Lessons Learned from the Silk Road Investigation
On January 21, 2025, the US president Donald Trump pardoned Ross Ulbricht, the creator of Silk Road, a darknet marketplace that facilitated anonymous transactions for illegal goods and services. Ulbricht had been serving a double life sentence without parole since his conviction in 2015. The investigation and arrest of Ulbricht remain a landmark case in digital forensics, illustrating the interplay of anonymization tools like Tor, cryptocurrency, and investigative persistence.
Ross Ulbricht and the Silk Road
Ross Ulbricht launched Silk Road in 2011 as a hidden service on the Tor network. He operated under the pseudonym "Dread Pirate Roberts" (DPR). The platform's success relied on two key technologies:
- Tor: Its layered encryption hid the marketplace's server location and users' identities.
- Bitcoin: This pseudonymous cryptocurrency enabled transactions—or so it seemed.
These innovations attracted users worldwide and made Silk Road one of the largest dark web marketplaces, presenting significant challenges for investigators.
The downfall of Dread Pirate Roberts
Despite the anonymity afforded by these technologies, Ulbricht made several mistakes that exposed his identity. He used the alias "altoid" in early forum posts promoting Silk Road and later linked the alias to his personal email. In addition, he posted questions on Stack Overflow (like many of us do) under his real name before changing it.
In October 2013, undercover agents observed Ulbricht accessing Silk Road's admin panel in a public library. He was arrested while his laptop remained open, allowing investigators to seize unencrypted evidence. Key findings included admin credentials for Silk Road, a journal detailing its creation and operation, and Bitcoin transaction records along with private keys. The Silk Road earned hundreds of millions of dollars in sales and more than $13 million in Bitcoin commissions. On November 3, 2020, law enforcement confiscated more than $1 billion in digital currency discovered during the inquiry.
Digital forensics in the Silk Road case
This investigation highlighted the critical role of advanced digital forensics tools in combating cybercrime. Investigators analyzed Tor browser history, configuration files, and network connections to uncover user activity. Investigators could access transaction records by reviewing wallet data, including hashes, blocks, and sender-receiver details. Blockchain analysis offered insights into transaction patterns that suggested potential links between wallets and Ulbricht's activities.
Modern digital forensics software, such as Belkasoft X, is designed to handle the complexities of such investigations. With Belkasoft X, investigators can:
- Extract and analyze Tor-related artifacts, such as browsing history and hidden service access.
- Trace cryptocurrency transactions by examining wallet files, reviewing transaction details, and interpreting blockchain data to uncover patterns and connections.
- Correlate evidence from memory dumps, file systems, and network traces to build a comprehensive picture of criminal activity.
By combining data from these sources, investigators can create a comprehensive timeline of events, identify key actors, prove their involvement, and build a strong case against cybercriminals.
Lessons learned
While exploring the journey of the Silk Road case, there are three valuable lessons that investigators beautifully demonstrated in practice along the way:
- Timing is everything. It was crucial to catch Ulbricht while he was logged into Silk Road's admin panel. This allowed investigators to obtain evidence that was not encrypted.
- Anonymity tools are not perfect: While technologies like Tor and Bitcoin are great for privacy, they are not foolproof. People make mistakes, and those mistakes can reveal their identities.
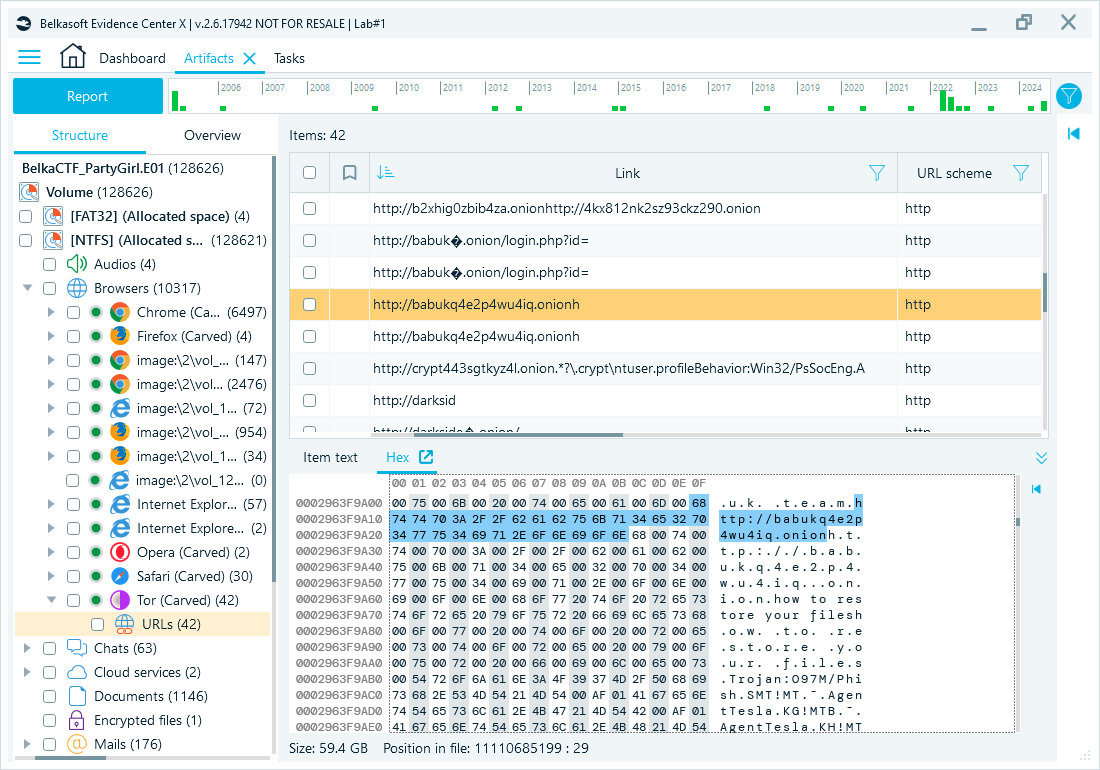
Carved data of website visits from Tor Browser
- Blockchain leaves a trail: Although blockchain technology is meant to be anonymous, transaction records found on digital devices can help investigators connect people to illegal activities.
