Android WhatsApp Forensics. Part I: Acquisition
Introduction
WhatsApp emerged in 2009, rapidly becoming the go-to communication app for iOS users. When its Android version was launched a year later, the app was already popular enough to quickly grow a large Android user base that has substantially increased over time. Today's global popularity of WhatsApp and the wide usage of Android mobile devices make Android WhatsApp one of the foremost sources of evidence in criminal and cybersecurity investigations.
In this article, we will begin to explore Android WhatsApp forensics, focusing on how to obtain WhatsApp data from an Android device:
- How Android WhatsApp stores and backs up data
- Forensically important WhatsApp files in the Android file system
- How to acquire Android WhatsApp data
- Best practices for acquisition of Android WhatsApp
For obtaining and navigating Android WhatsApp data, we will use Belkasoft X, a DFIR tool that streamlines mobile forensics tasks, enabling you to acquire and analyze a wide range of digital artifacts from mobile devices, computers, and clouds.
How Android WhatsApp stores data
Device file system
On Android devices, WhatsApp houses its resources in the Application Sandbox. The resource folder within the device file system contains chat databases in an unencrypted form, but you can only access this folder on rooted devices.
Backup folders within the device
Android WhatsApp creates daily backups of chat databases within the device, encrypting them with a key stored in the Application Sandbox. WhatsApp backup files are accessible through the Media Transfer Protocol (MTP) when connecting a device to a computer via USB. Depending on how the device is set up to store application data, you can find backups either within its internal memory or on the SD card in it.
Chat databases in the backup folder are encrypted in the CRYPT14 or CRYPT15 format, while media files are stored as-is.
Google Account cloud storage
Users can opt to upload WhatsApp backups to their Google Account cloud storage. Like on devices, media files in these backups are stored as-is, and databases are by default encrypted in the CRYPT14 format.
End-to-end encrypted backups
The WhatsApp end-to-end backup encryption option offers additional protection for backups. It involves securing access to backup files with a password or 64-digit encryption key and encrypting the database file in CRYPT15 format. If a user activates this protection, the application chats can only be restored from a backup with the additional password or key. Note that this setting affects both the files uploaded to the cloud and those stored on the device.
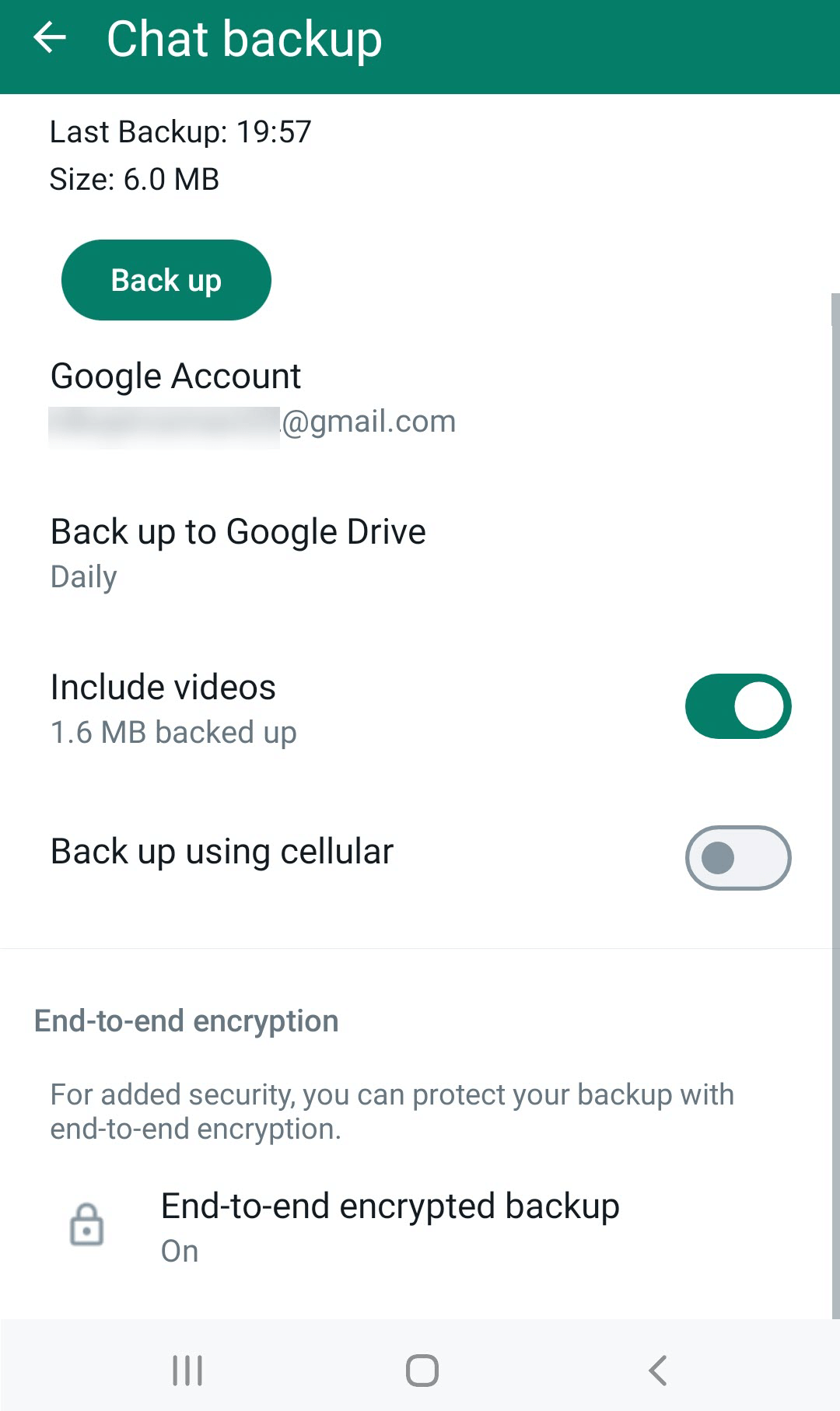
Figure 1: Backup Encryption options in Android WhatsApp settings
Android WhatsApp files of interest
Databases
On Android devices, WhatsApp stores account data in several SQLite databases and their transactional files. They are located in the application resource folder ..\data\data\com.WhatsApp\databases. The following are the key databases that contain forensically relevant information:
- msgstore.db is typically of primary interest; it includes records of calls, message texts, and details of other information exchanged in the conversations (locations, media file names, and so on)
- wa.db is another important table that includes the names of contacts, group chats, channel names, and other details
- companion_devices.db contains information about other clients (devices) linked to the account (at the time of the device acquisition)
We will take a closer look at these databases in the second part of this article.
