Jump Lists: Introduction
Jump Lists are an artifact of the Windows OS. It first emerged in Windows 7: this artifact has been present in all the subsequent versions of the Windows OS ever since. Jump Lists make it possible to get quick access to the most recent files opened by this or that app featured by the ‘Start’ menu or ‘Taskbar’.
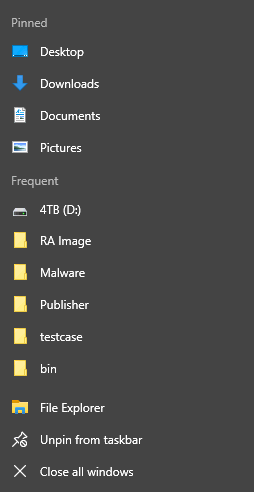
The pull-down menu that appears once the menu icon has been clicked features several zones:
- Destination Zone which includes such sub-categories as the pinned category, known categories (recent or recently closed), custom categories (important).
- Zone of Tasks which embraces User tasks (Tasks) and Taskbar tasks.
- Automatically generated: \Users\ %USERNAME% \AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations
The files to be found in this catalogue have a complex structure. As a rule, data of these files are stored in OLE containers.
- Created by Users: \Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Recent\ CustomDestinations
The files located in this catalogue possess a simpler structure. Among other things, these files indicate where the user pinned a certain Jump List, i.e. whether it is ‘Start Menu’ of ‘Task Bar’.
- Create (timestamp): this parameter indicates the time and date when this app was first launched.
- Modifies (timestamp): this parameter indicates the time and date when this app last launched.
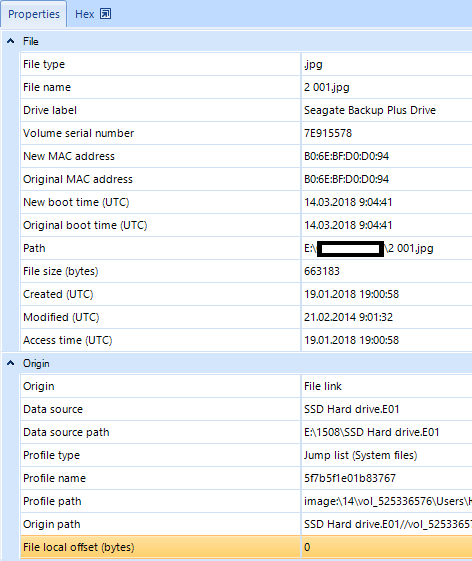
- Data related to the file opened via the app. This data is described in ‘File ’.
- Path means target file info.
- Such parameters as ‘New boot time (UTC)’ and ‘Original boot time (UTC)’ show the time when this file was last opened by the app.
- ‘Origin’ contains those parameters that identify the data source and location parameters examined by the Jump Lists file.
Windows Jump Lists
Users of the earlier version of Windows had to deal with a strictly limited amount of displayed Jump Lists. i.e. between 10 and 12. However, when Windows 10 was released, the situation changed. Now users can define their amount of Jump Lists by themselves via creating the following parameter in the Windows DWORD (32-bit) registry, with the following name: JumpListItems_Maximum.
As for its path, it looks like this: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced.
When it comes to Belkasoft Evidence Center, its users can find the NTUSER.DAT file, in ‘File System’. Its contents can be viewed via the built-in registry viewer.
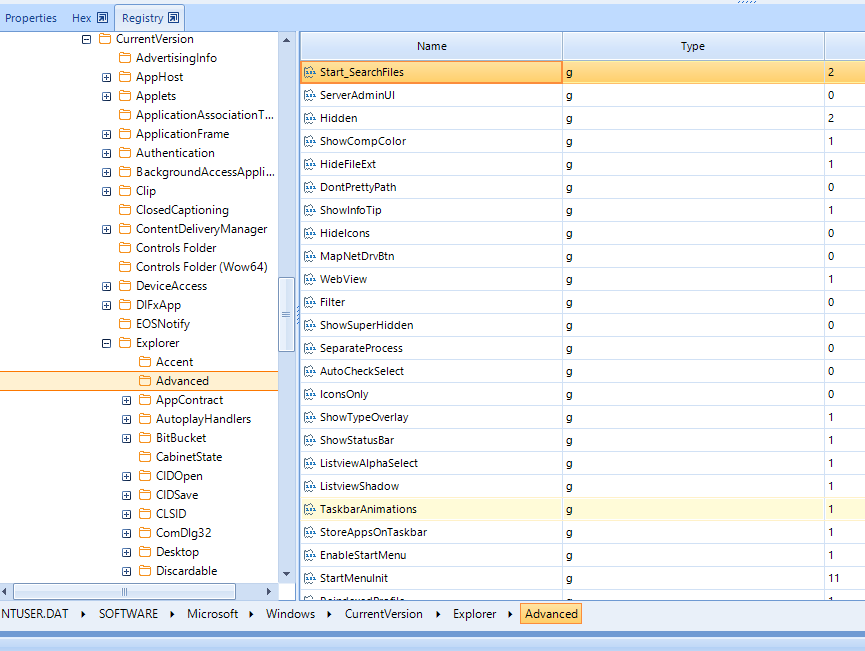
Within the Windows framework, the Jump Lists files can be found here:
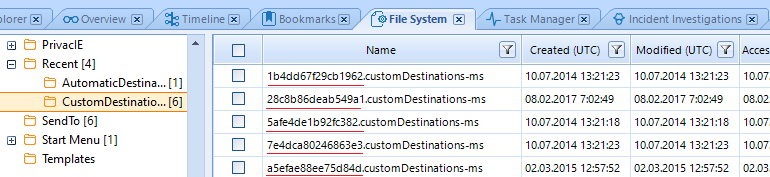
The files stored in these catalogues can be characterized by the following specific features:
AppIDs
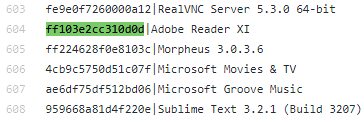
The files in these directories have specific names. The first part is the identifier called ‘AppID’ which makes it possible to identify the app via which one can view certain files.
