Case Study: From Hidden Databases to Key Evidence with Belkasoft X's SQLite Viewer
JB Brooks is the Lab Director for the Cyber Crimes Unit at a law enforcement agency, overseeing digital forensic investigations. He specializes in cases involving violent crime, narcotics, and ICAC (Internet Crimes Against Children) investigations, playing a crucial role in uncovering digital evidence to support criminal cases. He holds two graduate degrees, the first in information systems and the second in cybersecurity. He has worked both in the public and private sectors in digital forensics and cybersecurity and has presented to federal, state, and local law enforcement agencies and regulatory bodies, as well as INTERPOL.

In this case involving a pyramid scheme, key evidence was found in a hidden SMS database on the victim's iPhone. The investigator used Belkasoft X's SQLite viewer to uncover a critical text message exchange between the suspect and the victim, which was missed by other digital forensic tools. This discovery ultimately led to a successful conviction.
In this case study:
- Digital forensic process: Tools of the trade
- Challenges in evidence extraction: Where Belkasoft X SQLite viewer made the difference
- Case closed: Evidence that secured the verdict
- Belkasoft X features that make a real impact

“Other digital forensics tools missed the key message thread hidden in a SQLite database with an alternate name. Belkasoft X's SQLite viewer helped me find those missing messages, which became crucial evidence leading to a conviction.”
Digital forensic process: Tools of the trade
In our lab, we use a combination of commercial and open-source digital forensics tools for evidence extraction and analysis. For mobile device extraction, we rely on Magnet Graykey, Cellebrite Premium, UFED, Magnet Acquire, and Belkasoft X. For mobile analysis, we use Cellebrite Physical Analyzer, Magnet Axiom, Belkasoft X, ALEAPP, and ILEAPP.
This case I was working on, was a white-collar crime involving a pyramid scheme. The suspect had been convincing people to invest in his business, promising high returns but never delivering. One of the key pieces of evidence was a series of text messages exchanged between the suspect and one of his victims, which the victim preserved over three years through regular iTunes backups and transfers to newer phones.
Since the victim constantly needed his phone, we had to conduct a field-based logical extraction using Magnet Acquire. But when I started parsing the data, I couldn't locate the crucial text thread we were looking for. It was visible on the phone but absent in the artifacts extracted from the device image. I tried different commercial digital forensics software, including Cellebrite, but none of them found the messages. Searches by the phone number, contact name, and even text content turned up nothing.
Digging deeper into the file system, I found two copies of the SMS database: one containing the current messages and another with the older, backed-up messages from iTunes. The tools only pulled data from the current database and ignored the backups. Although Magnet eventually retrieved parts of the conversation, it was impossible to recover the entire thread.
“That's when I turned to Belkasoft X's SQLite viewer. It allowed me to manually explore the databases and locate the complete conversation from the backup, which ended up being critical evidence in the case.”
Challenges in evidence extraction: Where Belkasoft X SQLite viewer made the difference
The device involved in the investigation was an iPhone 6s. Due to time constraints and the need to conduct the extraction in the field, we performed a logical extraction, as a full file system extraction wasn't feasible. The database I was focused on was sms.db, but during the extraction, I found an alternative database labeled sms(1).db. I believe the extraction process resulted in two databases—one native to the phone and another from iTunes backup data.
I knew the path to the sms.db file, but when the digital forensics tools we were using failed to parse the messages correctly, I decided to inspect the database directly. That's when I noticed the two separate databases. It seemed that the tools were only parsing the native database, completely overlooking the one from iTunes backup.
