Android System Artifacts: Forensic Analysis of Application Usage
In mobile forensics, application artifacts are often the most significant. They contain valuable and relatively easy-to-interpret information. However, if these artifacts do not provide the expected evidence, deeper research may be necessary. This is where system files, which contain information about the device and application usage, can be instrumental in finding the clues.
In this article, we will overview several forensically interesting Android system artifacts associated with application usage:
- Application installation and updates (frosting.db, packages.xml)
- Searches in the Google Play Store (suggestions.db)
- User accounts used with applications (accounts_ce.db and accounts_de.db)
- Application usage statistics (app_usage_stats.xml)
- Application and device usage events (app_usage, dwbCommon.db)
- Application and device activities (reflection_gel_events.db)
We will explain how to examine these artifacts in Belkasoft X and provide tips on using them in digital investigations.
Note that, as part of the system files, all the artifacts we are going to discuss are only available in "file system copy" images of Android devices. You can learn how to obtain such an image in our article on Android device acquisition methods.
One more caveat is that due to the diversity of the Android operating system flavors, some of the files may be empty or absent in certain device models.
Application installations and updates (frosting.db)
Android users can install applications from the Google Play Store and other sources. When an application is installed or updated, the system records this event into the frosting.db SQLite database located in the following folder:
..\data\data\com.android.vending\databases
When analyzing Android artifacts in Belkasoft X, you can find the records from this database in the Artifacts window on the Structure tab under System files → frosting.db → Android app updates. This artifact profile reveals the applications installed on the device at the time of the acquisition, their resource folder location on the file system, and the time they were installed or last updated.
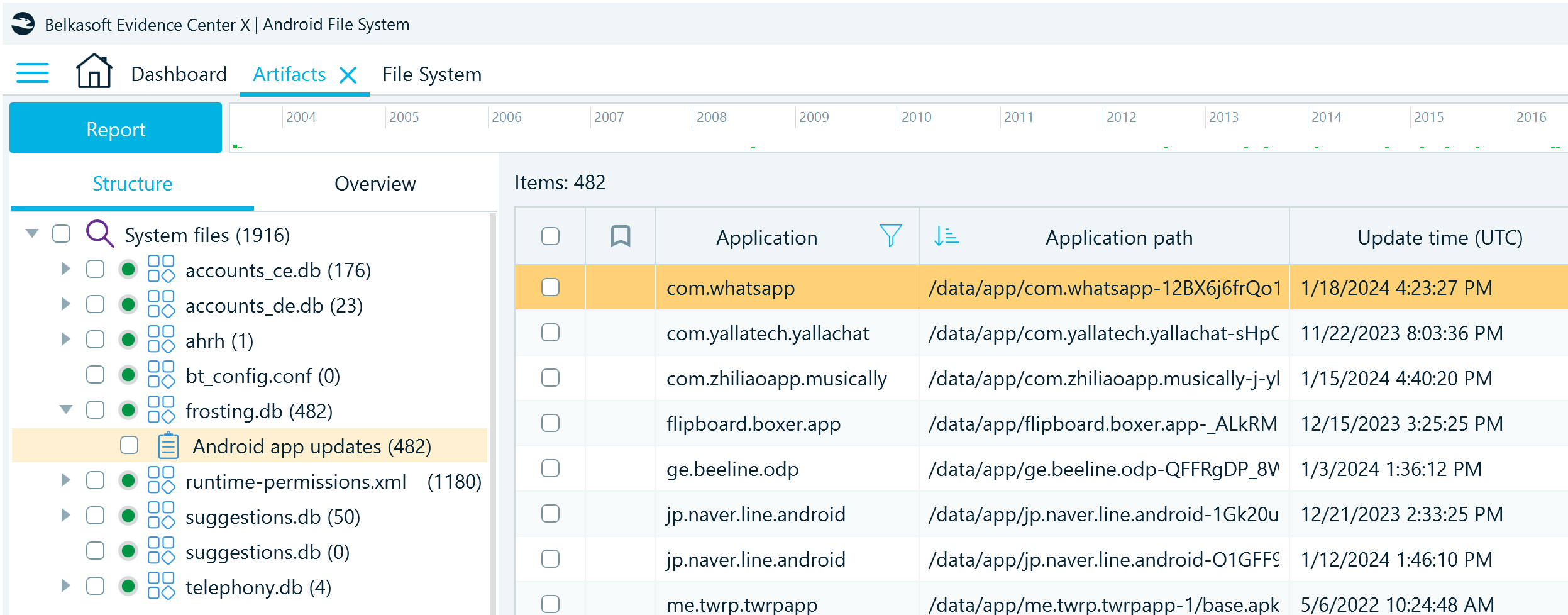
The frosting.db artifacts provide information about applications on an Android device, including those installed from the Google Play Store and other sources. They can be valuable in digital investigations for locating and identifying sideloaded, and thus potentially suspicious applications.
