Introduction
Belkasoft X is a comprehensive digital forensic and cyber incident response investigation platform. It features powerful tools and modules that help examiners extract, analyze, and report on digital evidence from a wide range of sources. One of the important features of Belkasoft X is its support for YARA rules.
YARA is an open-source tool designed to assist malware researchers in identifying and classifying malware samples. It has become a popular standard in the industry for automating the process of detecting and categorizing malware. With its ability to search for matching strings or patterns in data, YARA serves as a valuable resource for incident responders and malware researchers, playing a crucial role in threat intelligence efforts. By importing YARA rules into Belkasoft X, examiners can leverage these rules to automatically identify suspicious or malicious activity in their investigations.
In this walkthrough, we will show you how to import YARA rules into Belkasoft X and use them to analyze digital evidence.
What are YARA rules?
YARA performs signature analysis based on formal YARA descriptions—rules. These rules contain indicators of compromise for different types of malware. YARA rules are easy to write and understand, and they have a syntax that resembles the C language. Each rule consists of a set of strings and a boolean expression which determine its logic. Let us see an example:
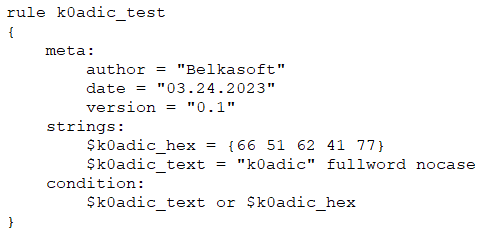
The example rule above instructs YARA to report any file that contains the specified hex or text string. This is just a basic example; more complex and powerful rules can be created by using wildcards, regular expressions, special operators, and many other features explained in the official YARA documentation.
- Official Repository: https://github.com/VirusTotal/yara
- Official Documentation: https://yara.readthedocs.io
How to create a YARA rule
You can find a variety of YARA rules on the Internet, or you can create your own. To create a YARA rule, you need to start by creating a file with a .yar extension. This file can be created and edited in any text editor.
Here is the simplest rule that you can write for YARA, which does nothing:

Rule identifiers
Each rule in YARA begins with the keyword rule followed by a rule identifier (in the example above, it is "empty_rule"). Identifiers must follow the same lexical conventions of the C programming language:
- They can contain any alphanumeric character and the underscore character
- The first character cannot be a digit
- A rule identifiers are case sensitive
- They cannot exceed 128 characters
- YARA keywords cannot be used as identifiers
Multiple rules can be combined into one .yar file, but each rule must have a unique identifier.
Strings definition
The strings definition section is where the strings that will be part of the rule are defined. This section can be omitted if the rule does not rely on any string. Each string has an identifier consisting of a $ character followed by a sequence of alphanumeric characters and underscores. These identifiers can be used in the condition section to refer to the corresponding string. Strings can be defined in text or hexadecimal form, as shown in the following example:
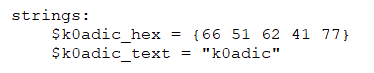
Text strings are enclosed in double quotes just like in the C language. Hex strings are enclosed within the curly braces.
Modifiers
In addition, you can apply modifiers, by appending them at the end of the string definition, in the same line:
- nocase: Indicates that the search should be case-insensitive, allowing for a more relaxed approach when searching for text strings within the malware
- wide: Searches for strings encoded with two bytes per character, commonly used in malware binaries
- fullword: Matches strings that are delimited by non-alphanumeric characters
- xor: Searches for strings encrypted with an XOR function, useful in identifying Command and Control frameworks like Cobalt Strike
- Base64: Searches for scripts encoded with Base64 encoding, a common tactic used by threat actors
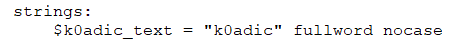
With the nocase modifier, the string above will match K0adic, K0ADIC , and k0Adic. With the fullword modifier, the string will match \k0adic* but will not match \k0adictionary.
Regular expressions
Regular expressions are one of the most powerful features of YARA. They are defined in the same way as text strings but enclosed in forward slashes instead of double quotes, like in the Perl programming language.
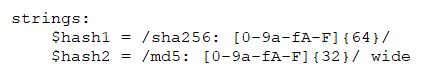
Regular expressions can be also followed by modifiers. The expressions above will look for SHA-256 and MD5 hash values, preceded by the prefixes "sha256:" and "md5:" respectively.
