Digital Forensics Playbook for Enterprise Forensics
For businesses today, a security incident is not a question of "if" but "when." Therefore, an incident response plan is essential for corporate forensics. Having a solid response plan ensures you can act systematically and effectively when threats emerge. Without one, chaos takes over, leading to greater damage, higher costs, and eroded customer trust.
Think of an incident response plan as your roadmap for identifying, containing, recovering, and reflecting on security threats. It gives you clear, actionable steps to follow when every minute counts. While several response models exist, this guide follows the six-step SANS Institute framework.
The table below outlines the six phases of the SANS incident response framework, along with the Belkasoft tools that support each stage.
| Incident Response Phase | Key Belkasoft Capabilities |
|---|---|
| 1. Preparation |
Deploy Belkasoft R (remote data collection software) agents proactively. Set up BelkaGPT Hub for shared AI analysis. License Belkasoft X Corporate edition. |
| 2. Identification | Use Belkasoft Triage for quick on-site checks and Belkasoft R by capturing volatile memory (RAM) or specific files without a full disk image. |
| 3. Containment | Use Belkasoft R to remotely acquire forensically sound data from computers and mobile devices. |
| 4. Eradication |
Use the Incident Investigation module in Belkasoft X to analyze all evidence. Add BelkaGPT (powered by BelkaGPT Hub) for AI-powered search and analysis. |
| 5. Recovery |
Use detailed reports from Belkasoft X to guide safe system restoration. Share findings using Belkasoft Evidence Reader for multifaceted analysis. |
| 6. Lessons Learned | Use the Belkasoft X case and report as the factual foundation for post-incident reviews. |
NIST, on the other hand, highlights four incident response steps:
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
However, since the "active" steps of both frameworks are actually aligned, this article will focus on SANS’ framework, as it offers a more detailed approach.
Although enterprise cybersecurity software is primarily designed to prevent attacks, security teams are often left unable to investigate incidents properly without the right approach and tools in place.
Remember: even the best plan fails without the right tools to support it. This guide outlines each phase in incident response and demonstrates how Belkasoft’s technology can be integrated into every step of your enterprise's digital forensics and incident response (DFIR) playbook.
Preparation: Getting ready before an incident
Incident response starts long before detection. Preparation lays the groundwork for everything you need and strengthens your response when it matters most.
Here is how you can prepare beforehand:
- Build your team. Assemble a dedicated incident management team with IT operations and security. At some point, you might want to assign the main contact from each involved department to simplify communication. Ensure that each member understands their role and has the necessary authority to act promptly.
- Create your plan. Develop a formal incident response plan that defines different incident types and outlines clear response steps. Build playbooks for common scenarios, such as ransomware attacks or data breaches. Having the proper checklist also cannot hurt.
- Train and test regularly. Run training sessions and simulations to identify gaps in your plan before a real crisis hits.
How Belkasoft helps with preparation
Being prepared means having your tools ready to go. You want to be able to act immediately, without wasting time.
-
Install and set up Belkasoft X Corporate, an enterprise forensics software suite. Keep it up to date and ready for instant analysis when needed.
Belkasoft X will check your software for updates
-
Pre-deploy Belkasoft R agents across your network. When an incident occurs, the tool capable of remote data collection will save you both time and money without shipping hard drives or deploying analysts on-site.
