Introduction
The 'push button forensics' is a sarcastic term for the job DFIR specialists perform when they use DFIR tools, which extract various useful data out of the box, alleviating the manual extraction of many different types of artifacts. While there is room for sarcasm, the automatic extraction of artifacts is not necessarily evil. Given the volume of data in which modern devices can store, an investigator or examiner cannot efficiently analyze everything manually. This means some reasonable level of automation is a 'must have'.
The problem that arises is when this automation is used blindly without challenging the obtained results and without cross-checking them with other tools' output, or by manual examination. This may lead to a situation when one's results are challenged later—by a counterparty.
It is worth mentioning that some digital forensic tools on the market provoke using the tools blindly. Such tools work as a black box and give results without explanations of how the artifacts were obtained. No surprise, that conclusions based on such results will not withstand in court, if challenged by a knowledgeable counterparty. A question as simple as: 'How was this deleted chat restored by “Software A?’, could appear extremely difficult to answer, if “Software A is a black box for you.
In this article, we will review a healthier approach to automatic extraction of artifacts for a digital forensic or an incident response case.
Origin path concept within Belkasoft X explained
'Origin path' is a property which every artifact has in Belkasoft X; Belkasoft's flagship product for computer, mobile and cloud forensics. This property aids the examiner by allowing them to understand where an artifact came from. Every chat, URL, document, picture, registry key, email, etc., has this property.
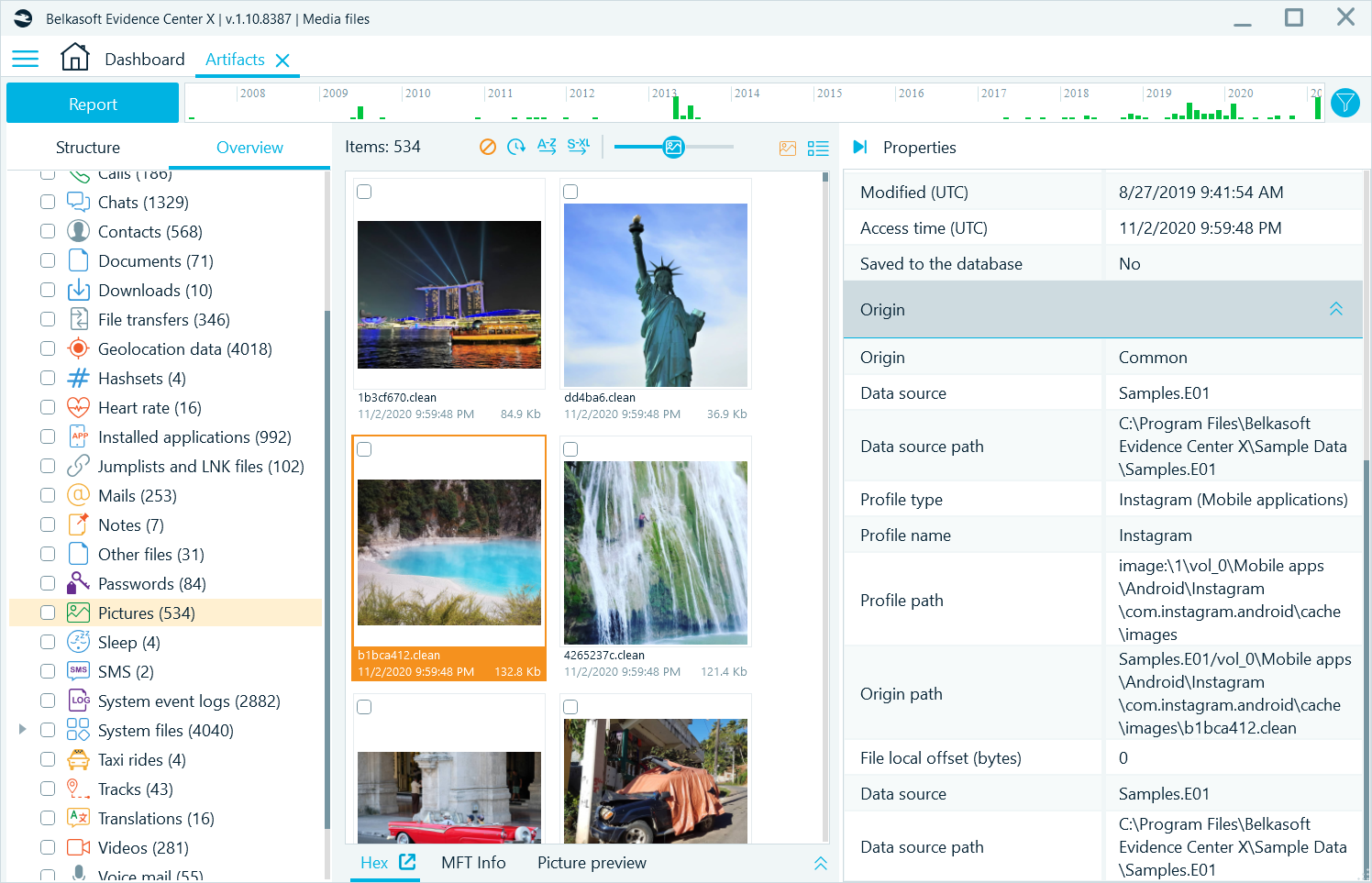
Figure 1: Properties pane
