Introduction
Carving is an irreplaceable technique widely used in data recovery and digital forensics. By using carving, we essentially perform a low-level scan of the media for various artifacts, looking for signatures—specific sequences of bytes, characteristic of this or that type of data.
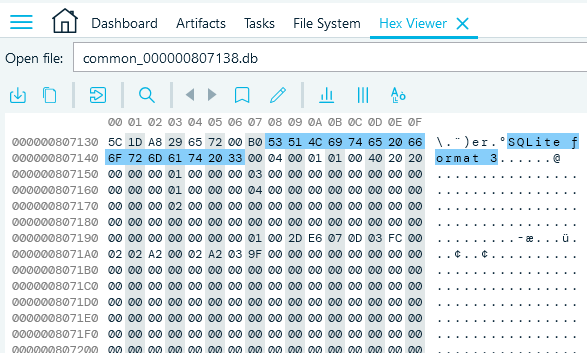
SQLite database signature in Belkasoft Hex Viewer
This also means that carving disregards files themselves in performing the byte sequence search, thus becoming extremely helpful in cases where data has been corrupted or deleted. However, its usefulness is not limited to one particular scenario. Let us take a look at various cases where carving comes in handy.
Renamed, relocated, hidden data
We have talked briefly about using carving to find hidden, renamed, and relocated data in our whitepaper about countering common anti-forensic efforts. Since carving does not take into account the file itself, it does not care about its name and location either. Therefore, by performing carving, we ensure that files that have been slightly modified (e.g. change of original location, name, or extension) will be found on the media despite the changes the user applied in an attempt to conceal data. This also applies to data hidden inside containers and other forms of hidden data. As an example, images inserted into an MS Word document or scripts injected into a PDF file would not be visible in the file system, however, we would be able to find them using carving.
Deleted data in unallocated space, free space, and slack space
Unallocated space
Another important implication of carving is searching for data inside slack space and unallocated space.
What is unallocated space?
Any physical space on hard drive that does not belong to a partition is considered ‘unallocated’. These areas are not recognized by the operating system and are generally unusable in regular means, unless you expand an existing partition or create a new one to include that space. In addition, there are some slightly more advanced techniques and tools that allow writing to the unallocated space, which is something that might be used by criminals.
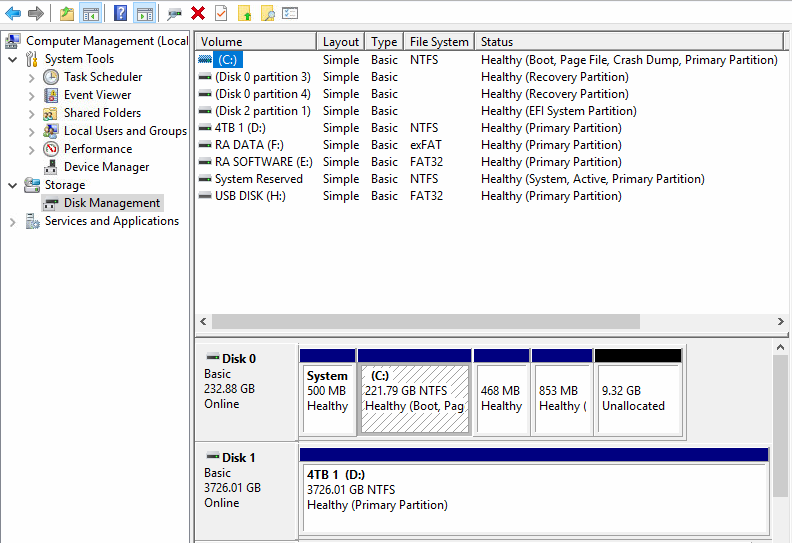
Unallocated space can be seen in Windows disk manager
Free space
Free space is a part of the allocated space on a drive that the operating system can use to write data to. However, it does not mean that this area is entirely empty, since deleting files does not physically remove them from the drive: it just means that the space they were using changes its status from occupied to free, and the operating system may now use it. Until some new file overwrites them entirely, it is still possible to locate the files that were deleted by carving free space.
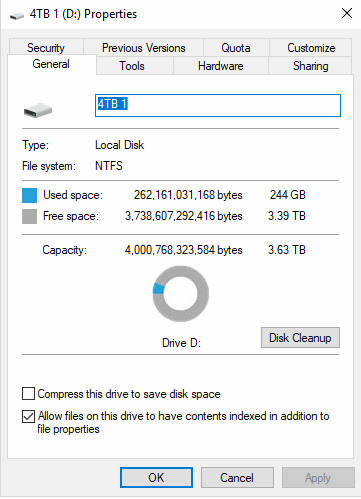
Free space for any disk can be reviewed in its properties
Slack Space
Slack space is the area of the drive’s allocated space that is unused by any files, which often contains remnants of files that previously were stored there. The reason for the emergence of the slack space is that while the disk is divided into sectors of equal size, the files saved in each sector vary in size, leaving chunks of unused space. This space may contain remnants of old files, as well as be used for hiding data, and therefore might be a valuable source of data.
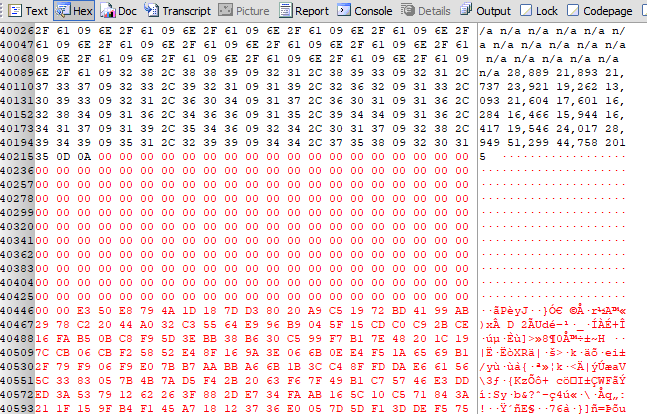
Slack space shown in hex viewer
How carving works
What can and what cannot we carve?