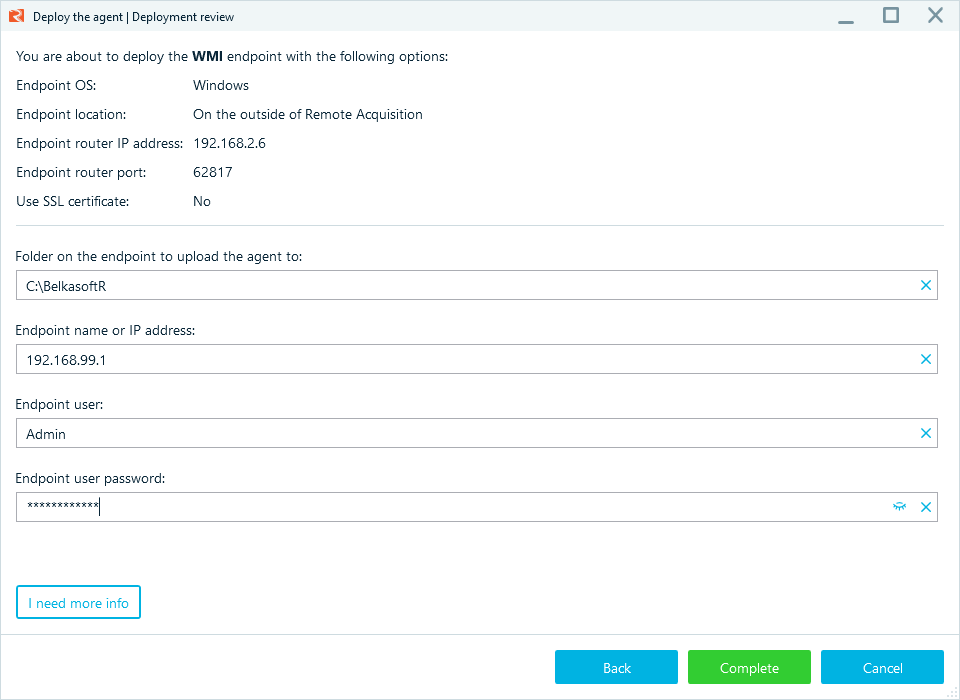
You can deploy Belkasoft R using a GPO, WMI, or locally
- Set up infrastructure for advanced analysis. The BelkaGPT Hub allows your entire team to share one powerful computer for AI analysis, eliminating the need for expensive hardware on each analyst’s workstation and making AI assistance available from day one.
Identification: Finding and confirming a problem
Your security tools generate thousands of alerts every day. The identification phase separates real threats from false positives. Your goal is to quickly confirm whether an alert represents a genuine security incident so you can launch an appropriate response.
Regardless of the tools you use, you need to:
- Document the event. Record suspicious activity immediately. Note when and how you detected it, which systems are affected, and any other relevant details.
- Classify the incident. Not all incidents are equal. Classify each by type and urgency. A ransomware attack on a critical server demands a much faster response than a user accidentally visiting a suspicious website.
How Belkasoft helps with identification
Investigating every alert by analyzing complete hard drives is not practical—it takes too long and creates an overwhelming backlog.
Belkasoft Triage is a free tool you can run from a USB drive on any live Windows computer for on-site corporate investigations. It can display an immediate alert on files with known hashes, scan for over 1,500 artifact types, and export its findings—either partially or fully—to review in Belkasoft X.
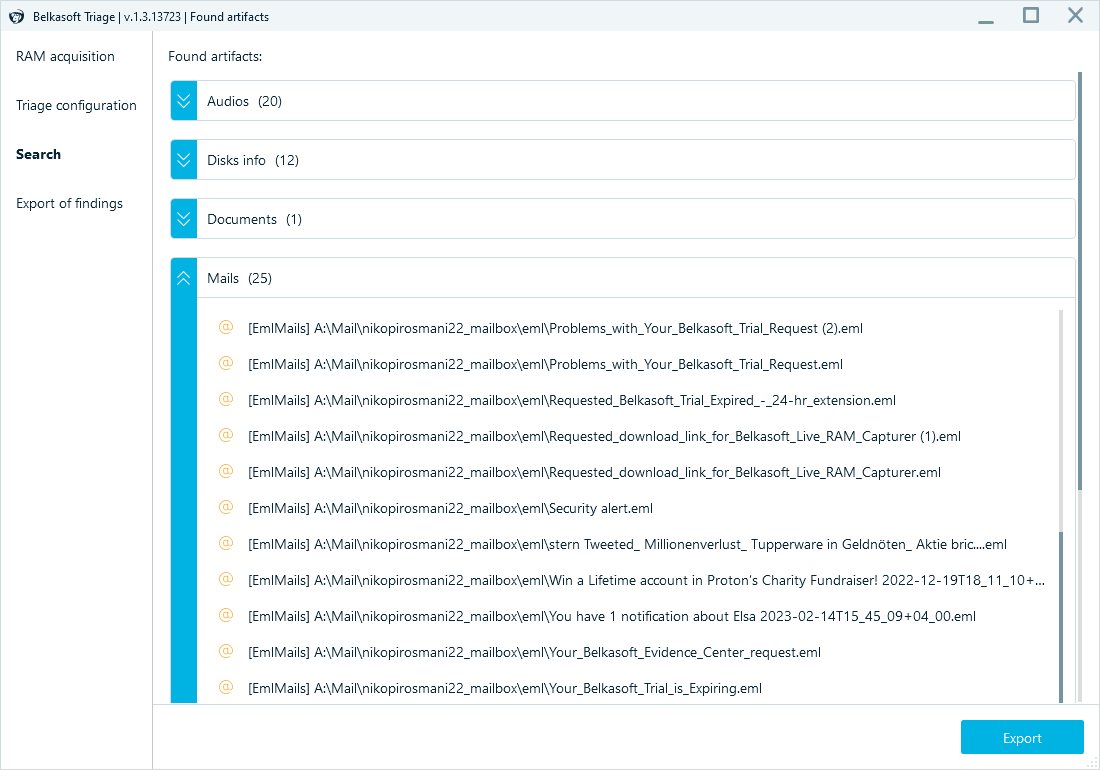
Belkasoft Triage collects the most common types of artifacts from a computer
Once you have identified the critical evidence, you can use Belkasoft X to acquire a physical or logical image of the computer’s hard drive for deeper analysis.
In a multi-site infrastructure, you can use Belkasoft R, a remote data collection tool, for quick checks on suspicious endpoints. For example:
- Check the computer's memory. Many modern attacks leave traces in volatile memory (RAM). With Belkasoft R, you can remotely capture a Windows computer's memory snapshot to identify malicious processes or network connections.