While simple artifacts such as a document parsed from an existing file, will likely not cause any issues, the following situations may bring some difficulties:
- Deleted chat or URL. How can you prove that they really existed? Can you show where they were recovered from? Can you repeat this manually?
- Embedded picture. Where did this picture come from?
- Email attachment. Which email was it attached to?
- Any carved artifacts
To illustrate how Belkasoft X's Origin path can help, let us review the first situation: a chat recovered from the Skype application.
Here is an example of an Origin path, that a Skype chat can have:
'image.e01//C:\Users\Smith\AppData\Roaming\Skype\smith48\main.db//Messages\Freelist'
You can see that this chat originated from an image 'image.e01'. This is the first part of the Origin path, and it always ends with a double slash.
The path to a profile, which is the second part of the Origin path value, is 'C:\Users\Smith\AppData\Roaming\Skype\smith48\main.db'. This is where the Skype data is stored for this particular profile (smith48).
Finally, after the second double slash, we can see the table name as well as a special area inside the table is mentioned too. This particular chat was extracted from the 'freelist' area from the Messages table inside the SQLite database 'main.db' (main Skype database file).
Note: you can learn more on freelists, write-ahead logs and SQLite journal files at https://belkasoft.com/sqlite-analysis
Now you have all the knowledge of where to find the artifact manually, if needed. Well, almost all.
Next to the Origin path, you will also see an offset inside the file (for artifacts recovered in a file) or an offset from the beginning of a partition (for carved artifacts). With this information, you will be able to accurately explain where an artifact originated from, and also how to manually validate the product interpretation of raw data by using built-in Hex viewer or a third-party tool.