Configuration file
In ..\data\data\com.WhatsApp\shared_prefs, you can find the com.whatsapp_preferences_light.xml file with account settings and timestamps of various application events enclosed in XML tags. For example, here are some tags that may provide insights for your investigation:
- <string name="registration_jid"/> includes the WhatsApp account owner's registration phone number
- <string name="my_current_status"/> encloses the account's "About" information at the time of the acquisition
- <string name="gdrive_account_name"/> specifies the Google Account email address used for cloud backups
- <long name="gdrive_last_successful_backup_timestamp:account@gmail.com" value="0000000000000"/> shows the UTC timestamp of the last cloud backup in the Unix format.
Backup encryption key
WhatsApp encrypts and decrypts database backups with a key that is generated when the user authenticates in the application using their phone number. You can find this key in ..\data\data\com.WhatsApp\files.
Note that this key only works to decrypt files with the .crypt14 extension. When end-to-end backup encryption is on (files have the .crypt15 extension), the second key or password required to decrypt the backup is only known to the user and it is not stored in the application folders
Media files
WhatsApp saves exchanged media files into the backup folders it creates on the device. You can find them in ..\Android\media\com.whatsapp\WhatsApp\Media. Other media files, such as contact avatars, are part of the application resource folders.
How to acquire Android WhatsApp data
The way Android WhatsApp stores data and creates backups allows for several approaches to data acquisition. In this section, we will explore these approaches and look into the files they let you extract.
Due to security measures, not all acquisition methods can provide you with access to messaging data. Obtaining the complete WhatsApp data set requires a specialized tool that can acquire unencrypted WhatsApp data. For this purpose, we will use Belkasoft X that includes advanced Android device acquisition and cloud acquisition methods.
Backup copy
