Windows Registry: Structure, Forensic Challenges, and Acquisition
The Windows registry serves as an important source of information for digital forensic investigations. It records system configurations, application data, and user activity, offering investigators valuable insights about a system’s past and present states.
The registry is central to many investigative workflows, whether you are identifying connected devices, tracing user activity, or uncovering persistence mechanisms used by malicious software. However, challenges such as protected keys, structural complexity, and anti-forensic techniques can complicate registry analysis.
In this article, we will explore:
- Structure and specifics of the Windows registry
- Challenges in Windows registry forensics
- Methods of registry acquisition
Read on to gain a clear understanding of the Windows registry and practical strategies for analyzing it.
Structure and specifics of the Windows registry
The Windows registry is a hierarchical database that stores configuration settings and options for the Microsoft Windows operating system and installed applications. While many registry features have evolved across versions, its core structure and purpose have remained largely unchanged since Windows XP.
Windows provides access to registry records through the Registry Editor application (also known as RegEdit). It displays the records organized as an hierarchy, with three primary elements:
- Root Keys: Act as containers for subkeys and/or values. Technically, root keys are predefined handles for specific keys kept in memory or stored in hive files in the local filesystem.
- Keys and Subkeys: Each root key contains several keys, which may contain further subkeys, creating a tree-like structure. Subkeys function similarly to folders in a file system, organizing related records into groups.
- Values: The actual data stored in the registry, typically in string, binary, or numeric formats. Values store the parameters and configurations that control system and application behavior.
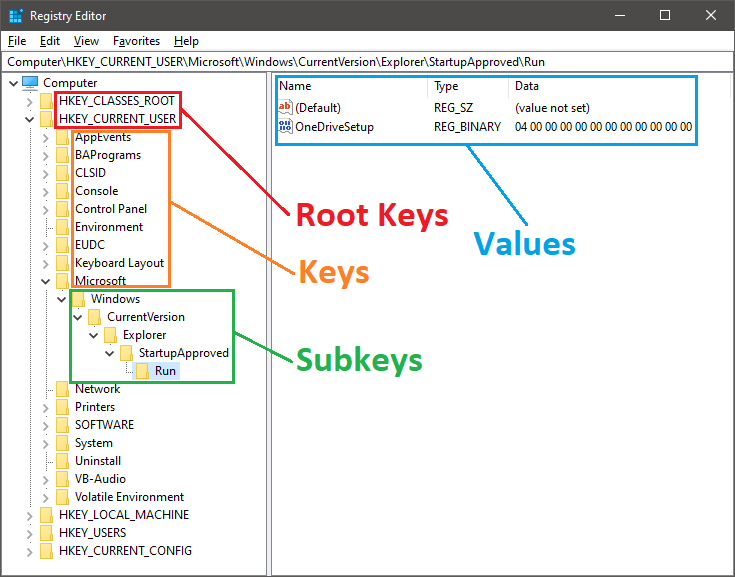
Registry structure in Windows Registry Editor
Registry Editor provides the interface to navigate and adjust registry entries. However, some of the keys and subkeys that affect system operation cannot be viewed or edited. When conducting a DFIR investigation, you typically work directly with the registry storage files, and it is useful to understand the correlations between those files and the record structure displayed in RegEdit.
How Windows stores registry data
From a storage perspective, the registry is divided into several physical hive files accompanied by a set of backups. The following are the key hive file locations, the associated registry root keys, and their forensic value:
- SAM (%SystemRoot%\System32\Config\SAM): Stores user account information, including SID-to-username mappings and authentication security details. Analyzing SAM helps investigators examine user accounts and potential credential-based attacks. This file stores data of the HKEY_LOCAL_MACHINE\SAM key in RegEdit.
- SYSTEM (%SystemRoot%\System32\Config\SYSTEM): Contains system-related configurations, including records of connected USB devices and mounted drives. These records can be found in HKEY_LOCAL_MACHINE\SYSTEM via RegEdit.
- SECURITY (%SystemRoot%\System32\Config\SECURITY): Contains local security policy settings, including user rights assignments and security descriptors. The related RegEdit key is HKEY_LOCAL_MACHINE\SECURITY.
