WhatsApp is, by far, the most popular instant messaging (IM) application. It provides free cross-platform messaging and VoIP (Voice over Internet Protocol) services to its users.
In this guide, for purposes in the digital forensics field, we intend to examine the WhatsApp desktop application and web client used on computers (Windows PCs and Macs).
We will also review a potential investigation operation on WhatsApp on a Windows PC while using Belkasoft Evidence Center.
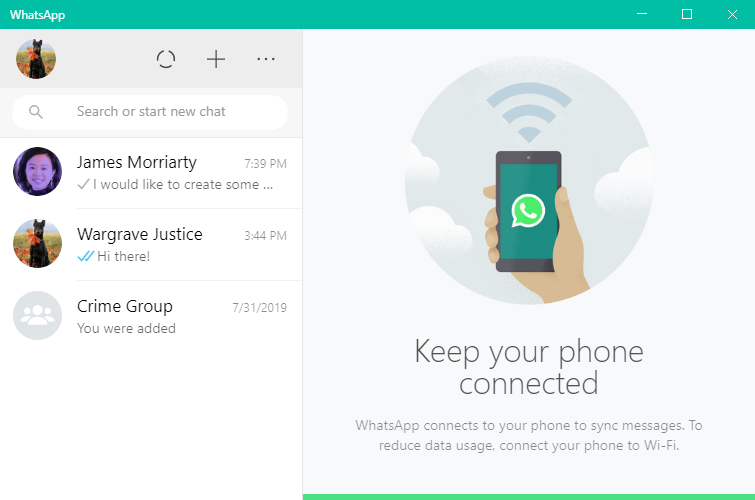
Figure 1. WhatsApp on a Windows PC
NoteIf you are interested in reading on WhatsApp forensics on Android and iOS devices, then you should see our WhatsApp Forensics on Smartphones paper instead.
Background information on WhatsApp and its relevance to investigations
WhatsApp was first released for public use in 2009 on the App Store for iPhones. It was supposed to serve as an alternative for the standard short message service (SMS) on mobile devices.
With over 2 billion users in over 180 countries, WhatsApp is easily the most popular and widely-used messaging application across devices. And with over 100 billion messages sent every day on the platform, WhatsApp is definitely one of the most frequently used apps in general.
Since its release, over the years, WhatsApp has grown to introduce applications for all mobile operating systems (Android, BlackBerry OS, Windows Phone, and others). WhatsApp developers also released the WhatsApp web client (which can be used on all major web browsers on PCs and Macs) and the WhatsApp desktop application (for Windows OS and macOS).
In the last few years, WhatsApp implemented new features like end-to-end encryption, which made decryption of intercepted messages over the air practically impossible. While users and privacy advocates welcomed the new setup supposed to keep their messages more secure, it spelled trouble for law enforcement agencies who had to find new methods of obtaining suspects' communications history.
WhatsApp's messaging capabilities, its broad coverage of all mobile and desktop OS platforms, and its extensive usage make WhatsApp forensics important—and hence, its relevance to investigations. The media regularly reports cases—such as the London Bridge attack—where an attacker communicated with people through WhatsApp before the attack.
WhatsApp's popularity on smartphones—in terms of users—did not completely translate to computers, but millions of people still use WhatsApp on their PCs and Macs. Invariably, on computers, WhatsApp web client (for browsers) and the WhatsApp desktop application are the objects of interest for us in this guide.