Most disks and disk images can be carved. It is also possible to perform partial disk carving. The implications of carving we mentioned above work on the types of media that employ hard drives or flash drives, but we have not touched SSDs.
If a device uses an SSD or eMMC, carving for deleted data is impossible. However, existing files with modified extensions, as well as hidden and embedded files can still be carved. It would also find data in slack space.
As we have already mentioned, carving works on the level lower than the file system, which implies that it is not possible to carve, for example, folders, as folders only exist in the file system.
In addition, carving is the only way to find data in the RAM.
Carving methods
Header signature
In most cases, carving looks for a stable signature of file header. A good signature is one that is unique to a file type. It usually needs to be fairly long in order to secure uniqueness, which helps to prevent confusion between file types. Another important condition is that the signature needs to be constant, i.e. it remains unchanged in various conditions. Failure to fulfill those conditions leads to discovery of false positives, which is a somewhat common problem with carving for header signatures. An example of a bad signature would be, say, something like “0000000000” (likely not unique) or “MZ” (too short). An example of a good signature is a SQLite database header “SQLite Format 3”, which is long, unique, and constant.
Footer signature
Another way of performing carving is looking for а footer signature, which determines the end of a file. The main problem with looking for а footer signature is that it may easily be overwritten or located at the end of the disk space due to the fragmentation, which makes this method less reliable. When it is used, it is usually controlled, i.e. limited by a certain amount of bytes: if, for example, after looking through five consecutive megabytes of data one has not found the footer, they stop looking and consider it the end of a file.
File size
In some cases, it is possible to fetch the file length from its header, in which case we look through the next X bytes as determined by the size. However, not all file types include this information in their headers, in which case one would have to set up a certain limit on the amount of bytes to be read. In other cases, the file size data in the header might be incorrect. Generally, this method requires a certain amount of control checks in order to guarantee its effectiveness.
File carving vs. Data carving
While talking about carving, it is important to distinguish between file carving and data carving, which are two related yet different terms. File carving is used as an attempt to use file header to reconstruct the whole file. If a file header were damaged, recovery of a file would be impossible.
Data carving can be seen as carving of parts of a file in order to try to collect bits of data that might be relevant to the case. Data carving is possible even if a file header is damaged, or if a file is fragmented or damaged. This type of carving is particularly useful and efficient when used on “small” types of data, such as chats, browser URLs, or emails in common formats (EML, MIME etc.).
How to perform carving
First, connect your data source to the computer to be used for running forensic analysis. A data source can be a device, a disk image, a memory dump, a hibernation file or even a file. Make sure it is one of the “carvable” types of data sources.
