Individuals and businesses, now more than ever, store their data in electronic formats. Regardless of where the data is stored, the ability to extract the necessary information and present it to the appropriate parties while keeping to rules and guidelines—especially in civil or legal proceedings—is crucial. And this is where computer forensics and eDiscovery come in.
In this article, we intend to examine eDiscovery, first on the basis of it being an important concept in litigation. Then, at important flashpoints, how to use Belkasoft Evidence Center X (Belkasoft X)—a digital forensics tool—we will also review the processes that define the typical eDiscovery procedure (a model), describe its data storage peculiarities (formats), and also walk you through important use cases.
What is eDiscovery?
eDiscovery (Electronic Discovery) refers to the process of identifying, collecting, legally validating, and analyzing electronic data with the aim of using it as digital evidence in a civil or criminal case. It encompasses the discovery procedures in litigation that are performed in electronic formats.
These are the typical eDiscovery objects: emails, database information, voicemail messages, chat information from instant messengers, image files, video files, information from social networks, and so on.
The primary purpose of eDiscovery—especially in the initial phase of litigation—is to ensure that parties in a dispute provide each other with the relevant electronic information, records, and details, which can serve as evidence.
- Technical experts work to store digital evidence securely to ensure the opposition cannot make claims the evidence was somehow tampered with, destroyed during the process in which it was obtained, or make claims that the evidence was acquired in violation of procedural rules.
- The highly sought-after digital evidence often exists in an array of poorly structured data. This data is typically stored in several locations such as company servers,
in the cloud, in databases, in archived backups, IoT (Internet of Things) devices, and others.
It is impractical to expect an individual (lawyer, in most cases)—who is not trained in eDiscovery—to find the necessary data while having to examine and search through many evidentiary sources. For this reason, technical experts are usually tasked to assist lawyers. These experts help lawyers by isolating large volumes of data and then extracting and presenting only information relevant to the case. This approach significantly reduces the time needed for audits or investigations.
- Because most judges, lawyers, and other legal practitioners are poorly versed in technical terminology, technical specialists must emphasize the importance of forensically-sound processes and methods used to detect, consolidate, and seize digital evidence. These experts, using language that legal practitioners can understand, also have to stress the usefulness of discovered information—which may not be obvious to untrained eyes—for cases or investigations.
Why is eDiscovery important?
Whether we intend to or not, activities in today's modern world produce a large number of digital footprints. These footprints—which intrinsically tend to exist in varying amounts and different formats—can always be detected and documented procedurally by technical experts. A client or their lawyer can then use this discovered information against the other party in court proceedings.
In the eDiscovery process, technical experts help to detect or find the digital footprints, process them appropriately, fix and analyze them (where necessary), and also evaluate the results and materials ultimately presented in court. Furthermore, technical specialists may help develop a model for the correct presentation of digital evidence in court, provide legally sound arguments, and also construct solid lines of defense based on discovered data.
Essentially, eDiscovery guarantees secure and instant access to a client's business information with respect to a strict access model while providing the means to search, view and/or analyze data and legally select specific documents or the items relevant to a client's request.
Model for detection and storage of electronic evidence
eDiscovery corresponds to all the processes and technologies that aid clients in discovering and securing digital evidence. This way, the relevant parties are able to analyze the data the quickest and most thorough way possible. The eDiscovery setup ensures that clients and their lawyers understand the value of acquired information used in winning court cases and settling different forms of litigation.