- Grab specific artifacts. Rather than copying an entire drive, you can instruct Belkasoft R to collect only specific, high-value artifact types like system logs or browser history. This targeted approach reduces data volume and cuts the time to confirm a real incident from hours to minutes.
Belkasoft R is also capable of multi-agent acquisition, saving your crisis team valuable time.
Containment: Stopping the problem from spreading
Once you confirm an incident, prioritize containment to prevent the threat from spreading or stealing more data. Quick action is essential to stop the attack while preserving evidence for investigation.
A common mistake is immediately shutting down a compromised computer, which erases important memory evidence. Instead, isolate the computer from the network first.
Then, make a secure copy of the affected systems’ data, effectively freezing the "digital crime scene."
How Belkasoft tool helps during containment
- Remote data collection: Belkasoft R is essential for organizations with distributed offices. The software does not rely on external servers, allowing your team to collect data from endpoints no matter their network location. It supports different connection scenarios, including devices on the same local network (either physically or via VPN), those on an external network, or even when both the server and endpoint are behind routers (which might require setting up port forwarding).
-
Granular acquisition: From a single console, your team can create forensically sound copies of a computer's hard drive, memory (RAM), and connected mobile devices, securely transferring the acquired data to a central storage location.
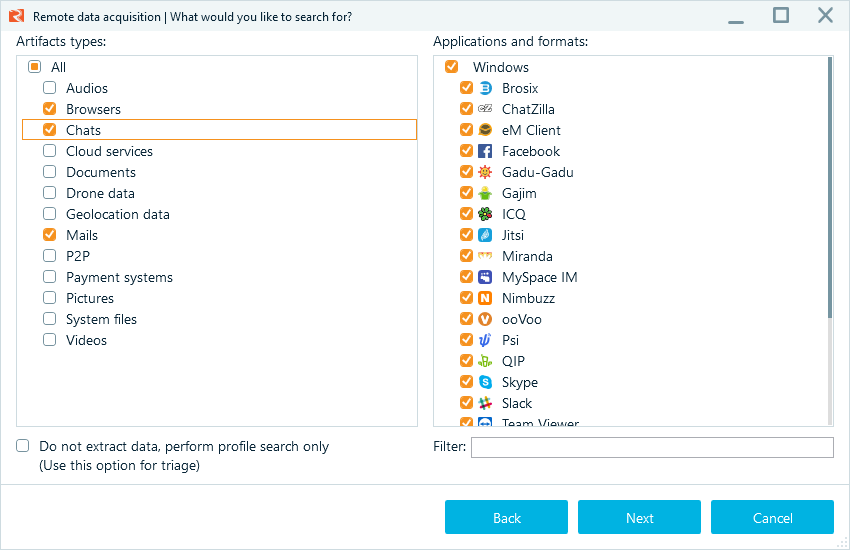
Collecting browsers, chats, and emails from multiple devices simultaneously
- Managing network usage: Belkasoft R allows you to save an image on the endpoint, compress it before sending, and even schedule the process to prevent network congestion. Additionally, for non-critical endpoints (where damage has not yet been confirmed and requires further investigation), data collection can be scheduled, and uploading can be postponed to off-peak hours.
