KnowledgeC Database Forensics: A Comprehensive Guide
Introduction
Apple devices are known to collect usage statistics in their system files. This data helps improve user experience, but it may also become a valuable source of information for digital forensics specialists during criminal and civil investigations. One particularly insightful file to examine on Apple devices before iOS 16 and macOS 13 is the knowledgeC.db database. This SQLite file includes records about various activities happening on the device, such as device usage, app usage, website visits, interaction with other devices, and much more.
Starting with iOS 16 and macOS 13, most of the data that was previously stored in knowledgeC.db is recorded in the Biome database. However, there are still many devices running older operating system versions. If one of them is involved in your investigation, knowledgeC.db file analysis can help discover important details and establish the device user's pattern of life.
In this article, we will explore the digital forensics of the knowledgeC.db file, covering the following topics:
- KnowledgeC.db in a nutshell
- How to acquire the knowledgeC.db file
- The knowledgeC.db database structure
Additionally, we will delve into analyzing knowledgeC.db using Belkasoft X, a specialized digital forensics and incident response tool developed by Belkasoft.
KnowledgeC.db in a nutshell
The knowledgeC.db database is an important asset during digital investigations as it contains detailed records of the device user's activities. The database typically includes about one month of records, so it is most useful when investigating recent incidents, establishing a timeline of events, or analyzing someone's pattern of life.
Here are the types of data you can find in knowledgeC.db:
- Application usage information: records of what applications were used, along with timestamps, durations, and frequency
- Internet activity: browsing history and search queries; however, note that if a user deletes their browsing history or uses private browsing mode, this data may not be available in knowledgeC.db
- Call and message history: details such as call and message numbers, timestamps, and call durations
- Device state: information on battery usage, charging events, connected devices, display backlight activity, and more
- Media usage: data related to audio input and output devices, as well as interactions with photos and media
Some knowledgeC.db records include additional details, such as contact names, input texts, search queries, and more. However, the information collected by the database may vary based on the iOS version, the device model, and the applications used. We will explore these details further in the article.
How to acquire the knowledgeC.db file
KnowledgeC.db is a part of the iOS/MacOS system files. Since Apple devices do not provide direct access to their internal file structure, accessing the system files requires either jailbreaking the device or using specialized DFIR software.
One of the DFIR tools that can help you with Apple device acquisition is Belkasoft X. This digital forensics tool allows you to extract the full file system of a wide range of Apple devices on different iOS versions.
When you launch the product, your first step is to create a case. Then, add a new data source either from the "Create case" window or from the Actions menu on the case dashboard.
In the following windows, select Acquire -> Mobile -> Apple, then select your device model and click Next.
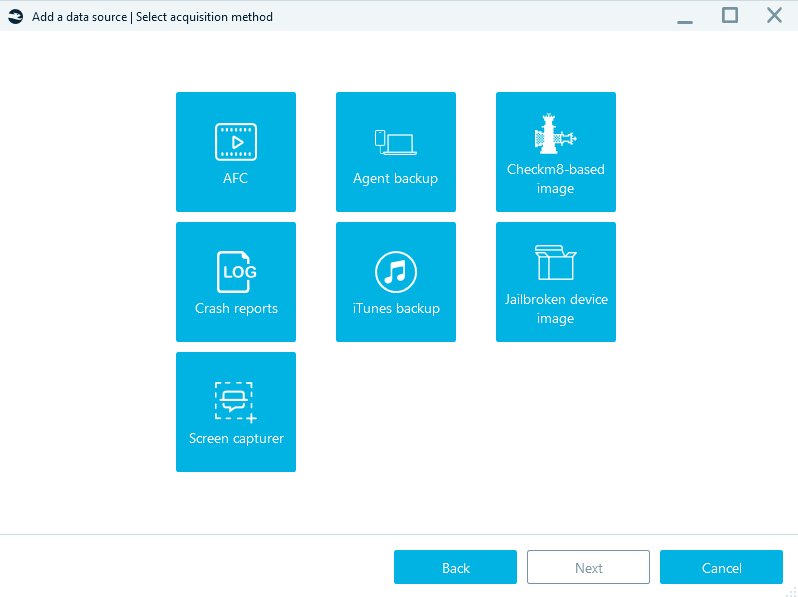
The acquisition method to choose in the next window depends on the device you are acquiring and its iOS version. The following three methods let you obtain the full file system:
- Agent-based backup can acquire all existing iPhone and iPad models running on iOS from 10 to 14.3 and from 15.0 and on. You can find more information about all supported devices and versions in our article "Agent-Based iOS Acquisition"
- Checkm8-based acquisition works for iPhone 5S to 10 (X) and a few iPad models running on iOS from 12.0 to 16.0 beta. You can find more information about the Apple devices and OS versions the method supports in our article on Checkm8
- Jailbroken device image acquisition is possible for devices with all the latest jailbreaks like checkra1n, odyssey, unc0ver, and others
Whatever method you choose, you should keep in mind that after iOS 16 and MacOS 13, Apple devices will store most device statistics in the Biome database instead of the knowledgeC.db file.