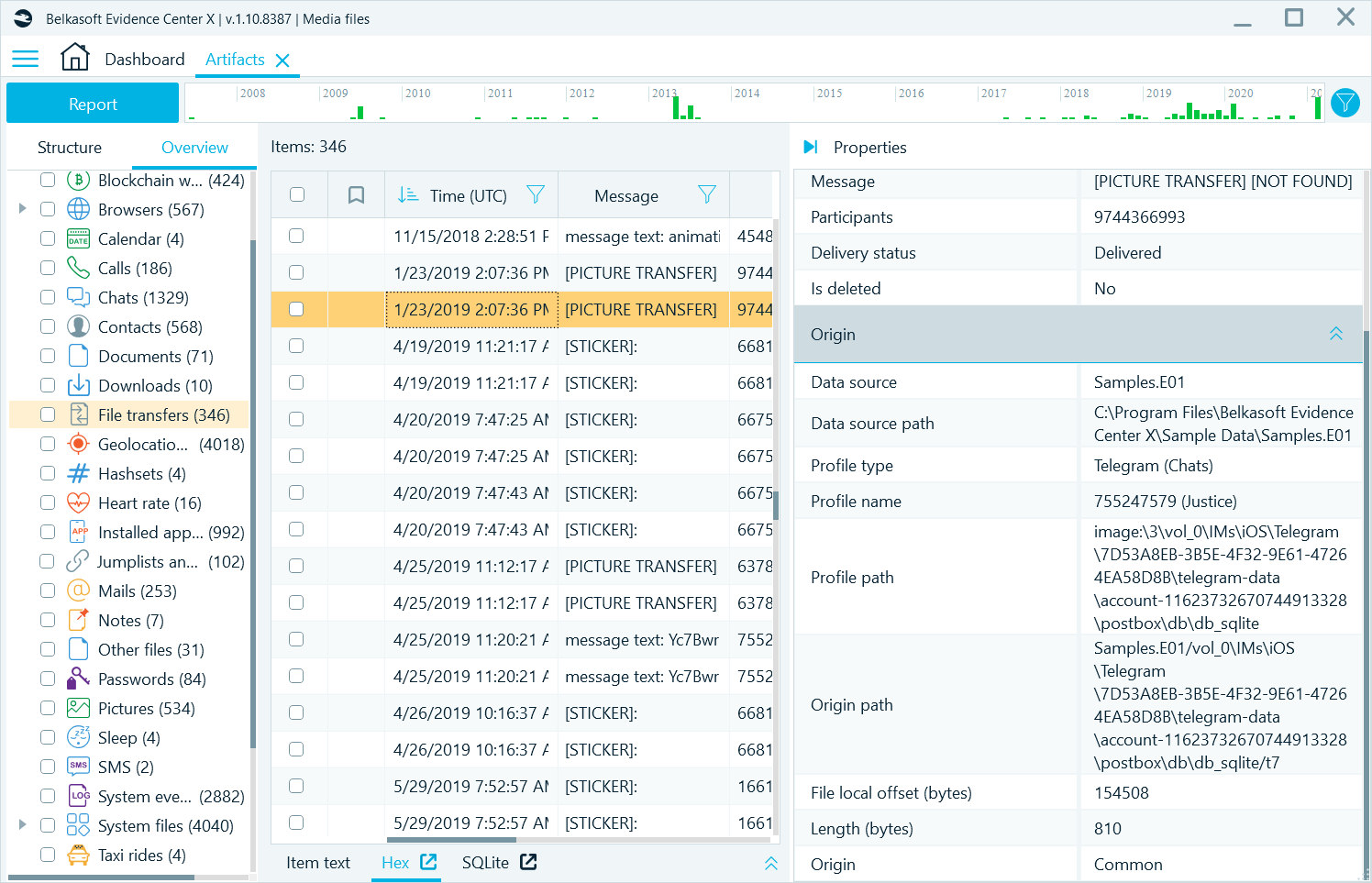
Figure 2: File local offset on the Properties pane
Reviewing artifacts on a database and at the raw byte level
One of the benefits of using Belkasoft X as your digital forensic tool of choice, is that it helps you to understand how and where artifacts were extracted from, on a few different levels.
The Interpreted level
You can see artifacts such as chats, URLs, pictures, registry data and so on in the artifact list on the Artifacts window. All values are fully interpreted, including date and time stamps, decoded or decrypted texts, message directions and more. Basically, you can rely on this information, unless you have doubts or a complicated situation when you need to double check the interpretation.