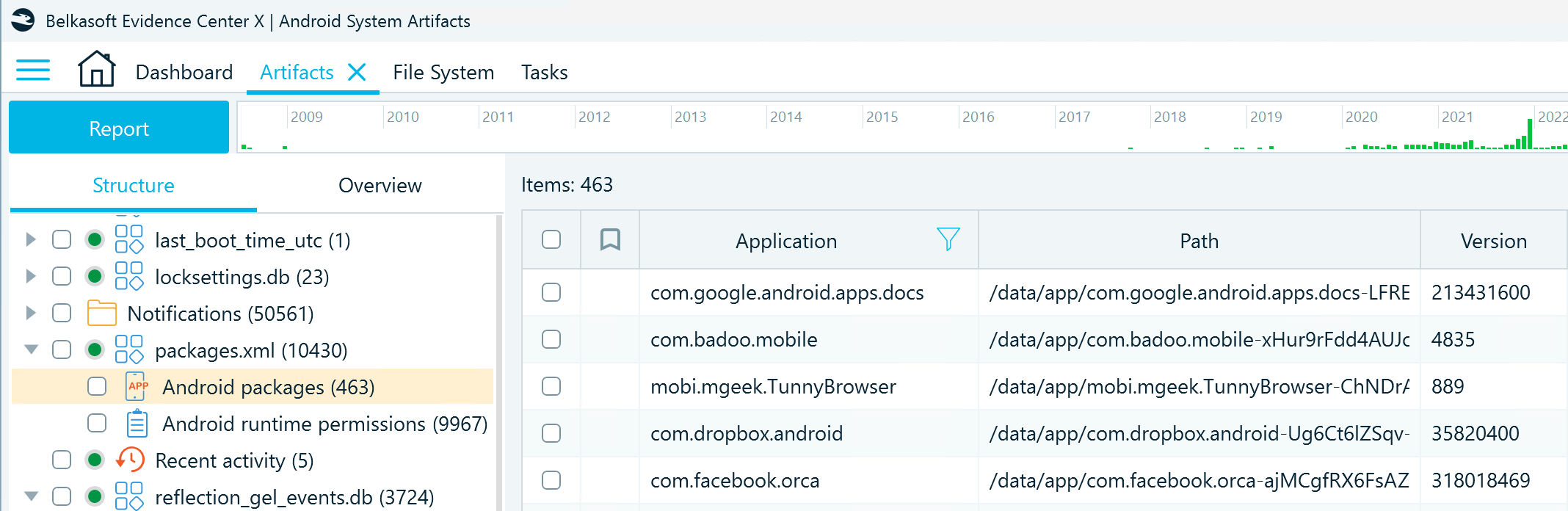
One more Android system file that includes similar details is packages.xml located in ..\data\system. In addition to the records of the installed applications, it also contains the last installed version and the information on the permissions assigned to the applications, such as access to the camera, microphone, or other resources on the device. In Belkasoft X, you can find this artifact profile under System files → packages.xml → Android packages:
Google Play Store searches
When Android users look for applications in the Google Play Store, the system records their searches into the suggestions.db SQLite database stored in the following folder:
..\data\data\com.android.vending\databases
In Belkasoft X, you can locate the artifacts from this database in the Artifacts window on the Structure tab under System files → suggestions.db → Google Play searches. They provide the details of the application suggestions displayed to the users and the associated timestamps:
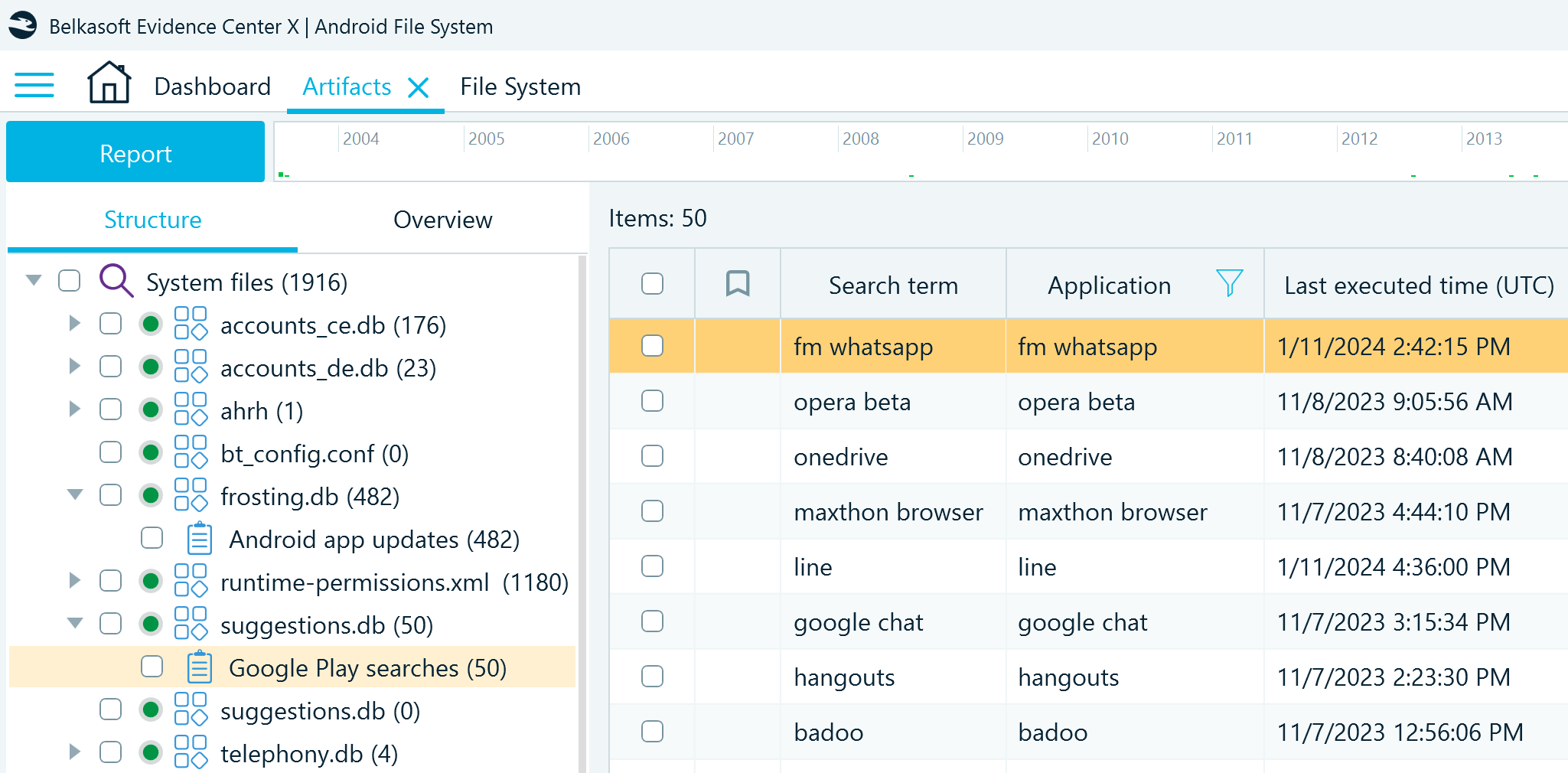
The suggestions.db artifacts can reveal the device user's activity in Google Play and contribute to building the timeline of events in digital investigations.
User accounts
Mobile applications that provide access to online services (like messengers, social networking apps, and email agents) typically require users to create an account. To facilitate repeated access to applications, Android devices store users' application account details, including login credentials, account IDs, authentication tokens, and more. In an Android file system copy, you can find these records in SQLite databases stored in the following locations:
..\data\system_ce\%USERNUMBER%\accounts_ce.db
..\data\system_de\%USERNUMBER%\accounts_de.db
In Belkasoft X, you can find these database profiles in the Artifacts window on the Structure tab under System files:
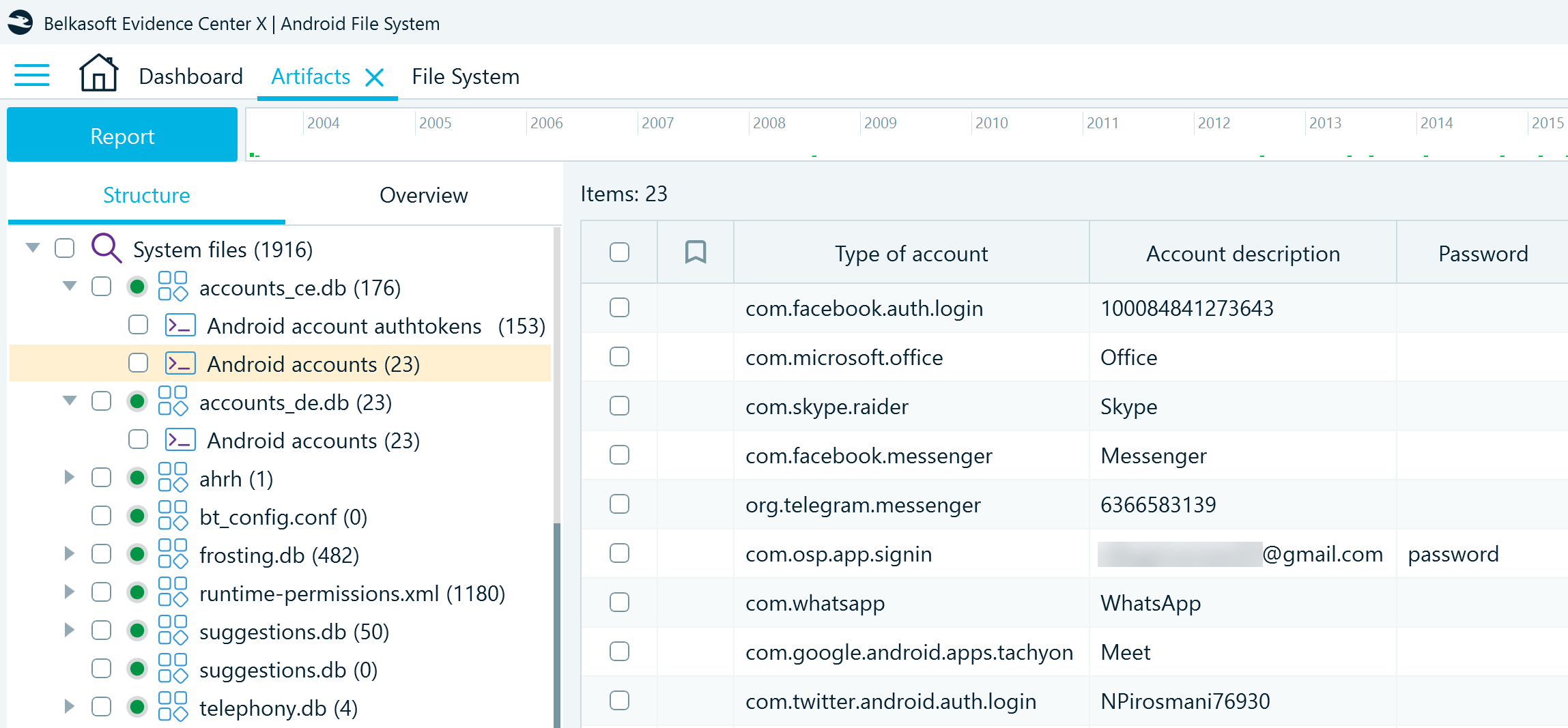
