Belkasoft CTF 7: Write-up
Belkasofts CTF7 began on 25 July, 2025 and took 48 hours. You can find the details, tasks, and scoreboard here: https://belkasoft.com/belkactf7/. The challenge was prepared by the Belkasoft and TODO: security teams.
Below is Belkasoft's official CTF write-up. And here is a plot twist: in our solutions, the extraterrestrial intelligence meets the power of the Earth's artificial one because as we went tackling the challs, we turned to BelkaGPT to help us find some of the answers.
Did you like this CTF? Share your feedback on your social accounts using the #BelkaCTF tag.
The Plot
The CTF kicks off with global chaos: airports, hospitals, and major organizations are brought to their knees by sudden BSODs. One air traffic control computer shows signs of malware, flashing ominous messages urging people to hit the streets.
Your task? Dig into a RAM dump, uncover the malware, and trace the operator. But the evidence takes a strange turn—the suspect was once a journalist, now seemingly replaced by… something alien.
Will your digital forensics and incident response skills be enough to reveal the truth and avert the Earth’s destruction?

1. Whoami (Baby)
Question
What is the username and hostname of the imaged machine?
Solution
- Open Belkasoft X and configure Volatility integration in Settings → Third-Party:
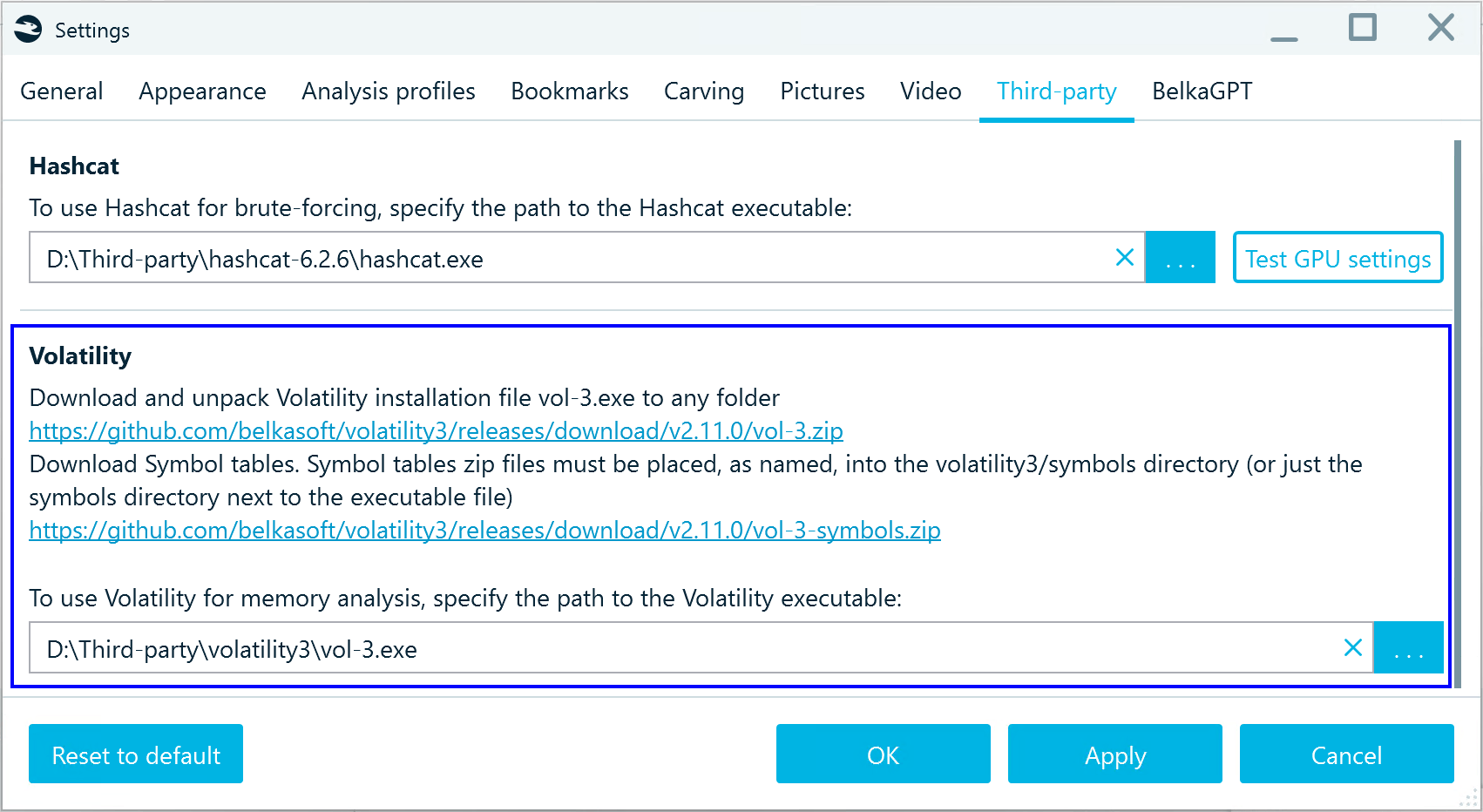
- Analyze the memory dump with the following options enabled:
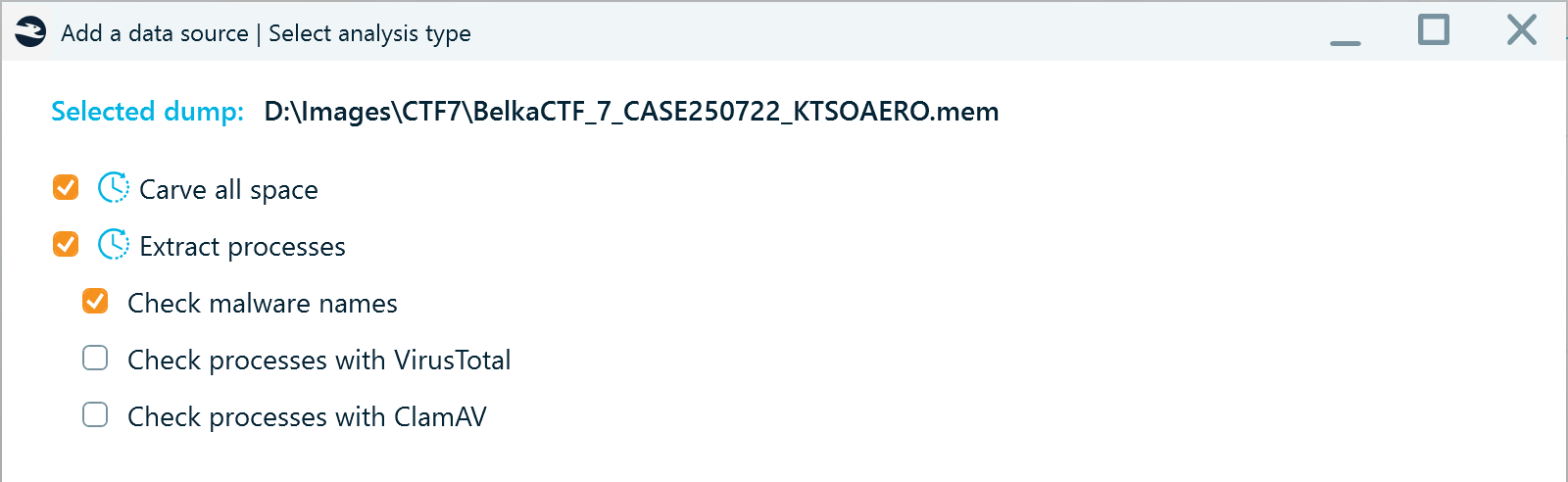
- Filter all artifacts by "user", and you will be able to locate the path to the Windows user folder under LNK files:
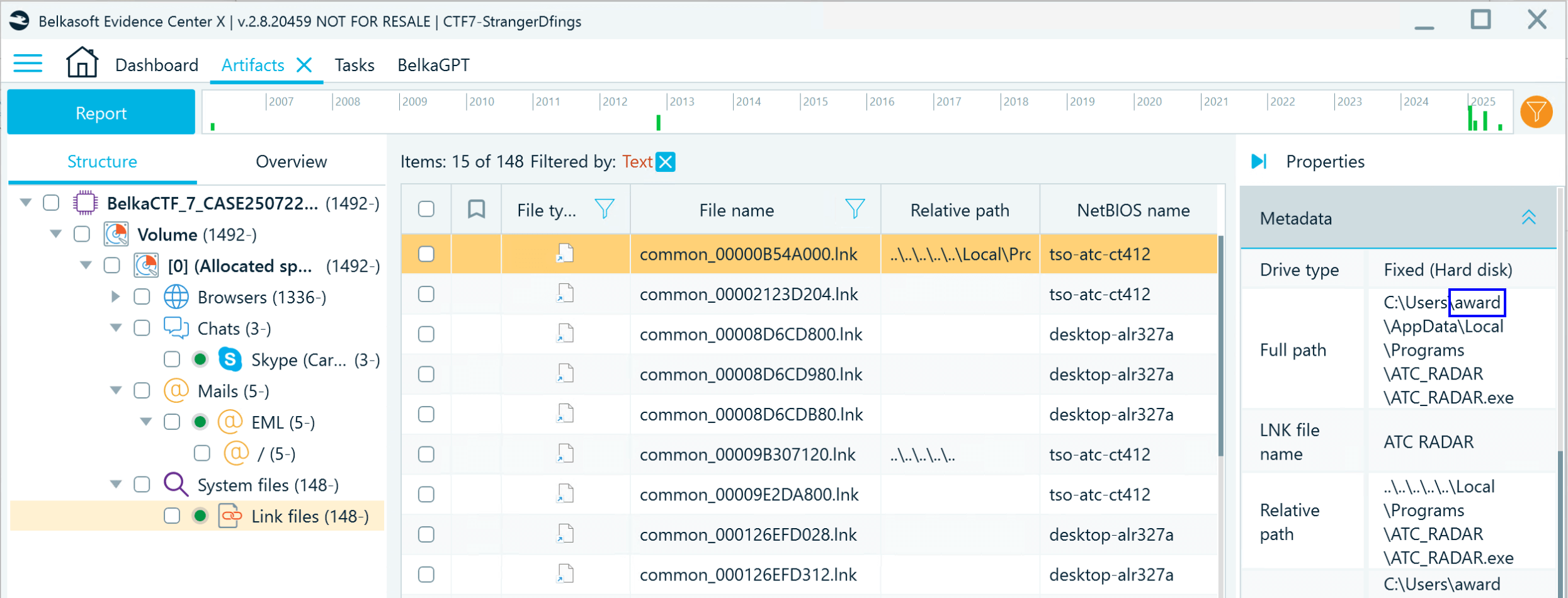
- The NetBIOS name column includes two computer names. To pinpoint the correct one, clear the filter and check the discovered System event logs. All of them list the same computer name:
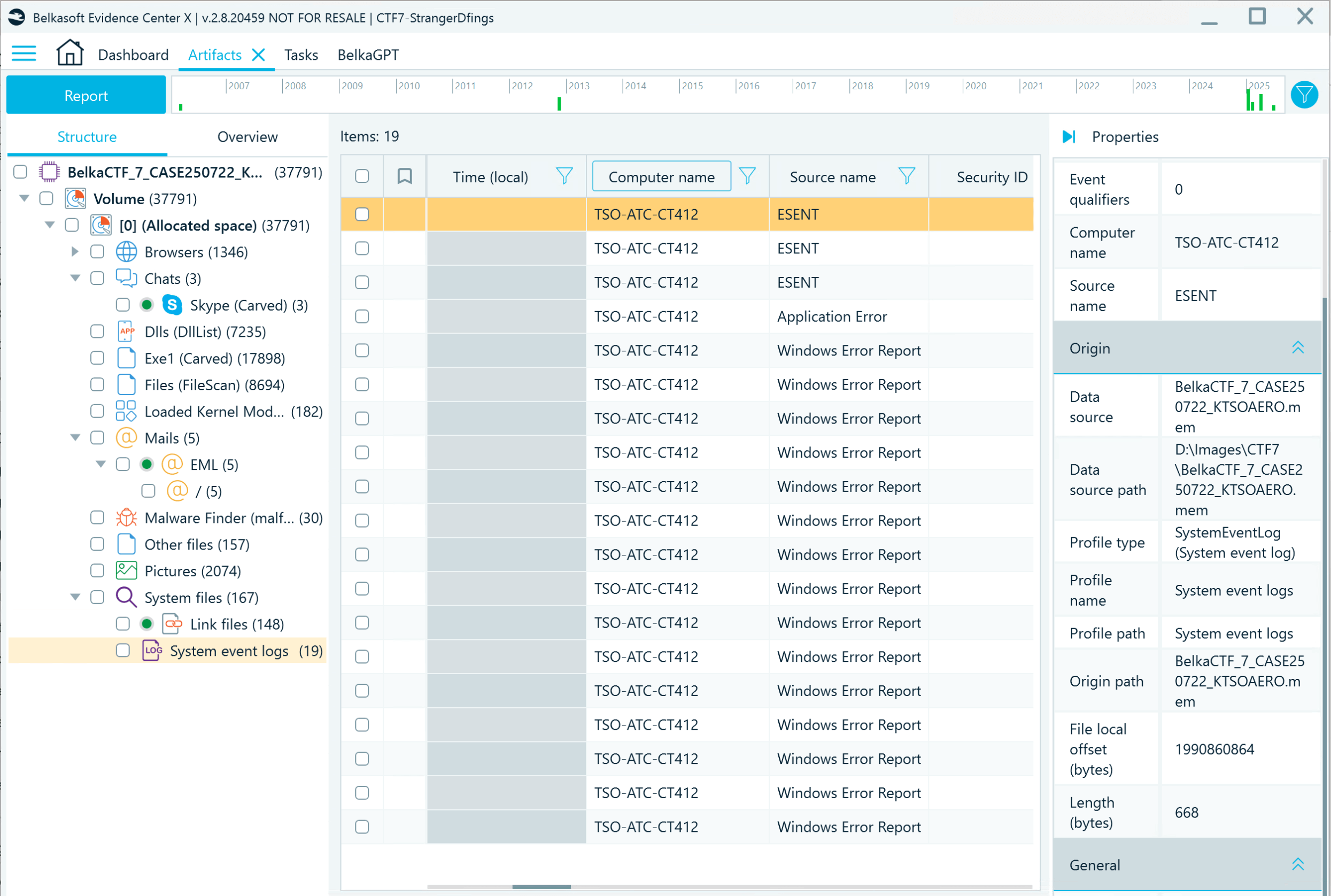
Flag
award@TSO-ATC-CT412
2. Locker (Warmup)
Question
What is the malware executable file name?
Solution
- One of the most popular attack vectors is a phishing email. Go to the Mails node and inspect the available items. You can quickly spot the suspicious email mentioning "epxlorer.exe" which is obviously trying to disguise itself as "explorer.exe":
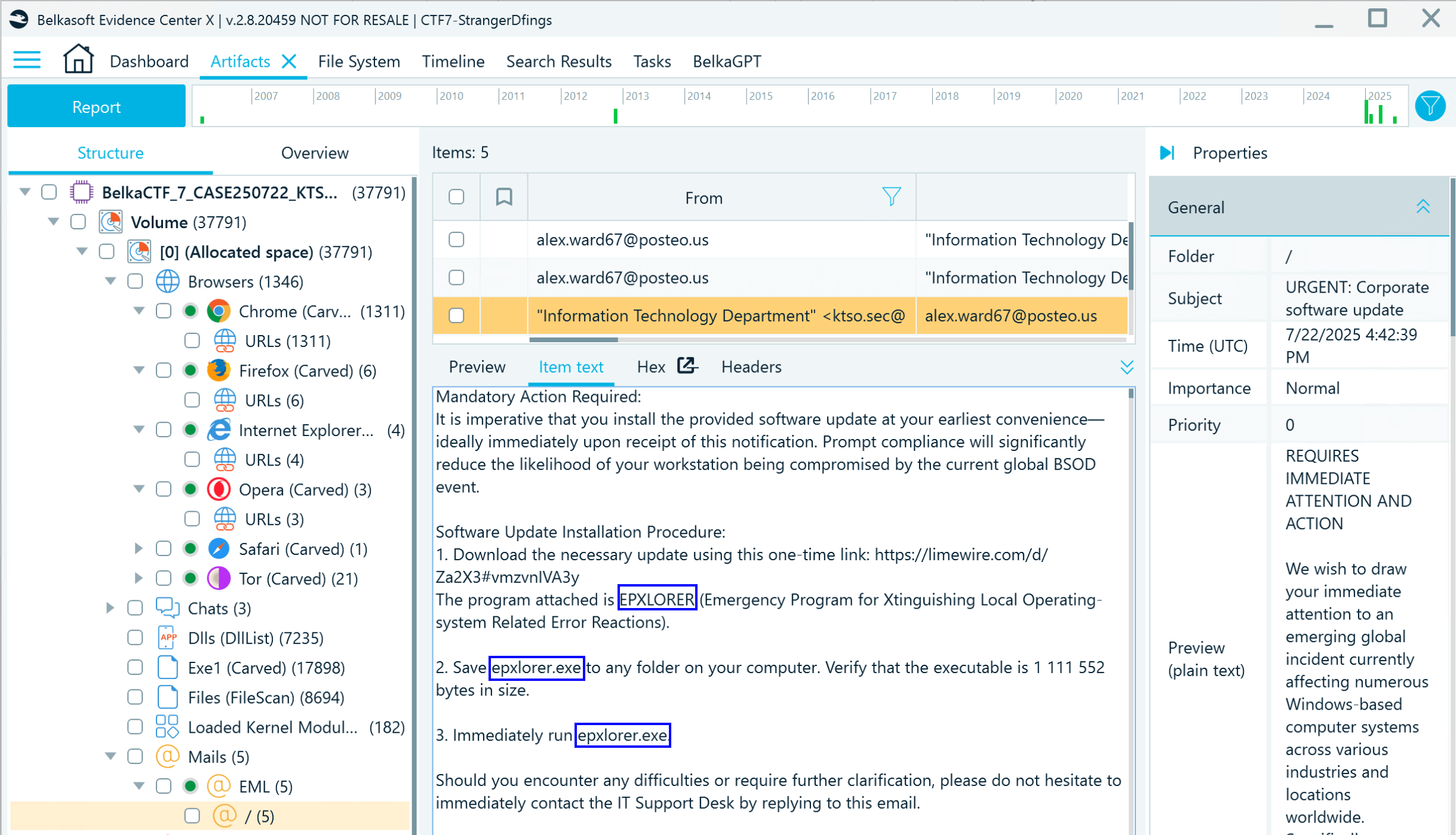
- You can also spot this executable file in the Malware Finder node, which lists the processes detected by the Volatility malfind plugin:
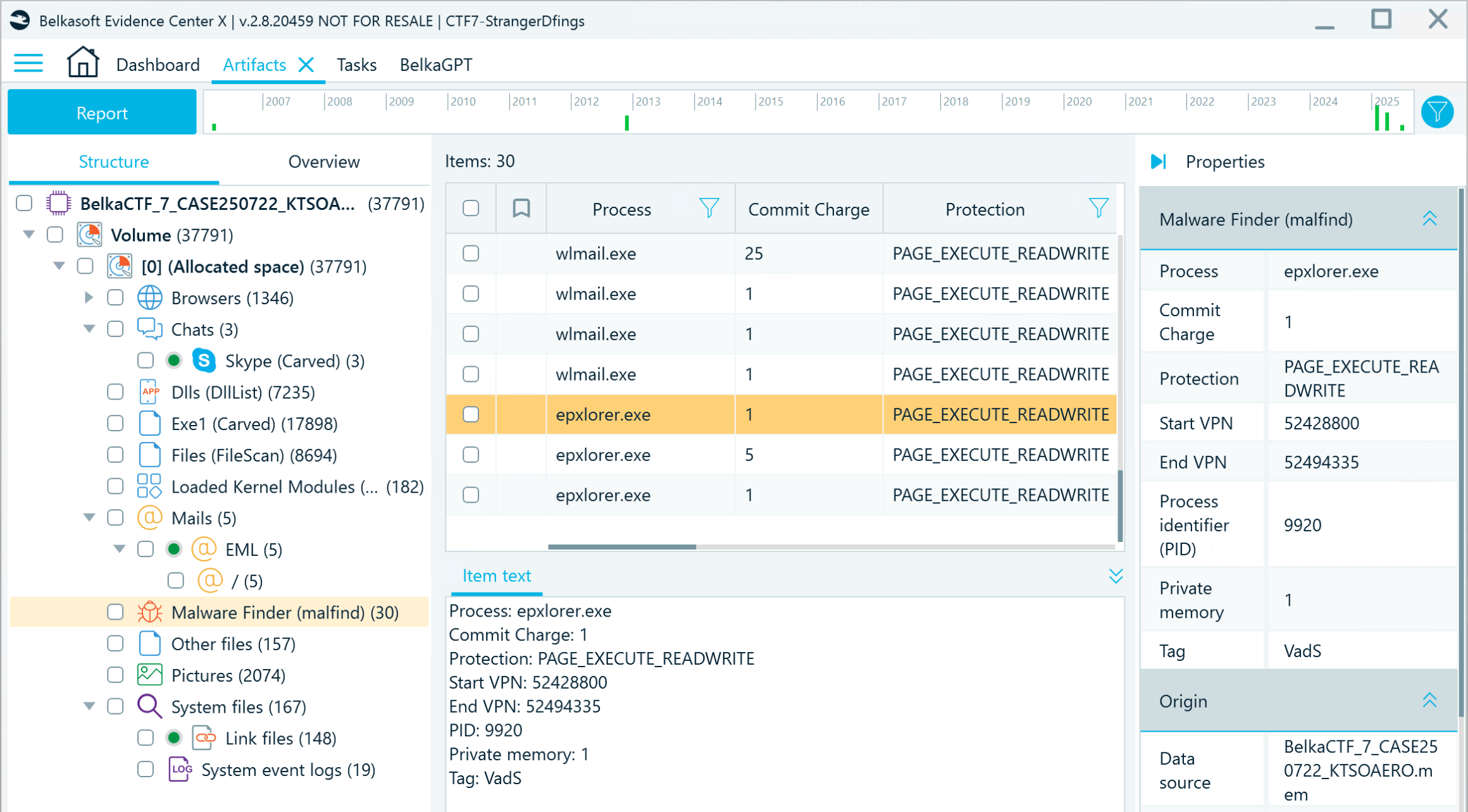
Flag
epxlorer.exe
3. Sample (Tricky)
Question
What is the MD5 hash of the malware running on the machine?