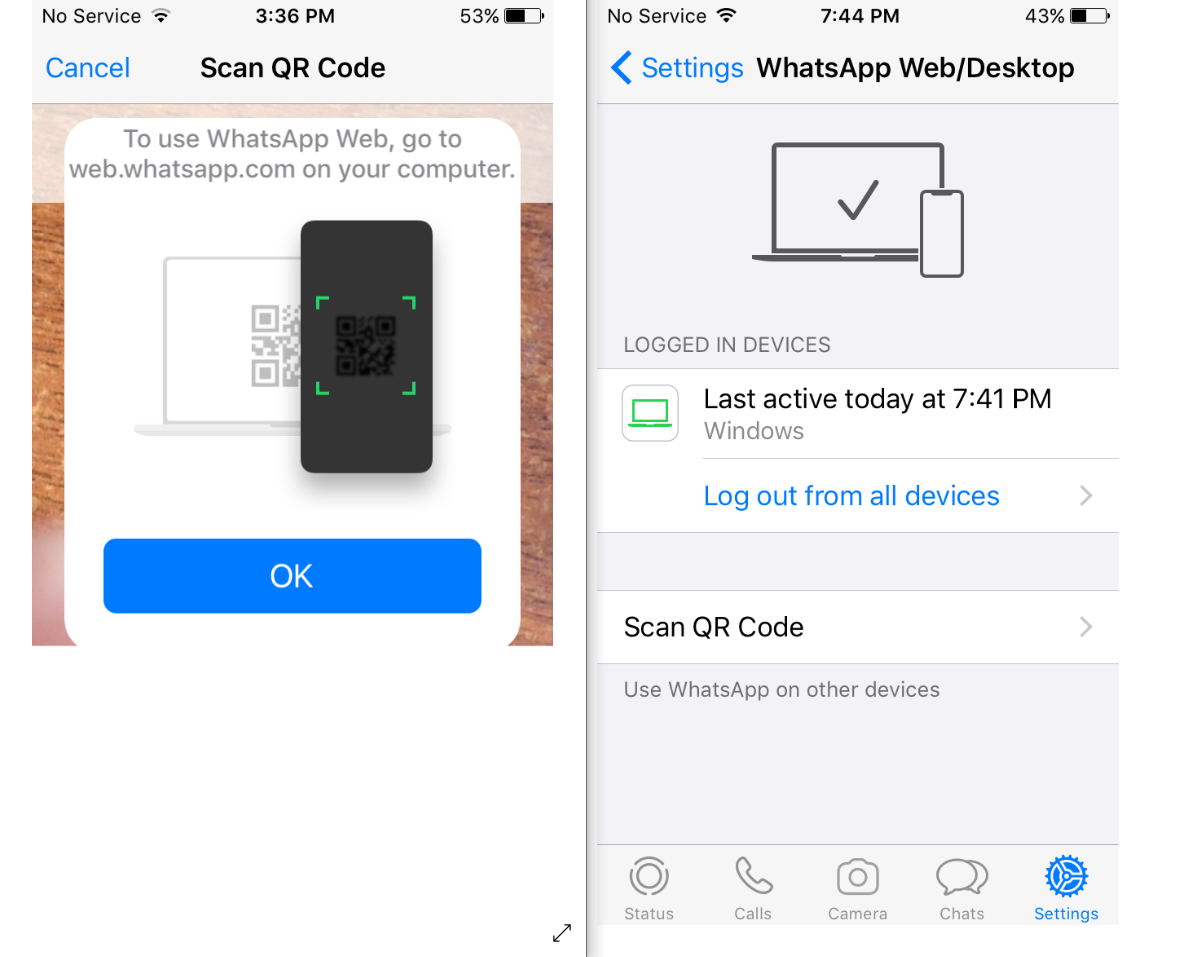
Figure 2. QR code on an iPhone used to configure WhatsApp for use on a Windows PC
- WhatsApp web client
A user simply has to visit the WhatsApp web page on a supported browser and then scan the QR code there using the WhatsApp app on their smartphone (usually an iPhone or Android device).
These are the supported browsers: Google Chrome, Mozilla Firefox, Microsoft Edge, and Safari.
- WhatsApp desktop application
A user has to visit the WhatsApp download page, fetch the appropriate package, and then run the file to install the application.
After the installation, the user will then have to scan a QR code (similar to the one for the web client above).
In any case, both the web client and desktop application are considered extensions of the WhatsApp application installed on a mobile device. They simply mirror the activity—what is sent and received—occurring on the smartphone. Therefore, if the mobile device gets disconnected from a network or dismissed from the WhatsApp platform, the web client and desktop application will become inactive.
