LNK files (labels or Windows shortcut files) are files that are typically created by the Windows OS automatically, whenever a user opens their files. These files are used by the operating system to secure quick access to a certain file. In addition, some of these files can be created by users themselves to make their activities easier.

Fig.1. Windows Desktop Shortcuts
In this article, we will explore the following aspects of LNK file analysis in cyber incident response investigations:
- LNK file location
- What is inside an LNK shortcut
- How to recover deleted LNK files
- Use of LNK files in information security incidents
We will look into this artifact with Belkasoft X, a digital forensics and cyber incident response tool that streamlines the acquisition and analysis of computers and mobile devices.
LNK file location
Normally, most LNK files are located on the following paths:
- For Windows 7 to 11: C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Windows\Recent
- For Windows XP: C:\Documents and Settings\%USERNAME%\Recent
However, there are many other places where investigators can find LNK files:
- On the desktop (such shortcuts are usually created by users to secure quick access to documents and apps)
- C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Office\Recent\ (for Microsoft Office documents on Windows 7 to 11)
- C:\Users\%USERNAME%\Downloads (Sometimes users send shortcuts via e-mails to other users instead of the documents to be delivered. Consequently, other users download those shortcuts. Again, this is for Windows 7 to 11)
- Startup folder
- Etc.
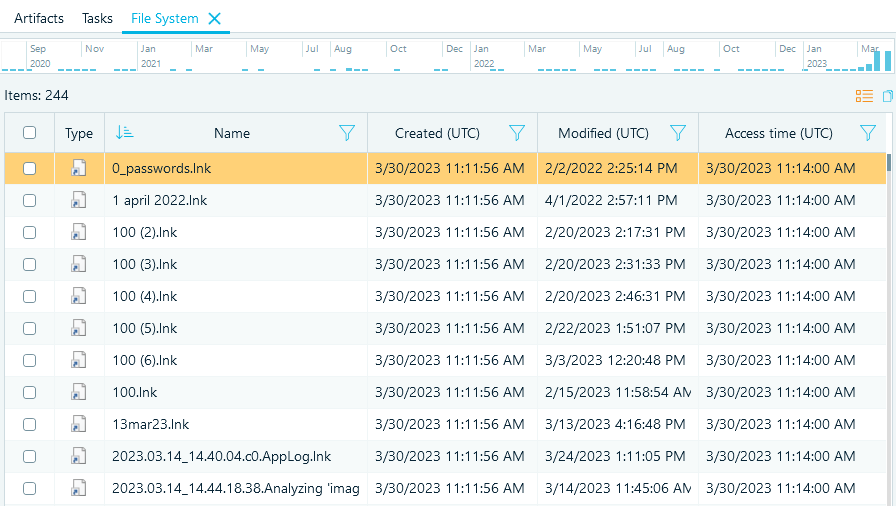
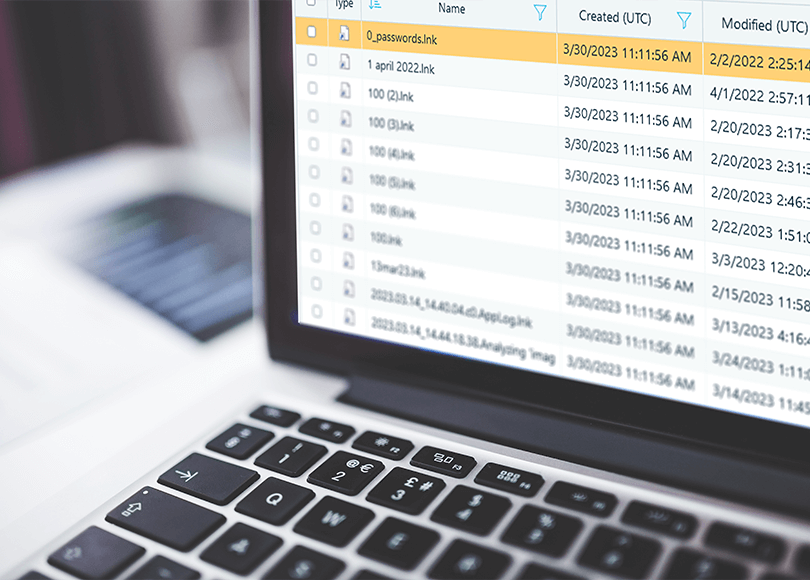
Fig.2. Shortcuts Found in the Recent Folder as shown by Belkasoft X
Contents of LNK shortcuts
Before Microsoft published the information about the format of LNK files, researchers had tried to describe the format by themselves. The complexity of such research is that the different shortcuts contain different data. Correspondingly, when you analyze one shortcut type, the contents and amount of data may be different than when analyzing another shortcut type. Besides, in Windows 10, new fields are present that cannot be found in earlier versions.
