iOS WhatsApp Forensics with Belkasoft X
Introduction
In the world of digital communication, WhatsApp takes the lead as the most popular messaging app, having a user base of over two billion people. With such widespread usage, it frequently becomes a central artifact in digital investigations, revealing users' connections, locations, intentions, actions, and more. As the app continues to evolve, it is essential to stay updated on its specific features to maximize extracting valuable user data for investigations.
WhatsApp is available on various mobile and computer platforms, and the way it works and stores data depends on the operating system of the device where it is installed.
In this article, we will cover iOS WhatsApp forensics and look into the following topics:
- Where iOS WhatsApp stores data
- How WhatsApp secures user data
- What happens to deleted messages in iOS WhatsApp
- How to acquire iOS WhatsApp data
- What databases store WhatsApp data in iOS
You will also learn how to effectively analyze and examine WhatsApp data using Belkasoft X.
Where iOS WhatsApp stores data
WhatsApp is a messenger that does not keep users' communication history on its servers. Instead, it employs user devices to store and back up its data. When analyzing an iOS device, you can find WhatsApp data in the following locations:
- Device internal storage: The primary location where WhatsApp keeps its data is the device's built-in memory.
- iCloud backup: WhatsApp enables users to set up automatic backups to iCloud. Though users can schedule backups daily, weekly, or monthly, they can also turn them off.
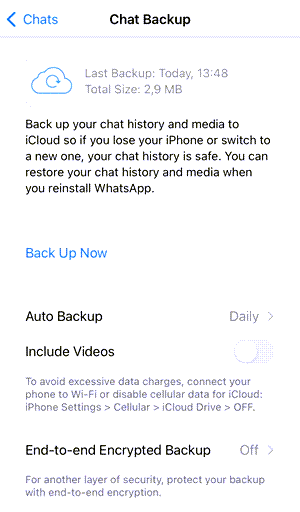
Figure 1: iOS WhatsApp is configured to upload its backup to iCloud every day
- iTunes backup: Additionally, WhatsApp data is saved when users create iTunes backups of their iOS devices.
How WhatsApp secures data storage
Within the device internal storage, WhatsApp keeps data in an unencrypted format while for backups, users can enable end-to-end encryption. This process involves setting up a password or generating an encryption key that is used to scramble the backup data. By doing so, users provide an additional layer of security to their WhatsApp backup files, ensuring that even if unauthorized access occurs, the data remains unreadable and protected.
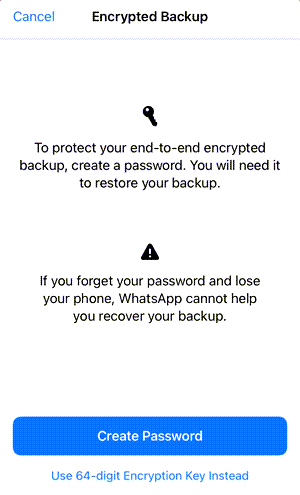
Figure 2: Backup Encryption options in iOS WhatsApp settings
When this type of encryption is enabled, WhatsApp secures its backup and lets users restore it only by providing the password or encryption key.
This setting also affects iTunes backups. If WhatsApp backup encryption is on, the application does not save user data into iTunes backups.
What happens to deleted messages in iOS WhatsApp
When WhatsApp users want to delete chat messages, they have two options:
- Delete for Everyone: If successful, this action removes sent messages from the devices of all participants in the chat. The option is available for approximately two days after sending a message, however, it leaves an indication of deletion:
- Delete for Me: This action applies to both sent and received messages and only removes messages from the device where it is performed
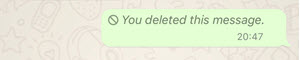
Figure 3: An indication of message deletion in iOS WhatsApp
When looking for deleted messages in WhatsApp data, you should be aware that those deleted "for Everyone" can still be found in WhatsApp databases. Although the actual content of these messages is absent, their associated data, such as timestamps and senders/receivers, persists.
In contrast, messages that are deleted "for Me" are unlikely to be recoverable due to how iOS processes the deletion of WhatsApp database records.
How to acquire iOS WhatsApp data
The variety of data storage options lets digital investigators use different methods to extract WhatsApp data. The volume of data you can obtain and its up-to-dateness depend on the WhatsApp storage type you can acquire. When working with specialized digital forensics software like Belkasoft X, you have a number of options:
- The full file system and iTunes backup acquisition methods let you obtain WhatsApp data currently available within the device storage
- The iCloud backup method enables you to access the application data that the device has backed up to iCloud by the time of the acquisition
The table below will help you define which method suits your situation the best when using Belkasoft X for device acquisition:
|
Method |
Full File System |
iTunes Backup |
iCloud Backup |
|
Requires physical access to the device |
Yes |
Yes |
Only for providing the 2FA password (you can also use the SIM card with the number tied to the device user's iCloud account for 2FA) |
|
Requires internet access |
Depending on the acquisition type |
No |
Yes |
|
Safe |
In most cases |
Yes |
Yes |
|
Works on all iOS devices |
No |
Yes |
Yes |
|
Extracts all WhatsApp databases |
Yes |
Includes all important databases (chat, calls, contacts, etc) |
If iCloud backup is on, the same amount as iTunes; up-to-dateness depends on the last WhatsApp and iCloud backup time |
|
Obtains data when WhatsApp backups are encrypted |
Yes |
No, but it is possible to turn off encryption |
No, but it is possible to turn off encryption |
|
Requires the Apple ID and password of the device |
No |
No |
Yes |
iOS full file system acquisition
Belkasoft X allows you to extract the full file system of Apple mobile phones on different iOS versions. Let us begin with this method, as it typically lets you obtain all the latest WhatsApp-related data.