Copying the WhatsApp backup folder from the device is a good starting point. Here is why:
- You can copy these files without specialized tools
- Though databases are encrypted, you can still view the exchanged media files (even with end-to-end backup encryption in place)
- For encrypted databases, you may be able to obtain the decryption key later using other acquisition methods
How to acquire
Connect the device to your workstation and unlock it. Navigate to ..\Android\media and copy the com.whatsapp folder to your machine. WhatsApp backups can reside either within the device internal memory or on the SD card, so you may need to check both of these storages to locate the files.
What you get
The Android WhatsApp backup comprises two folders with database backups and a structure of media file folders. The Databases folder includes msgstore.db.crypt14, the latest backup of the main WhatsApp database. It may also contain a few versions of this backup created earlier, named similar to msgstore-yyyy-mm-dd.db.crypt14. These earlier files may be of use for recovering messages that were deleted after these backups were made (if you manage to get hold of the decryption key).
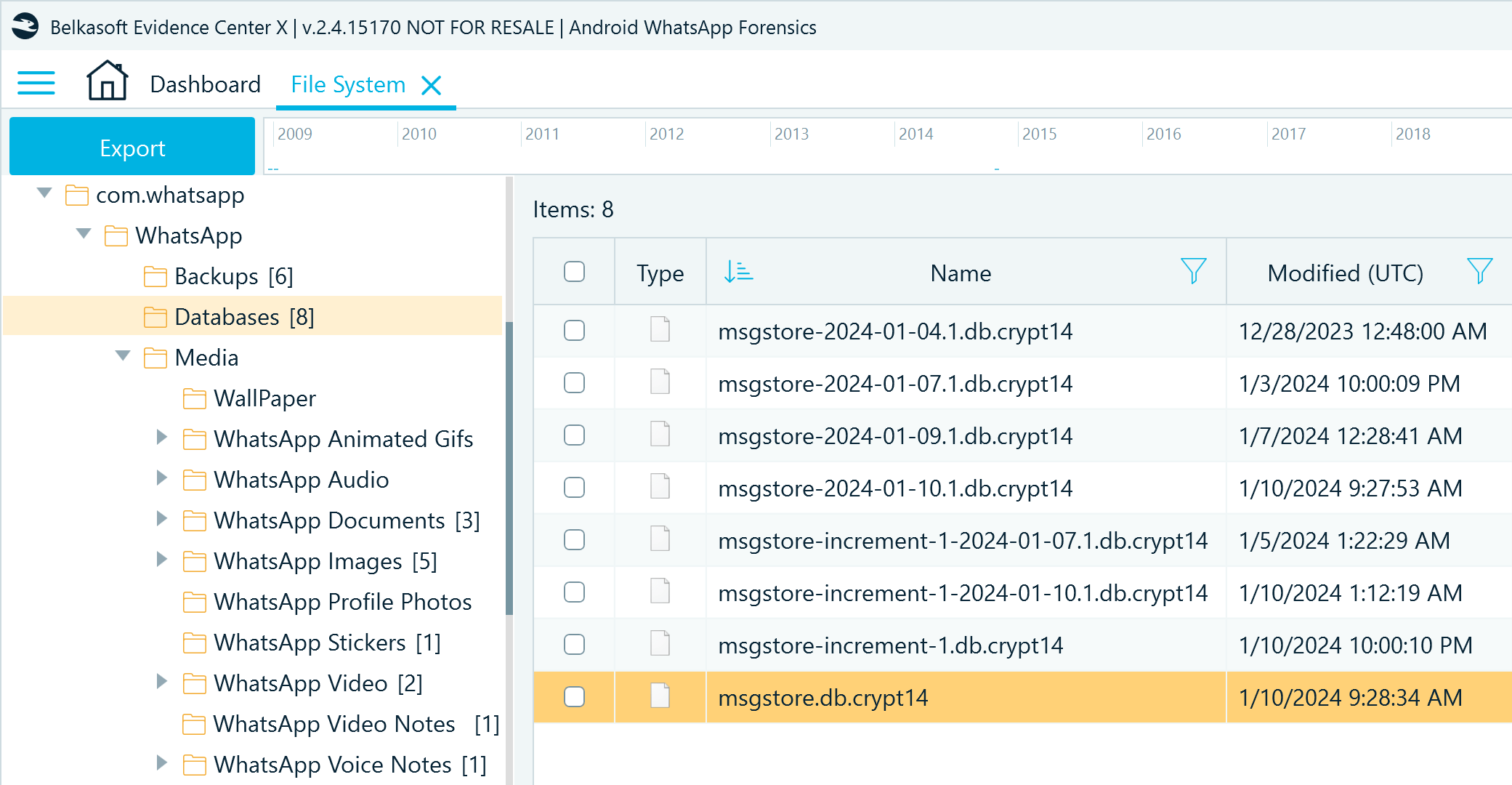
Figure 2: WhatsApp backup files copied from an Android device (Databases folder)
The Backups folder includes wa.db.crypt14 that, when decrypted, can help you identify the users with whom the account owner communicated.
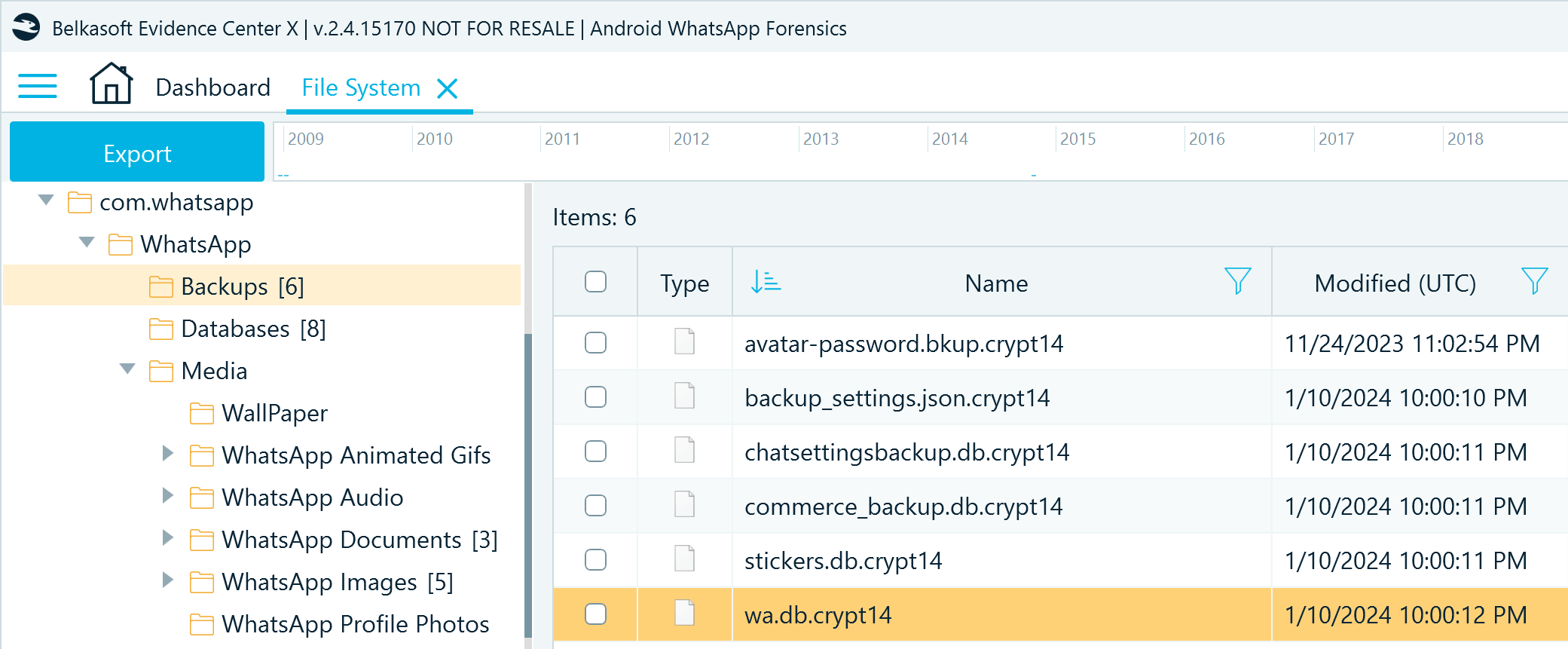
Figure 3: WhatsApp backup files copied from an Android device (Backups folder)
All database backups are encrypted with the same key tied to the WhatsApp account phone number. You can acquire this key from the device using the APK downgrade and Android file system copy methods that we will discuss later.
Note that if a WhatsApp account has end-to-end backup encryption activated, the application uses a more advanced cryptography format, CRYPT15. It applies this format to backup files on the device as well.
Cloud backup copy
If WhatsApp is configured to upload backups to its user's Google Account, you can find its data in the associated Google Drive storage.
