Case Study: Belkasoft X Helps to Define CSAM Recidivism Immediately

Brian Hempstead, a computer forensic examiner from Gainesville, FL, USA kindly shared his essay on the investigation case with Belkasoft X and his interaction with Belkasoft support.
"It is not often that you ask a question to a CEO of a company on LinkedIn and it leads to a conference call with him and his engineering staff explaining a workflow automation process you want to do with their product."
Belkasoft X usage experience
I have been using Belkasoft's DFIR software since September 2021 to analyze drives.
Currently, I am working on a complete workflow automation project that utilizes TX1 and Belkasoft X for imaging, case creation, parsing, and exporting Vics files for image analysis in Griffeye Analyze DI. Belkasoft X is my primary tool for conducting drive analysis, and the automation project using TX1 and Belkasoft.
Over the past six months, Belkasoft has been an indispensable tool for my cases. The software and support provided by the company have not only helped me solve complicated cases but have also streamlined my workflow.
Case study: CSAM recidivism
In one particular case, a suspect was released from jail, and shortly after, he began to relapse.
In this case, the suspect had been previously arrested for possession of CSAM and had been released after serving the sentence. Shortly after release, we began receiving Cyber tips from NCEMC (National Center for Missing and Exploited Children) that led us back to the suspect. Based on this information, we obtained a search warrant.
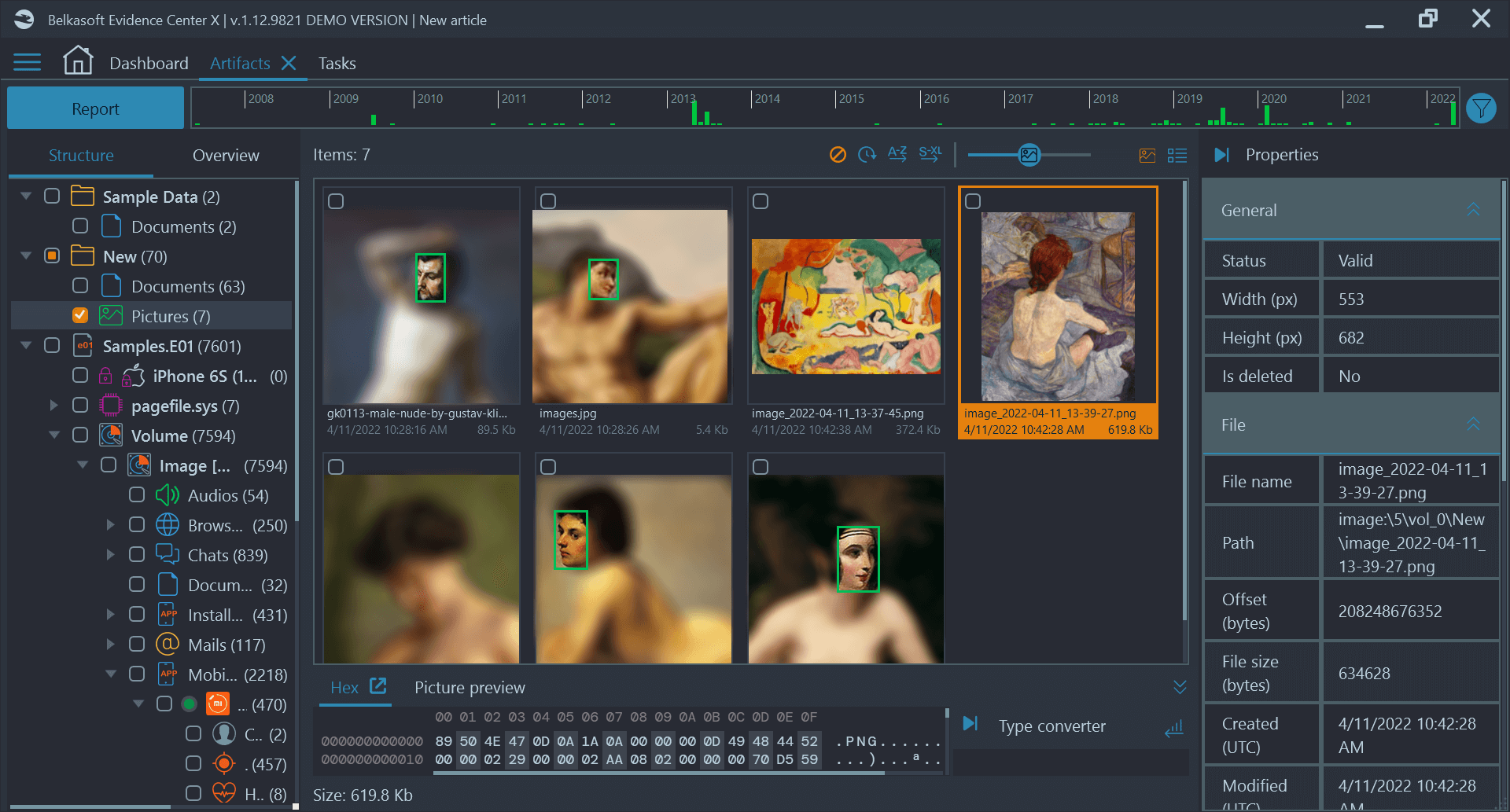
During the residential search warrant, we did not find anything "on view," and therefore, we had to rely on our examinations to find evidence to charge the suspect. The suspect was aware of some processes due to his prior arrest and conviction, and he was using obfuscation and forensic blocking techniques. For example, the suspect had enabled secure folders on this phone, and we found an encrypted zip file. In interviews, the suspect tried to obscure what devices he used by attributing them to family members. He also provided incorrect passwords to seized laptops. However, we were ultimately able to gain access to all devices.