-
On-site data collection: For main office devices, Belkasoft X seamlessly collects data from computer drives, phones, and tablets. Additionally, you can automate acquisition and analysis processes using scripting and Belkasoft CLI.
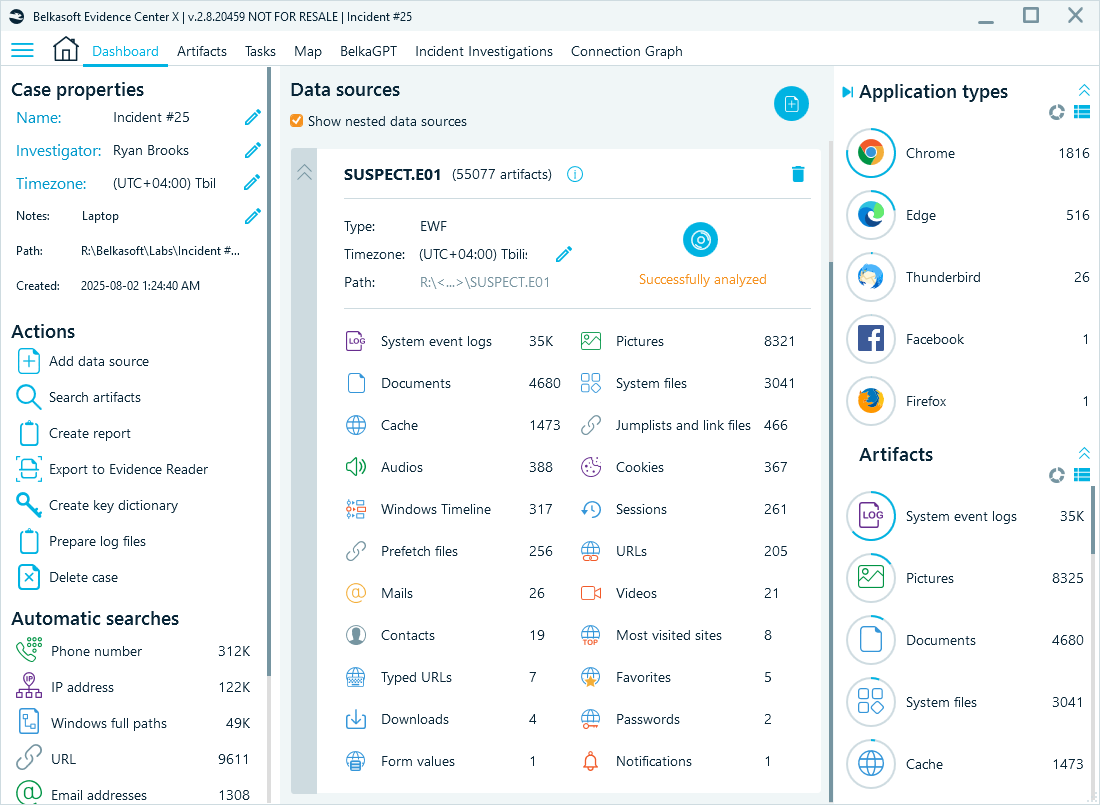
The Belkasoft X dashboard summarizes all found artifacts
-
Cloud data acquisition: In parallel, you can use Belkasoft X to start the cloud data collection from the accounts you suspect are affected.
