A jailbreak is a technique or program used to get past Apple's sandbox on iPhones, iPads, iPods, and other Apple devices. Since a jailbreak may permit root access to iOS in an iPhone, for example, it can grant users access to capabilities and functions that are not accessible under standard conditions.
Unc0ver is a relatively popular jailbreak developed by the unc0ver team. It leveraged on a zero-day kernel exploit, which was later identified and coded as CVE-2020-985. The exploit for unc0ver was discovered by someone who goes by the name pwn20wnd on Twitter.
In this article, we intend to examine the unc0ver jailbreak for purposes in the digital forensics field. We will describe unc0ver's properties and also walk you through a procedure involving its use in Belkasoft X in the course of a digital forensic investigation or an incident response case.
Unc0ver's relevance to forensics, investigations, and research

Figure 1. Unc0ver on an iPhone
In mobile forensics, the procedures that allow for the extraction of large volumes of information from iPhones—ranging from the full file system to keychain data—typically involve a jailbreak. While more forensically-sound procedures—which do not involve jailbreaks, such as agent-based acquisition functions—do exist, they may not be practical for use in a case, or they might not be supported on the devices involved.
With the release of iOS 9 in 2015, Apple introduced new, strong kernel security features to protect iOS. Useful jailbreaks largely dried up since then until very recently.
In August 2019, Apple inadvertently reintroduced a previously-patched flaw in its iOS 12.4 release, which then allowed people to jailbreak their devices. However, Apple quickly rolled out updates to patch the flaw again, so users only had a few days to use the public jailbreak.
A breakthrough came in September 2019: axi0mX published his discovery on "checkm8", which was based on an 'unpatchable' hardware flaw. The newly discovered vulnerability affected a wide range of iOS devices, including iPhones, starting from iPhone 4s and down to iPhone X, and many iPad models. Checkra1n was the popular jailbreak that resulted from checkm8.
We have an entire article devoted to checkm8. Read Belkasoft's checkm8 review.
Figure 2. Checkm8 being used on an iPhone through Belkasoft X
Digital forensic practitioners and security researchers use checkra1n to access iPhones' and iPads' full file system copies and extract data from them. However, since the checkm8 exploit can only be used on devices with the Apple's A11 Bionic chip down to the A5 silicon generation, its application gets a bit limited at times because it cannot be used on the newest Apple devices, starting with iPhone XS.
Therefore, unc0ver's entry—especially as an alternative to jailbreaks based on checkm8—is an important development for the security and forensics community. Unc0ver, after all, can be used on newer devices—iPhone XS, iPhone 11, iPhone Pro, iPad Mini (5th generation), iPad Air (2019), and others—that are not vulnerable to checkm8.
About unc0ver
The unc0ver jailbreak is based on software exploits that exist in the most popular iOS versions and almost all modern iPhone models. See the full details for this jailbreak below.
- Affected iOS versions: 11.0 to 13.5
- Affected iPhone models:
- iPhone SE 2 (released in 2020)
- iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max
- iPhone X, iPhone XS Max, iPhone XR
- iPhone 8, iPhone 8 Plus
- iPhone 7, iPhone 7 Plus
- iPhone 6s, iPhone 6s Plus
- iPhone 6, iPhone 6 Plus
- iPhone SE
- iPhone 5s
- Affected iPad models:
- iPad Mini (5th generation), iPad Air (2019, 3rd generation)
- iPad mini 4, iPad mini 3, and iPad mini 2
- 2nd-gen 12.9-inch iPad Pro, 12.9-inch iPad Pro, and 1st-gen 10.5-inch iPad Pro
- 9.7-inch iPad Pro
- iPad Air 2 and iPad Air
- Affected iPod models: iPod touch 6G
Unc0ver can be used on iOS 11 to iOS 13.5—and these iOS versions constitute the biggest proportion of iOS builds running on iPhones and iPads these days.
Unc0ver compared with checkm8

Figure 3. Checkm8 and unc0ver on iPhones
The unc0ver jailbreak has been around for a while now—even before checkm8 made its entry—but the unc0ver team released the program that supported many iOS versions and device models on May 23, 2020.
| Property | Unc0ver | Checkm8 |
| Term | Jailbreak program developed by the unc0ver team and hence its name | Exploit for jailbreak (not a program). Meanwhile, Checkra1n is the popular jailbreak program based on checkm8. |
| Vulnerability | Leverages on software exploits in iOS code | Leverages on a flaw in the BootROM |
| Support for blocked/locked devices | No | Yes, it can be used in BFU |
| Duration/support | Apple is capable of blocking the flaws that enabled the jailbreaking of devices through unc0ver | Apple cannot block the flaws that allow for checkm8 used on devices |
| Supported iOS versions | iOS 11 to 13.5 | All iOS versions as long as the device is vulnerable to the exploit |
| Vulnerable devices | iPhones, iPads, and iPods that appear on the list we provided above. Scroll up. | iPhone and iPad devices powered by Apple's A5 chip through A11 SoC (iPhone 4S through iPhone X and the corresponding iPad devices) |
| Exclusive usage opportunities | New jailbroken device models—such as iPhone XS, iPhone XS, iPhone 11 Pro, and others—that were not vulnerable to checkm8 in the first place | New (and future) iOS builds—such as iOS 13.5.1—for which Apple has blocked the flaws that allow for unc0ver. Certain blocked/locked devices. |
| Data extraction capabilities | Full file system and keychain data | Full file system and keychain data |
Note: Since the unc0ver jailbreak is based on exploits in the OS kernel, it is not as capable as checkm8 jailbreaks in getting past restrictions and security mechanisms put in place by Apple. It is still very useful, however, because it supports more iOS models and devices than checkm8.