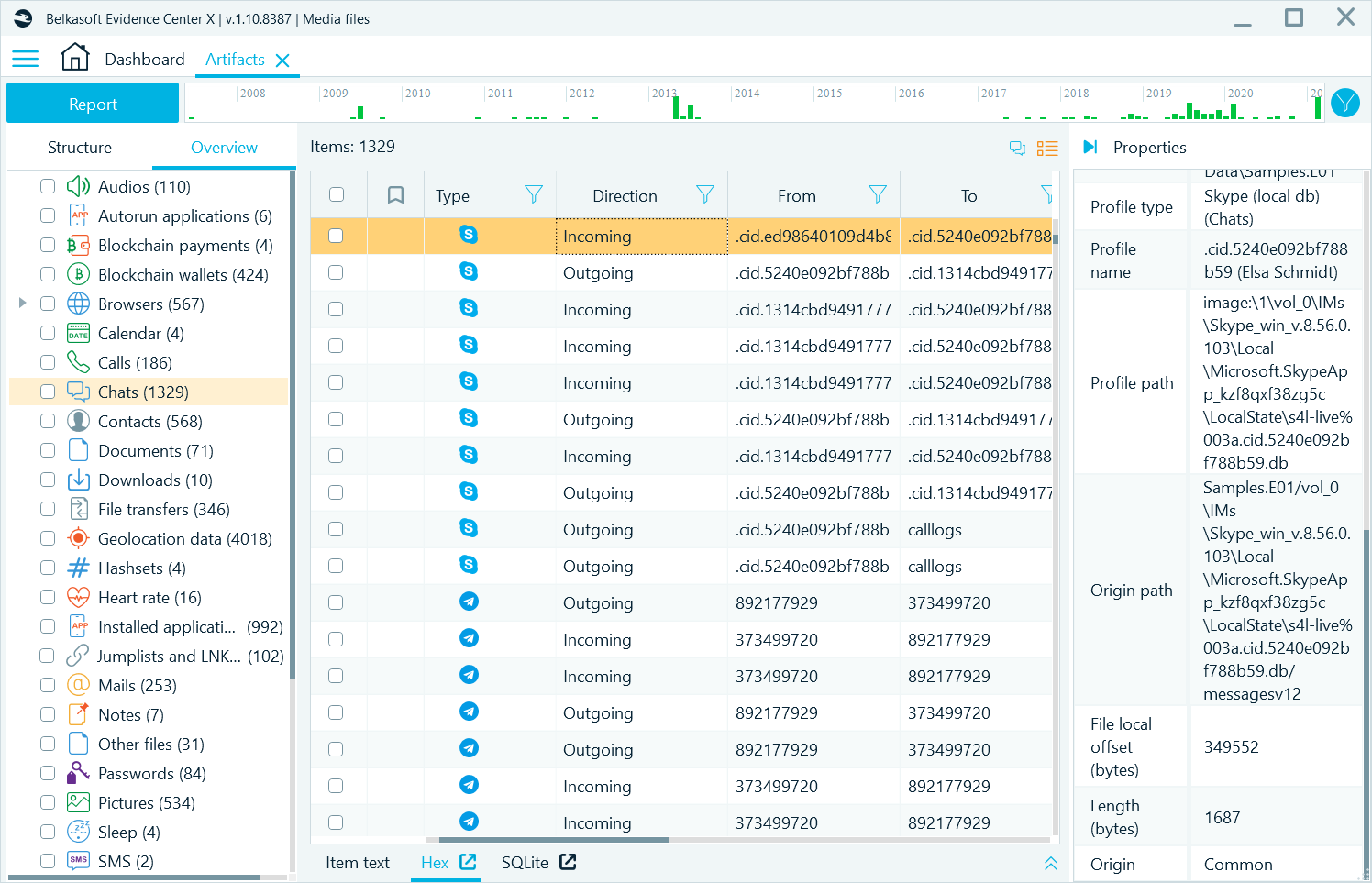
Figure 3: Chats as shown on the Artifacts window
The Database level
On this level, you can see particular artifact data as it is stored logically within a database or another file, such as a plist or a registry file. For example, when you click on an artifact, which is stored inside of a SQLite database, Belkasoft X will show you a separate SQLite viewer tab below the artifact list (in the so-called 'Tools' area). This tab will conveniently show the corresponding SQLite table and row selected.
