iOS System Artifacts: Revealing Hidden Clues
Introduction
When conducting a digital investigation, application artifacts like chats and browsers are usually the first in line to explore. With iOS devices, however, system files have great potential, too. Apple devices record and store various user settings and activities, and some of these records may help build a picture of events and reveal crucial evidence.
In this article, we will look into a few notable iOS system artifacts, such as:
We will explain how to acquire and analyze these artifacts with Belkasoft X and provide tips on using them in criminal and cybersecurity investigations.
CellularUsage.db
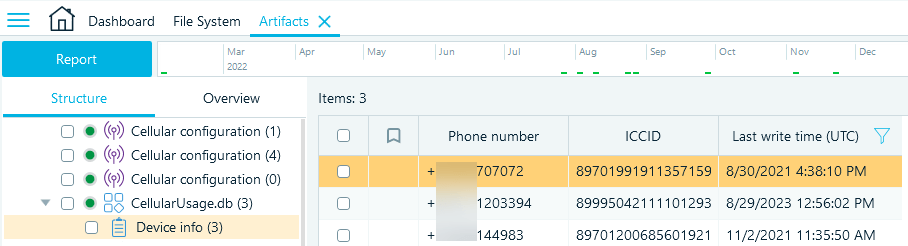
The CellularUsage.db file contains phone numbers and SIM card IDs associated with the device. It often retains details of SIM cards that are no longer tied to the device, which can help identify additional numbers of the device owner and when they were used.
When analyzing iOS artifacts in Belkasoft X, you can find this database profile on the Structure tab under System files → CellularUsage.db → Device info.
File System location:
- Full file system: \private\var\wireless\Library\Databases\
- iTunes / iCloud backup: \WirelessDomain\Library\Databases\
Tip: More details of this kind can be part of the Cellular configuration profile.
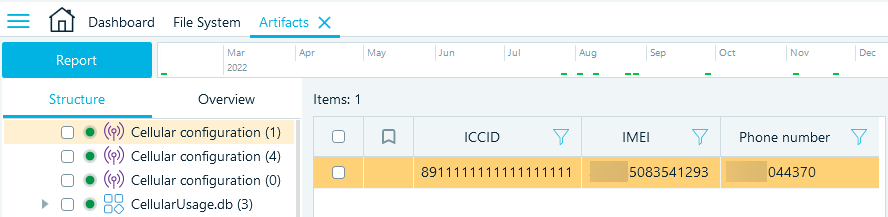
Accounts3.sqlite
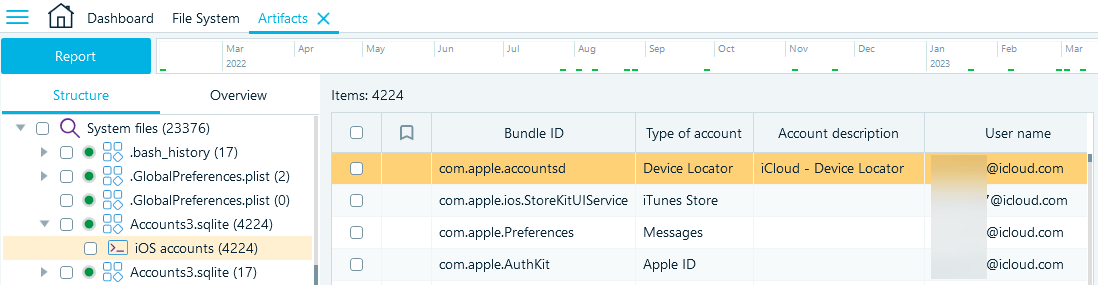
The Accounts3.sqlite file is another useful location to check when looking for additional contact details of the device owner. It includes email addresses associated with various iOS system services and applications.
In Belkasoft X, you can find the Accounts3.sqlite data on the Structure tab under System files → Accounts3.sqlite → iOS accounts.
File System location:
- Full file system: \private\var\mobile\Library\Accounts\
- iTunes / iCloud backup: \HomeDomain\Library\Accounts\
Note that this database includes a wider range of account records in the full file system copy of an iOS device.
ADDataStore.sqlitedb
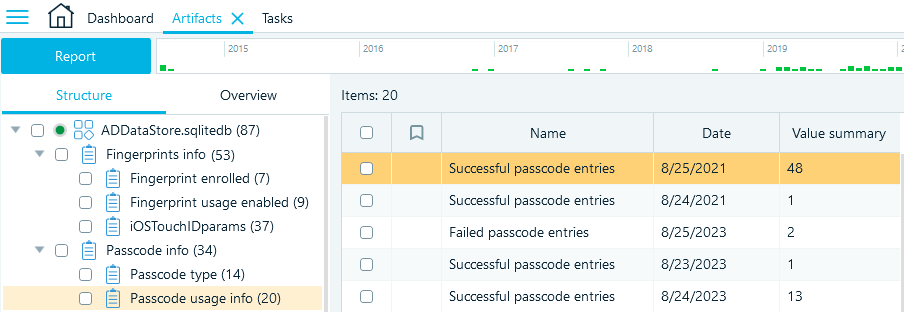
ADDataStore.sqlitedb is a versatile database that combines various device usage statistics. However, only some of its records provide value for digital investigations and have straightforward interpretation.
