Introduction
There is a common belief, that the Android platform has more bugs than iOS, and Android mobile devices are more vulnerable to security breaches. In other words, it means that it is relatively easy to extract data from mobile devices based on Android OS. Nevertheless, retrieving data from Android mobile phones for forensic purposes is becoming more and more intricate, even in comparison to the iOS devices.
Proving that thought last year and at the beginning of 2020 there were several publications in the journals like Forbes and Fossbytes. A couple of existing cases, demonstrating issues US detectives and forensic experts experience when working with Android smartphones, are provided by authors.
"Sources in the forensics community tell Forbes that the security of Google’s operating system has become, in some cases, too strong to allow police (or anyone else with direct access to an Android phone) inside."[1]
"Anyway, when it comes to cracking smartphones, iPhones are assumed to be superior to Android in terms of privacy and security. However, the story has taken a u-turn, and Android phones have become harder to crack than iPhones. That’s according to a forensic detective Rex Kiser who works with the Fort Worth Police Department."[2]
We examined one of the Android mobile devices from the point of view of data extraction from backup. For the purpose of this article we picked up Huawei Honor 20 Pro smartphone for analysis.
First, we tried to retrieve data from the backup, generated in ADB (Android Debug Bridge) mode, and we got nothing. No data was retrieved from the smartphone, even though the mobile device contained lots of data, including call history, phonebook data, messages, emails, multimedia files, etc. But we know how to cope with this kind of issues, we suggest using native apps developed by technology companies, for example, Mi PC Suite for Xiaomi mobile devices, Samsung Smart Switch for Samsung mobile devices, HiSuite for Huawei smartphones.
On the following pages we will explain to you how to retrieve data for Huawei smartphones with HUAWEI HiSuite, an intelligent manager for Android devices, and analyze it with Belkasoft Evidence Center.
Data Types in HiSuite Backups
A HiSuite backup contains the following data types:
- account data, passwords and tokens
- contacts
- calls
- text messages and MMS messages
- multimedia files
- databases
- emails
- documents
- archives
- application files (.odex, .so, .apk)
- cache data of mobile applications like Facebook, Google Drive, Google Photos, Google Mails, Google Maps, Instagram, WhatsApp, Youtube, etc
Let’s delve into the process of HiSuite backup creation and its analysis with Belkasoft Evidence Center (BEC).
How to Create Huawei Mobile Phone Backup with HUAWEI HiSuite
First of all, the HiSuite backup manager should be downloaded from the Huawei website: https://consumer.huawei.com/en/support/hisuite.
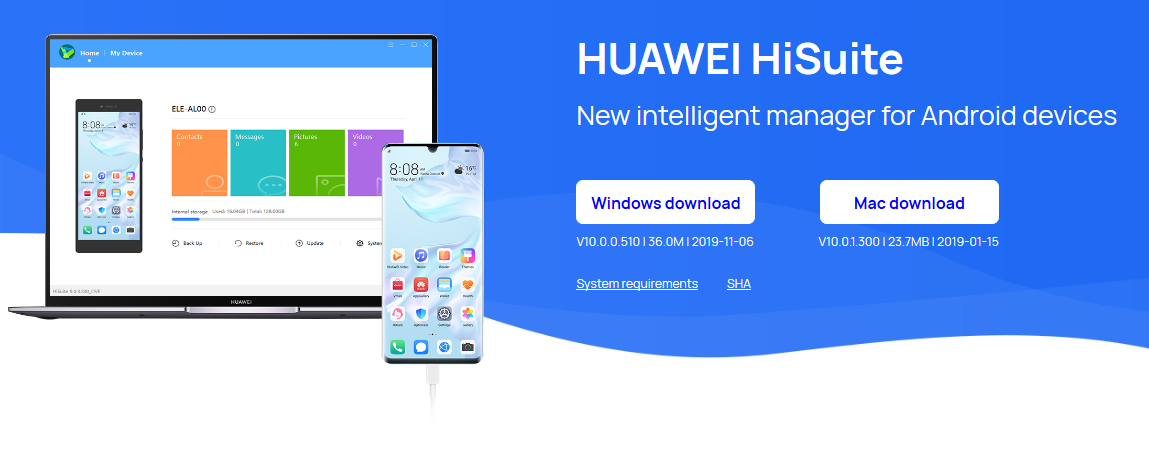
Pic. 1. Website page for HUAWEI HiSuite downloading
The HDB (Huawei Debug Bridge) mode allows you to connect a Huawei mobile device to a PC. The detailed instructions on how to activate the HDB mode on a smartphone are provided on the Huawei website, or can be found inside the HiSuite app.