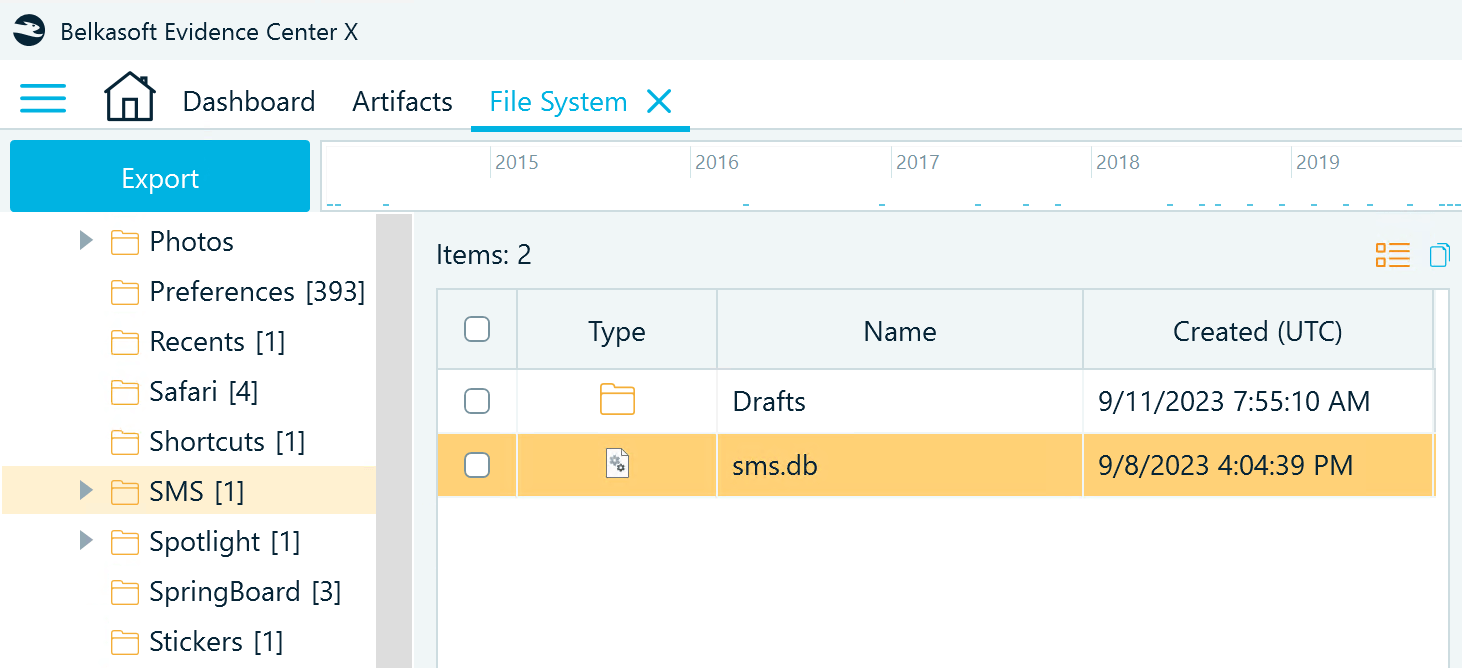
In a logical copy (iTunes backup), the iOS SMS database is stored under ..\HomeDomain\Library\SMS
When I used Belkasoft X's SQLite viewer, I loaded the database independently of the rest of the case data and manually located the specific phone number and conversation I was looking for. This process allowed me to discover the critical messages that had been missing from the previous analyses.
The conversation I found in the second database was pivotal to the case. It was a detailed exchange between the victim and the suspect, where they discussed the fraudulent activity at length. This information became a crucial piece of evidence in proving the nature of the crime.
In fact, when I couldn't locate this conversation using other tools, I started with the global search features built into most forensic tools. Cellebrite, for instance, didn't show any matches in the global search. Magnet recognized the contact but struggled to load the data from the alternative database. More importantly, Magnet's portable cases don't offer a file system view, which makes it challenging to explain during testimony how and where the data was obtained.
I also find the SQLite parsers in other digital forensics software lacking, especially when I need to compare multiple fields and their relationships. That's why I prefer using Belkasoft X's SQLite viewer—it offers more flexibility and clarity when navigating and understanding the data.
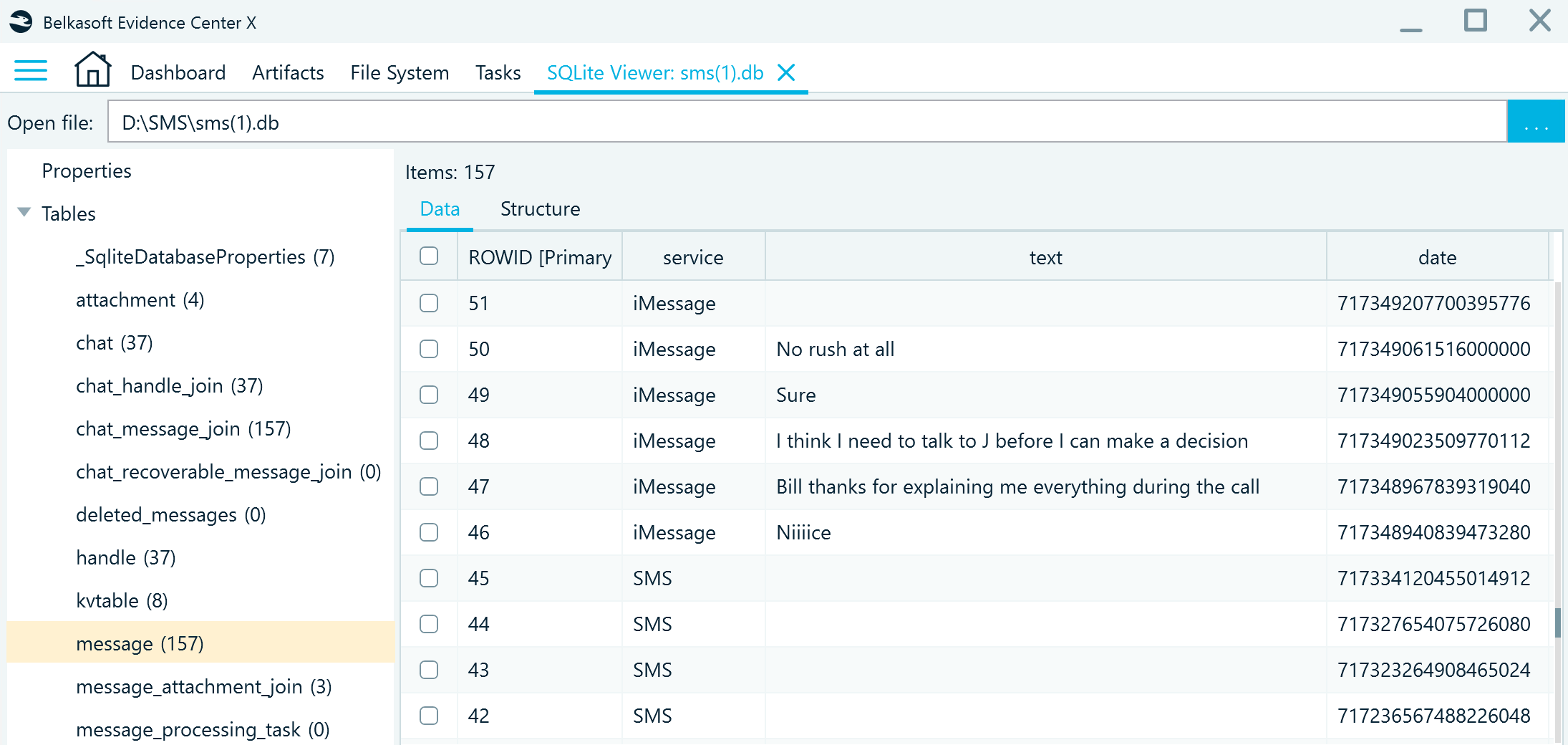
Belkasoft X's SQLite viewer includes an easy-to-use tool set for SQLite database analysis, allowing you to customize the columns to display, convert specific types of data for easier examination, and review binary records in a built-in Hex viewer
Case closed: Evidence that secured the verdict
We didn't run into any issues presenting this evidence in court. Our documentation was solid, and we clearly showed that the device had saved the messages in two similarly named databases in different formats. What also helped was that we had captured screen grabs of the conversation as it originally appeared on the suspect's device, further reinforcing the legitimacy of the evidence.
In the end, the case resulted in a successful conviction, and the perpetrator was found guilty.

