Forensic Extraction of Data from Mobile Apple Devices
This article examines the fundamentals of a forensic examination covering Apple mobile devices. A step-by-step guide describing the process of forensic data extraction and analysis exemplified by Apple mobile devices (iPhone) will be given below. This article will also familiarize its readers with such special-purpose software used in digital forensics as Belkasoft Acquisition Tool and Belkasoft Evidence Center. It will also show how to utilize them to examine devices of this type. As a result, our readers will be in the right position to evaluate the convenience of working with these software products as well as their functionality.
Introduction
We have already written about how forensic data is extracted from a laptop’s hard drive. Now we are going to discuss Apple mobile devices. Analysis of mobile devices is of great importance when it comes to incident investigations since a lot of information about the owner of a device and other sensitive data is stored on them. Apple's mobile devices, such as iPhones and iPads, make up roughly 15% of the mobile device market. That is why forensic laboratories have to deal with them quite often. Correspondingly, this piece will examine the following two key points related to forensic analysis of such devices: i.e. extracting data from the Apple mobile devices together with forensic analysis of such data.
Mobile Data Extraction Types
There are four main types of data extraction in the field of mobile forensics:
1.Logical extraction which handles only certain types of data such as contacts, calls, SMS, etc. Normally, such extraction is performed by installing special software on a mobile device. However, this method is not applicable here because of some features of data organization and security rules covering the Apple devices.
2.Creating a backup copy implies the extraction of logical data that is stored on a device’s memory and which can be extracted according to the security regulations. This is the most widespread data extraction method regarding Apple devices.
3.File system extraction. With this method, one can extract all the logical data from a device. It is applicable to all the Apple devices after jailbreak and makes it possible to extract the maximum amount of data from such devices. At the same time, not every Apple device can be jailbroken. For example, it is not possible when it comes to Apple devices with the latest iOS version.
4.Creating a physical dump. As for this method, one can extract not only logical but also deleted data. Unfortunately, this method can be used only with iPhone 4 and earlier models now.
iPhone Data Retrieval
In this article, it is an iPhone’s data that exemplifies the process of Apple data extraction for the creation and analysis of a forensic copy (the process is identical when it comes to iPads).
Let us use the free Belkasoft Acquisition Tool utility program. It is worth mentioning that it is impossible to extract data from a blocked Apple device. To confirm this statement, we can recall the following notorious story: the US Government, represented by the Department of Justice, requested Apple to unlock a terrorist’s device. Another article will tell which forensic methods can be used to unblock such devices. As of now, it is time to launch Belkasoft Acquisition Tool.
Then click on ‘Mobile Device’ on the screen.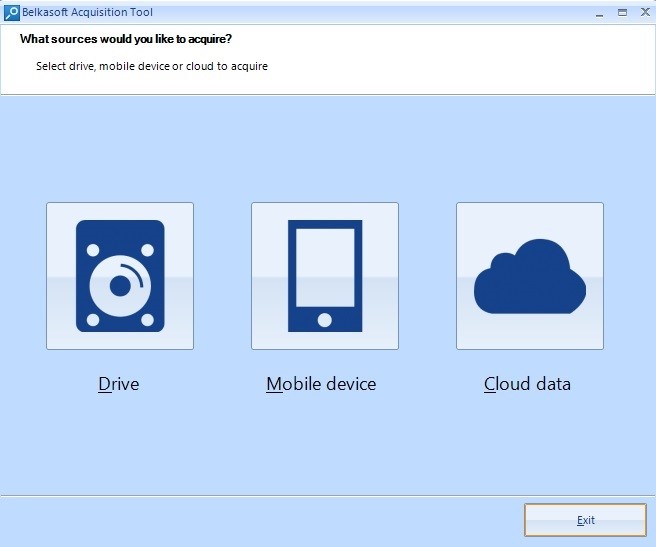
Main Window of Belkasoft Acquisition Tool
Click on ‘Apple’ in the next window.
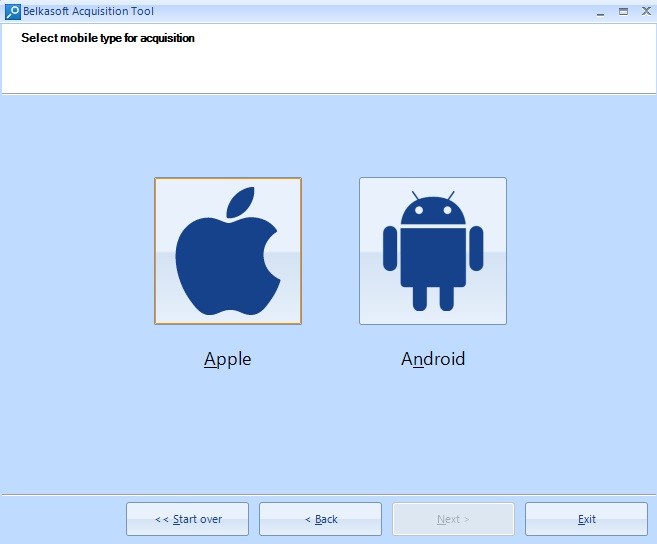
Device Type Selection Type Window
Unlock the device whose data you need to retrieve, plug it to a computer and click on ‘Trust’ on the request on the device’s screen. In the next window, locate the folder to save the data and click on ‘Next’.