To use this method, you must install iTunes from the Microsoft Store and be ready to provide the device passcode. If you do not have the passcode, you can try Belkasoft's brute-force solution.
Launch Belkasoft X and create a case. Then, add a new data source either from the "Create case" window or the Actions menu on the case dashboard:
Figure 4: Adding a data source in Belkasoft X
In the "Add a data source" window, select Acquire → Mobile → Apple and choose your device model:
Figure 5: Selecting the Apple device model to acquire
The acquisition method to select in the next window depends on the device you are acquiring and its iOS version. The following three methods let you obtain the full file system:
- Agent-based acquisition can create a full file system image for any iPhone and iPad running a wide range of iOS versions. Learn more about the supported devices and iOS versions in our article "Agent-Based iOS Acquisition"
- Checkm8-based acquisition works for iPhone 5S to 10 (X) and iPad models with the same systems on a chip (SoC), running on iOS 12.0 to 16.0 beta. You can find more information about the supported devices and iOS versions in our article on Checkm8
- Jailbroken device image acquisition is possible for devices with any jailbreak installed like checkra1n, odyssey, unc0ver, and others
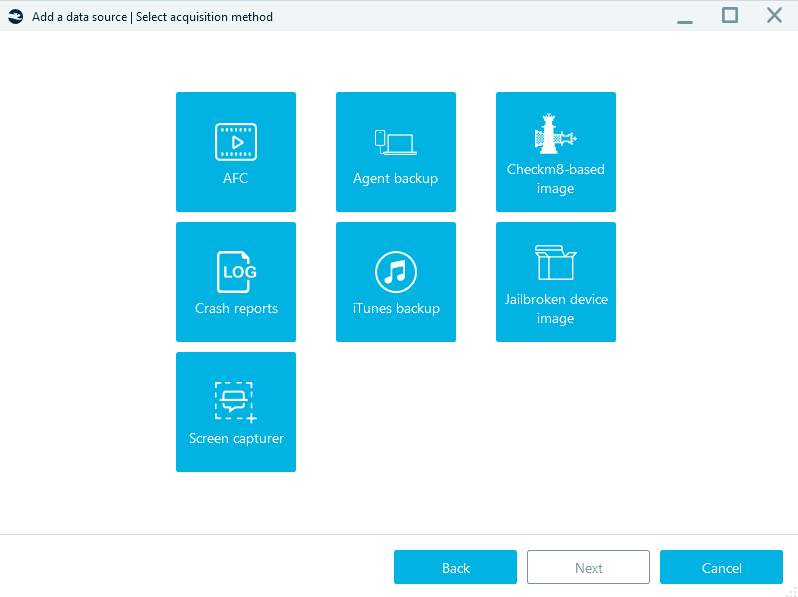
Figure 6: Selecting the acquisition method
Select the appropriate method for your device and follow the prompts to go through the acquisition process. Refer to the product manual reference for more details on each acquisition method supported by Belkasoft X.
When the acquisition is complete, proceed to the instructions in the next chapter, "How to analyze and examine iOS WhatsApp data in Belkasoft X."
iTunes backup acquisition
Belkasoft's iTunes backup method is the easiest way to obtain the iOS WhatsApp data:
- It mimics the standard iTunes backup process, so it is safe for the device
- You can use it for any Apple device model and version of iOS
- It is relatively quick to run
Note that if end-to-end encryption is enabled for WhatsApp backups, you need to manually turn it off in the application settings to be able to acquire WhatsApp data with the iTunes backup method. To do it, you do not need to know the WhatsApp backup password—you can use the "I forgot my password" option and provide the device passcode for identification. Keep in mind, though, that when you turn off the encryption using the passcode, WhatsApp makes a new unencrypted backup, which will overwrite the data currently stored in iCloud:
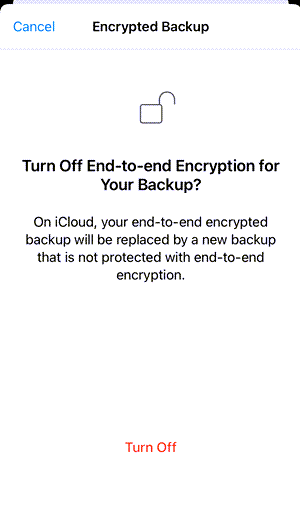
Figure 7: Turning off encryption for WhatsApp backup in iOS
Before you begin the acquisition, verify that you have the passcode to access the device and the iTunes application installed from the Microsoft Store on the workstation you use for acquisition.
The iTunes acquisition starts like the full file system acquisition: you create a case in Belkasoft X and add a new data source; select Acquire → Mobile → Apple and choose your device model.
