How to Investigate Telegram Crime without Arresting the Company’s CEO
On Sunday, August 26, 2024, Telegram CEO Pavel Durov was taken into custody by French authorities in Paris. Reports indicate that Durov's arrest is connected to an ongoing investigation into his alleged involvement in several serious crimes and his refusal to comply with data requests from French investigators.
It is not the first time the Telegram founder's commitment to communication privacy has been challenged by law enforcement. Back in 2018, Russian authorities attempted to block Telegram after Durov refused to grant the FSB access to requested data.
But how can the company's CEO assist agencies if Telegram users' data is end-to-end encrypted and private?
In this article, we will explain why Telegram is not as secure as it is marketed and look into the mechanisms that allow it to decline user data requests. We will also explore how it can play a role in investigations when analyzed with digital forensics tools, such as Belkasoft X.
Telegram security
Many people assume that all Telegram communications are protected by end-to-end encryption. In reality, only a portion of Telegram's features offer this security measure. "Secret chats" indeed exchange information in a form that can only be decrypted on the two devices participating in the chat and are stored exclusively on those devices. However, this feature is only available in mobile Telegram apps, and there is no equivalent option for "secret group chats."
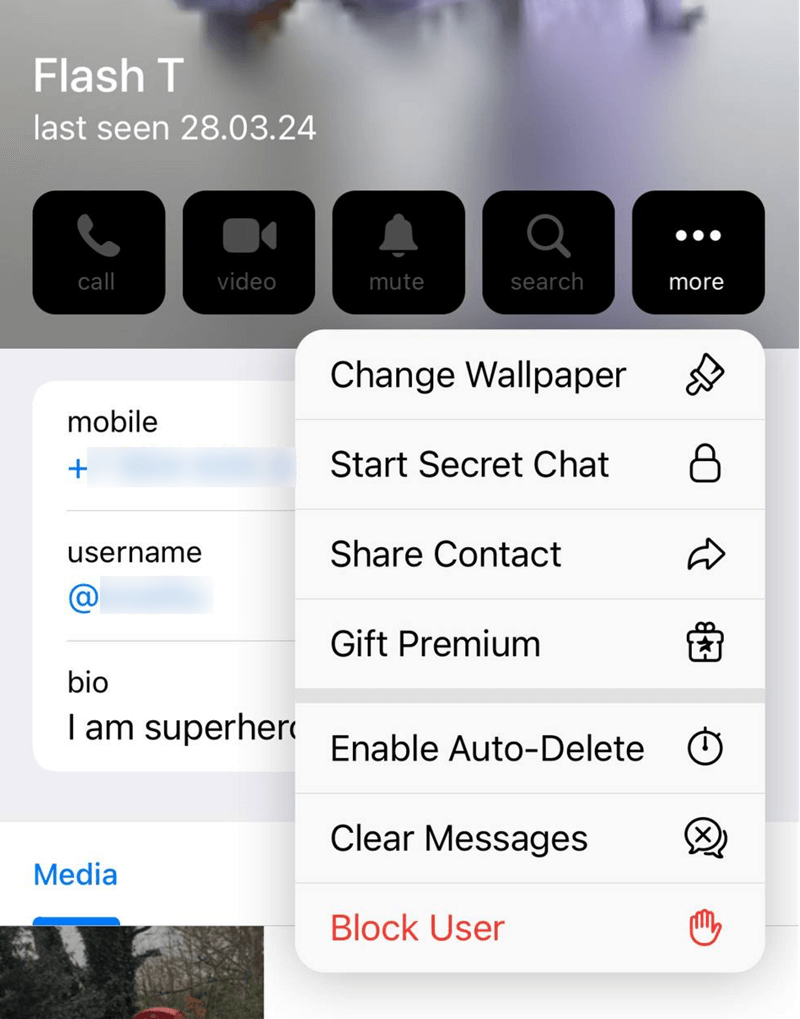
Finding the “secret chat” option in the Telegram app is not that easy
Most Telegram users typically communicate in regular "cloud chats," which are saved on the company's servers. Such chats employ a different kind of encryption known as client-server / server-client encryption. This architecture protects Telegram data from man-in-the-middle attacks, preventing third parties, including special agencies, from intercepting and reading the messages exchanged. However, can they access the data stored on Telegram's servers?
According to the messenger's FAQ page, all user information is stored in an encrypted format as well. Moreover, it is spread across multiple data centers in different jurisdictions, and the decryption keys are split and never stored together with the data. This setup makes it almost impossible for user data requests to be approved. So, what options are available when investigating Telegram-involving crimes?