- SOFTWARE (%SystemRoot%\System32\Config\SOFTWARE): Holds details about installed applications and their configurations. You can find them under the HKEY_LOCAL_MACHINE\SOFTWARE key in RegEdit. SOFTWARE helps identify installed programs, persistence mechanisms, and potentially malicious software.
- NTUSER.DAT (%UserProfile%\NTUSER.DAT): Tracks user-specific settings and recently accessed documents. It can be handy for reconstructing user activity and application usage.
- USRCLASS.DAT (%LocalAppData%\Microsoft\Windows\UsrClass.dat): Captures Shellbag data, which tracks folder navigation and file access patterns, providing insights into user behavior. Shellbag data appears in multiple registry locations due to how Windows manages user-specific and system-wide configurations. If you are working on a live system, the registry presents the same information under HKEY_CURRENT_USER or HKEY_USERS.
Root keys
Now that we have figured out how the registry is stored on your hard drive, let us review registry root keys and their value.
HKEY_CLASSES_ROOT (HKCR)
HKCR contains information about file associations, registered applications, and Object Linking and Embedding (OLE) object class IDs. For example, it determines which application is used to open .txt files. Within the registry structure, HKCR is a merged view of the other two keys:
- HKEY_LOCAL_MACHINE\SOFTWARE\Classes (system-wide settings)
- HKEY_CURRENT_USER\SOFTWARE\Classes (user-specific settings)
During a session, the keys under HKCU\SOFTWARE\Classes are overridden with user-specific settings from NTUSER.DAT. These overrides are only valid for the specific user and do not affect the SYSTEM hive file (as mentioned before, HKEY_CURRENT_USER is the subset of HKEY_USERS that corresponds to the active user's profile).
HKEY_USERS (HKU) and HKEY_CURRENT_USER (HKCU)
HKU stores user profile data, such as desktop preferences and application configurations (for example, theme preferences and Explorer settings) for each user who has logged in to the system. As we mentioned earlier, HKCU in RegEdit shows the subkey of this hive, corresponding to the active user.
HKCU is dynamically loaded at login from the NTUSER.DAT file, located in %UserProfile%. Any changes to HKCU are written to NTUSER.DAT during the user’s session.
HKEY_LOCAL_MACHINE (HKLM)
Holds configuration information specific to the computer, including hardware configurations, installed software, and security policies. HKLM applies to all users and is composed of the following physical hives:
- SYSTEM
- SOFTWARE
- SECURITY
- SAM
HKEY_CURRENT_CONFIG (HKCC)
Links to the active hardware profile settings detailing system device configurations relevant to the current session. Its content is dynamically derived from the SYSTEM hive and does not exist as a separate file on disk.
Control sets
One more notable feature within the registry is the system's ability to maintain historical snapshots of its configuration, known as Control Sets. Control Sets are registry snapshots of the computer's settings.
The HKEY_LOCAL_MACHINE\SYSTEM key includes several control set subkeys. They store information about services, drivers, and other necessary settings for booting. Windows maintains multiple copies, like ControlSet001 and ControlSet002, and so forth, in case an issue arises and the system needs to revert to a previously functioning state.
CurrentControlSet is not an independent set but a symbolic link to the active control set used during the current session. Any changes made to CurrentControlSet affect the underlying snapshot it is linked to.
Control sets can provide valuable clues about system behavior. By analyzing them, you can:
- Detect recovery attempts: If Windows had a problem, it might have switched to an older control set. The Select (HKLM\SYSTEM\Select) subkey within the SYSTEM hive holds this information.
- Identify suspicious changes: Spot unusual modifications, such as unexpected driver installations or service alterations that could signal malware activity. For example, entries in the Services subkey pointing to unusual locations might be a red flag.
Registry values
Values are parameters or settings that define how the system and applications operate. Like files within folders, each value is associated with a specific subkey.
Each registry value consists of three key components:
- Name: Identifies the purpose or context of the value. Displayed as "(Default)" if unspecified.
- Data Type: Specifies the format in which the data is stored (for example, strings, integers, binary data).
- Data: The actual information stored (for example, a file path, a numerical value, or a configuration setting).
Here are the most common registry value types:
- REG_SZ: A text-based string value. Typically used to store user login names, application paths, or other textual settings.
