Having discussed what workplace bullying generally implies and how Belkasoft could help you to deal with this problem in broad terms, we now can get a closer look at what you can do, practically. To begin with, workplace bullying, as a special sort of abusive behavior, can manifest itself in the following three forms:
- Intimidation, humiliation or threats.
- Verbal offense.
- Deliberate counterproductive interventions or direct sabotage.
In fact, each of these dimensions inevitably leaves certain digital footprints. As we can see in this article, up to 93% of info never leaves the digital boundaries. It means that you can investigate cyber workplace bullying, just like any other kind of wrongdoing at the office.
If you deal with continuous bullying, not with just a single isolated instance of misbehavior, there will be digital evidence to analyze.
Let’s imagine that you have been contacted by a bullied employee. If such a worker addresses you personally, it is a good sign which most likely signals his or her trust and commitment. Appropriate measures are to be taken in this case. At the same time, such claims must be substantiated and formalized.
You can use Belkasoft Evidence Center (BEC) for this purpose. Here is what your possible sequence of actions may look like (the following guide is based on a real-world scenario described by one of our customers):
Ask the employee for details
Ask the employee to submit his or her report describing the recent record of bullying. Ask this employee to cite some evidence in digital form (such as e-mails, chat quotes, etc.) proving mistreatment and to attach those pieces to the main report.This step is needed to both narrow your search across the extracted data and to have some first-person evidence to compare with your BEC analysis results (either to verify and confirm the employee’s claims or to reject them if they are ungrounded).
Launch Remote Acquisition process with Belkasoft Evidence Center
You require this stage in order to investigate the preceding bullying record in a confidential manner. Otherwise, the bully/bullies might try to cover up their trace and delete the evidence. Sometimes, if the victim’s claims generate doubts, it may also be reasonable to acquire the victim’s device image as well. We all know that some accusations may be exaggerating or misinterpreting from time to time.By the way, if your current jurisdiction, corporate regulations, and HR-policies (such as employees’ informed consent to be monitored) make it possible, it may also be a good idea to acquire images of ALL devices on a regular basis to monitor your workplace climate. Do not forget to acquire all the possible images, not only PCs, but also RAM and mobile devices.
Start to analyze the data
- Compare your findings with the victim’s claims. If there are inadequate evaluations, sabotage, offensive language, etc., you will find something. You can even compile a special dictionary of words associated with bullying and mistreatment to automate such queries across all the search results.
- If the claims are verified and confirmed, you can intervene with the situation and call the bully to account.
- If the claims are not confirmed, do not make haste. Bullies might have tried to conceal the evidence. That is when you need data carving to extract data they have tried to delete.
Perform additional analysis
There are two additional capabilities that will make any situation much more transparent and clearer for you.First, use BEC's Connection Graph to visualize the entire landscape of a situation. Such a graph is an advanced visualization of different communications between your employees associated with a certain case. Each person is depicted as a dot or an avatar with lines connecting him or her with other employees: the latter depicts communications between them.
The Connection graph covers all the possible channels of communication, such as calls, SMS, e-mails, voice messages, and most importantly, chat applications. This option allows you to examine ties between individuals and even groups in incredible detail. More than that, you can see specific weight of all the formal and informal opinion leaders and central figures.
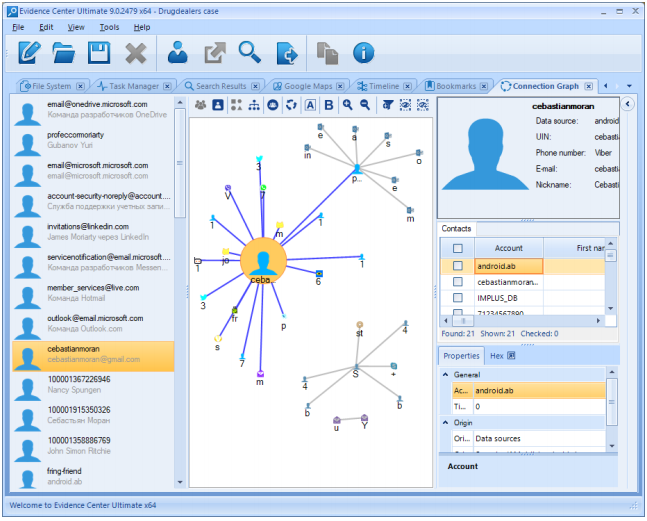
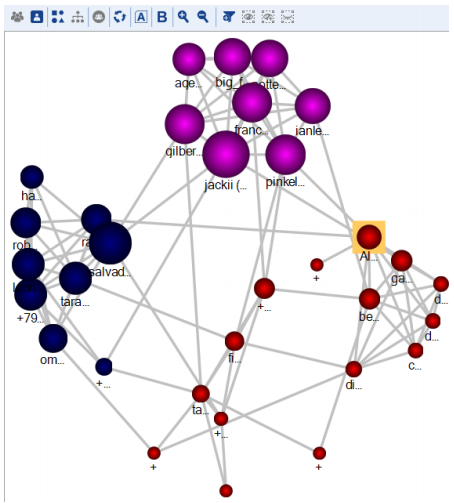
You can focus on all the possible elements of the communication process: intensity, character, context, and even contents of a single message. If you deal with a group of bullies or bullied employees, there is one more feature for you—Detect Communities. This button makes it possible to identify closely connected people who are denoted as ‘communities’ by BEC.
