Introduction
Belkasoft X is a comprehensive platform for digital forensic and cyber incident response investigations. It features powerful tools and modules that help examiners extract, analyze, and report on digital evidence from a wide range of sources. One of the standout features of Belkasoft X is its support for Sigma rules.
Sigma is a popular open-source format for describing detection rules for security information and event management (SIEM) systems. Sigma rules are used to identify specific patterns of behavior, events, or indicators of compromise (IOCs) in log files, network traffic, and other digital artifacts. By importing Sigma rules into Belkasoft X, examiners can leverage these rules to automatically identify suspicious or malicious activity in their investigations.
In this walkthrough, we will show you how to import Sigma rules into Belkasoft X and use them to analyze digital evidence.
What are Sigma rules?
Sigma rules are a series of conditions applied to data, particularly system event logs, that filter out relevant details. The authors of the format suggest the following definition:
Sigma is a generic and open signature format that allows you to describe relevant log events in a straightforward manner. The rule format is very flexible, easy to write and applicable to any type of log file. The main purpose of this project is to provide a structured form in which researchers or analysts can describe their once developed detection methods and make them shareable with others.
Sigma is to log files what Snort is to network traffic and YARA is to files.
Official Repository: https://github.com/SigmaHQ/sigma
How to create a Sigma rule
Official guide
Unofficial, but also a good guide
You can find a variety of Sigma rules on the Internet, or you can create your own. To create a Sigma rule, you will need to start by creating a file with a .yml extension and opening it in a text editor. We recommend using VS Code as it has extensions for working with yml files, including formatters.
Next, you will need to define the input fields for the rule, such as the name, log source category, product, tags, description, and more. These fields are not required, but it is recommended to fill them in as it will help you work more productively with the information. For example, you can filter the collection of detected rules by name or category.
The rule fields can look like this:
In addition to the essential fields, it is also useful to set other, optional fields:
The fields are well described in the official guide.
Now let us figure out what we are going to filter and how to do that. Explore any log entry in Event Viewer:
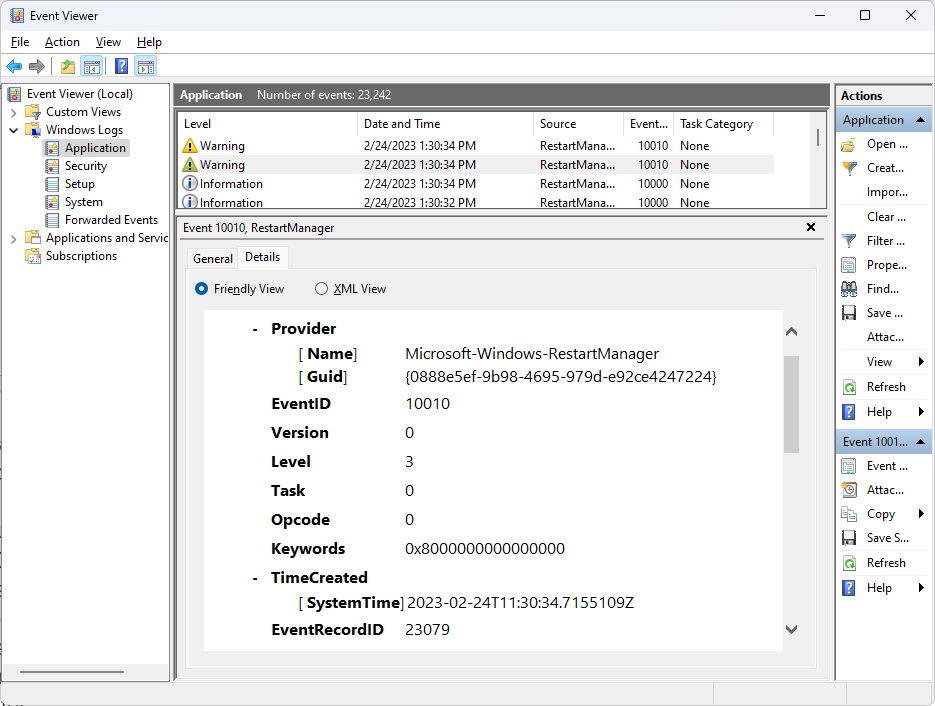
Each log has its own set of properties. Different logs may have different sets of properties, but there are properties that are present in almost all logs.