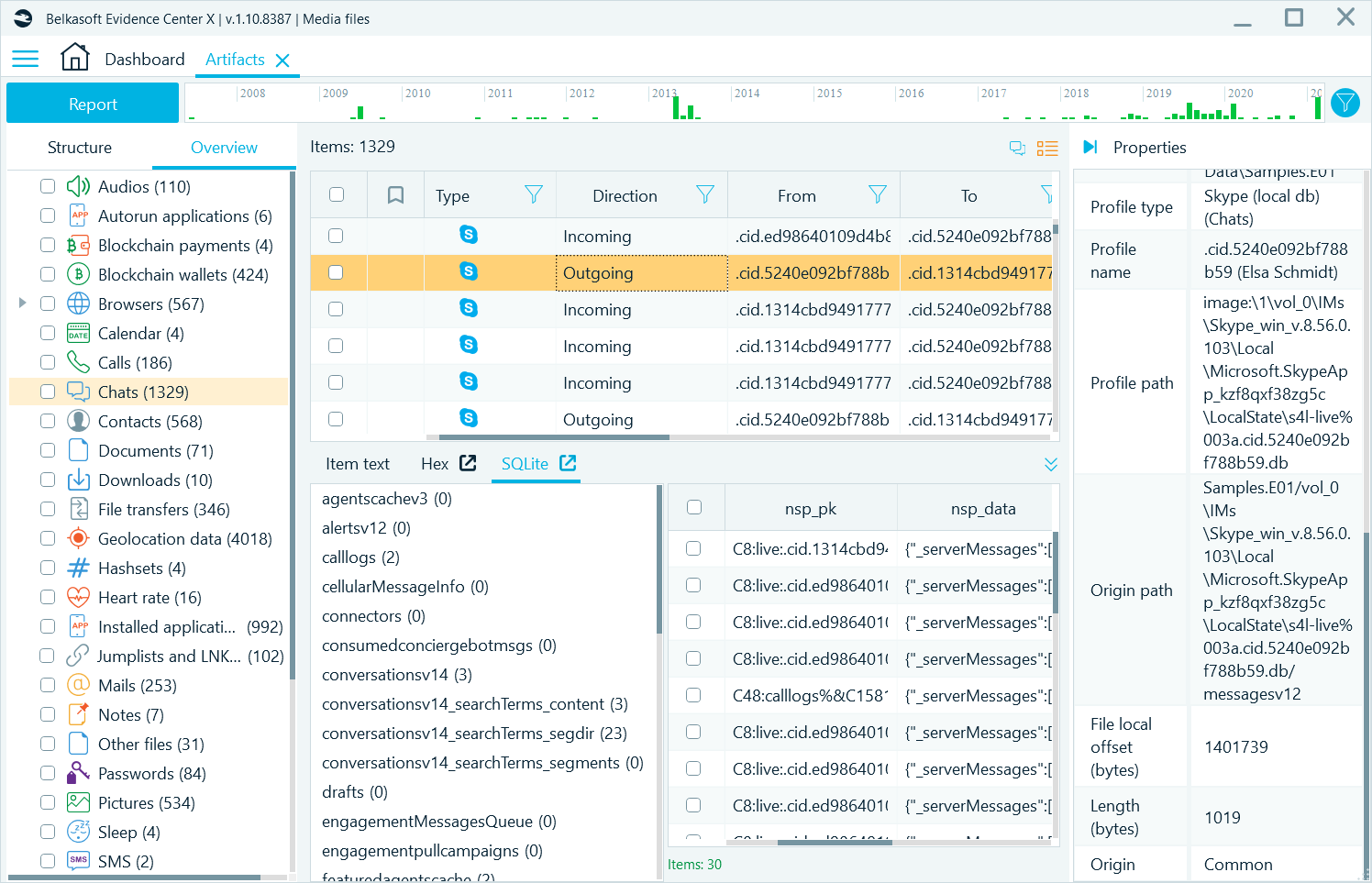
Figure 4: SQLite Viewer tab
You can click on the 'Expand’ icon to open a full-size SQLite Viewer.
Figure 5: Full screen button to open SQLite Viewer
At the database level, you may expect to see certain types of data that are not interpreted. Particularly, date and time stamps may be in Unix format, while texts can be in ASCII, not UTF. Belkasoft’s SQLite Viewer allows for changing the format of the date and time for integer columns and encoding for text columns.