Next, choose what you are going to carve, taking into account the amount of time you have, the types of data you are looking for, and the data source itself. Usually, the best option is to perform carving on the entire data source, including both allocated and unallocated space. However, if you are short on time and/or looking for specific data, you can choose which parts of the disk you want to carve. For example, if you are only looking for something that you know has been just deleted, it would make sense to start with carving only the allocated space, as most likely you would find the recently deleted information there. Some forensic software products (one of them is Belkasoft X) allow you to choose disk partitions to be carved.
As the final step, you would need to analyze the results—whatever carving was able to find and recover.
Using recovered data
Data collected using carving may further be examined with the help of various forensic software. With the help of an appropriate product, one can analyze dozens of various types of data, including pictures and videos, databases, etc, discovered by carving.
If after performing the analysis you are still missing some information, you may reverse to the custom carving.
Custom carving
Although most of the modern forensic tools are powerful and are designed to perform automatic carving in an efficient manner that almost eliminates the chances of missing data, in case this does happen, you can always perform custom carving. Most modern forensic software products come with some sort of a tool that can help you look through data and search for signatures.
Carving with Belkasoft X
Carving is a built-in feature of Belkasoft X. The product allows users to perform full disk carving, or carve one or several partitions, carve memory dump or a physical image of a mobile device. Belkasoft X can carve a few hundred types of files and formats.
After the case has been created and the data source has been selected, Belkasoft Evidence Center prompts user to choose which types of data carving to select. Carving variations are offered depending on the selected data source.
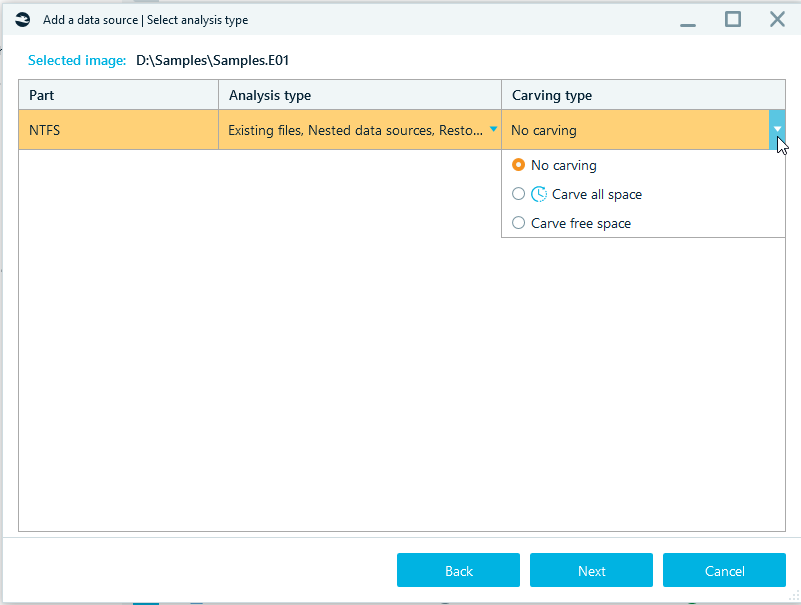
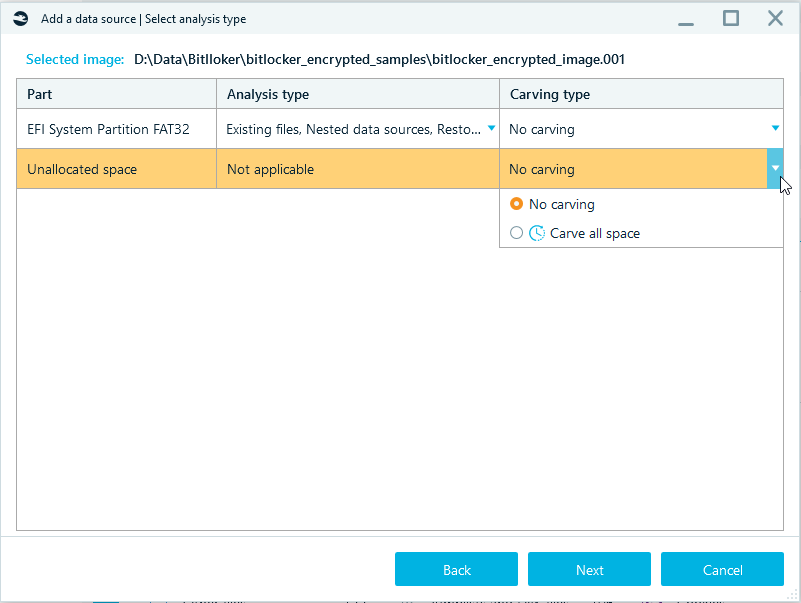
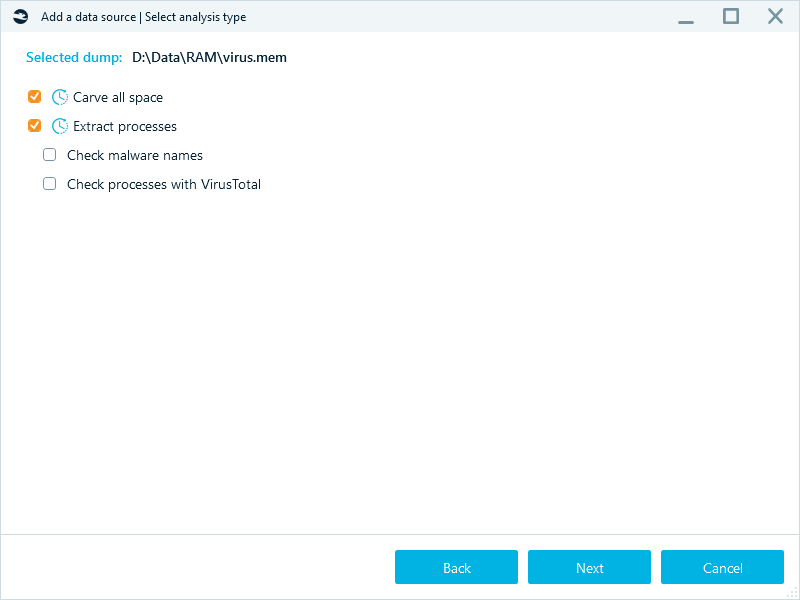
In order to make Belkasoft X to not only analyze files that exist on the data source but to carve data as well, it is important to select Carving type.
The available options are:
- Carve all space—carving the selected data types, including carving files and free space.
- Carve free space—carving the selected data types in free space only.
- Unallocated space—carving the selected data types in unallocated space. The Unallocated space feature is available for a full physical disk image.
- Extract processes —extracting processes from memory dumps. Restored files will contain the following information in their name: file type (‘document’, ‘picture’, etc.), index number and an extension matching the file type.
When both Carve free space and Unallocated space boxes are ticked, Belkasoft X will only restore deleted files thus separating them from any other files found on a data source.
Files restored by Belkasoft X carving are indexed and named according to their
file type
In case when both Analysis type and Carving type options are selected, analysis results may contain duplicates.
The information about whether the file was extracted during a common analysis or was carved can be viewed in the Properties tab, in the section called Origin.
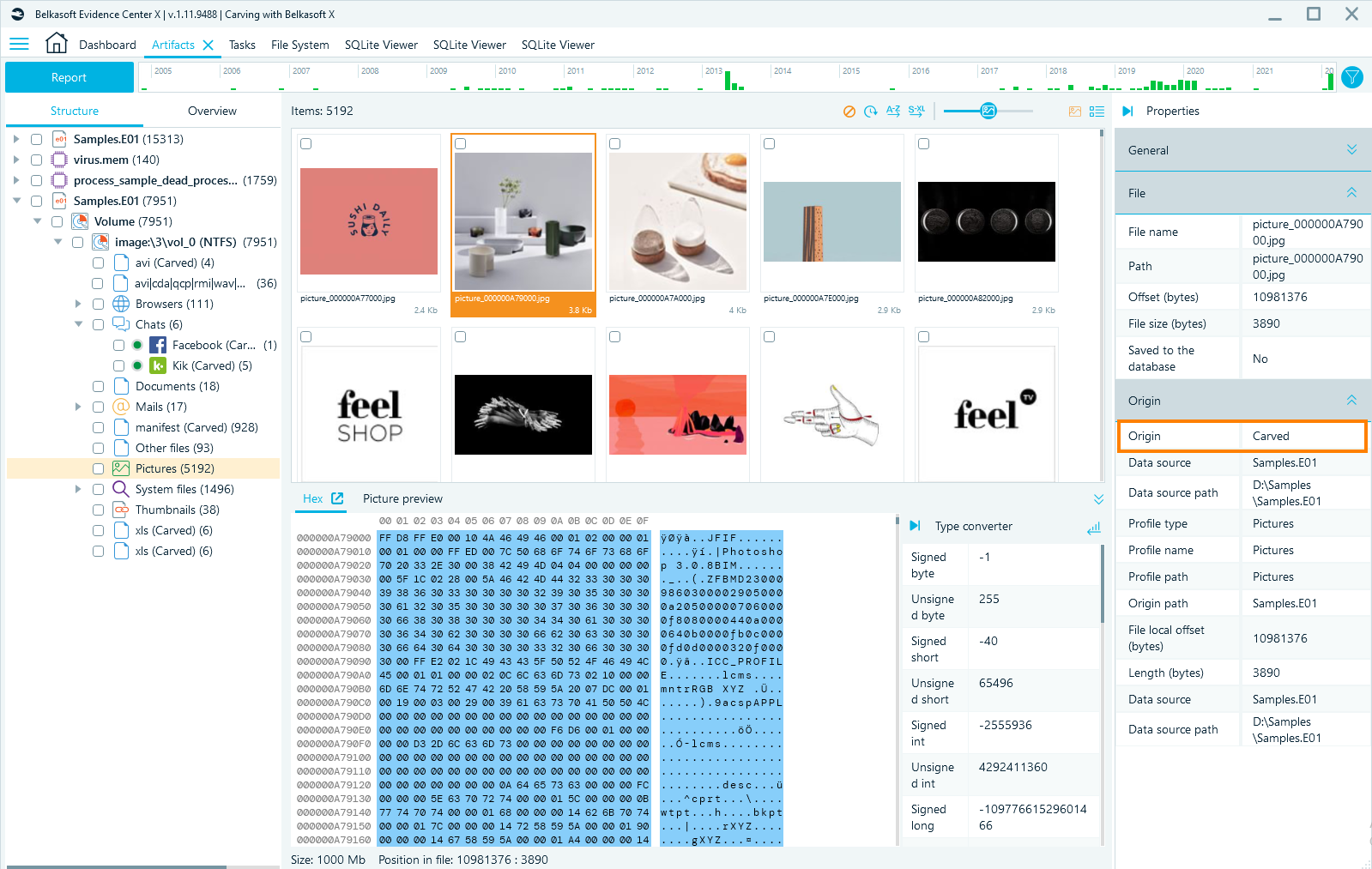
This is an example of the file that is marked as Carved
Belkasoft Custom Carving
Belkasoft Custom Carving is a feature of Belkasoft X, which allows users to add their own headers and footers or signature sets, so these signatures could be used by Belkasoft X during the carving process. This functionality greatly expands the possibilities of carving performed by the tool. The non-standard user's headers and footers are most commonly used when conducting the investigation of DVR and CCTV systems.
