Case Study: Leveraging Belkasoft X for a Multi-Source Fraud Investigation
In August 2023, United Kingdom media widely spread a case: a fraudulent builder from Swindon who left work unfinished after pressuring victims to pay more than the agreed price has been sentenced at Reading Crown Court.
During work carried out between October 2015 and January 2019 within several home renovations, Mr Corcoran left customers in severe emotional and financial distress after stopping work mid contract and demanding further sums of money for its completion.
Mr Corcoran was prosecuted following a large investigation by officers from the Council's Public Protection Partnership (PPP) Investigation Team supported by the PPP Joint Case Management Unit, the Council's Legal Services, and the National Trading Standards Tri-Regional Investigation Team.
Digital evidence acquired and processed with Belkasoft X digital forensics software played an important role in proving the defendant guilty.

We interviewed Mark Morris, the digital forensics expert from Aardvark Forensics Ltd who worked the case, about how he conducted this successful investigation.
In this interview:
- Why the Swindon builder case attracts public attention
- When digital forensics comes into play
- The process and techniques of the digital forensic investigation
- Reporting on the findings: ways to share digital forensic evidence
- ISO standards regulating digital investigations
- The role of digital forensic evidence in fraud cases
Why the Swindon builder case attracts public attention
According to media sources, Mr. Corcoran used to secure jobs by declaring dishonest pricing and time promises. Then, he pressured people to pay more by threatening to leave the work unfinished, and he did so on multiple occasions.
Is that accurate? Do you have any details to add to the picture of events?
The term 'rogue trader' may be considered by many as referring to an individual who simply overcharges a (usually vulnerable) homeowner for repairing a roof or driveway.
But it can be far more serious than that. What we see here are victims who wished extensive home improvements, such as an extension to their house, and the sums at stake are well into the tens of thousands of pounds. The work is scoped, and based on promises, a contract is agreed. Often, staged payments are also agreed, so the customer thinks they retain fiscal control of the project.
These are large projects and so require not just a large financial investment from the customer, but an emotional one as well. The amount of stress that a customer may experience by such a project failing can cause ill health, as the matter is so personal to them as it involves their home.
Essentially, the project starts and then 'runs into difficulty' causing demands of money up front to continue. The excuses used to extract additional money are far-reaching, and non-payment can leave the customer in a terrible situation, hugely out of pocket, and then having to pay another company to complete the project.

When digital forensics comes into play
At what stage did the digital forensic department become involved in this investigation?
The investigation agency contacted us to examine the devices once they had been seized by law enforcement in raids on various addresses.
"The ability to examine data from multiple types of devices on a single investigative platform saved time."
What led your team to choose Belkasoft X for this investigation? Were there specific features or capabilities that made it stand out?
We used Belkasoft X software for this investigation because it was a tool we had experience with. The ability to examine data from multiple types of devices on a single investigative platform saved us time.
The process and techniques of the digital forensic investigation
Could you walk us through the process of conducting this investigation?
In cases like these, each device was booked into our exhibit system, evidence bag seal numbers were recorded, and the bags were photographed.
We supply the client with an Evidence Submission form, and this can reveal whether the device is powered on or off, and whether mobile devices have already been put into airplane mode. If necessary, Faraday pouches (that block radio communication to or from a device) will be utilized, if not already used. The form also tells us whether there is any other procedure we need to be aware of (such as fingerprinting or DNA testing).
The bags were then carefully opened (so they could be resealed with security tape, thus reducing the use of fresh plastic).
The contents were then examined, their condition recorded, and they were photographed. With the device then in a protected state, mobile devices were charged.
We then considered the best method for data extraction. In cases such as these, we are provided with many different devices. What is required by the client is a quick turnaround, so they can quickly see and assimilate the evidence.
Which methods did you use to extract data from the devices?
In the case of the computers, it was possible to physically remove the hard drives and connect them to a forensic workstation via a hardware write-blocker. We then used Belkasoft X to extract a cluster-level image of the hard drive.
The phones and tablets were attached to a forensic workstation via USB, and a logical image was taken. We used ADB backup on the Samsung phones and iTunes backup on the iPhones and iPads. This was sufficient as email had been recovered from elsewhere, and it was mainly photos, videos (of building work), and native messaging that were sought from the mobile devices.
What kind of artifacts were you looking for?
In such cases, we look for messaging, voicemail, photographs, and videos of properties and building work. In addition, evidence from geolocation can be useful as it may show that a suspect has misled a victim as to their whereabouts, and it can also reveal evidence of financial flows.
"The advantage of having the evidence from all the devices in one environment is that it makes it easy to remove duplicates."
How did you analyze the acquired data in Belkasoft X? Which techniques helped you do it effectively?
We opened a new case in Belkasoft X and added the data from each exhibit in turn. The advantage of having the evidence from all the devices in one environment is that it makes it easy to remove duplicates. In this particular case, we exported emails into Excel and used conditional formatting to deduplicate them and provide the customer with a tidier output.