In the next window, select the iTunes backup option and follow Belkasoft X's prompts to start the acquisition:
- Connect the device to your workstation
- Unlock the device with its passcode
- When the tool prompts you to select whether to encrypt the iTunes backup, select Yes; note that in this step you only encrypt the iTunes backup, which does not affect the WhatsApp data
- Select the path where to save the acquired data
After you configure the acquisition options, click Start and wait while the tool acquires the backup:
Figure 8: The iTunes acquisition log in Belkasoft X
When the acquisition is complete, proceed to the instructions in the next chapter, "How to analyze and examine iOS WhatsApp data in Belkasoft X."
iCloud backup acquisition
If an iOS device is set to create iCloud backups, you can acquire and analyze them in Belkasoft X. The amount and up-to-dateness of the WhatsApp data you can retrieve from iCloud backups depend on the following factors:
- Last iCloud synchronization time: iOS devices typically synchronize to iCloud daily, but only when connected to power, locked, and connected to Wi-Fi. You can find the last synchronization date within the iCloud backup settings:
- WhatsApp backup frequency (daily, weekly, monthly): These settings define when the application data was last saved to the backup. You may also obtain no data at all if the user has WhatsApp backups turned off or not included in iCloud backups.
- WhatsApp backup encryption: If end-to-end encryption is turned on, it is not possible to obtain WhatsApp data from the iCloud backup. However, if you do not mind overwriting it with the current WhatsApp data stored on the device, you can manually turn off WhatsApp backup encryption in the application settings. As a result, the application creates a new unencrypted backup that you can obtain after synchronizing the device to iCloud.
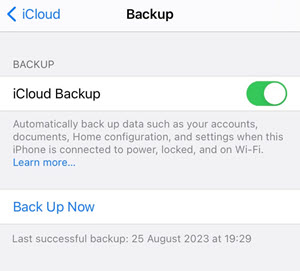
Figure 9: iCloud backup settings in iOS
Before you begin the iCloud backup acquisition, you need to install the iCloud and iTunes applications from the Microsoft Store. You also need to launch iCloud and log in to it with an Apple ID that is different from the one you want to acquire.
To begin the acquisition, create a case and add a data source in Belkasoft X. Select Acquire → Cloud → iCloud Backups and provide the Apple ID and Password of the iCloud account you want to acquire:
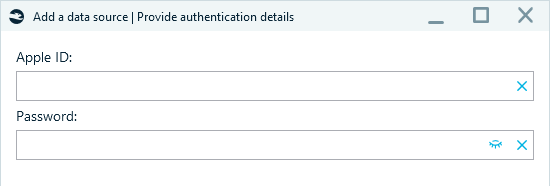