Solution
- Navigate to the Files node, which includes the items detected by the Volatility FileScan plugin, and filter it by "epxlorer.exe":
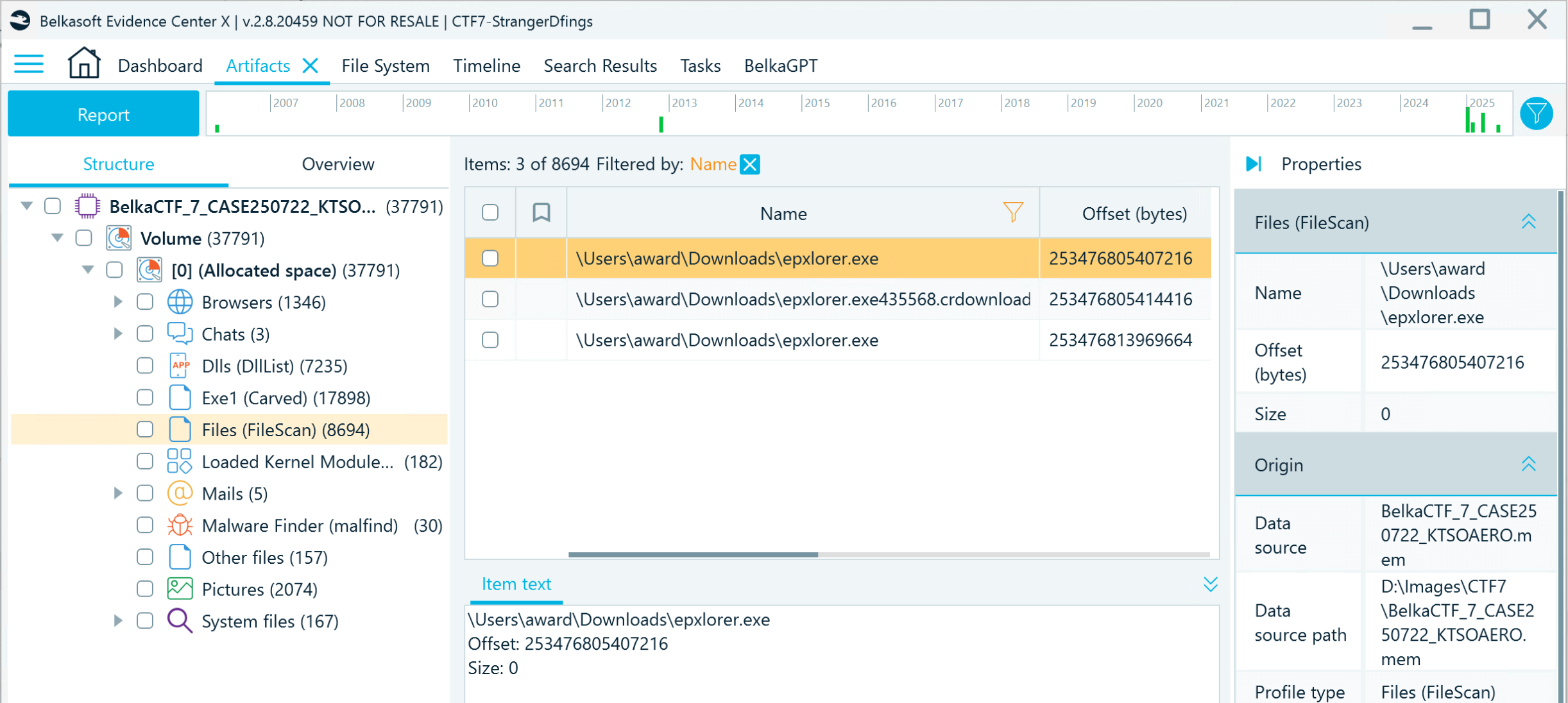
- Now that you know the file's offset, you can extract it from the dump using the following volatility command:
vol.py -f BelkaCTF_7_CASE250722_KTSOAERO.mem windows.dumpfiles --virtaddr 253476805407216
- You will get two files of different sizes.
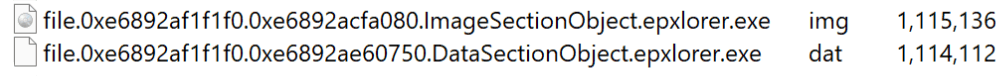
Volatility does not care about making the file size correct and often appends extra blocks of zeros at the end, while the exact amount of zeros may be different. Before calculating the hash, you must find out the exact file size to trim it properly.
- Luckily, the phishing email also mentioned the exact size of the malware executable:
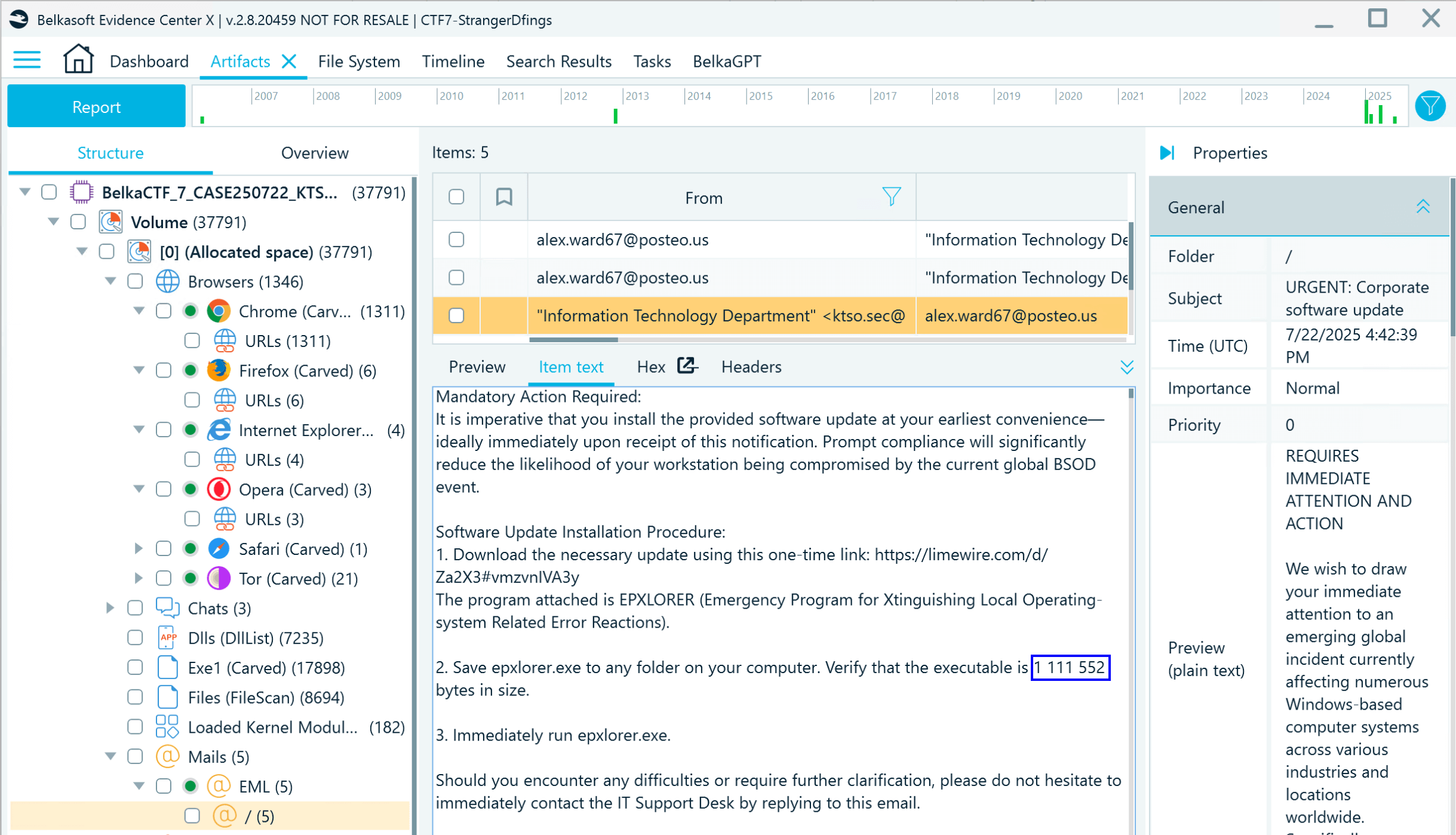
- Open the epxlorer.exe file dump extracted by Volatility with Belkasoft X's Hex Viewer. Right-click the code, go to Selection → Select block, and specify the offset:
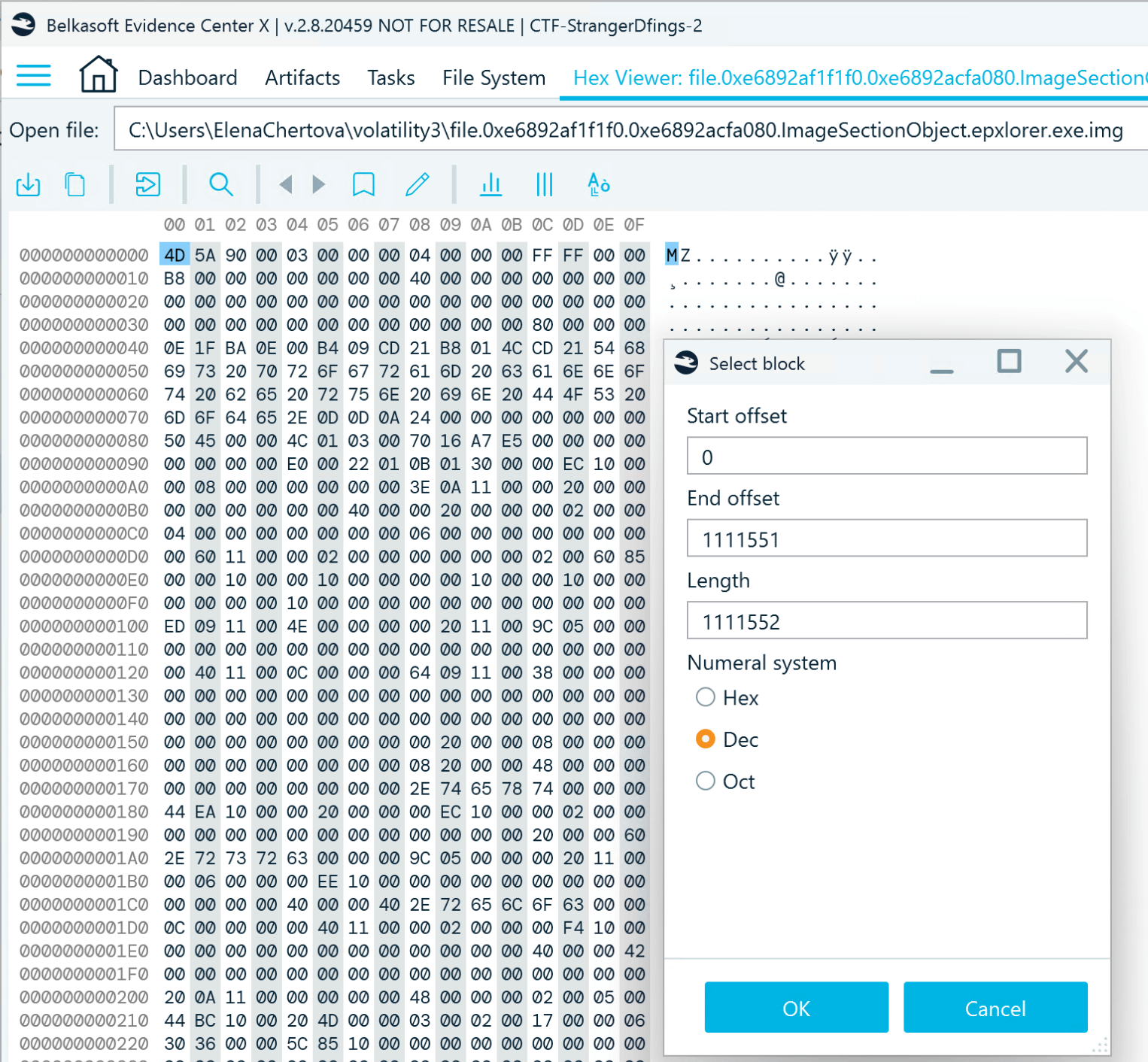
- After selecting the block, click the Save selection button in the top left corner of the viewer.
- Calculate the hash of the resulting file.
Flag
75ea94b54420c39dcd3d8ce574ba9d34
4. Infection (Warmup)
Question
What was the email address of the person spreading the malware?
Solution
Assuming you have already found the phishing email, you can also easily locate the address used to send it:
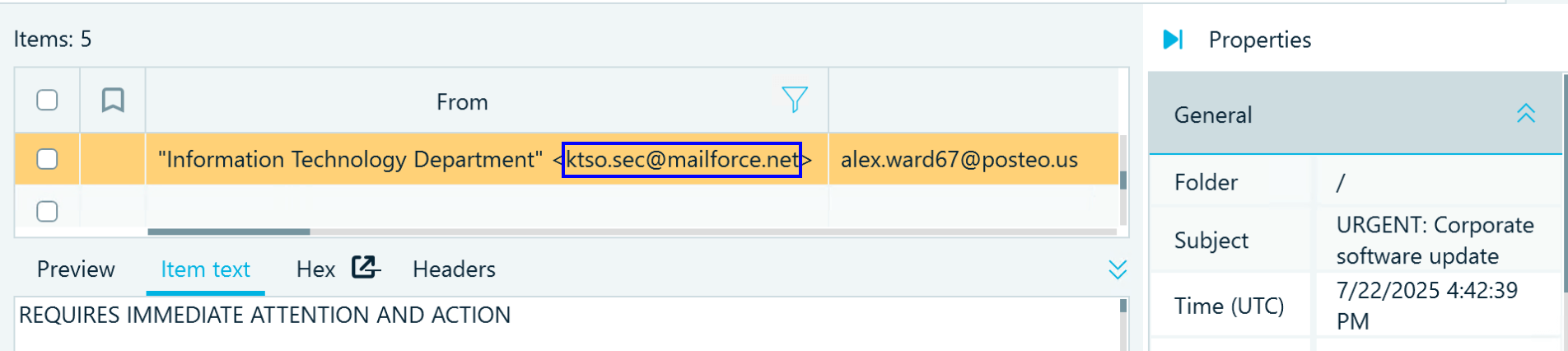
Flag
ktso.sec@mailforce.net
5. Command and Control (Baby)
Question
What is the intruder-hosted Telegram API server used by the malware?
Solution
- After extracting the malware sample in challenge #3, you can analyze the executable more thoroughly. First, let us check what file type it is.
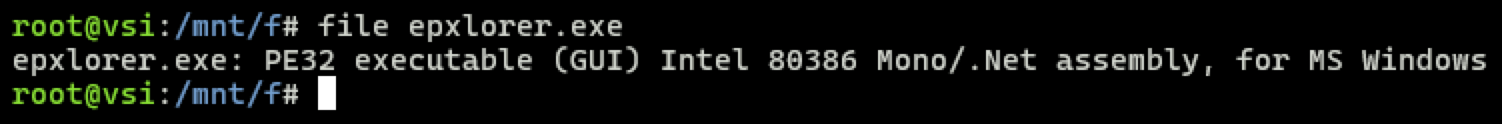
The malware is a "Mono/.Net assembly," and .NET compiles into bytecode easily decompilable back to almost original source code. There are numerous tools that can help with this task, one of the most prominent being dnSpy.
- Load epxlorer.exe into dnSpy and analyze its internals.
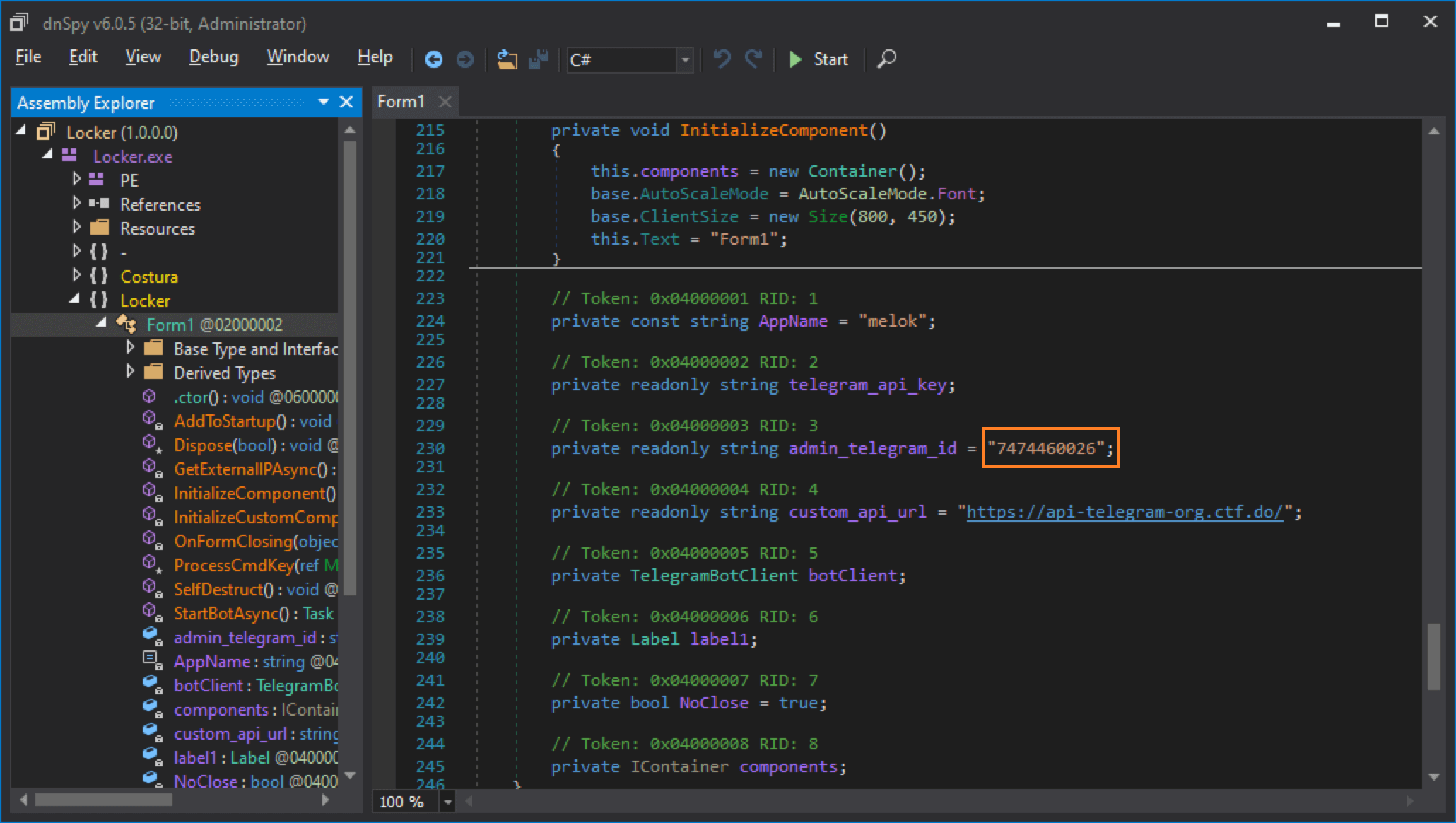
- By inspecting Form1 source code, you can locate the malware operator's API endpoint in the custom_api_url variable.
Flag
https://api-telegram-org.ctf.do/
6. API Key (Tricky)
Question
What is the Telegram Bot API key hard-coded into the malware executable?
Solution
- While the previous challenge could be solved by just going through strings contained in the malware binary, this one is trickier: the Telegram bot token used by the sample is encrypted at rest. Here is the algorithm at the top of Form1 decompiled source code:
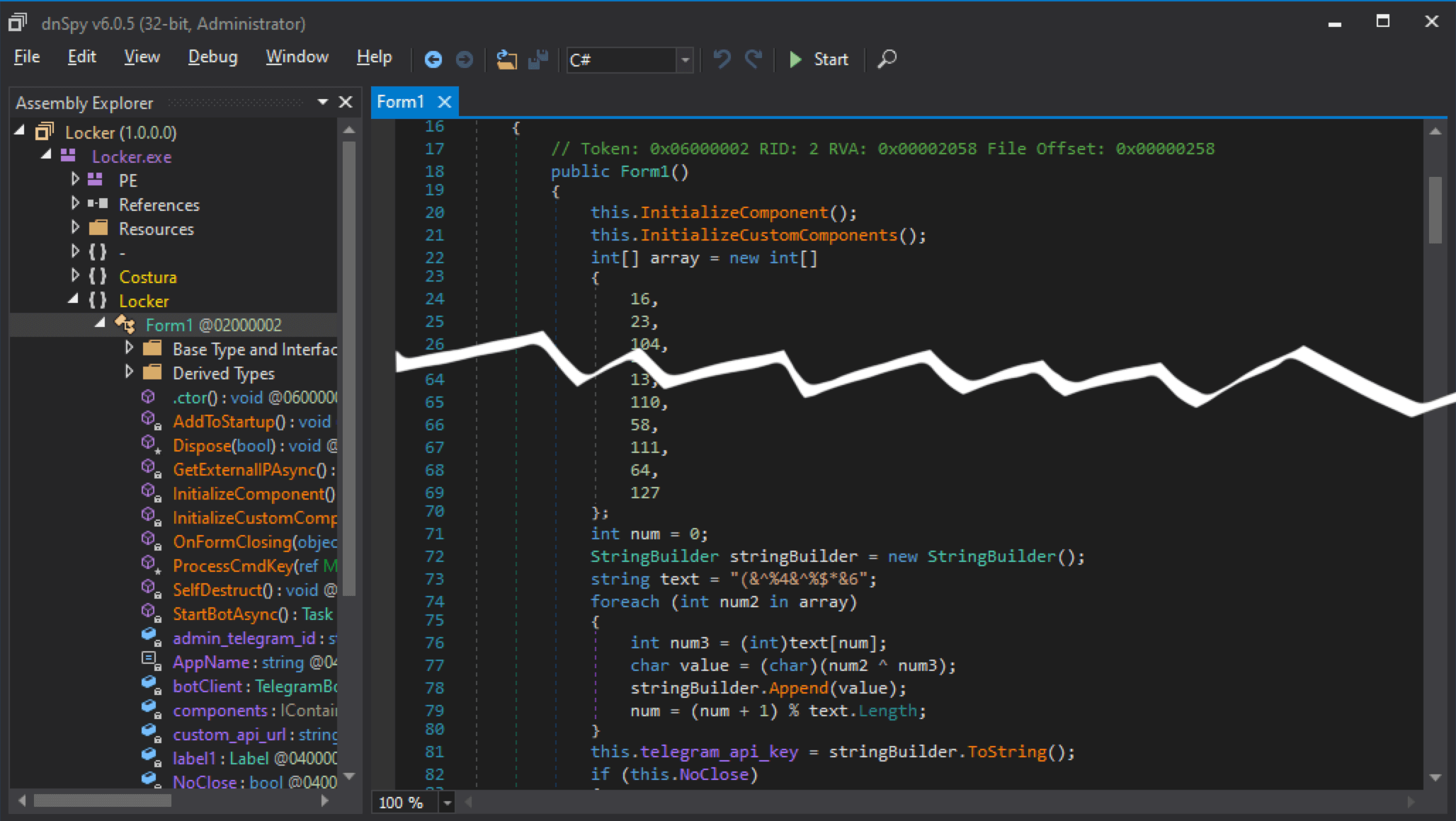
- Rewrite the API key decryption algorithm using your favorite language and execute it:
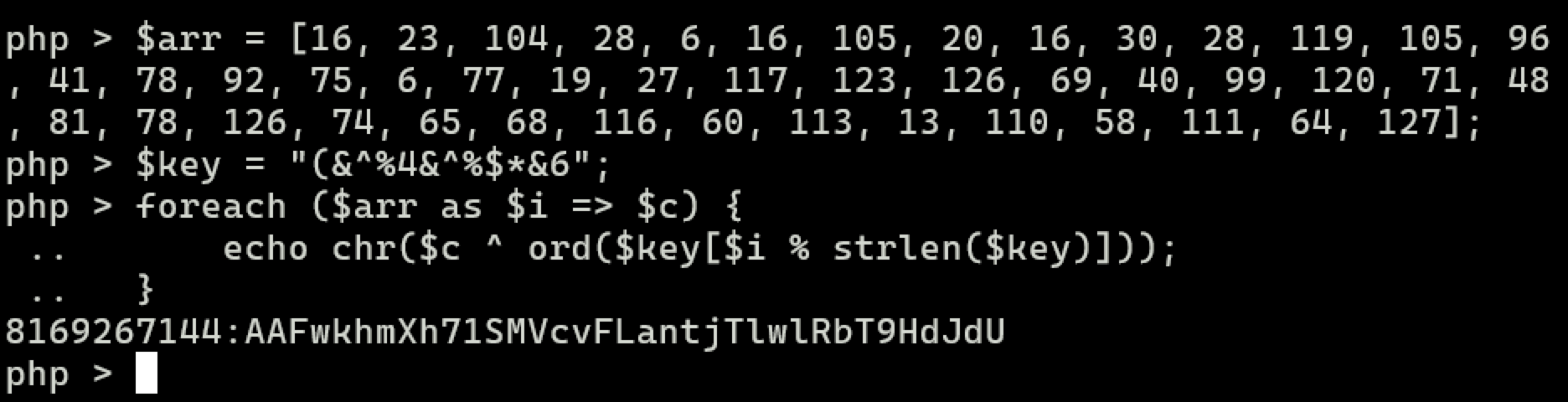
Flag
8169267144:AAFwkhmXh71SMVcvFLantjTlwlRbT9HdJdU
7. Puppetmaster (Hard)
Question
What is the phone number of the malware operator?