One could add headers and footers using Settings menu.
- Go to Home → Settings
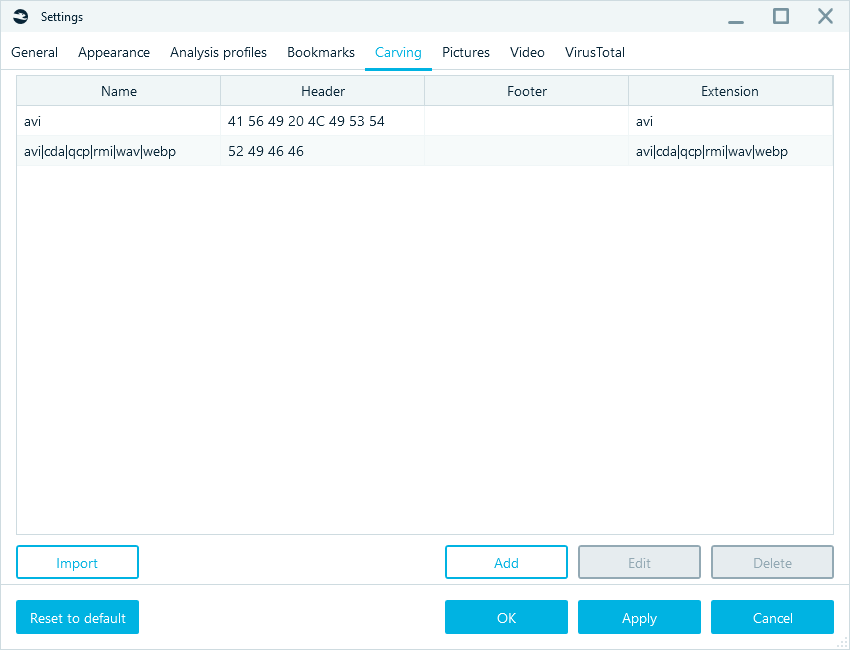
- Click on Carving tab
- Click on Add button and add your own header and footer.
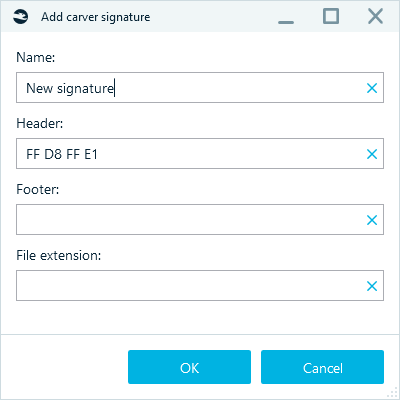
In addition, one could import the third-party signature sets using the same Carver signatures tab.
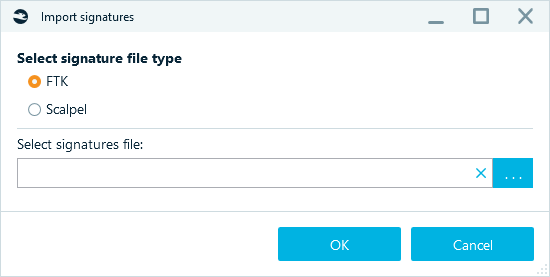
- Click on Import button and specify the path to the Scalpel or FTK (AccessData) signature file.
- Click on OK button. Signatures will be imported from these files into Belkasoft X.
Extract processes
Extract processes option could be activated in the Advanced carving options window. Extract processes is a special algorithm that allows you to investigate fragmented data inside a RAM dump and restore processes that were running on the system. This functionality is available when analysing memory dumps, hibernation and page files.
In addition to the live processes, this feature is capable of restoring the dead processes. The following information on a detected process is extracted:
- Process name
- Malware name
- File size (bytes)
- Offset (bytes)
- status (whether the process is alive or dead)
- Is process name suspicious
The selected process can be viewed in the Hex Viewer.
