Windows Forensics: Analyzing Prefetch Files with Belkasoft X
Prefetch files are a key artifact in Windows forensic investigations, often categorized as "evidence of execution." They help identify which applications or scripts were run on a system and when. Their scope includes regular programs as well as potentially harmful scripts, malware, or tools like CCleaner or SDelete which are sometimes used to remove traces of activity.
Forensic analysts rely on Prefetch files to piece together execution patterns and timelines. These files can reveal the sequence of events on a system, helping investigators understand user actions, detect malicious activity, and identify attempts to conceal evidence.
In this article, we will explore the mechanics of Prefetch files, the data they contain, and their role in Windows forensics:
- Prefetch basics
- Reading Prefetch files
- Forensic value of Prefetch files
- Considerations and limitations
- Registry settings controlling Prefetch
- How Belkasoft X helps in Prefetch analysis
- Practical tips
Learn how Prefetch file analysis helps uncover evidence of execution and how Belkasoft X facilitates this process.
Prefetch basics
Windows Prefetch files are designed to optimize application performance by pre-loading commonly used applications. This functionality speeds up their future execution and, in doing so, leaves behind valuable forensic traces, including details about application runs and associated file access.
Reading Prefetch files
Prefetch files have a proprietary format and lack an official public specification—all known details about the format come from third-party researchers. They consist of a file header and several sections, each containing distinct data types. It is important to note that the Prefetch file format continues to evolve, with version 31 introduced in 2024 for Windows 11. Thus, to parse a Prefetch file into readable pieces of information, you will need to use tools or libraries capable of decoding them.
You can install one of the various open-source tools made specifically for this task or use a specialized digital forensics tool that helps to analyze prefetch and other system artifacts comprehensively. Alternatively, if you are accustomed to working with Python, you can use one of the pre-made libraries, such as windowsPrefetch.
Prefetch files are stored in C:\Windows\Prefetch with the .pf extension. They are created or updated whenever an application runs, enabling the operating system to preload data for faster execution during future runs. Each Prefetch file is named using the format <EXECUTABLE_NAME>-<HASH>.pf, where:
- <EXECUTABLE_NAME>: The name of the executed application in uppercase letters.
- <HASH>: A hash value representing the path from which the executable was launched.
For example, if cmd.exe was executed, its Prefetch file might be named CMD.EXE-2EB3E6E2.pf, where 2EB3E6E2 is the hash of its directory path:
Prefetch folder contents in Belkasoft X's file system viewer
Forensic value of Prefetch files
Prefetch files offer several key pieces of information valuable to digital forensic investigations:
- Execution timestamps: They record up to eight execution timestamps detailing the last time the application was run. Notably, these timestamps may include an additional ten seconds because the Prefetch process monitors application activity for ten seconds after execution.
- Run count: Indicates how many times the application has been executed.
- Referenced files and directories: Lists files and directories the application interacted with during its execution, which can help identify potentially malicious activities or directories.
Considerations and limitations
While Prefetch files are powerful forensic artifacts, they involve certain complexities that investigators should be aware of:
- Multiple entries: Executables like svchost.exe and rundll32.exe can have multiple Prefetch entries because they can spawn separate sub-processes. Each entry corresponds to a unique execution path or command-line invocation, which can clutter the Prefetch directory and make it challenging to pinpoint specific activities.
- Limited retention: Windows stores only a limited number of Prefetch files, and critical application launches may be lost if the system has been active for a long time or if many legitimate launches follow a malware execution.
- Data volatility: Prefetch data resides on disk but can be altered or removed using administrative privileges or cleaning utilities.
- DLL hijacking: An attacker can place a malicious DLL in legitimate system directories. Prefetch files will reference these loaded DLLs, but identifying them as malicious will require a deeper investigation into file paths and hash checks.