Belkasoft X extracts the following properties:
- EventID
- Level (shown as "Event type" in Belkasoft X)
- Category
- Qualifiers
- System time
- Computer
- Provider_Name (shown as "Source name" in Belkasoft X)
- Channel
- Security_UserID (shown as "Security ID" in Belkasoft X)
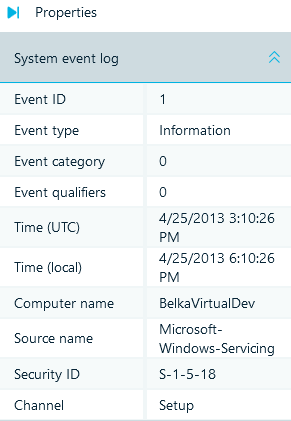
Belkasoft X stores the remaining properties of a log entry in the Description property of the corresponding artifact. Please refer to the product manual for any limitations caused by this.
After we have identified what we want to filter and defined the set of properties and values, we can start building the rule. The main node in a rule responsible for filtering is called "detection":
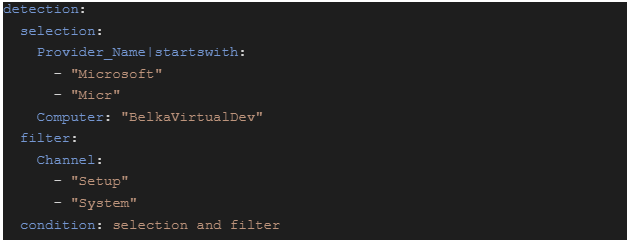
It contains information about the filtered properties and their values. The node is composed of a set of subnodes, each of which imposes a condition on a specific property. For example, the "selection" node on the screenshot above applies a filter to Provider_Name (i.e. Source name) and Computer properties.
Node types
There are several types of nodes:
- Mapping node: represents a key-value object, for example, the node Computer: "BelkaVirtualDev" applies a condition to the computer name
- Sequence node: represents a key-sequence_of_values object. For example, the Channel node in the example above is a sequence node and it applies a condition to the Channel property, which is Channel = "Setup" OR Channel = "System". The sequence must contain at least one value
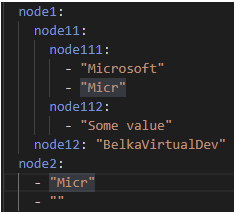
- Complex node: consists of several other nodes. For example, the selection node in the example above consists of two other nodes. The level of nesting for such nodes can be unlimited:
How rules are interpreted
It is important to understand how Sigma rules are interpreted, particularly in terms of conjunctions and order of precedence.
- Mapping nodes are straightforward to interpret: the tool looks for a match of a property name to its value
- Sequence nodes are interpreted a list of values connected with "OR" conjunction: Channel = "Setup" OR Channel = "System"
- For complex nodes, a logical expression can be considered a compound expression of simpler expressions, starting with the innermost node and going up. The conjunction between inner nodes is "AND". In the example above, the rule is interpreted like this:

Condition
The top-level nodes participate in the final logical expression, which is defined by the "condition" key and a logical expression, for example, "condition: selection and filter".
A rule can also contain the "not" operator, for example, "condition: keywords and not filter".