Also, note that you can only extract knowledgeC.db from a physical device, while iCloud and iTunes backups do not include the full file system.
Select the appropriate method for your device, and follow the product prompts to start the acquisition process. Refer to the product manual reference for more details on each acquisition method supported by Belkasoft X.
After acquiring the device, you can locate knowledgeC.db in its file system. MacOS systems include two knowledgeC.db files:
- system context database in the /private/var/db/CoreDuet/Knowledge directory
- user context database is the user's ~/Library/Application Support/Knowledge/ directory
On iOS devices, both user and system context are merged into one knowledgeC.db file located in the /private/var/mobile/Library/Coreduet/Knowledge/ directory.
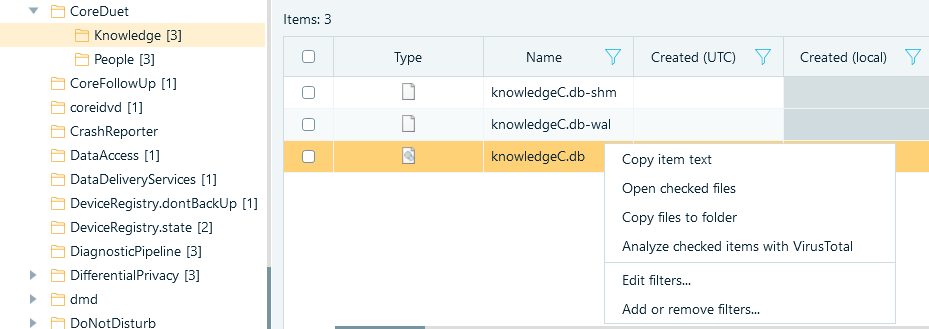
To locate the file system in Belkasoft X, open the main menu and select File System.
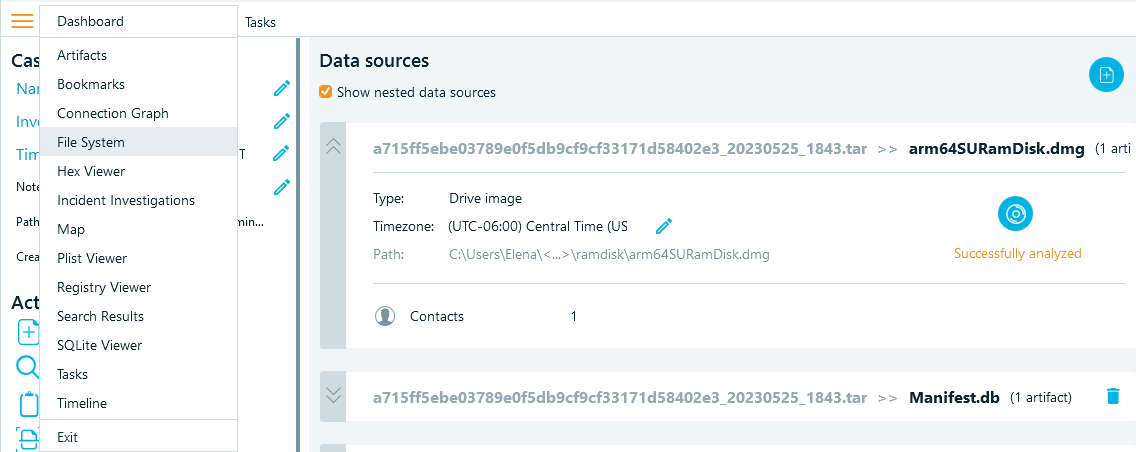
In the folder view on the left, navigate to the /private/var/mobile/Library/Coreduet/Knowledge/ directory. Right-click the knowledgeC.db file, select Copy files to folder, and browse to the folder where you want to save the file.