We found evidence of CSAM on the suspect's phone after bypassing the anti-forensic measures the suspect had in place. However, we did not know how the suspect obtained the new CSAM. Our Assistant US Attorney had expressed interest in taking the suspect's case to the federal level. They wanted to show the court the process by which the suspect acquired CSAM, and in this case, they wanted to determine when the suspect began reoffending.
"Belkasoft made it easy to locate this critical artifact and understand when and from where it was accessed. This information was not found in the other paid program."
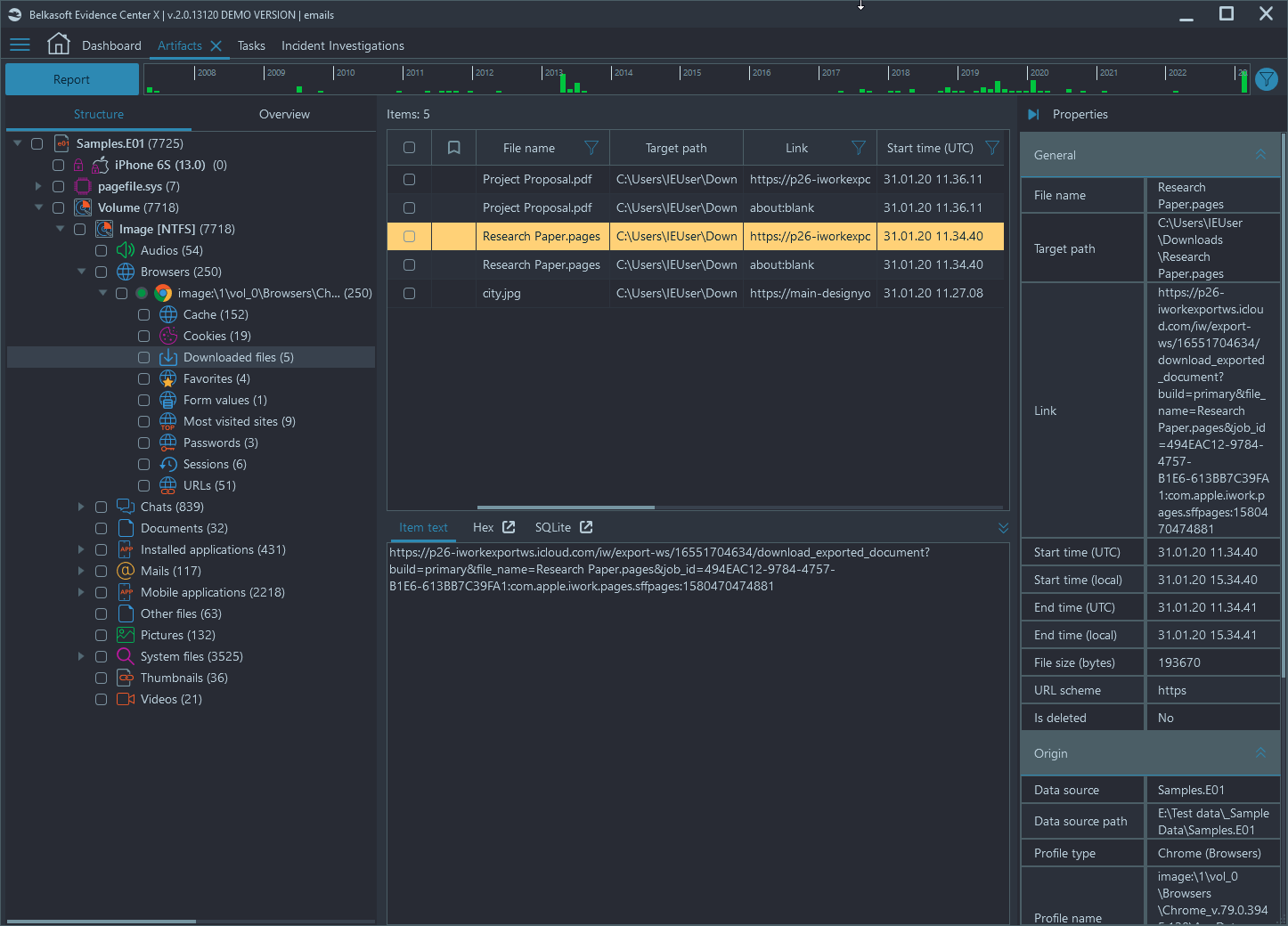
To recover artifacts that might show how the suspect obtained CSAM, we examined the phone's download and browser history. I used Belkasoft, and my coworker used Magnet's Axiom. While using Belkasoft, I found a browser artifact in which a bookmarks file was downloaded from an email account. Upon exporting the downloaded file, I discovered that it contained a list of hundreds of links to CSAM sources. However, the same artifact did not appear in Magnet Axiom. As a result, my coworker had to examine the file source data from Belkasoft to locate the artifact in the other tool.
The discovery of the bookmarks file enabled us to piece together the events that led to the suspect's reoffending. We could show how quickly after being released, the suspect accessed his email, downloaded the backed-up bookmarks, and began reoffending. Belkasoft's tools proved especially helpful in this regard, given its ability to identify the artifact that other tools had missed. Additionally, exporting and examining the bookmarks file was straightforward. Once we identified the file as containing links to CSAM, I was able to quickly scroll over a few columns and determine when it was downloaded. This information was useful in illustrating the timeline of events to our Assistant US Attorney.
Belkasoft made it easy to locate this critical artifact and understand when and from where it was accessed. This information was not found in the other paid program, which we reviewed for this case. Belkasoft allowed us to identify this offense within days of the criminal being released from prison. The attachment download was a key piece of evidence used to paint a picture of recidivism for prosecutors and the court.
As this case is still pending, I have taken care to avoid including any details that could potentially identify the suspect. The case is currently being pursued at the federal level, and we are eagerly awaiting news of a trial date or a plea.