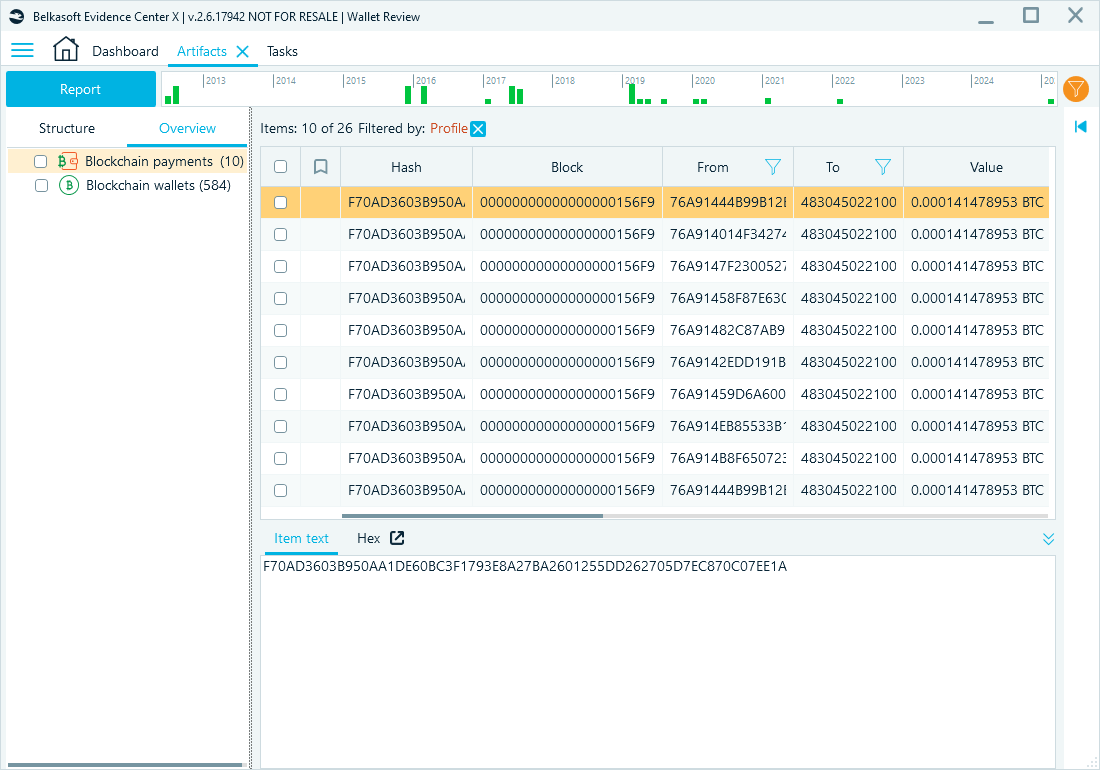
Blockchain payment record data recovered from target PC
Dark web challenges and opportunities
The fall of the Silk Road did not end the dark web marketplaces. Similar platforms have since emerged, with many adopting advanced anonymization technologies. Investigators must up their game with cutting-edge tools and skills to counter these threats.
To address this, Belkasoft offers a variety of opportunities to help forensics professionals enhance their skills:
- Digital forensics training: Learn how to investigate organized crime cases involving drug trafficking, cryptocurrencies, and encrypted data. Explore more at Belkasoft Training.
- CTF challenges: Participate in Capture The Flag (CTF) events to practice investigating cases involving Tor and crypto artifacts.
- Dedicated Windows forensics course: Dive into practical scenarios using Belkasoft X, including extracting Tor data and other critical evidence. Access this course at Windows Forensics Training.
Conclusion
As cybercrime evolves, the Silk Road investigation reminds us that no tool or technology can completely hide evidence from determined forensic analysis. With the right skills and digital forensics software, investigators can find the bad guys even when they try to hide.
Tools like Belkasoft X assist investigators in solving cases involving anonymization technologies, cryptocurrencies, and encrypted data. They help forensic professionals uncover concealed evidence and resolve complex cases with the help of forensic data recovery techniques and the extraction of critical artifacts.