Solution
- To unmask the malware operator, you need the API URL from task #5, the bot token from task #6, and the ID or of the bot's administrator—the only person authorized to send commands to the winlocker. You can locate it under the admin_telegram_id variable visible in the decompiled code:
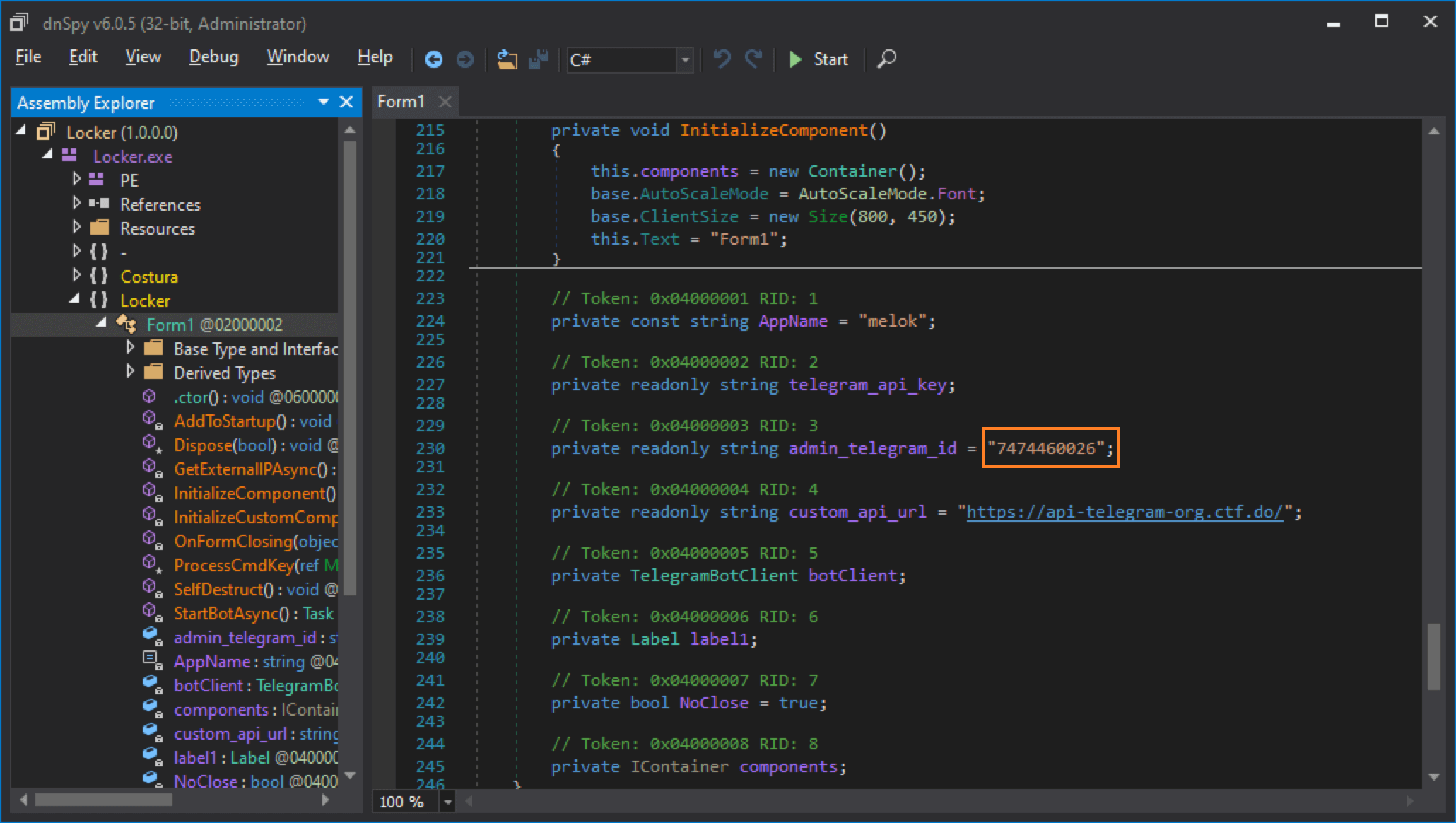
- According to Telegram Bot API reference, you can invoke getChat method by passing this ID to it.
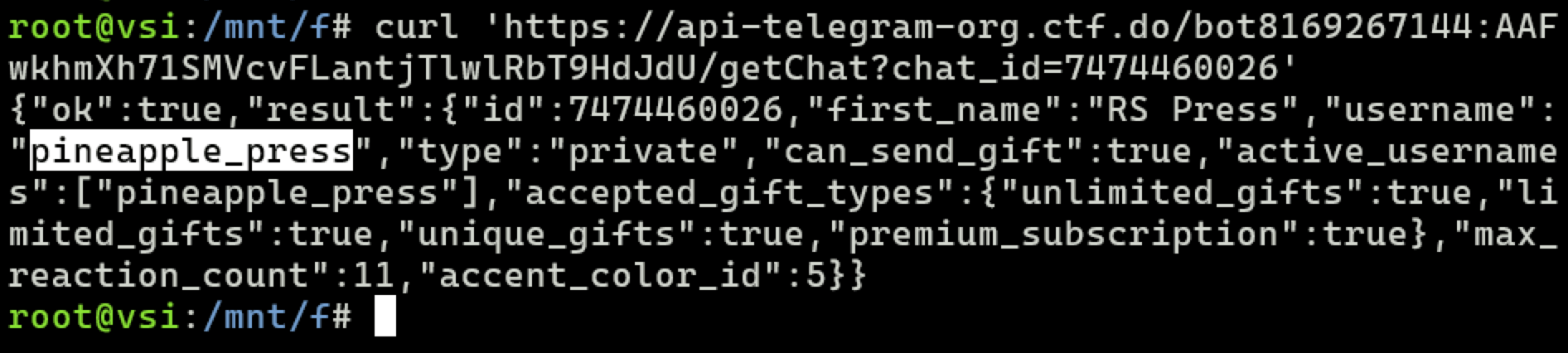
Since the bot has an open chat with the malware operator, Telegram API allows it to look up some info on the ID. Now you know the Telegram username of the perpetrator: @pineapple_press
- Search for this username on Telegram, and you will discover an account with a publicly shared phone number.
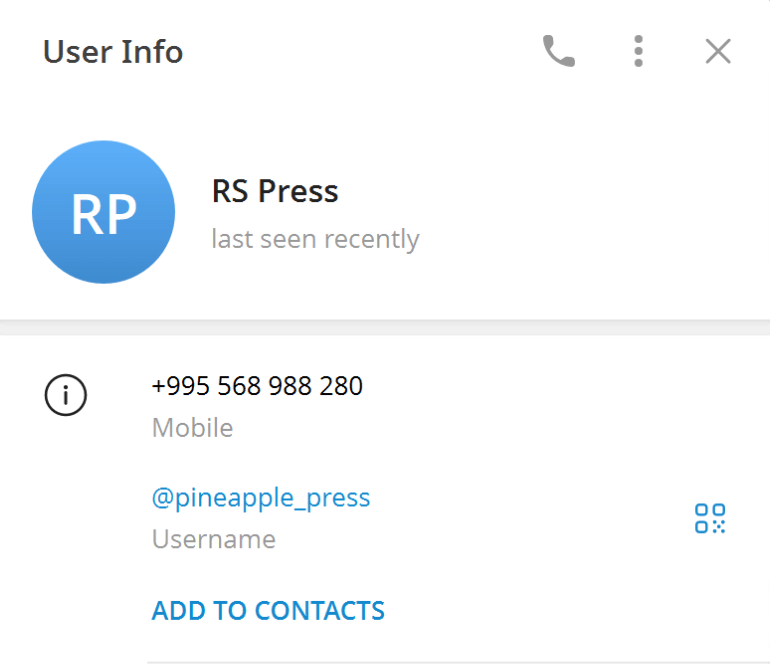
Flag
+995568988280
8. Android
Question
What is the Google account this phone is set up with?
Solution
- This time, let us allow AI to help. Open the BelkaGPT window and paste the question:
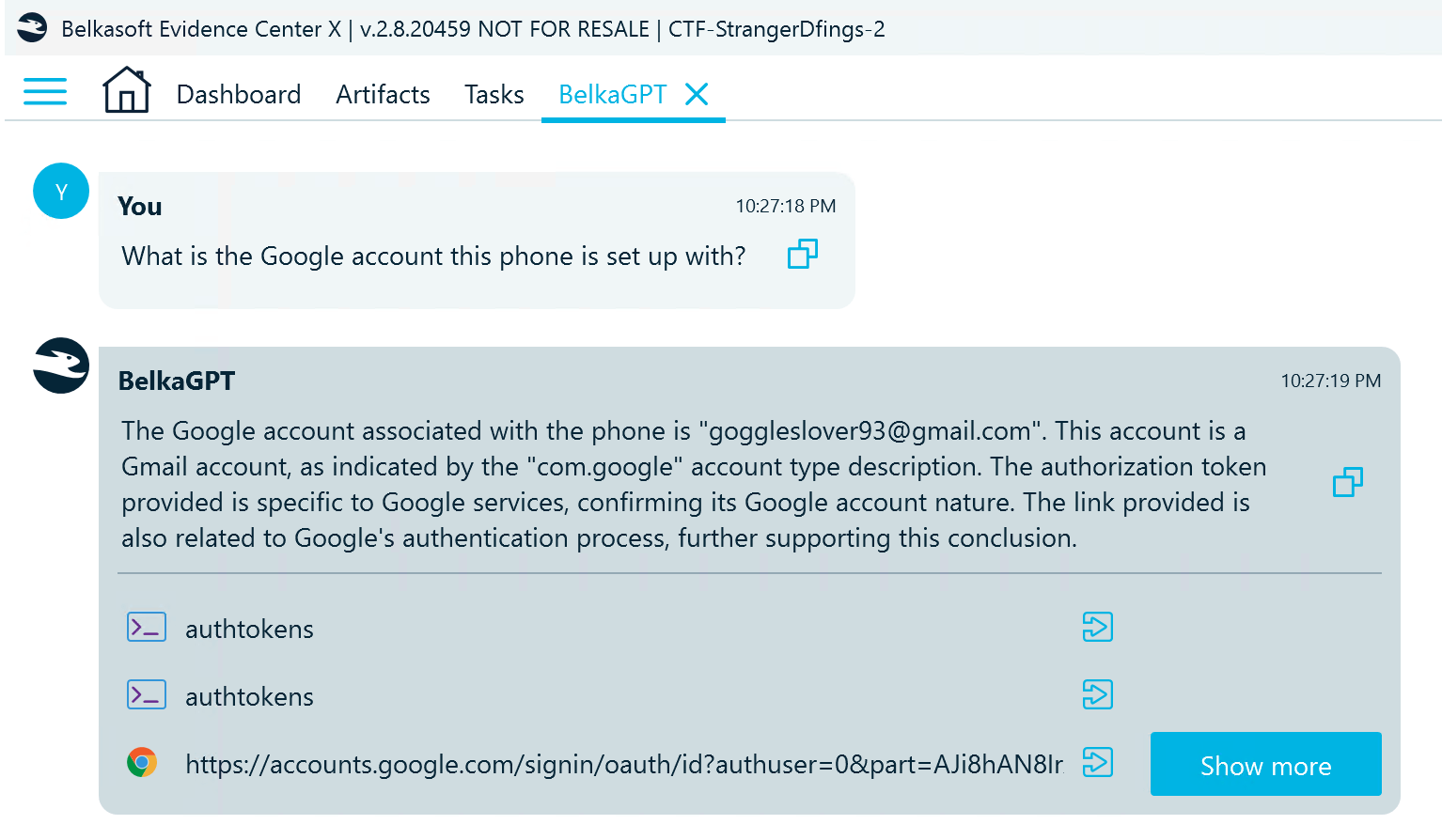
- Below the answer, BelkaGPT references the artifacts it found most relevant and used to generate the answer. The first referenced artifact points to the accounts_ce.db profile that includes details of the application accounts used on the device:
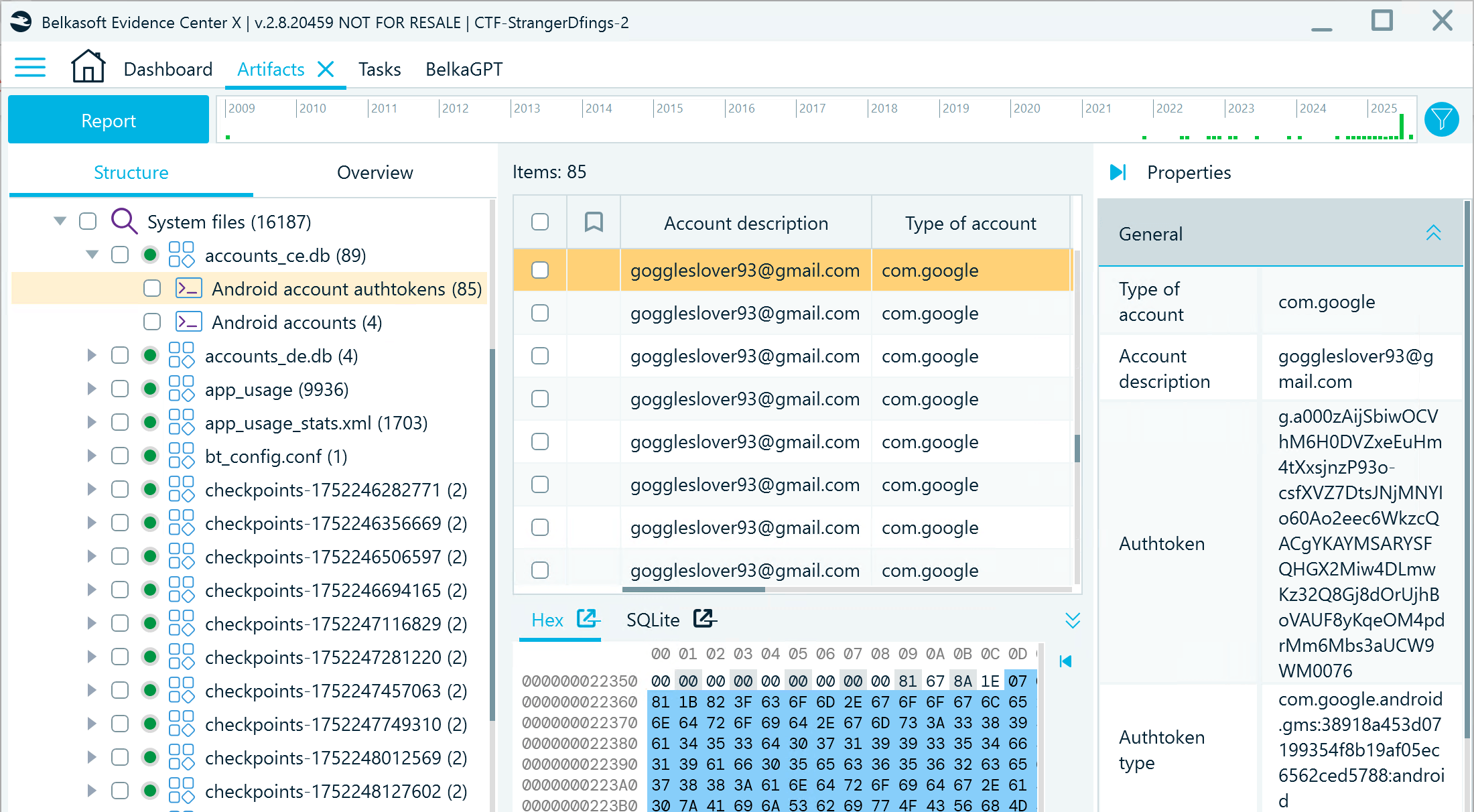
Flag
goggleslover93@gmail.com
9. Workspace (Warmup)
Question
Where does the phone owner work and what's his position?
Solution
Here, you can explore the Mails category and locate a mailbox used with a professional account. When inspecting emails under the Sent node, you can spot an email signature containing the device owner's name and job title:
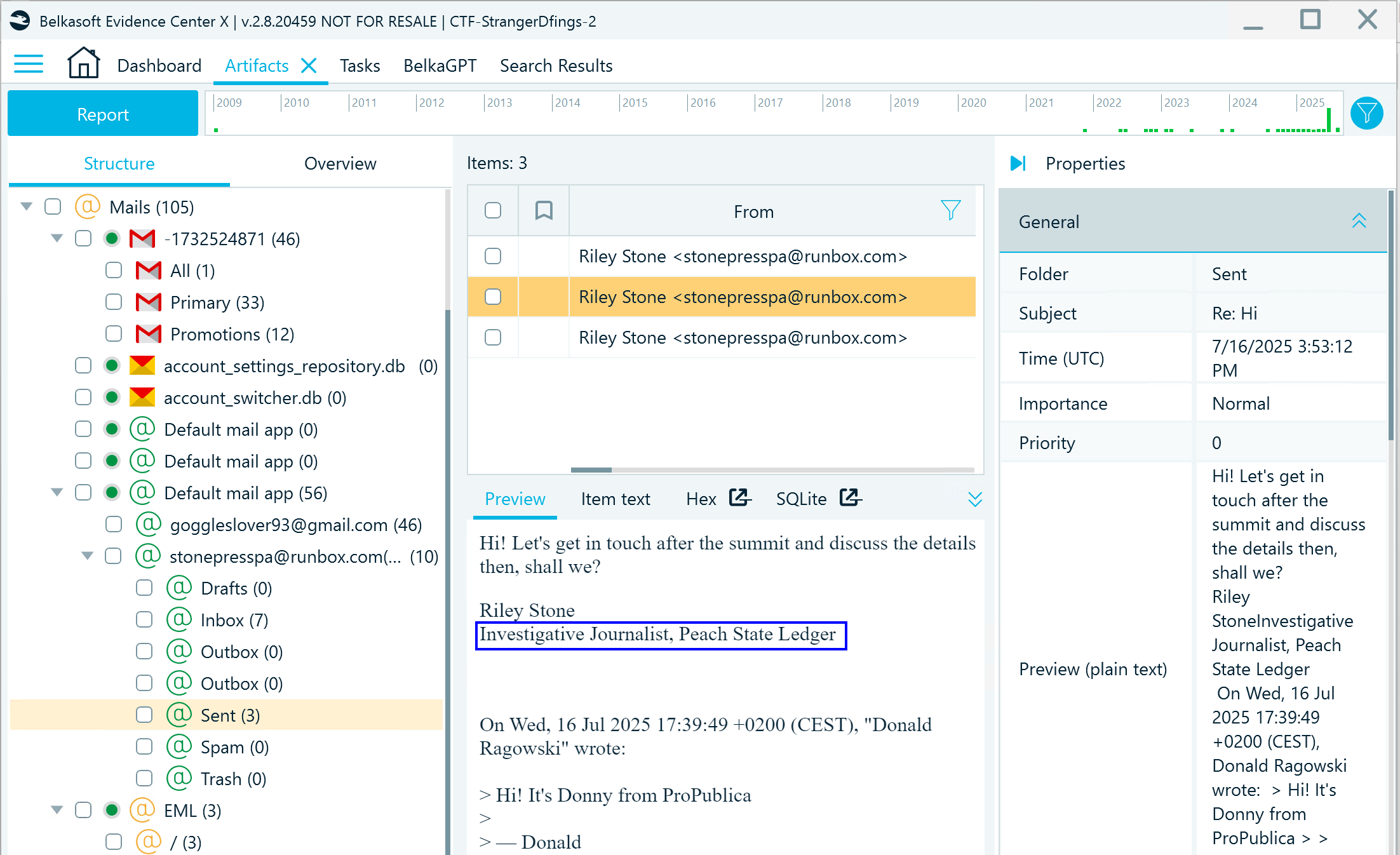
Flag
Investigative Journalist at Peach State Ledger
10. Banking (Tricky)
Question
What are the last 4 digits of the suspect's bank card, and the contact phone number of his bank?
Solution
- Banking receipts often end up in mailboxes. But this time, instead of looking through them manually, let AI do the job and limit the scope by the Mails category.
- You can see that Riley has used Google Pay, however the Google Wallet emails do not include card details. Click Show more to explore additional artifacts discovered by BelkaGPT and check their contents in the Artifacts window.