Figure 10: Providing Apple ID credentials for iCloud backup acquisition in Belkasoft X
If asked, accept the request for administrative access to the iCloud application folder. Then, specify a folder for the acquired data and click Start.
In the two-factor authentication screen, choose the authentication method to access the iCloud account and provide the required code:
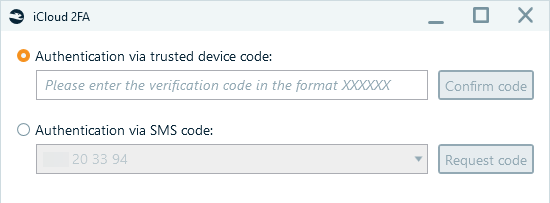
Figure 11: Supplying the 2FA code for iCloud backup acquisition
When Belkasoft X finishes downloading the iCloud backup data, proceed to the instructions in the next chapter, "How to analyze and examine iOS WhatsApp data in Belkasoft X."
How to analyze and examine iOS WhatsApp data in Belkasoft X
When Belkasoft X finishes the acquisition, it prompts you to define the analysis options. If you are only interested in WhatsApp data, you can accelerate the analysis by selecting it as a single item to analyze.
In the "Select advanced analysis options" window, under Artifact types, clear the All check box. Then, in the Filter field, start typing "whatsapp" and select the iOS WhatsApp check box only as shown in the screenshot:
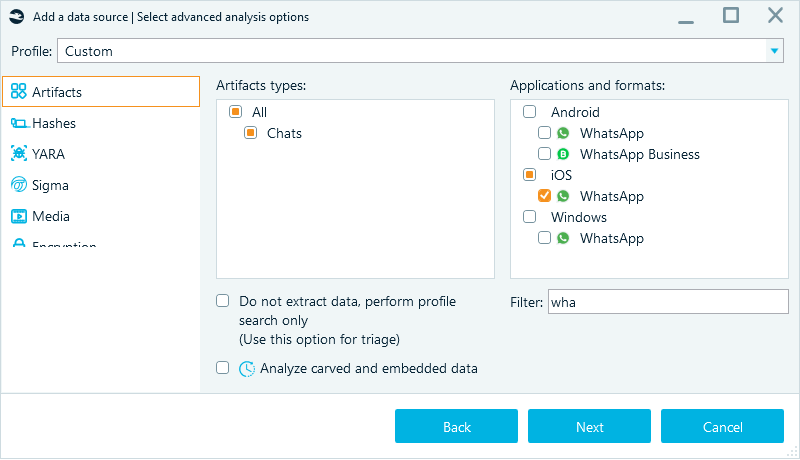
Figure 12: Selecting WhatsApp for analysis
Upon the analysis completion, Belkasoft X displays extracted chats in the "Artifacts" window. You can locate WhatsApp artifacts in the Structure or Overview tabs under Chats:
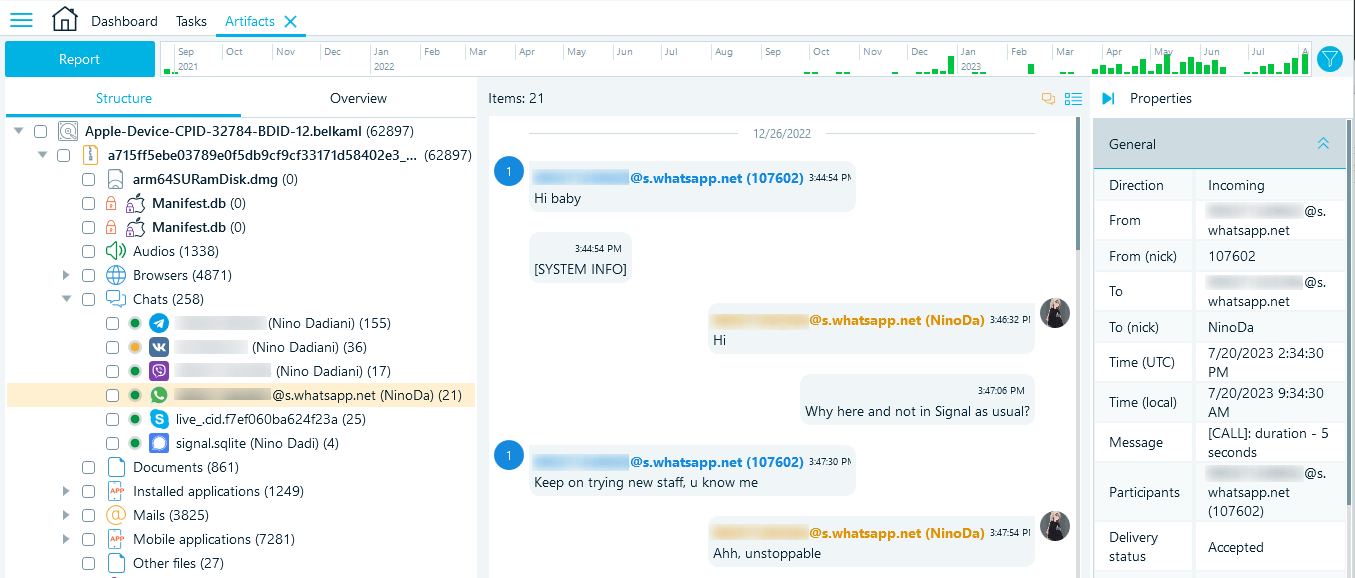
Figure 13: Locating the WhatsApp profile in the “Artifacts” window
If you right-click the WhatsApp profile and select Show contacts, Belkasoft X breaks down the records by chats as they display on the device:
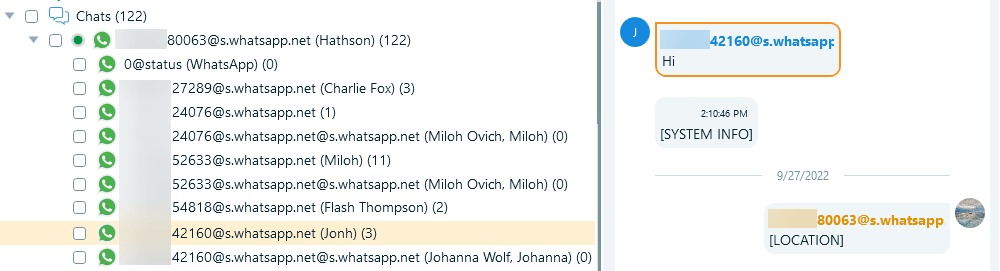
Figure 14: Viewing WhatsApp messages by groups and private chats
When browsing through the conversations, you can find texts, voice messages, location pins, media files, contact cards, and documents sent or received.
Bubbles in the chat view display the contents of exchanged messages. The Properties pane provides their details, such as direction, delivery status, timestamps, sender and recipient phone numbers, and nicks. Depending on the message type, they can also include text, location URLs, file names, and more. Empty bubbles represent the messages that the user deleted "for Everyone." While they include no text, they can still provide valuable data, indicating that a message was sent at a certain time by a certain user.