eDiscovery encompasses 9 key stages:
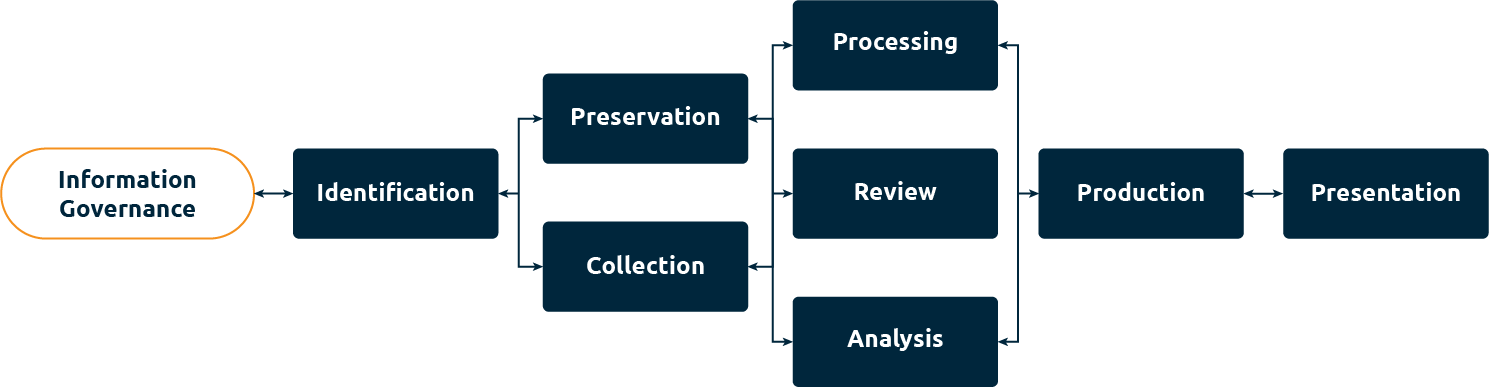
Figure 1. The 9 key stages in eDiscovery
Stage 1: Information Governance
In this stage, a client's policies, procedures, and electronic turnover policies are studied. You get to determine the wide range of sources holding the client's information: workstations, servers, clouds, mobile devices, data storage systems, virtual storage mediums, etc.
Stage 2: Identification
The identification stage is used to search for sources that may contain data potentially relevant to a client's request.
Belkasoft Remote Acquisition (Belkasoft R) and Belkasoft Triage (Belkasoft T) could be used to produce quick results and enable a decision to proceed or not with a full acquisition of this data source. Belkasoft R allows a user to access data remotely, while Belkasoft T functions as an effective portable acquisition tool.
Stage 3: Preservation
Having identified potential sources of information, you get to perform certain tasks to ensure that the information contained in the evidentiary sources is protected from damages—accidental or not—and alterations.
Stage 4: Collection
In this stage, you collect information from the provided sources based on the request and perform legal registration tasks. Apart from the desired information, you should also collect metadata, which may point to a file's creation date and size, its cryptographic hash, and other facts that could prove helpful. These details can later be used to confirm that the information collected was not modified.
Belkasoft X allows you to collect evidence from a wide range of sources
- Physical storage media (hard drives, flash drives, servers, storage mediums attached to networks, etc.).
- Mobile devices (phones, smartphones, fitness bracelets, etc.).
- Cloud storage (cloud service providers: Microsoft 365, Google Drive, OneDrive, iCloud, and others; social networks; and email servers).
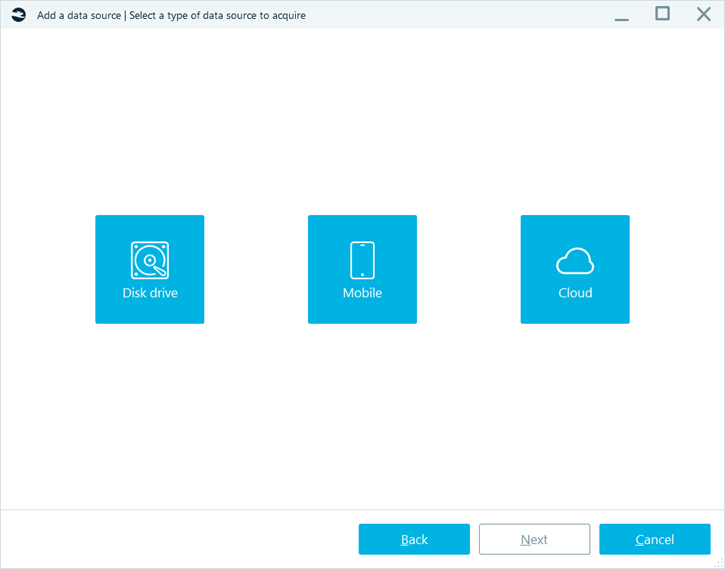
Figure 2. The data types that can be extracted using Belkasoft X
Another Belkasoft tool, Belkasoft R, is developed specifically for remote extraction and will be useful in cases when the devices in question are situated in geographically distributed locations and evidence needs to be gathered remotely. This software can be used to acquire hard and removable drives, volatile RAM, and connected mobile devices remotely.