Unc0ver in Belkasoft X
Belkasoft X, as a digital forensics tool, provides solid support for mobile and computer forensics. In this regard—since unc0ver is of interest—Belkasoft is capable of acquiring data from jailbroken iPhones.
The acquired images—which Belkasoft obtains from iOS devices—typically contain the full file system and keychain data [link]. With the release of unc0ver 5.0.1, which was the most ignificant unc0ver release, Belkasoft supported the acquisition of the same volume of data from jailbroken iOS devices.
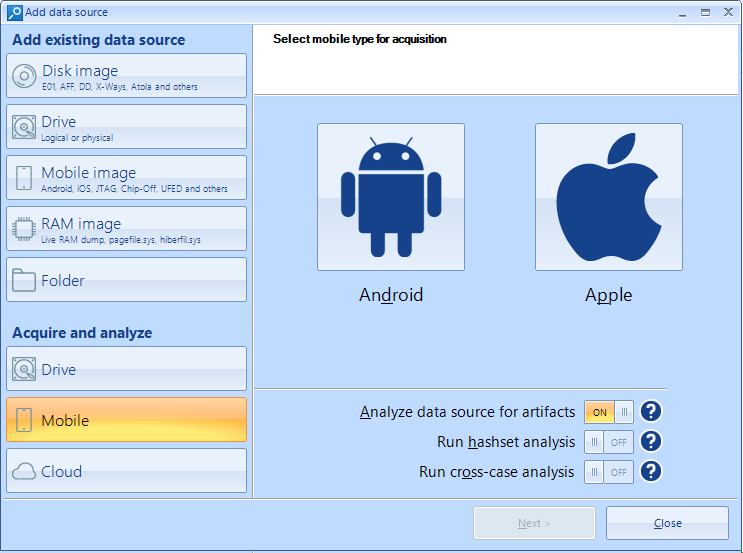
Figure 4. The Add data source screen in Belkasoft X
Sample data acquisition procedure in Belkasoft X
To acquire an iPhone or iPad that was jailbroken through the unc0ver jailbreak, do this:
- Connect the device to your PC. Run Belkasoft X
- Create a new case or open an existing case
- Go to the Add data source screen (using the Ctrl + Shift + F shortcut, perhaps)
- Click on Mobile. Click on Apple
- Click on Full logical backup
- Click on the Verify jailbreak status button. Once the device gets verified, you will be allowed to continue.
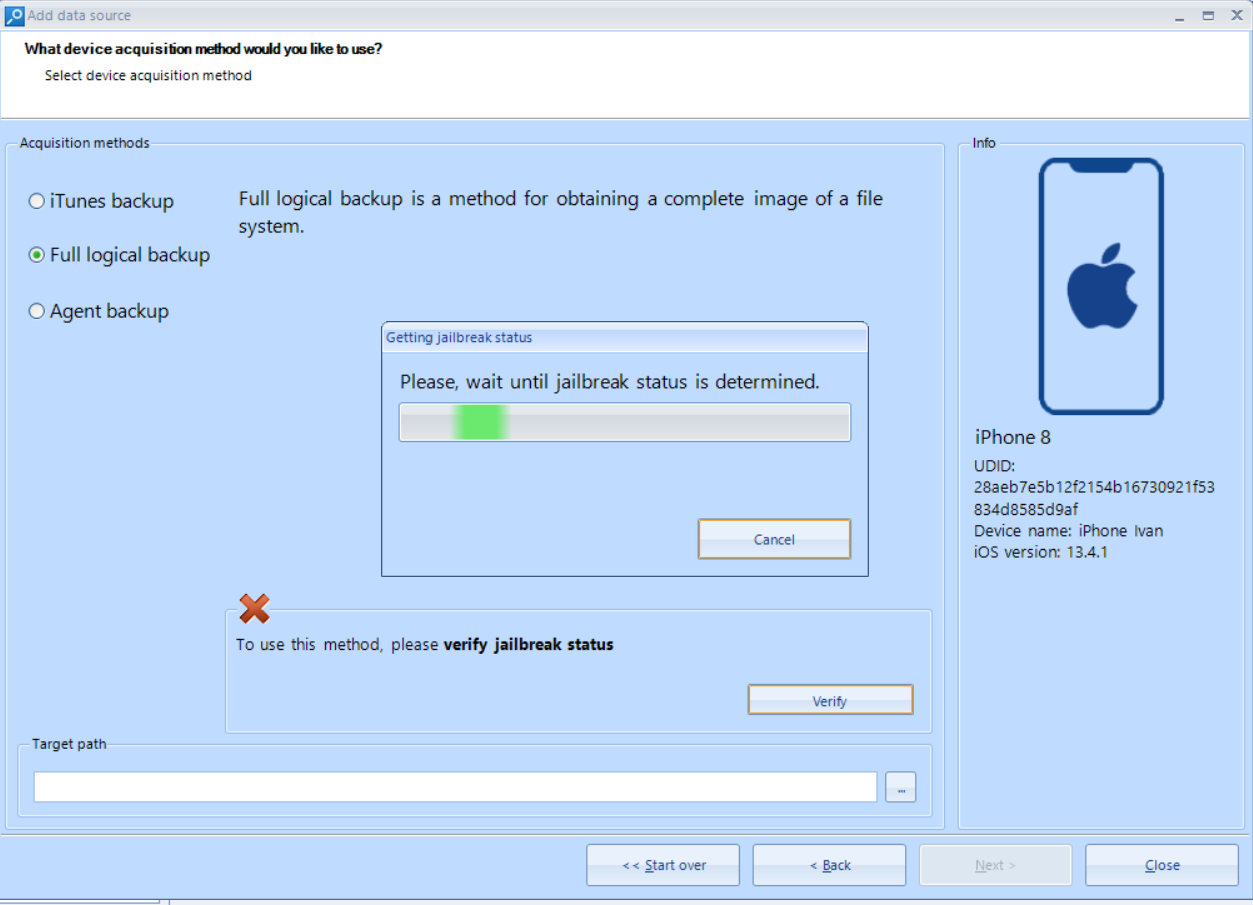