Registry settings controlling Prefetch
Prefetch files may be missing on systems where the feature is disabled, such as on Windows servers or systems with solid-state drives (SSDs), as the performance benefits are minimal in these cases. The registry key controls the Prefetching behavior:
HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management\PrefetchParameters
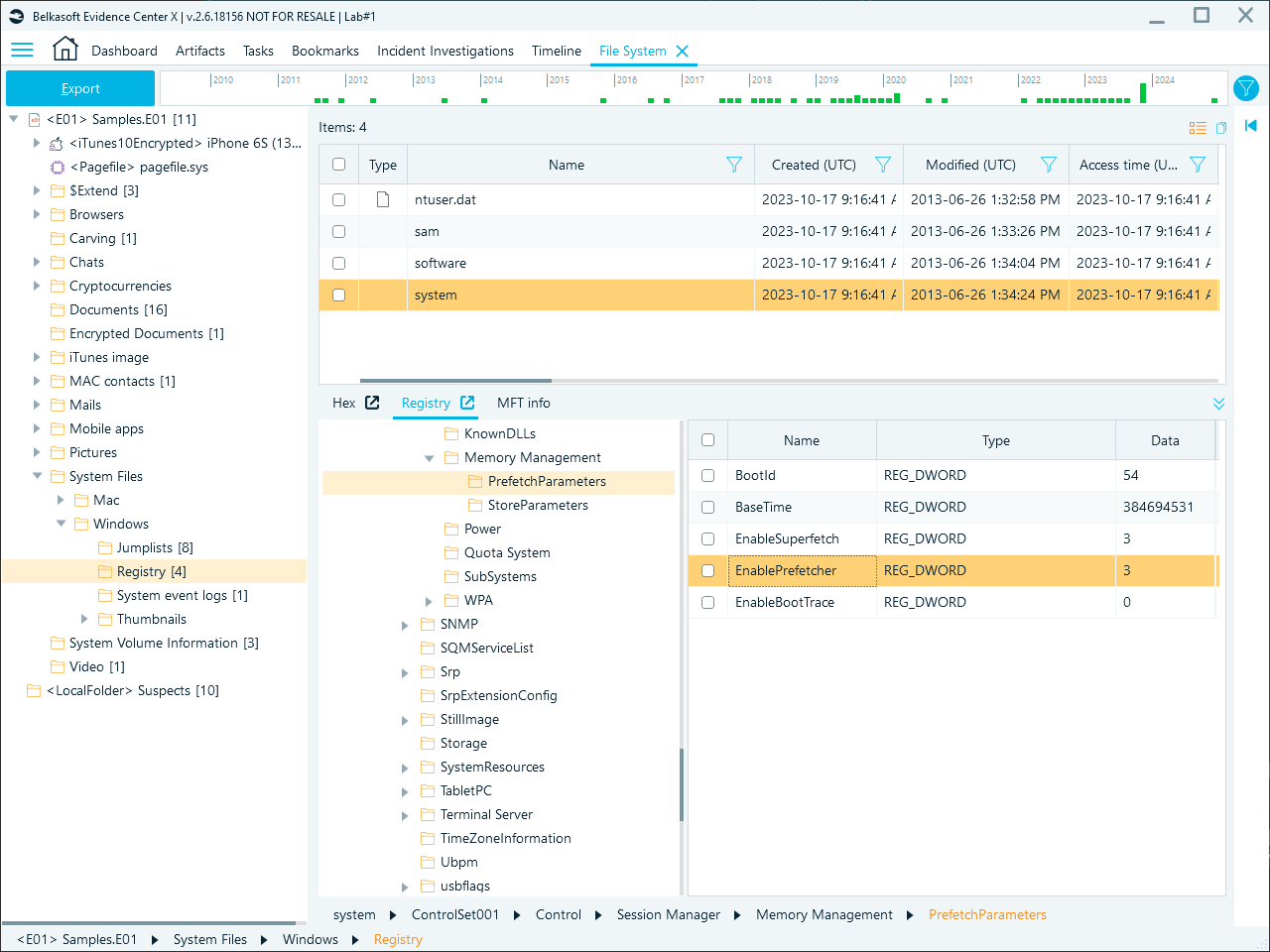
Prefetch parameters in the Windows registry
The EnablePrefetcher value determines the prefetching behavior:
- 0: Disabled
- 1: Application launch prefetching enabled
- 2: Boot prefetching enabled
- 3: Application launch and boot prefetching enabled
