Abstract
This article was inspired by an active discussion in one of the forensic listservs. Original post was asking on how to fight with an argument “This is not me, this is a malware”. The suspect was allegedly downloading and viewing illicit child photos and was denying that, explaining the fact of these photos’ presence by malicious software they presumably had. So how can you figure out whether or not the suspect’s computer has actually been subject to unauthorized activities?
I’ve Been Hacked
The “I’ve been hacked” tactic is the most common defense when it comes to crimes committed on or with computers. However obvious it might be, the burden of proof lies on you and not on the suspect. So how can you figure out whether or not the suspect’s computer has actually been subject to unauthorized activities?
Checking for Malware
Well, what about checking if there indeed was a malware? Will the absence of malware prove the suspect’s lie?
Scanning the disk image for malware is one thing, yet it rarely proves anything. No malware means nothing, and any malware that does exist does not prove anything. Why? If there is NO malware, why can’t it be explained by the fact that it just deleted itself by a command from a remote control center? If there IS malware, it does not automatically mean that it indeed downloaded anything.
Capturing a memory dump and looking for active VPN sessions may give you a hint of some unusual activities, but again it won’t prove anything.
In order to discover whether or not the “hacked” defense has grounds, you will need to look at other factors.
Physical Presence
One of the easiest things to check is proving whether or not the person was physically present at the crime scene. And since we’re talking about high-tech crimes, how about collecting location data from the suspect’s smartphone? Android smartphones record GPS coordinates every 15 minutes, passing them on to Google’s servers for location reporting. You may access these records by logging in to the suspect’s Google Account and either reviewing their Location History or using Google Takeout to download the data for offline analysis. Apple’s iPhones also collect location information, and although extracting the data is not as easy as acquiring Android phones it still can be done.
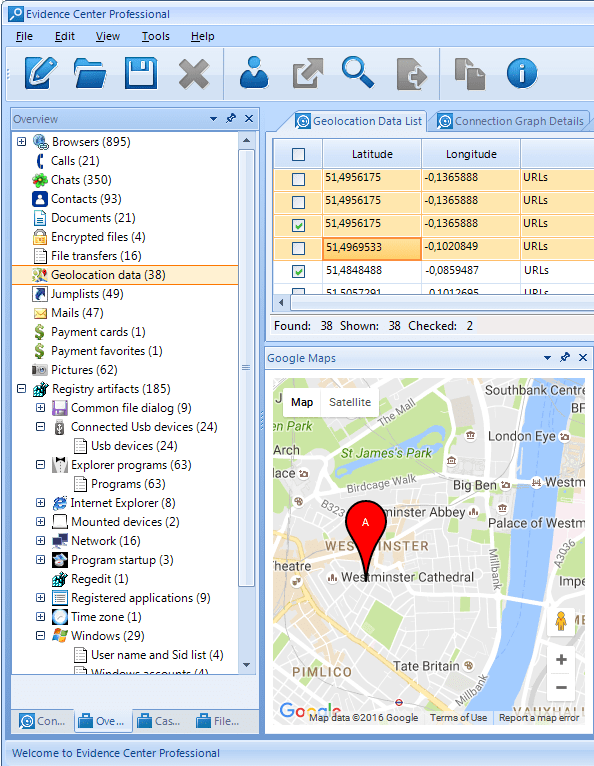
Belkasoft Evidence Center (BEC) can gather geolocation from different sources, such as Google Maps apps, browser searches, geo-enabled chats and so on. You can review one or multiple locations in the Google Maps window right inside the tool.
Timeline
Building a timeline based on multiple data sources is arguably one of the best ways to show the activity happened when the suspect was physically present at the crime scene. Don’t assume; instead, try to acquire as much data as possible to build a comprehensive, geo-tagged timeline.
- Location data. Proves physical presence at the crime scene
- Photos captured with their smartphone. Can contain GPS tags which coupled with time prove the physical presence.
- Posts to social networks. Could have location data as well, and even if not, sometimes allow proving that a post was made from the computer or mobile device from the crime scene. If you extracted such post from a running computer memory dump, it was definitely made from that computer
- Text messages or emails. Are they sent from a desktop computer? Someone present physically at the computer (while alone it does not prove that it was the suspect; theoretically it also could be a malware, while basing on email text you can prove otherwise).
- Logs acquired from the suspect’s mobile service provider.
All of those may link points in time with points on the map or a stationary device, helping you build a connection between a suspect’s activities and their physical presence at the crime scene.
Windows Event Logs and Registry Records
Event logs and Registry records are a valuable source of information that is rarely cleaned. These may contain information which can prove suspect’s presence at a particular desktop computer at a time of illicit actions:
- Logging in. Both Event log and Registry store information on user login attempts. Remember the question above: was it the suspect who sent an email or text chat? If you compare time of sending an email with login times, you can prove that it was indeed a suspect, logged in at the time of interest, not their spouse or children. The same info and logic can be used if an illicit picture has “last access time” matching time of interest.
- Running a program and opening files. Registry stores last opened files and last run applications (e.g. in Windows Explorer registry keys); you can also inspect User Assists. While malware can run a program and open a file, it is not likely that it will download illicit images, then open a Word document and run Windows Media Player