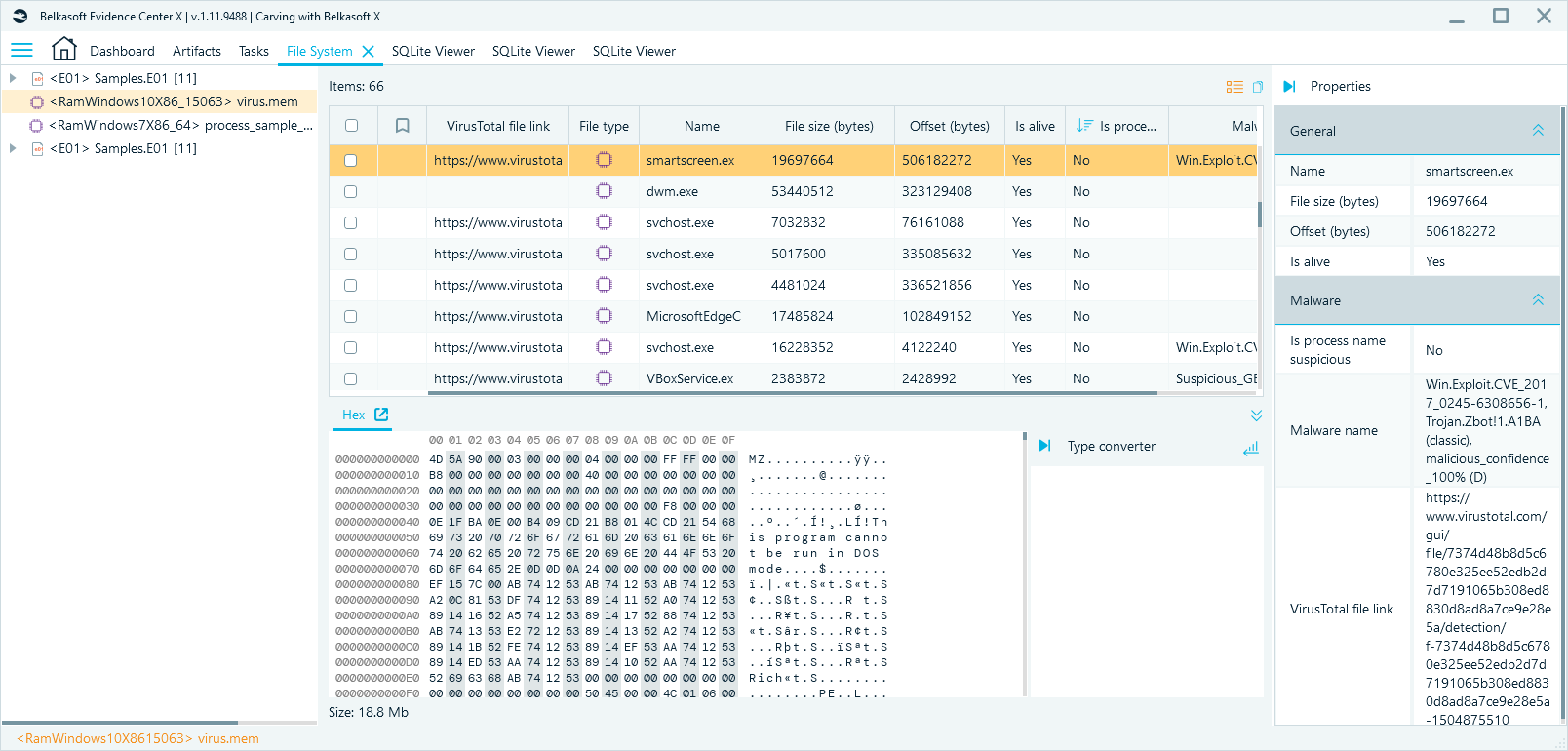
In addition, the process can be analysed with VirusTotal or saved to a file for further investigation.
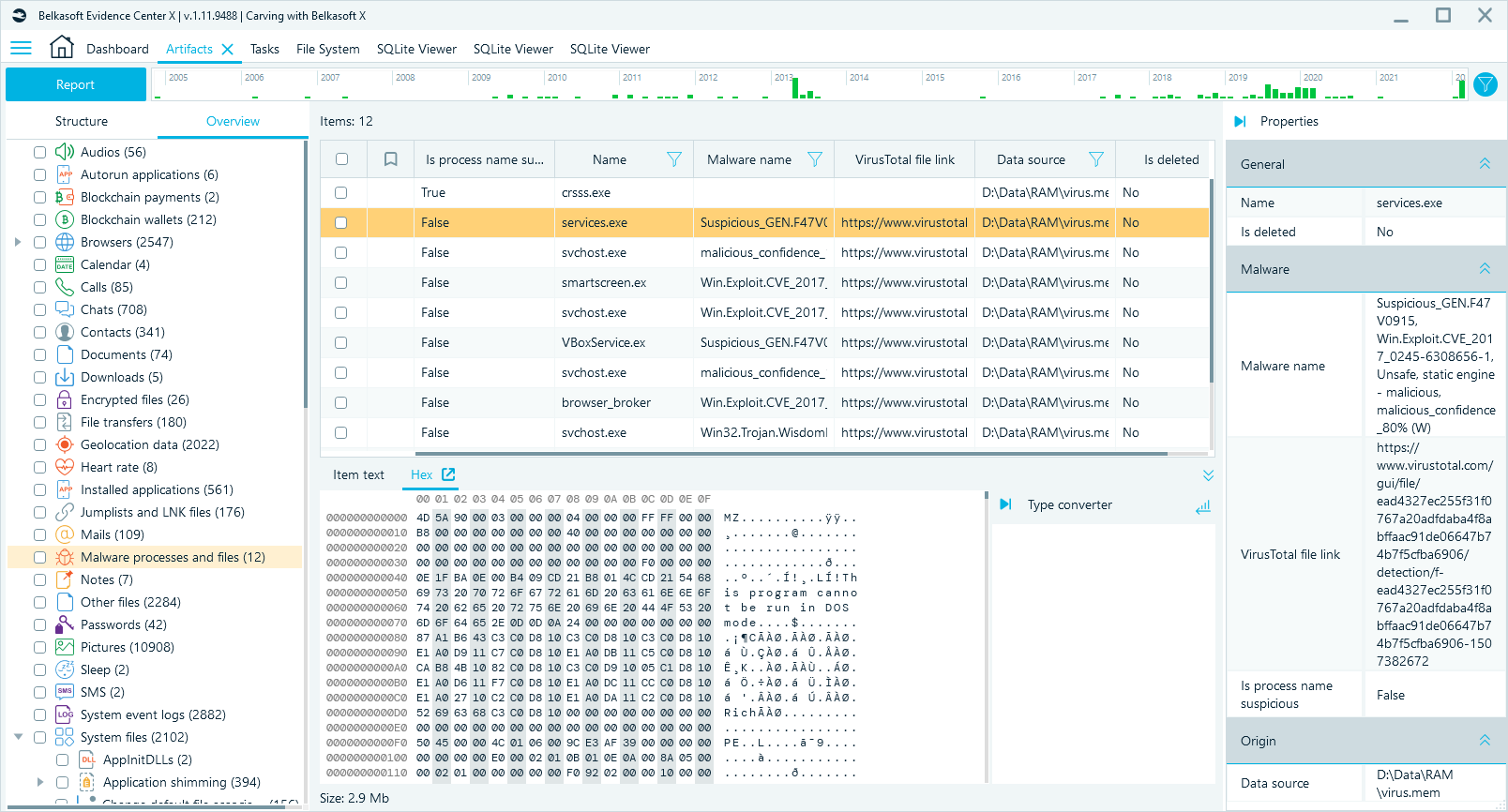
The found malware processes can be seen on tab Artifacts Overview in node Malware processes and files:
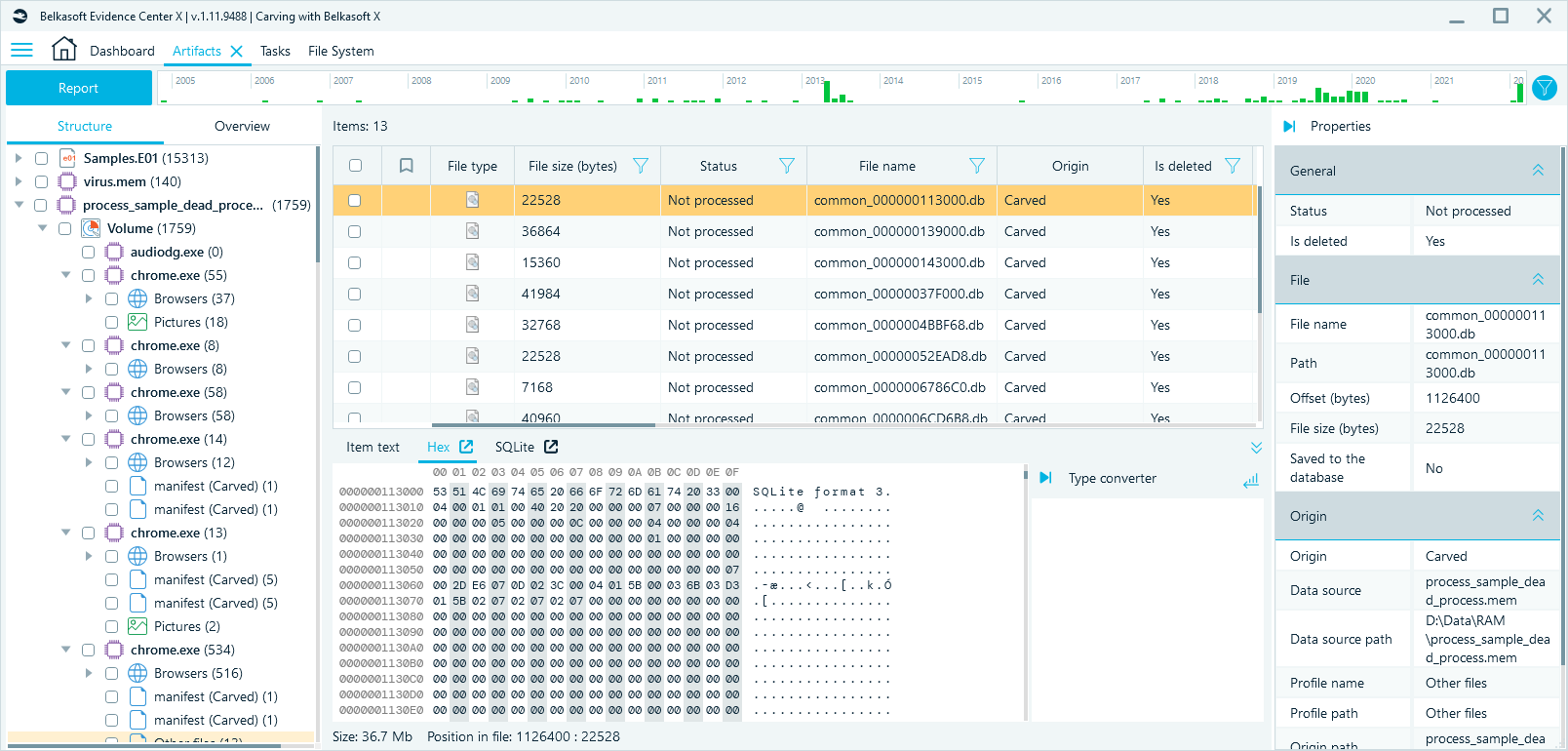
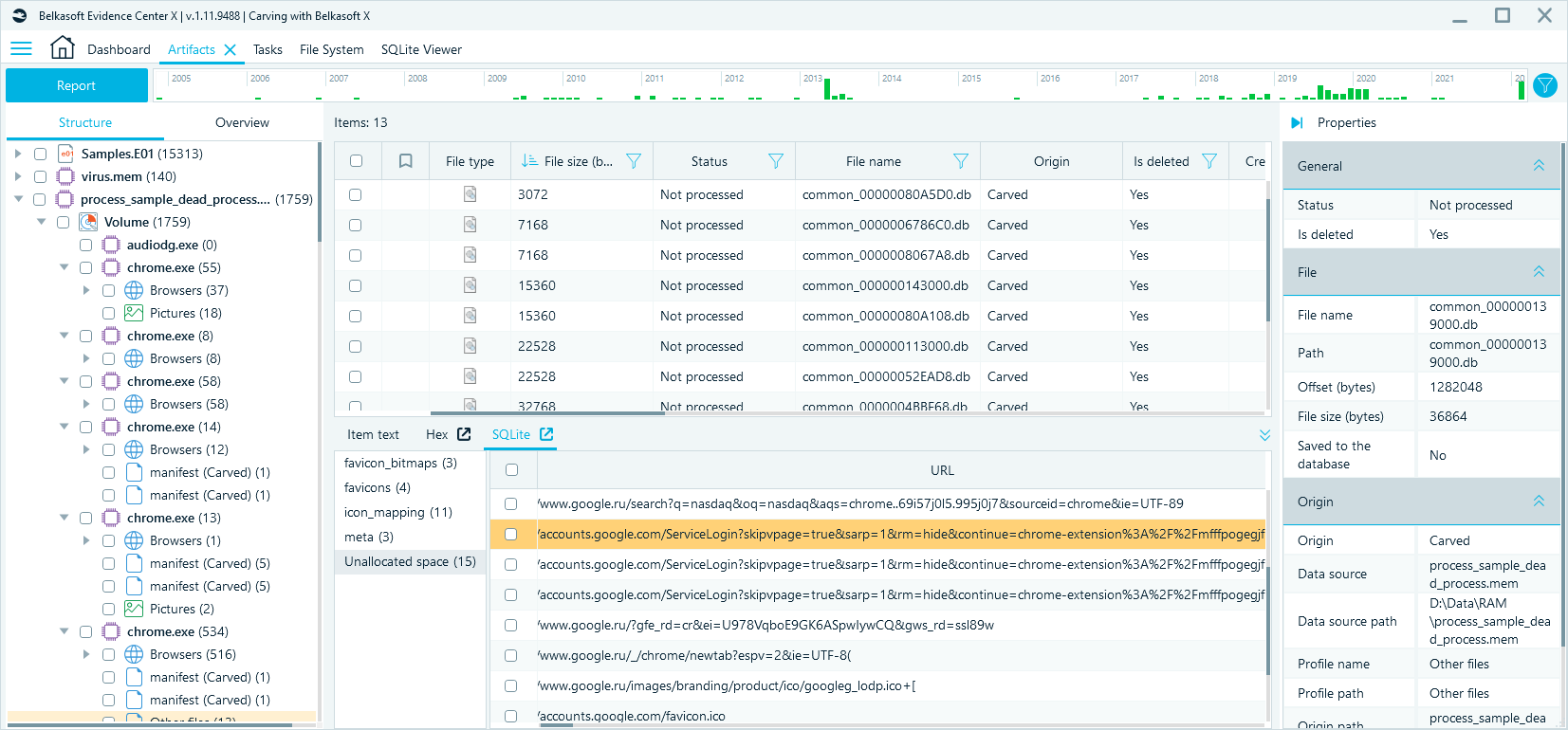
Using the Extract processes feature, you can not only restore databases, but also associate them with a specific application. For