Android System Artifacts: Forensic Analysis of Device Information and Usage
The Android operating system governs multiple processes on devices: besides providing a platform for applications, it tracks user accounts and settings, creates logs, and collects various application and device usage statistics, saving this information into system files. In digital forensic investigations, these files help uncover detailed records of activities on the device and corroborate other findings.
Android system files can be very useful, but they are also not that easy to obtain. As such files are typically only available in the file system copy image of a device, you need digital forensics tools for the acquisition and analysis of digital data.
In this article, we will overview several forensically interesting Android system artifacts that include device information and keep track of various usage statistics:
- Device property artifacts (settings_secure.xml, version, last_boot_time_utc, and more)
- SIM card details (telephony.db)
- Device battery usage (turbo.db)
- Battery usage by apps (battery-usage-db-v4)
- Battery usage by Bluetooth (bluetooth.db)
- Paired Bluetooth devices (bt_config.conf)
- Lock screen settings (locksettings.db)
- ADB connections (ADB_keys)
We will showcase the details these artifacts can provide using Belkasoft X software and offer insights into leveraging them in your digital forensics and cyber incident response investigations.
Note that due to the diversity of Android devices and operating system flavors, there is no standard set of system artifacts that are consistently available and populated with data. The files we are going to discuss may be absent or empty on device models where the manufacturer does not use them.
Device properties
In Belkasoft X, you can begin examining Android system artifacts by reviewing the properties of the acquired device in the "File System" window (later in the section, we will explain where to find them on the file system if you do not have a digital forensics tool).
In the tree view, right-click the image data source node and select Show properties:
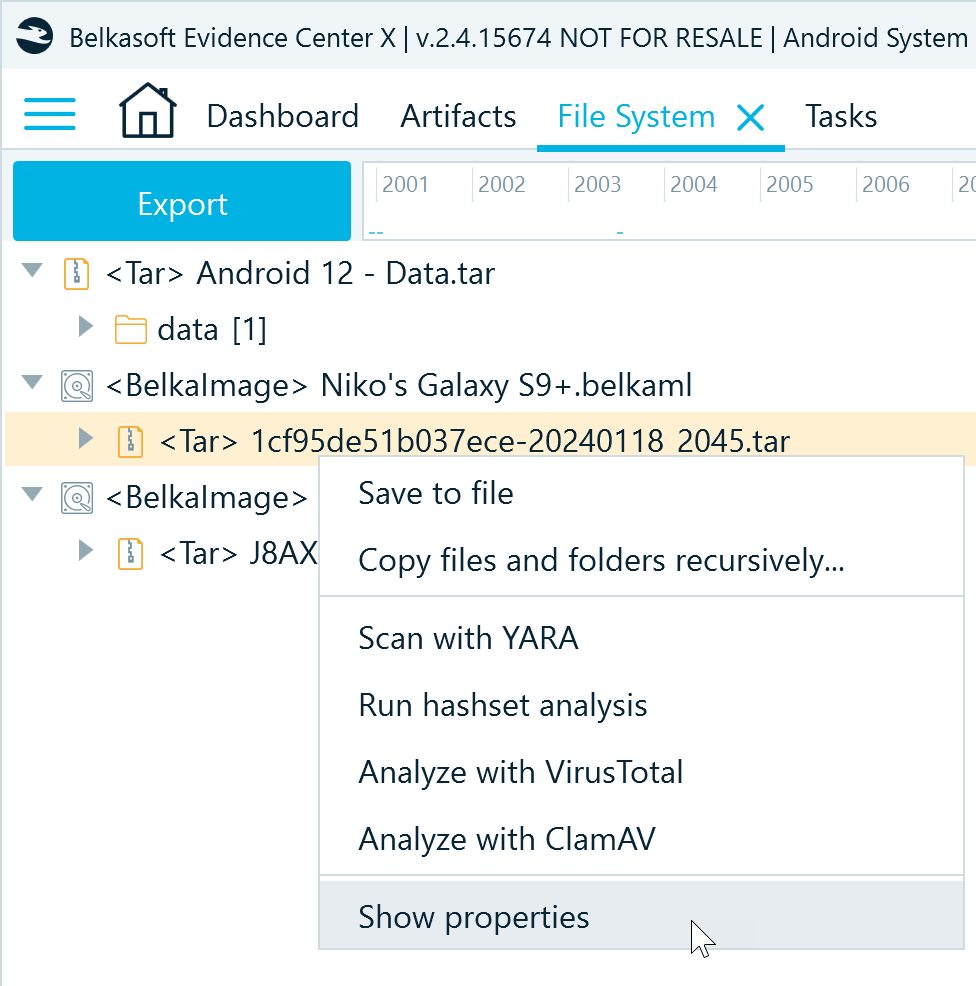
The set of details you can find in the Device properties dialog depends on the data source type. Logical images like ADB backup typically only include general information about the image whereas file system copy images provide a comprehensive dataset:
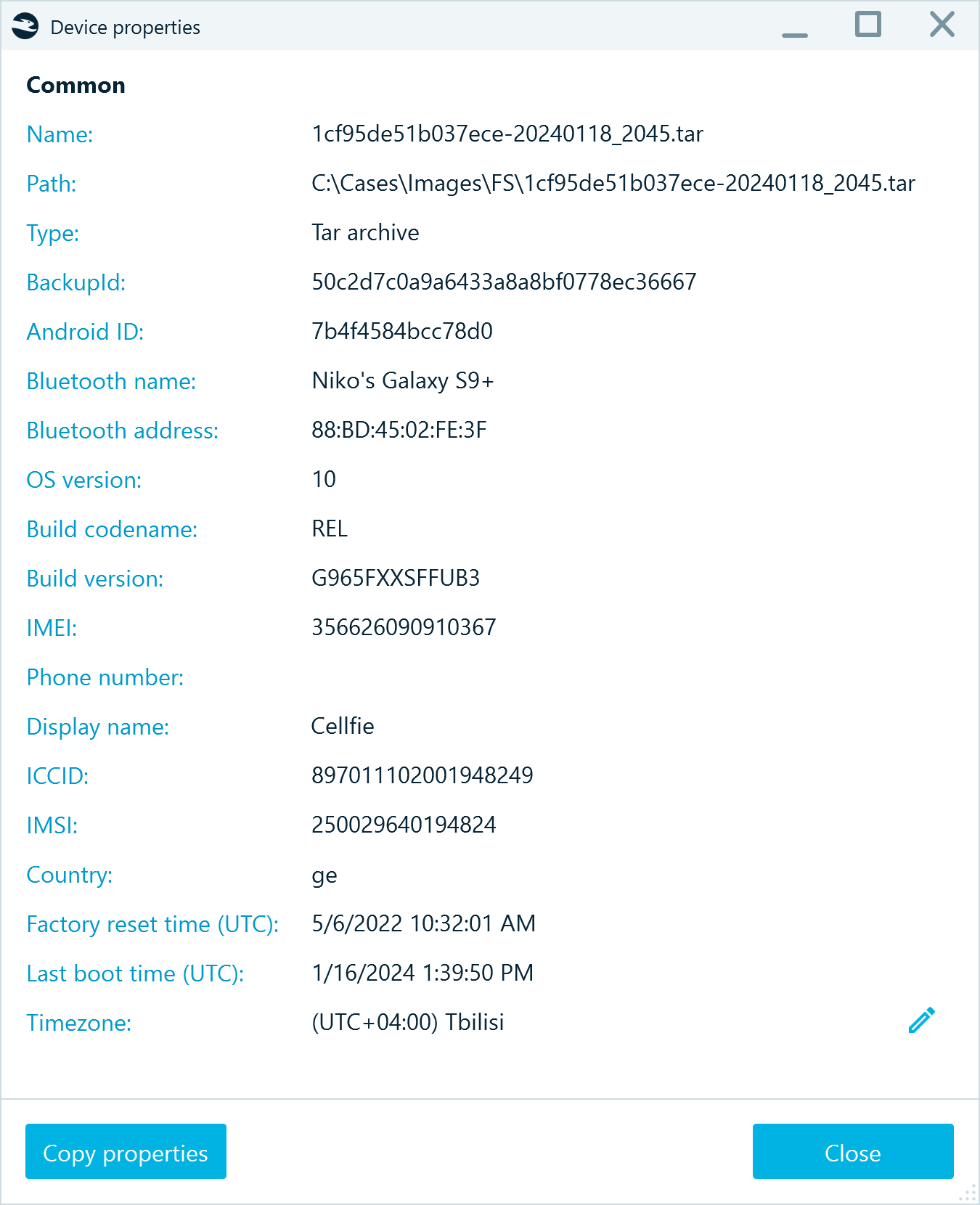
Belkasoft X collects these details about the device from a number of system files:
- Android ID, Bluetooth name, Bluetooth address: ..\data\system\users\%USERNUMBER%\settings_secure.xml
- OS version, Build codename, Build version: ..\data\system\usagestats\%USERNUMBER%\version
- IMEI: ..\data\drm\pvt\ahrh
- Display name, ICCID, IMSI, Country (SIM card details): ..\data\user_de\%USERNUMBER%\com.android.providers.telephony\databases\telephony.db
- Factory reset time (UTC): ..\data\misc\bootstat\factory_reset
- Last boot time (UTC): ..\data\misc\bootstat\last_boot_time_utc
You can also find these and other details summarized in the Artifacts window on the Overview tab under System files → Device info.