WhatsApp on PCs (Windows computers)
- WhatsApp desktop application
You are likely to find the WhatsApp desktop application files along this path:
C:\Users\{USERNAME}\AppData\Roaming\WhatsApp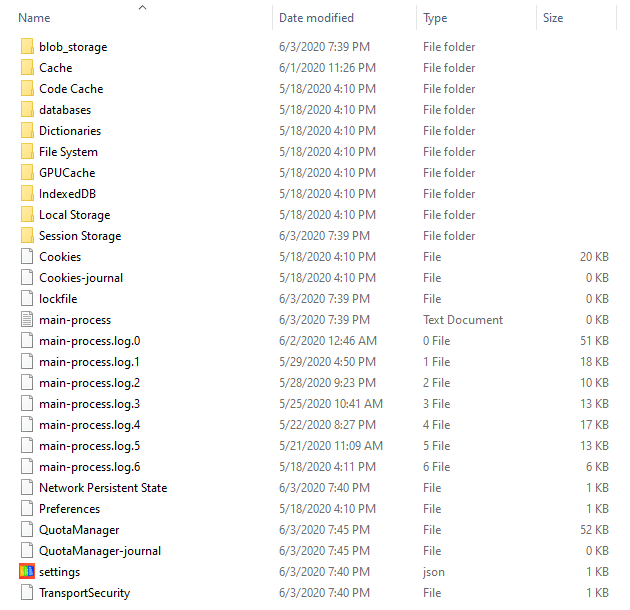
Figure 3. Sample WhatsApp folder on a Windows PC
And you may want to check these paths too:
- \Program Files (x86)\WhatsApp\
- \Users\{USERNAME}\AppData\Local\WhatsApp\
- \Users\{USERNAME}\AppData\Local\VirtualStore\Program Files (x86)\WhatsApp\
- WhatsApp web client
We examined the WhatsApp web client on Windows linked to the WhatsApp application on a smartphone. The task was performed on a Windows 10 computer on Google Chrome. The latter is by far the most popular browser on the platform, so we chose it.
On Windows 10, Chrome stores its files in the folder along this path:
C:\Users\{USERNAME}\AppData\Local\Google\Chrome\User Data\DefaultYou will find the WhatsApp web client (when used on Chrome) files here:
Users\{USERNAME}\AppData\Local\Google\Chrome\User Data\Default\IndexedDB\https_web.whatsapp.com_0.indexeddb.leveldb\ {######}.log
Potential case: Investigating the WhatsApp web client used on Chrome on a Windows machine
Web browsers always leave artifacts—such as cache, history logs, and cookies—behind on a device's disk. In an investigation, you might come across multiple browsers on a computer. And those browsers might store or present information in different ways; the browsers might keep their artifacts in different locations. Furthermore, there might be multiple browser versions installed on a WhatsApp user's computer, so dealing with all of them simultaneously might prove tricky.
For one, if you are to research browsers, you will do well to identify the browsers that were used and locate the artifacts corresponding to them. Here, for example, you can check Windows Prefetch files, which exist along this path: C:\Windows\Prefetch
For another, it also makes sense for you to figure out the time format used within the files and browsers applications. This way, you get to obtain an accurate picture of the events that took place. For example, Chrome uses this time format: WEBKIT Time: microsecond (10-6); Since January 1, 1601 00:00:00 (UTC).
Ideally, you should use a forensic tool—like Belkasoft Evidence Center—that can search for, organize, and analyze web browser artifacts. Belkasoft is likely to find all the relevant items and also present them in formats you understand while saving you time.
In general, on Windows, you can also use Belkasoft to access and analyze WhatsApp data from these sources:
- The system registry
The Windows registry keeps records of installed programs. Windows creates unique installation locations—in Programs Files and Programs Files (x86) directories, for example— and entries in the registry for all installed programs on drives.