The accounts_ce.db → Android accounts profile includes details of the application accounts used on the device:
- Type of account specifies the ID of the application associated with the account
- Account description includes the user's account ID; this description may be different depending on how the application identifies users (for example, it may be the user's login name, email, internal ID number, a generic application description, and so on)
- Password may include an encrypted account password or its generic description
The accounts_ce.db → Android account authtokens profile displays the application accounts that use tokens for user authentication. The notable column to inspect here is Authtoken type. It includes token configuration data that may reveal the applications and services where the user authenticated with their Google account:
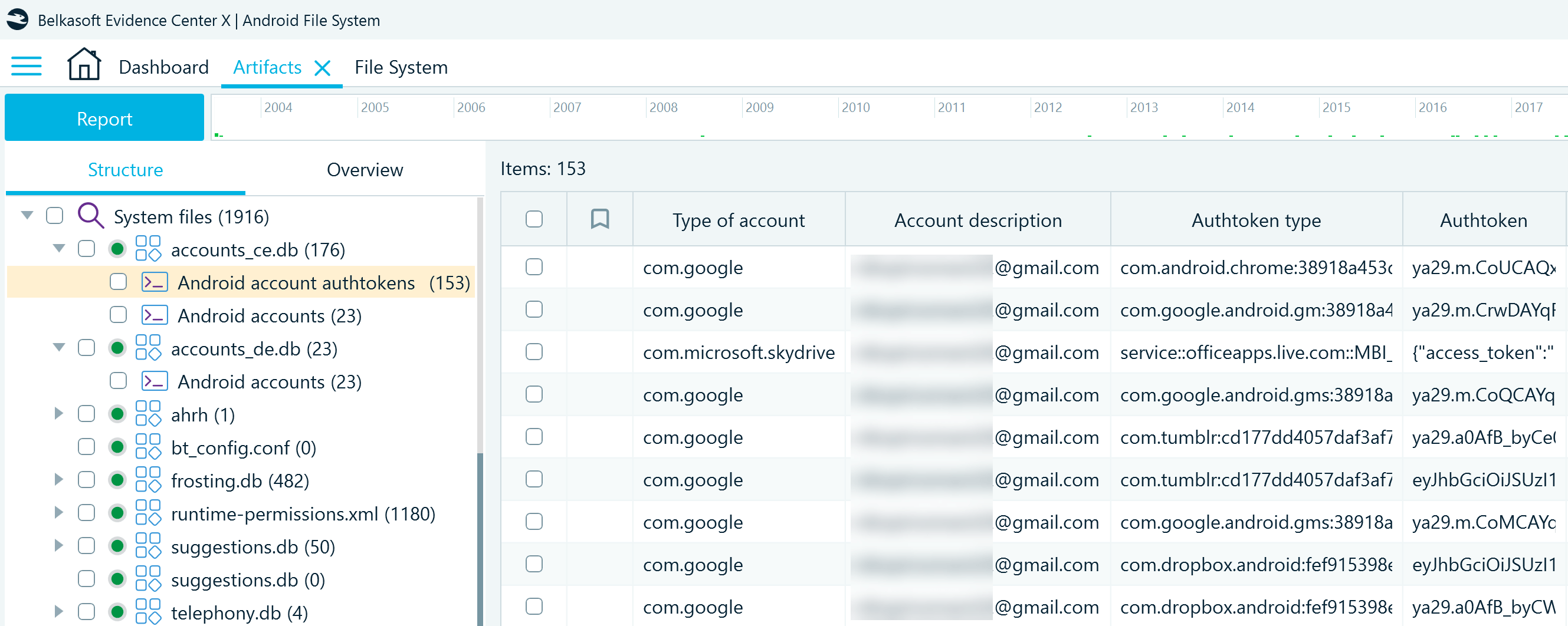
The accounts_de.db → Android accounts profile provides a valuable addition to account data. Last logon time indicates when the user provided their account credentials for the last time:
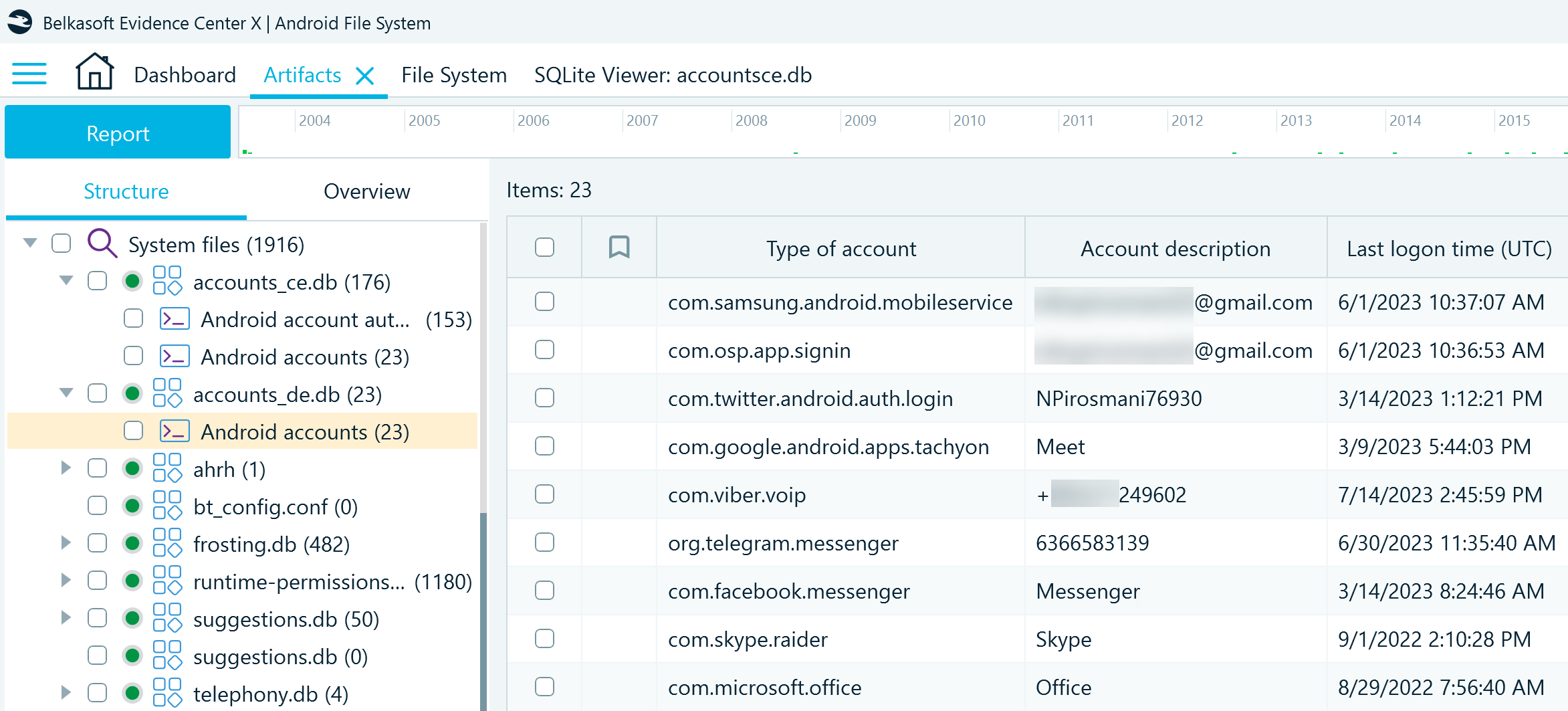
To sum up, the accounts_ce.db and accounts_de.db artifacts can help you determine which applications were in use on the device at the time of the acquisition, the accounts used to log into them, and the last logon time details.
Application usage statistics
The Android OS includes internal services that keep track of hardware and software usage statistics. Among the artifacts generated through device health monitoring, there is the app_usage_stats.xml file containing timestamps of recent activity in various applications. You can find it in the following folder:
..\data\user\%USERNUMBER%\com.google.android.apps.turbo\shared_prefs
In Belkasoft X, you can locate the records from this file in the Artifacts window on the Structure tab under System files → app_usage_stats.xml → Usage statistics. The tool displays the package names of the applications and the recent timestamps of when they were in use.
