Android WhatsApp Forensics. Part II: Analysis
Introduction
Android WhatsApp is undeniably one of the most sought-after applications in mobile forensics. In the first part of this article, we explored the folders and files that store WhatsApp data on Android devices and the methods that let you extract them. As you begin to examine Android WhatsApp data, you should consider the application features that create the database records. This knowledge helps you understand what evidence to look for and how to interpret your findings accurately.
In this part of the article, we will look into the forensic analysis of Android WhatsApp, covering the following topics:
- Features to consider in WhatsApp forensics
- Digital forensic evidence in Android WhatsApp databases: wa.db, msgstore.db, companion_devices.db
- Tips on how to analyze Android WhatsApp in Belkasoft X
Belkasoft X provides a comprehensive toolset for analyzing and navigating data acquired from mobile devices and computers.
Forensically important features of WhatsApp
You may be curious to know that the initial idea behind WhatsApp was to show its user's status updates—hence the name; though, quite quickly it grew into a messenger. Present-day WhatsApp users can engage in one-to-one and group chats by exchanging:
- Text messages
- Media files such as pictures, video, audio, and documents
- Location pins and live locations
- Contact cards
- Polls
WhatsApp messages can be starred, edited, and deleted. Users can also configure disappearing messages that are wiped from selected chats after a specified period of time.
The WhatsApp status transformed into several one-way communication features:
- The multimedia status that lasts 24 hours
- The broadcast feature that allows sending messages to multiple conversations individually
- Channels used to post content for a group of followers
The application also supports VoIP and video calls, including conferences. Additionally, in some countries, it can be used for payments. With such a variety of features, WhatsApp users leave numerous digital traces that provide insights into their connections, interactions, behaviors, locations, and more.
Moreover, a single WhatsApp account can be used across multiple devices. This feature can aid in identifying additional devices involved in the account usage.
Evidence in Android WhatsApp databases
Now that you know how users can interact with the WhatsApp application, let us delve into the database records these activities create.
wa.db
The wa.db table is your source of information about the account owner's contacts and groups.
wa_contacts can reveal the names of the account owner's contacts, their phone numbers, "about" information, and other details. When exploring the jid column containing user's chat IDs, you may notice that several types of contact records are available:
- @broadcast indicates broadcast groups, with status@broadcast being reserved for the user's multimedia statuses
- @s.whatsapp.net stands for one-to-one chats
- @g.us indicates group chats
- @newsletter identifies channels
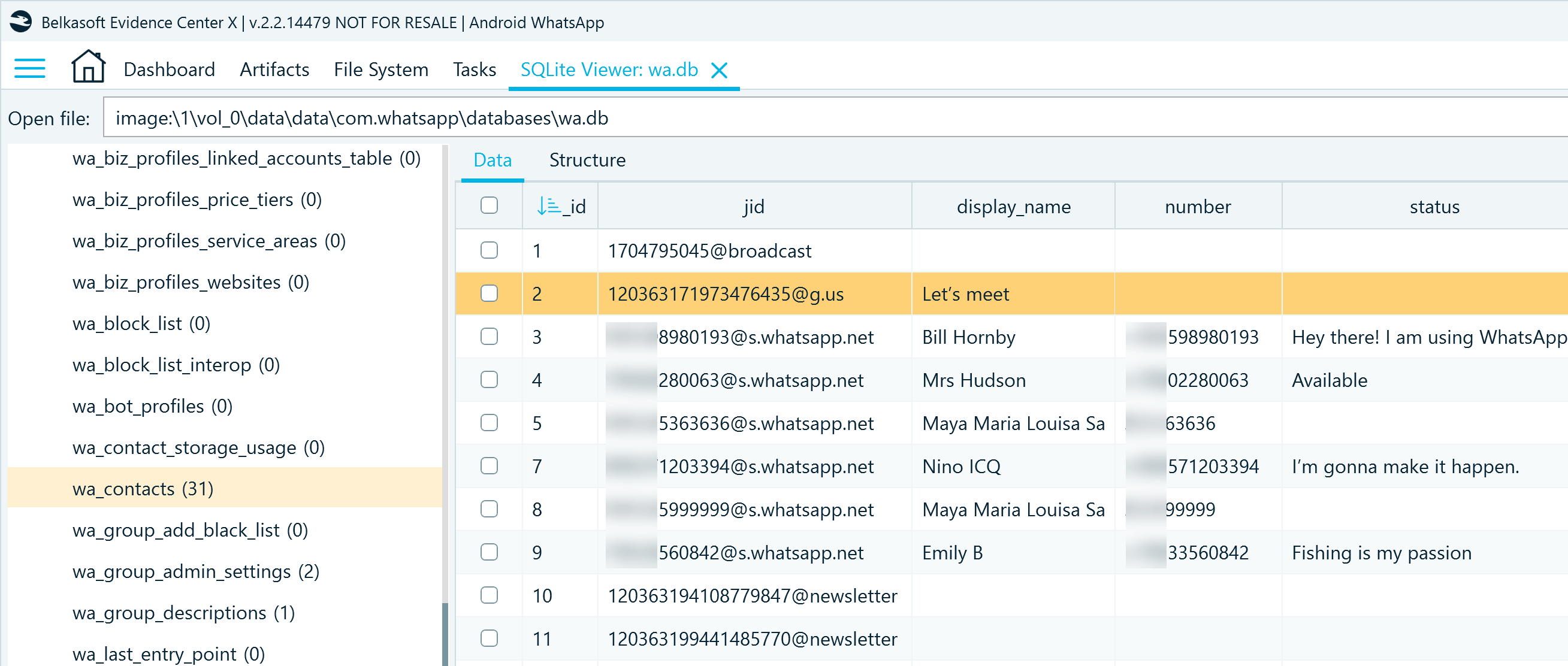
Figure 1: WhatsApp contact records in wa.db, wa_contacts table
wa_bloc_list offers insights into the unwanted contacts in the user's list. Interestingly, it also includes the blocked contact's internal WhatsApp ID indicated by @lid.
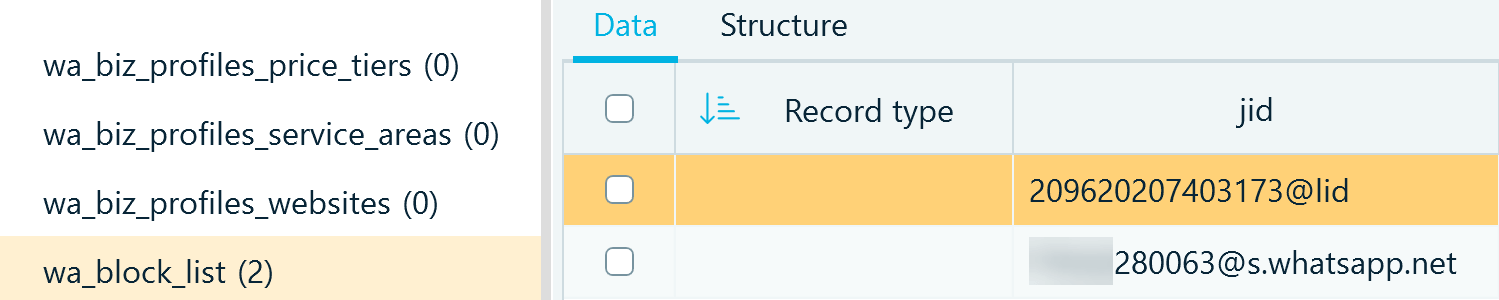
Figure 2: WhatsApp blocked contact records in wa.db, wa_block_list table
wa_group_admin provides one more notable piece of information. creator_jid helps you define the admins of the group chats where the user participates.