Belkasoft X features that make a real impact
“In our high-volume lab, processing speed is crucial, and Belkasoft X has helped us handle cases more efficiently, particularly when compared to other commercial solutions that can be slower to process large datasets.”
One of the Belkasoft X features that has streamlined our investigations significantly is automation. I've optimized our workflow by configuring a NAS (network-attached storage) device where we prioritize evidence processing using Belkasoft X and Python scripts. This automation allows me to have several cases, instead of just one or two, processed overnight, and we have them ready for examination by the next day. This setup has been a game-changer for our lab, which handles about 700 devices a year.
Another feature we routinely use is the screen capturer that allows auto-scrolling. It has been invaluable for capturing long text message conversations and scrolling through image galleries, especially for investigations involving Amazon Fire tablets. These devices are notorious for hiding images that don't appear in typical extractions, but with Belkasoft X's client and auto-scroll feature, we can capture incriminating images directly from the gallery.
Belkasoft X's Android screen capturer automates the acquisition of screenshots from popular messengers (Signal, Telegram, WhatsApp) and can automatically scroll and capture the screens from other apps and windows
The auto-scroll feature also serves as a useful triage step, allowing us to document what we see on the device before diving deeper into more complex analysis. This has been particularly effective in ICAC (Internet Crimes Against Children) investigations, where it helps us isolate entire conversations without taking victims' phones for extended periods, which has resulted in more cooperation from victims.
I've also found Belkasoft X's Map View and Connection Graph features highly useful for navigating and making sense of data. Recently, I've also experimented with the BelkaGPT tool for generalized searches, and I'm finding it helpful for pinpointing some details in investigations.
The Belkasoft team appreciates detailed feedback from DFIR and eDiscovery experts. Please share your testimonials and case studies at support@belkasoft.com.