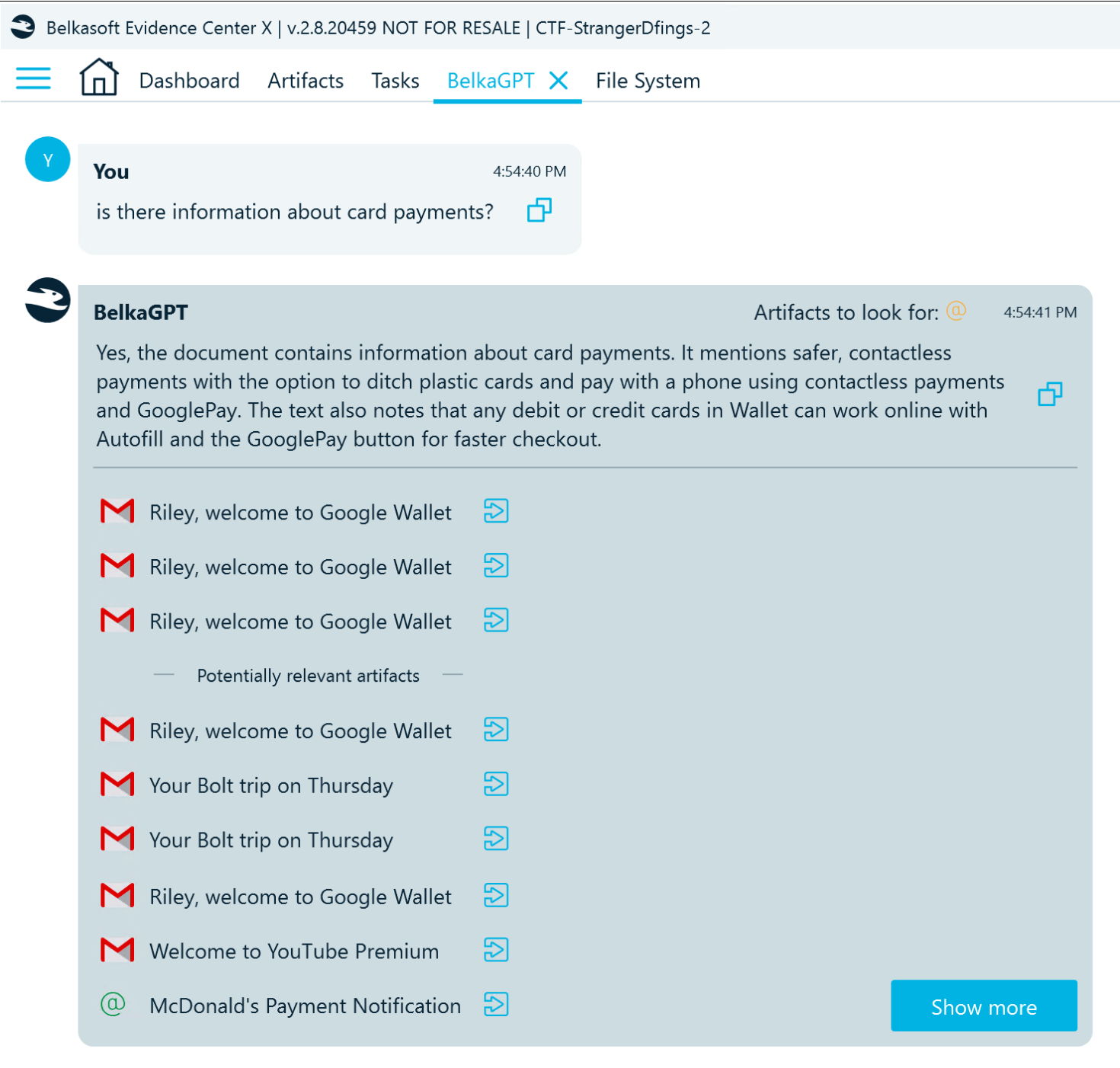
- Quite quickly, you can spot the reference to an email from YouTube Premium that includes card details:
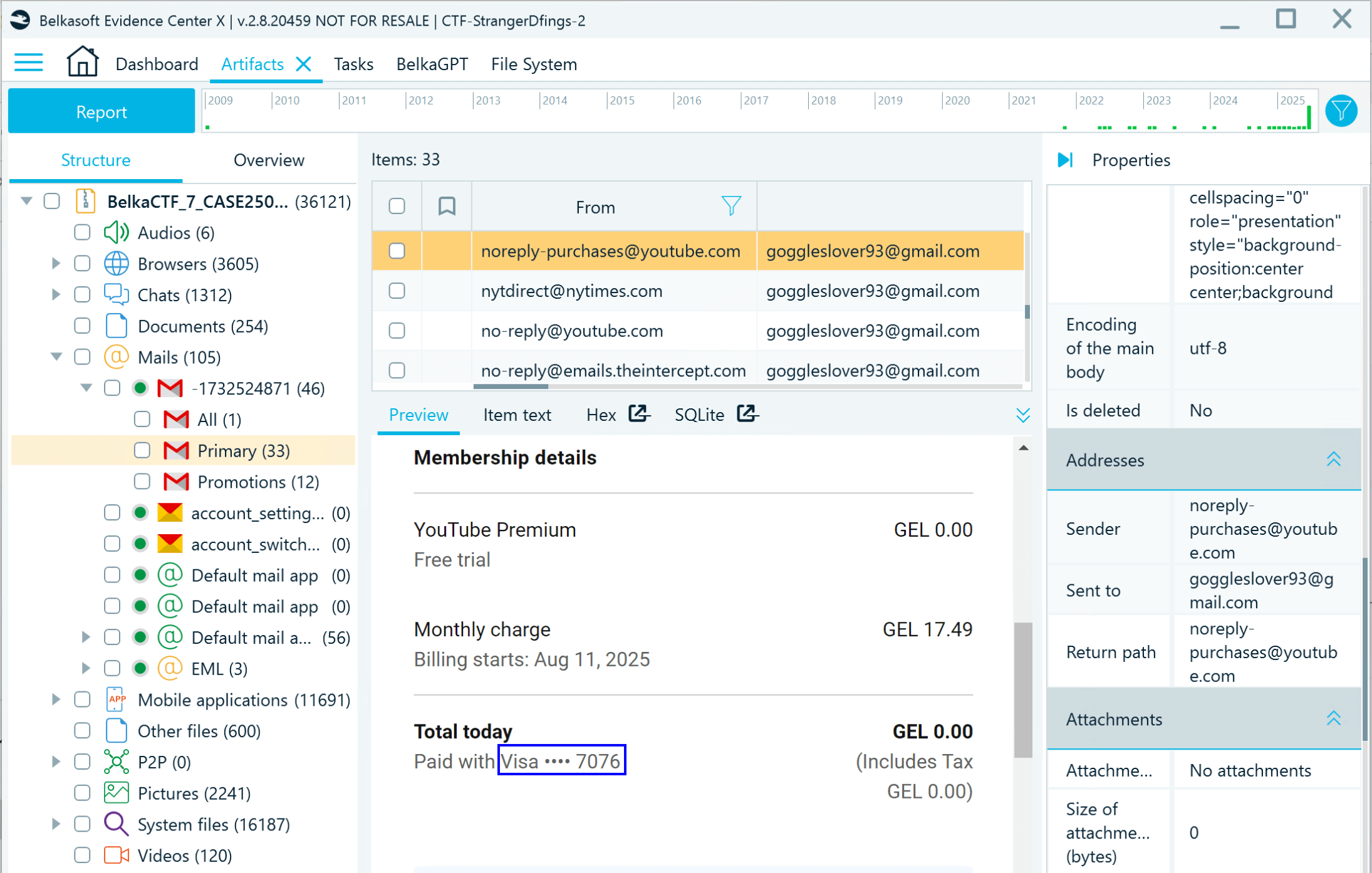
- There are two ways to find out the bank that issued the card. The easy way is to ask BelkaGPT or filter all data by "bank". This way, you will discover a number of browser artifacts related to the same financial organization (whose phone number you can find on its website):
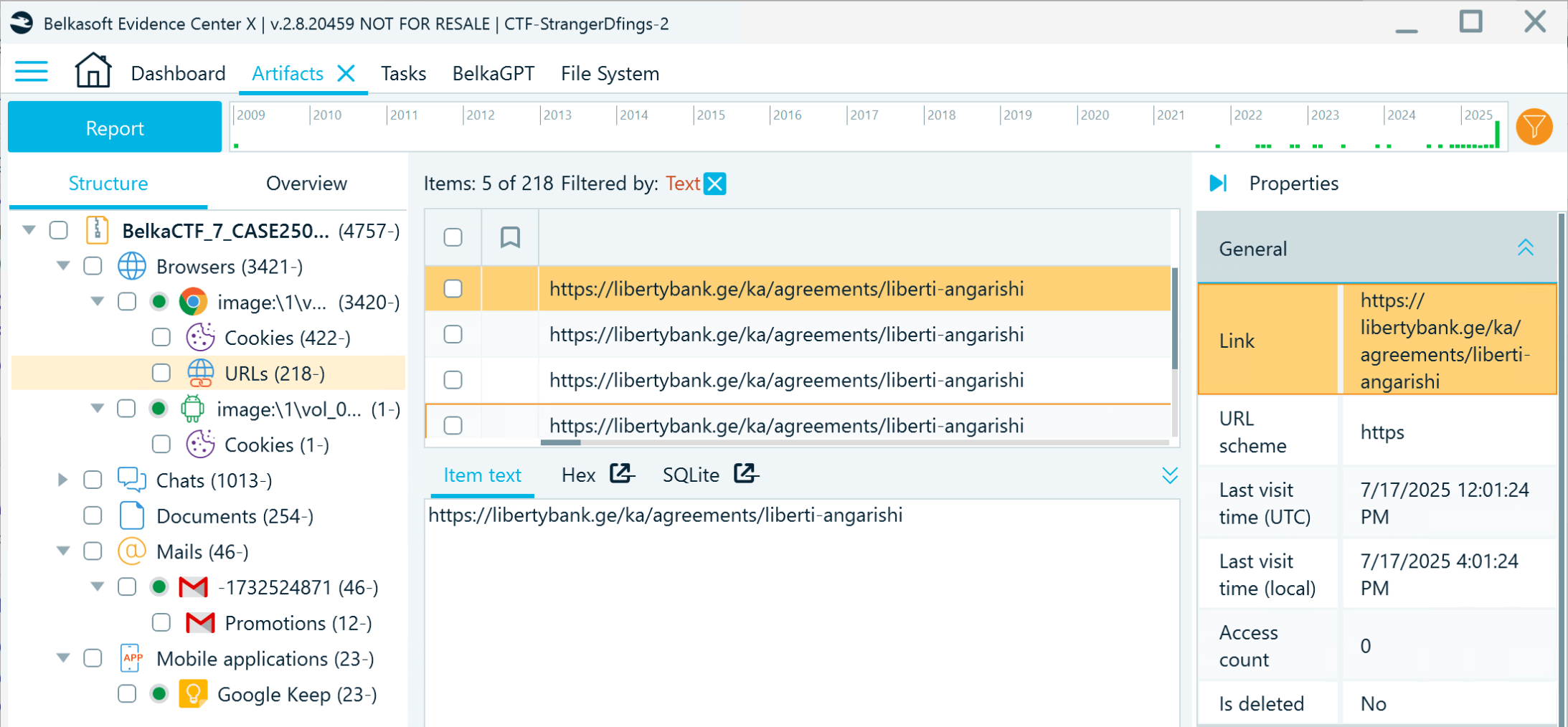
- However, if you want to be sure it is not just a web search, you can analyze Google Pay application data. First, locate the application database (data/data/com.google.android.gms/databases/pay).
- Next, go to the PaymentMethods table and explore the Protobuf blob in the payment_methods field. You will find several references to the same bank and even its contact number:
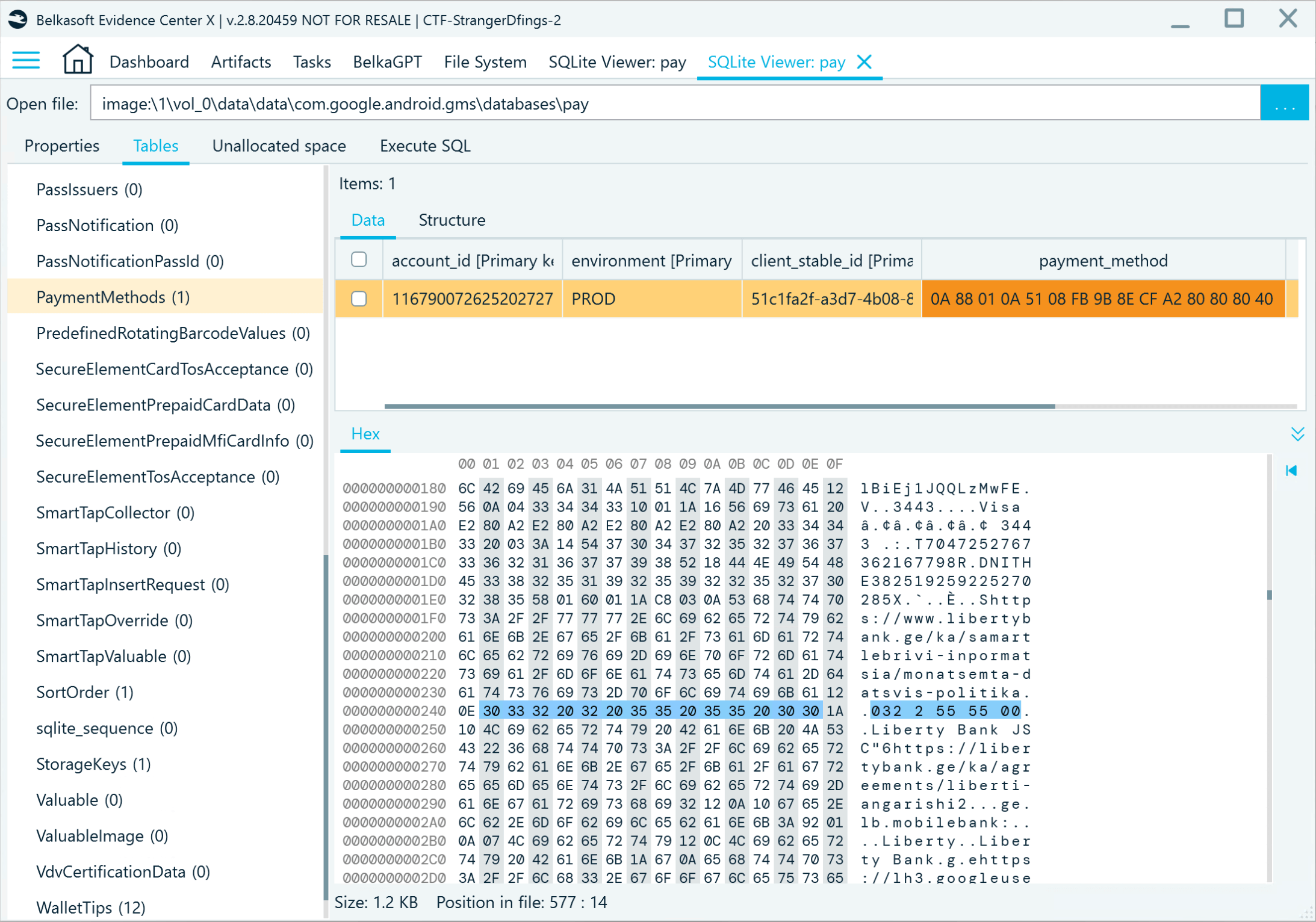
Flag
7076, 032 2 55 55 00
11. Junk Messaging (Tricky)
Question
Which dependency-causing substance is mentioned in the chat logs on the phone?
Solution
Let us turn to BelkaGPT again since it is particularly good at identifying topics of interest:
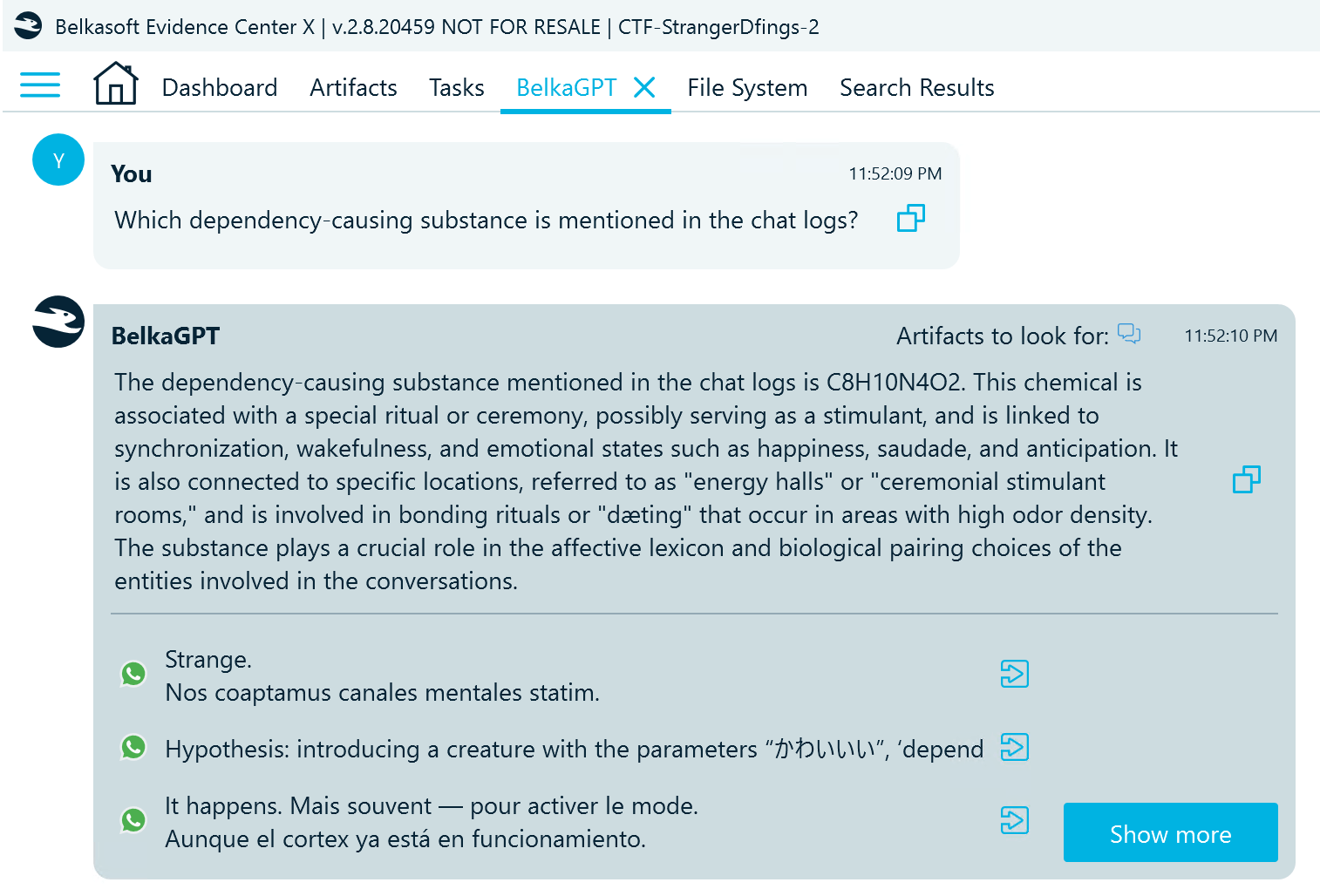
BelkaGPT references a peculiar WhatsApp conversation that seems to involve many different languages. It also mentions the mysterious C8H10N4O2, which is actually the chemical formula of caffeine.
Flag
caffeine
12. Search (Hard)
Question
Where the two missing people—an activist and a teenager—can be retrieved?
Solution
- First, let us find information about the disappeared individuals:
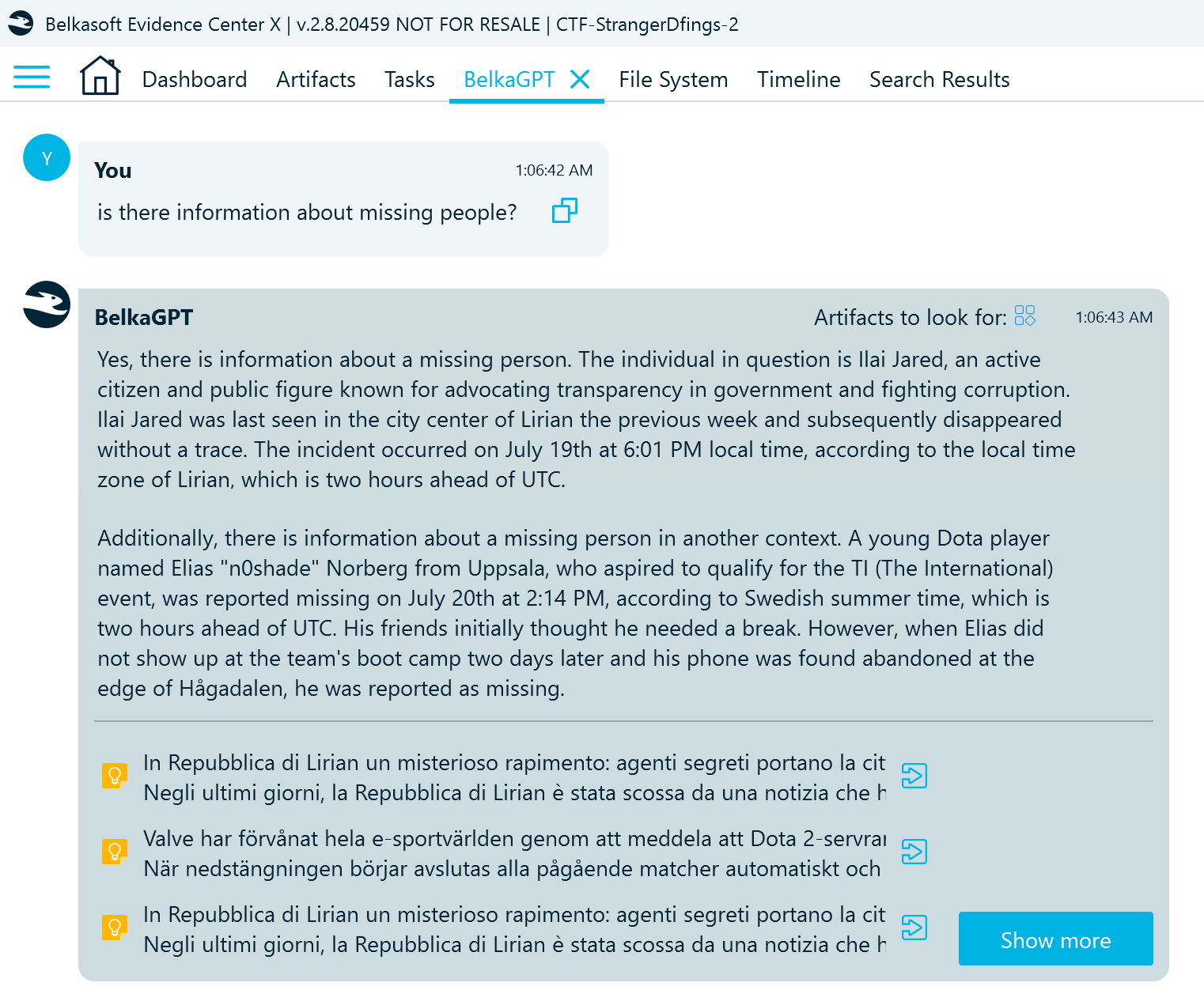
The answer and the referenced artifacts name the exact dates and times of the abductions:
- July 19th, 6:01 PM (Liria time is UTC+2)
- July 20th, 2:14 PM (Swedish summer time, also UTC+2)
- Now inspect what occurred on the device at these moments using the Timeline window.