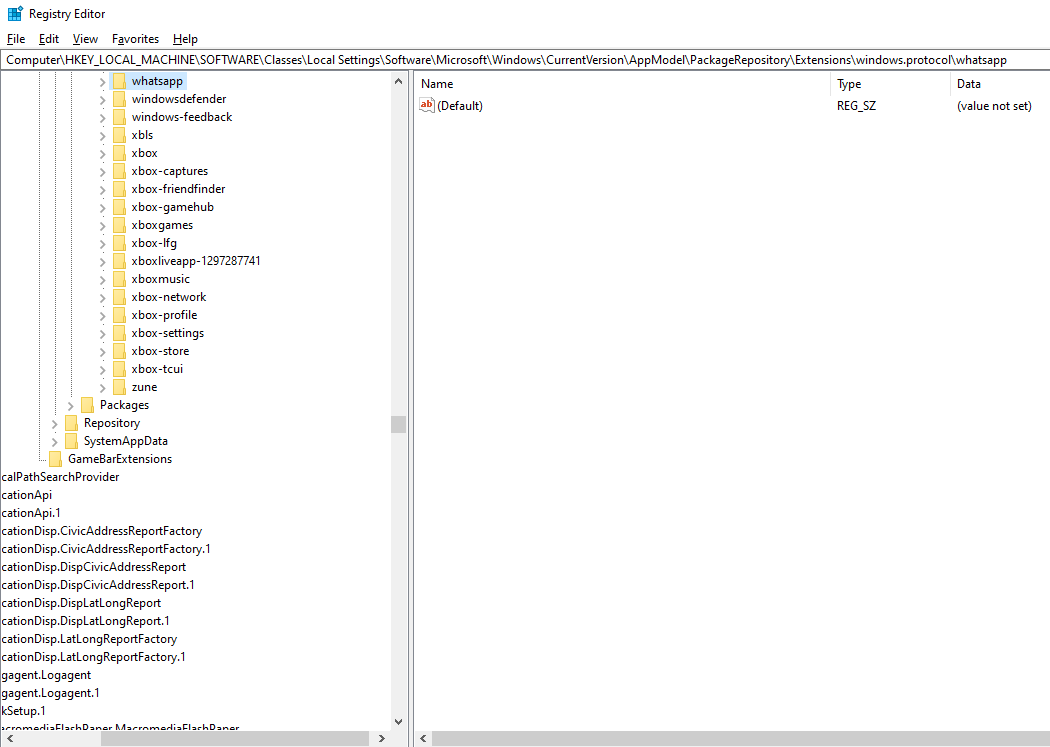
Figure 4. WhatsApp key in Windows Registry
For example, you may find the registry key for the WhatsApp desktop application along the path shown in the image above.
- Prefetch and LNK files
From these files, you get to figure out how many times a user ran an application (the WhatsApp desktop app, for example) and the date/time the application was used. Read about LNK files.
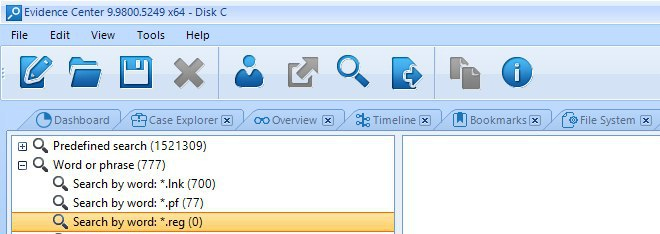
Figure 5. Search task for Prefetch and LNK files in Belkasoft Evidence Center
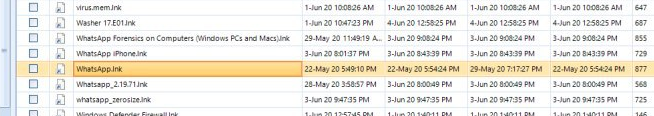
Figure 6. WhatsApp LNK file shown in Belkasoft Evidence Center
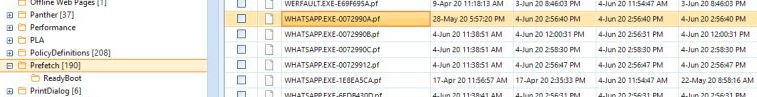
Figure 7. SWhatsApp Prefetch file shown in Belkasoft Evidence Center
For example, you may find the prefetch data for the WhatsApp desktop application along this path:
C:\Windows\Prefetch\WHATSAPP.EXE-XXXXX.pf - Cache WhatsApp profile pictures
From the cache folder, you may find pictures of the suspect, their victims, and pictures sent in group chats.