example, you could see on the picture below that 13 files with the '.db' extension were associated with the restored process 'chrome.exe'. When viewing the file 'common_000000113000.db' in Hex Viewer, you can see that this file is a SQLite database.
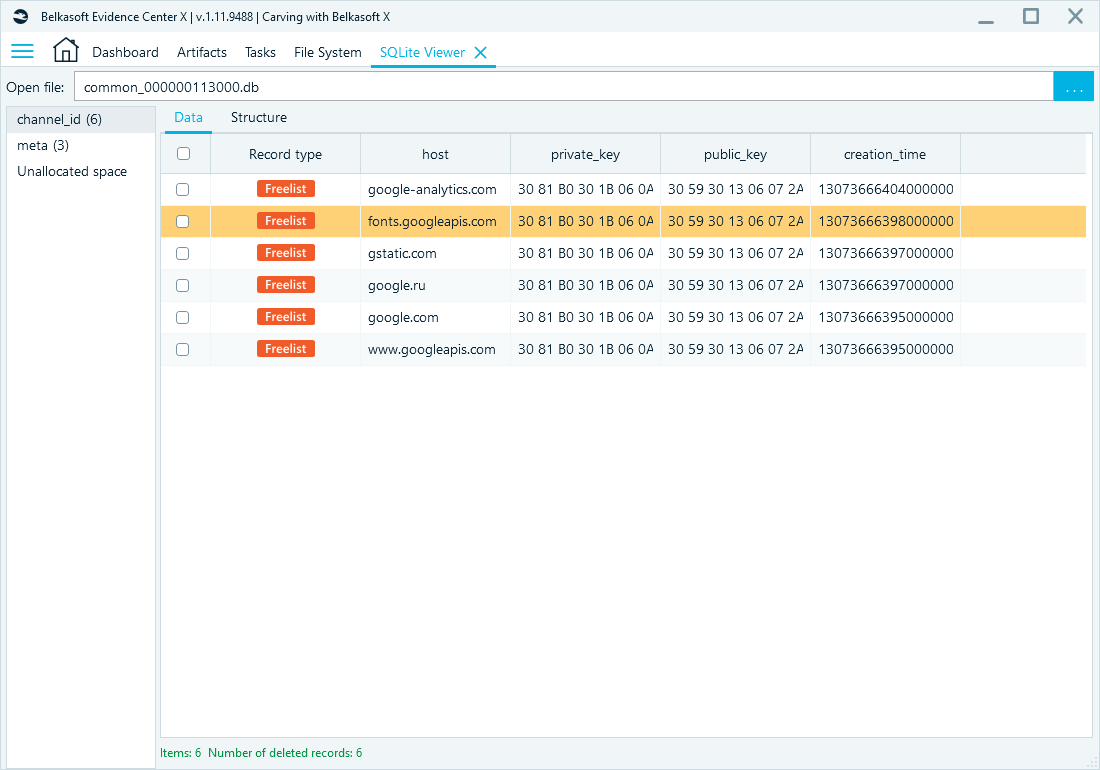
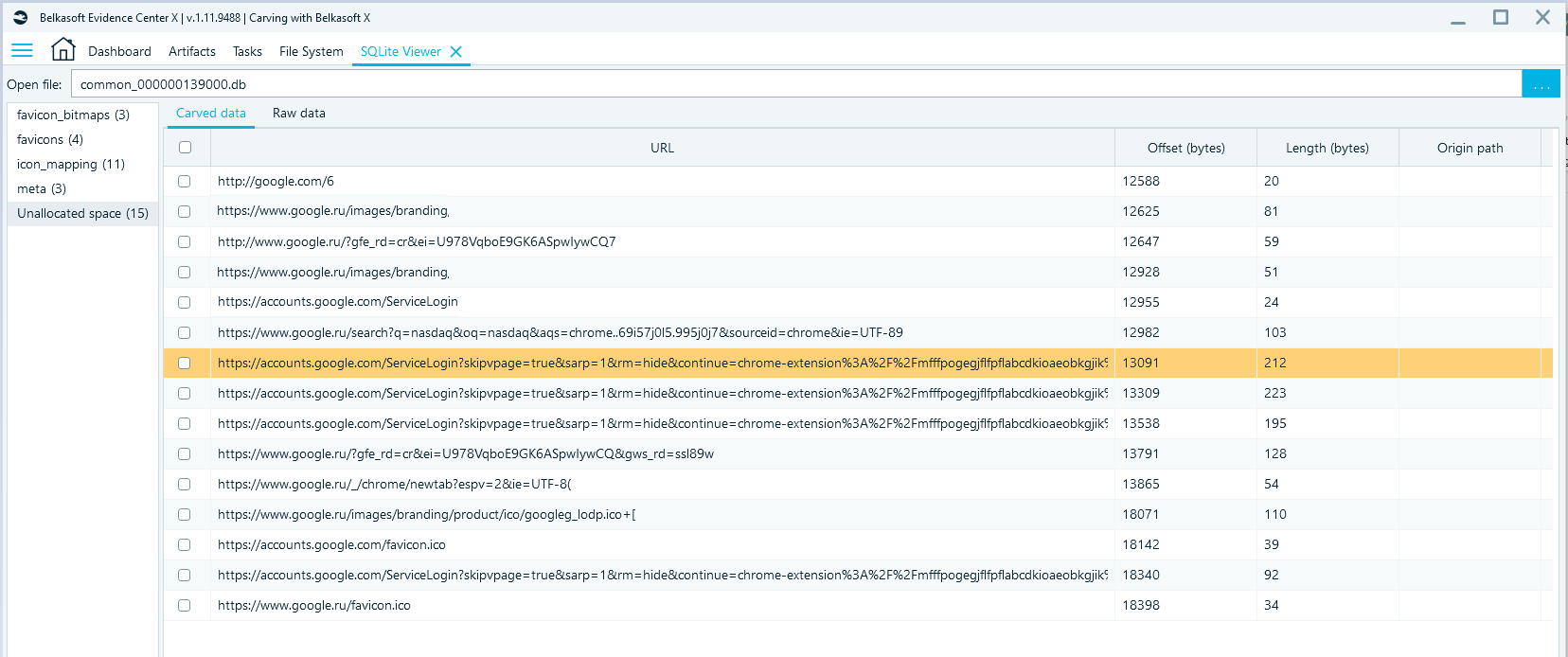
The contents of a SQLite file can be viewed using SQLite Viewer tab:
SQLite records carving
In addition to the deleted files, Belkasoft X can carve SQLite database