After the HDB mode is activated, you should launch the HiSuite app on the mobile device, enter the security code taken from the mobile app in the desktop version of HiSuite manager.
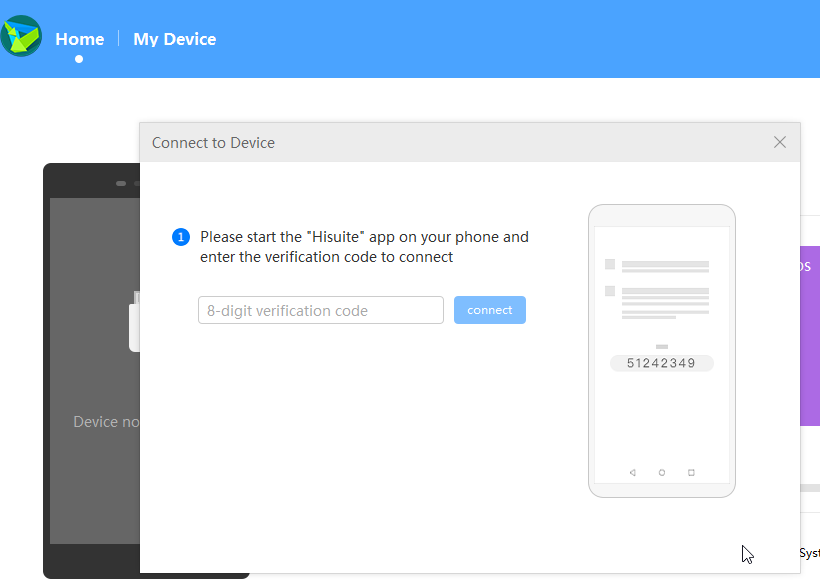
Pic. 2. An input window to enter the code in the desktop version of HUAWEI HiSuite
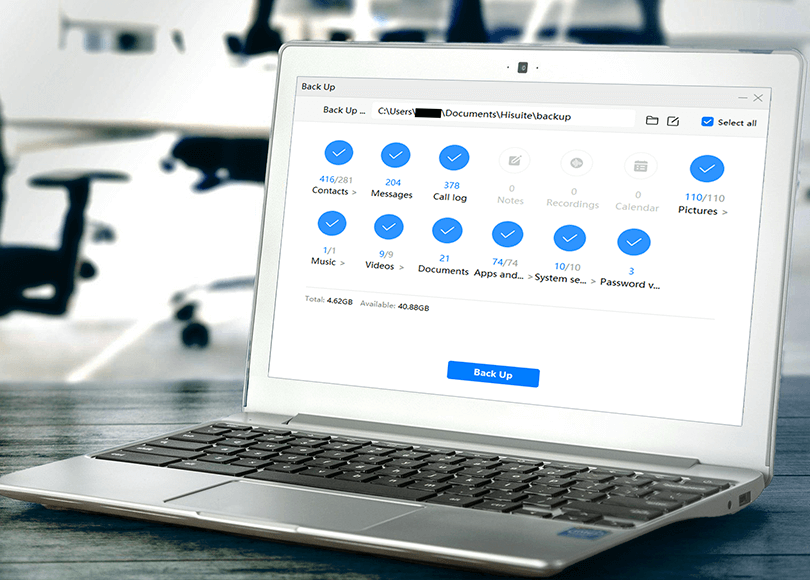
While the backup copy is generated the system will ask you to enter the password, which protects all data retrieved from the device memory. The created backup is in the corresponding folder: C:/Users/%User profile%/Documents/HiSuite/backup/.