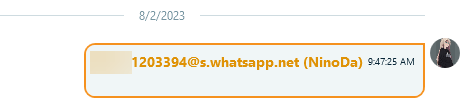
Figure 15: Representation of a WhatsApp message deleted “for Everyone” in Belkasoft X
Besides the message texts and details, Belkasoft X extracts the documents and media files sent and received by the user. You can locate these files in the corresponding artifact tabs. For example, copy a picture file name from a WhatsApp record and filter the records in the Pictures profile by it. You can then instantly preview the found pictures in the Gallery view:
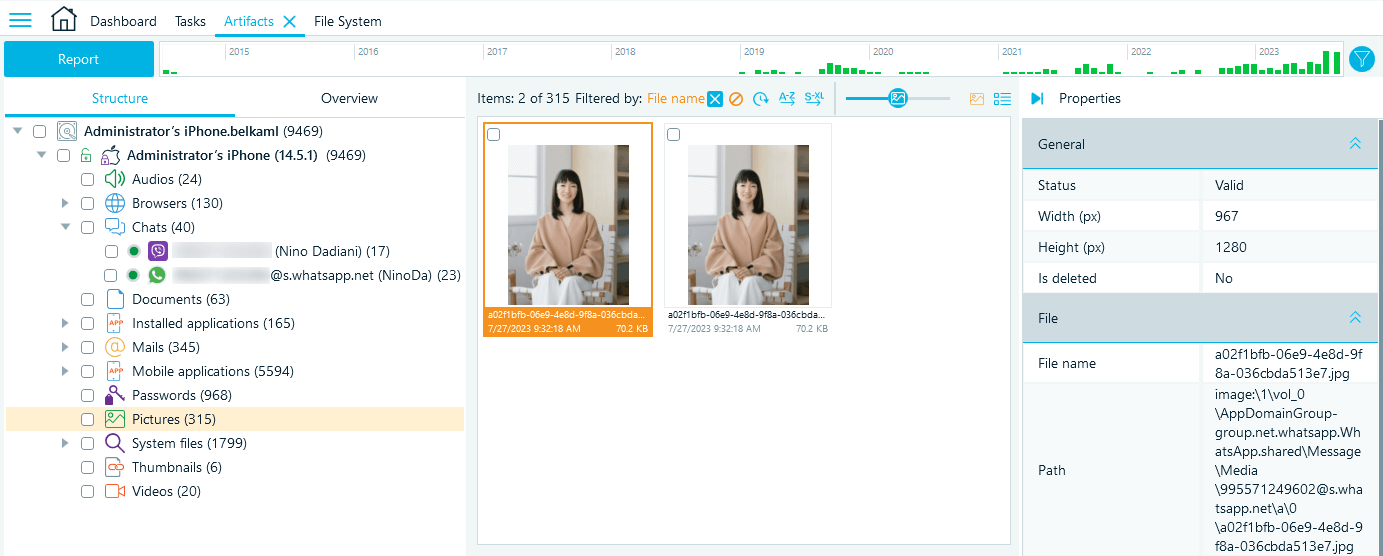
Figure 16: Viewing the found images in the Gallery view
To locate the application database files, right-click the WhatsApp profile and select Show on File System.
- If you have the full file system copy of the device, the WhatsApp database folder name is the GUID that the system assigned to the application when it was installed on the device.
Belkasoft X detects this folder during the analysis, but if you need to look for it manually, check the folders under ..\private\var\mobile\Containers\Shared\AppGroup\: - In iTunes and iCloud backups, the database files are stored under ..\AppDomainGroup-group.net.whatsapp.WhatsApp.shared:
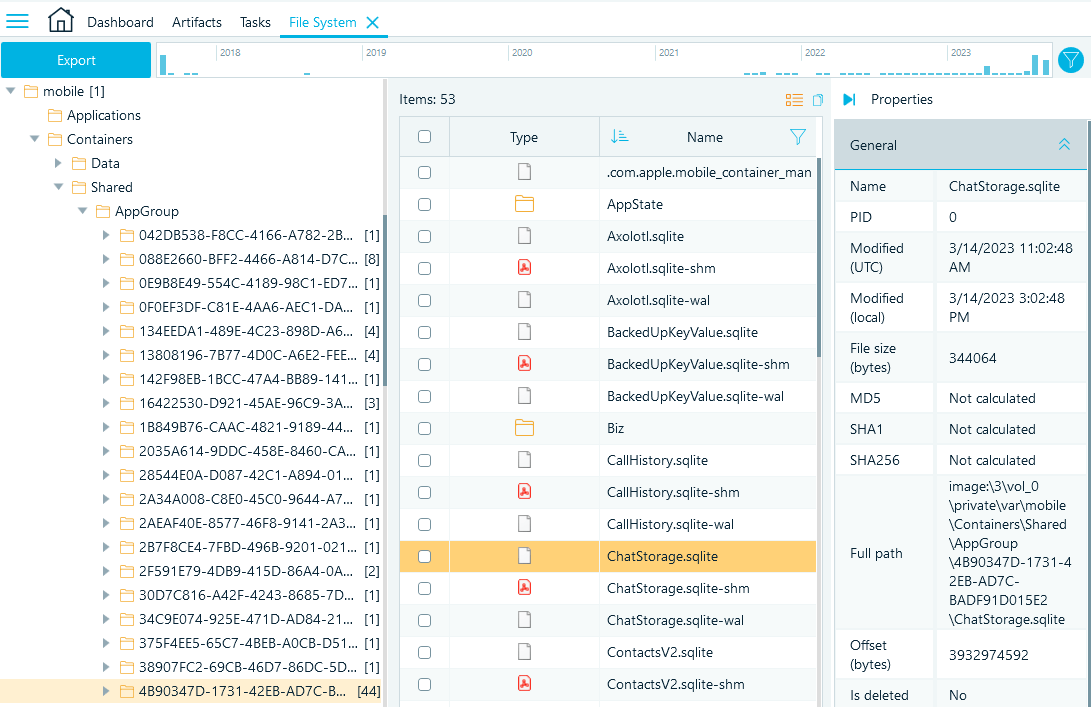
Figure 17: Locating WhatsApp database folder in the device file system
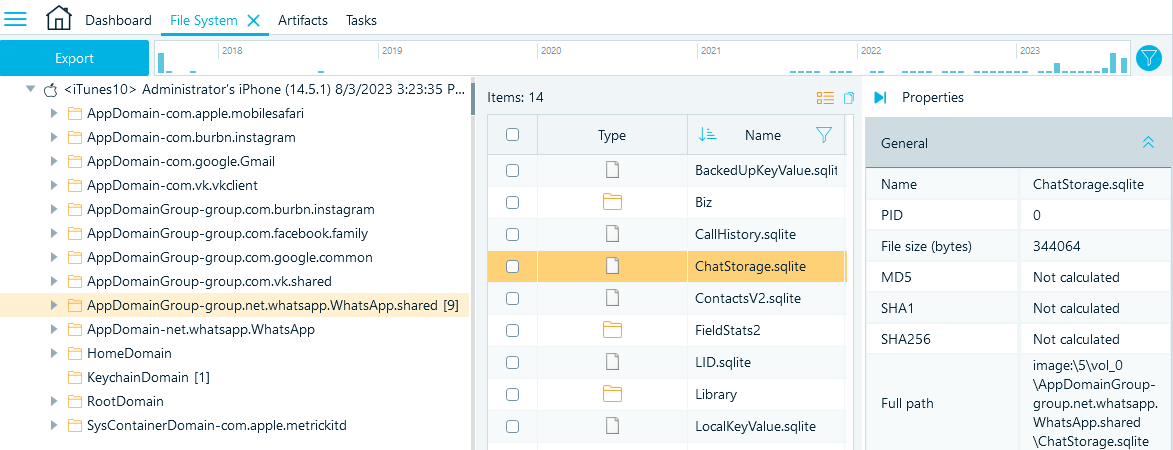
Figure 18: Locating the WhatsApp database folder in the device backup file system
What databases store WhatsApp data in iOS
On iOS devices, WhatsApp holds the most valuable information for investigation in the ChatStorage.sqlite, CallHistory.sqlite, and ContactsV2.sqlite files. In this chapter, we will explore them with Belkasoft X SQLite Viewer.
To open a database in Belkasoft X, in the "File System" window, select the database file and click on the SQLite tab below the grid or go to the full-screen mode:
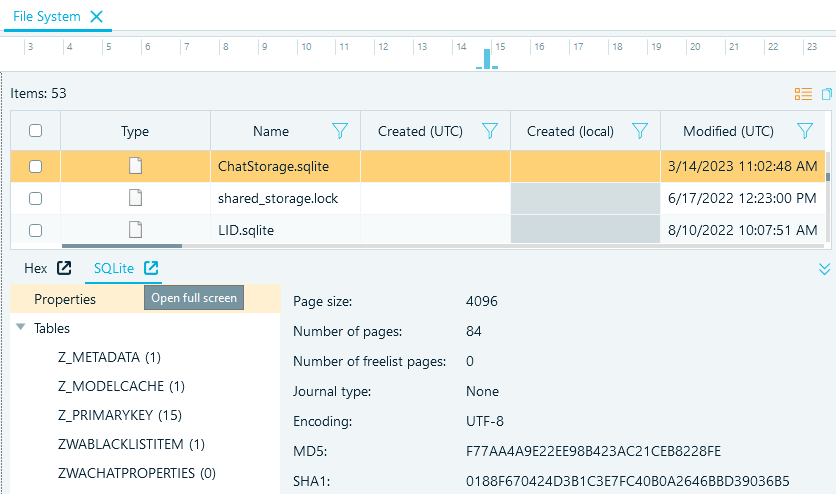
Figure 19: Selecting a database file to display in the SQLite viewer
ChatStorage.sqlite