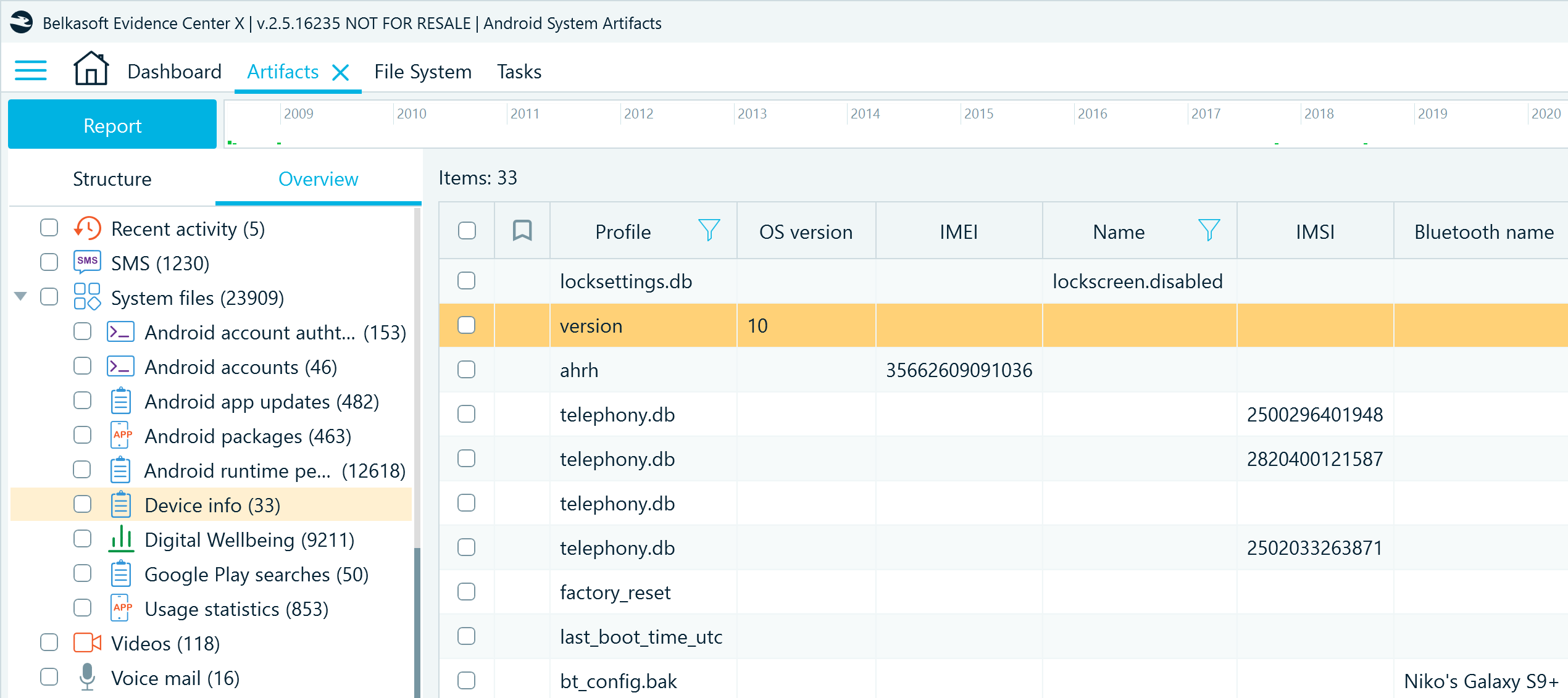
Device information is an indispensable part of digital forensics reports, and having it summarized in one place can help you create them faster.
SIM card details
Details of SIM cards used on an Android device are stored in the telephony.db SQLite database located in the following folder:
..\data\user_de\%USERNUMBER%\com.android.providers.telephony\databases
According to our observations, this database retains records of all SIM cards ever used with the device.
When examining Android system files in Belkasoft X, you can find this artifact in the Artifacts window on the Structure tab under System files → telephony.db → Device info. This profile reveals such details as the code of the country where the SIM card is registered and the mobile carrier name. The Integrated Circuit Card Identification (ICCID) is the unique ID of the card, and the International Mobile Subscriber Identity (IMSI) identifies its carrier.
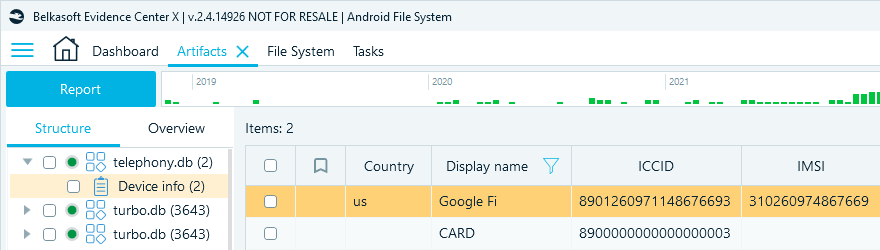
The telephony.db artifact can offer insights into the history of SIM card usage on the device. In digital investigations, it helps identify the SIM card mobile carriers and provides SIM card IDs that can be used to request information about their owners.