- July 19th, 4:01 PM (UTC):
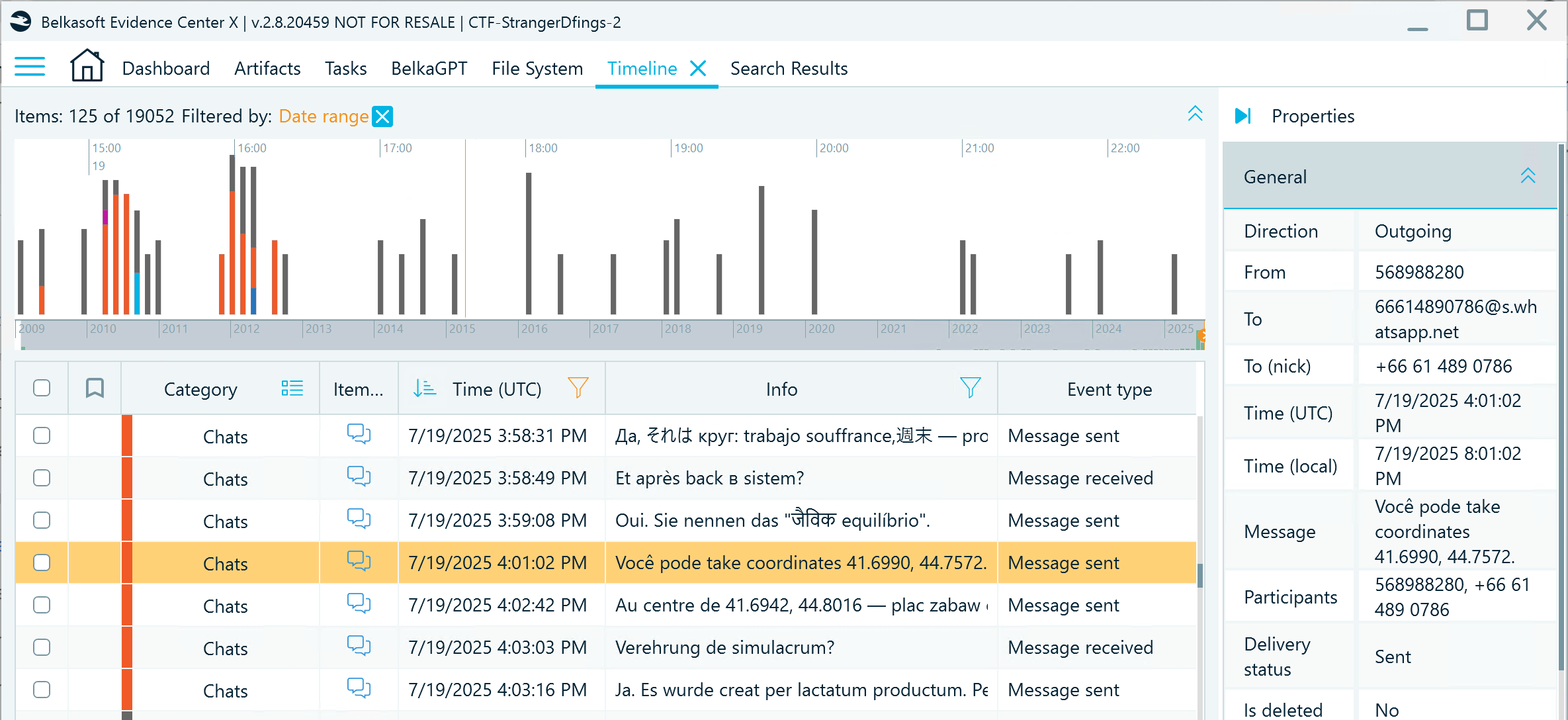
- July 20th, 12:14 PM (UTC):
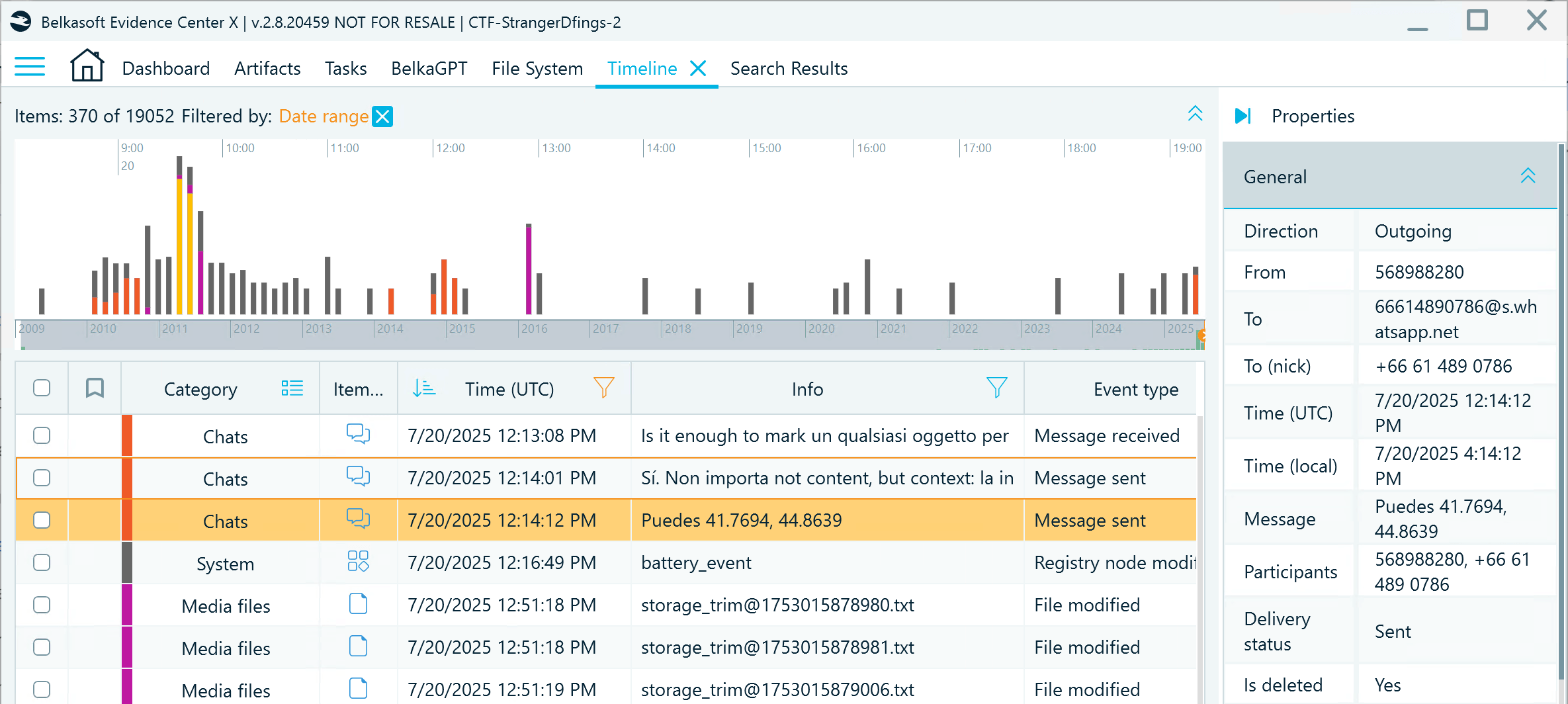
Flag
41.6990,44.7572 41.7694,44.8639
13. Party Van (Baby)
Question
What is the password of the suspect's home Wi-Fi network?
Solution
Navigate to the System Files → Wi-Fi connections node. You will find two entries with Wi-Fi details. One of them has the -GUEST tag, which is unlikely to be a home Wi-Fi name. The other has a name resembling the Telegram username you have encountered in a previous challenge:
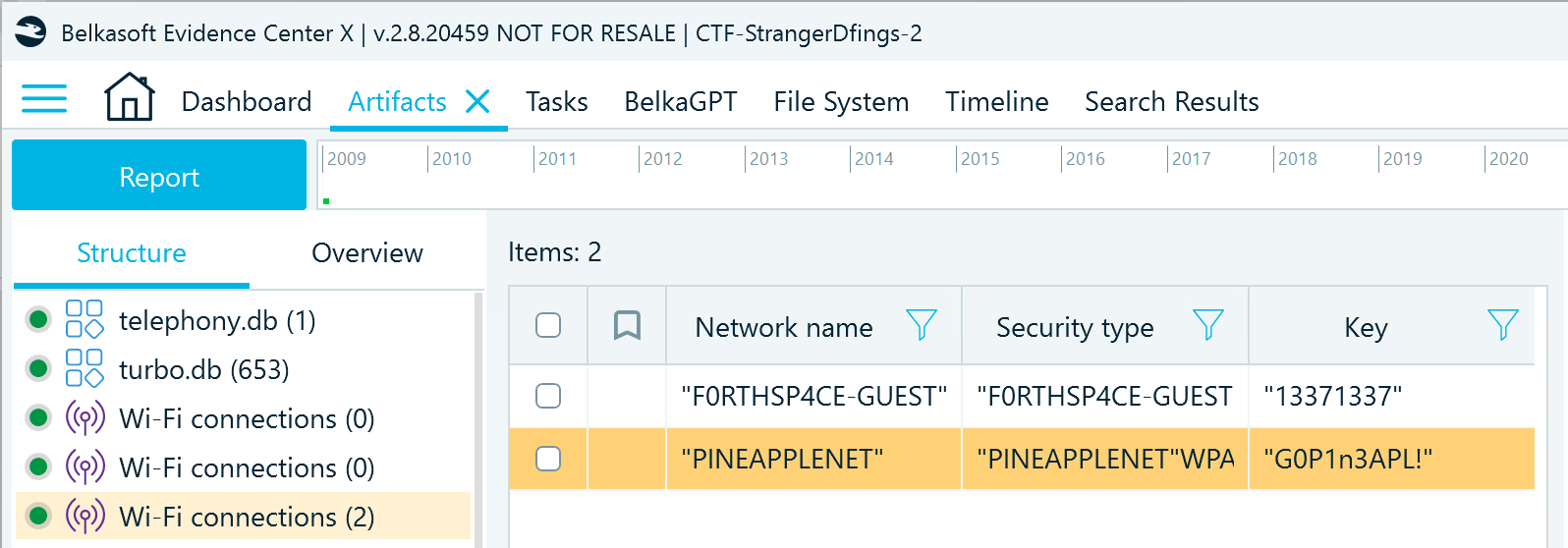
Flag
G0P1n3APL!
14. New Name (Tricky)
Question
What does the suspect call himself since recently?
Solution
- Here you will need Wireshark. Before you can analyze the traffic, decrypt it with the password discovered in the previous chall. Go to Edit → Preferences → Protocol → IEEE 802.11 and next to Decryption keys, click Edit. Add the Wi-Fi password key with the wpa-pwd type:
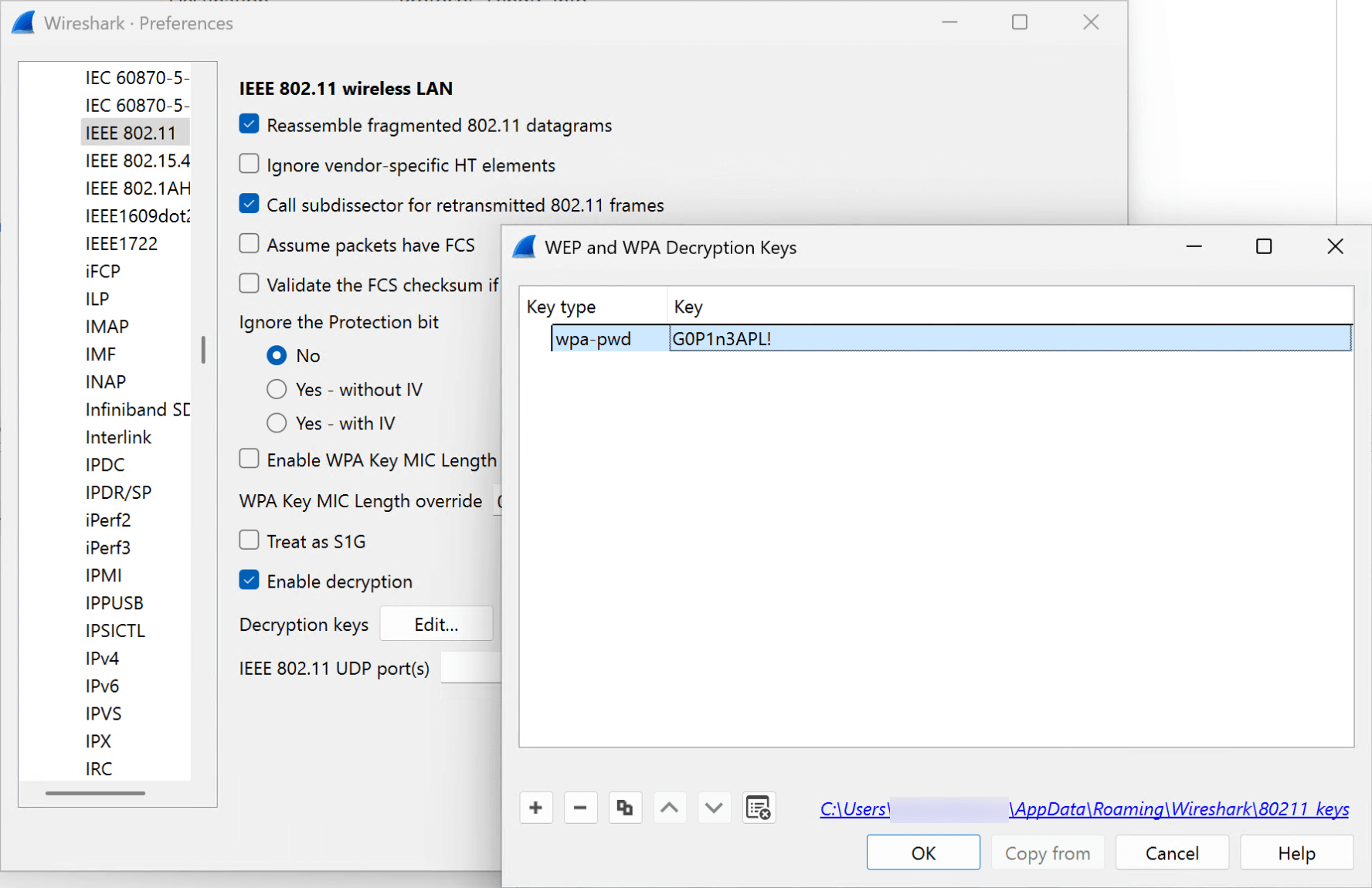
- In the traffic, the files are shared using the Server Message Block (SMB) protocol. Wireshark can extract such files. Open the intercepted traffic dump and select File → Export Objects → SMB:
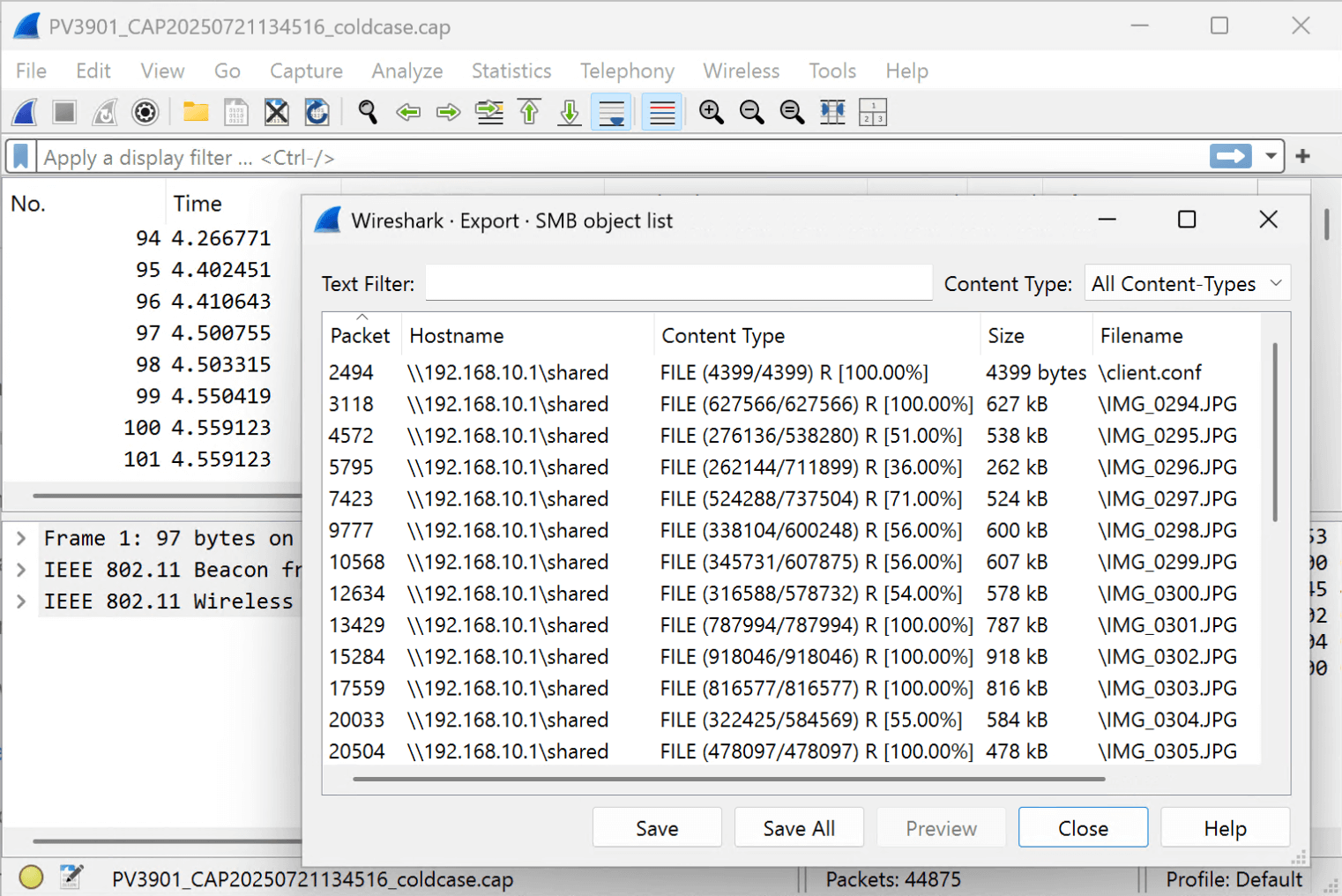
- Among exported files, you can locate a photo with a Starbucks cup held using a very unusual grip.
Flag
Y Æ B-12
15. Metamorphosis (Tricky)
Question
Figure out the moment when the suspect's body started acting weird as precisely as you can.
Solution
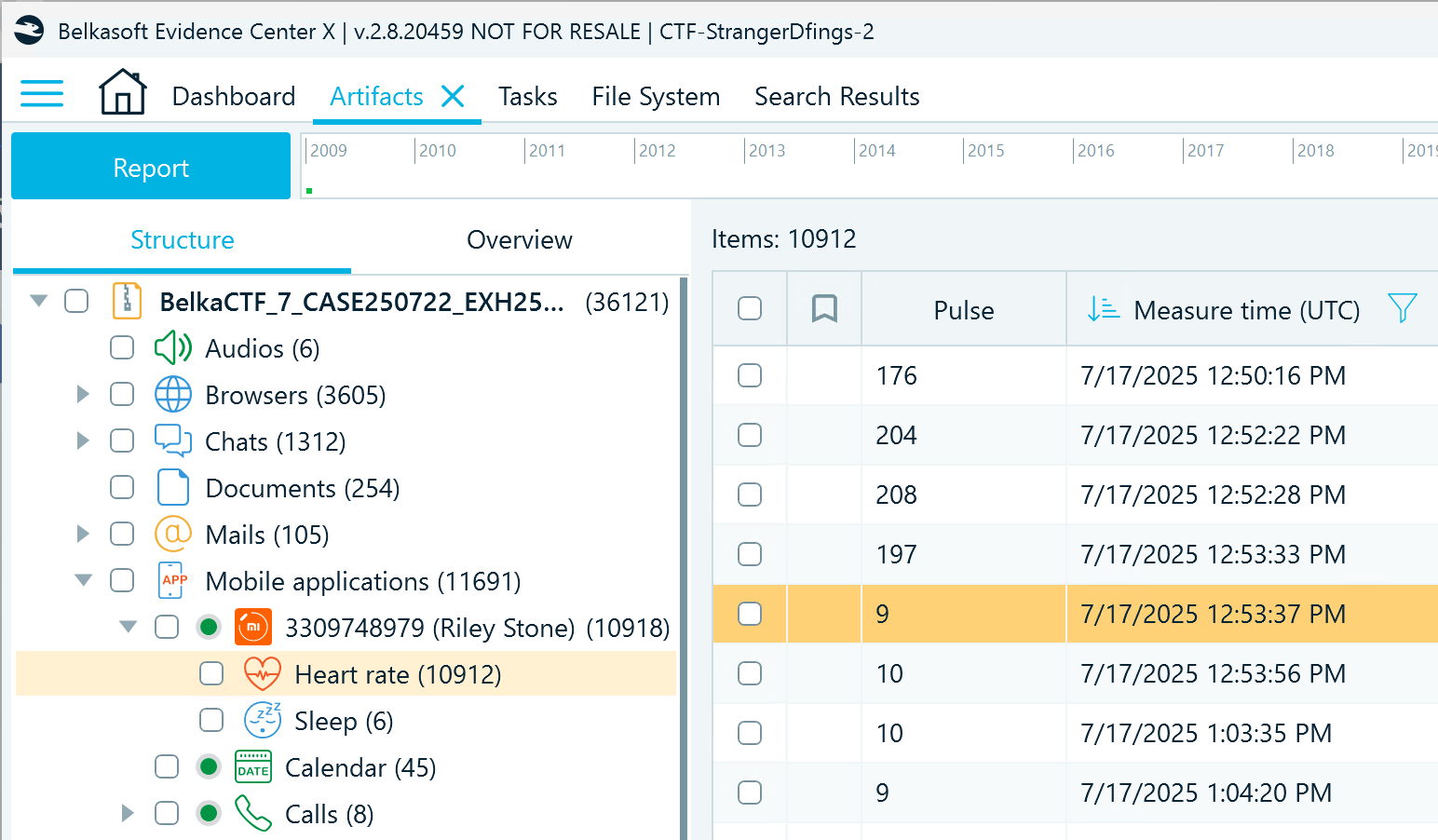
Here, you will need to analyze health data. Navigate to the Mobile Applications → Mi → Heart rate profile and sort the records by the Measure time (UTC) column. After a bit of scrolling, you can find the moment when the suspect's pulse goes very high and then drops to 9 bpm:
Flag
7/17/2025 12:53:37 PM
16. Thought Trap (Hard)
Question
At which event the journalist became puppeteered by aliens?