Now that you have the file, you can proceed to explore its contents and analyze the data – either manually, or with the help of Belkasoft X.
The knowledgeC.db structure
Working with knowledgeC.db data involves analyzing the tables and columns within the SQLite database to extract meaningful information. While there are about 20 tables in knowledgeC.db, in our experience, the following tables tend to have the most relevant records for investigations:
- ZOBJECT
- ZSTRUCTUREDMETADATA
- ZSOURCE
Let us examine each of them individually.

ZOBJECT
The ZOBJECT contains records of each activity tracked by the device system. We found the below columns the most insightful.
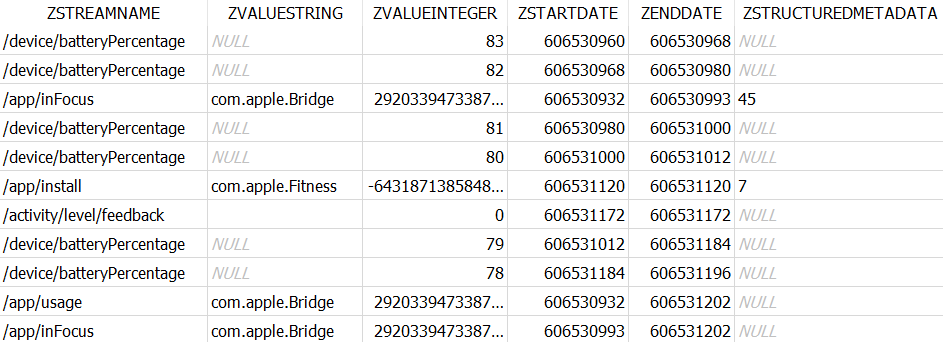
ZSTREAMNAME includes the system names of the activity types happening on the device. These names are descriptive enough to assume what activity each record is about. To name a few:
- '/app/inFocus', '/app/activity', '/app/install', '/app/usage', and '/app/webUsage' can tell a story about the user's interaction with various apps
- '/safari/history' will show the websites that the user visited
- '/device/batteryPercentage', '/display/isBacklit', '/device/isLocked' can suggest what happened inside the device
- '/device/isPluggedIn', '/bluetooth/isConnected', '/carplay/isConnected' can tell you when the device interacted with other devices and what devices those were
- '/audio/inputRoute' and '/audio/outputRoute' will show when the device produced or received audio, and '/media/nowPlaying' can suggest when the device played an audio or video file.
The system logs the information related to device usage in the ZVALUEINTEGER column. For '/device/batteryPercentage', it will store the battery charge value, while for "boolean" activity types, such as '/display/isBacklit', '/device/isLocked', '/device/isPluggedIn', '/bluetooth/isConnected', it will have 1 or 0 indicating whether the activity went on or off at a certain time.
The ZVALUESTRING column indicates the entity involved in the activity if it is available. For example, for '/app' activity types, it includes the bundle ID of the application. For '/safari/history', it contains the URL, and for '/media/nowPlaying', it will show the source of the media.
Each ZOBJECT record has a timestamp recorded in the ZSTARTDATE and ZENDDATE columns. These timestamps use the Apple Mac Absolute Time (number of seconds since 01/01/2001 00:00:00 UTC). You may need to convert these values to build the timeline of events according to the time zone of the investigation location. However, you should be careful when using the timestamps because they depend on the device settings. If the user changes the time manually, the system creates records according to the time they set instead of the actual time. Make sure to cross-check knowledgeC.db timestamps with other evidence if the time of events is critical for your case. You can learn how to avoid time zone and timeline pitfalls in our article "5 MORE Bloopers of a Digital Forensic Investigator (Part 2) "
Along with time and app ID, some activity types have their specific metadata recorded in the database. You can check if the system stores metadata for an activity in the ZHASSTRUCTUREDMETADATA column. When it is set to 1, you can find the metadata ID reference in the ZSTRUCTUREDMETADATA column that works as the foreign key of the ZSTRUCTUREDMETADATA table.