So, what kind of information does an LNK file contain? Belkasoft X displays the following three sections with data related to LNK files: 'Metadata', 'Origin', and 'File'.
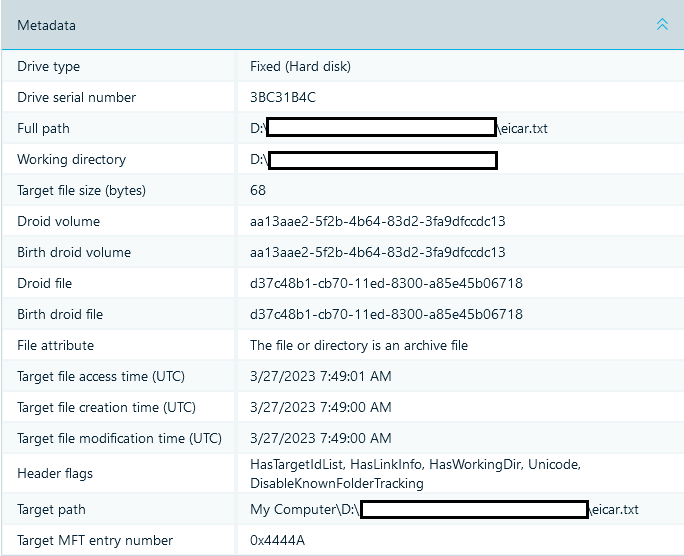
Fig.3. 'Metadata' Section Contains Multiple Details About a Target File
The most important data displayed by the 'Metadata' Section include:
- Source path of a file and its time tags (Full path, Target file access time (UTC), Target file creation time (UTC), Target file modification time (UTC))
- Drive type
- Volume serial number (Drive serial number)
- Volume label
- Target file size (bytes), i.e. the size of the file with which the shortcut is associated
As you can see, such fields as 'Droid file' and 'Birth droid file' can be found. DROID (Digital Record Object Identification) is the individual profile of a file. This structure (i.e. that of a droid file) can be used by the Link Tracking Service in order to determine whether the file has been copied or moved.