Second, do not forget about BEC's Cross-Case Search. Once you have identified a bully, you can perform a deeper background check. Bullying is a lasting and repeated pattern. According to the recent estimates, over half of bullies have been bullying for more than five years. 80% of them have mistreated more than five colleagues. That is why it may be reasonable to dive deeper into earlier cases.
With Belkasoft Evidence Center you can find intersections between a current case and other existing or archived cases. The facts identified in your current case are examined in contrast with your BEC archive, with all the matches being reported. Such facts include:
- phone number
- e-mails
- profile names and app UINs
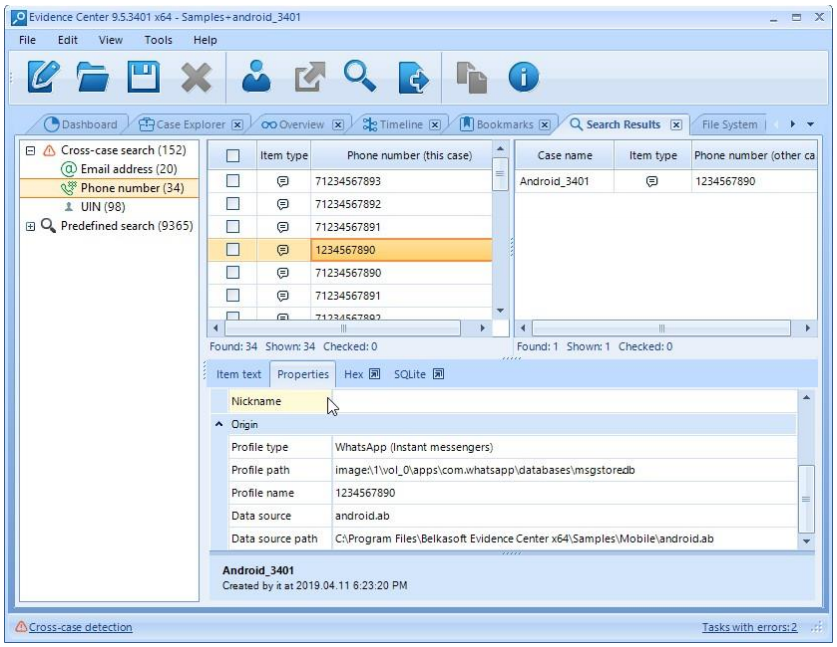
With this tool, you can scan the entire story of a trouble making bully across all the cases he or she has been involved in.
If you use these two features appropriately, in addition to the main analysis, you will have more than enough evidence either to reject an employee’s claims or to substantiate them and act accordingly.
For all intents and purposes, your business will be protected.
Conclusion
We do not mean reputation risks alone. Bullying harms your business, your performance, and your talent pool. Let us cite some findings provided by the Workplace Bullying Institute:
- You lose the work time of both the bullies and the bullied ones since you pay for every minute they spend on their conflict and the bullying process.
- Turnover-associated costs. If a bullied person leaves your organization, you may have to pay for overtime hours other employees will work to cover his or her absence. You will also bear costs related to headhunting, integration, and adaptation of a new employee (who might also leave soon because of bullying).
- Lost opportunities i.e. those goals the bullied employee could have reached (and those the new employees are unlikely to attain because they will be mostly preoccupied with their integration).
- Costs associated with litigation and settlements are harder to estimate, but they are always high nonetheless (in the US in particular).
That is why it is a good idea to insure against this costly risk.
If you are a boss, do not ignore employees’ complaints or other wake-up calls. Keep an eye on the situation constantly. Talk to people. Act proactively. Update your anti-bullying corporate policy. Use Belkasoft Evidence Center to ease your investigation. It is efficient, intuitive, and easy-to use.
You can check this out for yourself and download a free trial.
Read the first part
5 Reasons Why Corporate Investigators Need Belkasoft to Fight Workplace Bullying