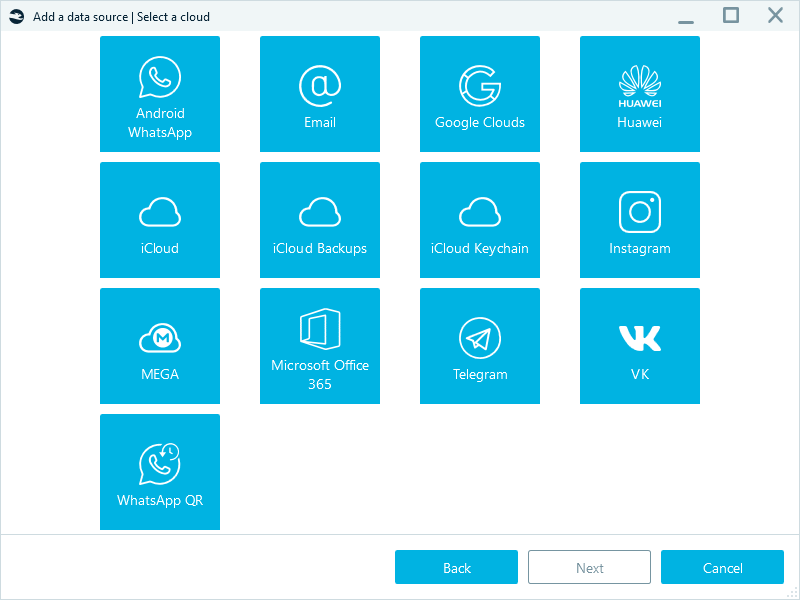
With Belkasoft X, you can collect data from most cloud services
Eradication: Removing the threat and analyzing the cause
After containment and evidence preservation, move to eradication. This phase eliminates every trace of the attacker and identifies the incident root cause to prevent future breaches.
Here are the general steps for the eradication phase:
- Determine the root cause: Before removing the threat, it is essential to identify how the malefactor gained initial access and what vulnerabilities were exploited. This involves analyzing system files, event logs, and registry entries to trace the attacker's path and actions. The goal is to identify and address the cause of the incident, rather than just its consequences.
- Eliminate malicious components: Once the root cause and all compromised systems are identified, the next step is to remove every trace of the attacker. This can include deleting malicious files, terminating unauthorized processes, removing persistence mechanisms (like scheduled tasks or registry keys), and closing backdoors.
- Address vulnerabilities: Simply removing the malware is not enough. You must patch the vulnerabilities that allowed the initial intrusion. This process can involve applying security patches, updating software, changing compromised passwords, or reconfiguring systems to be more secure.
- Consolidate and analyze evidence: To ensure a comprehensive understanding of all aspects of the attack, it is beneficial to consolidate evidence from all affected sources, such as laptops, servers, mobile phones, and cloud accounts, into a single case for a thorough overview.
How does Belkasoft help with eradication?
Here, Belkasoft X serves as a supplementary tool, offering a range of features to analyze evidence and quickly find answers. The software analyzes RAM dumps to find volatile evidence, including active processes, network connections, and executables that might not exist on a physical drive. For threat hunting, it integrates with YARA rules to scan data for specific patterns and Sigma rules to analyze log patterns. To enhance malware detection, the tool can use ClamAV for offline signature-based scanning and also utilize VirusTotal to compare files against online security databases.
The Belkasoft Incident Investigation module identifies hacking traces on Windows computers by analyzing various system artifacts, such as event logs, prefetch files, and registry entries. These artifacts can reveal how attackers accessed systems and what actions they took.