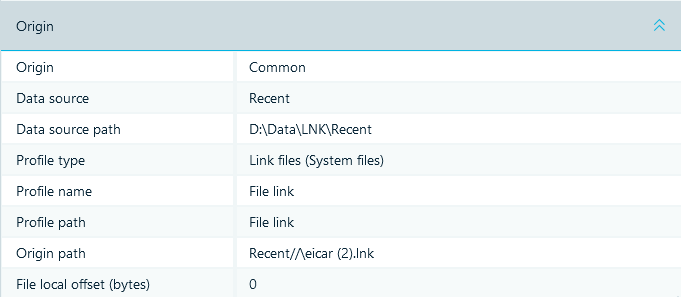
Fig.4. 'Origin' Section Tells Where Selected Artifact Was Extracted From
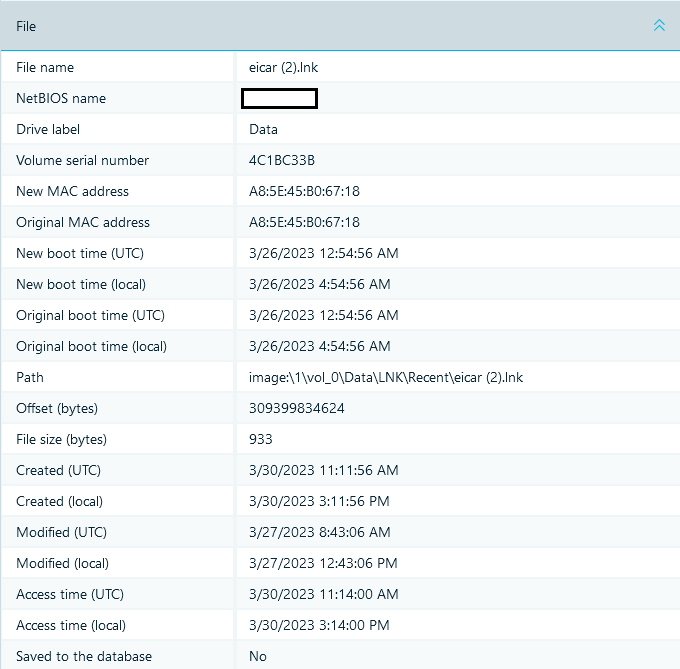
Fig.5. 'File' Section Shows File System Metadata of an LNK File
In the 'File' section you can see the MAC address of the device on which this shortcut was created. This information may help you identify the device associated with when the LNK file was created.
While conducting an investigation, one should pay attention to the time tags of an LNK file. The reason for that is that, as a rule, the time of file creation corresponds either to the time the file was created by a user or to the time of the first file access event associated with a shortcut. As for the time modification time, it normally corresponds to the last file access event associated with a shortcut.
Recovery of deleted LNK files
If one examines the 'Recent' folder described above, up to 149 LNK files will be found there. What should be done, if the shortcut we need was deleted? The answer is simple: for sure, it should be recovered! Recovery of LNK files can be executed with the file header signature, hex: 4C 00 00 00 01 14 02 00.
If you use Belkasoft X, you just need to enable carving and make sure that Link files are selected, and they will be recovered automatically. You can learn about the carving methods with Belkasoft X in greater detail in the article 'Carving and its Implementations in Digital Forensics'.
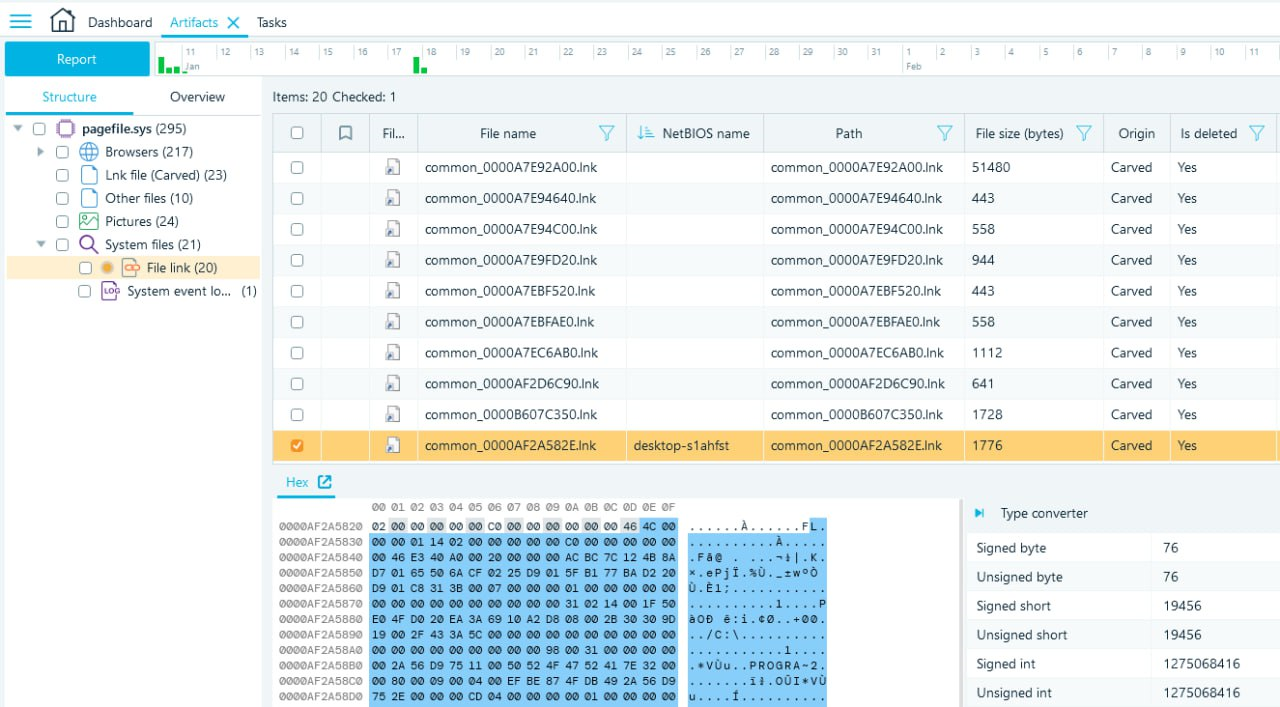
Fig.6. Recovered LNK files
Use of LNK files in information security incidents
Compromising an attacked system
Over 90% of malware is distributed via e-mails. Normally, malware e-mails contain either a link to a network resource or a specifically designed document. If such a document is opened, malware will be downloaded to a machine.