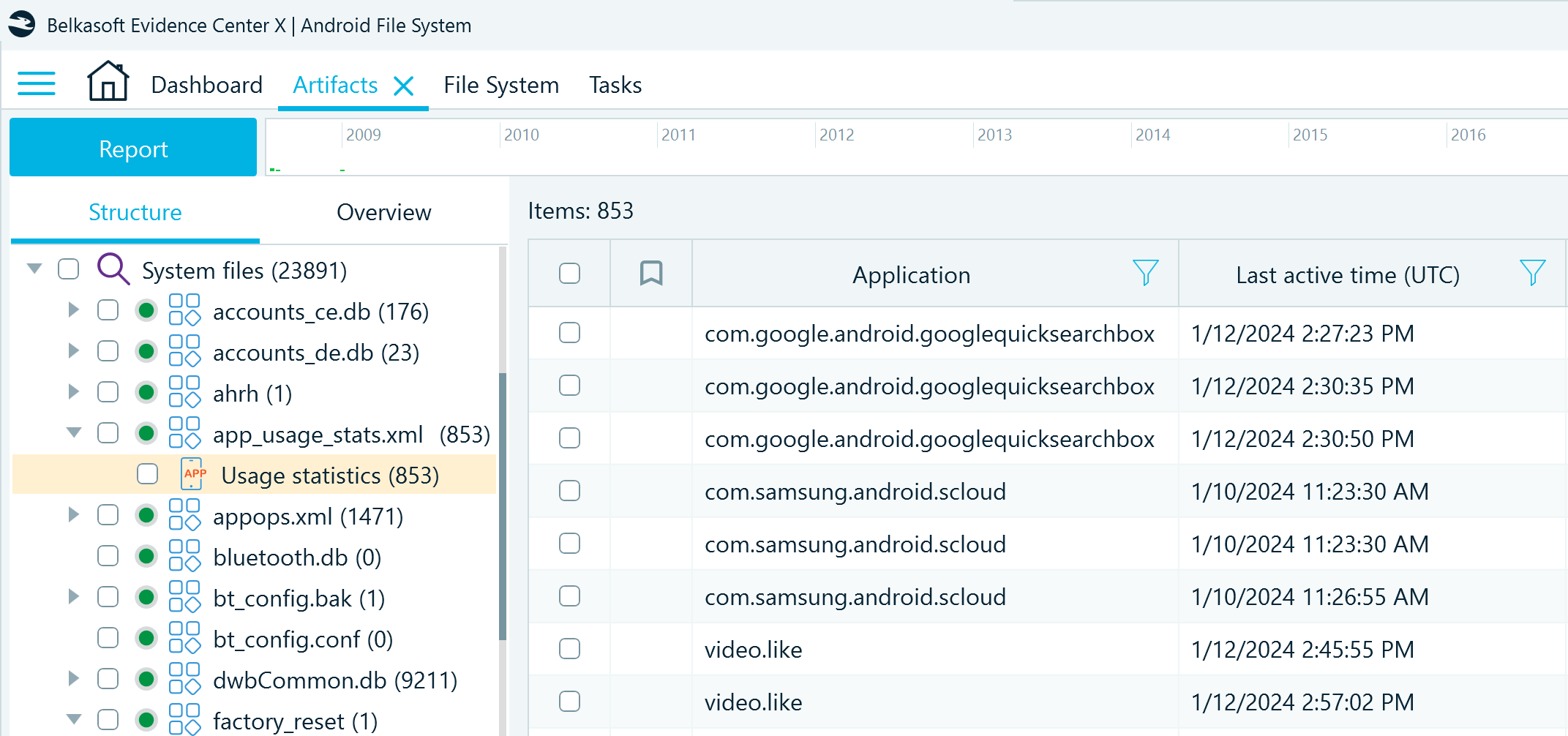
The app_usage_stats.xml artifacts can help build a timeline of events and establish patterns of behavior that may be relevant to the investigation. However, it keeps records for a limited time period.
Application and device usage events
Many Android devices include the Digital Wellbeing service that collects usage statistics and provides users with insights into their interactions with the device and the time spent in various applications. Most devices store data recorded by this service in the app_usage SQLite database located in the following folder
..\data\data\com.google.android.apps.wellbeing\databases
Samsung devices store similar data in dwbCommon.db located in the below folder:
..\data\data\com.samsung.android.forest\databases
In Belkasoft X, you can find Digital Wellbeing data in the Artifacts window on the Structure tab. Navigate to System files → app_usage → Digital Wellbeing or System files → dwbCommon.db → Digital Wellbeing, depending on the extracted device model:
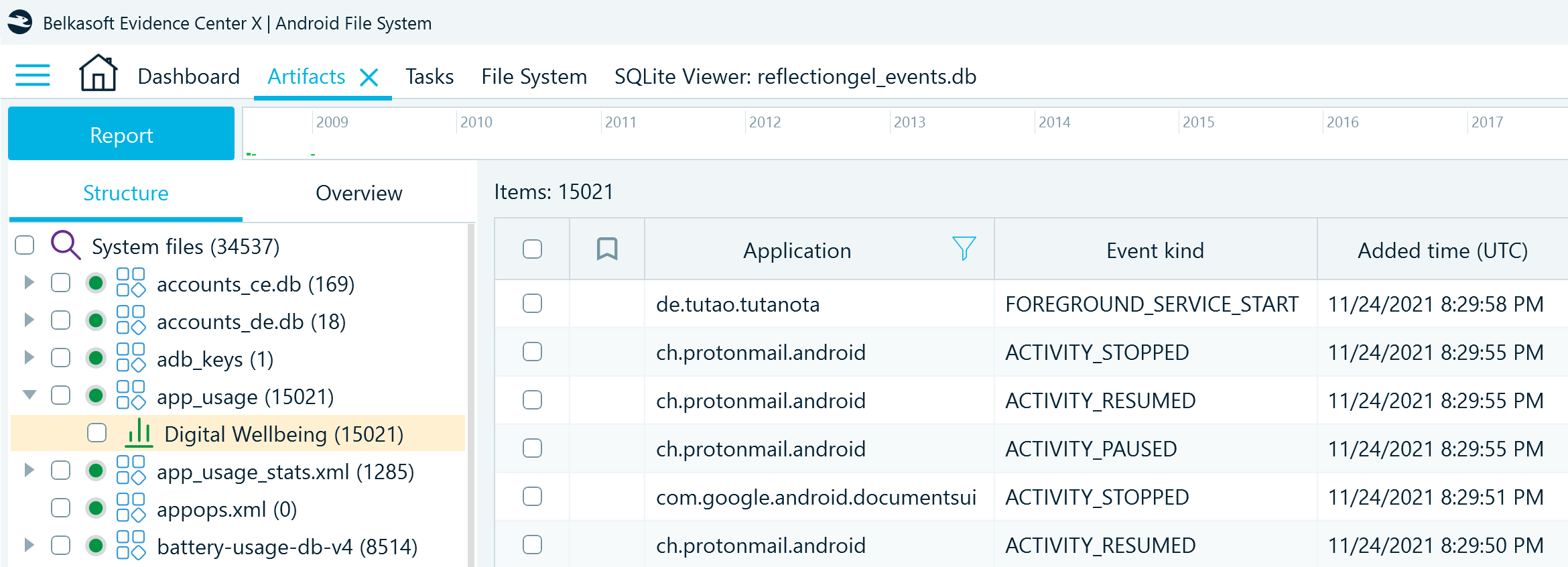
The profile displays the records of the device and application events, including their timestamps. For example, ACTIVITY_RESUMED indicates that an application was moved to the foreground, meaning that it was in active use at a specified moment. You can find descriptions of events in Android developer documentation.