The ChatStorage.sqlite database file contains the user's text communication data. Let us look into several tables of interest in it.
The ZWACHATSESSION table stores the information on the user's conversations. Here are some of its most informative columns:
- ZSESSIONTYPE includes the conversation type ID: 0 indicates private messages with a contact, 1 stands for a group chat, 2 for a broadcast, and 3 for a status change
- ZCONTACTJID contains the identifier of the contact or group; contacts end with @s.whatsapp.net, groups with @g.us, and @status indicates user status update
- ZPARTNERNAME provides the name of the contact or group
- ZMESSAGECOUNTER includes the number of messages exchanged with the contact or group
- ZUNREADCOUNT shows the number of unread messages in the contact or group chat
- ZLASTMESSAGEDATE provides the timestamp of the last message from that contact/group displayed
- ZLASTMESSAGE includes the foreign key for the last message from the contact or group in the ZWAMESSAGE table
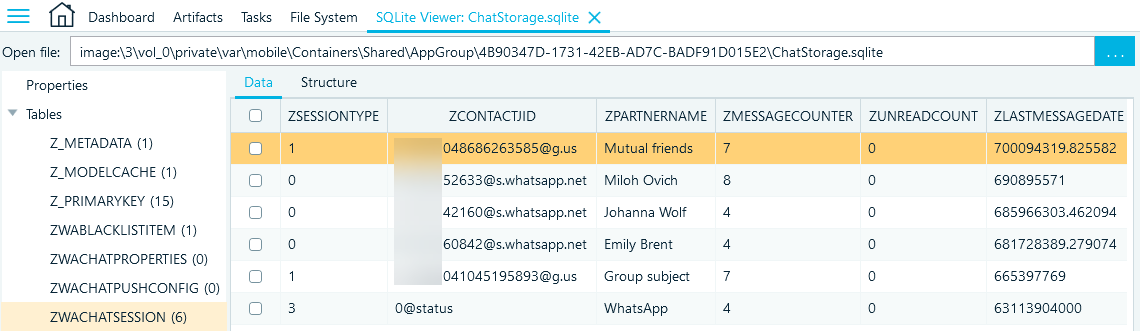
Figure 20: Columns of interest in the ZWACHATSESSION table (ChatStorage.sqlite)
The date columns in WhatsApp databases display the timestamps in the Apple Core Foundation Absolute Time, also known as Apple Cocoa Core Data Time (number of seconds since 01/01/2001 00:00:00 UTC). You can convert them to view the actual UTC time instead. Right-click the date header and select Choose column type → Apple Cocoa time:
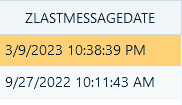
Figure 21: A timestamp column converted to Apple Core Foundation Absolute Time
The ZWAMESSAGE table contains the exchanged messages and attachments. Here are some useful columns that include their details:
- ZCHATSESSION is the foreign key that links to the ZWACHATSESSION table and helps to identify what conversation the record belongs to
- ZSORT includes the order of the message by the time of the appearance in a conversation; if numbers are missing (going like 1,2,4,7), it may indicate that some messages in the conversation were deleted "for Me" by the user
