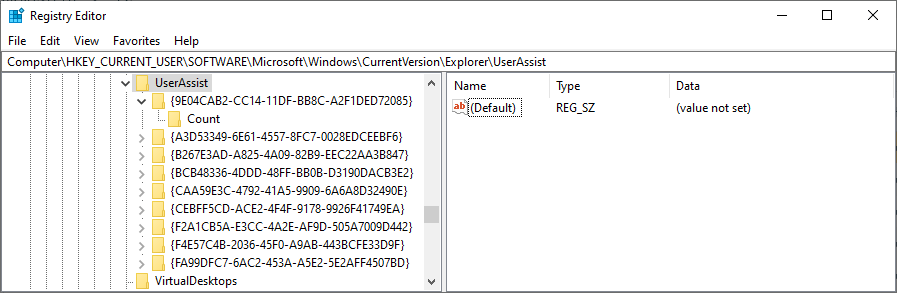
However, it is important to note that not all applications use the Windows Registry to store their configuration and execution details. Even if a record is not found there, it does not necessarily mean that a certain application was never part of the system.
Extracting UserAssist information from the Windows registry
Windows registry stores the HKEY_CURRENT_USER hive data in the NTUSER.DAT file located in C:\Users\%useraccount%. Each user account on the system has its own NTUSER.DAT. This file contains live user configuration information that updates every second. Therefore, copying the file from the system is only possible when the user is not logged in to their account or with the help of specialized tools.
The quickest way to obtain UserAssist data is to analyze the C:\Users\%useraccount% folder using a digital forensics and cyber incident response (DFIR) tool like Belkasoft X.
Alternatively, you can acquire the whole registry as part of the system disk drive in Belkasoft X or—if you are dealing with a remote machine—Belkasoft R. Physical acquisition is particularly useful if you suspect some registry entries may have been deleted. It enables you to use carving to try and restore deleted records when analyzing the acquired disk.
Analyzing the UserAssist artifact in Belkasoft X
You can parse NTUSER.DAT manually; however, it involves delving into file structures and encoding techniques since the file stores information in binary format, and the UserAssist data is obfuscated with ROT13 encoding. Additionally, when dealing with potentially deleted records, regular tools like Registry Editor might not work as expected.
Belkasoft X analyzes registry files and presents UserAssist information under the Explorer programs profile:
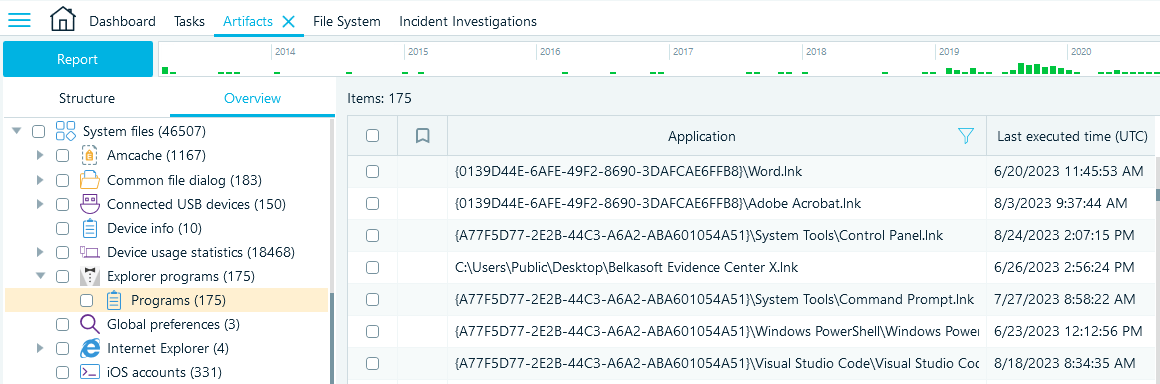
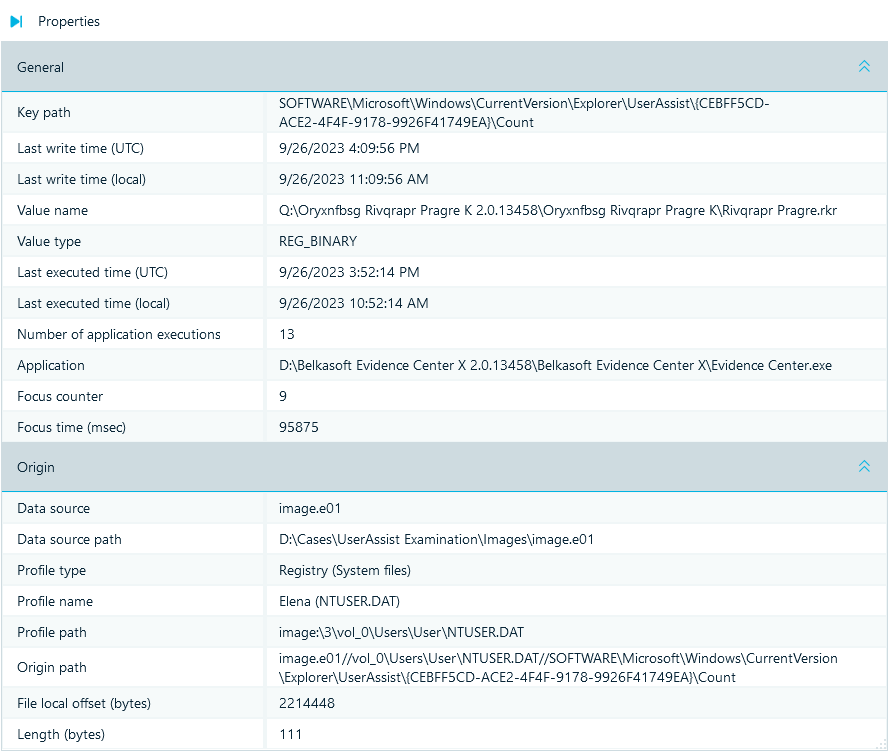
It parses data, decodes ROT13, and provides you with comprehensive details of each application execution recorded in the registry:
- Executed application name and path (the Value name field displays the original value encoded in ROT13)
- Date and time of the last execution
- Application run count
- Additional context details, such as the key path, focus counter, and time
The Application field may display the path in two ways, depending on where the program was run:
- The actual execution path on the machine, such as "C:\Program Files\ExampleApp"
- The GUID/path combination, where GUIDs represent a standard system folder. You can find information on how to interpret these GUIDs in Microsoft’s article "Known Folder GUIDs for File Dialog Custom Places"
You should also keep in mind that the focus details, as well as the application run count and execution time values, are not always reliable and straightforward to interpret, as observed by forensic examiners.
Conclusion
The UserAssist registry artifact is a valuable resource for uncovering evidence of application execution and user activities. While obtaining and analyzing this data may be complex, Belkasoft X simplifies the process. It allows you to access and decode UserAssist information, providing comprehensive details on the application execution, thus facilitating and accelerating your digital investigations.
If you want to gain hands-on experience in analyzing UserAssist data, you can download our sample USER.DAT file and request a free trial of Belkasoft X. To import the file into the tool, you will need to save it in a folder and add this folder as an existing data source to a case.