Device battery usage
Some models of Android devices (for example, Google Pixel) log battery statistics and keep several months of their records in the turbo.db SQLite files located in the following folders:
..\data\data\com.google.android.apps.turbo\databases
..\data\user\%USERNUMBER%\com.google.android.apps.turbo\databases
In Belkasoft X, you can find the information parsed from this database in the Artifacts window on the Structure tab under System files → turbo.db → Battery percentage. This profile reveals the battery percentage values and the charging states at specific times, the time zone set up on the device, and whether the device was in Battery Saver mode:
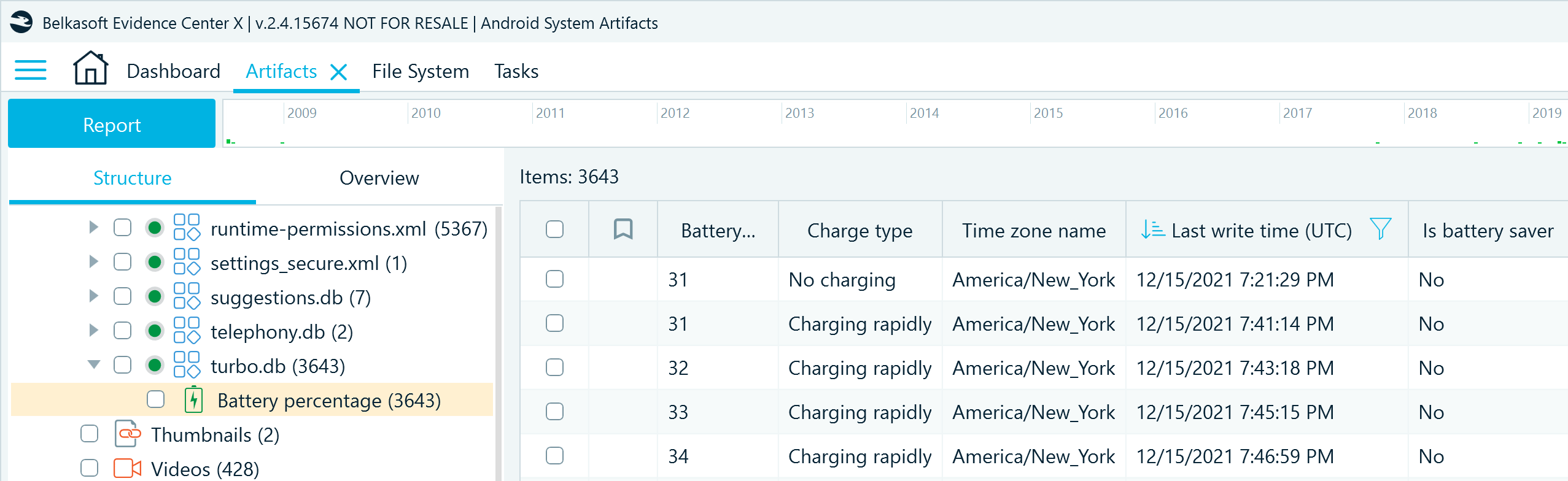
The artifacts extracted from turbo.db can provide insights into the timeline of battery events on the device, indicating whether the device was connected to other devices, power outlets, or wireless stations (if supported) at certain timeframes. By analyzing the timeline, you may spot periods of faster drain, which may mean some power-demanding applications, like the Flashlight, were in use.