Belkasoft X also makes it possible to identify patterns of communication amongst various parties using the connections screen, which provides a graphical representation of how often a particular third party was contacted. This makes it easy to disprove a claim that Party A only vaguely knew Party B and was not in regular contact with them and show the jury a graphical representation of such contact in context.
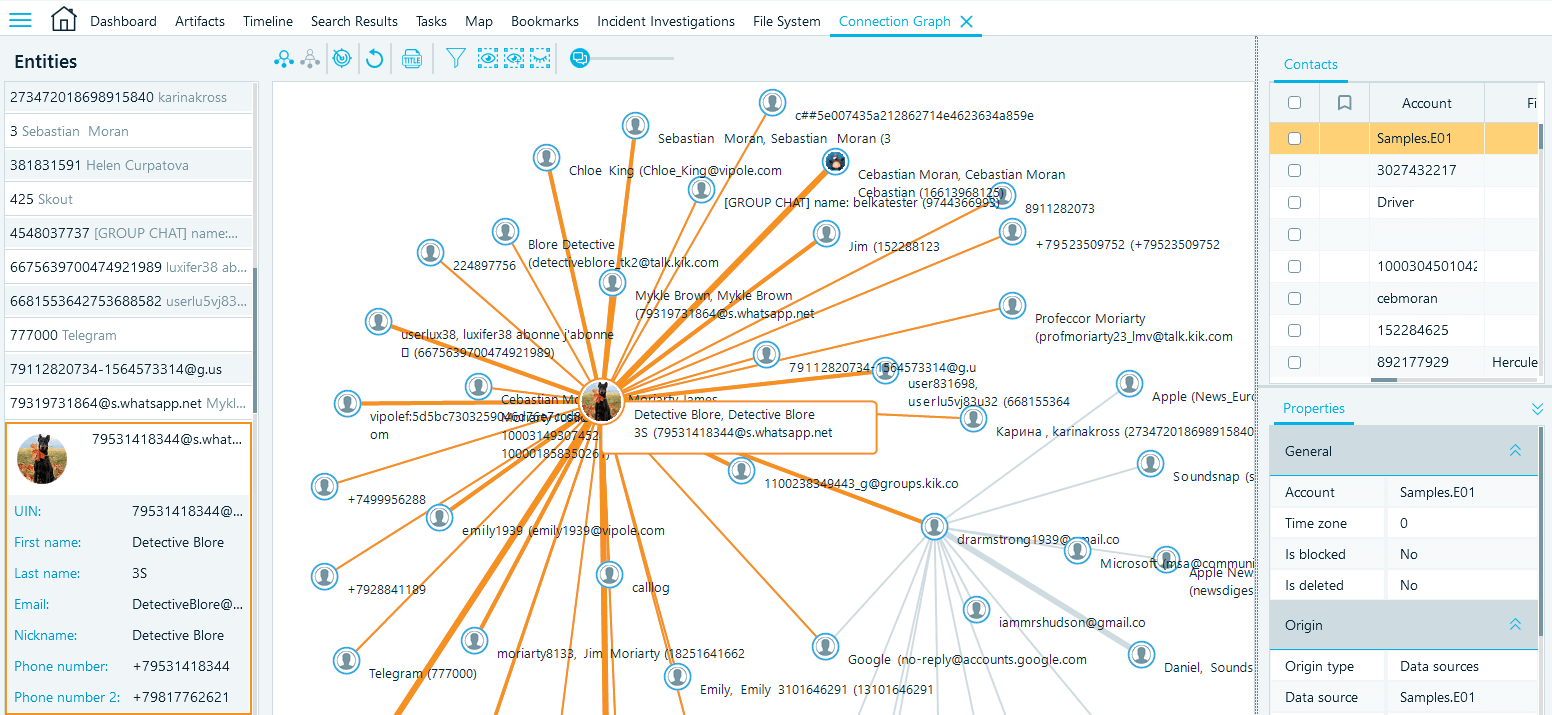
Belkasoft X Connection Graph helps you visualize communication between individuals involved in a case
We were then able to search the artifacts using the search terms provided and report on the results.
At the conclusion of our investigation, the devices were resealed in evidence bags and returned to secure storage. We then kept a master working copy of all the data that we worked from and used for disclosure requests.
What digital artifacts revealed the most important evidence for the case? How did it help in court?
The main areas of interest were, call records, SMS, WhatsApp, and Messenger, together with photographs of building work and contact with other building companies. We also assisted as to the movement of money. I cannot go into greater detail here, as there are matters outstanding.
You mentioned "The ability to examine different types of devices in the same environment of a single tool was particularly useful." Could you please describe this experience in detail?