- ZISFROMME indicates the message direction: 0 stands for incoming messages, 1 for outgoing
- ZMESSAGEDATE contains the timestamp of the message creation
- ZSENTDATE provides the timestamp when the message was sent
- ZMESSAGETYPE indicates whether the message is a text (0), an image (1), a video (2), a voice message (3), a contact card (4), location (5), group (6), URL (7), file (8), and so on
- ZTEXT includes the text of the message, and it is empty if the text was deleted, or the message only included an attachment
- ZMEDIAITEM provides the foreign key to the ZWAMEDIAITEM table
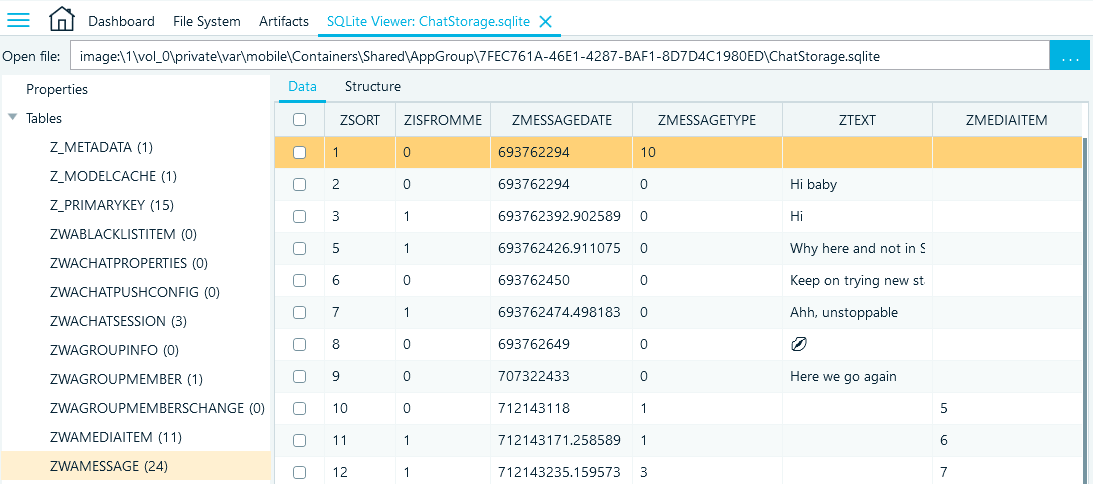
Figure 22: Columns of interest in the ZWAMESSAGE table (ChatStorage.sqlite)
The ZWAMEDIAITEM table includes the details of the exchanged attachments. Messages deleted "for Everyone" are part of this database as well. Here are some columns of interest:
- ZVCARDSTREAM contains information about the type of the attachment (for example, image/jpeg)
- ZVCARDNAME includes IDs of the exchanged media files, contact and location names, or the sender's ID for deleted messages
- ZMEDIALOCALPATH provides the location of the media file or document within the device file system (typically, .../<WhatsApp data folder>/Messages/Media)
- ZTHUMBNAILLOCALPATH, similarly, displays the location of the thumbnail file within the device file system
- ZLATITUDE and ZLONGITUDE include the coordinates of the location pin, while for images and videos, they show the width and height values
- ZTITLE contains the text sent along with the attachment; for messages deleted "for Everyone", it includes an alphanumeric value
- ZMEDIAURL includes the URL of the file during the transfer, while for locations, it displays the URL of the place
- ZAUTHORNAME may include metadata of exchanged documents
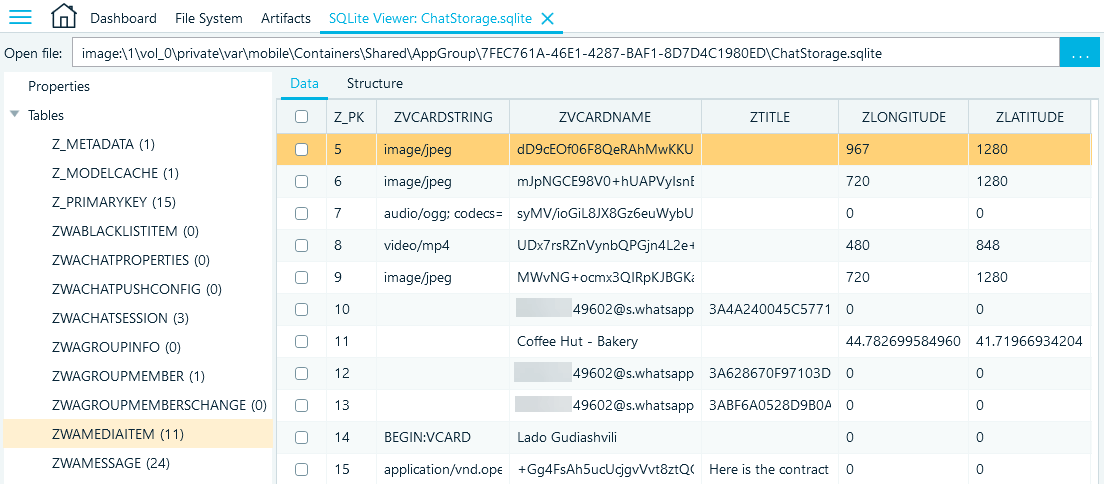
Figure 23: Columns of interest in the ZWAMEDIAITEM table (ChatStorage.sqlite)