Solution
- Since you know the day when the journalist was "replaced," you can filter the data by 7/17/2025 and check the records created on this date. Go to Mails → GMail and locate the email received after a taxi ride:
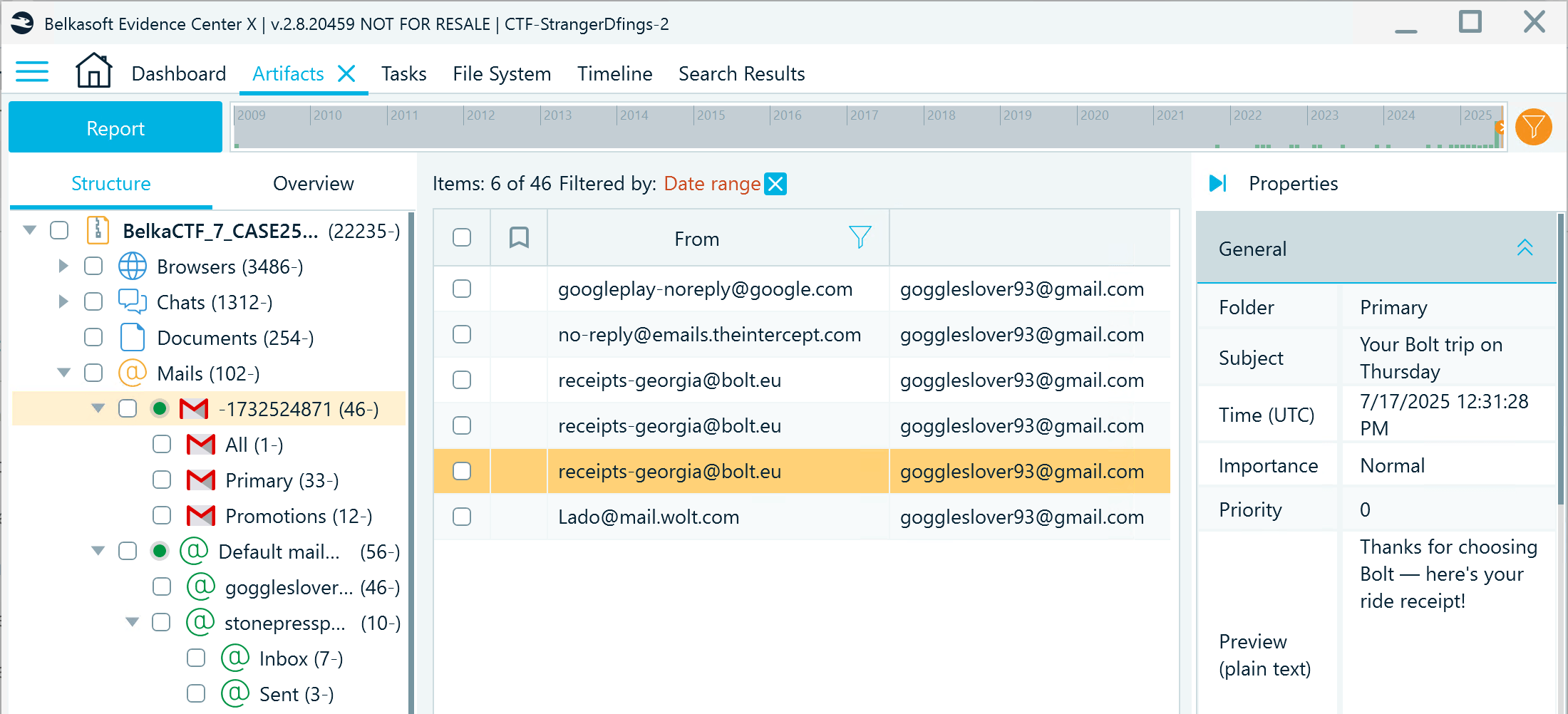
- Next, navigate to System Files → app_usage → Digital Wellbeing and find out what other apps were used shortly after the taxi ride. Besides various system apps, you can find a speed test app package name:
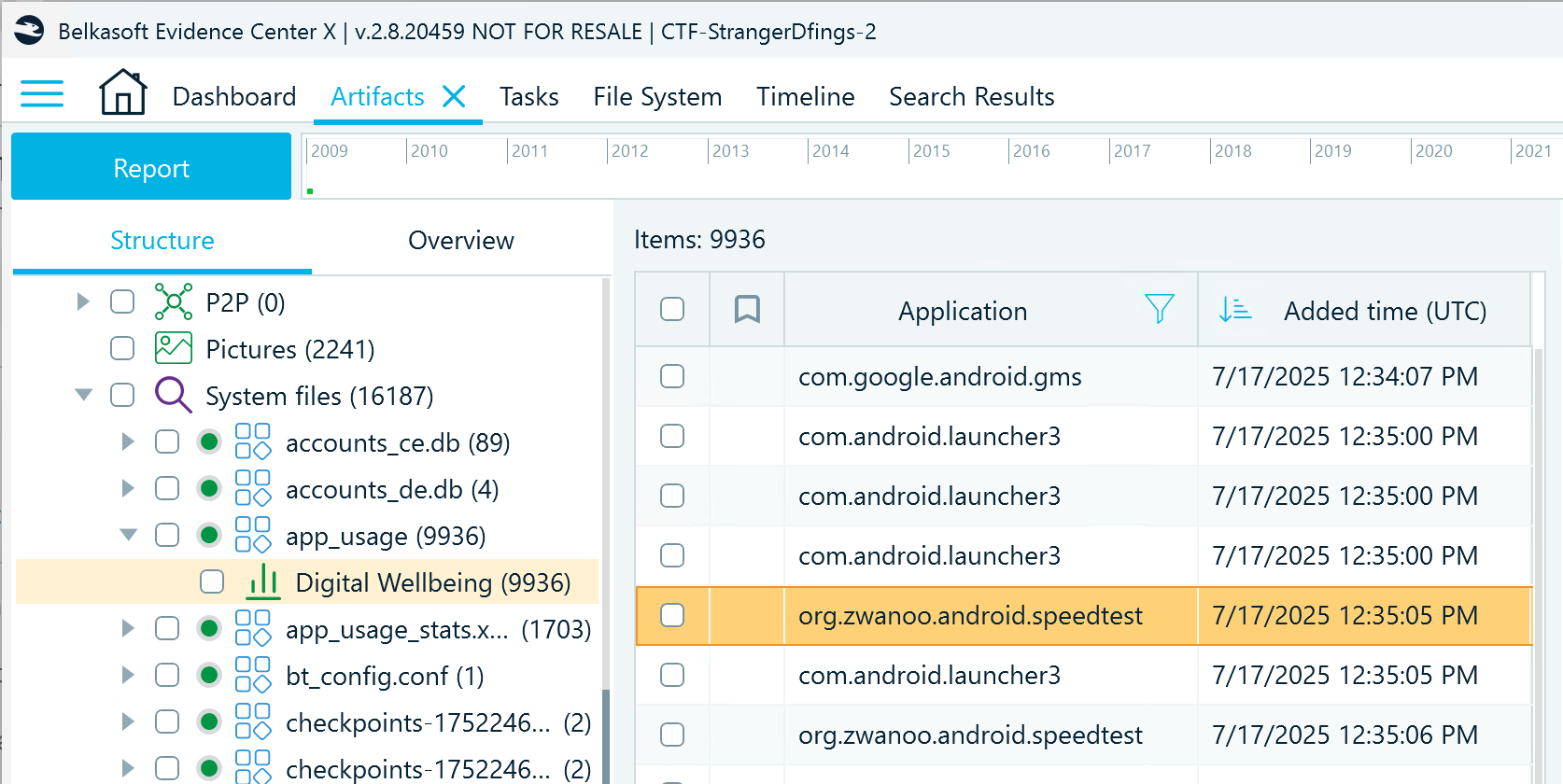
- Locate the application folder (org.zwanoo.android.speedtest) in the File System window and navigate to the Databases folder. Inside, you can find AmplifyDatastore.db with speed test records, one of which shows a Wi-Fi hotspot named the same as the event:
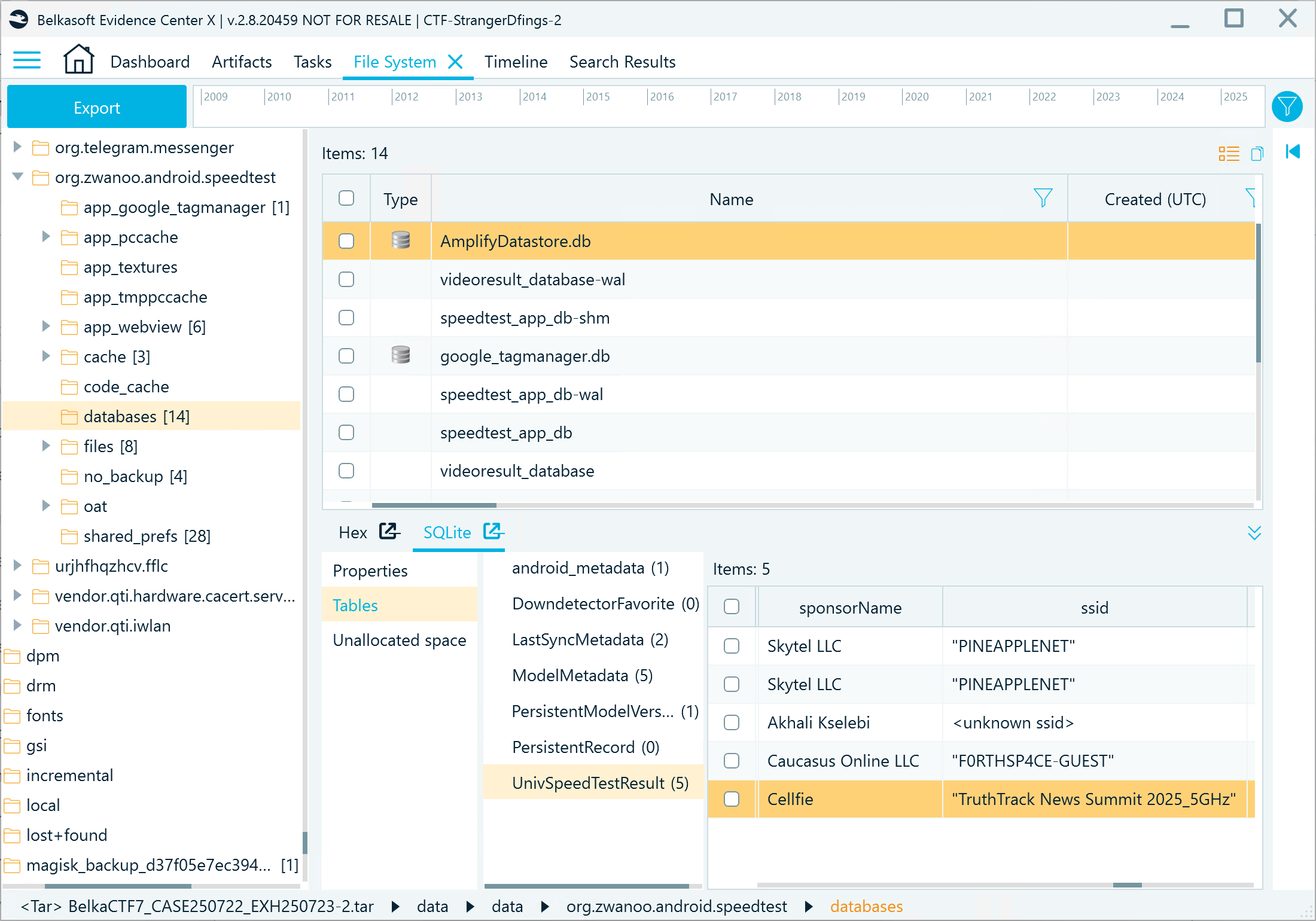
Flag
TruthTrack News Summit 2025
17. Vehicle (Tricky)
Question
What is the car the jour… alien drives?
Solution
In the File System window, locate the Android Auto application folder (com.google.android.projection.gearhead) and navigate to the Databases folder. carservicedata.db reveals the car model:
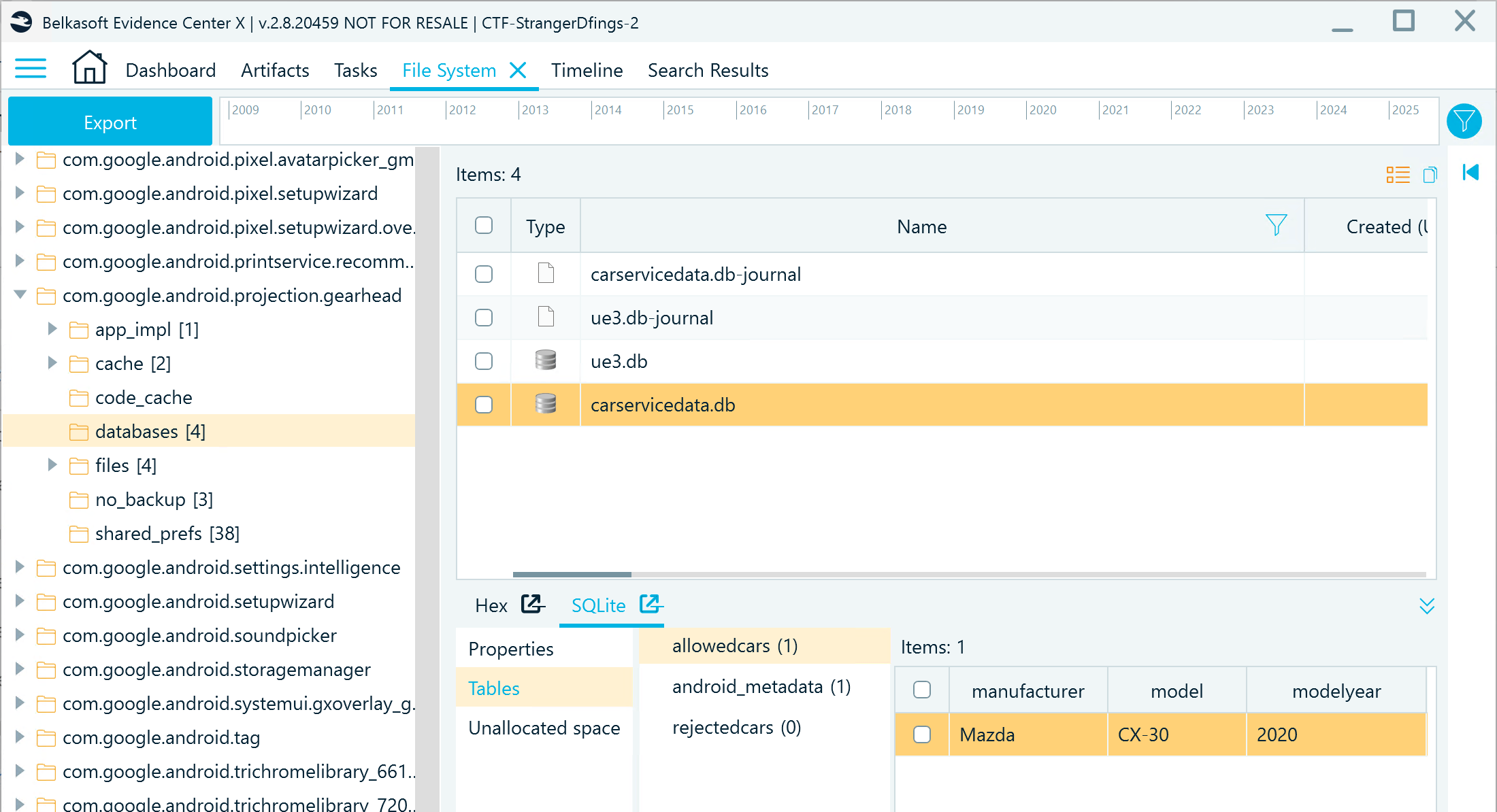
Flag
Mazda CX-30 (2020)
18. Radars (Warmup)
Question
Mine the ATC software logs for serial numbers of the radars that spotted a UFO flying by.
Solution
- First, you need to identify where the ATC Radar software stores logs. Return to the RAM dump and inspect the extracted processes in the File System window. You can see one named ATC_RADAR.exe:
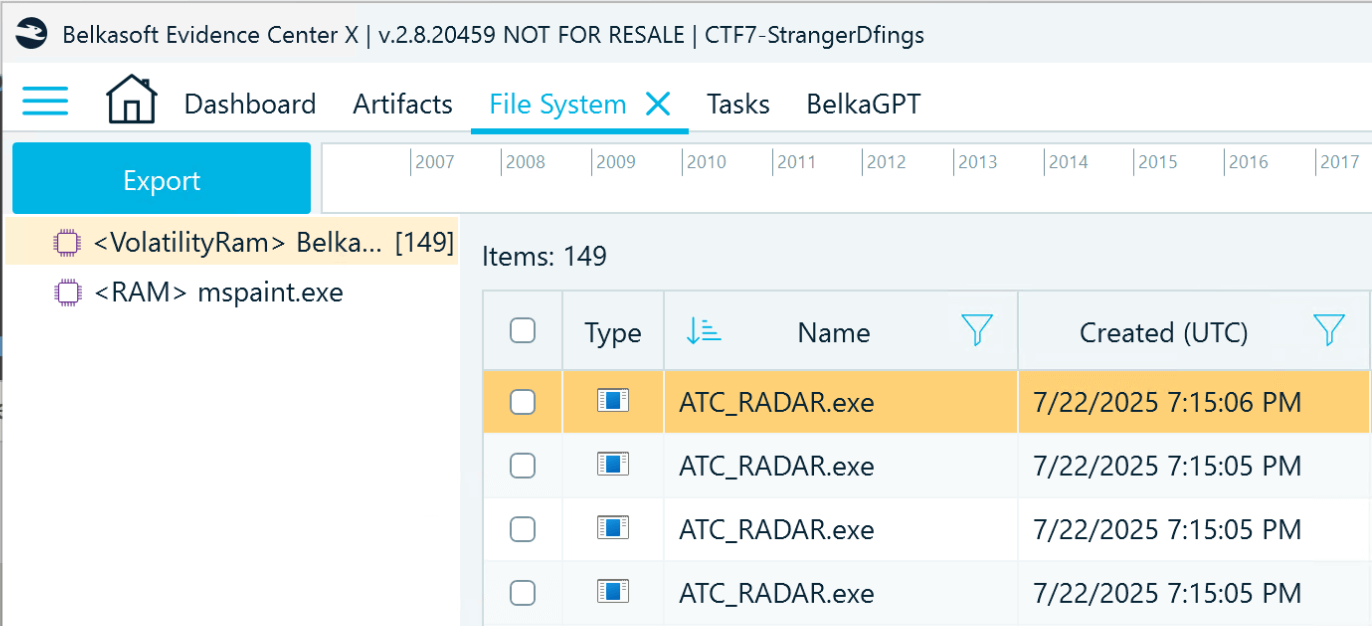
- Go to the Artifacts window, and in the File (FileScan) node, filter the files by "ATC_RADAR.exe" to locate the application along its path in the file system:
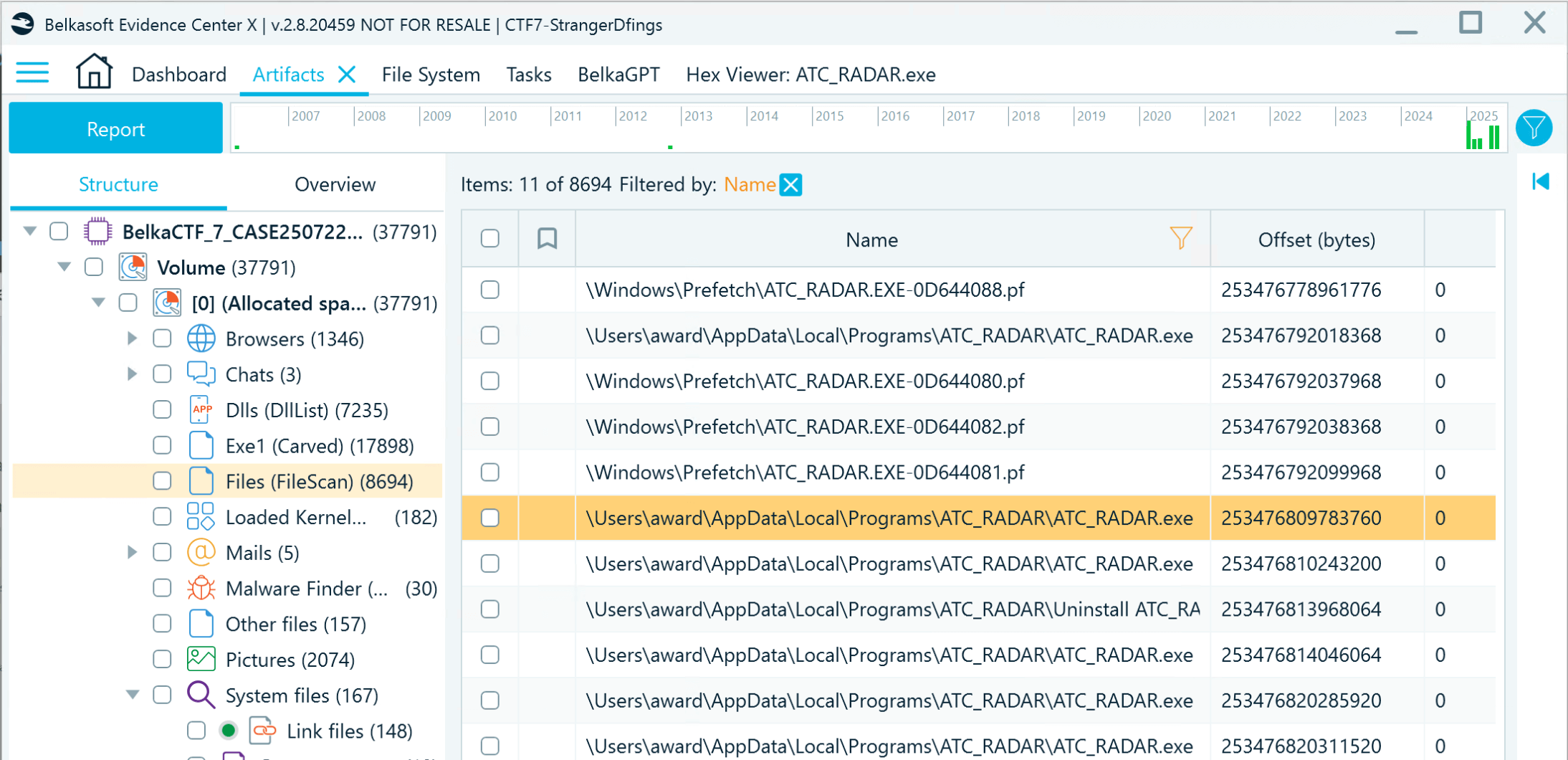
- Filter the files by the storage path and inspect them for the ones that resemble logs. You will find an SQLite-like looking database:
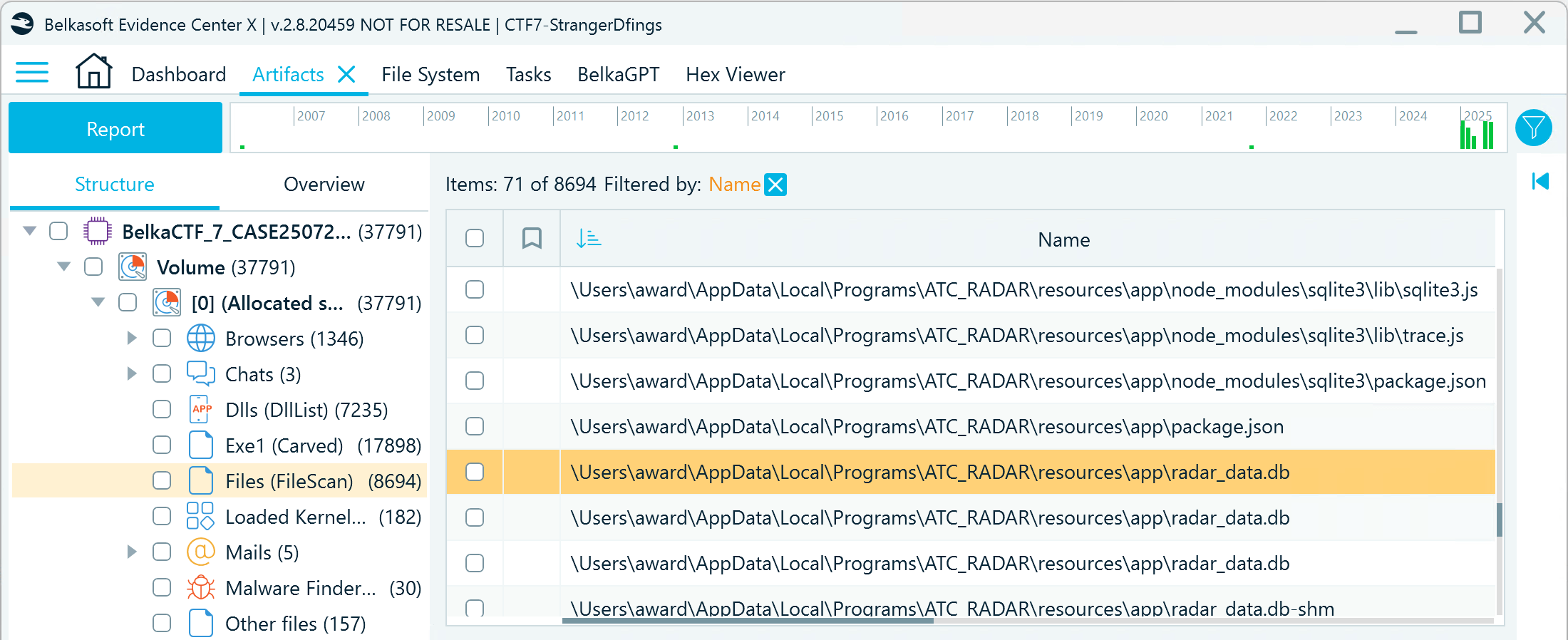
- Extract the file with Volatility using the following command:
vol.py -f BelkaCTF_7_CASE250722_KTSOAERO.mem windows.dumpfiles --virtaddr 253476792055168
- Rename the file to "radar_data.db" and open it with Belkasoft X's SQLite Viewer. Inspect the objects table:
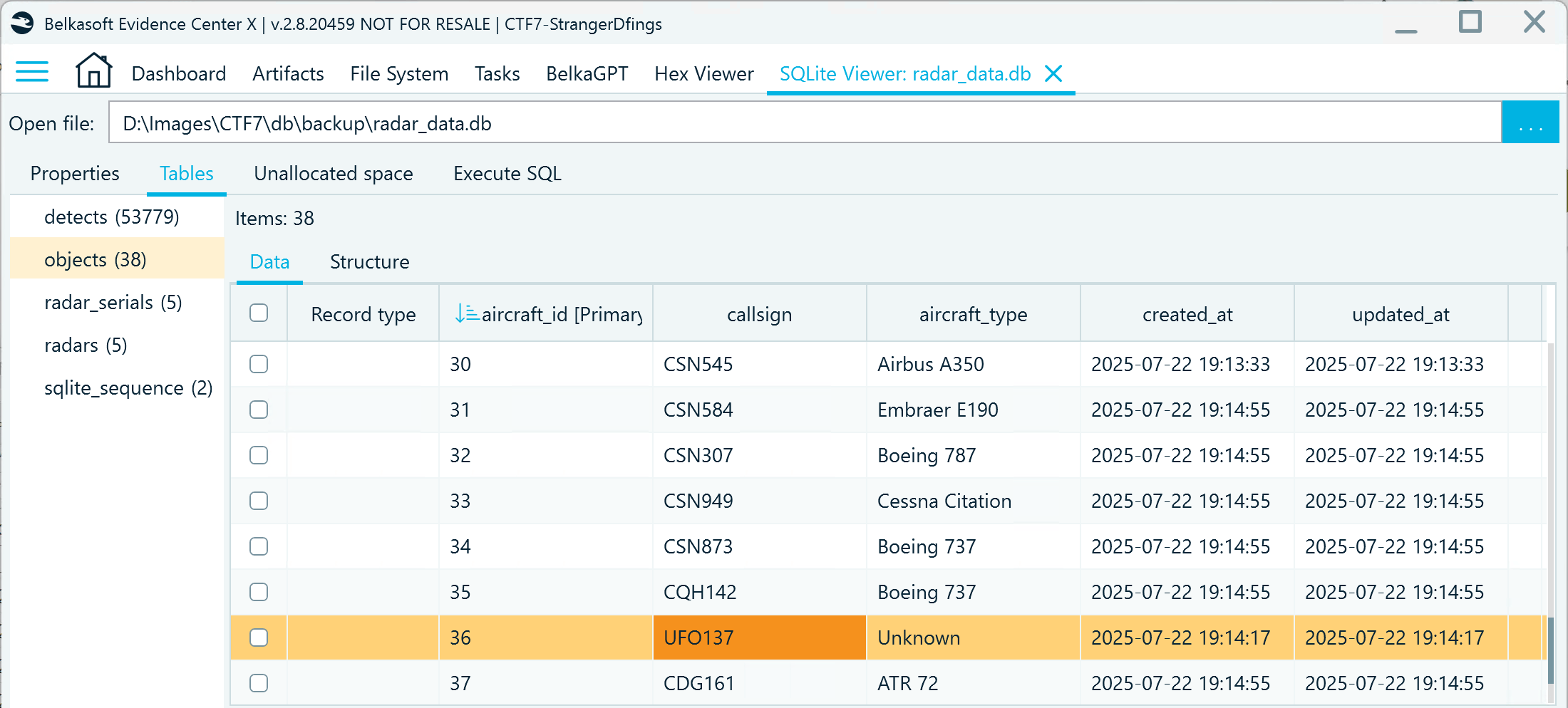
- Now that you know the UFO object ID, you can use a query to identify the radar serial numbers by consolidating data from the detects and radar_serials tables:
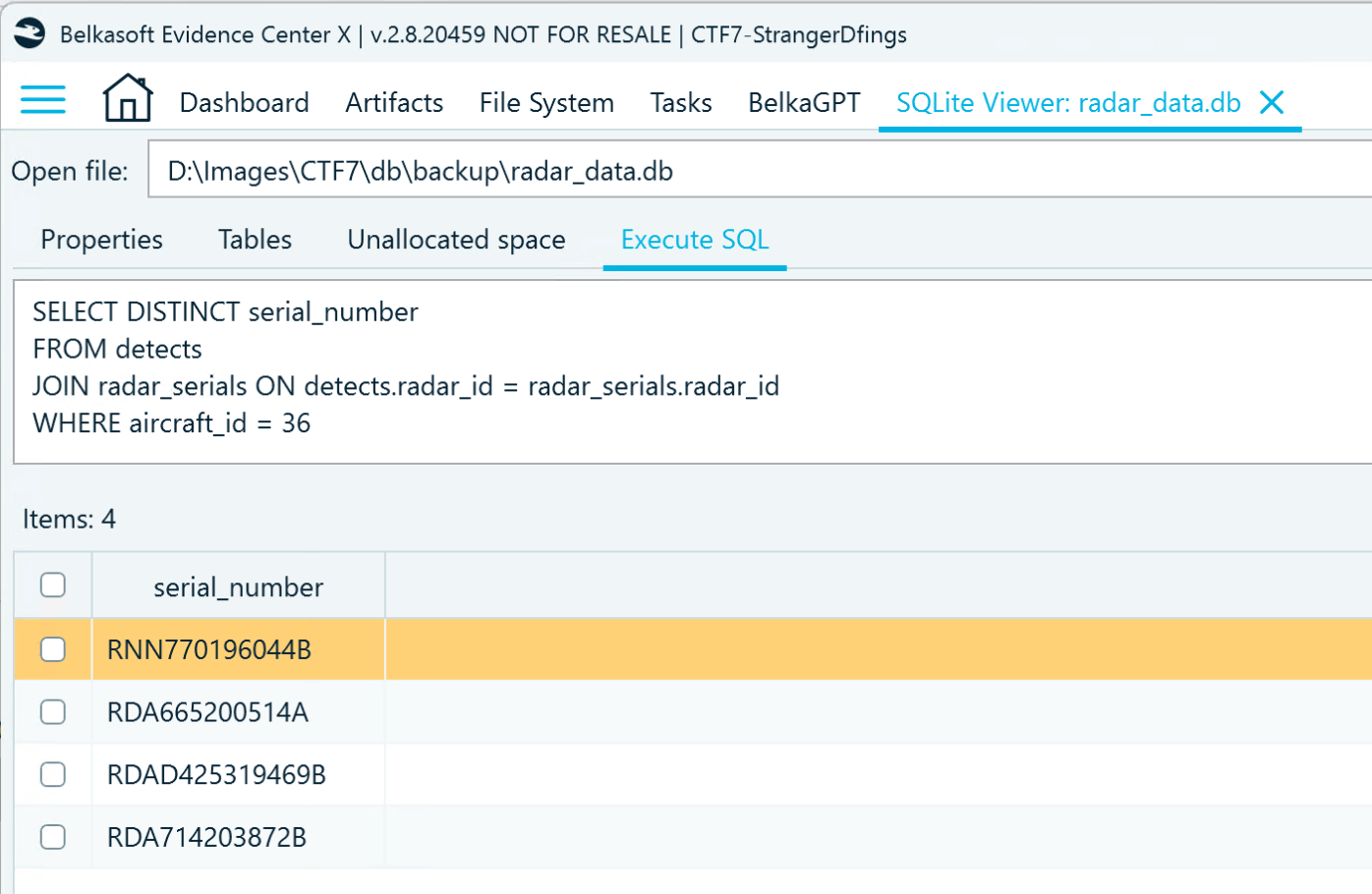
Flag
RDAD425319469B, RDA665200514A, RNN770196044B, RDA714203872B
19. Foo Fighter (Tricky)
Question
Pull the full UFO label reported by the radars, as it was shown on the ATC software display.