For example, you may find a user's WhatsApp pictures here:
C:\Users\{USERNAME}\AppData\Roaming\WhatsApp\Cache - Browser history
You may find information on when a user last accessed WhatsApp web on their browser, such as the last date/time they visited the platform, the number of visits, and even the number of times the WhatsApp URL was used.
For example, if a user accessed WhatsApp through Chrome, you may find and analyze their browsing data here:
C:\Users\{USERNAME}\AppData\Local\Google\Chrome\User Data\Default\History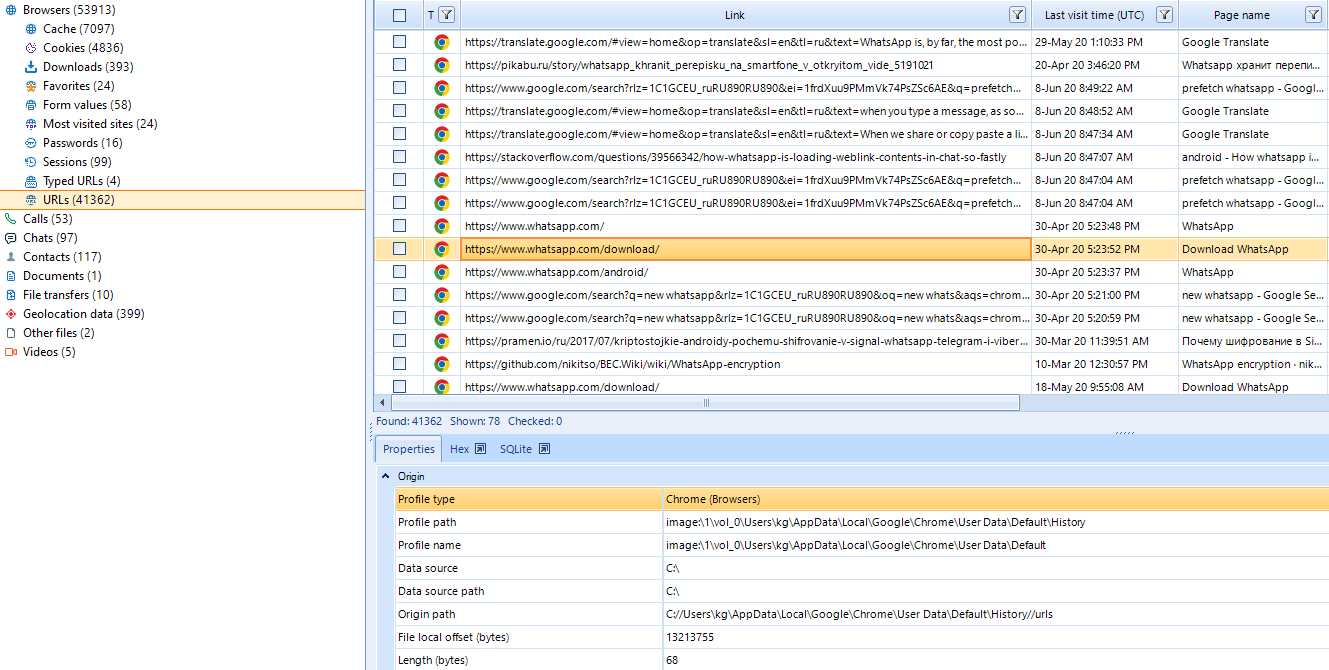
Figure 8. A user's web browsing history analyzed in Belkasoft Evidence Center
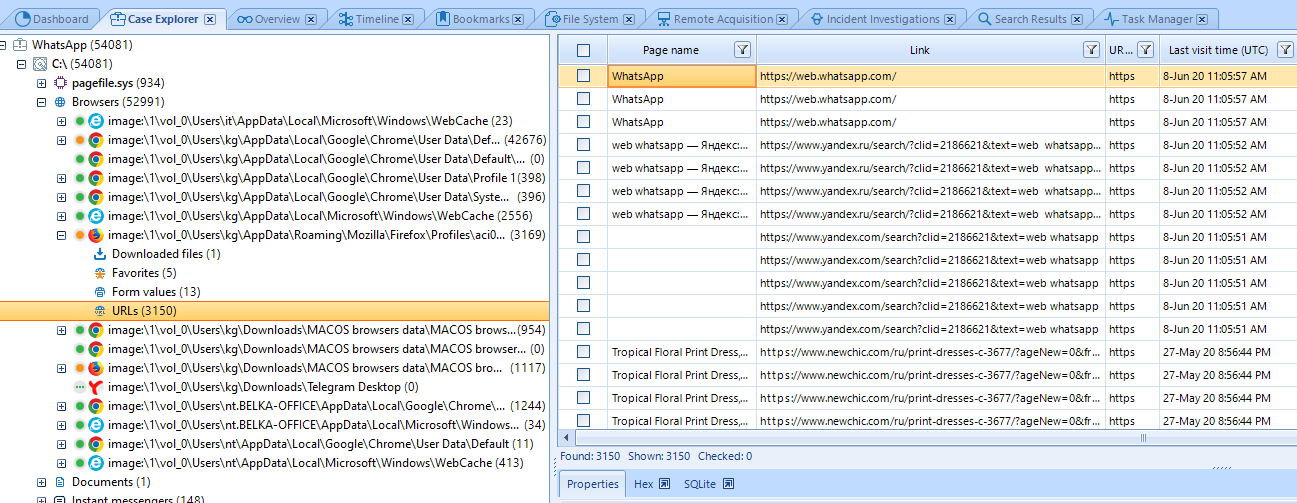
Figure 9. Chrome data analyzed in Belkasoft Evidence Center
WhatsApp on Macs (macOS computers)
- WhatsApp desktop application
You are likely to find the WhatsApp desktop application files here:
/Users/{USERNAME}/Library/Containers/desktop.WhatsApp
Figure 10. WhatsApp data folder on a MAC
And you may want to check these paths too:
- /Applications/._WhatsApp.app
- /Users/{USERNAME}/Library/Preferences
- /Users/{USERNAME}/Library/Logs/WhatsApp
- /Users/{USERNAME}/Library/Saved Application State/WhatsApp.savedState
- /Users/{USERNAME}/Library/Application Scripts
- /Users/{USERNAME}/Library/Application Support/CloudDocs
- /Users/{USERNAME}/Library/Application Support/WhatsApp.ShipIt