In an examination where there are mobile phones, tablets, and PCs from the same person, due to synchronization, there can be a degree of duplication of data, such as emails and messages. Being able to examine different devices in the same environment is far better than having different tools for each device. The same email may reside on an iPhone, an iPad and a Windows PC. Being able to examine the data from each device in the same environment, as opposed to switching between tools, saves a lot of time.
Reporting on the findings: ways to share digital forensic evidence
How do you present findings to your clients?
In some cases, we provide the client with the Belkasoft Evidence Reader output for them to browse and search themselves, in other cases we extract the different types of artifacts and provide an output in folders sorted by file or artifact type.
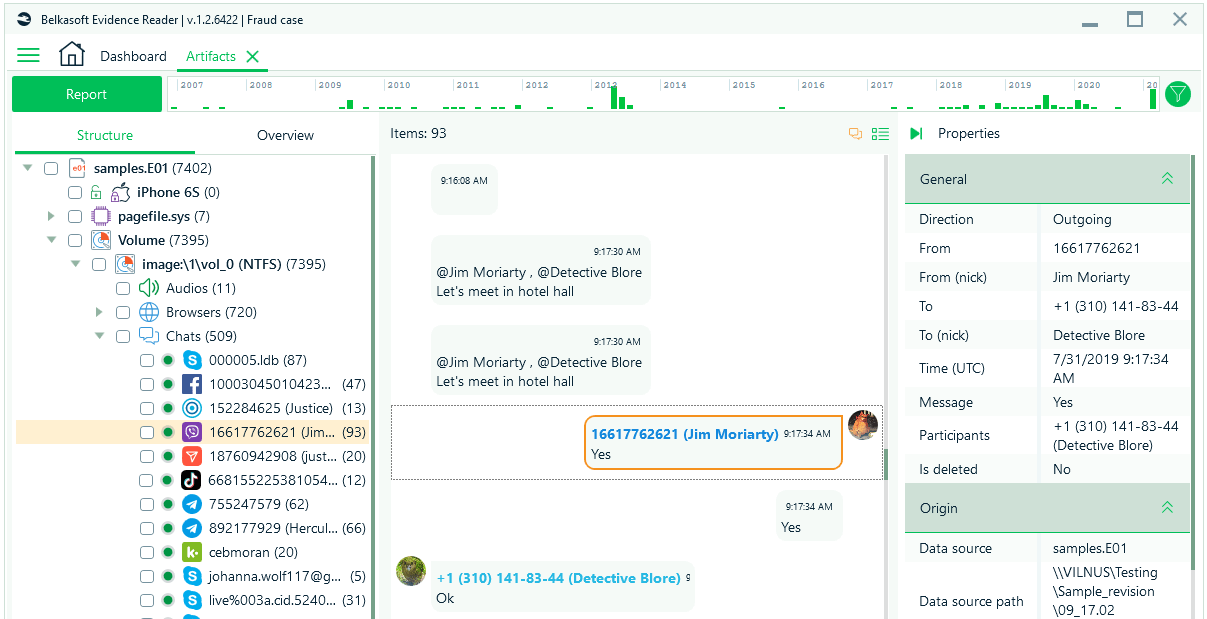
Evidence Reader is an easy way to create a portable case and share curated artifacts with others
Using Belkasoft, we were able to quickly fulfill the requirements of the client, providing them with data that supported their inquiries. The messaging, voicemails, and geolocation proved contact between various parties and showed intent. The financial information proved the loss and demonstrated where the money had gone.
ISO standards regulating digital investigations
From time to time, we hear complaints (especially in the United Kingdom) about the need to align investigations with strict ISO 17025 and ISO 270343 standards.
Can you please describe how Belkasoft X fits into these standards for people who never used Belkasoft before?
This is a huge topic, and not one that can be dealt with here. Suffice to say, the competency of an expert both in their actions and in their provision of findings to the Court, goes to the very heart of their evidence. The most important protocols are the most basic ones, that were set out in the ACPO guidance 30 years ago:
- Make no change to the data that you are investigating.
- If your investigation does make a change, then note it, and be prepared to explain how it has, or has not, affected your findings and conclusions.
- Use software tools that allow a copy of the evidence to be made available to a third party, who then can also examine it and verify your own findings.

The role of digital forensic evidence in fraud cases
In your opinion, how crucial was the role of digital forensics and the Belkasoft X tool in achieving a successful outcome in this case?
In examinations of such cases, there can be little or no documentation relating to the contract, and claims of mistaken identity, or customers misunderstanding the issues, can be encountered. So digital forensics was crucial in this case as it was able to demonstrate the modus operandi used, the identity and association of several different parties, and the flows of money.
Belkasoft X allowed us to do all the required tasks in one tool, thus saving a lot of valuable time.
The Belkasoft team appreciates detailed feedback from DFIR and eDiscovery experts. Want to share your testimonials and case studies? Contact us at support@belkasoft.com.