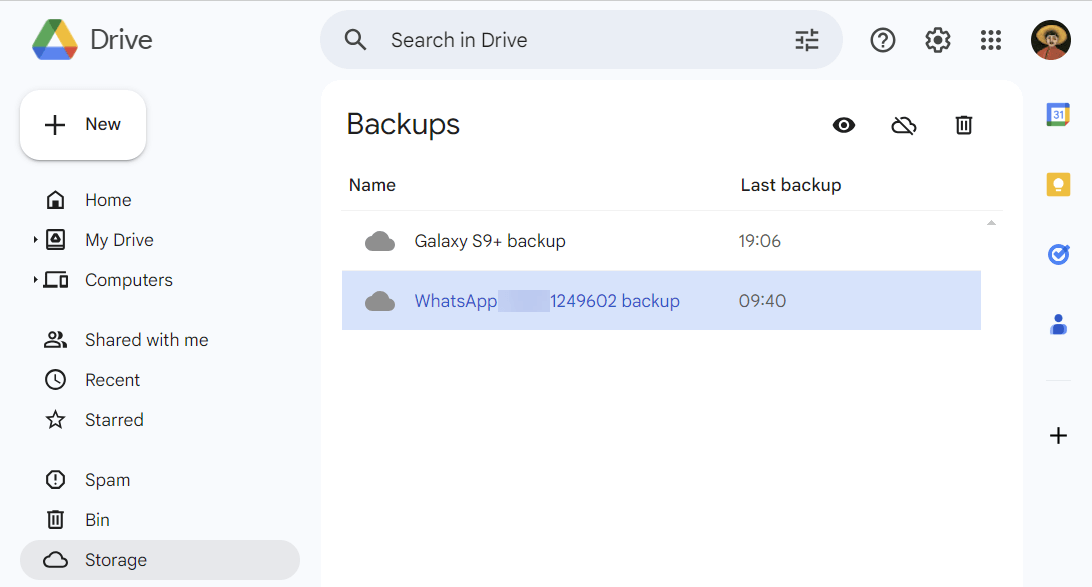
Figure 4: Android WhatsApp backup in Google Drive
Google Drive does not provide a way to download the files directly, so you will need a specialized tool to obtain them.
How to acquire
To begin the acquisition, launch Belkasoft X and create a case. Add a new data source either from the Create case window or the Actions menu on the case dashboard:
Figure 5: Adding a data source in Belkasoft X
In the Add a data source window, select Acquire → Cloud → WhatsApp:
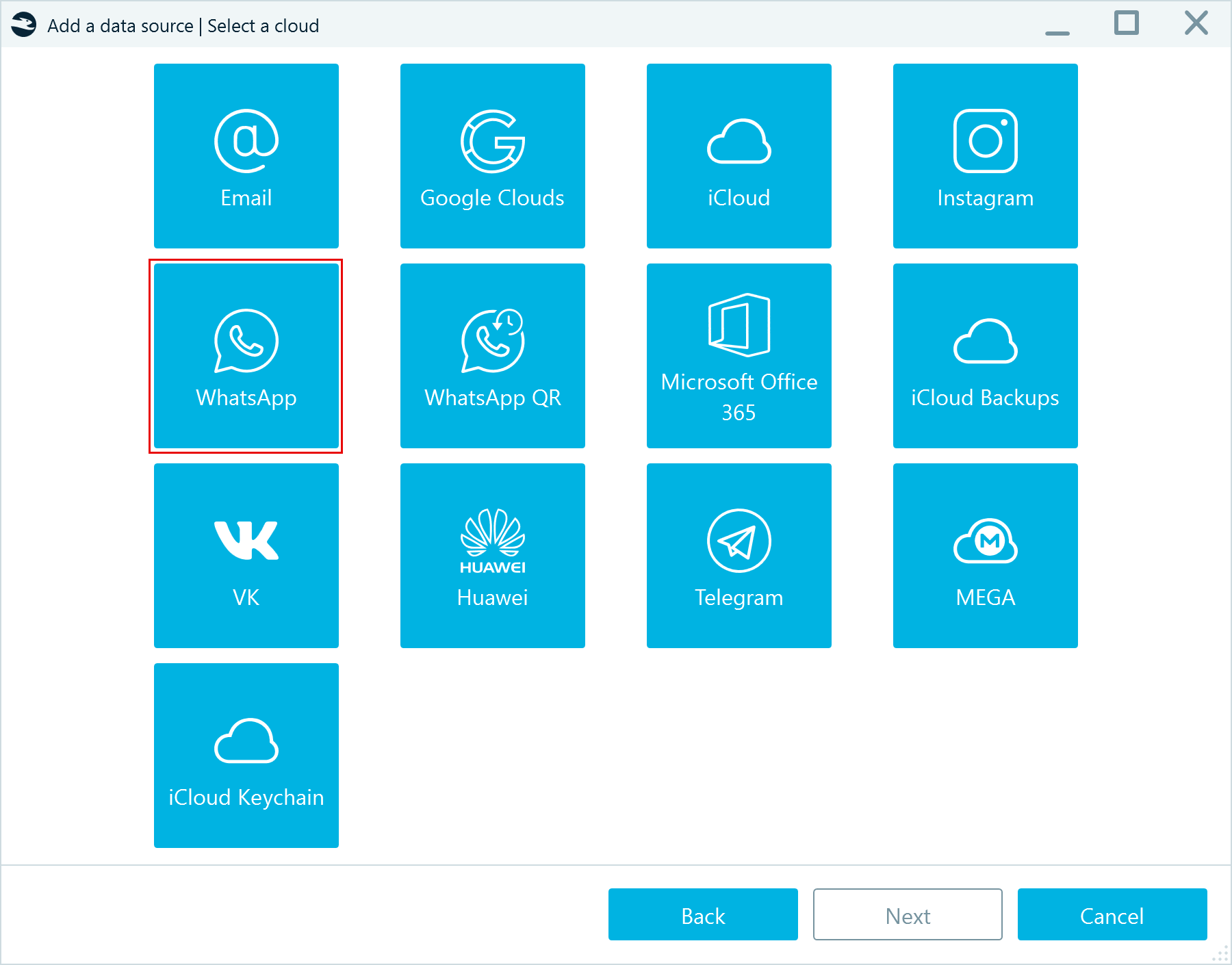
Figure 6: Selecting the WhatsApp cloud acquisition method
Provide the Android WhatsApp user's Google account login and password, click Next, and follow the on-screen instructions to complete the acquisition:
Figure 7: Specifying Google account credentials to acquire WhatsApp
What you get
The Android WhatsApp backup is stored in a folder named after the phone number registered with the account. The files you can obtain from a Google Account are typically the same as those stored on the device but with only one version of the encrypted msgstore.db.crypt14.