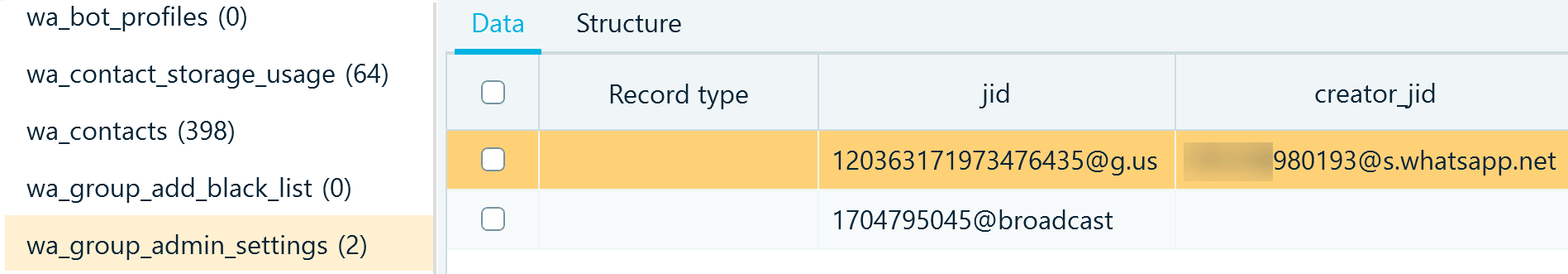
Figure 3: WhatsApp group records in wa.db, wa_group_admin_settings table
msgstore.db
msgstore.db is the largest database in the Android WhatsApp dataset. It contains the account owner's conversations stored in the message table and all associated information spread across other tables. Here are the columns of primary interest in the message table:
- chat_row_id indicates in what chat a message was exchanged; it is a foreign key that links to the _id column in the chat table that stores chat details
- sender_jid_row_id indicates the contact that sent the message; it is a foreign key to the _id column in the jid table that stores contact IDs
- from_me specifies if the message is incoming or outgoing
- message_type indicates what kind of data the message includes; it may be a text (0), picture (1), audio (2), video (3), contact card (4), location (5), system info (7),document (9), deleted message (15), live location (16), and so on
- timestamp contains the Unix timestamp (UTC) of when the message was sent or received; additional timestamps can be found in the received_timestamp and receipt_server_timestamp columns
- text_data includes the text of the exchanged message
- starred indicates if the user bookmarked the message
- message_add_on_flag helps you find out if the message received reactions or was marked to be kept in disappearing chats; the number in this column links to the _id column in the message_add_on table where you can find further information on the add-on type (we will look at it more closely later)
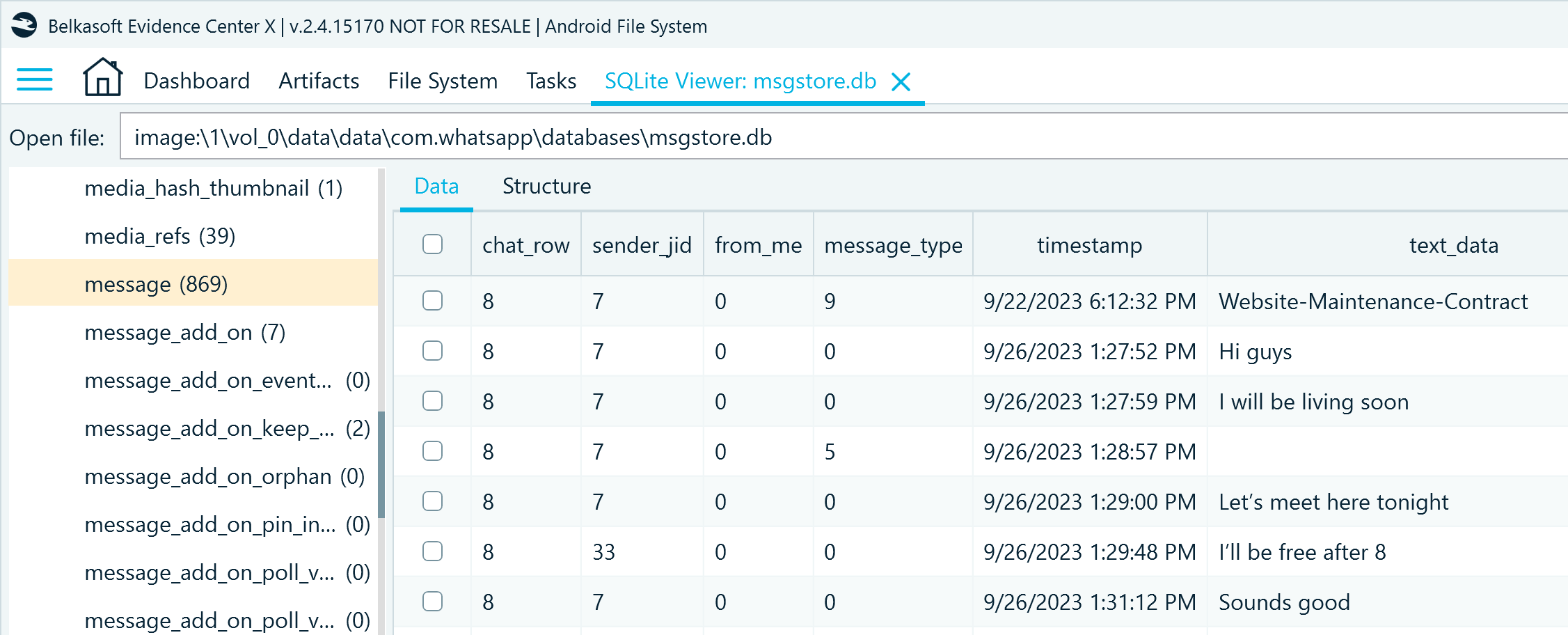
Figure 4: WhatsApp conversation records in msgstore.db, message table
You can find additional details of non-text messages in the following tables:
- message_location stores the geolocation data exchanged in the messages
- message_media reveals the paths to the exchanged files stored in WhatsApp backup folders and other details
- message_tumbnail stores the graphic previews of the exchanged non-text messages
- message_vcard includes the details of the exchanged contact cards
The message_add_on table stores the details of the messages that received reactions, were edited, or marked to be kept in disappearing chats:
- parent_message_row_id defines the affected record _id in the message table
- timestamp shows when the add-on was applied
- message_add_on_type helps identify the type of add-on: 56 indicates an emoji reaction (see table message_add_on_reaction for details), 68 stands for the "keep disappearing" flag (with more details in the message_add_on_keep_in_chat table), 74 indicates that the message was edited (with more details in the message_edit_info table)
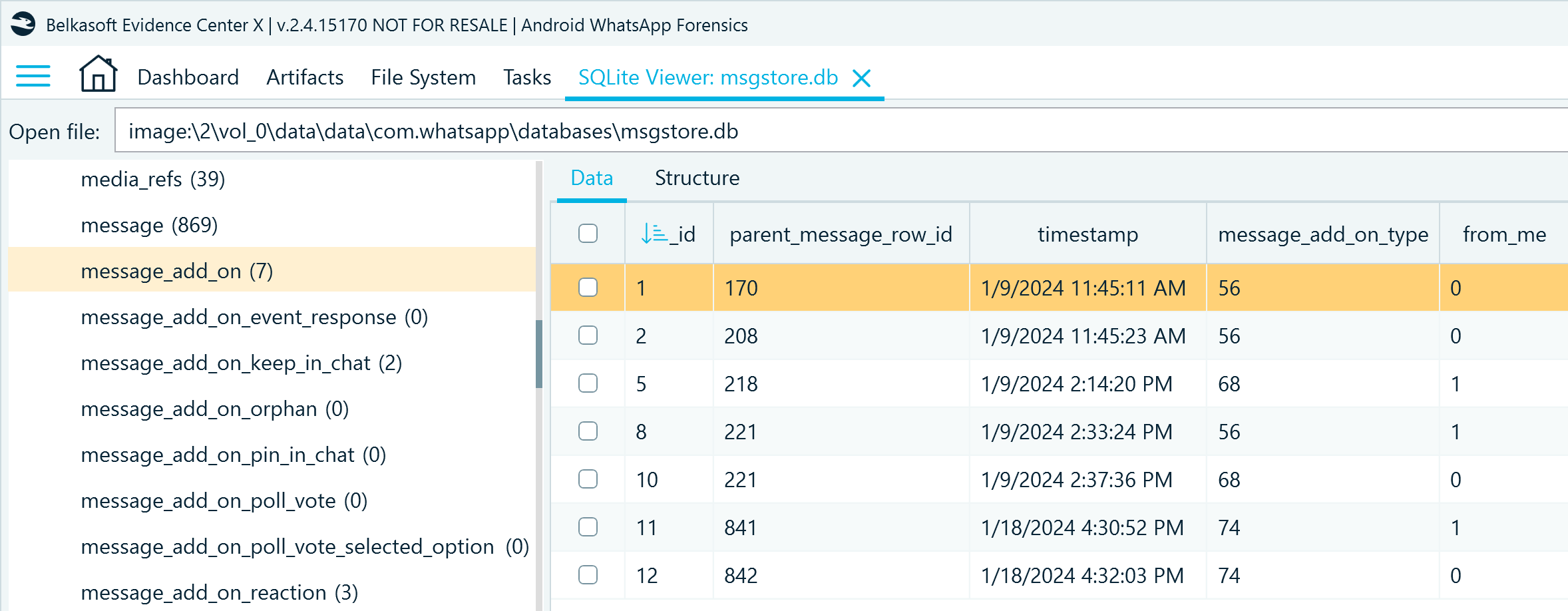
Figure 5: Records of messages with reactions and other marks in msgstore.db, message_add_on table
The message_quoted table can help you identify if a message in a chat was sent as a reply to another message:
- message_row_id includes the reference of the message that was posted as a reply (_id in the message table)
- from_me indicates if the message was sent by the account owner
- timestamp shows the time when the reply was sent
- text_data includes the text of the quote
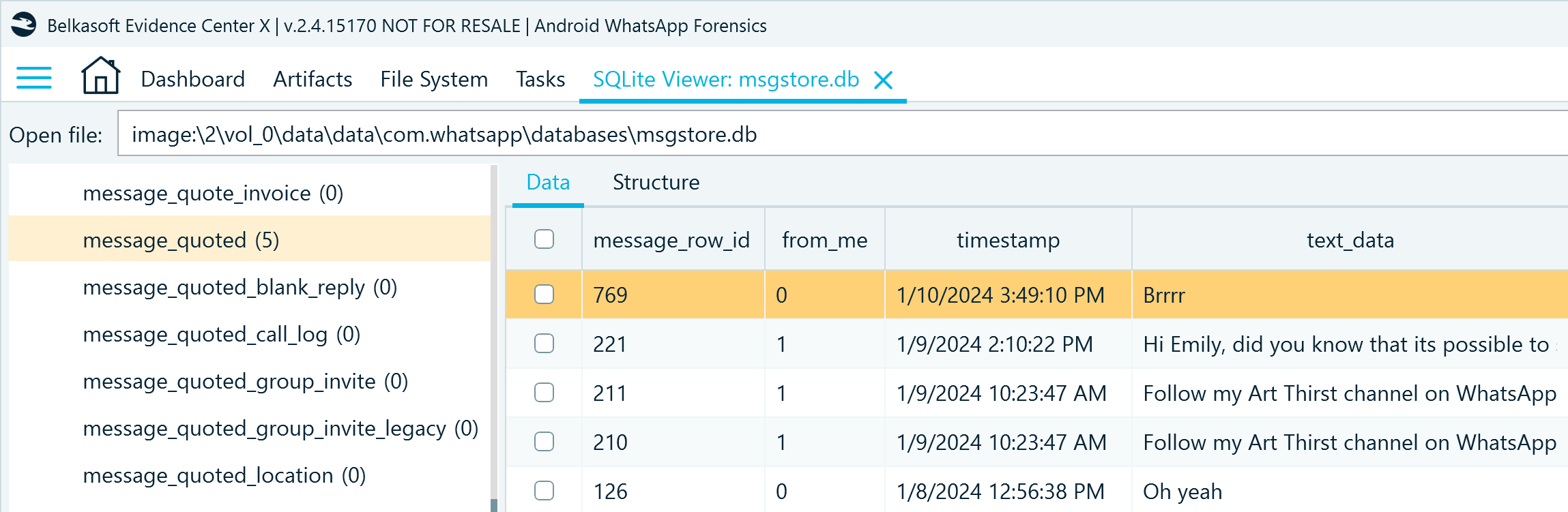
Figure 6: Records of message replies in msgstore.db, message_add_on table
If the quotes include other data like media files, locations, and so on, additional details are stored in message_quoted_media, message_quoted_text, message_quoted_location, message_quoted_vcard, and other associated tables. "message_quoted" tables are particularly interesting because they preserve the contents of deleted messages that were quoted before being deleted.