Belkasoft support and open-minded approach
"Belkasoft provides impressive support and attention to its customers. I don't know of any other company in the tech sector, not just DFIR, that is as responsive to their customers."
In my work during 2022, many critical challenges were related to investigating specific apps and data formats, the increasing use of anti-forensic techniques, large data volumes, and lengthy processing times. I believe that encryption is an ever-growing anti-forensic threat. I anticipate that in 2023, we will see more platforms and devices adopting encryption into their products like Belkasoft did.
I feel confident in my work, thanks to the support of the Belkasoft team and their open-minded approach. It is not often that you ask a question to a CEO of a company on LinkedIn and it leads to a conference call with him and his engineering staff explaining a workflow automation process you want to do with their product. Yuri Gubanov and his team spoke with me and my team, and they made sure they understood our workflow. Belkasoft then implemented the necessary changes and updates for Belkasoft X to automate 90% of our workflow. Belkasoft provides impressive support and attention to its customers. I don't know of any other company in the tech sector, not just DFIR, that is as responsive to their customers.
When I completed the Belkasoft 2022 end-of-the-year customer survey, I was asked if there was anything that could be improved to make Belkasoft more suitable for my needs. My answer was "No".

Olga, Customer Support Specialist
When I completed the Belkasoft 2022 end-of-the-year customer survey, I was asked if there was anything that could be improved to make Belkasoft more suitable for my needs. My answer was "No". Belkasoft has been very receptive to my suggestions in the past and has even implemented some of them into Belkasoft X version 1.15.
I highly recommend that every digital forensic investigator and cyber incident responder take advantage of the educational resources offered by Belkasoft to advance their DFIR knowledge. The video tutorials, webinars, and training courses provide great opportunities to gain hands-on practice and fully grasp the capabilities of Belkasoft products. I particularly enjoyed the Belkasoft CTF events, which were real-world-focused and included believable workstation images. I would love to see more of these events in the future.
The Belkasoft team appreciates detailed feedback from DFIR and eDiscovery experts. Please share your testimonials and case studies at support@belkasoft.com.