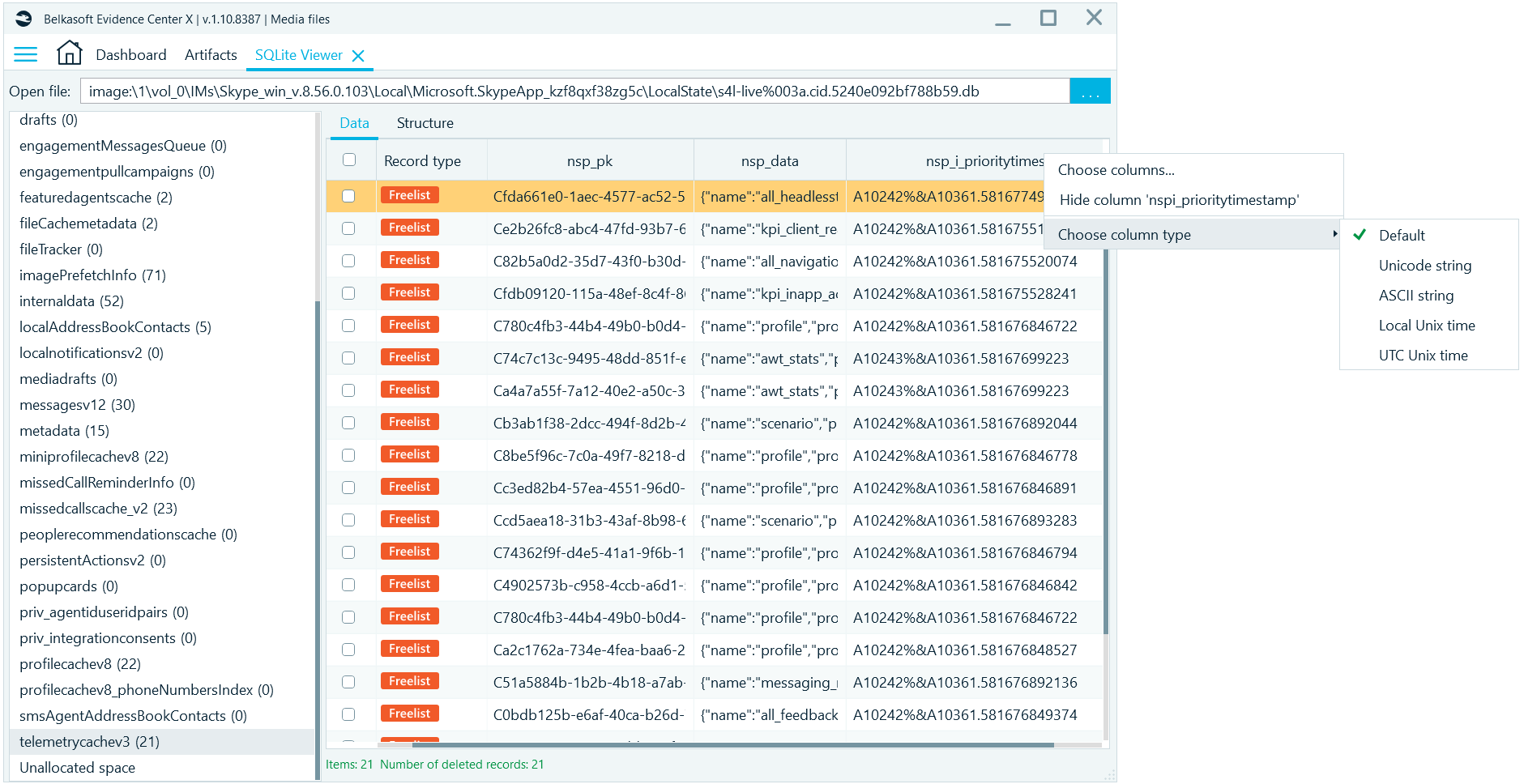
Figure 6: You can choose the date and time format
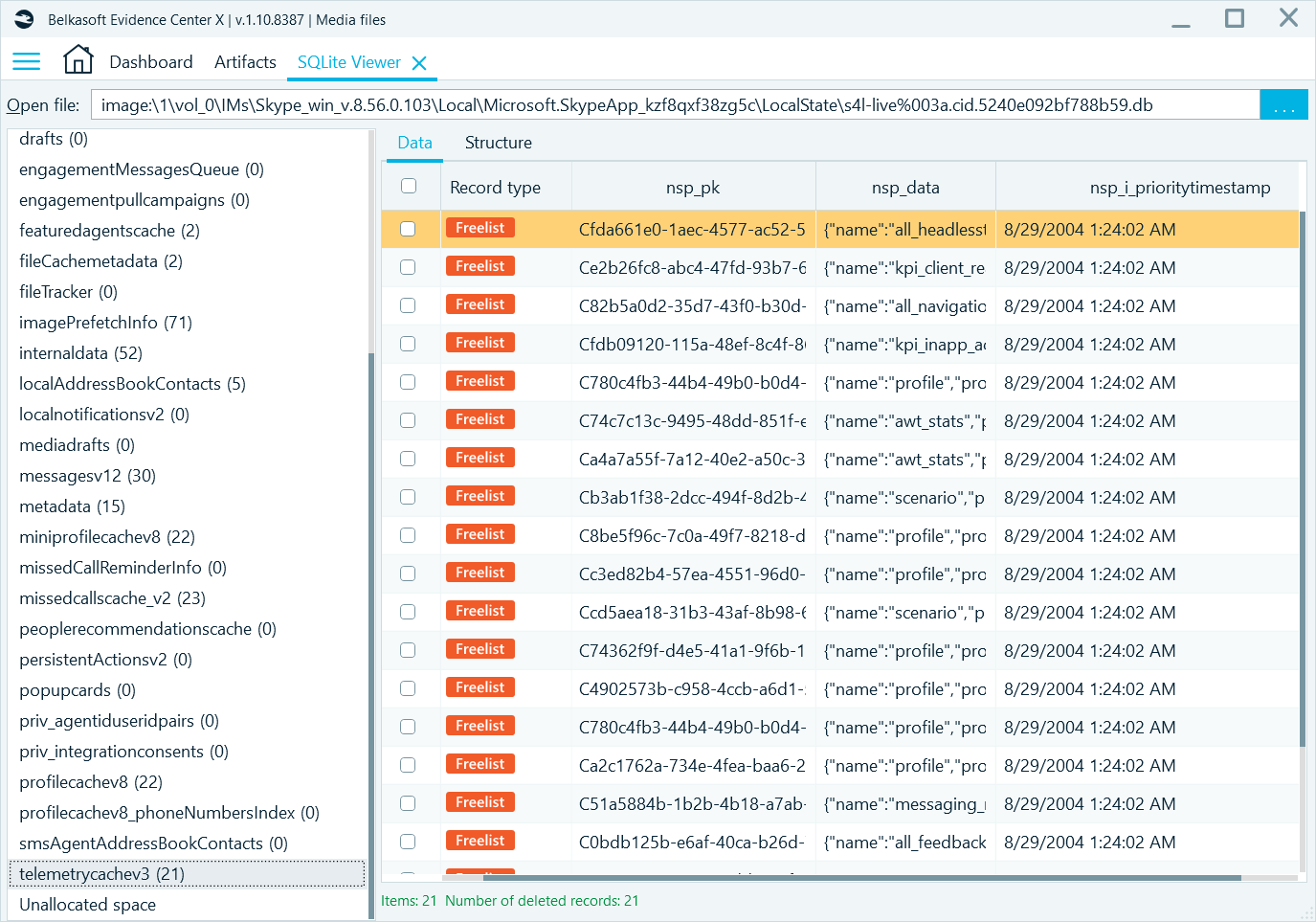
Figure 7: Time stamp converted to UTC Unix time
The Raw byte level
On this level, you can see particular artifact data as it is stored on the hard drive or other media. Every artifact has its own offset and length, which enables you to review its original binary data. Belkasoft’s Hex Viewer tab shown in the Tools region of Belkasoft X, conveniently shows a selected artifact’s raw bytes. It highlights the entire portion of bytes which belong to the artifact, which enables you to copy these bytes and interpret manually or by using any other third-party tool.