Condition section
The condition section is where the logic of the rule resides, and this section is always required. The condition section must contain a Boolean expression that determines under which circumstances a file or process complies with the rule. Generally, the condition will refer to previously defined strings by using their identifiers. In this context, the string identifier acts as a Boolean variable that evaluates to true if the string was found in the file or a memory process, or false if otherwise.
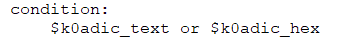
Conditions can contain the typical Boolean operators and, or, and not, as well as relational operators >=, <=, < , >, ==, and !=. You can also use arithmetic operators such as +, -, *, , and % in numeric expressions, as well as bitwise operators such as &, |, <<, >>, ~, and ^. The keywords any, all, and none can also be used.

The condition above means the same as the previous one—at least one of the strings must be present in the file.
More advanced options are available as well, for example, you can check if the string is at a specific offset, how many times the string appears, and so on.
Metadata
Besides the string definition and condition sections, rules can also have an optional metadata section where you can put additional information about your rule. The metadata section is defined with the keyword meta and contains identifier/value pairs like in the following example:
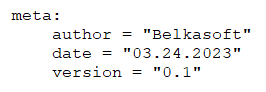
As can be seen in the example, metadata identifiers are always followed by the "equals" sign and the value assigned to them. The assigned values can be strings (valid UTF8 only), integers, or one of the Boolean values true or false. Note that identifier/value pairs defined in the metadata section cannot be used in the condition section, their only purpose is to store additional information about the rule.
The fields in the metadata section can vary depending on the analyst's preference but typically include author, incident, date, last_modified, actor, category, family, description, MD5, and SHA256.
Final expression
Let us take a look at the rule:

This rule will be interpreted as follows: if a file or a memory process contains either text or hex string above, it will be detected by this rule.
Let us consider another example:
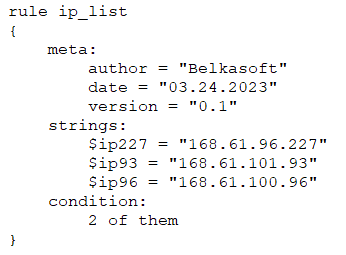
This rule will be interpreted as follows: if a file or a memory process contains at least two of the listed IP addresses, it will be detected by this rule.
Useful YARA rules
Below you can find just a few examples of YARA rules usage scenarios:
- Detecting PEs with PDB paths that have unique, unusual, or overtly malicious-looking keywords, terms, or other features
- Identifying crypto routines
- Discovering injection / hooking functionality
- Detecting malicious documents targeting Microsoft Office format
- Identifying anti-RE malware techniques
- Detection for exploits, infostealers, ransomware, trojans, and viruses
- Detection for packers, mimikatz, and specific malware
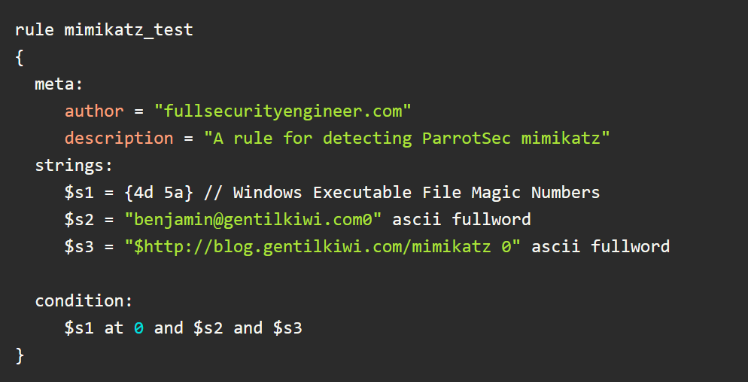
Here is a test rule crafted to detect the mimikatz from ParrotSec/mimikatz, which is a well-known tool used by hackers to dump credentials or Kerberos tickets from Windows servers:
A curated list of YARA rules, tools, and people can be found here: https://github.com/InQuest/awesome-yara.