Solution
- Since you know that the screenshot you need to find was left unsaved in Paint, pull the application process using the File System window. Filter the processes by "paint", and copy mspaint.exe to a folder.
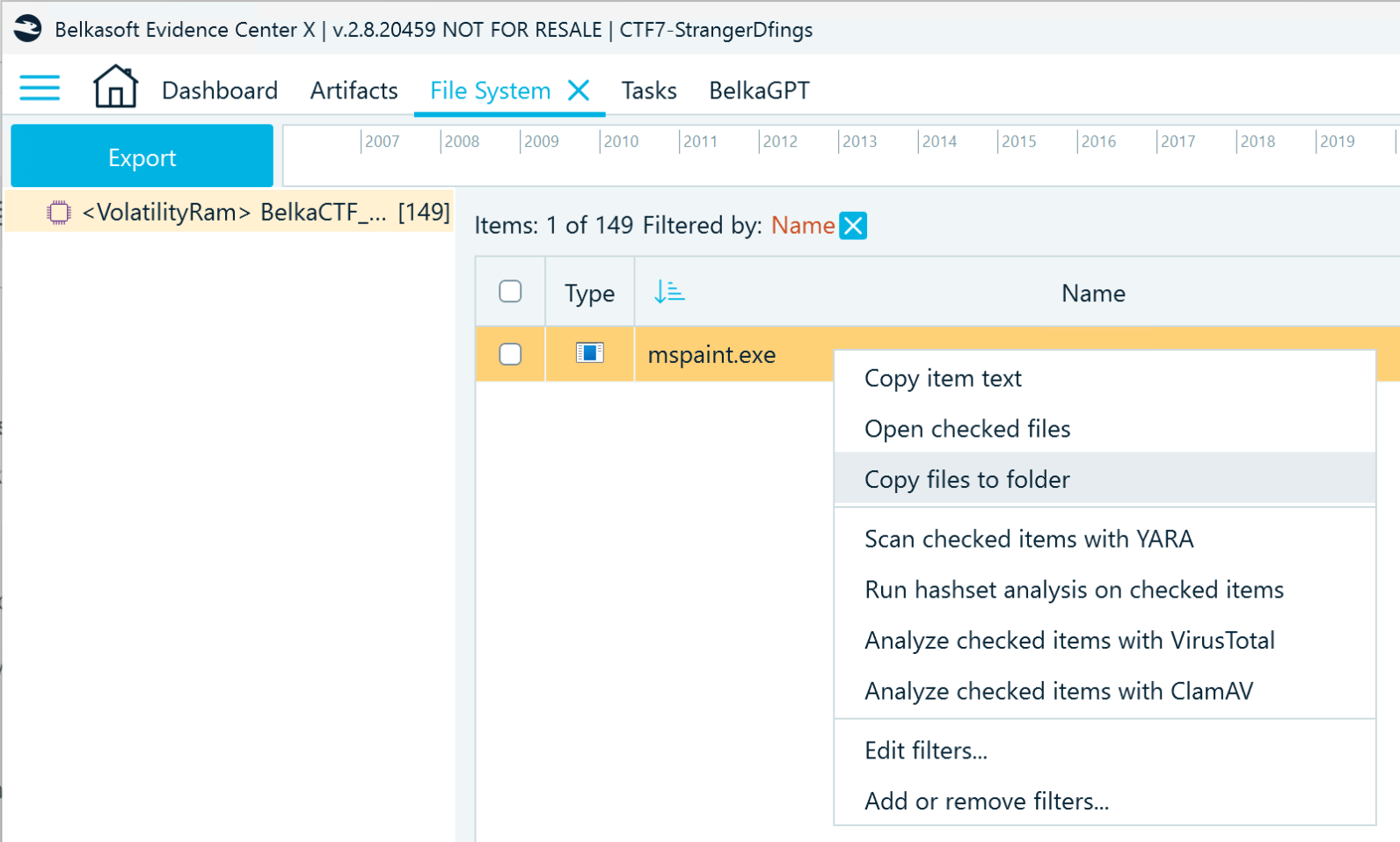
- Add the extracted mspaint.exe process memory as a data source and analyze it with the Carve all space option enabled. Then, inspect the discovered pictures:
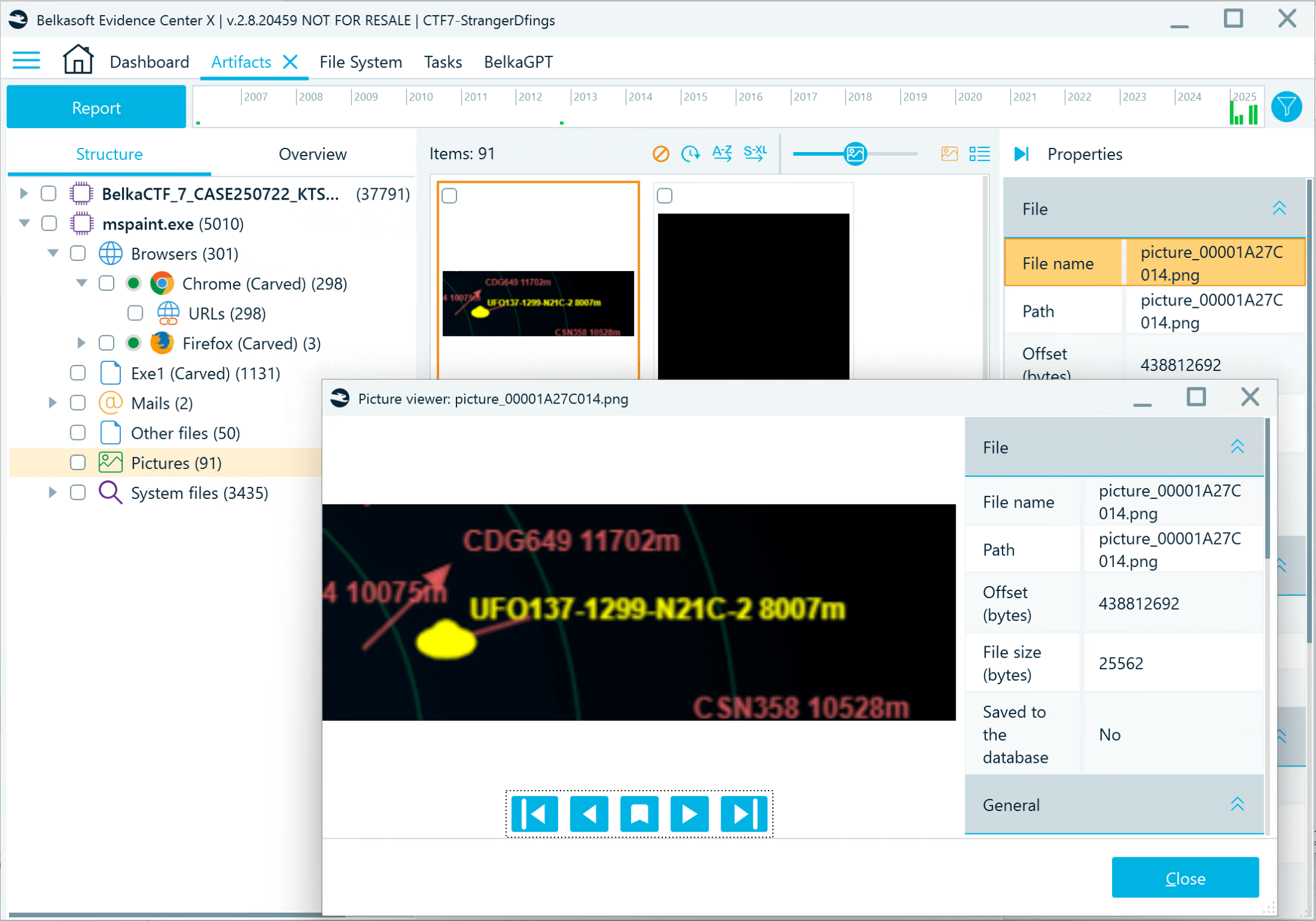
Flag
UFO137-1299-N21C-2
20. Fly-by (Hard)
Question
What identification number is painted on board of the aliens' spacecraft?
Solution
- The detects table contains the ts field with the timestamps of aircraft detections. Choose a point in time when three of the radars detected the spacecraft. Then pull the azimuth and add radar location details from the radars table:
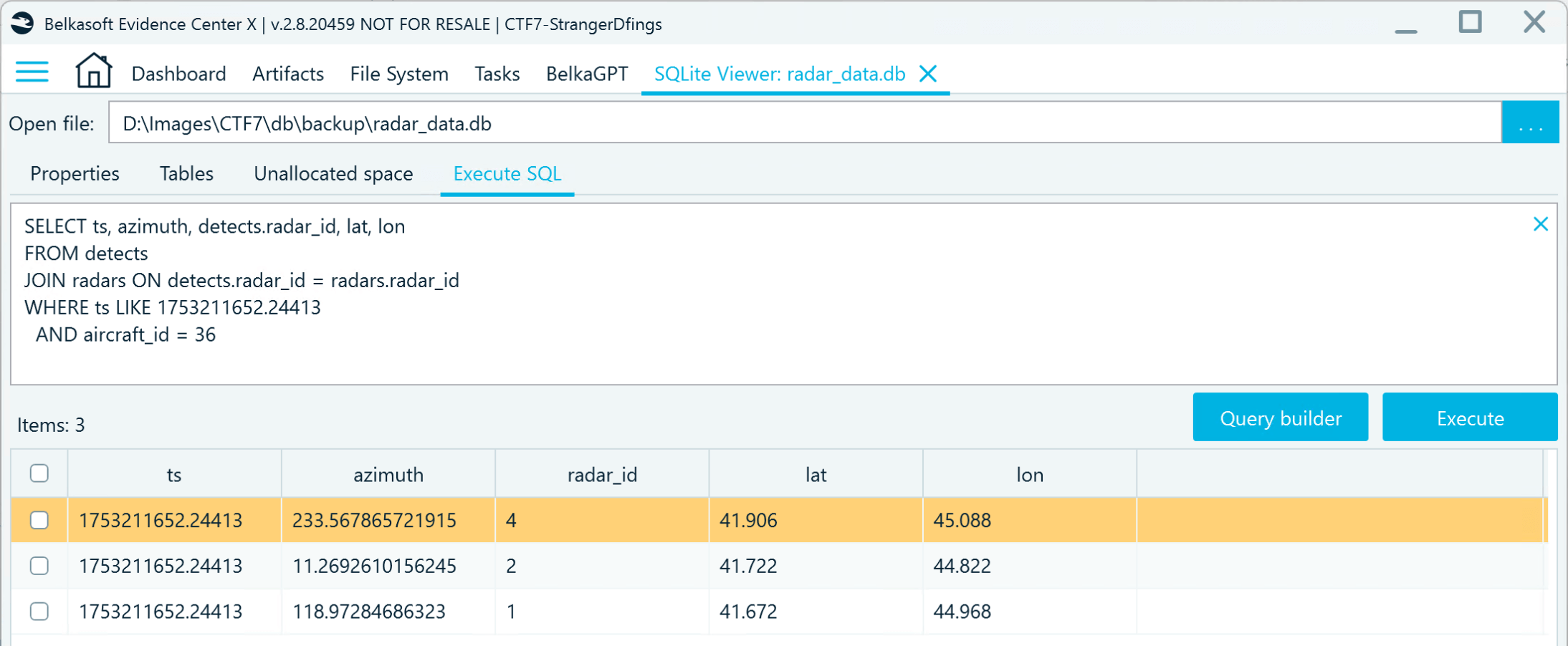
- Visualize your findings on a map service to identify the exact location of the UFO:
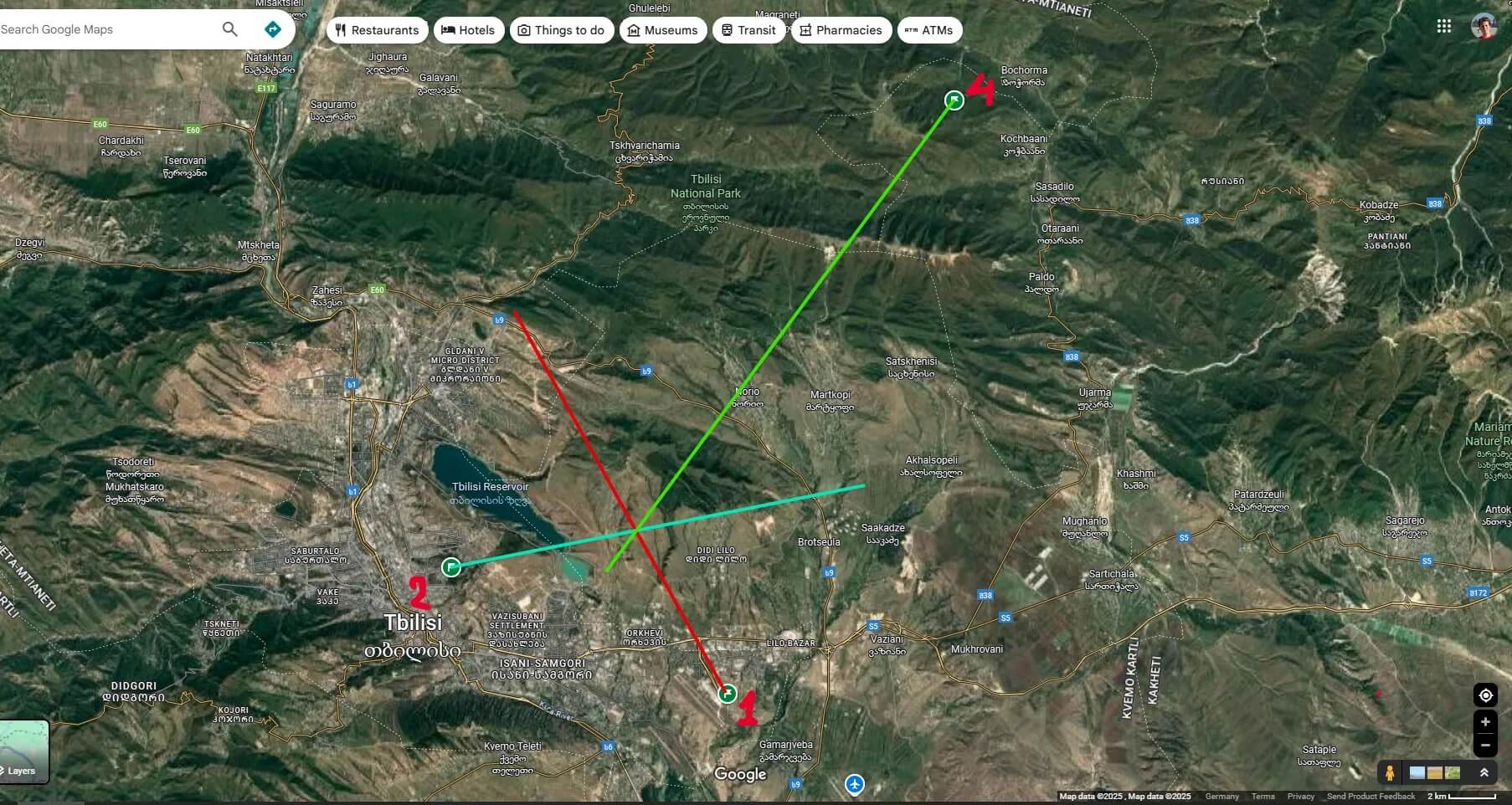
- Request the point coordinates:
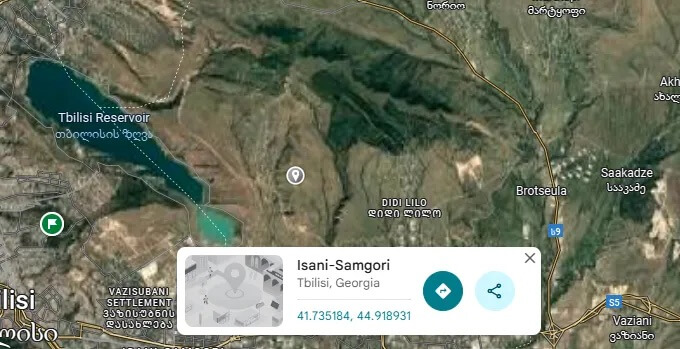
- Go to https://spysatarchive.nsa.fyi/ to request the satellite picture of this location at the time you selected in the database (in our example, 1753211652 = 22 Jul 2025 19:14:12 UTC).