The range of events recorded by Digital Wellbeing services varies depending on the device manufacturer. For instance, on some devices, such as Samsung phones and tablets, you can additionally find details on when the device was powered on (DEVICE_STARTUP) or off (DEVICE_SHUTDOWN), and when it displayed the lock screen (KEYGUARD_SHOWN):
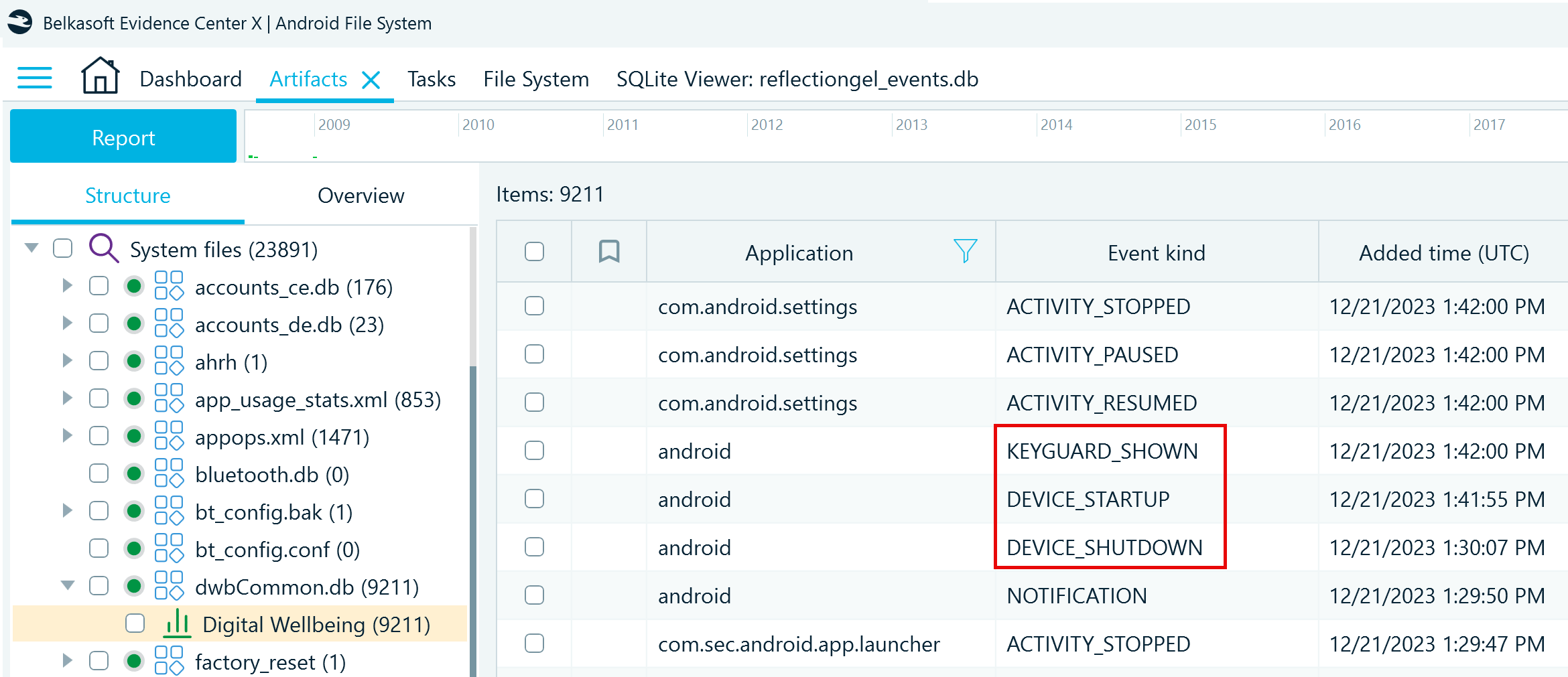
Digital Wellbeing records can add precision to the timeline of events in an investigation as they provide information on the application and device states at certain periods of time.