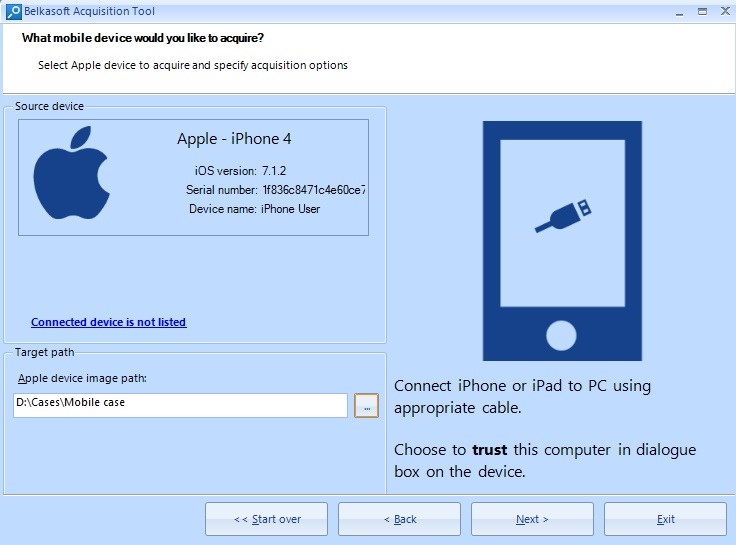
Screen for Plugging a Device
The data extraction process will be launched. After it is finished, the window containing info about the extraction will be displayed. You can find the data extracted by clicking ‘Open target folder’ in the same window.
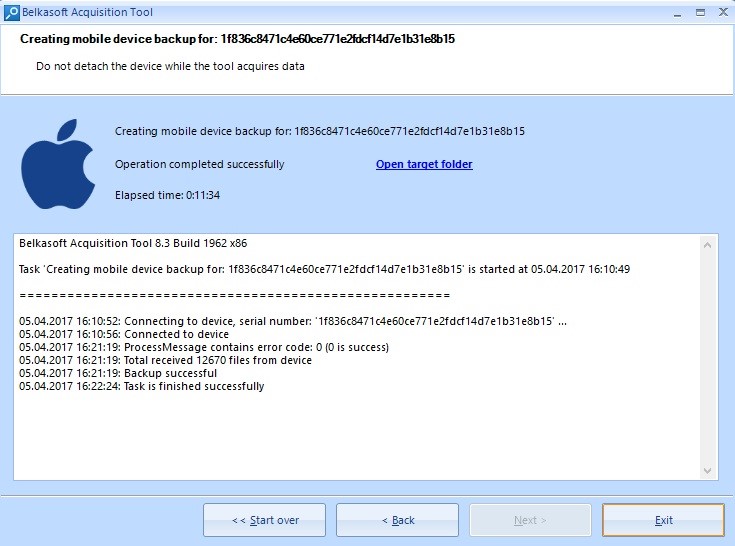
Extracted Data Window
Forensic Analysis of Extracted Data
Use Belkasoft X to analyze the extracted data. Launch the product, define the parameters of a new case, such as its name, folder, the investigator’s name, your description and time zone. Click on ‘New case’.
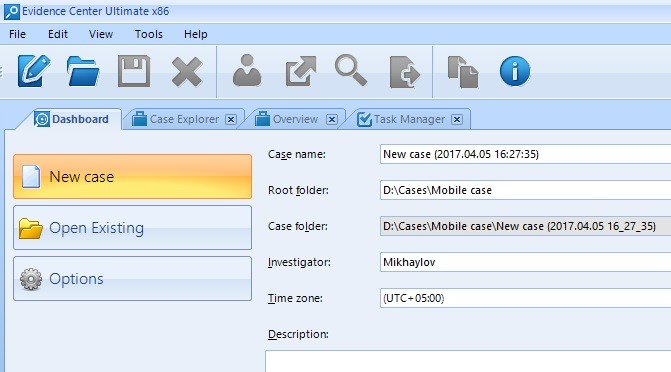
New Case Window
In the next window, define the path to the data previously extracted from your mobile devices.