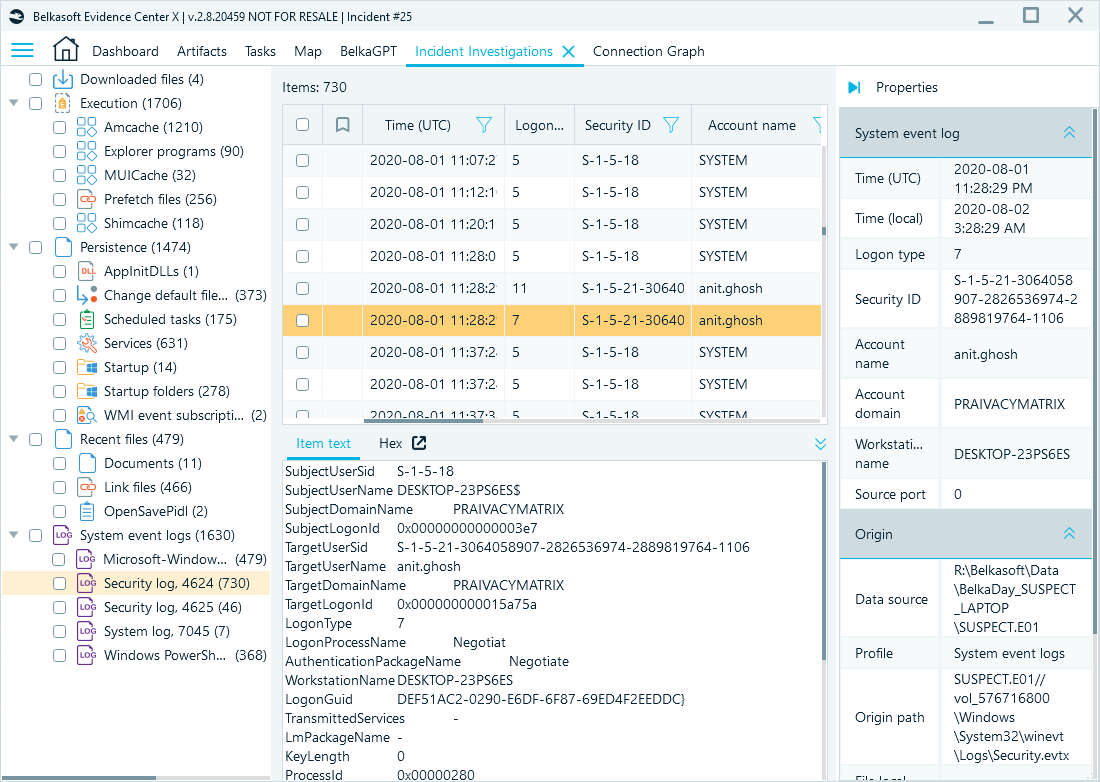
You can review the major indicators of compromise within the same window
Belkasoft X will provide you with the following benefits:
- All evidence in one place. Consolidate evidence from laptops, servers, phones, and cloud accounts into a single Belkasoft X case for a complete attack overview.
- Automatic analysis. Belkasoft X identifies and organizes over 1,500 types of digital evidence, including web history, emails, documents, chats, and various system records.
- Visual tools. Use Belkasoft X's tools to visualize attacks. The Connection Graph reveals communication links, while the Timeline orders events chronologically to help you reconstruct attacks.
- Recovering deleted data. Belkasoft X uses techniques such as carving to recover files that attackers tried to delete.
- AI-powered search. BelkaGPT, an AI assistant built into Belkasoft X, lets you search massive data sets with natural-language queries. It works offline to keep your data secure.
- BelkaGPT Hub enhances AI processing for teams by allowing multiple investigators to share a server, speeding up analysis by up to 60 times.
Recovery: Getting back on track
During recovery, you need to restore business operations securely. Simply restoring from a backup will not work if vulnerabilities remain unaddressed.
Recovery must be methodical and step-by-step:
- Fix the problem. Address the exploited vulnerability by installing patches or changing passwords before bringing systems back online.
- Restore from a clean source. Use a trusted backup created before the incident to restore your systems.
- Test everything. After restoring, thoroughly test systems to ensure they are working correctly and remain threat-free.
- Monitor closely. Once systems return to production, monitor them carefully for any signs of trouble.
How does Belkasoft help with recovery?
Your thorough investigation during eradication enables safe recovery. The detailed report from Belkasoft X provides your IT team with a clear action plan, identifying vulnerabilities, compromised accounts, and malicious files that need removal.
Lessons learned: Improving for the future
Focus on learning from the incident to strengthen security and create a cycle of continuous improvement. Hold a blameless post-incident review that identifies process and technology gaps rather than assigning blame.
Center your discussion around these key questions:
- What happened and when?
- Did our plan and team perform effectively?
- What could we have done better?