Modifiers
In addition to conditions on values and logical expressions, you can apply modifiers:
- base64
- startswith
- contains
- endswith
Final expression
Let us take another look at the rule (or more specifically, at the detection node):

This rule will be interpreted as follows:
(Provider_Name starts_with "Microsoft" OR Provider_Name starts_with "Micr")
AND
Computer = "BelkaVirtualDev"
AND
(Channel = "Setup" OR Channel = "System")
Sigma rules in Belkasoft X
It is straightforward to add and execute Sigma rules in Belkasoft X. Sigma rules are defined in the product in a similar way to Yara rules, during advanced analysis options specification:
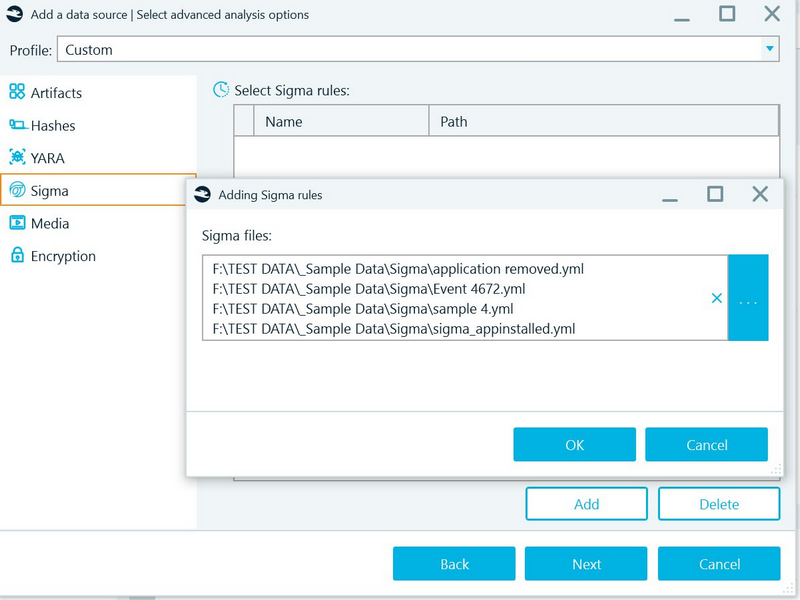
The rules will be triggered only if the analysis of Windows event logs has been selected.
To visualize Sigma rule matches, Belkasoft X has a column called "Sigma rules", which has appeared in the System event logs list accessible from the Structure and Overview panes of the Artifacts window. This column indicates that a specific log was detected by a certain rule, and the name of the matched rule is listed as the value.
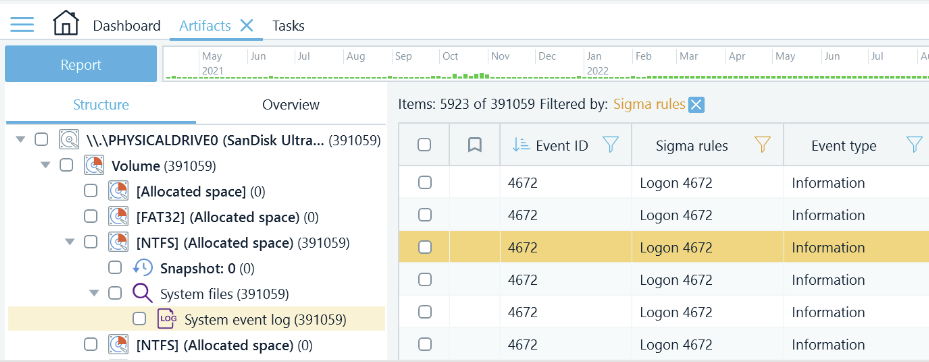
A new Sigma node has been added to the Overview window, which contains logs that have been detected by any of the defined rules, along with information about the rule itself (name, product, category). Thanks to these additional fields, it is easy to filter through the many values and retrieve, for example, all logs detected by a specific rule or logs detected by rules in a certain category.