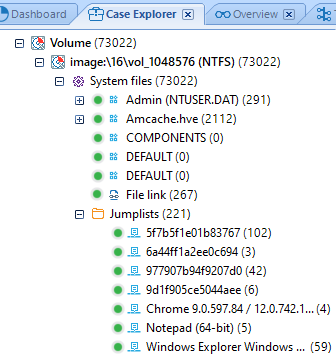
As for the known apps, Belkasoft Evidence Center is capable of displaying their names. When it comes to the unknown apps, one can identify them with these two lists: they match AppIDs with specific applications.
Let us address the following example:
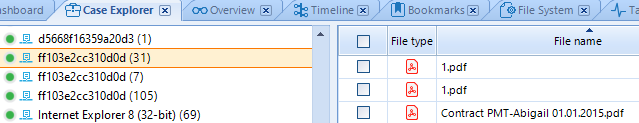
As you can see on the screenshot, several PDF files were opened via the app identified by AppID ff103e2cc310d0d. It is time to find this AppID on the list.
Jump Lists in Belkasoft Evidence Center
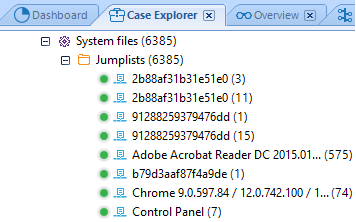
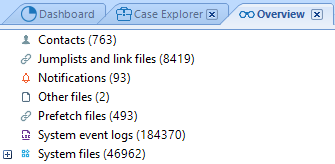
Belkasoft Evidence Center can retrieve data from the Jump Lists files. Their contents can be viewed in BEC’s ‘Case Explorer’ (‘System Files’ category) and ‘Overview’.‘Case Explorer’:
‘Overview’:
Using Jump List to Investigate an Incident
As a rule, while investigating an incident, one examines Jump Lists in conjunction with other artifacts. They include LNK files, Windows Registry (Recent section), system logs, etc.
For example, Jump Lists can be used to analyze such a customary vector of attacks as compromising a target computer via an email with a malicious document. Sometimes, a PC user, being afraid of what happened, may try to destroy such a document (or the archive file in which the malicious document was located). In this case, Jump Lists will help prove that the user did open the document.
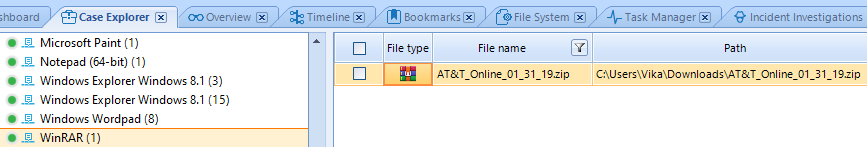
The screenshot below shows some info about the archive file from the email in which the malicious document was located.
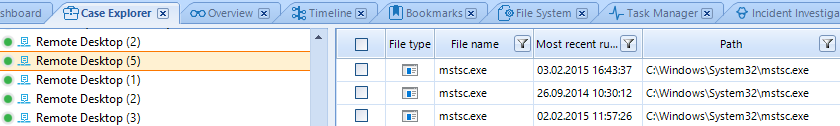
Via analyzing Jump Lists, additional information can be also obtained about actions that attack a compromised computer. The screenshot shows that the attackers activated the command line and launched an RDP client:
Conclusion
Jump Lists are one of the traditional Windows artifacts that can provide an insight into a user's actions on the computer. They can also tell something about their habits (for example, about the applications a user he prefers to use to open certain types of files). Analysis of Jump Lists, in conjunction with other Windows artifacts, can give a more complete picture of attackers on a compromised computer.Download the trial version of Belkasoft Evidence Center at https://belkasoft.com/trial.
Request a quote at https://belkasoft.com/quote.