- How can we prevent similar incidents?
How Belkasoft helps with lessons learned
Effective reviews depend on facts, not opinions. The evidence and reports from your investigation provide these crucial facts, and that is where your Belkasoft X case becomes an efficient incident record. You can export the full case or specific data types to Belkasoft Evidence Reader for review by concerned departments or third-party auditors.
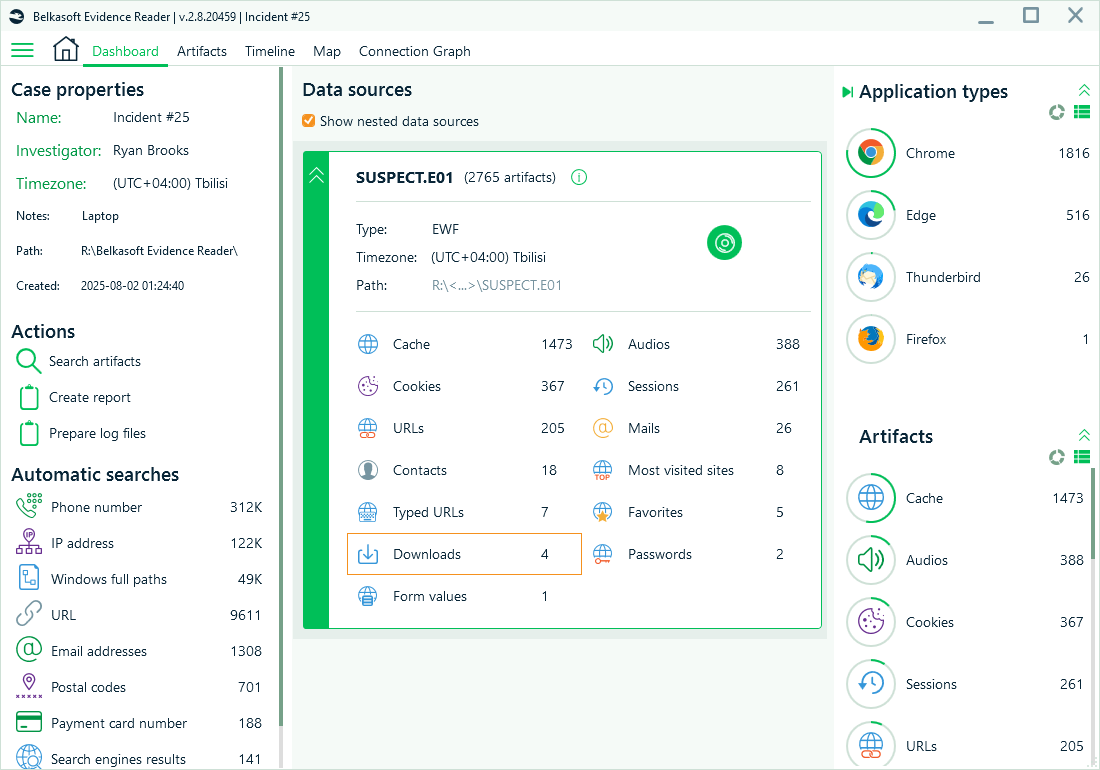
Belkasoft Evidence Reader shows the same data in a similar interface
During reviews, reference Timeline data or Connection Graph details to provide factual answers. These findings justify security improvements, such as enhanced email security and user training, when phishing emails were the primary attack vector.
Conclusion: Complete approach to incident response
You cannot prevent every security incident. A truly secure organization can respond to and recover from incidents quickly and effectively. A successful response depends on three things: the right people, a clear process, and the right technology.
- People: A trained and empowered team with members from different departments.
- Process: A clear, tested plan, like the six-step SANS framework.
- Technology: A powerful set of tools that supports every step of your plan.
The Belkasoft suite of tools provides the technology you need. Belkasoft Triage and Belkasoft R help you identify, collect data, and contain threats. Belkasoft X, powered by the AI capabilities of BelkaGPT and the BelkaGPT Hub, enables you to investigate more efficiently and thoroughly. By combining a skilled team, a proven process, and a powerful technology platform, you can build a company that is ready to handle any security incident and emerge stronger.