As for the call records, you can find them in the call_log table:
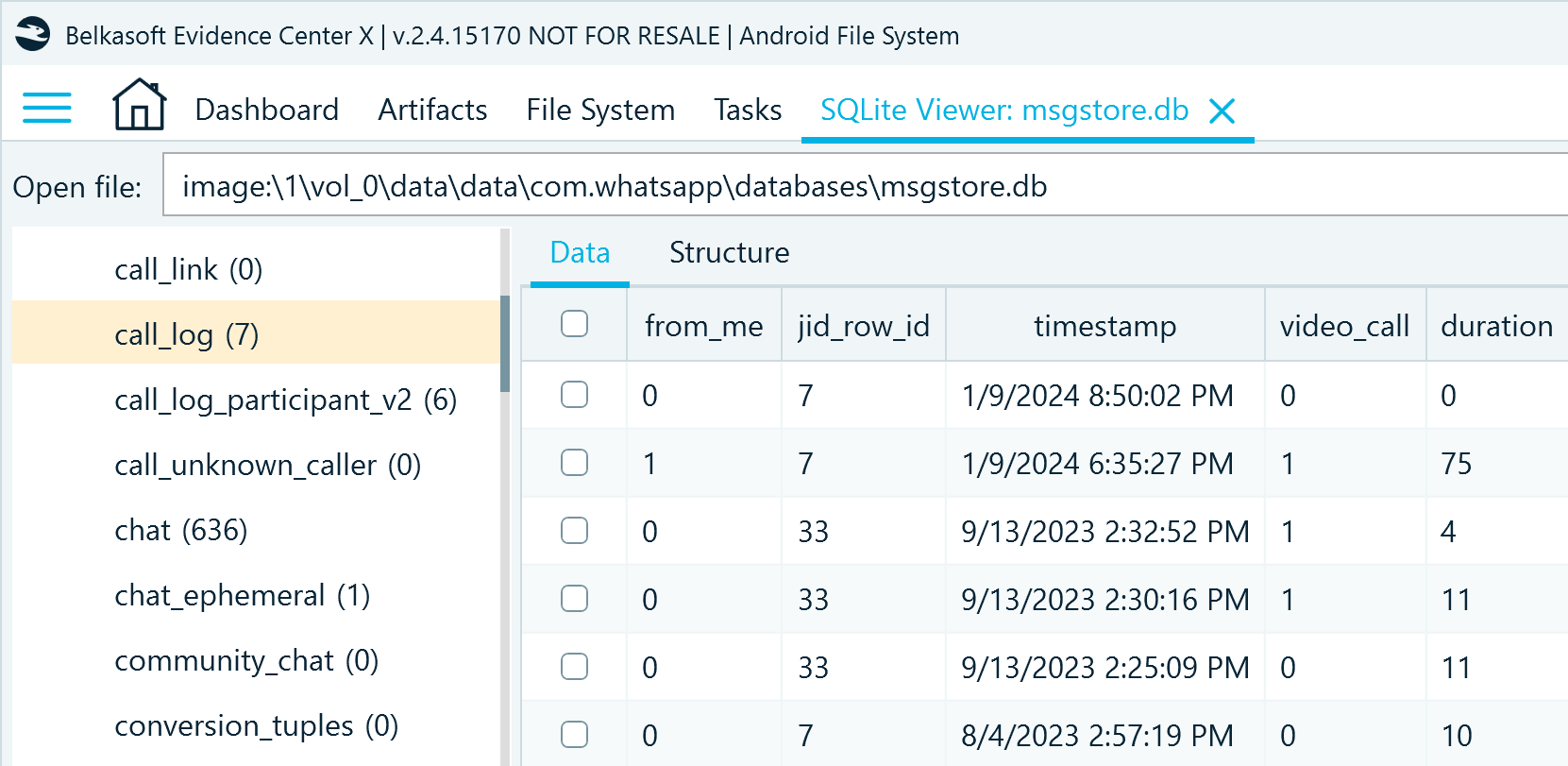
Figure 7: WhatsApp call records in msgstore.db, call_log table
companion_devices.db
By analyzing companion_devices.db, you can find additional details about WhatsApp account usage. The devices table reveals information about the devices connected to the account through the linking functionality:
- device_id includes the account phone number appended by a connection ID and the @s.whatsapp.net suffix
- device_os indicates the type of operating system where the account is or was used. In the screenshot below, you can notice that some records list Belkasoft in device_os records. These records appeared when we used the WhatsApp QR method to acquire account data.
- platform_type specifies the type of WhatsApp client used to access the account; 1 represents the web browser client, and 21 stands for the Windows desktop client
- place_name reveals the approximate geolocation of where the linking took place
- last_active, login_time, and logout_time contain UTC timestamps of the linking events in the Unix format; in the screenshot below, they are converted for easier examination.
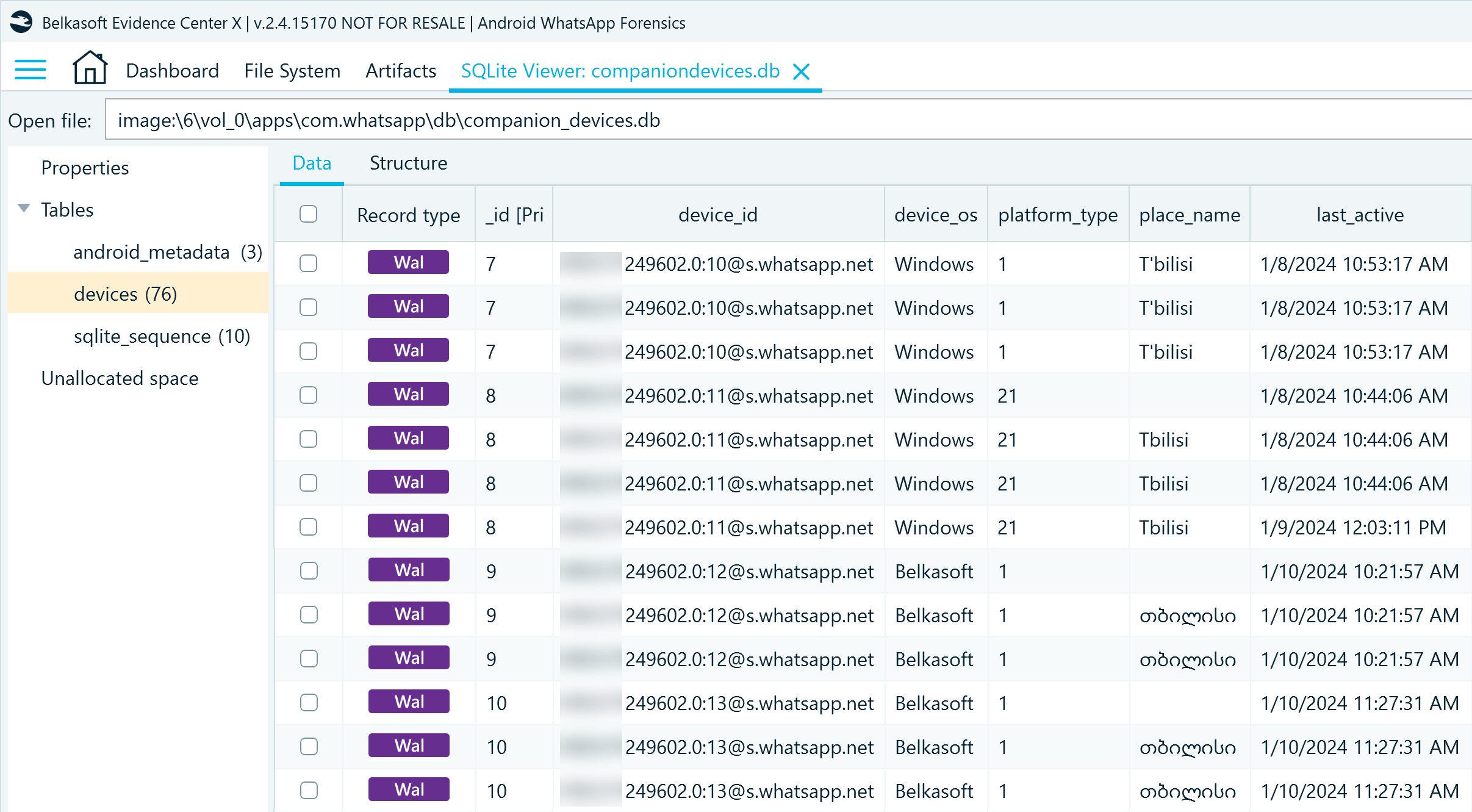
Figure 8: Records of devices linked to a WhatsApp account in companion_devices.db, device table
These records can provide insights into additional devices used by the WhatsApp account owner and help with a timeline of events. In some cases, they may also indicate that a third party had access to the account owner's conversations and could exchange messages on their behalf.