Here is an example of what ZOBJECT data may look like if you run a query for the columns of interest.
|
SELECT ZSTREAMNAME, ZVALUESTRING, ZVALUEINTEGER, ZSTARTDATE, ZENDDATE, ZSTRUCTUREDMETADATA |
ZSTRUCTUREDMETADATA
The ZSTRUCTUREDMETADATA table includes additional information about certain entries in the ZOBJECT table that the system tracks in knowledgeC.db. Each type of activity has its metadata recorded into specific columns. Let's explore the columns that we found most informative for some of the activity types we mentioned in the previous section.
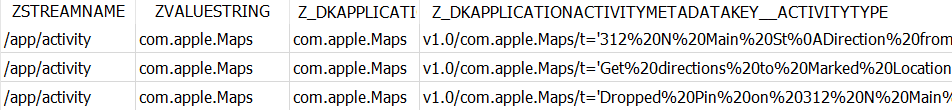
For '/app/activity', the table can reveal the action the user made in the application (Z_DKAPPLICATIONACTIVITYMETADATAKEY__ACTIVITYTYPE) and the item with which the user interacted (Z_DKAPPLICATIONACTIVITYMETADATAKEY__USERACTIVITYREQUIREDSTRING).
In the example below, after running the query, you can find out that the user looked for directions to a certain location.
|
SELECT ZSTREAMNAME, ZVALUESTRING, Z_DKAPPLICATIONACTIVITYMETADATAKEY__ACTIVITYTYPE, Z_DKAPPLICATIONACTIVITYMETADATAKEY__USERACTIVITYREQUIREDSTRING |
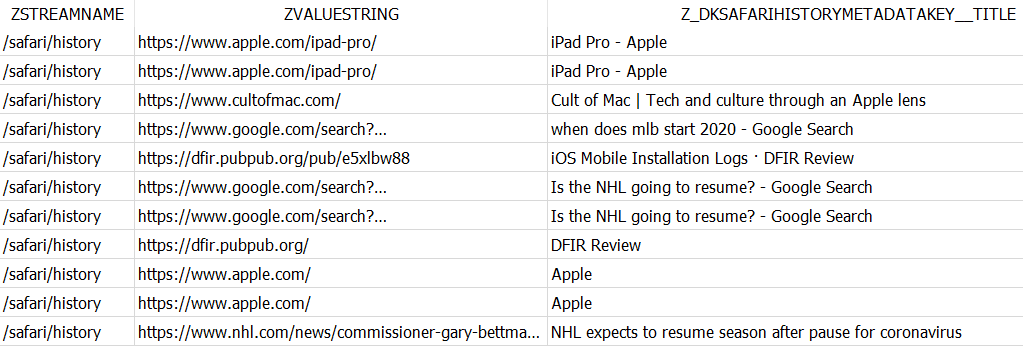
For '/safari/history', you can find the title of the viewed page or the search query in the Z_DKSAFARIHISTORYMETADATAKEY__TITLE field.
|
SELECT ZSTREAMNAME, ZVALUESTRING, Z_DKSAFARIHISTORYMETADATAKEY__TITLE |
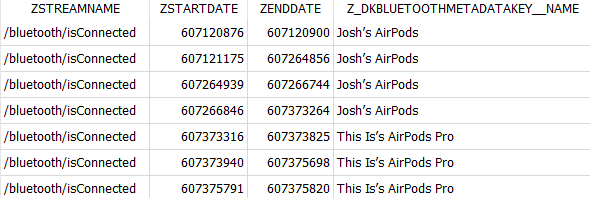
For '/bluetooth/isConnected', you can see when the device interacted with other devices through Bluetooth and locate the names of those devices in the Z_DKBLUETOOTHMETADATAKEY__NAME field.
|
SELECT ZSTREAMNAME, ZSTARTDATE, ZENDDATE, Z_DKBLUETOOTHMETADATAKEY__NAME |
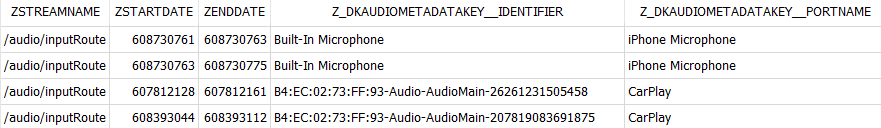
For '/audio/inputRoute', the system logs the Z_DKAUDIOMETADATAKEY__IDENTIFIER, Z_DKAUDIOMETADATAKEY__PORTNAME, and Z_DKAUDIOMETADATAKEY__PORTTYPE. They show through what the user talked, and these details may be useful for cases that involve distracted driving. In the below example, you can see that after using the iPhone built-in microphone, the user switched to CarPlay, so you can assume their hands were free at a certain time.