Likewise, LINK files are used for hacking attacks.
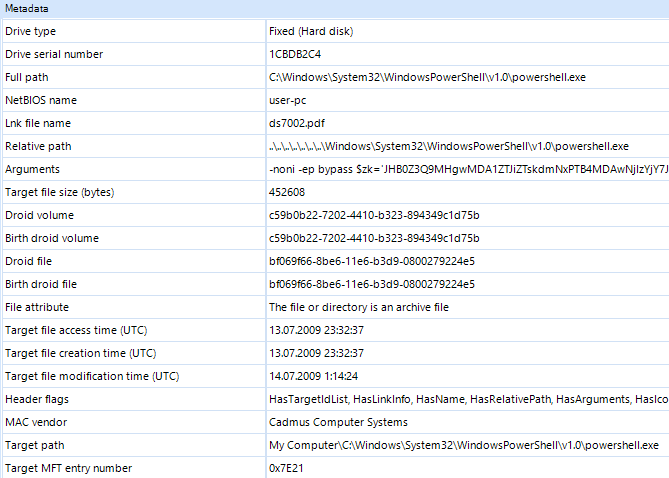
Fig.7. 'Metadata' Section Associated with a Malicious LNK file
The general rule is that such an LNK file contains a PowerShell code that is executed when users try to open the shortcuts previously sent to them. As you can see in Fig.7, such shortcuts can be easily detected with Belkasoft X: there is a path to an executable powershell.exe in the metadata. In the 'Arguments' field, there are arguments of a PowerShell command and encrypted 'payload'.
Embedding in a compromised system
One of the methods to use LNK files is to embed them in a compromised system. In order to activate malware whenever a corresponding machine is turned on, the following trick can be utilized. An LNK file with a link to an executable malware file (for example, to a file with the loader code) should be created, a shortcut is to be placed at the following address: C:\Users\%User profile%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup.
In this case, as soon as a machine is launched, the malware will be activated as well. Such shortcuts can be found in the 'File system' tab of Belkasoft X.
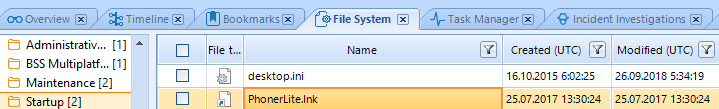
Fig.8. 'PhonerLite.lnk' Shortcut in Startup
Conclusion
LNK files are Windows system files that are important in digital forensic and incident response investigations. They may be created automatically by Windows or manually by a user. With the help of these files, you can prove the execution of a program, opening a document or a malicious code start-up.
Belkasoft X can help you to locate existing LNK files, recover deleted ones, and analyze their contents.