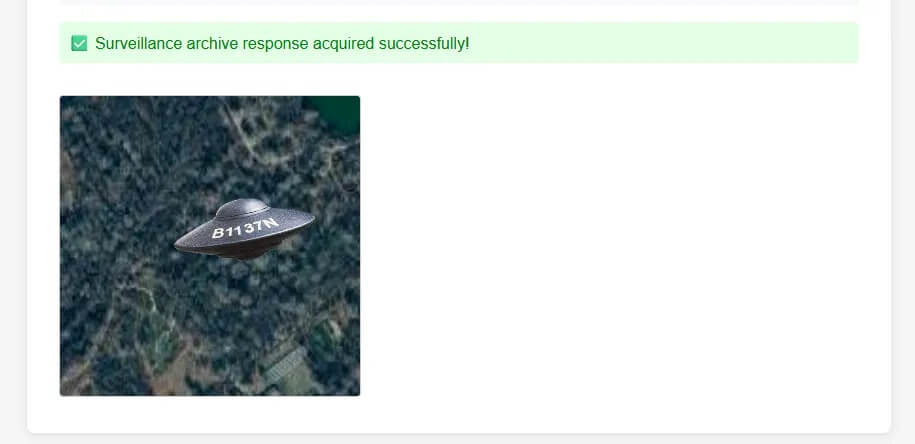
Flag
B1137N
21. Inside (Baby)
Question
Where is the aliens' craft parked right now?
Solution
Now that you have the aliens' VPN network password, you can use the OpenVPN config file you have extracted from Wi-Fi traffic to access their infrastructure.
- Install OpenVPN GUI and place the client.conf file to the application configuration folder (for example, C:\Program Files\OpenVPN\config). Rename the file to client.ovpn.
- Launch OpenVPN GUI and log in with any usernmame and the password from the previous task:
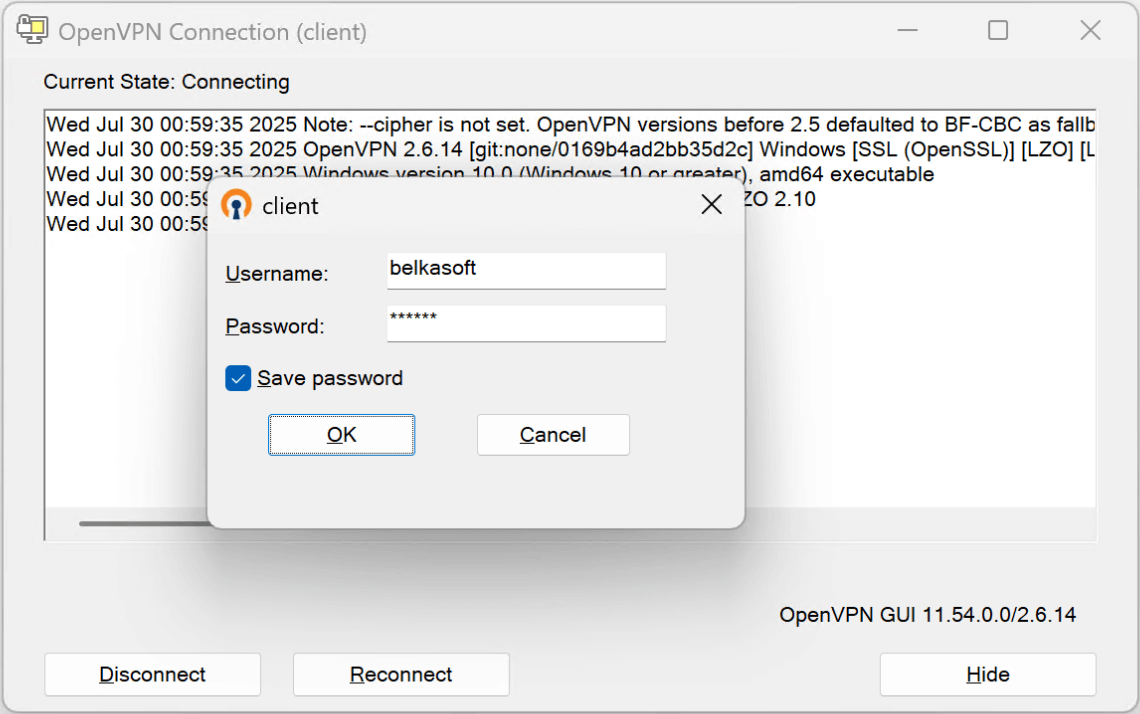
- Run the route print command to review the VPN routes and locate the VPN server address:
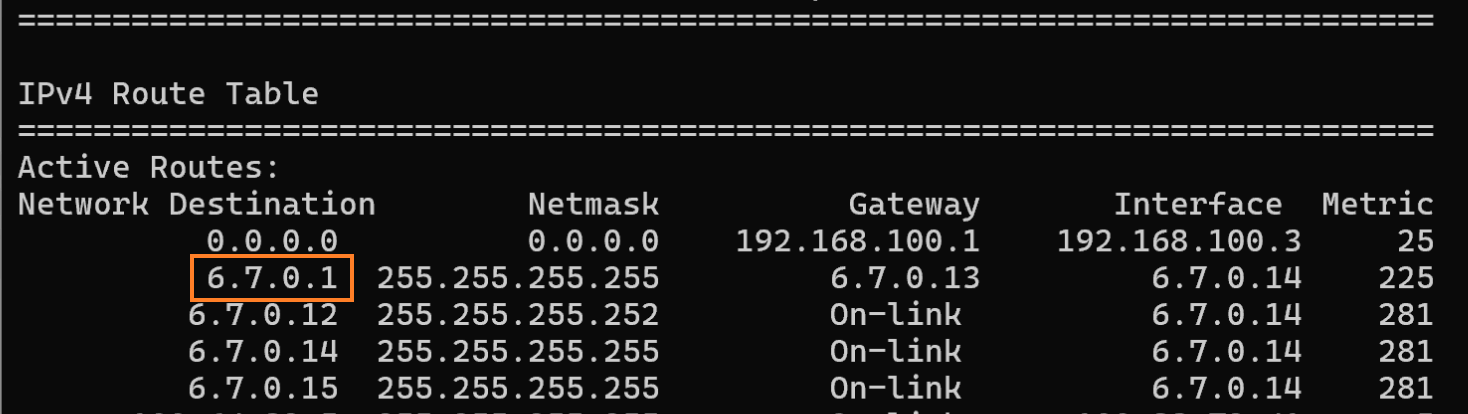
- Navigate to http://6.7.0.1. Now you are inside the mothership. Go to the Find My Drone tab and locate the spacecraft you have been looking for:
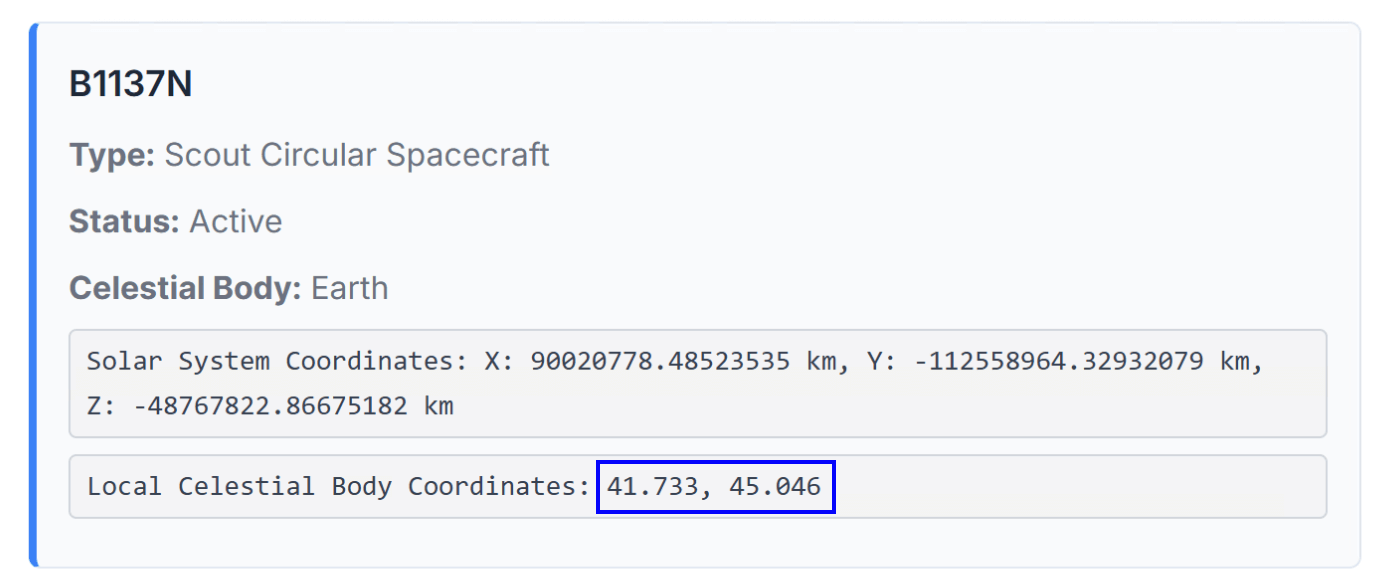
Flag
41.733,45.046
22. Salvation (Warmup)
Question
To save the Earth we need to instead point the beam at something useless... How about Pluto?
Solution
- Now you need to roll up your sleeves and save the Earth from destruction. First, explore the page source code. You can spot that the targets are identified with the icrs-x, y, z coordinates, which are used by the barycentric celestial reference system.
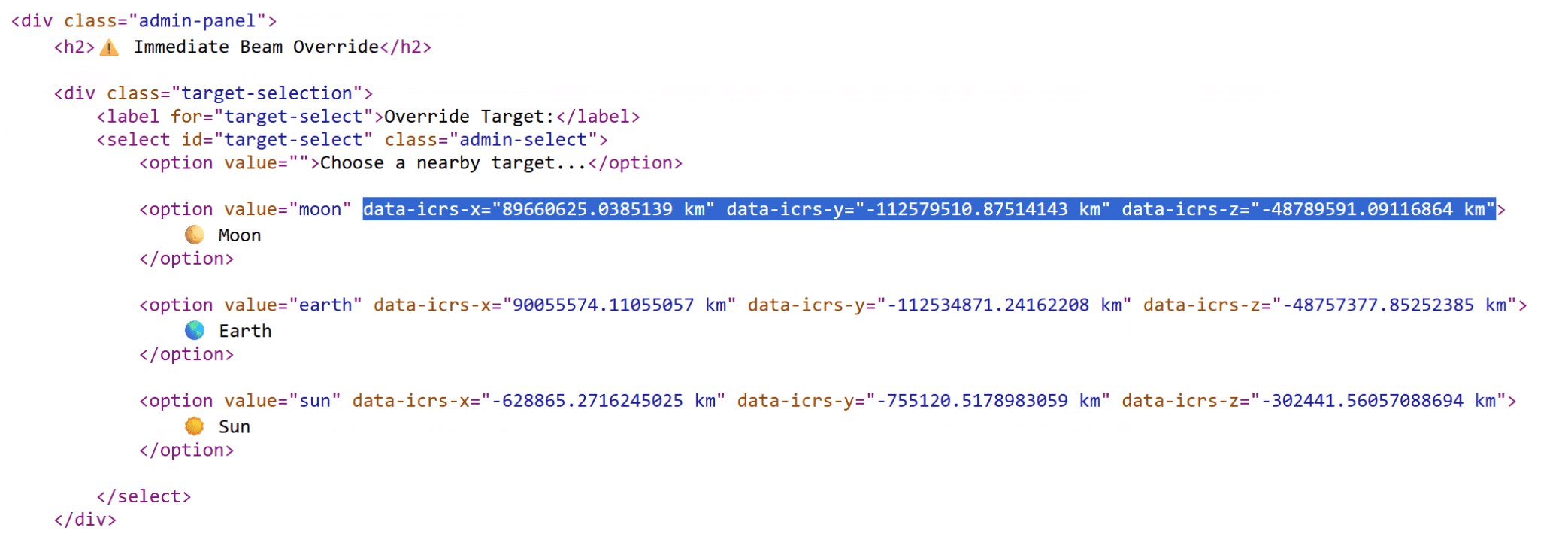
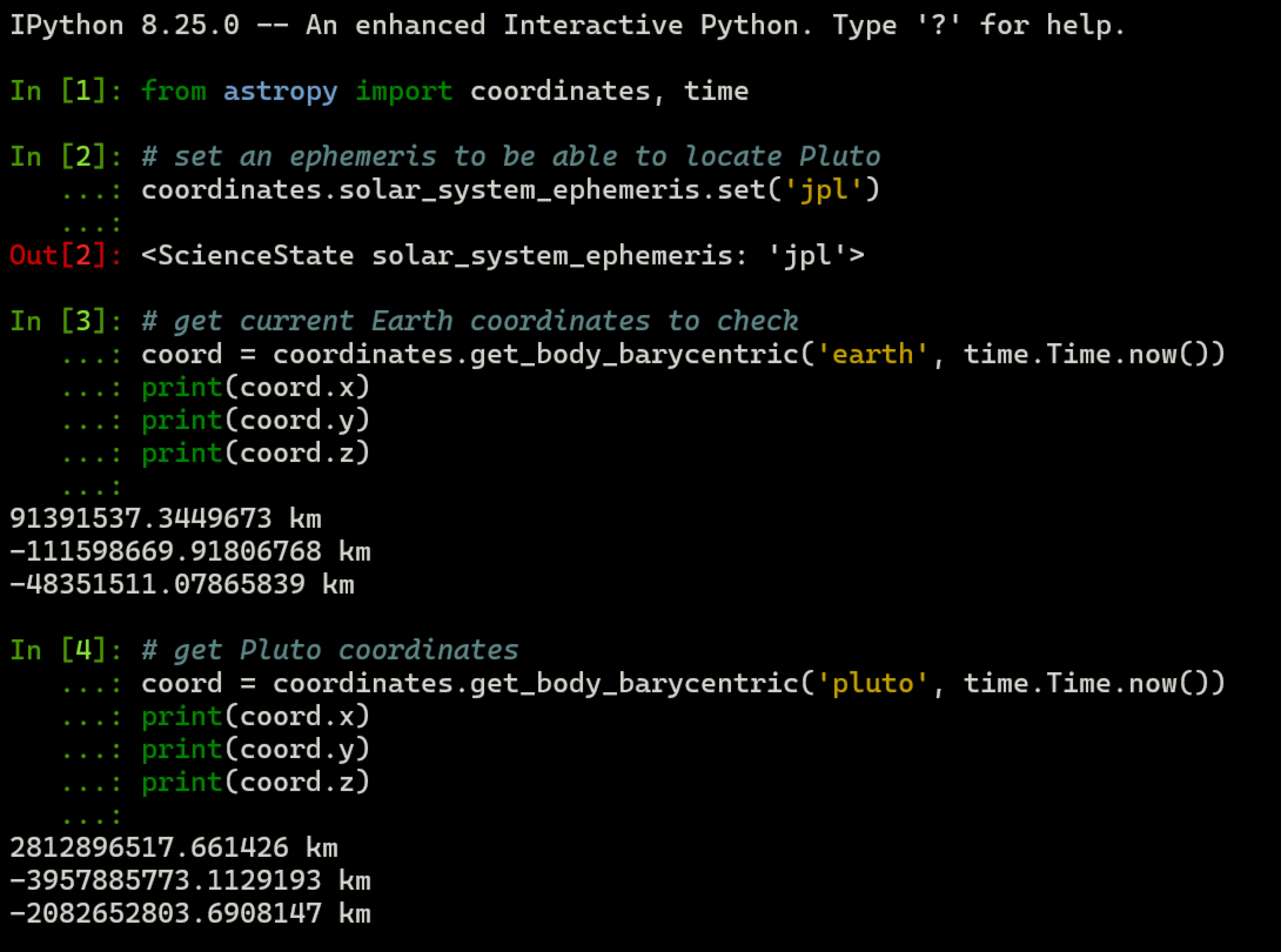
- To get the coordinates for Pluto, you will need to calculate its current location. You can do it with the astropy library. Compare some known coordinates, e.g. of Earth, to verify that you're using the correct coordinate system.
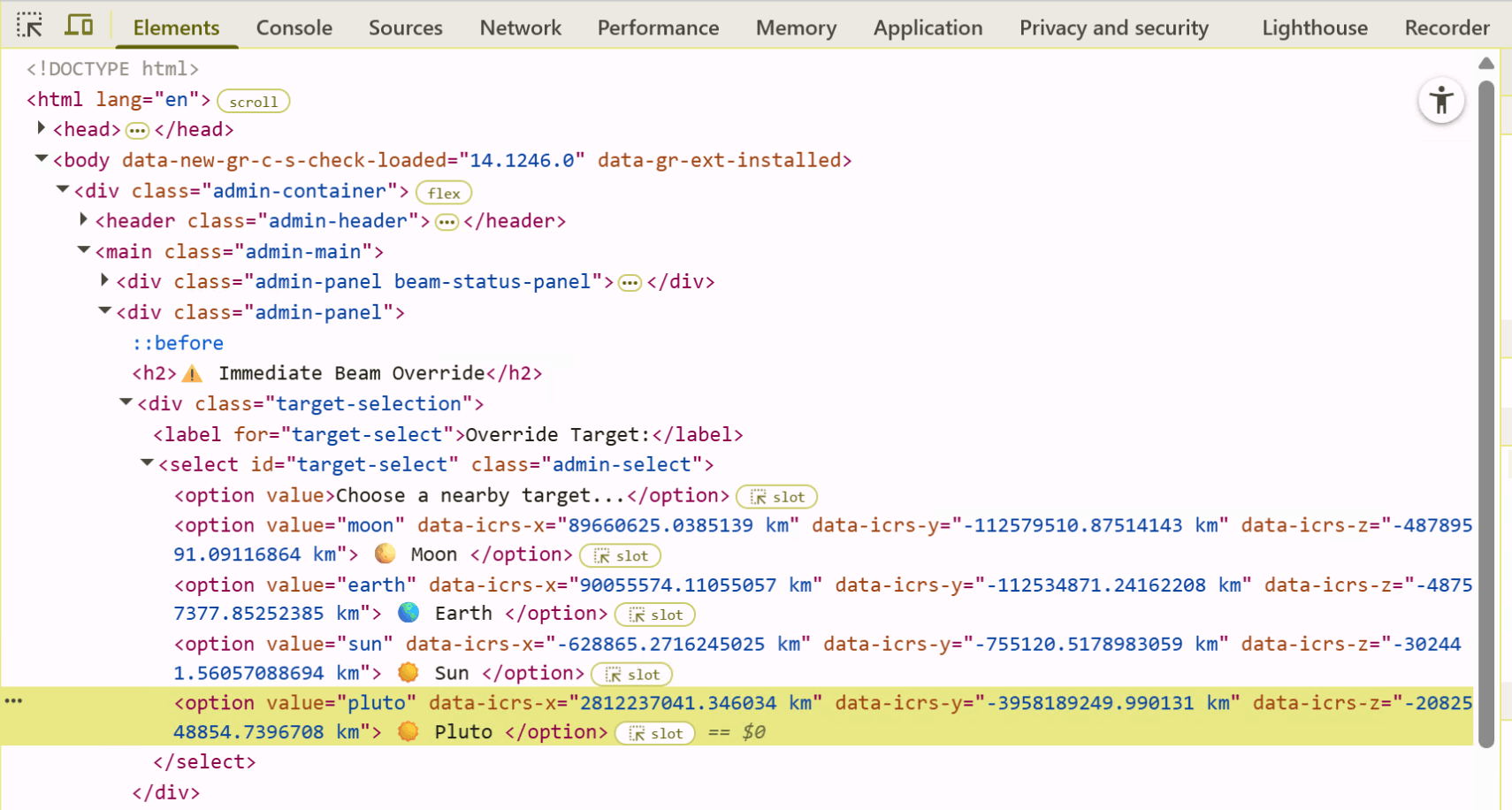
- After you get the coordinates, you can edit the web page to add the Pluto option to the beam override list. Go to developer tools in your browser, and insert the element with Pluto's current coordinates into the page code.
- Then select the Pluto option and activate the beam. Celebrate!
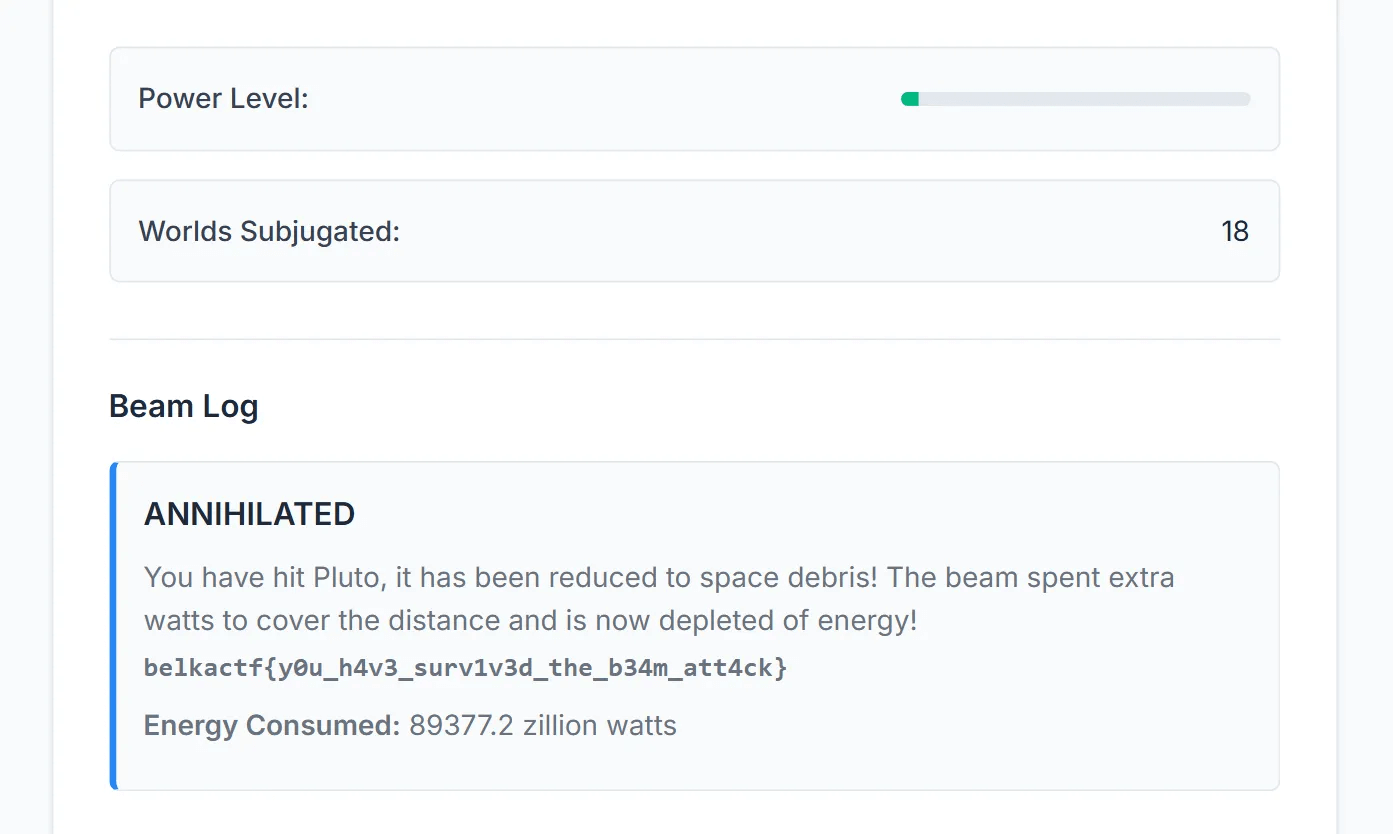
Flag
belkactf{y0u_h4v3_surv1v3d_the_b34m_att4ck}
We hope you enjoyed the "Stranger Dfings" CTF. If so, please share your writeups and feedback via your social media accounts using the #BelkaCTF tag. See you next time!
See also:
- Enjoy past Belkasoft CTFs
- Learn more on the Belkasoft X product used for this write-up
- See Belkasoft's webinars on digital forensics and cyber incident response
- A Uni student or a professor? Check out our academic page!


