This story took place a few years ago. A city drug enforcement unit noticed a rise in the consumption of a few new types of drugs, known as "designer drugs". Unlike more traditional drugs, these were mostly consumed by teenagers, and consumers were becoming addicted at a frightening speed.
What are "designer drugs"?
These drugs were frequently labeled as "bath salts", "cactus fertilizers", "shoe polish", or even "aquarium fish food". Designer drugs were being specifically designed to circumvent the restrictions imposed by the list of prohibited substances and contain no chemical structures exactly matching those of available (and prohibited) drugs. The slightly altered—compared to already banned substances—formula, allowed them to be semi-legally sold, unless it got banned—and when that happened, a new formula was quickly developed. These drugs were mostly being sold over the Internet from ordinary looking online stores.
In this case, the drugs were sold via street advertising, painted pavements, containing a Skype contact. It was also advertised on a Facebook page. Dealers communicated with their customers via Skype while the Facebook account contained images of the "goods".
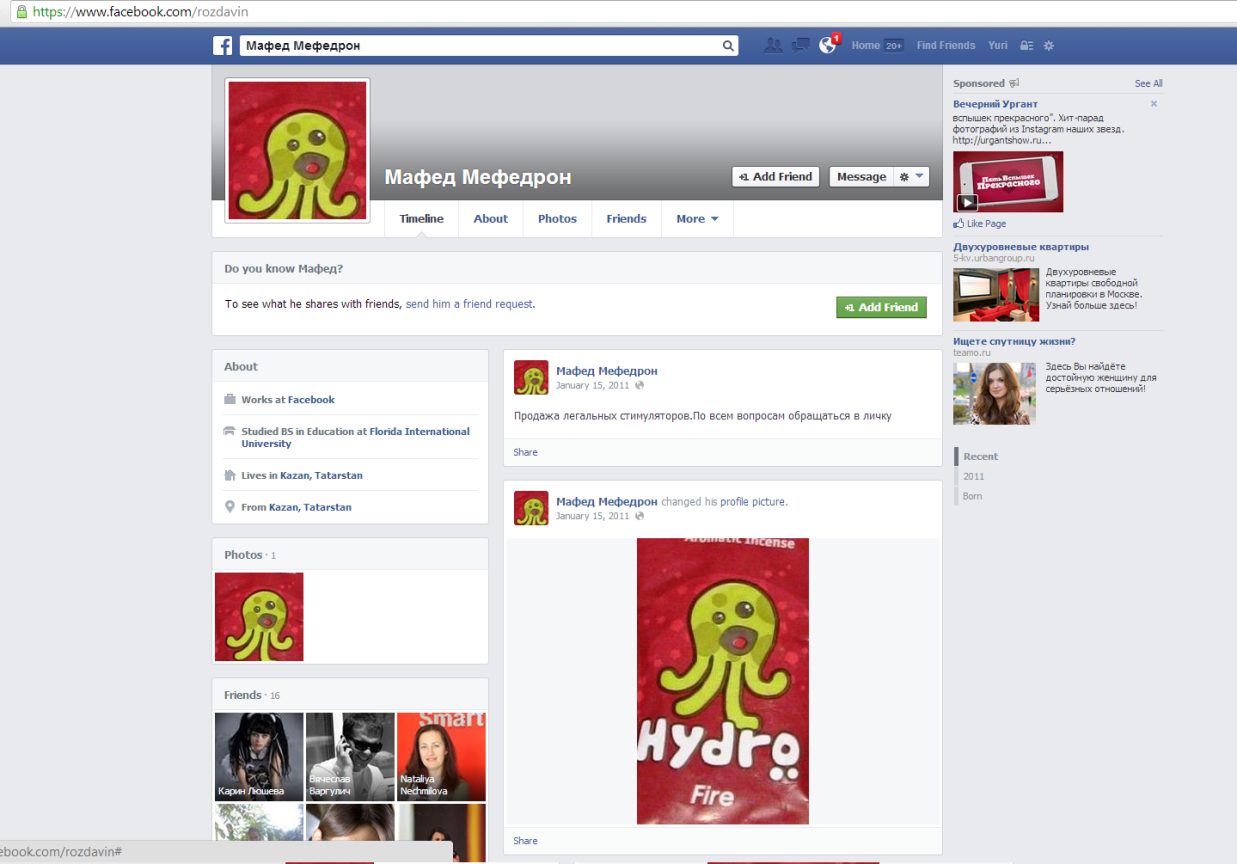
One of the real accounts—now blocked—used to advertise designer drugs on Facebook
With the amount of contact information available to the police, one of the suspects was quickly identified and arrested, and his computer was seized for an investigation. Apparently, the suspect used elevated security settings, so no immediately visible Skype histories were discovered after a quick manual search.
Facebook communications were cautiously performed with the browser's "InPrivate" mode enabled, which leaves no cached items, no cookies, and no history files on the hard drive. The analysis of the hard drive image returned no data relevant to the investigation, due to the precautions taken by the suspect. The analysis of the page file revealed some traces of information including fragments of chat conversations. However, that was not nearly enough to make the case.
Fortunately, a digital investigator assigned to the case, was able to acquire a memory dump, apart from the image of the hard drive.
When given a chance, we always stress the importance of obtaining a memory dump when acquiring a suspect's computer. Memory dumps tend to contain essential volatile evidence, often allowing investigators to establish the necessary links when there is little to no evidence available on the hard drive. To make it easier for investigators to acquire a memory dump, we offer a free Belkasoft Live RAM Capturer tool.
At first, the results were quite discouraging, because pictures of goods, though recognizable, were carved incorrectly:


They were definitely not enough to prove the suspect's involvement in the maintenance of the Facebook page. The reason behind the partially incorrect pictures was memory fragmentation. RAM can be fragmented in the same way that a hard drive can. Simply carving for a JPG or PNG signature will give you the correct beginning of a picture, while some random data may follow, which may belong to another memory process.
Is it possible in such cases to somehow combine pieces together or is it a magic wand expectation?
Belkasoft X (as well as its predecessor Belkasoft Evidence Center, used in that case) has a feature that allows for the extraction of memory processes. If it is switched on during a memory dump analysis, the product will carefully combine fragmented parts of every process into one continuous piece. With this option on, the examiner was able to obtain complete pictures:




Now, when the pictures of these "goods" were recovered, it was important to prove that it was the suspect who uploaded them to the Facebook page, not that he downloaded them from that Facebook page. Fortunately, EXIF metadata was intact within these pictures, while it is known that Facebook strips out most of this information for the sake of security when a picture is uploaded, meaning that such pictures cannot be originated by downloading from Facebook if EXIF data was not removed.
The results of the suspect's computer analysis enabled the investigator to establish a definite connection between the suspect and the Facebook account used to advertise these designer drugs. In addition, evidence of communication between the suspect and their customers was acquired.
As a result, two designer drug dealers were arrested. The naive label "Not for human consumption", which you may notice on one of sachets above, naturally did not help.
More than 30 kilograms of drugs were seized. Distributed in 1-gram packets, this constituted some 30,000 doses—enough to kill several hundred addicts in one year. Fortunately, this did not happen—thanks to the proper forensic analysis of volatile memory.
See also
- Why RAM dumping is so important and what tool to use?
- Magic wand or scientific approach? Myths and realities about digital forensic software
- The case of a missing girl and the power of a memory dump
- 5 Bloopers of a Digital Forensic Investigator
- Why Belkasoft should be your tool of choice for Mobile Forensics