Battery usage by apps
Many Android devices running on version 12 and later collect detailed battery usage statistics to provide users with details on how various applications and services consume power. They collect up to seven days of this data and record it into the battery-usage-db-v4 SQLite database stored in the following locations:
..\data\data\com.google.android.settings.intelligence\databases
..\data\user\%USERNUMBER%\com.google.android.settings.intelligence\databases
In Belkasoft X, you can find these battery usage details in the Artifacts window on the Structure tab under System files → battery-usage-db-v4 → Battery percentage. This profile provides information on the amount of power (in mAh) consumed by various applications and services on the device, showing whether the applications were running in the foreground or background and for how long they ran. Additionally, this profile shows the time zones where the device was used, while the Last boot and Last write time columns indicate the days when the applications were run:
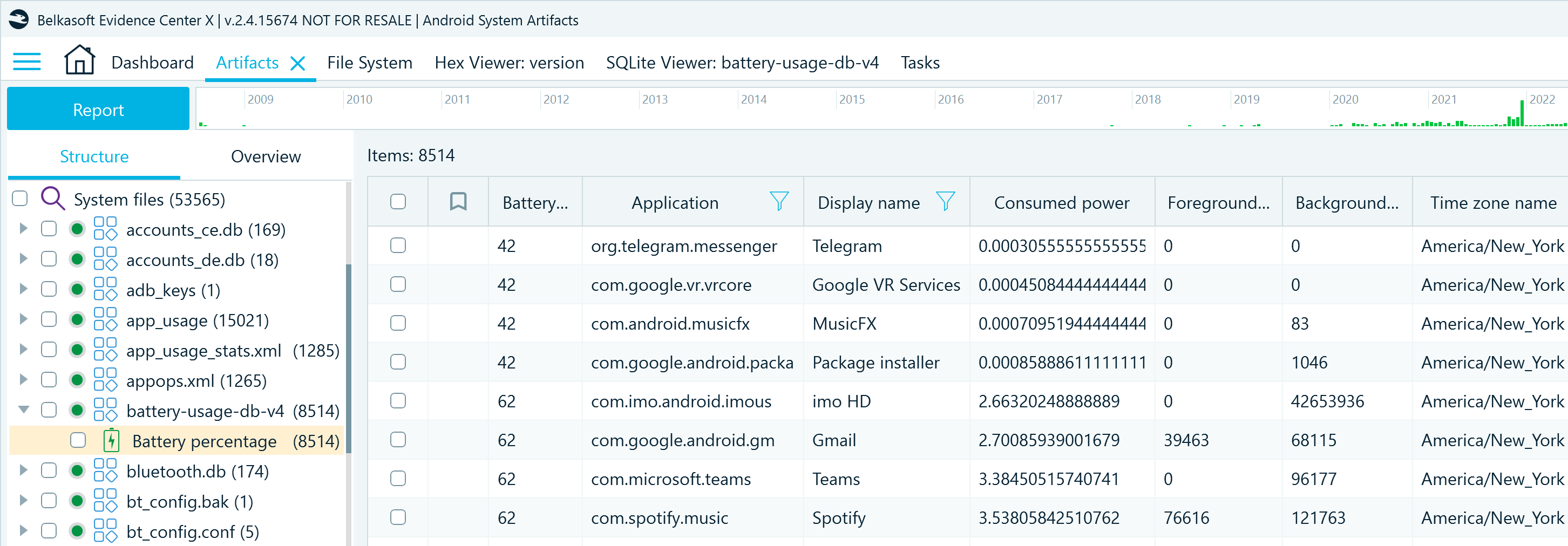
The battery-usage-db-v4 can reveal the device's whereabouts (or at least, time zone settings) and help understand which applications were in use more often and thus need more attention. It can also be valuable for tracking down suspicious applications that often run in the background and consume substantial battery power.
Battery usage by Bluetooth
Another notable source to check when examining the battery usage on an Android device is the bluetooth.db SQLite database that is located in the following folders:
..\data\data\com.google.android.apps.turbo\databases
..\data\user\%USERNUMBER%\com.google.android.apps.turbo\databases
In Belkasoft X, you can find the details from this database in the Artifacts window on the Structure tab under System files → bluetooth.db → Battery percentage. This profile includes the MAC addresses and identifiers of the Bluetooth devices that consumed device power and the timestamps of when they were in use:
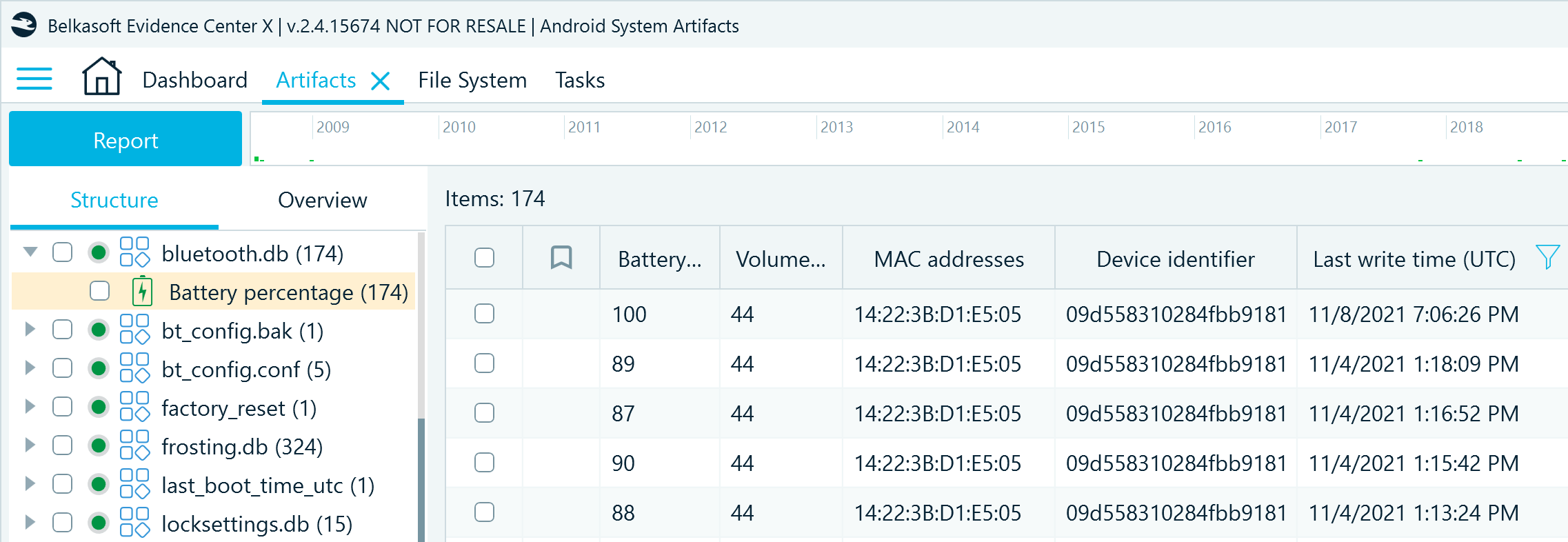
The bluetooth.db system artifact contains detailed timestamps of the periods when the device was used with external equipment.
Paired Bluetooth devices
If you need to find information on the Bluetooth devices used with an Android phone or tablet, examine the structured bt_config.conf file stored in the following location:
..\data\misc\bluedroid
In Belkasoft X, you can find this artifact profile in the Artifacts window on the Structure tab under System files → bt_config.conf → Paired Bluetooth devices. Besides the MAC addresses of the paired devices, it also provides their default or user-assigned names and the timestamps of when they were first paired with the device.
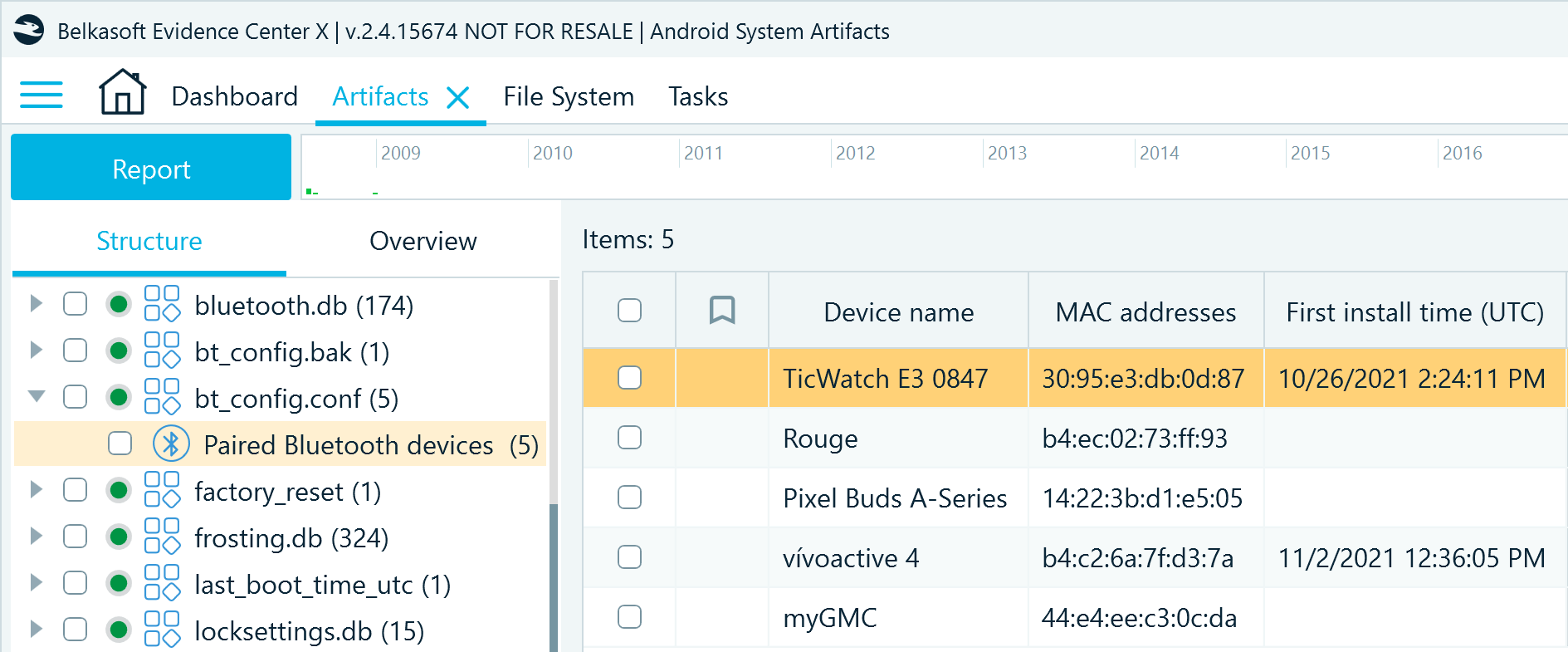
The bt_config.conf artifact can help you find additional devices that may be of interest for your investigation (like a smartwatch, for example). Cross-referencing data from this file with bluetooth.db can help identify when paired Bluetooth devices were in use.
