Challenges in Digital Forensics: The Case of the Trump Rally Shooter's Phone
According to CNN, two days after Donald Trump's assassination attempt at his rally, the FBI was able to gain access to the cell phone of the shooter, Thomas Matthew Crooks. Investigators are searching the phone for clues about Crooks' motive and mindset but still have no leads.
What took so long to get into his phone, and what can the FBI find on it? To answer these questions, it is necessary to understand the specifics of the electronic device investigation process.
Law enforcement and special agencies have forensic departments specializing in different evidence areas. Crime scene researchers collect and analyze fingerprints and objects, medical experts examine bodies, and firearms specialists focus on ballistics. For electronic devices, digital forensics experts take the lead. They are responsible for examining and finding evidence in the information stored on digital devices such as computers, phones, tablets, drones, and the like.
At Belkasoft, we develop digital forensics tools tailored for the tasks involved in such investigations and used by law enforcement in US and overseas. In this article, we will shed some light on the challenges in the forensic analysis process and explain how they apply to the device involved in the investigation of the Trump assassination attempt. We will also try to make a few educated guesses about the evidence the FBI may find on it.
Seizing a device
The initial step of a successful investigation is to properly handle the electronic device. Mobile devices constantly interact with networks, apps, and services, leading to continuous data changes. Once seized, devices must be immediately isolated from networks to prevent remote wiping or further data alteration. The volatile nature of digital data means that any delay in securing the device can result in the loss of critical information.

Gaining access to device data
The next challenge digital forensics specialists face in their pursuit of evidence is unlocking the mobile device. Modern devices are protected by advanced encryption mechanisms that make their data unreadable without the passcode. This obstacle caused the delay in Trump's assassination attempt investigation as the shooter was taken down during the security operation, and it was not possible to obtain his phone passcode or unlock the device through face identification.
According to The Guardian, the FBI had to ship the shooter's phone to a lab in Virginia, where agents managed to gain access to the device. But how were they able to do it?
It is widely known that device manufacturers are not cooperative with requests to unlock their products, even in high-profile investigations. Manually guessing the passcode is not a viable option either, as after several unsuccessful login attempts, most devices get deactivated.
However, forensic technicians can bypass the lock screen or login attempt restriction on some device models. In the latter case, they can run automatic guessing of mobile passcodes, known as brute-force. This technique entails feeding the device various number combinations until the correct one is accepted.
Brute-force is very effective and is often the only way to access device data, but it is not always fast. Its performance depends on the device model and state; sometimes, finding the correct combination of the numbers may take years. With Thomas Matthew Crooks' phone, it looks like fast brute-force was possible, which is why the specialists could unlock it fairly quickly.
Our flagship product, Belkasoft X, offers a Mobile Passcode Brute-Force module that allows examiners to run both fast and slow brute-force on iOS and Android devices.
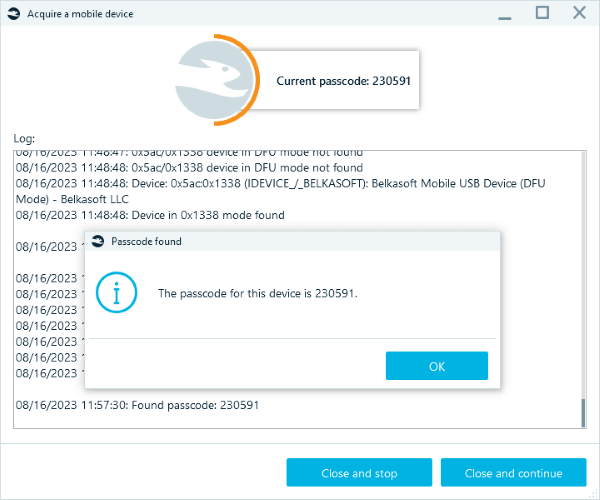
Acquiring device data
When the passcode is known, the challenges do not end. The next step in a digital forensic investigation is to make a copy of the data available on the device. With standard methods, like iTunes backup for iOS and ADB backup for Android, experts can only get a smaller portion of the information. In fact, there is no straightforward way that provides access to the device internal files.