records. This feature is the most useful for the investigations of logical images of mobile devices, file systems of mobile devices, instant messengers, web-browsers, etc.
For example, you can recover records deleted from the contacts database of a mobile device, deleted SMS and MMS messages, calls and so on. Here is an example of a deleted records recovery from a SQLite Telegram (Android) database.
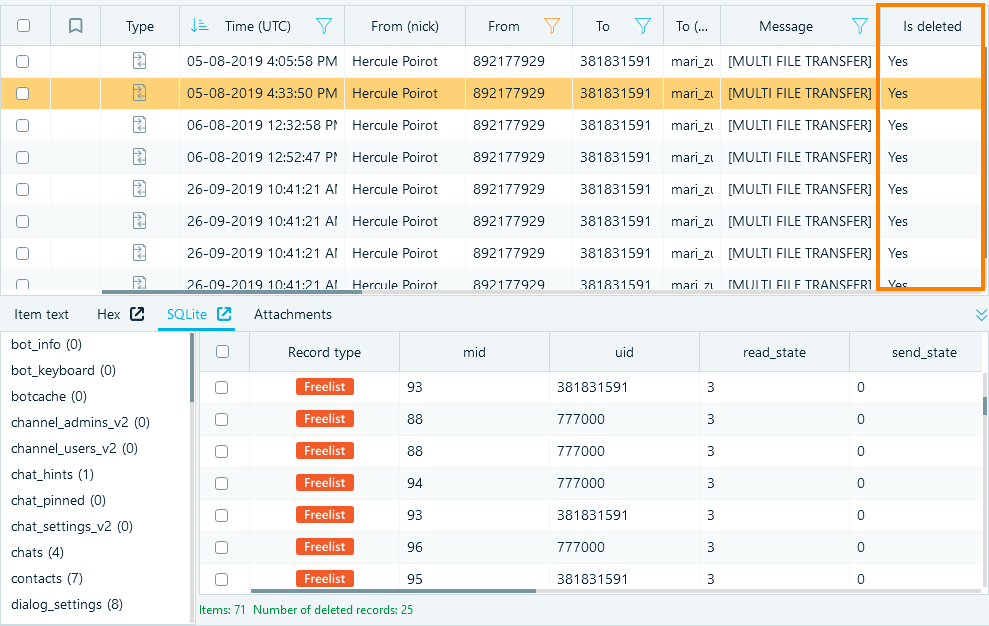
One can use SQLite Viewer, which is integrated in Belkasoft X, for the in-depth SQLite database records recovery. Belkasoft X can also carve and restore data from unallocated space in SQLite databases.
Conclusion
Belkasoft X has a unique functionality for carving different file types: standard files that are supported out of the box, and custom user files via signatures. Belkasoft X can use carving to restore deleted SQLite database records including carving from an unallocated space. The article describes the flexibility of Belkasoft X carving features.