Figure 5. Belkasoft checking the jailbreak status for an iPhone 8
- Click on the button under Target Path to specify your preferred location
- Click on the Next button
- Pay attention to your screen
Belkasoft will initiate the data acquisition task now. Once the process reaches completion, you will see the iPhone or iPad image, which comes out as a TAR archive housing all the acquired data (including keychain).
You can instruct BEC to parse various iOS artifacts from the image. Belkasoft will present the extracted data in known formats.
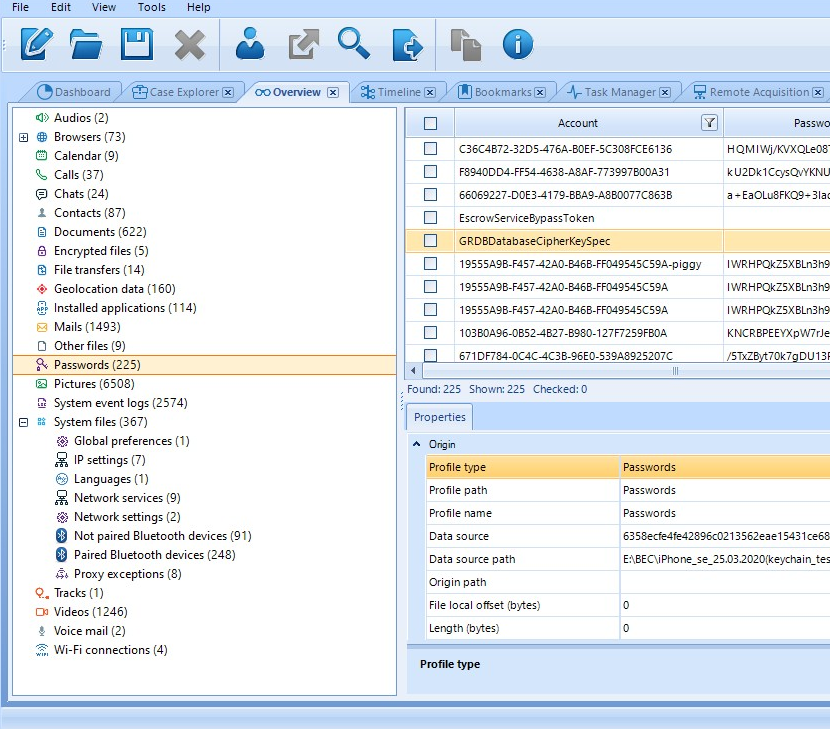
Figure 6. Extracted data from an iPhone presented in Belkasoft X
Conclusion
The proliferation of jailbreaks may point to a shift in the levels of iOS security. Unc0ver's entry is not as groundbreaking as checkm8's, but it is still an important development in the digital forensics community.
While there is no simple all-in-one solution that allows for the acquisition of data from all iPhones and iPads irrespective of the device's age or model, investigators and researchers can take advantage of the wide range of functions and procedures available to do their jobs.