How Belkasoft X helps in Prefetch analysis
Belkasoft X simplifies Prefetch analysis by extracting data from prefetch files and providing you with search and filtering options that help narrow down your focus. The Incident Investigations window includes a dedicated Execution category where Prefetch artifacts are listed with the following details:
- Program names
- Last execution timestamps
- Run count
- Referenced files and directories
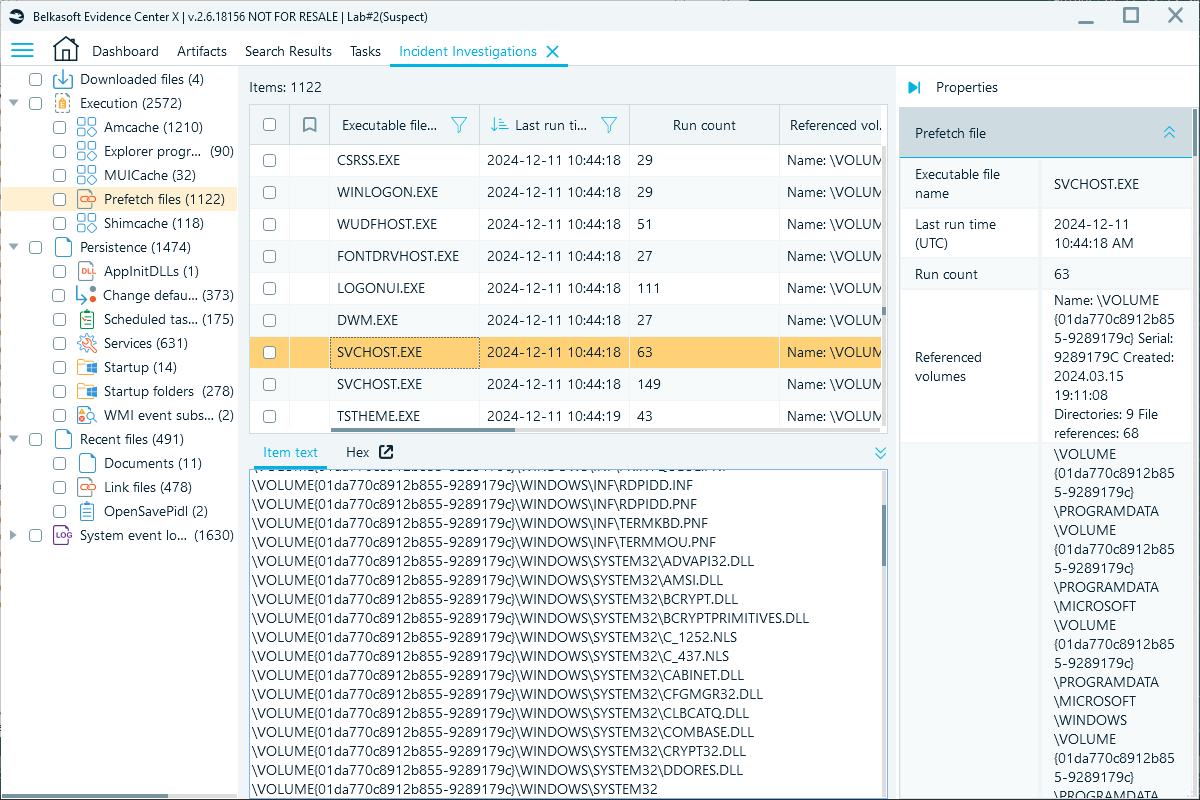
Execution node contents with Prefetch in Belkasoft X
Alternatively, you can review Prefetch files in the Artifacts window, which displays an extended