UserAssists are automatically extracted by BEC when processing registry files. You can see that VirtualBox.exe was executed twice with last run time on June 26, 2013.
- Attaching and detaching USB devices such as flash drives. It is hard to imagine attaching of a USB device by malware, so if a device was plugged in, someone was definitely present at the computer.
- Remote control sessions, established VPN connections and so on. While theoretically could be opened by malware, coupled with activities of other kinds it is very unlikely.
Thumbnails
For performance reasons, Windows stores smaller previews of all pictures in a folder, being browsed in Windows Explorer under some views, such as “Large icons”. The format is different for different versions of Windows (thumbs.db, ehthumbs.db, Thumbnail Cache) but presence of a preview can give you important evidence. At least it means that a folder containing pictures was open in Windows Explorer and a user could have viewed them. Even if malware indeed downloaded some illicit images, it is not a regular behavior to open the containing folder and switch it to “Large icons” view.

Belkasoft BEC supports searching for thumbnails in any format created by Windows, and if deleted, can carve them.
See related story of how thumbnails were used in real FBI investigation dealing with child abuse: https://www.cnet.com/news/fbi-posts-fake-hyperlinks-to-snare-child-porn-suspects/
File Activities and Jumplists
While thumbnails do not give you an answer about whether the suspect explicitly opened a picture, jumplists can help with that.
Jumplists are a feature of Windows 7, 8, and 10 that keeps information about recently accessed applications and documents. Unlike other indicators (such as the “last accessed time” NTFS attribute), jumplists indicate that a certain file was opened or launched by the user logged into a certain Windows account. Jumplist records are not created if files are being copied or moved by malware; however, they will be created whether the user opens files locally or over a remote control session. Jumplists can give a certain answer to whether or not a certain file (such as a picture) has been opened in a certain app or not.

BEC shows pictures opened with IrfanViewer along with last opening time. This is a definite proof that a file called “board2.jpg” has been viewed by someone at the computer mentioned in NetBIOS name field (alexcomputerdev) at the specified time (2013.06.27, 16:08:54).
While jumplists can be cleaned (just as every other artifact), they are still relatively little known and rarely wiped. And again, if you see someone with completely cleared jumplists, this is at least suspicious.
Jumplists are preserved during Windows updates; we’ve seen computers with jumplists going back several years.
Privacy Guards and Cleaners
The use of privacy guards, InPrivate browsing and temporary file cleaners is not a crime. However, installing such a cleaning app or performing a wipe session immediately after an alleged crime does look suspicious (yet does not prove anything by itself).
Conclusion
You can work around the “I’ve been hacked” defense by collecting information from the PC/mobile being analyzed as well as from multiple other sources. Establishing physical presence, proving the use of a certain USB drive and proving access to certain files at certain times can be enough to make a weighted decision.
- The software used in this article is called Belkasoft Evidence Center (or BEC, in short) and you can download a full trial at https://belkasoft.com/ec.
- Sign up to a free webinar on this tool at https://belkasoft.com/webinar.
About authors
Oleg Afonin is an author, expert, and consultant in computer forensics.
Yuri Gubanov is a renowned digital forensics expert. He is a frequent speaker at industry-known conferences such as HTCIA, FT-Day, CAC and others. Yuri is the Founder and CEO of Belkasoft, the manufacturer of digital forensic software empowering police departments in about 70 countries. With years of experience in digital forensics and security domain, Yuri led forensic training courses for multiple law enforcement departments in several countries. You can add Yuri Gubanov to your LinkedIn network at
http://linkedin.com/in/yurigubanov.
A full list of articles by Belkasoft Research can be found at belkasoft.com/articles.