YARA rules in Belkasoft X
Adding and executing YARA rules in Belkasoft X is very easy. YARA rules are defined in the product whilst adding a data source, when specifying advanced analysis options:
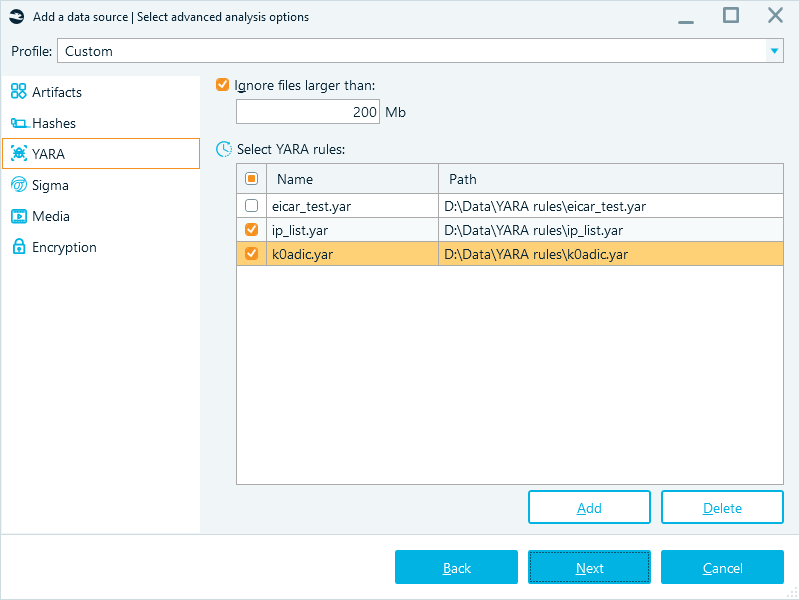
On the YARA tab, you can specify that files should be skipped if they exceed a certain size:
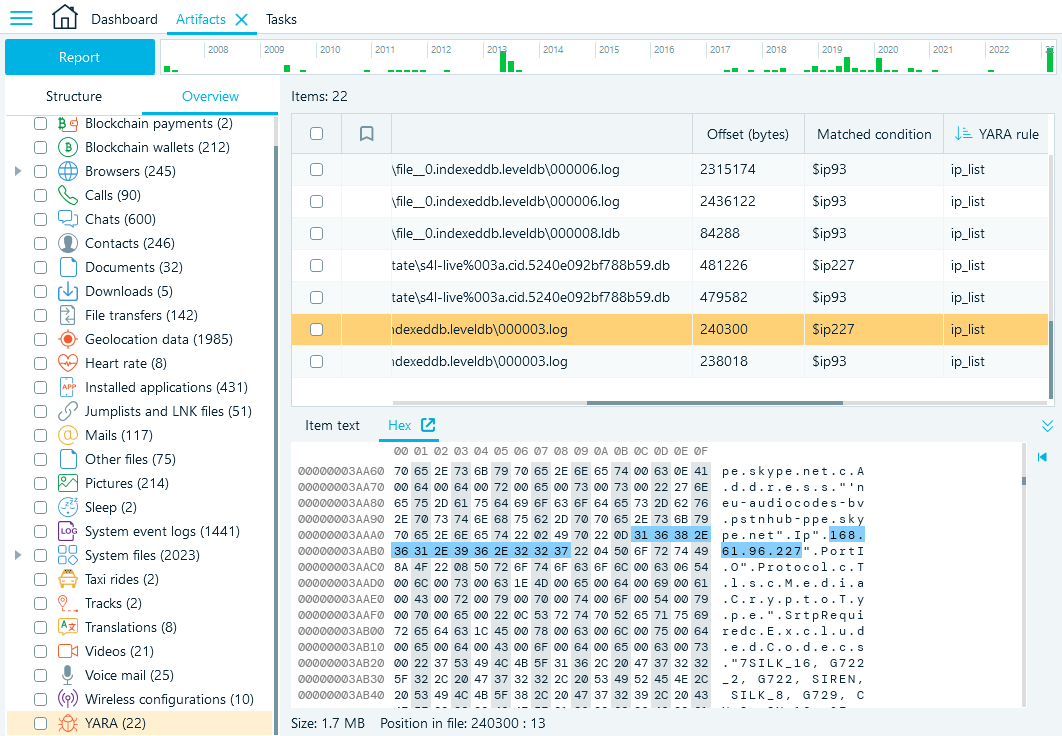
To visualize YARA rule matches, Belkasoft X shows the YARA node on the Overview tab in the Artifacts window. This node contains information about files that have been detected by any of the defined rules, along with the offset and matched conditions.
Availability
YARA rules functionality is included in the X Corporate version of Belkasoft X product.
Conclusion
YARA can be used for various purposes, including regular threat detection, threat hunting, and threat intelligence. These functions make YARA a powerful tool for securing computer systems and networks from malware attacks.
The use of classification techniques brings numerous advantages, including improved control and advanced detection. Other benefits include reduced costs in reverse engineering through the recognition of patterns in malware samples and enhanced threat intelligence and community information sharing.
The X Corporate edition of Belkasoft X has YARA rules built-in and conveniently applied to a case. The Overview window allows you to review matches found by the product, and all the relevant information can be included in the final report.