view, such as run history (up to 8 last launches) and prefetch files' filesystem timestamps, which may help you pinpoint user activities, program usage, and potential evidence tampering attempts:
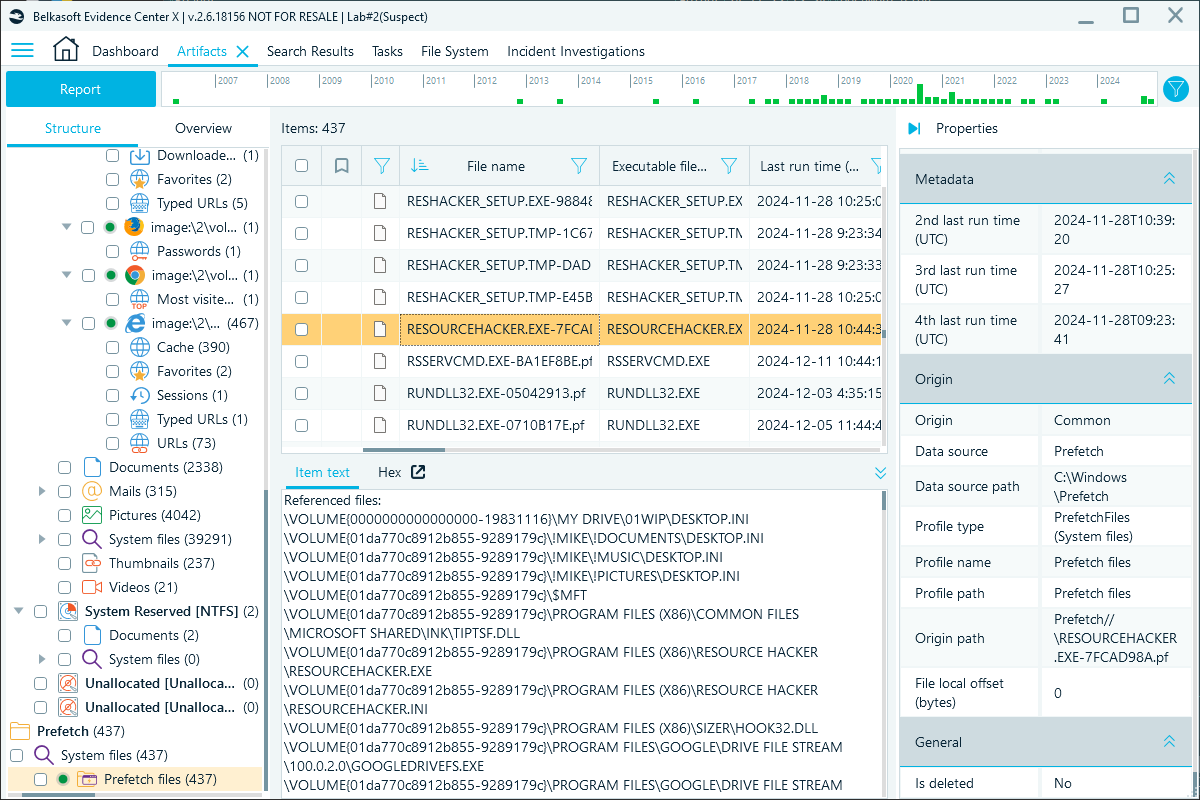
Prefetch files in Belkasoft X's Artifacts window
Similarly, inspecting the Prefetch file for cmd.exe can indicate whether attackers used it to run batch files:
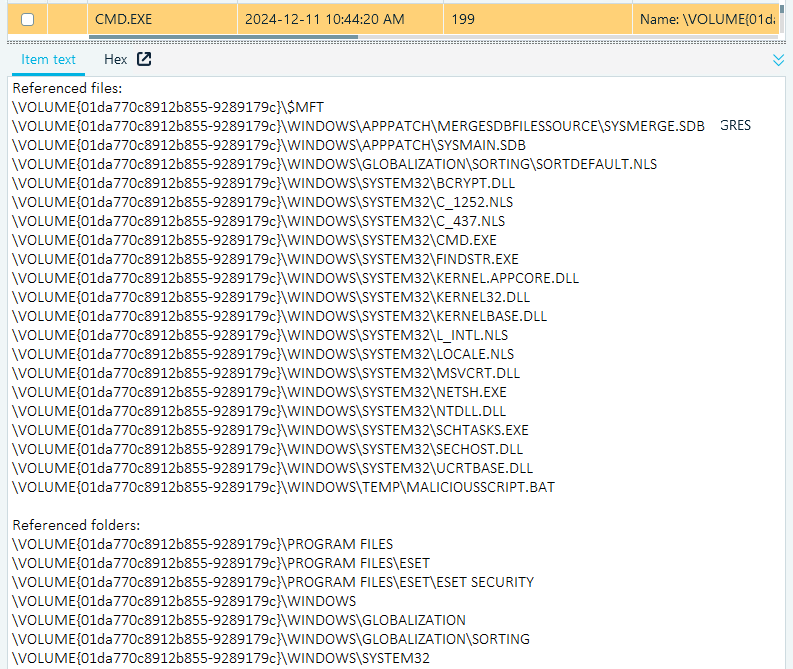
Prefetch file contents preview in Belkasoft X
The previous example demonstrates that Prefetch files contain a list of referenced files, proving that cmd.exe ran a batch script (the final line) from C:\Windows\Temp.