CallHistory.sqlite
The CallHistory.sqlite database contains the timestamps, durations, and participants of the user's calls in the ZWACDCALLEVENT table. You can find this information in the following columns:
- ZDATE includes the call timestamp
- ZDURATION provides the call duration (in seconds)
- ZGROUPCALLCREATORUSERJIDSTRING indicates what contact initiated the call
- ZBYTESSENT and ZBYTESRECEIVED include the call traffic details
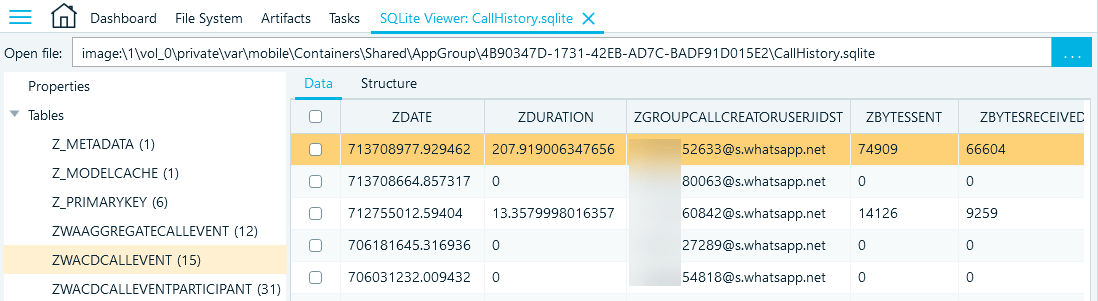
Figure 24: Columns of interest in the ZWACDCALLEVENT table (CallHistory.sqlite)
ContactsV2.sqlite
The ContactsV2.sqlite database includes the user's WhatsApp contacts in the ZWAADRESSBOOKCONTACT table.
- ZFULLNAME, ZGIVENNAME, and ZHIGHLIGHTEDNAME include the contact's naming details
- ZPHONENUMBER provides the contact's phone number
- ZWHATSAPPID includes the ID used to identify the contact in the chat
- ZABOUTTEXT includes the contact's "about" message
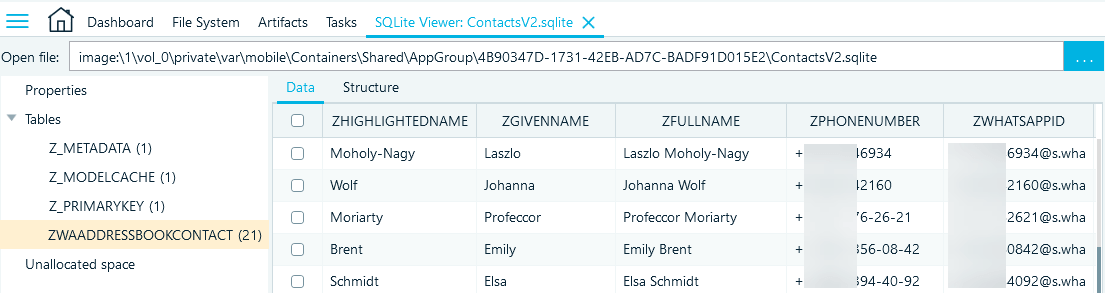
Figure 25: Columns of interest in the ZWAADRESSBOOKCONTACT table (ContactsV2.sqlite)
You can export WhatsApp databases and examine them in other DB browsers if needed.
Conclusion
When examining iOS WhatsApp, you have several methods available to acquire its data. In this article, we described the criteria for choosing the appropriate method, which include the way the messenger is configured to store data and manage backups, and how the iOS backups are configured.
Belkasoft X helps you to conduct an in-depth analysis of iOS WhatsApp. The product enables you to acquire WhatsApp data through various methods, such as agent-based and checkm8-based acquisition, iTunes backup, and iCloud backup downloading. Belkasoft X automatically locates and analyzes WhatsApp databases, presenting all the extracted information in a user-friendly format to facilitate the examination process. It also lets you locate the application databases in the file system and examine them in the built-in SQLite Viewer.