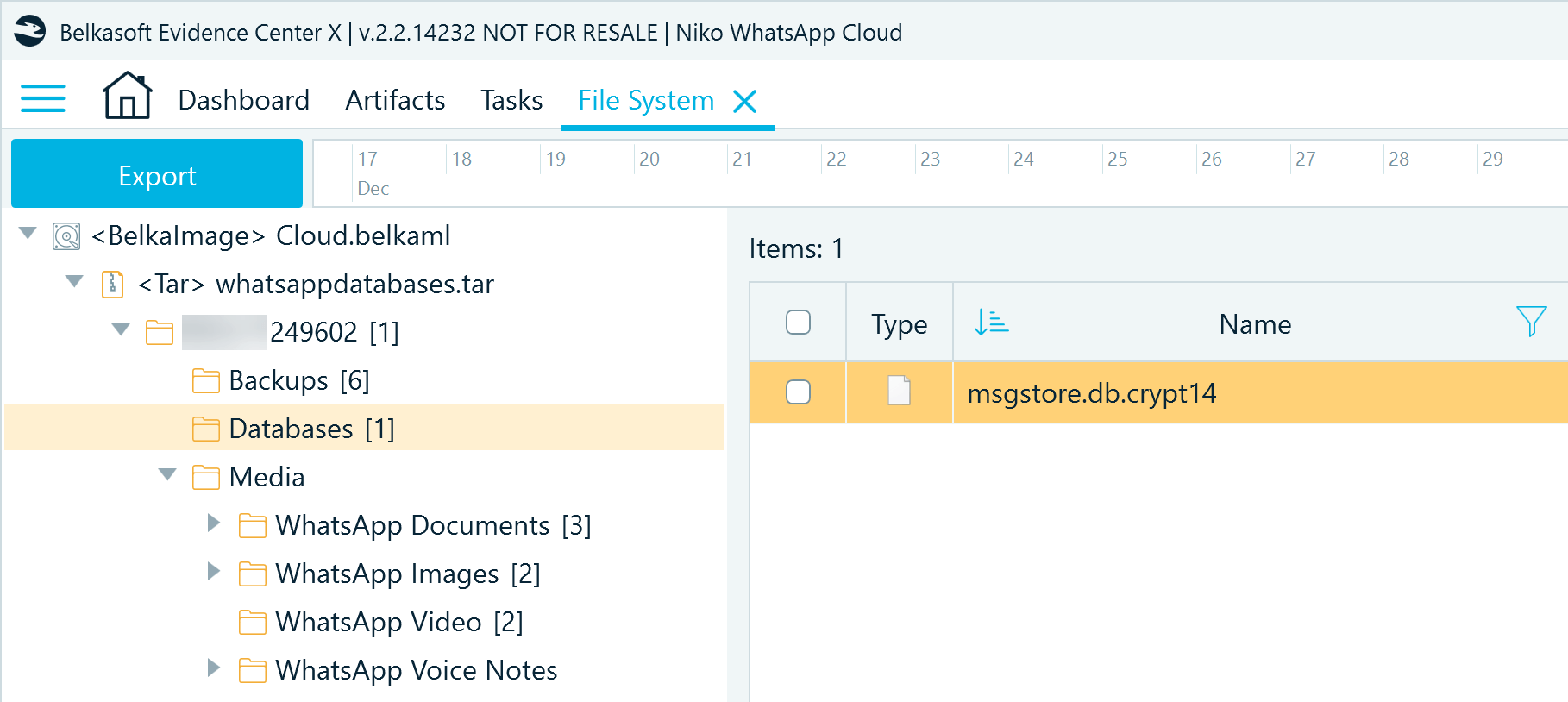
Figure 8: Android WhatsApp backup files acquired from Google Drive
WhatsApp QR
WhatsApp QR is a cloud acquisition method. It emulates linking a device to a WhatsApp account to download application data. This method is useful for obtaining recent conversations and media files. The extent of information you can acquire is limited due to the specifics of the mechanism governing data transfer to connected clients.
How to acquire
Before you begin the acquisition, you should verify that the device camera is working. You will need it to scan the authentication QR code. The device must also be online for the linking functionality to work.
To start the acquisition, launch Belkasoft X and create a case. Add a new data source either from the Create case window or the Actions menu on the case dashboard. In the Add a data source window, select Acquire → Cloud → WhatsApp QR and follow the on-screen instructions to complete the acquisition.
Figure 9: Selecting the WhatsApp QR cloud acquisition method
What you get
Belkasoft X writes the acquired conversations into a Cloud.belkaml file (in XML format) and downloads a WhatsApp folder with files exchanged in those conversations.
Automated screen capture
The Android screen capturer method takes automated screenshots of chats and images within the application and saves them to your workstation.
How to acquire
You can find detailed information on using this method in our article "How to Acquire Digital Evidence with Android Screen Capturer in Belkasoft X."