Cloud Telegram forensics
In fact, investigators can download and examine Telegram data stored in the cloud for criminal investigations or legal proceedings. This process requires the account owner's SIM card and, if two-factor authentication (2FA) is enabled, the corresponding password. While cloud data does not include “secret chats” (as these are only available on devices), it does provide the entire history of the user's “cloud chats” and exchanged files. For more information on what can and cannot be retrieved from Telegram cloud data, read our previous article, “Telegram Forensics: Getting Started.”
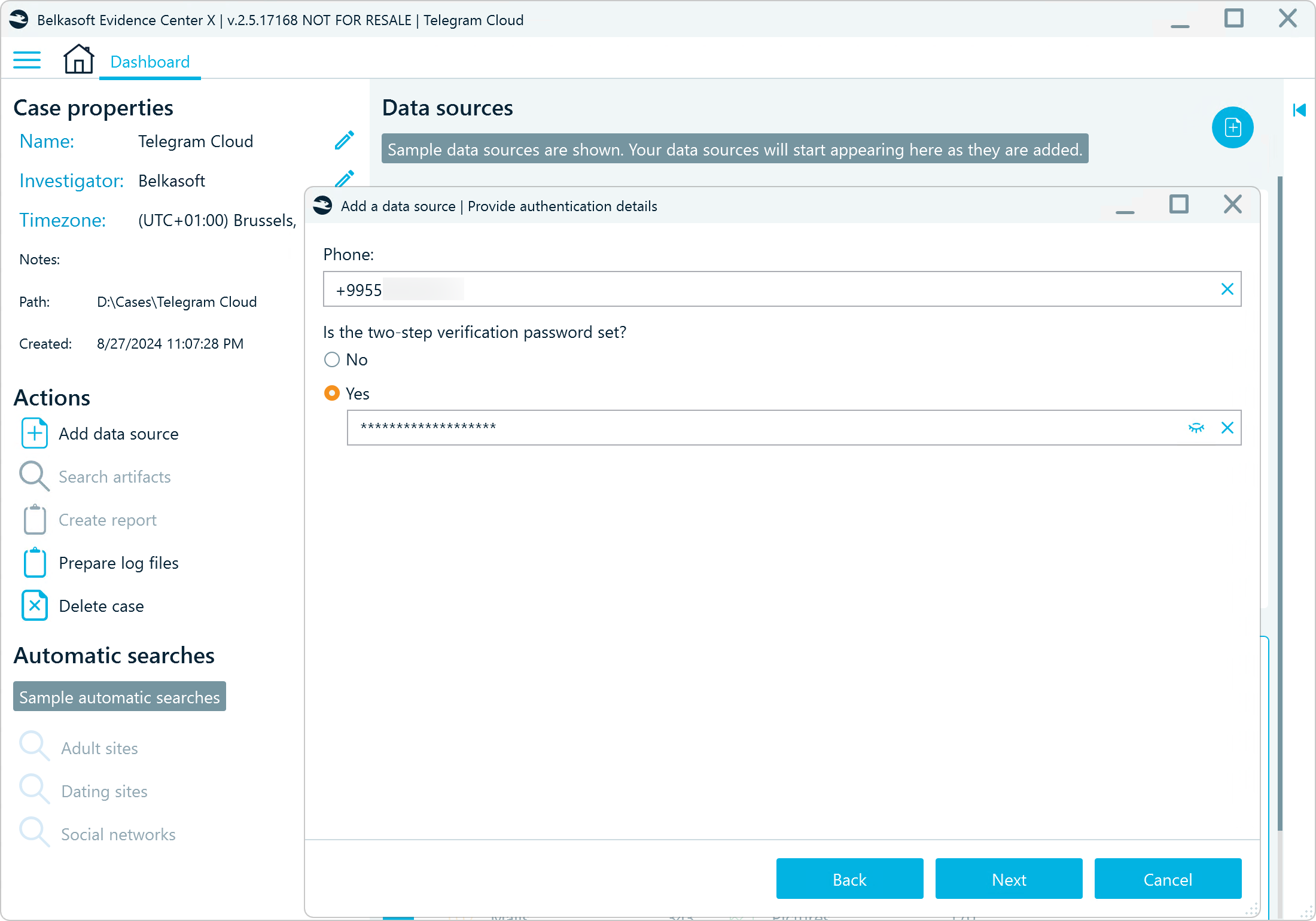
Cloud Telegram acquisition with Belkasoft X
Accessing and downloading Telegram account data from the cloud is not always possible. Users might create accounts using one-time SMS services, virtual or foreign country numbers not traceable to their identity, or even anonymous blockchain accounts. Investigators may also face challenges if the 2FA password is unavailable.
Mobile Telegram forensics
Devices where the user is logged into their Telegram account can provide more valuable information for the investigation. If “secret chats” are available on a device, digital forensics tools can retrieve them along with other data. Device data also typically includes recent channel posts, which may be of interest if those channels are related to illegal activities.