How to analyze Android WhatsApp in Belkasoft X
Belkasoft X analyzes WhatsApp folders available in the device image, extracting and reconstructing the account owner's conversations. In this section, we will cover how to streamline Android WhatsApp examination tasks in the tool.
Explore the artifacts
When you add an Android device image as a data source in Belkasoft X, the tool presents the extracted findings in the Artifacts window. You can locate the WhatsApp profile on the Structure tab under Chats:
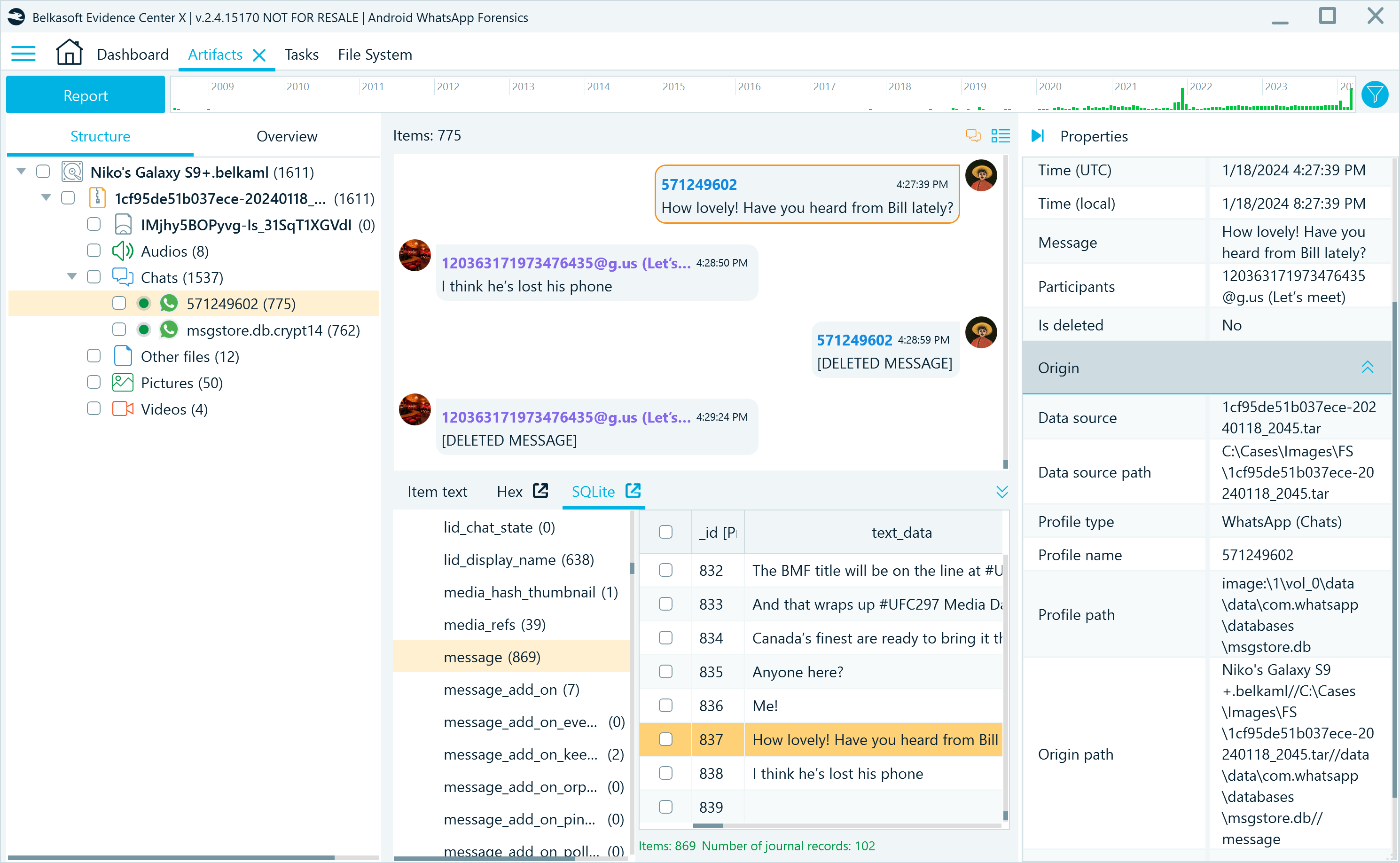
Figure 9: WhatsApp application profiles in Belkasoft X, Artifacts window
The profile appearance depends on the type of device image you examine. The screenshot above showcases an analyzed "File system copy" image. Such images typically include two or more profiles:
- The main database profile extracted from the application folder; it is identified by the user's phone number without the country code
- The msgstore.db.crypt14 profile that originates from the automatically decrypted database backup; its earlier versions will also be displayed, if available
If you have an APK downgrade image, you will only find the main database profile since this method does not copy backup folders.
The middle pane in Belkasoft X reveals the user's sent and received messages in the bubble chat view. You can select a message and inspect its details in the Properties pane. You can also find its source SQLite record highlighted in the SQLite viewer.
Examine chats individually
By default, the Artifacts window displays messages from all user's chats in one view. If you want to look into each chat individually, in the Structure tab, right-click a WhatsApp profile and select Show contacts:
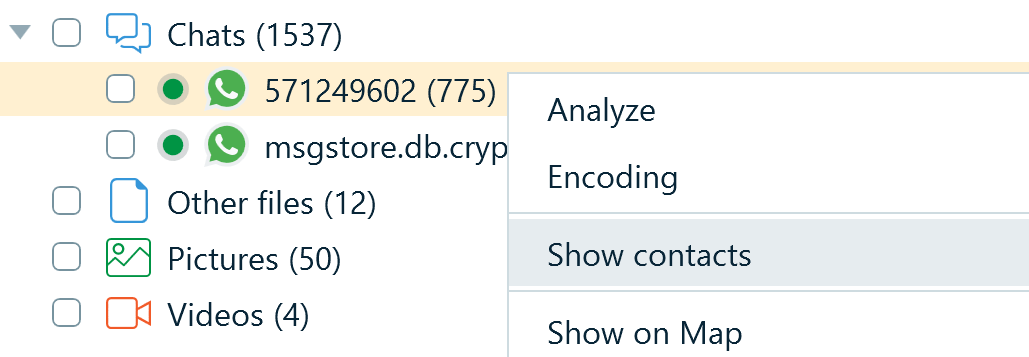
Figure 10: Configuring the WhatsApp profile to show chats individually
The database may also include cached chats with which the user did not interact. For example, such records are created when the user browses through WhatsApp channels. To avoid scrolling through multiple empty nodes, you can right-click the profile and select Hide empty conversations.