|
SELECT ZSTREAMNAME, ZSTARTDATE, ZENDDATE, Z_DKAUDIOMETADATAKEY__IDENTIFIER, Z_DKAUDIOMETADATAKEY__PORTNAME |
'/audio/outputRoute' has its metadata stored in the same fields. One more useful finding on these activity types is the MAC address of the external speaker or receiver to which the device connected. With this data, you can make assumptions about the user's riding in certain cars and interacting with certain Bluetooth devices.
Lastly, for the '/media/nowPlaying' type, the table stores the metadata of the media played on the device. You can find this information in the following columns:
Z_DKNOWPLAYINGMETADATAKEY__ALBUM
Z_DKNOWPLAYINGMETADATAKEY__ARTIST
Z_DKNOWPLAYINGMETADATAKEY__GENRE
Z_DKNOWPLAYINGMETADATAKEY__MEDIATYPE
Z_DKNOWPLAYINGMETADATAKEY__TITLE
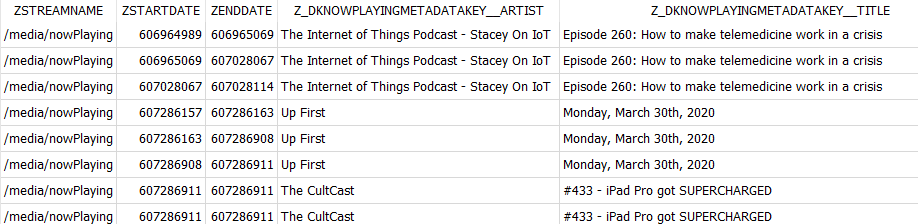
For example, this query shows that the user listened to certain podcasts and when they did it.
|
SELECT ZSTREAMNAME, ZSTARTDATE, ZENDDATE, Z_DKNOWPLAYINGMETADATAKEY__ARTIST, Z_DKNOWPLAYINGMETADATAKEY__TITLE |
ZSOURCE
The ZSOURCE table can provide additional insights into the activities on the device. It is connected to the ZOBJECT table through the ZSOURCE column. You can find some valuable data in the below ZSOURCE table columns.
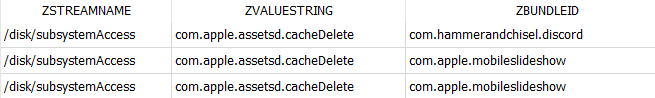
ZBUNDLEID stores the bundle ID of the app involved in the activity. For some activity types, it is the same value as the ZVALUESTRING field in ZOBJECT, but for others like, for example, '/disk/subsystemAccess', ZVALUESTRING displays the entity accessed within the system while ZBUNDLEID indicates the app involved in the activity.
|
SELECT ZSTREAMNAME, ZVALUESTRING, ZBUNDLEID |
ZGROUPID may shed some light on what the user was doing within the app. It is particularly interesting for storing contact names and numbers for some message activities.