What you get
When analyzing WhatsApp screenshots, Belkasoft X uses text recognition algorithms to reconstruct captured chats and display them under the messenger profile in the Artifacts window.
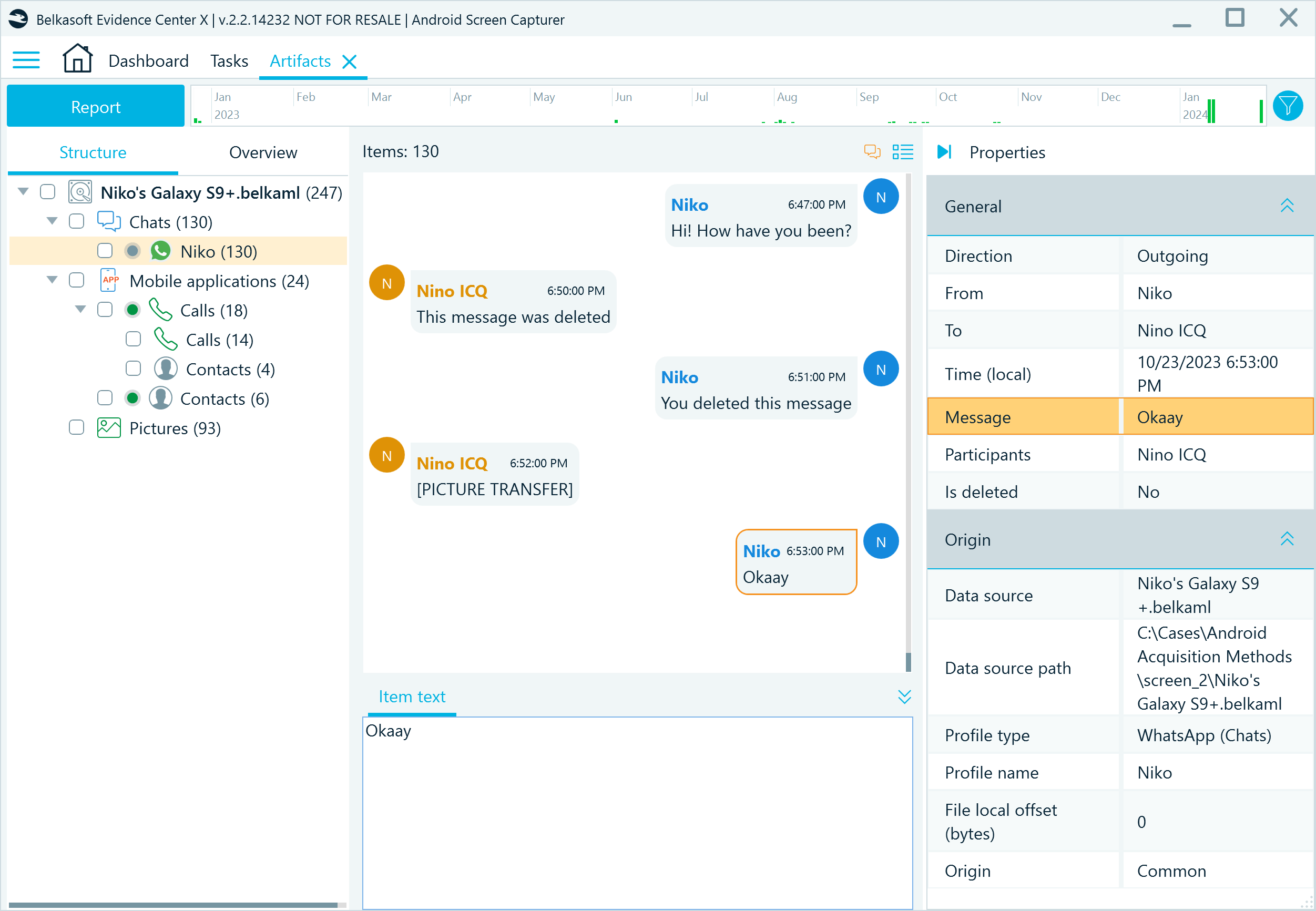
Figure 10: Belkasoft X displaying Android WhatsApp chats reconstructed from screen captures
Android file system copy
If the Android device you are investigating is rooted, you can use the Android file system copy method. It extracts a wide range of artifacts, including the WhatsApp resource folder.
How to acquire
Before you begin, go to the device Settings and, under Developer options, enable the USB debugging and Install via USB options.
Connect the device to your workstation that runs Belkasoft X. To add the device as a data source to your case, select Acquire → Mobile → Android and choose your device model:
Figure 11: Selecting the Android device model to acquire
In the following window, select the Android file system copy option and follow the on-screen instructions to complete the acquisition.