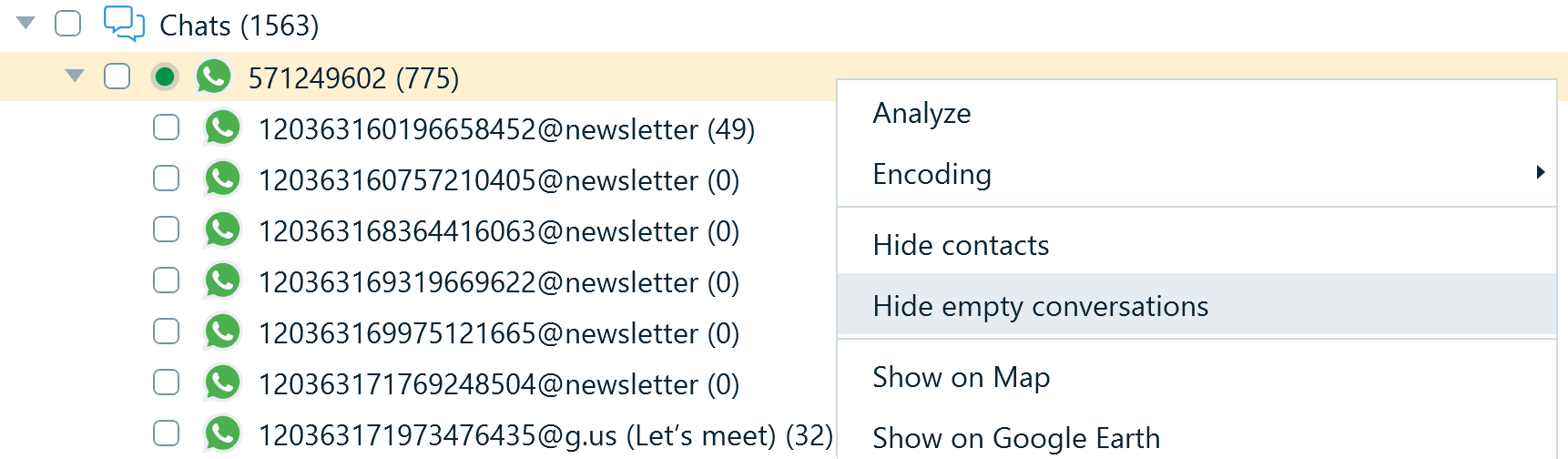
Figure 11: Configuring the WhatsApp profile to hide chats without message history
As a result, Belkasoft X only displays chats with message history. You can understand the types of these chats by their "@ suffixes," which we have covered when exploring the wa.db database records.
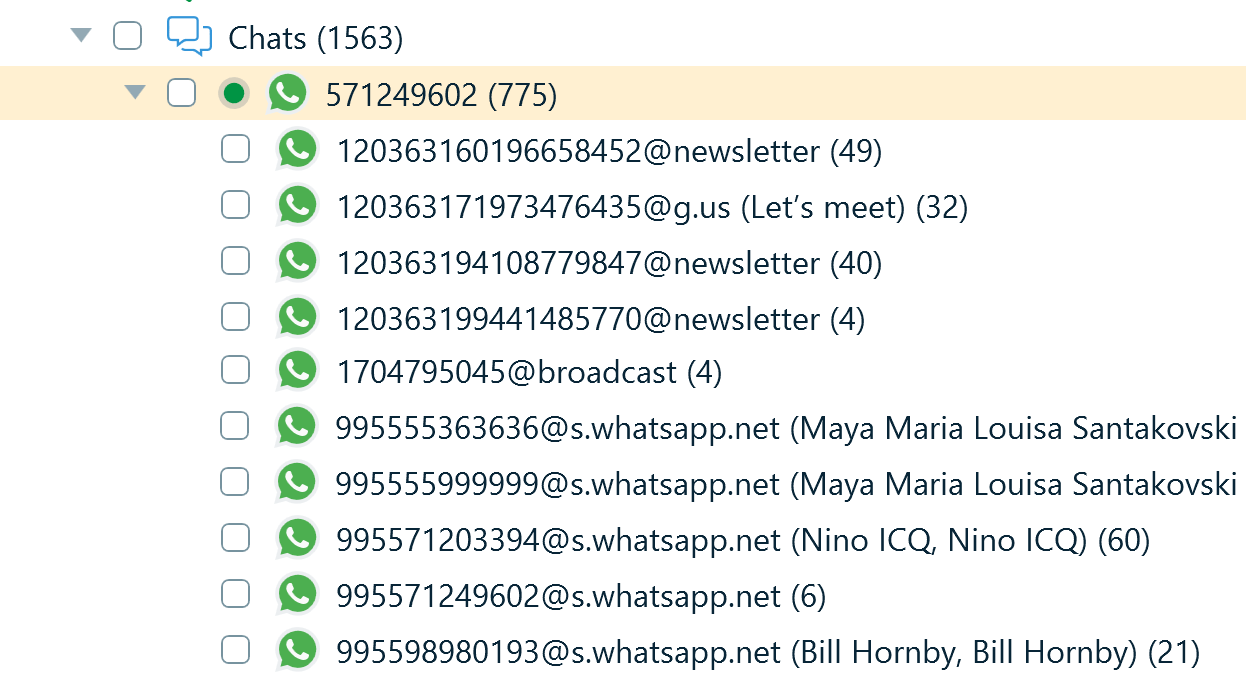
Figure 12: WhatsApp profile displaying various types of individual chats
Apply search filters
When you need to narrow down your search, you can switch to the grid view and apply search filters. For example, you may want to search the exchanged messages for specific keywords or locate all files the account owner received in the conversations:
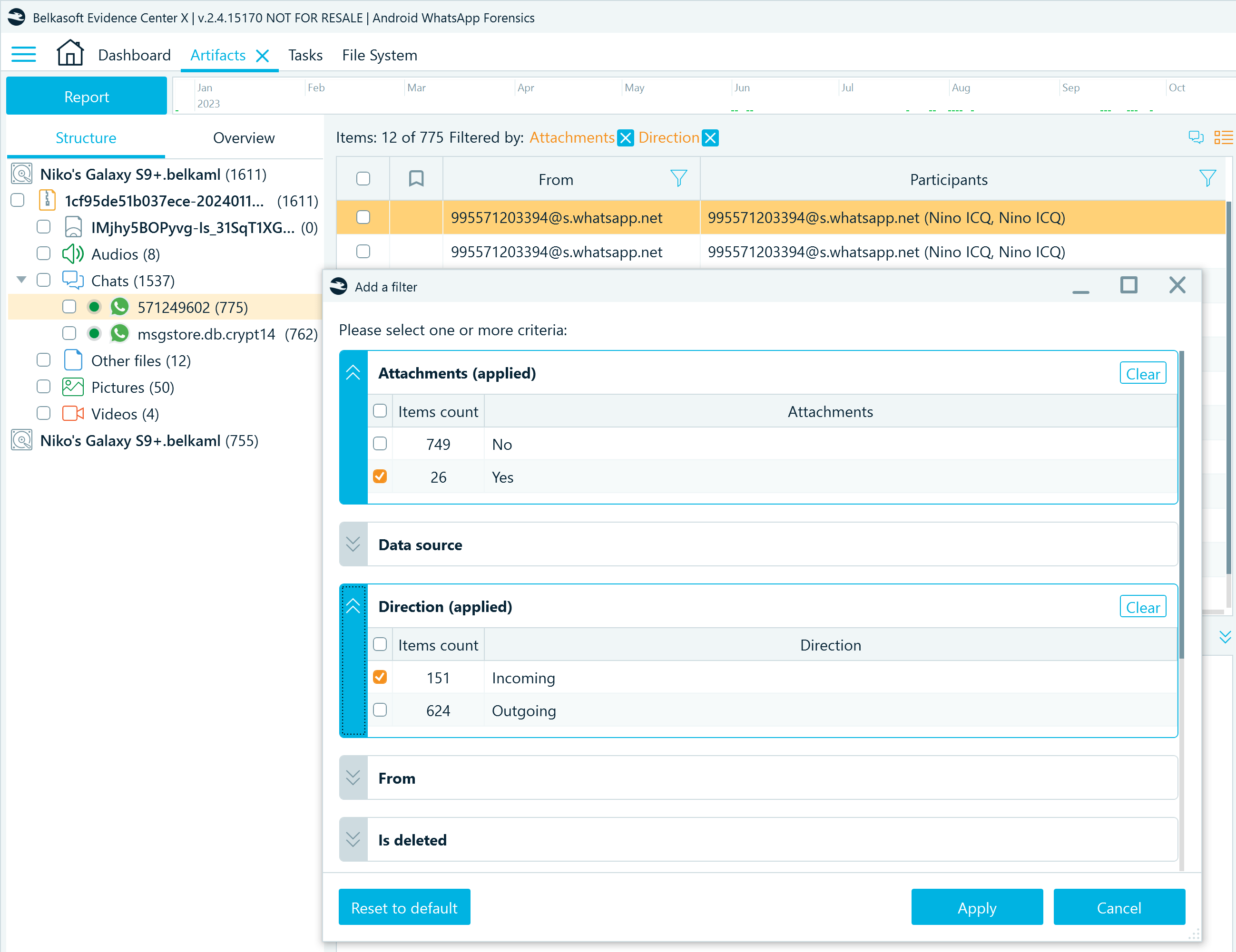
Figure 13: WhatsApp artifacts filtered by attachment availability and message direction
Locate attachments
When WhatsApp users exchange media files, the database records their binary representation and location on the device file system. When Belkasoft X analyzes these records, it marks messages with attachments by the TRANSFER tag that also includes the description of the exchanged file type (for example, [VIDEO TRANSFER], [FILE TRANSFER], and so on). When examining such messages, you can find the representations of exchanged files in the Attachments pane.