Lock screen settings
If you need to find out how the lock screen was configured on the Android device whose image you are examining, check the locksettings.db SQLite database located in the following folder:
..\data\system.
In Belkasoft X, the information parsed from this database can be found in the Artifacts window on the Structure tab under System files → locksettings.db → Device info:
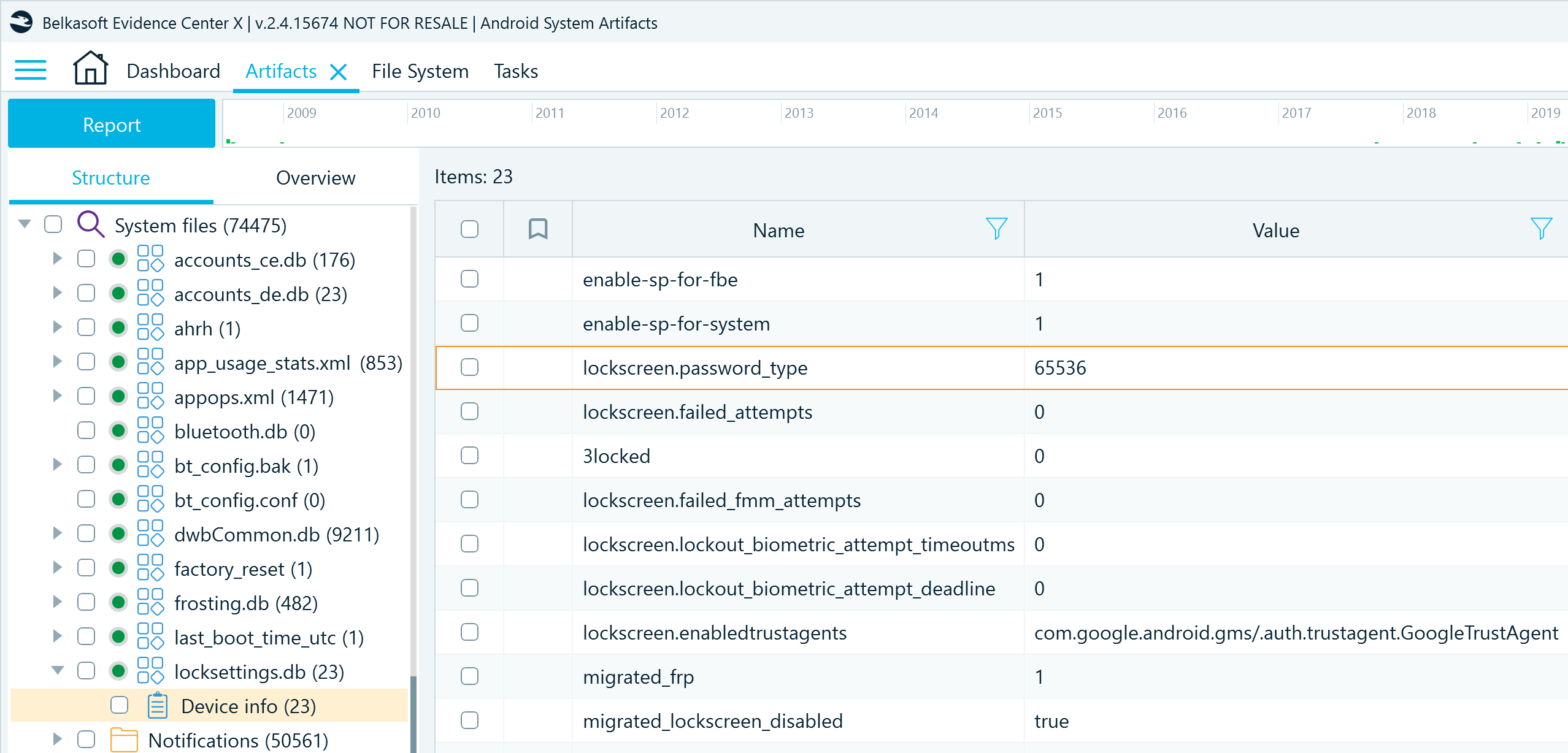
The type of password used to access the device is stored under the lockscreen.password_type name. It is represented by a constant value, established by Android developers. For example:
- 196608: a complex numeric value
- 262144: an alphabetic value with symbols
- 65536: a pattern or pin with repeated or ordered numbers
You can find more information on how to interpret these values in Android developer documentation.