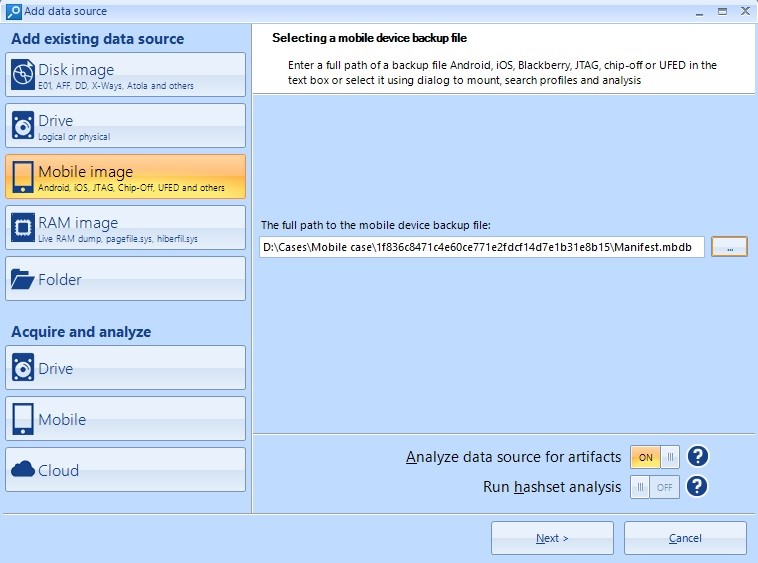
Window to Select a Data Source
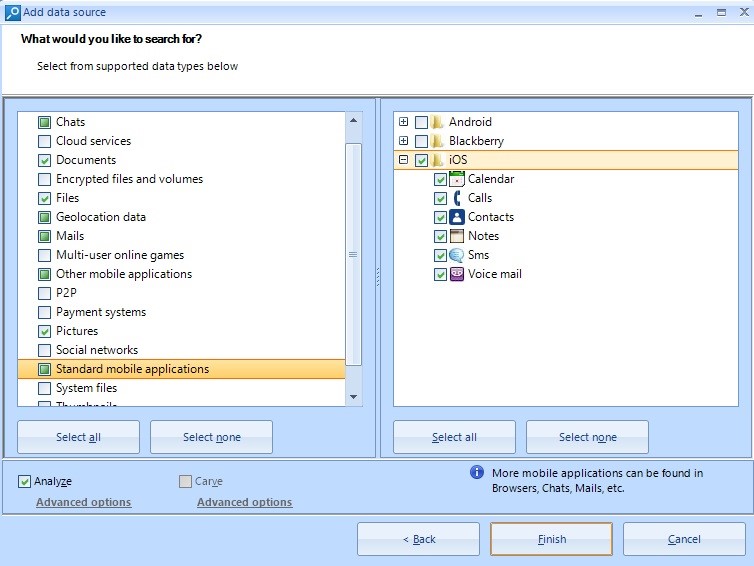
Window to Select Data Types
After the analysis process is finished, the following data types will be shown.
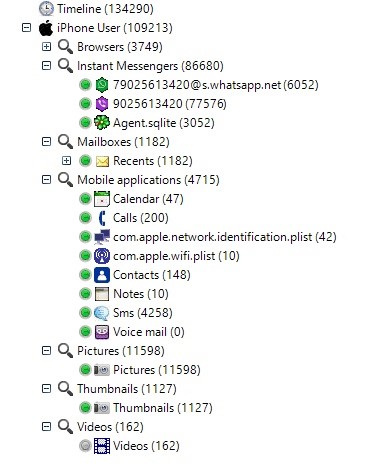
Data Types Retrieved
In spite of the fact that, in this case, a backup copy of the device is created, i.e. a copy containing only those files that are explicitly present on the device, our analysis retrieves as much data as follows: deleted contacts, calls, chats, deleted SMS and notes.
In addition, via analyzing the thumbnails of graphic and video files, once can comprehend what pictures and videos were previously located on the device examined here.
Conclusion
If one does not take into consideration the BlackBerry mobile devices with the BlackBerry 10 OS on them (their amount nowadays is quite limited nowadays, it is shrinking quickly), then Apple devices are the most complex objects for forensic research. The limitations of access to user data imposed by them do not allow us to extract data in full. In addition, the utilization of encryption makes all other known file recovery algorithms useless.
Even if you somehow manage to restore a file in any fashion, its contents will still be inaccessible, since it will remain encrypted.
So, you can fully examine an Apple device, if you jailbreak it. In this case, you can extract the file system from such a device: analysis of this system is capable of extracting the maximum amount of user data. However, such an operation may not be possible for all the types of these devices.