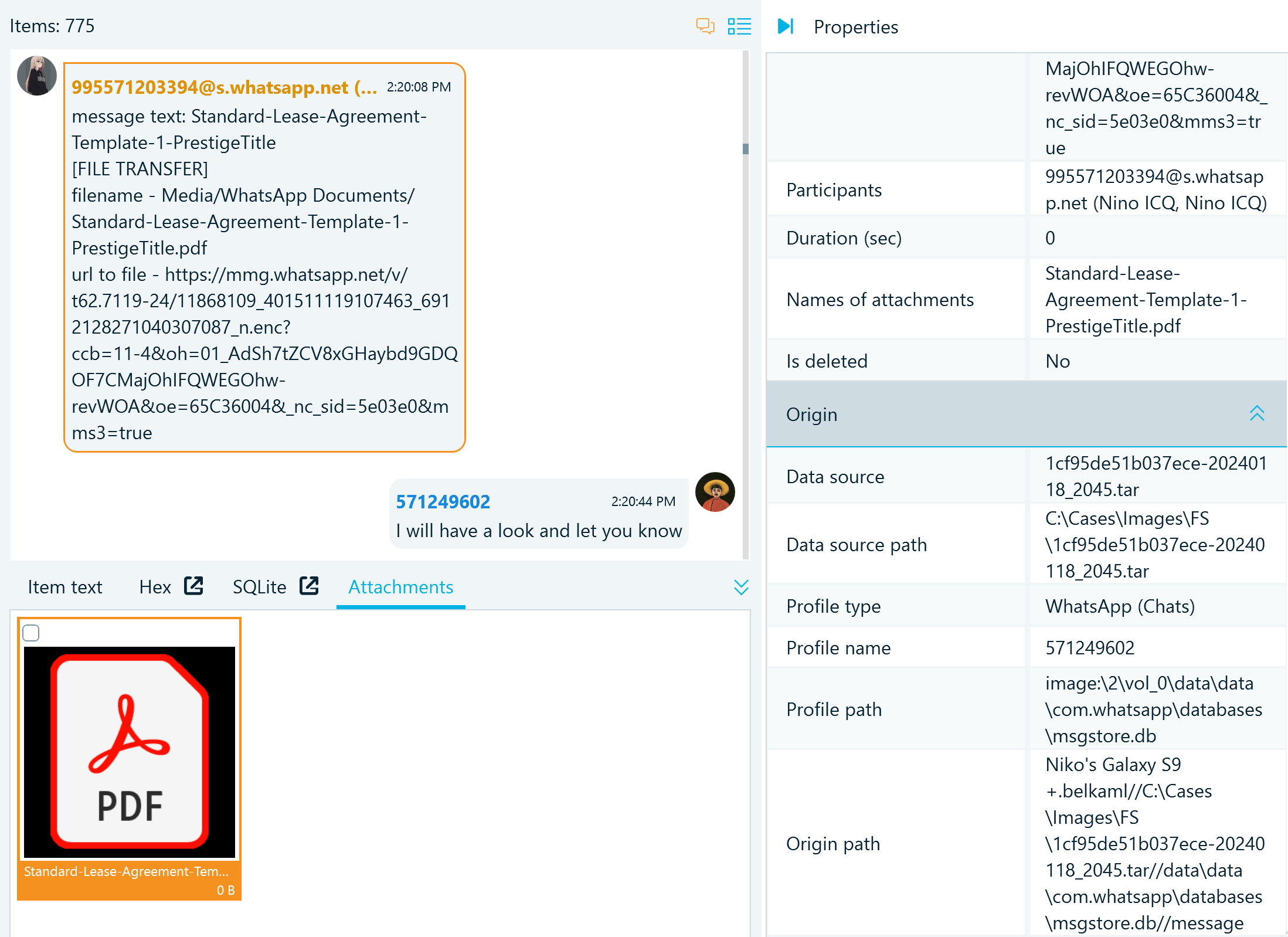
Figure 14: The representation of a WhatsApp message that includes a document attchment
Note that the original files stored in WhatsApp backup folders may be missing from some device images, such as those acquired with the APK downgrade method. This is why, in the previous article on WhatsApp acquisition, we emphasized the importance of copying backup folders from the device as the first step in WhatsApp data acquisition. You can later import these folders as an additional data source to your case to complete the application dataset.
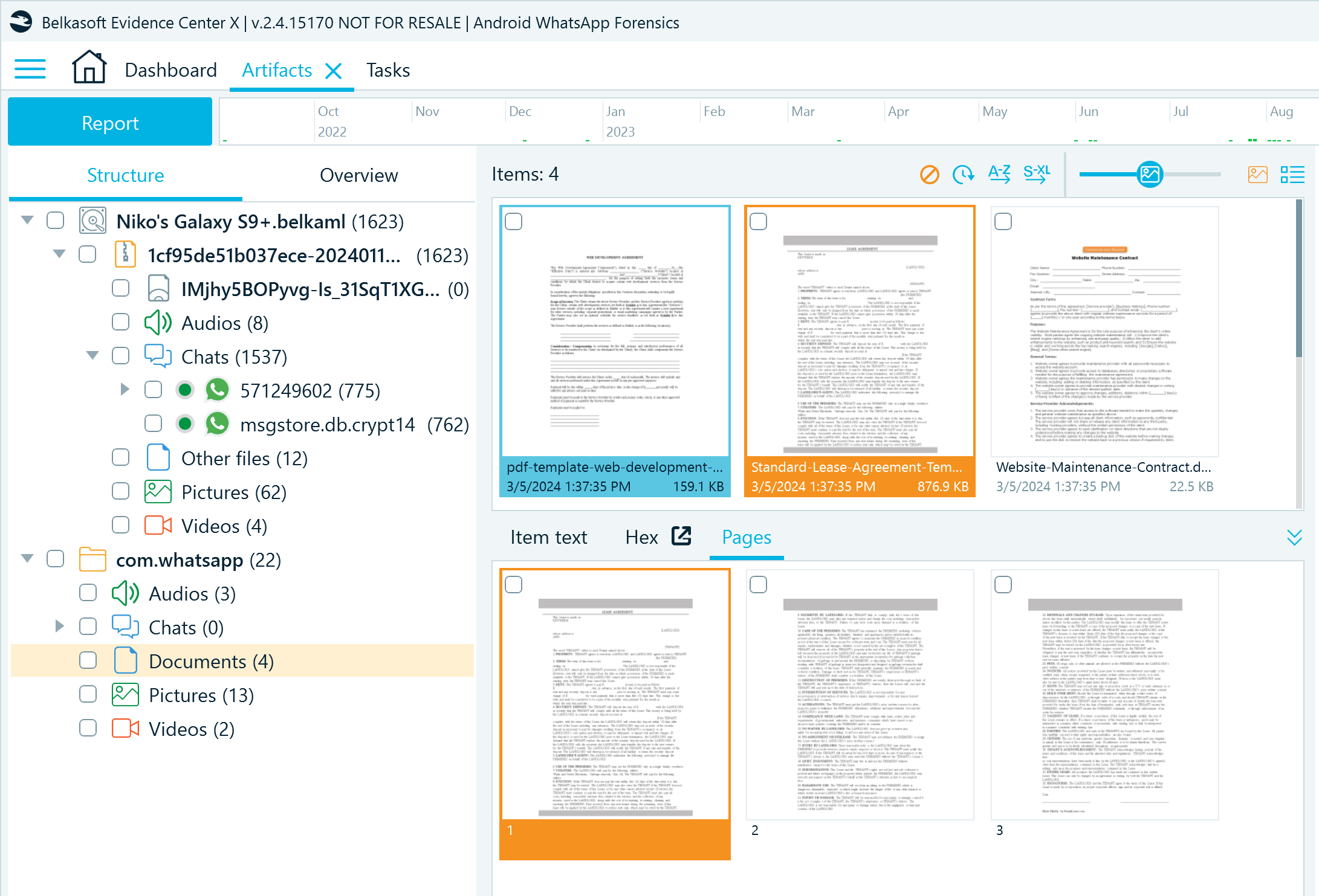
Figure 15: Android WhatsApp media files extracted from the backup folder copy
Decrypt database backups
When analyzing WhatsApp backup folders, Belkasoft X also locates the msgstore.db database backups, but to view their contents, you need to decrypt them.