Acquiring Telegram data from a mobile device requires access to the device file system, which is only possible through advanced mobile acquisition methods available in digital forensics tools. However, the data obtained may be incomplete. Since Telegram employs cloud storage, users do not need to keep all exchanged files on their devices. They can configure the app to automatically remove cached files after a specific period or when storage limits are reached.
Can digital forensics software recover deleted Telegram messages from mobile devices? The answer is: it depends. Telegram uses SQLite databases to store messaging data on iOS and Android devices, and this format is known to retain some deleted data in transactional files for a limited time.
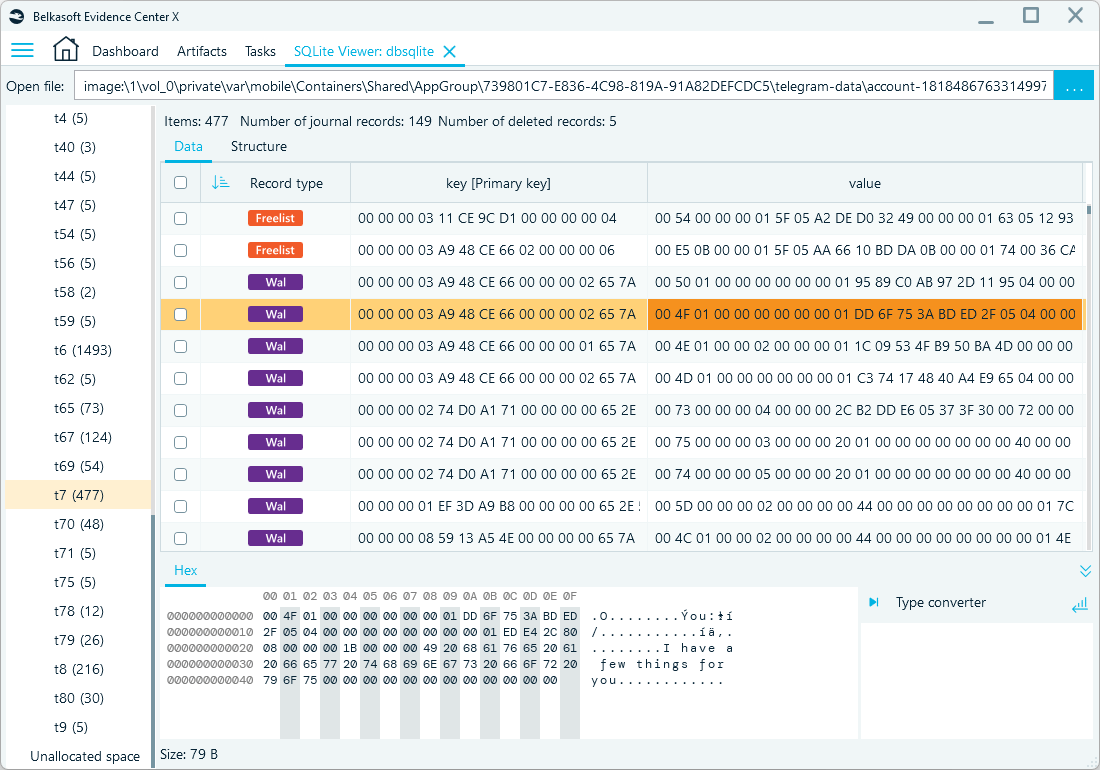
An iOS Telegram database with transactional records in Belkasoft X's SQLite viewer
Some message texts may also persist in the notification databases. In general, the sooner the device data is copied after a message is deleted, the better the chances of recovery. However, certain items, such as deleted “secret chats” and the messages within them, are usually unrecoverable.
Telegram forensics on computers
Telegram is typically used on computers either through web browsers or the Telegram desktop app, available for macOS, Windows, and Linux. While the web version usually leaves only minimal cached traces, desktop apps have more potential for providing valuable evidence.
For instance, on macOS machines, Telegram artifacts can be accessed in the file system. In contrast, forensic analysis on Windows computers is more complex and often requires RAM analysis to retrieve the most comprehensive data.
If investigators already have access to cloud and mobile device data, examining the user's computer is unlikely to provide additional unique details. However, the desktop app can still reveal valuable evidence, such as exchanged media files or user login patterns.
Telegram forensic analysis
Telegram is a large-scale messaging platform that offers various communication features, including calls, one-to-one chats, groups, and channels. In these settings, users can share text messages and media files, video and audio messages, documents, and static or live locations.
The platform also allows users to build private and public bots interacting with internal resources and external databases or programs. For example, the Wallet bot enables users to purchase cryptocurrency and exchange crypto transactions with their contacts.