- /Users/{USERNAME}/Library/Containers/com.rockysandstudio.app-for-whatsapp
- /Users/{USERNAME}/Library/Mobile Documents/<text variable>WhatsApp/Accounts
- WhatsApp web client
The same variables (for Windows devices) come into play here.
We examined the WhatsApp web client on macOS linked to the WhatsApp application on a smartphone. Here, the WhatsApp web client was accessed from both Safari and Google Chrome, which are the most popular browsers used on Macs.
On macOS, Chrome stores its data in the folder along this path:
/Users/{USERNAME}/Library/Application Support/Google/Chrome/DefaultOn macOS, Safari keeps its stuff along these paths:
- Users/{USERNAME}/Library/Safari/
- /Users/{USERNAME}/Library/Caches/com.apple.Safari/
Meanwhile, when used on Google Chrome, you will find the WhatsApp web client files here:
/Users/{USERNAME}/Library/Application Support/Google/Chrome/Default/IndexedDB/https_web.whatsapp.com_0.indexeddb.leveldb/{######}.logAnd when used on Safari, you will find the WhatsApp web client files here:
- /Users/{USERNAME}/Library/Safari/Databases/___Indexed
- DB/https_web.whatsapp.com_0/wawc/IndexedDB.sqlite3
To search for and analyze artifacts from a Mac, you will need a tool that supports APFS, the file system used in macOS. Fortunately, BEC is one of the few forensics tools that support APFS.