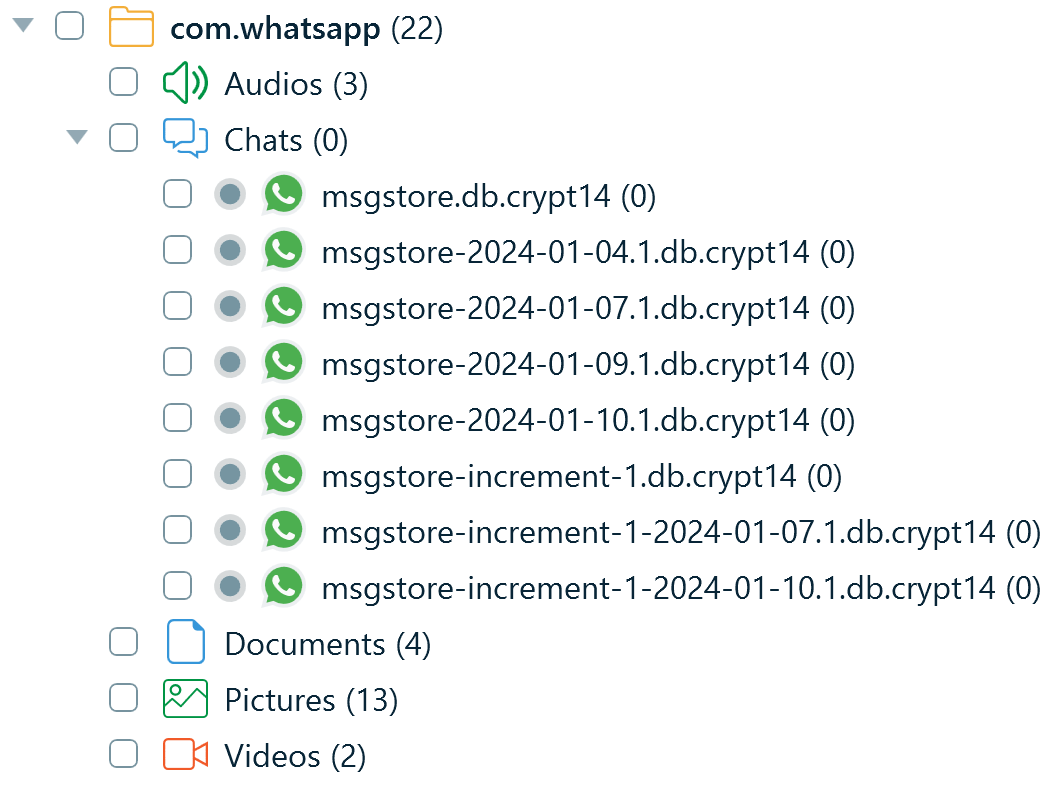
Figure 16: Profiles of encrypted Android WhatsApp database backups extracted from the backup folder copy
As we explained in the first part of this article, WhatsApp database backups are encrypted with the key stored in the application resource folder. The location of the key depends on the type of the device image you have:
- File system copy: ..\data\data\com.WhatsApp\files\key
- APK downgrade image: ..\apps\com.WhatsApp\f\key
To get a copy of the key, from the main menu, select File System and locate the key file. Then, right-click the file, select Copy files to folder, and specify the path where you want to save the file:
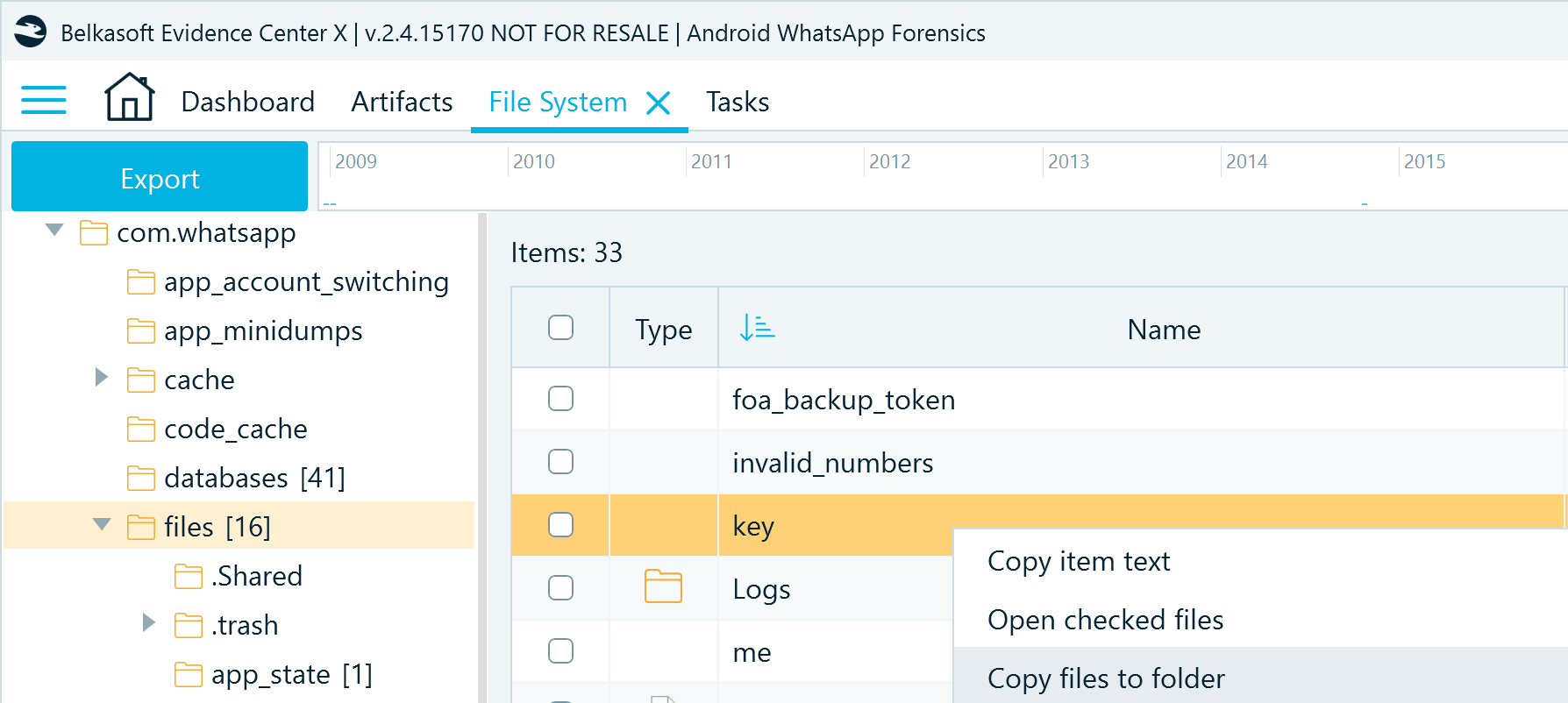
Figure 17: Copying the Android WhatsApp decryption key file from the application resource folder
Next, go to the Tasks window. The pending decryption tasks display the Enter missing data button:
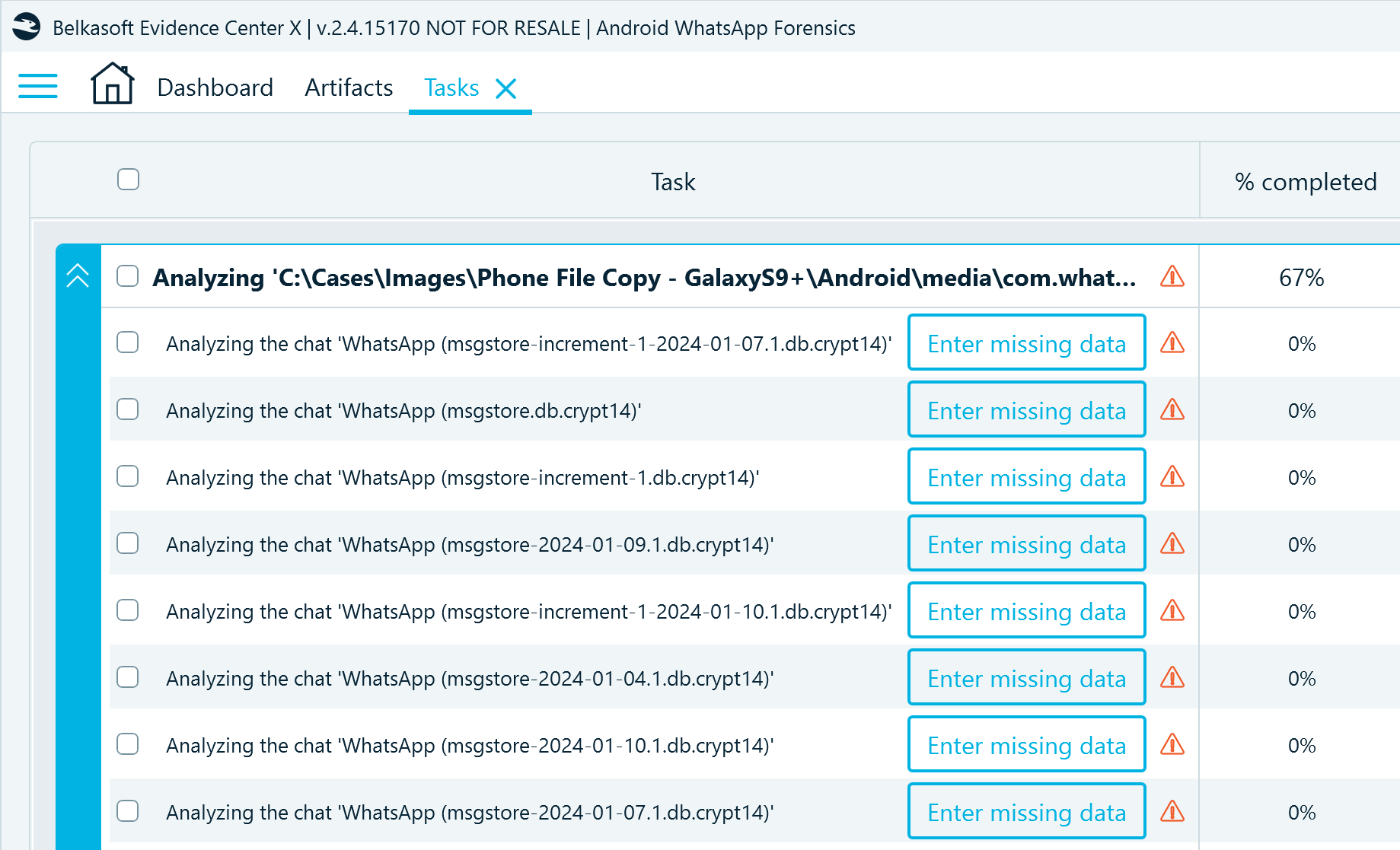
Figure 18: The Tasks window in Belkasoft X displaying the pending database decryption tasks
Click Enter missing data and specify the path to the decryption key:
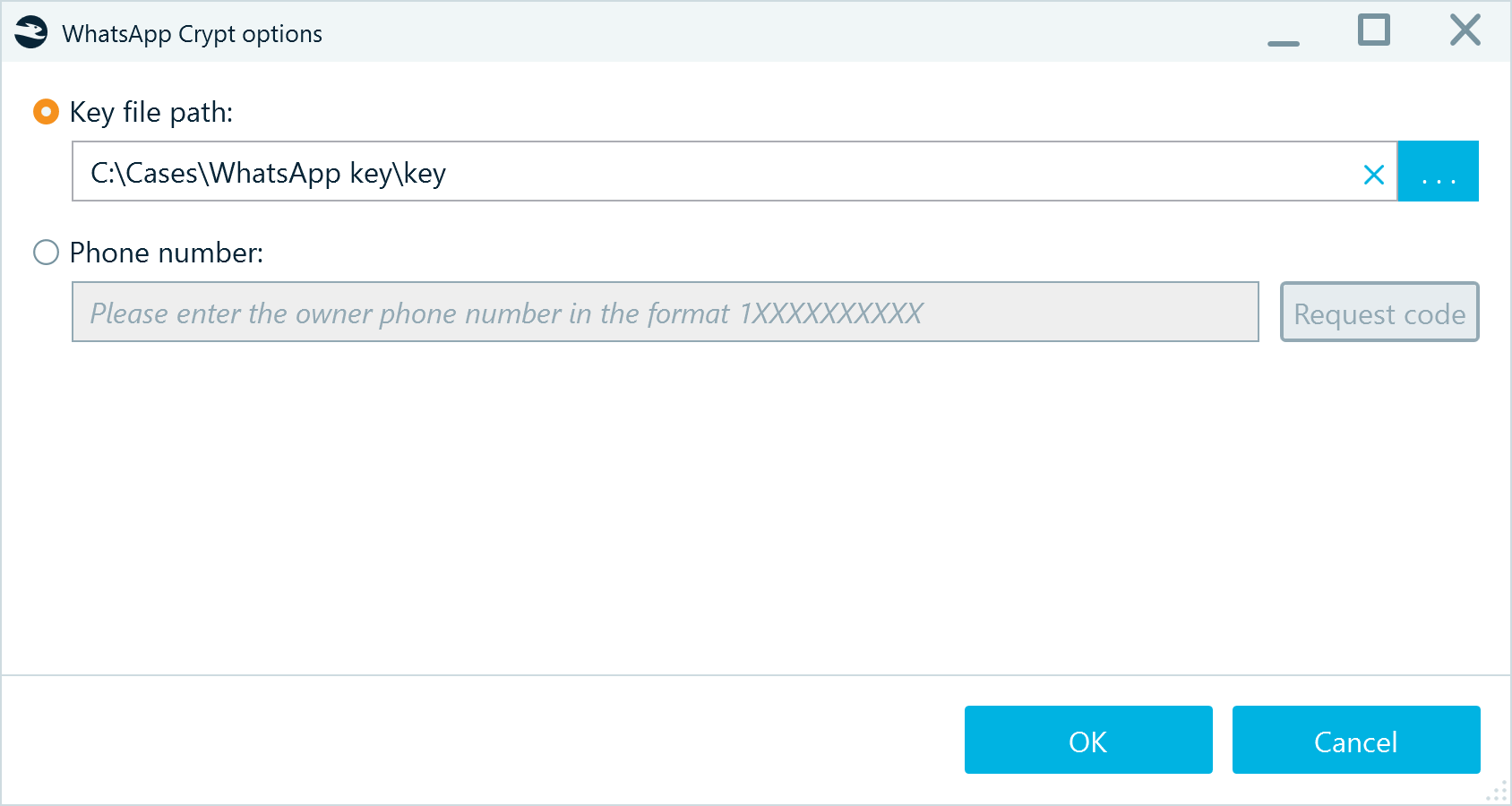
Figure 19: Supplying the path to the WhatsApp database decryption key
Repeat these steps for all encrypted WhatsApp databases. To avoid navigating to the key file each time, you can copy its path after specifying it for the first time and paste it in the Key file path field for all subsequent decryptions.
When all tasks are completed, you can view and compare decrypted database backups in the Artifacts window:
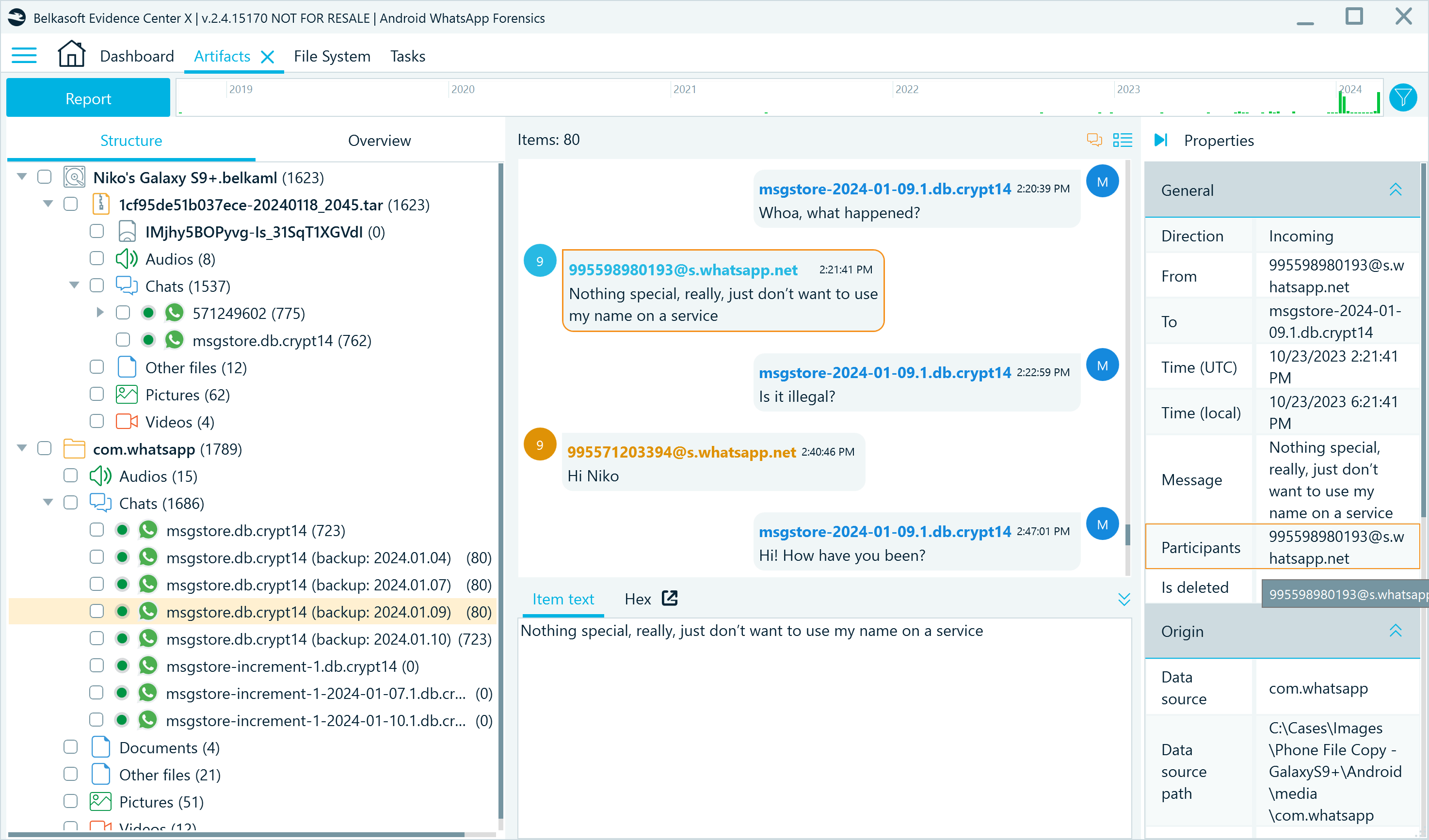
Figure 20: The Artifacts window displaying decrypted database backups and their contents
Conclusion
Analyzing WhatsApp data from Android devices provides valuable insights into users' interactions, behaviors, and connections. The examination of databases such as wa.db, companion_devices.db, and msgstore.db uncovers a detailed picture of WhatsApp usage, including contacts, groups, linked devices, conversations, and media exchanges. With tools like Belkasoft X, you can efficiently explore and interpret this data, identifying key details and reconstructing timelines of events for your digital investigation.