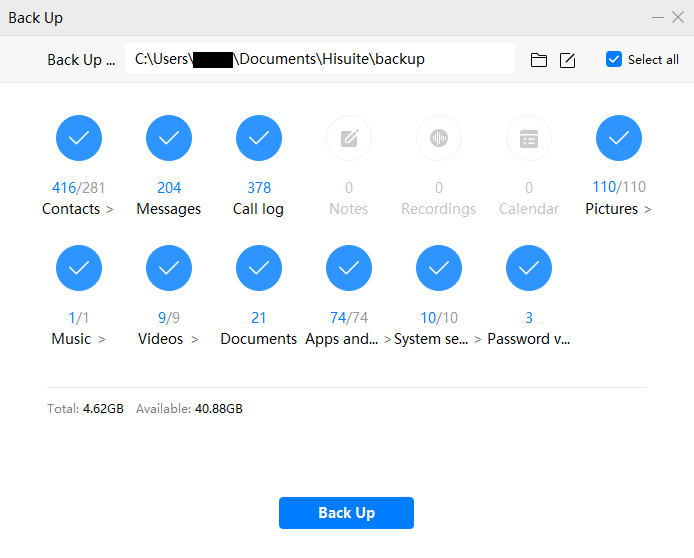
Pic. 3. HUAWEI Honor 20 Pro backup
HiSuite Backup Analysis with Belkasoft Evidence Center
The HiSuite backup analysis starts with the new case creation in Belkasoft Evidence Center. Then you choose “Mobile Image” as a data source. In the new window you enter the pathway to the folder, where a mobile phone backup is saved, and select the file info.xml.
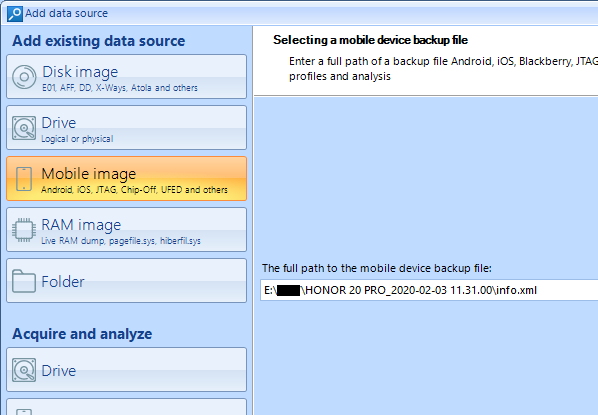
Pic. 4. Selecting file info.xml
In the next window Belkasoft Evidence Center will offer you to pick up artifact types, which are to be extracted. After scanning is completed, you switch to the tab Task Manager, click the Configure task button and enter a password.
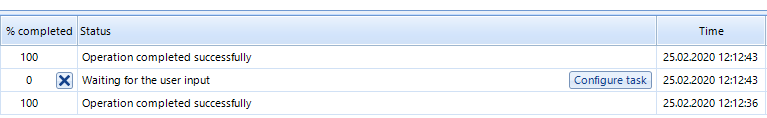
Pic.5. The Configure task button
After backup decryption is completed BEC asks to select the artifact types which are to be retrieved. The results of artifact extraction are provided in Case Explorer and Overview tabs in BEC.
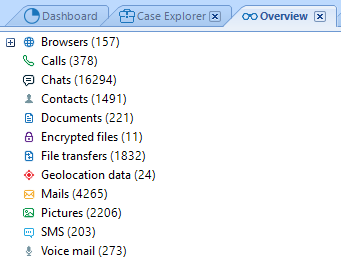
Pic. 6. Presentation of the Huawei Honor 20 Pro backup analysis
Conclusion
Summing up what has been said above, HiSuite intelligent manager allows to retrieve much more data for Android devices in comparison to extracting data from mobile phones with the help of ADB mode.
Even though there is a great number of apps designed for managing backups and data retrieving from Android mobile devices, Belkasoft Evidence Center is one of few solutions on the market, supporting HiSuite backup analysis.
- Google Is Making Android As Difficult To Hack As iPhone—And Cops Are Suffering, May 23, 2019, Forbes
- Android Phones Now Harder To Hack Than iPhones, January 30, 2020, Fossbyte