Other things you should know
- The WhatsApp log file, regardless of the operating system environment, is a useful source of artifacts. We can classify the important artifacts that are extracted
from the WhatsApp log file this way:
- The timestamps for user actions:
Sending of messages (text, photos, audio, video, contact), receiving of messages, deleting of messages, blocking contacts, changes made to a user account information (changes in profile picture or name, for example), creating of group chats, and so on.
- Information associated with a mobile client device:
The smartphone build number, the version of the operating system running on the smartphone, WhatsApp version, name of the device manufacturer or device model, and battery level.
- Information associated with browser user agent:
The computer's operating system and the web client being used.
- The timestamps for user actions:
- WhatsApp does not store major data in its log file. When a suspect sends a contact to someone, for example, WhatsApp only records the name of the contact that is being sent, and not the contact's number. WhatsApp only collects information on users' usage, log, device connections, and similar details.
- WhatsApp constantly updates its log file as the user interacts with the desktop application or web client; WhatsApp might overwrite the information it stores on its log file. A timestamp or action might get overwritten by another. Therefore, you must understand that the WhatsApp log file might not hold a user's entire history. We do not know how frequently WhatsApp updates or overwrites timestamps and actions.
- You can find other important artifacts in other packages (besides the WhatsApp log file). In fact, this way, you get to find a user's WhatsApp profile picture, the recipients' pictures, and group chats pictures. You might also be able to figure out the date/time the application was run (by analyzing prefetch and LNK files), the visit counts and date/time associated with them (by analyzing web browser histories), and so on.
- While you are unlikely to find chats or pictures in the WhatsApp log file, you will still do well to analyze this file to get timestamp information, which might serve as
evidence in your investigation or direct you to a better path. For example, from the WhatsApp log file, you can get valuable data (based on timestamps) that points towards a suspect using his iPhone to send child porn images to someone.
In the projected scenario, since you would know the operating system on the smartphone, you will be able to decide what forensics tools or techniques would suit your work best a nd help you solve the case.
- While you can find cached profile pictures for all WhatsApp web clients on both Windows and macOS, there is one exception: The Chrome client on macOS. For some reason, you
might struggle to find the cached profile for the latter.
You can also find the pictures for contacts or groups chats. This way, you get to know with whom the WhatsApp user has been interacting or the groups in which they have been active.
NoteBy extracting and analyzing artifacts from the RAM of a computer, you might be able to access or view a user's chat history for WhatsApp, pictures, and so on. WhatsApp, when open, like the vast majority of applications in Windows, also keeps its stuff in volatile memory.
To acquire a memory dump from a computer, you can use Belkasoft Live RAM Capturer, which is a free tool designed to reliably extract the contents of a machine's volatile memory. After getting the memory dump, you can open it in Belkasoft and view its contents using the built-in HexViewer.
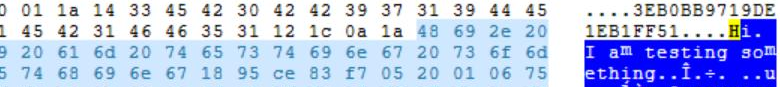
Figure 11. WhatsApp messages from a computer's RAM show in HexViewer in Belkasoft Evidence Center
Conclusion
The WhatsApp desktop application or web client on Windows or macOS will not provide you with the volume of artifacts gotten from WhatsApp on smartphones. However, what you get from WhatsApp on a computer is better than nothing.
And more importantly, by extracting and analyzing the available artifacts with a tool like Belkasoft Evidence Center, you can still obtain forensically valuable data, which can help you with an investigation or case.
For further reading
Other useful links