|
SELECT ZSTREAMNAME, ZVALUESTRING, ZBUNDLEID, ZGROUPID |
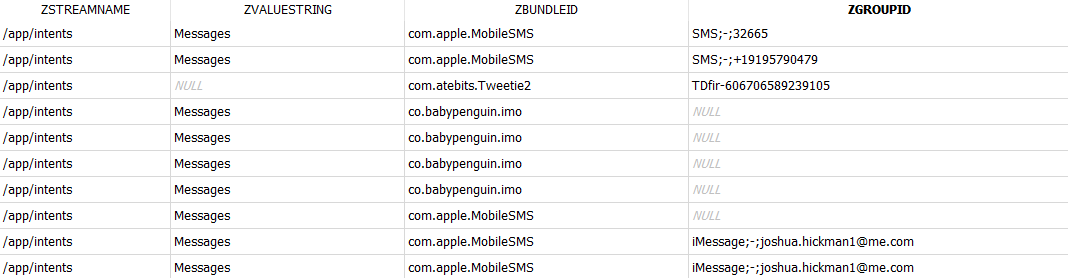
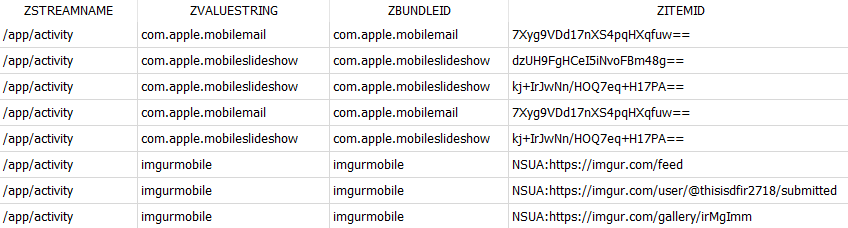
ZITEMID displays the ID of the item in use. Even though it may not be possible to discover the actual item, this field lets you detect if the same item was in use on different records. For some web apps, this column can also show the URL of the item the user interacted with.
|
SELECT ZSTREAMNAME, ZVALUESTRING, ZBUNDLEID, ZITEMID |
To conclude the knowledgeC.db exploration part, we would like to note that Apple devices log the details we mentioned for other purposes than digital forensics, and it may not always be possible to tell exactly what each piece of data is about. To figure out the patterns and build a story, it is important to consider all pertinent knowledgeC.db and other investigation data comprehensively and not focus exclusively on the information extracted from a single activity type or database row.
How to analyze knowledgeC.db with Belkasoft X
Now that you know how to acquire the knowledgeC.db file and what you can find in it, we will show you how to analyze it with Belkasoft X. While you may opt to manually investigate knowledgeC.db using the details outlined above, Belkasoft X can save you some time by conducting this analysis out of the box.
After you obtain the file through the chosen acquisition method and import it as a data source into your case, Belkasoft X will analyze the database records and present them in the Artifacts window. For example, it can extract the following artifacts:
- "Application activity", "Application in focus", "Application installations", and "Application usage" will show the user's interactions with various apps on the device
- "Safari history" and "Web usage statistics" will display data about the user's browsing activities
- "Battery percentage" and "Device is plugged in" will provide you with the information on when the device was charged and plugged into other devices
- "CarPlay usage" and "Bluetooth connections" can reveal if the device connected to certain cars and Bluetooth devices
- "Audio statistics" provides insights into the audio input and output channels used with the device
- "Media statistics" can tell you about audio and video content played.
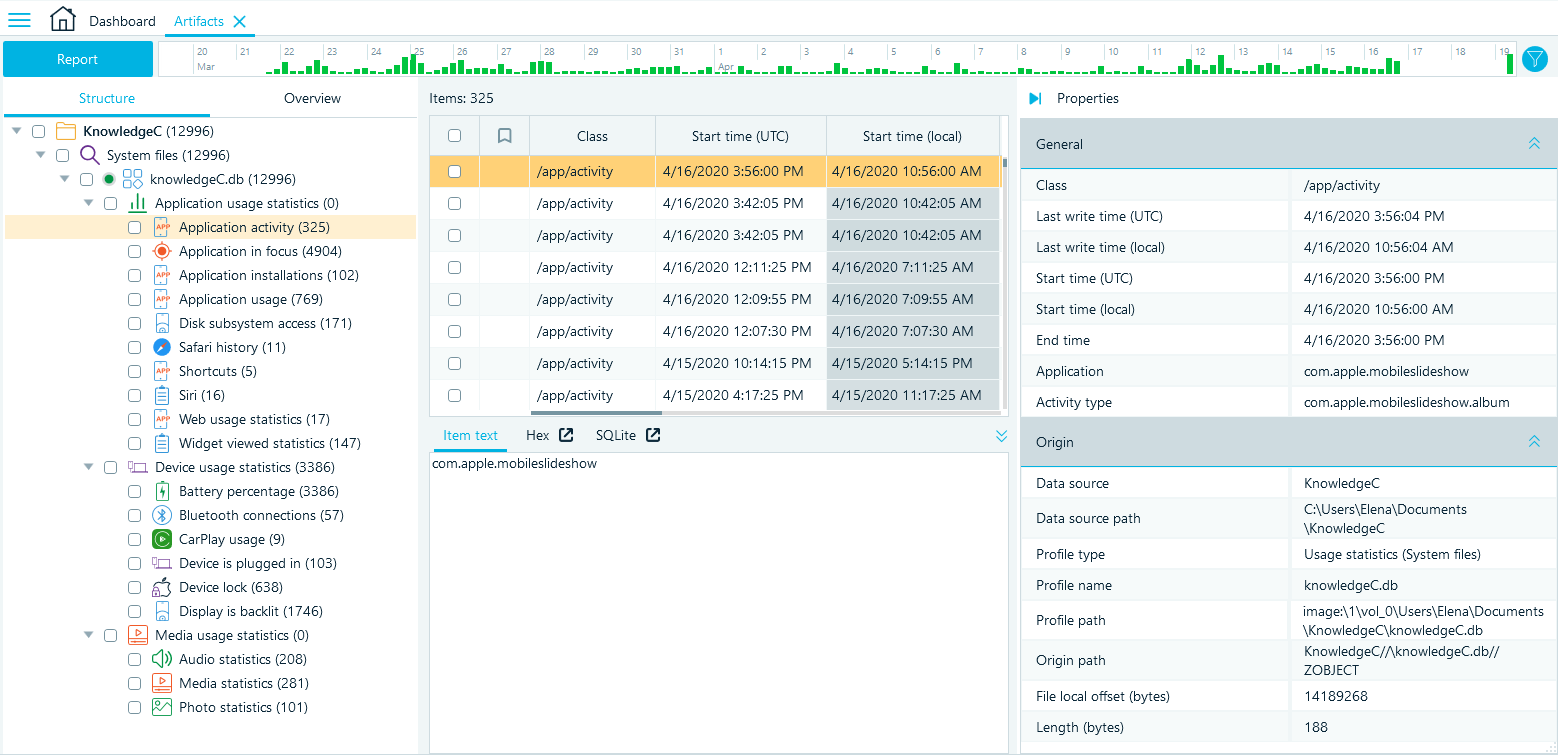
You can see the Structure view of the artifacts in the left pane. For knowledgeC.db files, the structure of the artifacts is based on the activity types (ZSTREAMNAME) that are split between larger categories, such as Application, Device, and Media usage statistics.
The Grid view in the middle pane displays the database rows parsed from the knowledgeC.db tables providing all data relevant to a record in one place. Belkasoft X also maps the original column names to more understandable descriptions and converts record timestamps into a human-readable format.
To inspect a record individually, click the required row and review its details in the Properties pane.
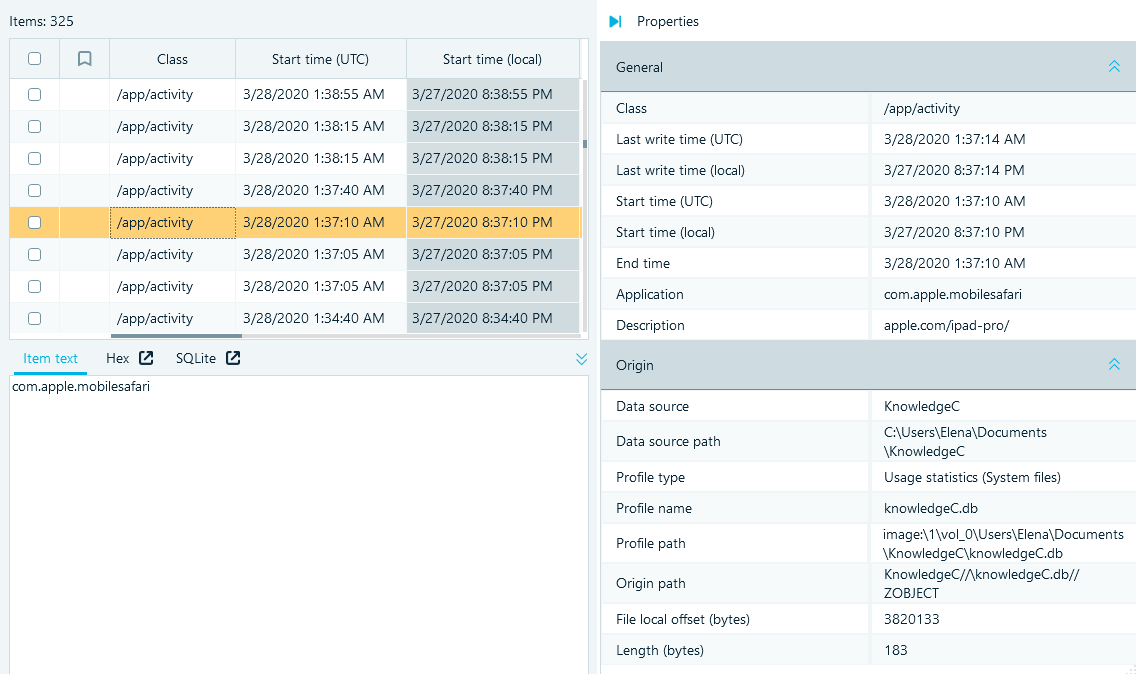
While the properties summarize the most important information, you can also inspect and search the raw data of each record in the lightweight Hex Viewer under the Grid view.