ADB keys
Android Debug Bridge (ADB) is a command-line tool that allows communicating with Android devices via USB or through Transmission Control Protocol (TCP) over Wi-Fi networks. When a host connects to a device, the system caches connection details into a file and stores them in the following location:
..\data\misc\adb\adb_keys
In Belkasoft X, you can find this artifact profile on the Structure tab under System files → adb_keys → ADB hosts. It displays the host computer name and the user name of the account that has interacted with the device through ADB:
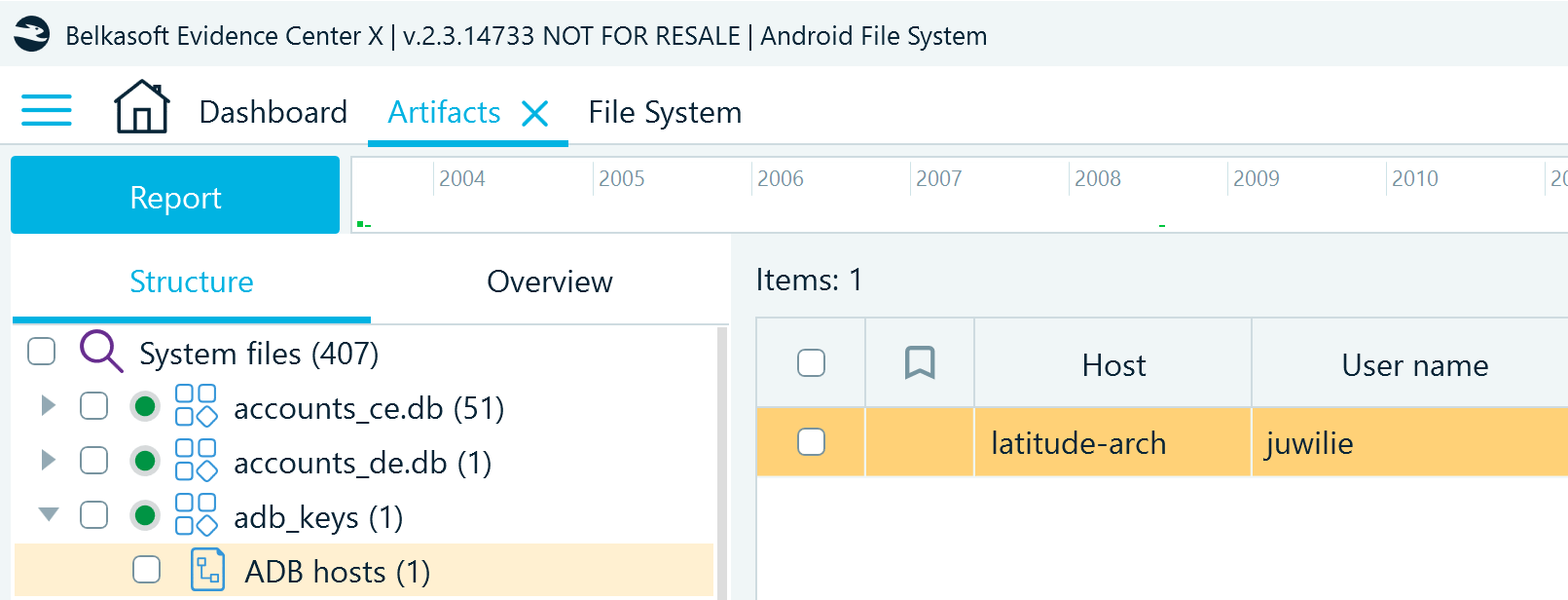
ADB allows performing various actions on the device, including application installation. In digital investigations, the ADB_keys artifact can help understand if an external user could manipulate the device and reveal some of this user's details.
Conclusion
Android system artifacts play a crucial role in digital forensic investigations, offering insights into device information and usage patterns. While acquiring such files can be challenging, digital forensics tools like Belkasoft X facilitate the process and enable thorough analysis. By exploring artifacts with information on device properties, SIM card details, battery usage records, and Bluetooth connections, you can reconstruct timelines and identify potential evidence pertinent to your inquiries. These artifacts not only shed light on device activities but also aid in understanding user behaviors, enhancing the efficiency and depth of forensic examinations.