Figure 12: Selecting the Android file system copy acquisition method
What you get
In a file system copy of an Android device, WhatsApp stores its resources under ..\data\data\com.whatsapp\. You get the full dataset, including the unencrypted databases:
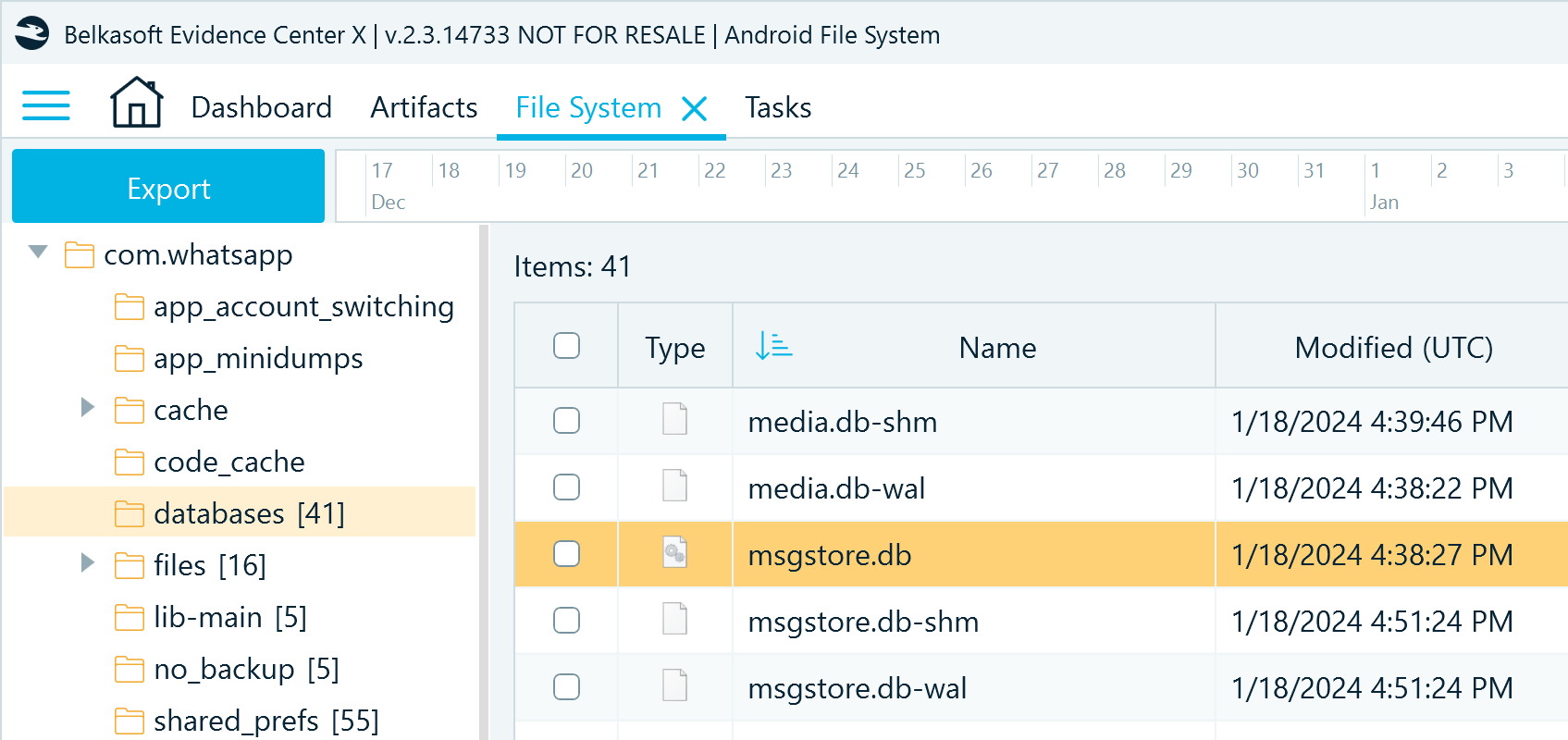
Figure 13: WhatsApp files acquired with the Android file system copy method (application resource folder)
There is more to explore:
- In the files folder, you will find the key file to use for decrypting database backups
- The \files\Avatars folder contains the profile pictures of the user's contacts
- The shared_prefs folder includes the com.whatsapp_preferences_light.xml configuration file
Note that WhatsApp does not store the exchanged media files in the application resource folder. You can locate them in the backup folders.
For the backup files, go to ..\data\media\0\Android\media\com.whatsapp:
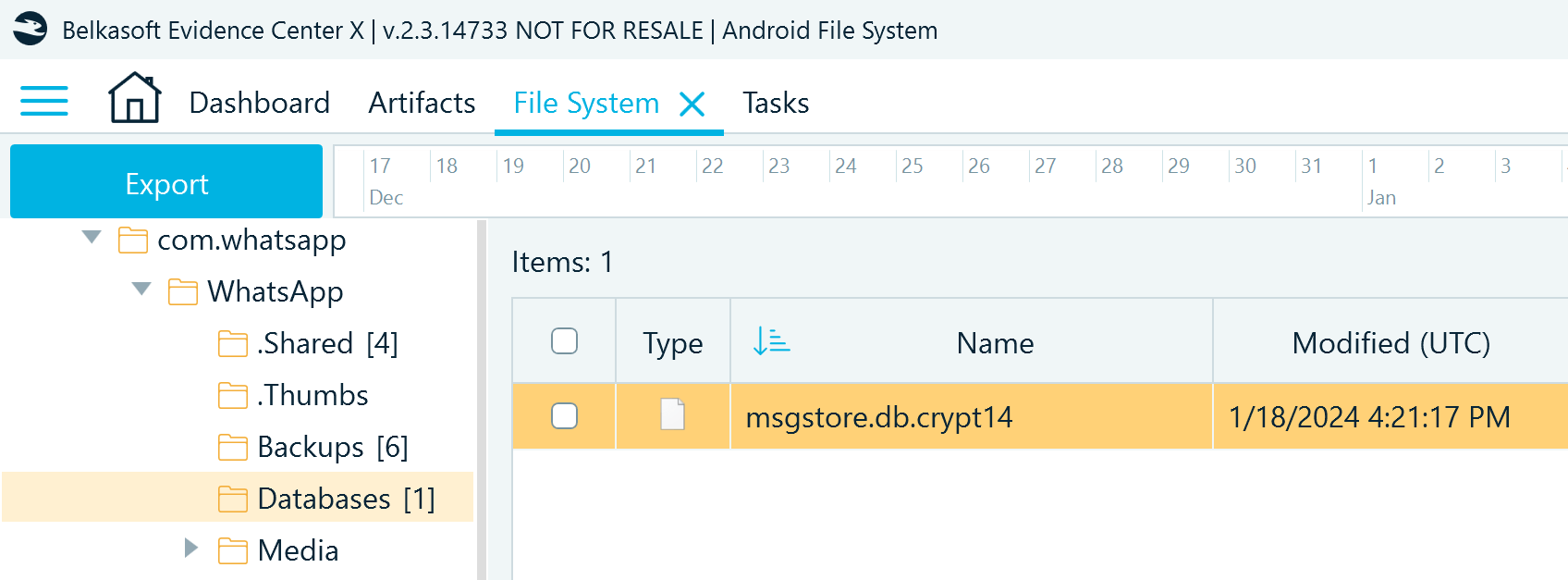
Figure 14: WhatsApp files acquired with the Android file system copy method (backup folder)
APK Downgrade
If you are dealing with a non-rooted device, you can acquire an unencrypted backup copy of WhatsApp data using the APK downgrade method. It relies on the ADB backup mechanism through which, in the past, many applications allowed users to create backup copies of their data. Since security was not such a concern in those times, most applications did not encrypt their ADB backups.