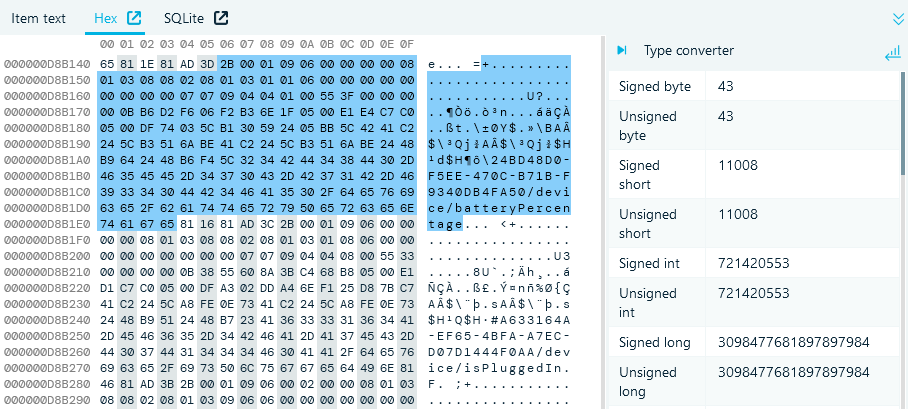
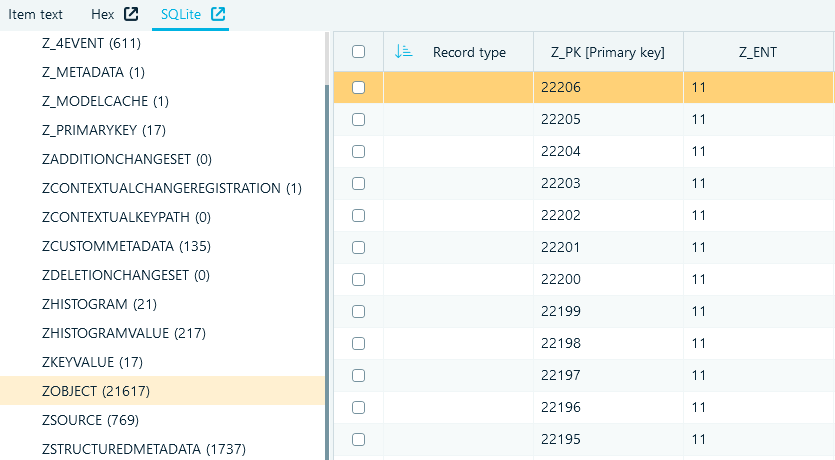
If you need to look up source data records, you can switch to the SQLite Viewer built into the product.
As you work with the artifacts, the Belkasoft X toolset lets you search, filter, bookmark the records, and export them into reports.
Conclusion
When it comes to examining Apple devices prior to iOS 16 and MacOS 13, the knowledgeC.db file is a valuable source of information for digital forensics and cyber incident response. It contains a wide range of records and metadata about how the device was used, such as app interactions, browsing history, device connections, power status, and more.
You can only acquire knowledgeC.db through jailbreak or with the help of the DFIR tools that support the full file system extraction method of device acquisition. One such tool is Belkasoft X. It not only facilitates obtaining the knowledgeC.db file, but also analyzes the database and extracts valuable artifacts from it, displaying data in a user-friendly manner and also providing raw and source data for in-depth investigation.