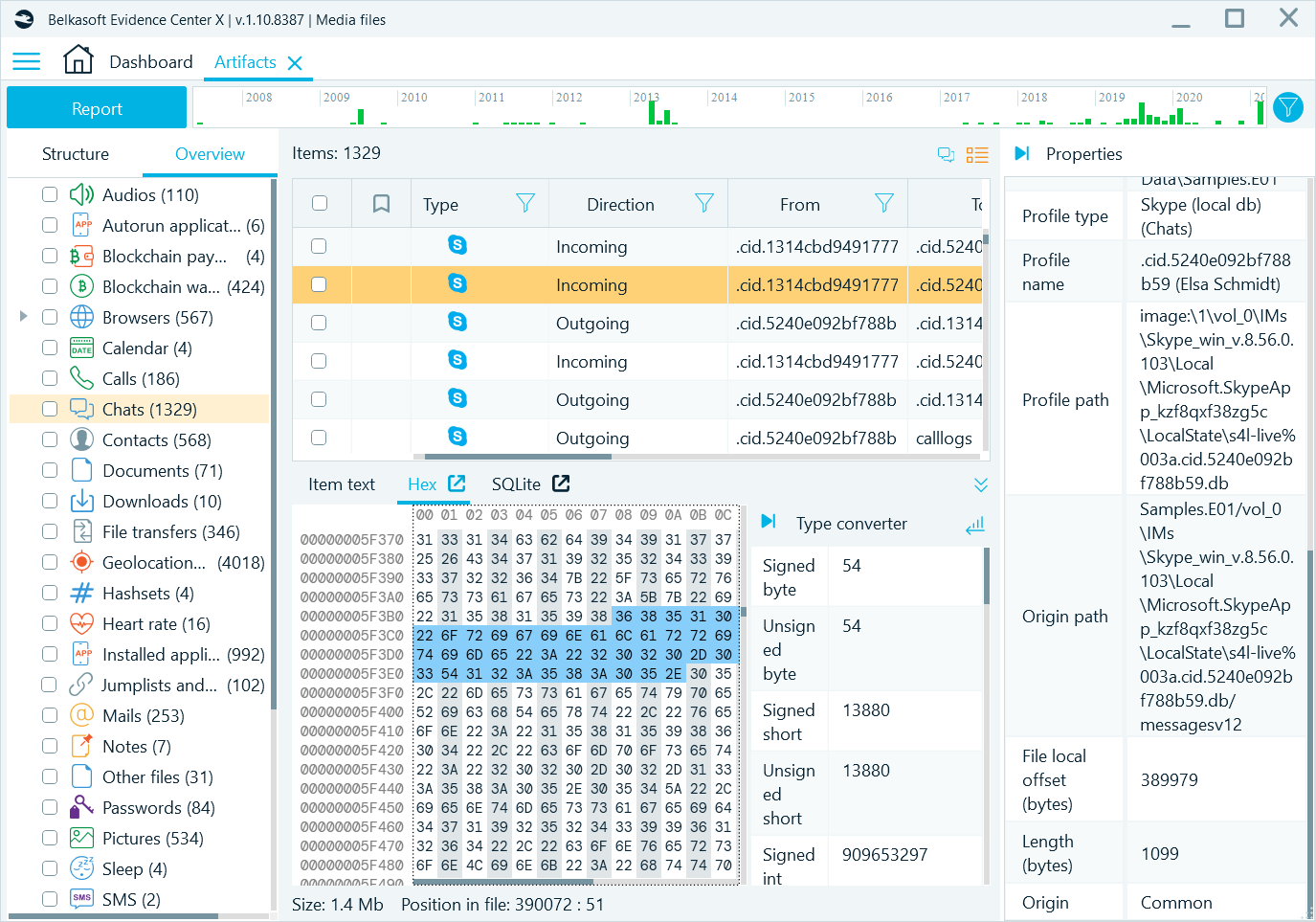
Figure 8: Hex Viewer tab
Just like with the SQLite tab, you can open a full size Hex Viewer by clicking on the 'Expand' icon.
Conclusion
As a digital forensic investigator or an incident responder, you must be ready to answer the question of 'How did your tool obtain a particular artifact?'. To assist with answering this question, Belkasoft introduced the Origin path property within the Belkasoft X product. Using this property, you can give exhaustive replies to such questions.