When running APK downgrade, Belkasoft X replaces the current WhatsApp application package on the device with its older version that was set up to back up its data through ADB. Then, it runs the backup command that copies the application files. Importantly, the tool does not launch the downgraded application, ensuring that the databases on the device remain unaffected.
How to acquire
You can find detailed instructions and safety notes for this method in our article "How to Acquire Data from an Android Device Using the APK Downgrade Method."
What you get
The resulting image is an ADB backup (.ab) archive that includes a copy of WhatsApp files from the application resource folder under ..\apps\com.whatsapp. The ADB backup folder structure differs from the one stored on the device but contains essentially the same files:
- The db folder includes the application databases
- In the f folder, you can find the key file and the Avatars folder
- The sp folder contains the com.whatsapp_preferences_light.xml configuration file
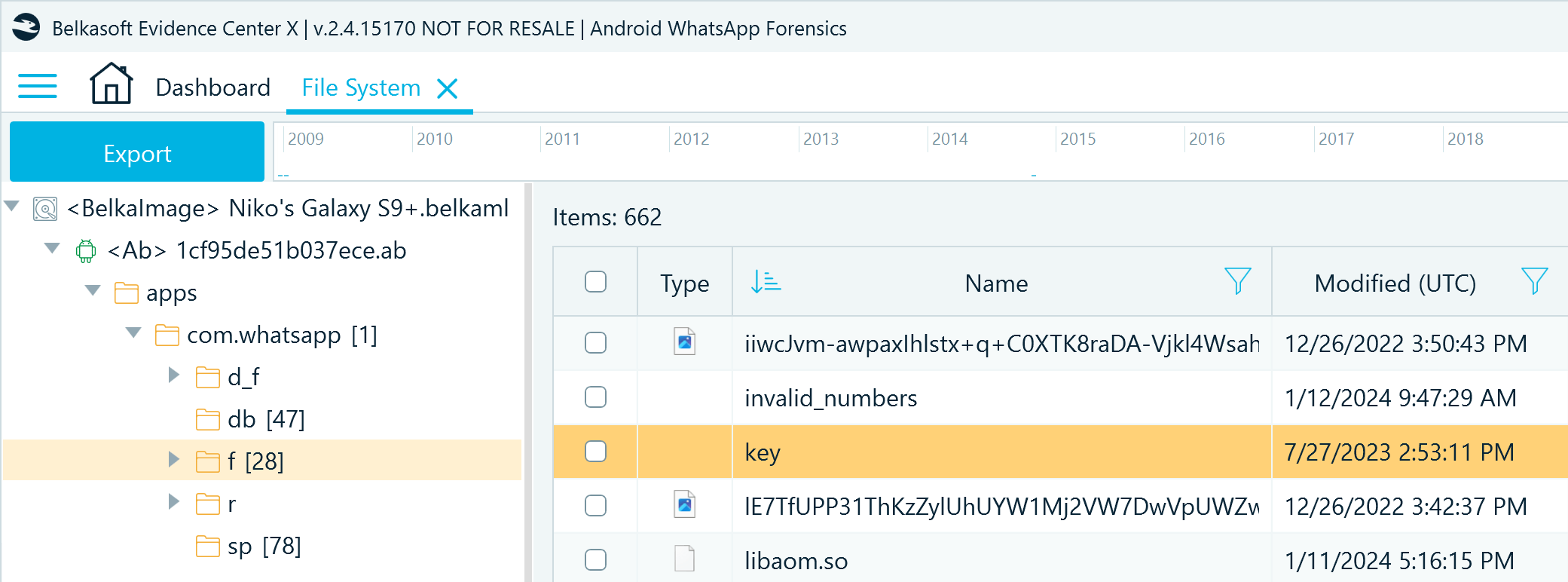
Figure 15: WhatsApp files acquired with the APK downgrade method
Best practices for Android WhatsApp acquisition
Here are a few ideas on how to build your WhatsApp acquisition workflow based on the SANS Institute guidelines:
- Begin with copying backup folders directly from the device, which is the safest way to obtain data
- Next, if the device is rooted, go for the Android file system copy method
- If you are dealing with a non-rooted Android device:
- After copying WhatsApp backup files, use all possible cloud methods
- Then, run the Android screen capturer
- Finish the acquisition with the APK downgrade method as the riskiest one
This way, you will have a few copies of the WhatsApp databases and will be able to corroborate their contents with screenshots and data acquired from the cloud.
Conclusion
To acquire Android WhatsApp, you can use both cloud and device acquisition methods. Each method has its opportunities and limitations. It is best to use them in combination to acquire the most comprehensive data set.
Belkasoft X is equipped with a comprehensive set of acquisition methods that empower you to acquire Android WhatsApp data from a digital device or a cloud. It can further decrypt the acquired data (given that the key is accessible) and prepare it for the following steps of your forensic investigation.
We will take a deep dive into WhatsApp data analysis in the second part of this article. Stay tuned!