Here is an example of a suspicious file found during Prefetch file analysis:
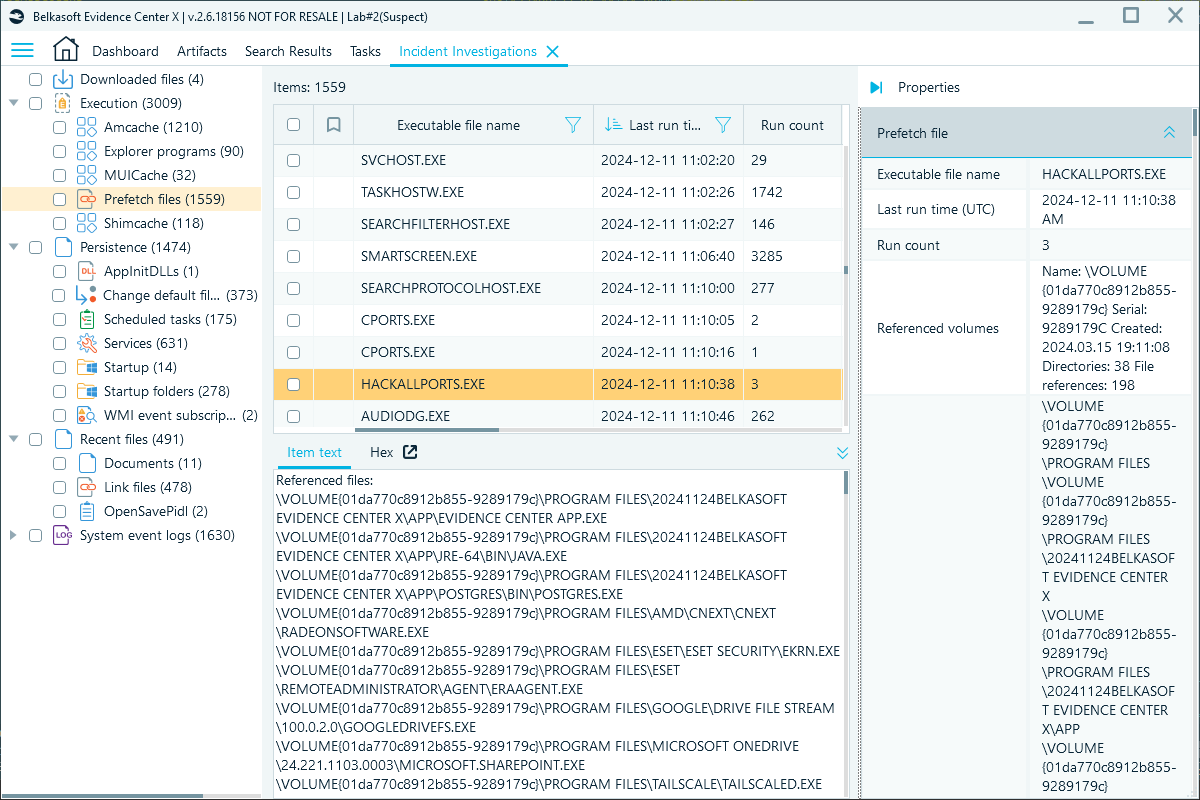
A suspicious executable file found in Belkasoft X
Practical tips
Analyzing Prefetch files effectively requires knowing what to look for—and how to interpret findings. Investigators can uncover evidence of malicious activity by applying targeted analysis techniques. Here are some practical tips to help you with examining Prefetch files:
- Check timestamps: Look for unusual timestamps indicating recent activity.
- Monitor known tools: Identify Prefetch files linked to commonly abused executables like svchost.exe, powershell.exe, or rundll32.exe.
- Reconstruct command-line invocations: Look for batch or script file references in cmd.exe and PsExeSvc.exe Prefetch files.
- Correlate with other artifacts: Combine Prefetch data with logs, registry entries, and system event records.
- Compare hashes: When the same executable appears with different hash values in its filename, it often indicates execution from different paths. This behavior may point to lateral movement, like malicious file transfer tactics.
Note: For system services and applications like svchost.exe, multiple prefetch files with different hashes may be normal. As mentioned earlier, these services often execute from multiple paths or use distinct command-line parameters, resulting in separate prefetch records.
Conclusion
Windows Prefetch files are invaluable in digital forensics, providing a timeline of application execution and interaction. Prefetch analysis uncovers suspicious user and system activity and highlights malicious tactics and techniques, enabling a deeper understanding of cyber incidents. Using Belkasoft X, investigators can efficiently parse, analyze, and correlate this data, transforming it into actionable evidence.