Belkasoft X uses this database to extract the information associated with unlocking the device: what type of passcode was set, Touch ID usage, failed unlock attempts, and so on.
You can locate the database profile on the Structure tab under System files → ADDataStore.sqlitedb.
If you want to look into more details available in ADDataStore.sqlitedb, you can find it in the device file system:
- Full file system: \private\var\mobile\Library\AggregateDictionary\ADDataStore.sqlitedb
- iTunes / iCloud backup: N/A
Photos.sqlite
The Photos.sqlite file includes additional information about the images stored in the iOS Photos application. What may be of particular interest in this database is the timestamp indicating when media files were deleted.
In iOS, when a user deletes images or videos from an album, they are not immediately removed from the device. Instead, they are moved to the "Recently Deleted" storage for 30 days until the application automatically deletes them or the user deletes them manually. If the user is unaware of this feature and attempts to hide evidence by deleting media files, Photos.sqlite will contain records of this activity. This information can help you identify which items under the Pictures profile to examine first.
The Photos.sqlite profile is located on the Structure tab under System files → Photos.sqlite → Photos info.
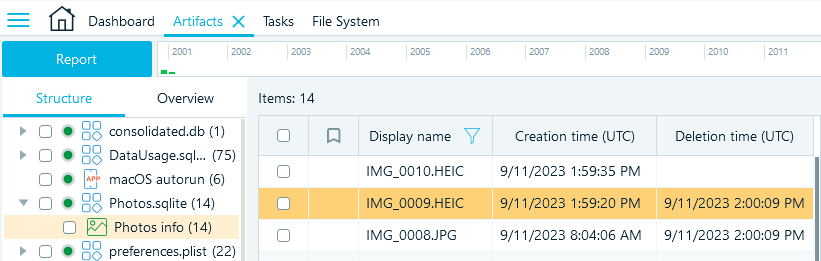
File System location:
- Full file system: \private\var\mobile\Media\PhotoData\
- iTunes / iCloud backup: \CameraRollDomain\Media\PhotoData\
DataUsage.sqlite
The DataUsage.sqlite database includes the details of the mobile network traffic usage on the device. It can help you determine which applications were installed on the device and when they were used for the first and last time. The volume of traffic used by each application and process may prove helpful as well.
When analyzing iOS artifacts in Belkasoft X, you can find this database profile on the Structure tab under System files → DataUsage.sqlite → Process statistics.
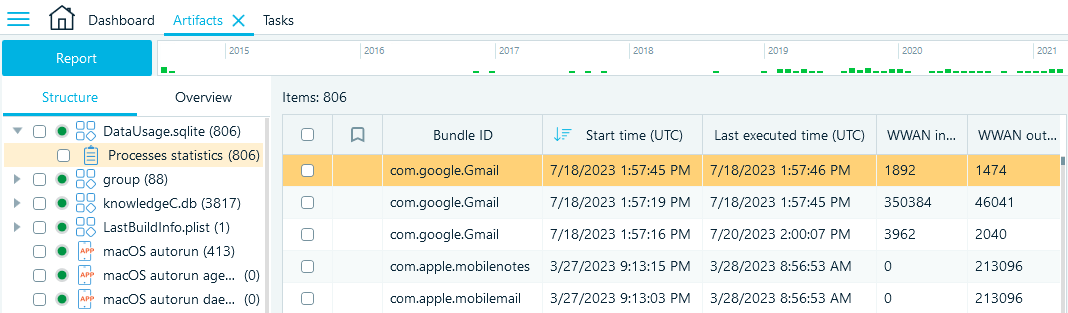
File System location:
- Full file system: \private\var\mobile\Library\Accounts\
- iTunes / iCloud backup: \HomeDomain\Library\Accounts\
Note that this database includes more records in the full file system copy of an iOS device.
KnowledgeC.db
The knowledgeC.db database includes records of various activities occurring on the device, such as device usage, app usage, website visits, interactions with other devices, and much more. It is only accessible in the full file system copy and contains valuable data on devices up to iOS 15. We covered it in detail in our previous article, "KnowledgeC Database Forensics—a Comprehensive Guide".
Tip: Starting with iOS 16, Apple mobile devices track a larger portion of this data in SEGB files, also known as Biome.
Conclusion
When it comes to digital investigations involving iOS devices, you can go beyond examining application data. The often-overlooked system artifacts can provide valuable insights and critical evidence.
In this article, we have covered a few of them, explaining how you can find additional user contact details in CellularUsage.db and Accounts3.sqlite, determine when and how the device was unlocked using ADDataStore.sqlitedb, set priorities in media file examination with Photos.sqlite, and discover application usage statistics with DataUsage.sqlite and knowledgeC.db. Belkasoft X can assist in acquiring and analyzing these valuable databases, offering deeper insights for your investigation.