- REG_DWORD: A 32-bit integer that represents numerical or Boolean settings. Often used for system configurations, such as auto-login status, service states, or feature toggles.
- REG_BINARY: Raw binary data. This format stores various information, including device configurations, execution history (for instance, UserAssist tracking EXE file usage with timestamps), and encryption keys or cryptography-related data.
- REG_MULTI_SZ: A multi-string value for storing multiple related text strings. Usually lists multiple paths, settings, or related strings.
- REG_EXPAND_SZ: A string value that includes expandable variables. Usually stores paths or commands with environment variables.
Challenges in Windows registry forensics
When performing forensic analysis of the Windows registry, you should account for a number of intricacies that may impact your investigation:
- Accessing protected keys: Some sensitive areas, such as HKEY_LOCAL_MACHINE\SAM and SECURITY, are heavily restricted by the operating system and cannot be accessed directly while Windows is running. These hives are constantly in use, preventing standard copying or direct examination. You typically need to use special tools and techniques, such as offline extraction or elevation of privileges, to access this information safely.
- Handling volatile data: Registry entries can change quickly, which makes it difficult to get an accurate copy. Preserving the integrity of the data requires using write-blocking mechanisms and thoroughly documenting actions.
- Data and structure mismatch: The physical storage of the registry on disk (in hive files) does not align with its representation in the operating system, often leading to confusion in registry interpretation.
- Countering anti-forensic techniques: Attackers can attempt to alter or delete registry entries containing their activity traces. Advanced digital forensics tools can help recover modified or deleted data, though expertise is needed to identify tampering effectively.
- Navigating complex systems: It can be challenging to navigate through enormous amounts of registry data—especially on old systems, which keep a lot of outdated records.
- Ensuring data accuracy: Registry corruption and parsing errors can mislead investigations. Corroborating registry findings with other evidence, such as event logs and file metadata, ensures a reliable narrative and minimizes misinterpretation.
Specialized digital forensics software like Belkasoft X simplifies investigations by supporting the acquisition and automatic extraction of critical registry data. It offers a structured framework for in-depth analysis and correlation of registry data with other Windows application and system artifacts.
Methods of registry acquisition
Acquiring Windows registry hive files requires careful consideration of forensic soundness, especially on live systems—where registry files are actively used and protected—and file locks can create complications. Several methods exist, each with its own strengths and limitations:
- Disk imaging
Disk imaging is the most forensically sound method, whether physical (bit-by-bit copy of the entire drive) or logical (capturing the file system structure and content). Belkasoft X facilitates this process, allowing acquisition in formats like RAW or E01. This approach minimizes the risk of data corruption.