For this step, digital forensics tools like Belkasoft X offer advanced acquisition methods that help bypass security measures and copy the device file system or application resources.
Breaking encryption
Even though most device data is secured, some applications introduce additional protection by encrypting their files. Without the decryption key, these files are unreadable.
When digital forensics tools process the files acquired from devices, they detect encrypted files and decrypt them if their keys are available in the file system. For example, this way Belkasoft X can automatically decrypt iOS Signal, Facebook, and CoverMe, Android WhatsApp backup databases, and more. It also provides the investigators with the ability to decrypt other application databases if they have the associated passwords or keys.
However, if it is not possible to decrypt some files and databases, experts can use screen capturing to acquire data from the application interface.
Extracting digital artifacts
Device users mostly see their data in convenient application interfaces, but the way the applications store it is very different. Some employ databases with a multitude of tables and columns; others use structured formats like XML or JSON. Reconstructing the information from all these storage types requires specialized skills and is a very time-consuming task.
Digital forensics tools help examiners by analyzing device files and automatically extracting forensically important data, known as digital artifacts. These are usually chats, emails, browsing history, geolocation data, pictures, videos, documents, and a multitude of system files. Device file system analysis can take from a few hours to several days, depending on the amount of data on the device.
It is also important to mention that in digital forensic investigations, it is the industry standard to use multiple tools for extracting data. Software vendors use different techniques for extraction, and the sets of artifacts they can discover may vary. For this reason, experts usually have several products in their toolkit, which allows them to cross-check and validate the extraction results.
Analyzing device data
Modern smartphones are like tiny black boxes that record their owners' contacts, calls, plans, conversations, interests, thoughts, movements and much more.
What data would the FBI be interested to discover on the Trump shooter's phone? According to the media coverage, they are looking for the motives of his act. This focus would involve searching through Crooks' notes, calendar events, documents, browsing history, conversations, emails, purchases, financial and cryptocurrency transactions.
All these data types can include thousands of text records that need thorough attention. To accomplish such tasks, investigators typically search for specific words and filter data by various criteria, such as timeframes, application types, or contacts. However, this method is not always effective. Searches can only cover a part of the words that people use to express their thoughts and may miss some important records. Artificial Intelligence-based text analysis can help fill in this gap, and tools like BelkaGPT, which has been recently released by Belkasoft, already show promising results in evidence discovery.
There are other information types found on devices that may be important for the investigation:
- Geolocation records can show routes and frequently visited places
- Pictures and videos can add details to the picture of events and reveal hidden information
- System artifacts can provide additional information on the user's interactions with the device and applications and help with pattern-of-life analysis
Forensic analysis is not a straightforward process. Some artifacts types can be extracted and examined faster, and others need additional efforts. Digital forensics tools do not support each and every application, and if a suspect uses rare ones, examiners need to analyze them manually. To perform such analysis, they first need to detect the usage of such apps and find their files in the device file system. Then, they use low-level analysis tools to identify important information and, if needed, create scripts to output it into a convenient form for further examination. These tasks can take a longer time, though the results may be rewarding.
Conclusion
The investigation into the Trump rally shooter's phone highlights the common challenges in digital forensics. Every step, from accessing device data to finding useful information, requires special skills and tools.
As investigators search the phone for clues about Crooks' motives, the importance of digital forensics tools becomes clear. Tools like Belkasoft X assist in unlocking devices, acquiring and decrypting data, and extracting digital artifacts. During data examination, they streamline the discovery of evidence with a comprehensive toolset.
As digital devices continue to evolve, so do the challenges in forensic investigations. Belkasoft remains dedicated to developing innovative solutions that help experts navigate the complexities of modern electronic evidence and enhance the efficiency of digital forensic investigations.