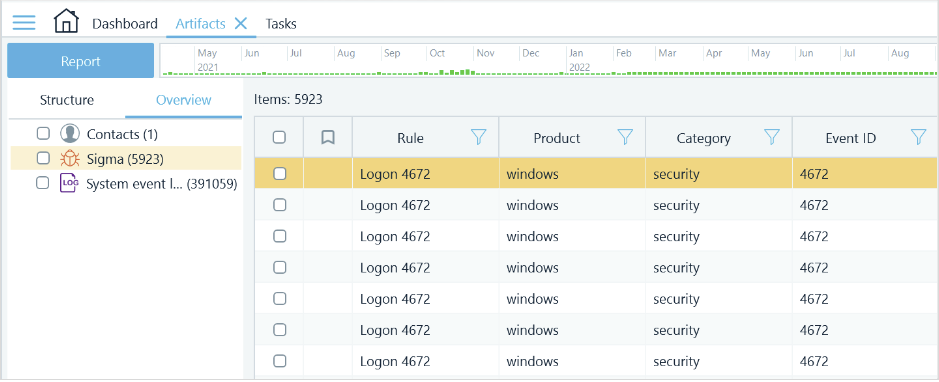
Useful Sigma rules
Below you can find just a few examples of Sigma rules, which you may consider using in your cyber incident investigation:
- Suspicious cmdlets used to enable PSRemoting
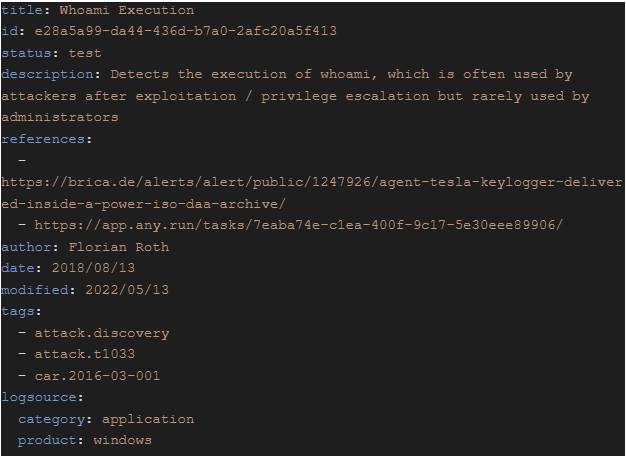
- Execution of whoami, which is often used by attackers after exploitation / privilege escalation but rarely used by administrators
- Application uninstallation
- Events generated by user-mode applications when they call the CveEventWrite API when a known vulnerability is trying to be exploited
- Backup catalog deletions
- Mimikatz keywords in different event logs:
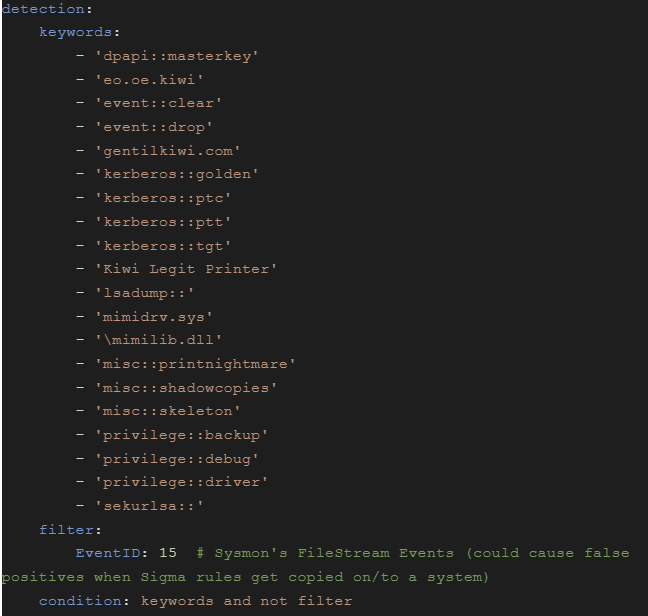
Multiple useful ready-made rules can be found here: https://github.com/SigmaHQ/sigma/tree/master/rules
Availability
Like YARA rules, Sigma rules functionality is included in the X Corporate version of the product.
Conclusion
Sigma rules have become an essential tool for Digital Forensics and Incident Response (DFIR) analysts. With Sigma rules, analysts can easily and efficiently detect and investigate potential security incidents in their organization's digital environment. Sigma rules are flexible and customizable, allowing analysts to tailor them to their specific needs and environments. They also provide a common language for sharing detection techniques and findings among the DFIR community. As the threat landscape continues to evolve, Sigma rules will undoubtedly continue to play a critical role in helping organizations stay ahead of potential security threats.
The X Corporate edition of Belkasoft X has Sigma rules built-in and conveniently applied to event logs found by the tool. Both the Overview window and Event log list allow you to review matches found by the product.