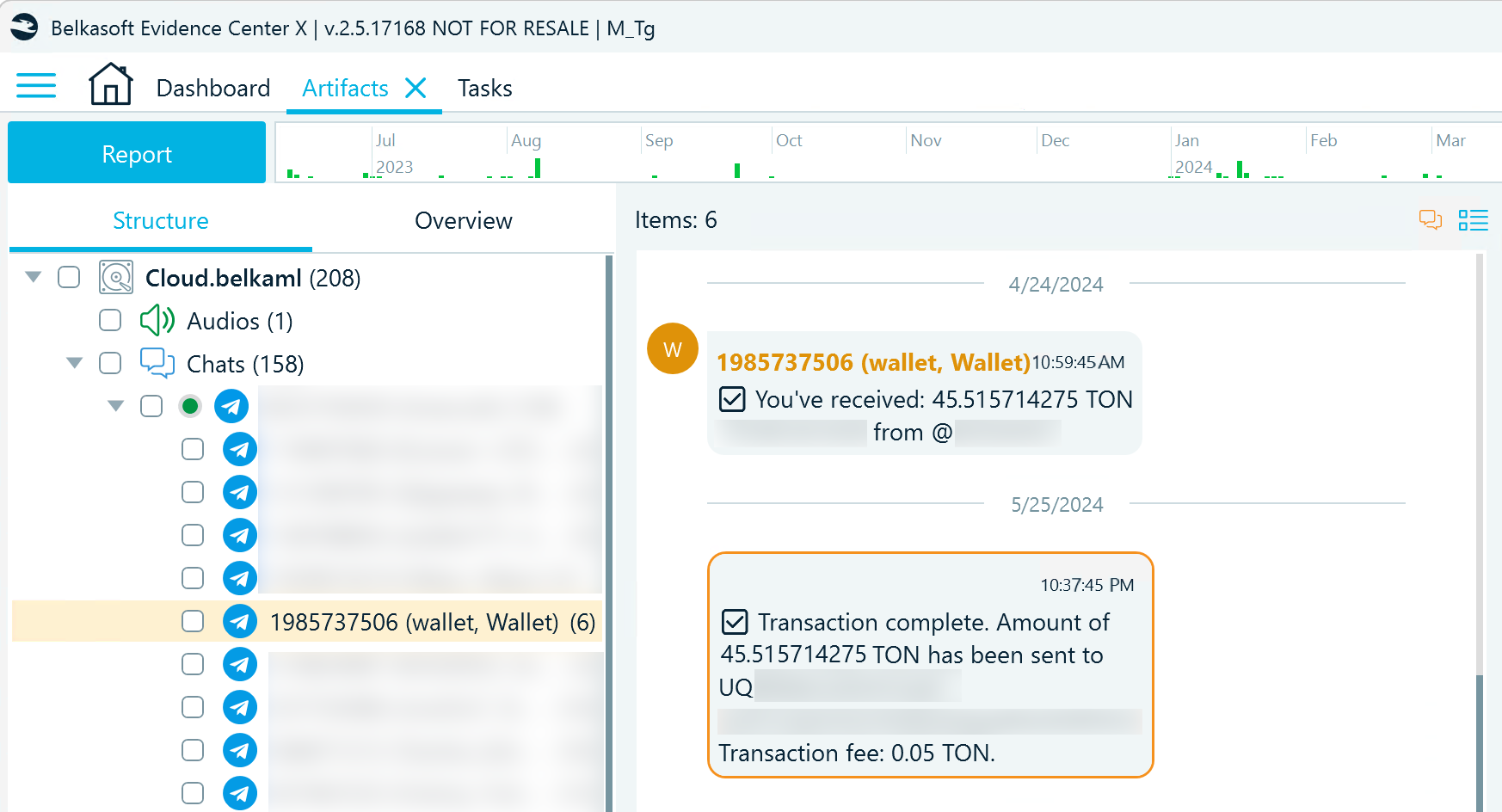
Belkasoft X displaying Telegram user's cryptocurrency transactions made with the Wallet bot
Telegram records reveal valuable information and provide clues about users' contacts, interactions, financial transactions, locations, and patterns of life.
While cloud Telegram data can provide the complete user profile, data extracted from mobile devices allows investigators to uncover what users may try to conceal, such as end-to-end encrypted conversations and private channels.
Conclusion
Telegram's commitment to privacy poses challenges for investigators, especially given the end-to-end encryption of certain communications and the secure distribution of user data across various jurisdictions. However, some of its technical solutions rather help than impede investigations.
Advanced digital forensics tools like Belkasoft X offer effective solutions for downloading Telegram data from the cloud and extracting it from electronic devices. These tools also provide a forensically sound environment to analyze the data and uncover valuable information that can support investigations.