Nonetheless, there are a few caveats you should consider when examining these artifacts:
- Device owners can opt out of sharing their usage statistics. The absence of Digital Wellbeing records does not mean that the user did not interact with the device and applications.
- Not all event records imply the user's interaction with the device. For example, some NOTIFICATION records may indicate internal communication events that are not visible to the user. DEVICE_SHUTDOWN may both suggest that the user turned the device off and that the device battery ran out.
- Like app_usage_stats.xml, Digital Wellbeing records only include recent activities.
Application and device activities
One more interesting database with detailed records of application and device usage is reflection_gel_events.db. It stores information used by Device Personalization Services (DPS) that collect various usage statistics to predict and suggest apps and content to the user. The noteworthy property of this database is that it may keep records of the applications that were deleted from the device.
The reflection_gel_events.db file is located in the following folder:
..\data\data\com.google.android.as\databases
In Belkasoft X, you can find DPS records in the Artifacts window on the Structure tab under System files → reflection_gel_events.db → Device Personalization Services. This artifact profile displays the timestamps of the activities and the applications in use. After the slash (/) sign in the application records, you can find the details of the activities that may help identify what exactly the user was doing:
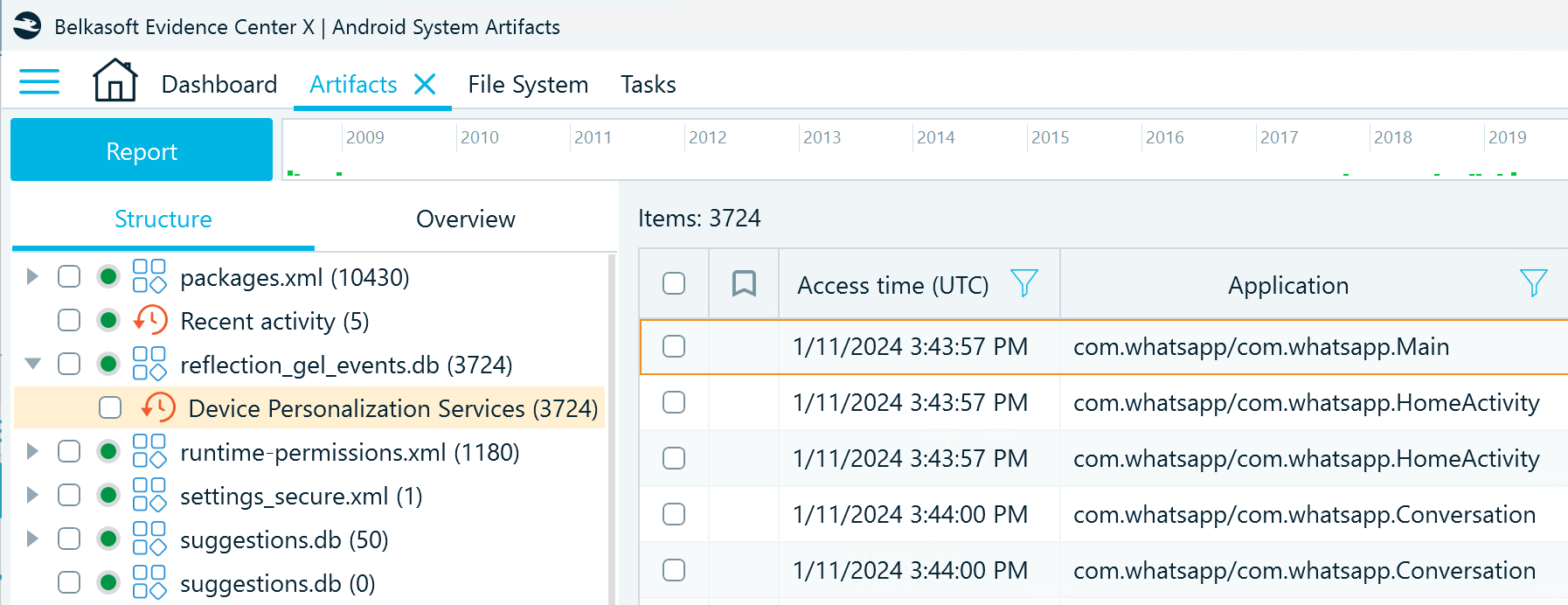
The reflection_gel_events.db artifacts can help establish a detailed timeline of events on the device in a larger time frame than Digital Wellbeing records. There is no exact information on how long it preserves the records, but our test device included about a year of data. However, Android devices that use Device Personalization Services allow users to control data collection, so they may clear this database at a certain point.
Conclusion
Android system artifacts related to application usage can provide an additional perspective on users' activities in digital forensic investigations. They reveal the applications installed on a device, usage events and timestamps, account details, Google Play searches, and more. This information helps establish timelines and patterns of user behavior.
System files store information in various formats and folders. A digital forensics tool capable of locating and extracting this data significantly enhances the investigation process. Belkasoft X supports the acquisition of the required image type that includes these files and the automatic extraction of a wide range of Android system artifacts, allowing you to focus on uncovering critical evidence.