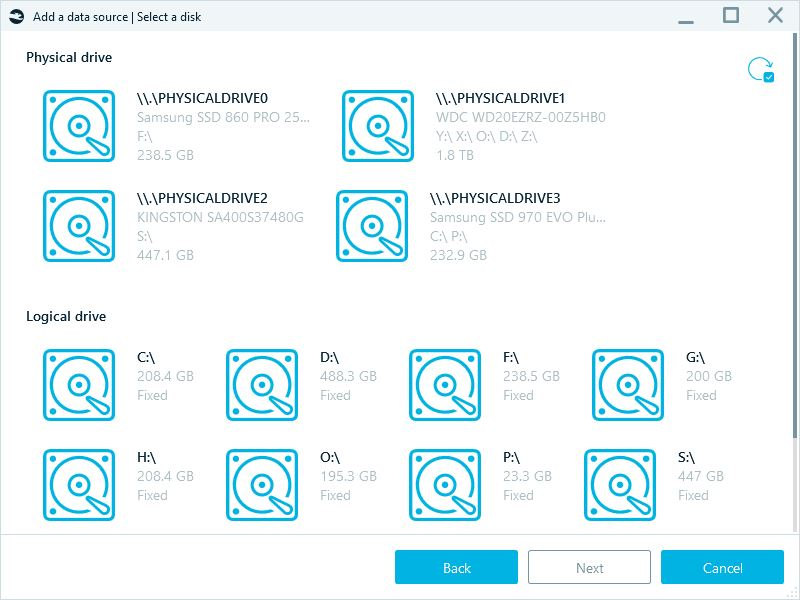
Belkasoft X allows you to acquire physical or logical drives
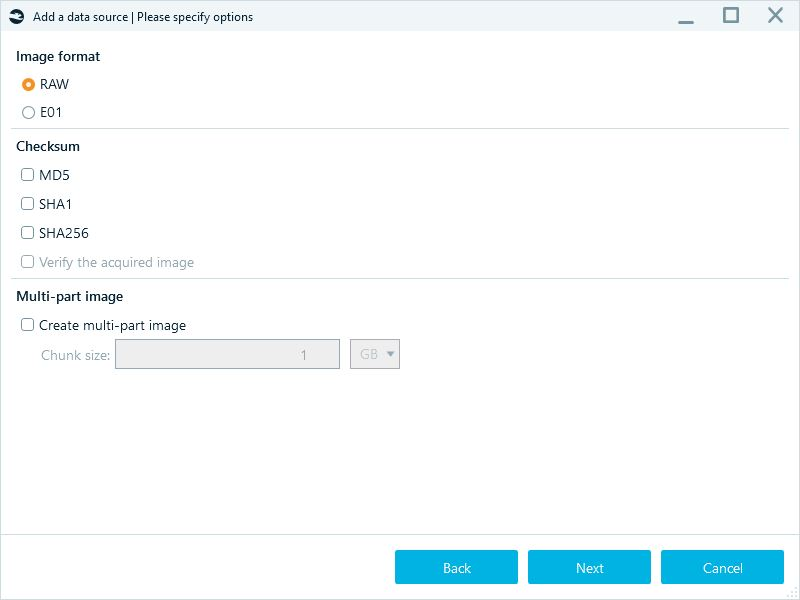
Disk imaging options in Belkasoft X
- Volume Shadow Copy Service (VSS) acquisition
When enabled, VSS creates file system snapshots, including registry hives, even on an active system. While not as comprehensive as full disk imaging, VSS acquisition enables access to locked registry hives. Forensic tools can leverage these snapshots to retrieve registry data that would otherwise be locked. However, VSS snapshots reflect the system state at the moment of capture and may not contain the latest registry changes—particularly on highly active systems, where data is frequently modified. - Copying registry hives
Investigators can locate and manually copy hive files from the computer’s file system. However, this method is not forensically sound, as the registry files can change after they are copied, and sometimes those files are locked by the system. - Exporting with reg save command
To access the hives locked by the system, you can use the built-in reg save command as a workaround. For example, the below command will save the SAM hive file, otherwise locked by the system:reg.exe save HKLM\SAM C:\TEMP\SAM
- Exporting with RegEdit
Registry Editor lets you export hives or keys to a .reg file. This method is the least forensically sound due to logical acquisition limitations, such as potential discrepancies in exported data (for example, keys or values that may not be fully captured if the registry is actively being used or modified) and metadata loss (such as the loss of original timestamps or other attributes when exported). Additionally, it lacks data integrity verification, which makes it vulnerable to tampering or corruption. Use it only when other options are unavailable.
Note: Another valuable approach is to capture RAM. Since active registry data is stored in memory, it can reveal even more about the registry state. Belkasoft RAM Capturer can help you create a full dump of RAM as it operates in the kernel mode and works around anti-debugging and anti-dumping systems.
Whenever possible, disk imaging with a write blocker is the gold standard because it preserves all data, including unallocated space and deleted files, without modifying the original media. However, when full disk imaging is not feasible, alternative methods like VSS snapshots or targeted forensic acquisition can be used, though they carry risks of system changes. Specialized forensic tools are usually better at handling live system acquisitions and can provide more effective registry analysis methods.
Conclusion
The Windows registry is a valuable asset in forensic investigations that reveals details about system configurations, user activities, and application behaviors. By comprehending its structure, addressing its challenges, and utilizing specialized digital forensics tools such as Belkasoft X, you can transform the registry into a significant source of evidence.
Whether you are dealing with offline images or examining a live system, the registry holds crucial artifacts that can provide significant insights for your investigation. Implementing the right methodologies and best practices help effectively extract, analyze, and interpret this data.