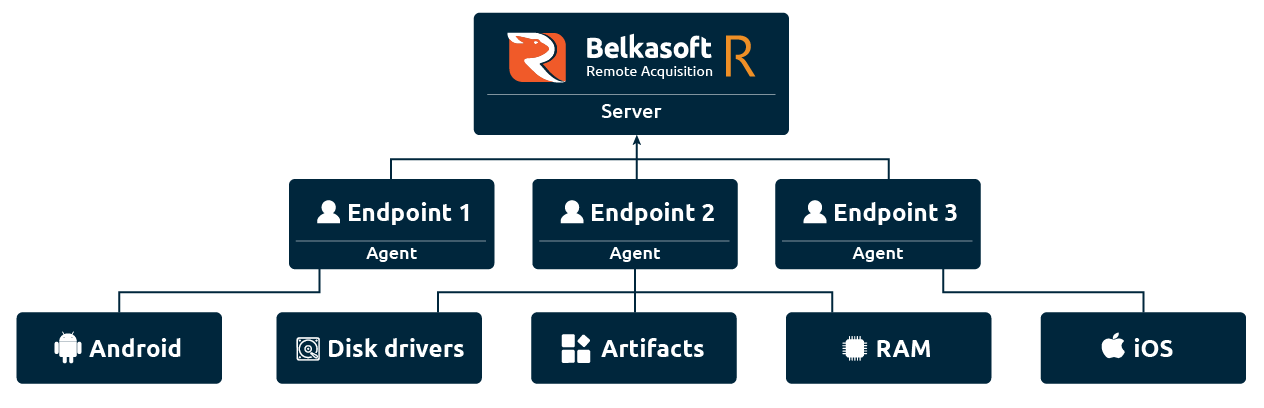
Figure 3. Belkasoft R interaction scheme
Endpoints could be acquired from both local and global networks, including subnets behind routers, and access remote devices even on VPN.
Stage 5: Processing
In stage five we begin to move into the processing phase. This is where the collected information is prepared for a variety of analysis tasks. As a general rule, a special forensics tool is used to process information. In this information processing stage, files can be extracted from different directories; artifacts can be obtained from forensics copies and redundant system files; duplicates can be removed.
With Belkasoft X, you can process information drawn from different sources. This specialized forensics tool will present findings in a format convenient for further analysis.
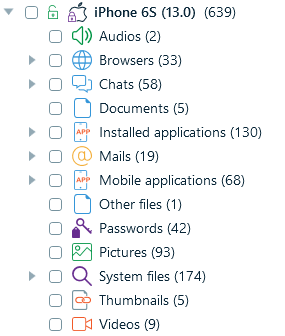
Figure 4. The artifacts from an iPhone device presented in known formats in Belkasoft X
Stage 6: Review
In this stage, a digital forensics expert—alongside the client and/or their lawyers—can analyze the results obtained from the information processing tasks to establish the most useful artifacts (while culling irrelevant items). Depending upon the tools in use, Artificial Intelligence (AI) may also be employed to speed up things here.
As a high-tech digital forensics tool, Belkasoft X uses AI to effectively separate or group objects from the results. For instance, Belkasoft uses AI to assign detected images to specific categories (faces, for example).
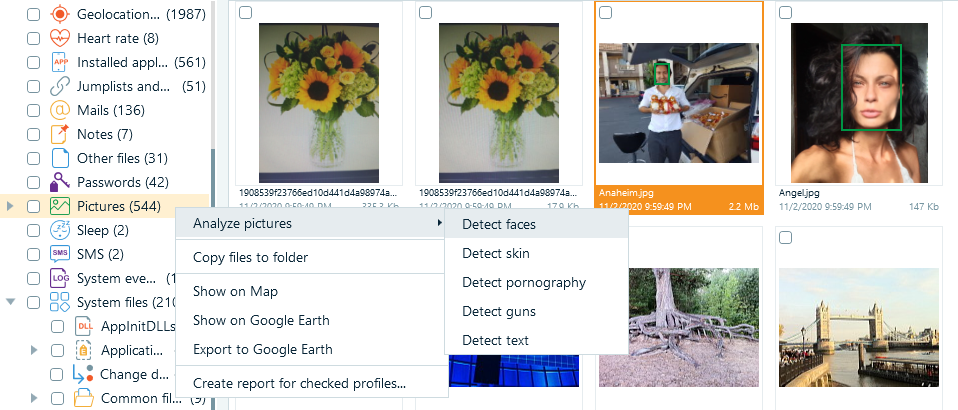
Figure 5. Belkasoft using AI to place images into different categories or groups
Text detection
The detection of text in imagery is complemented by Optical Character Recognition (OCR) with one of 50 available alphabetical languages, such as various European character sets, as well as hieroglyphics (Chinese and Japanese). Recognized characters and words are indexed to enable an examiner to easily find text within pictures.
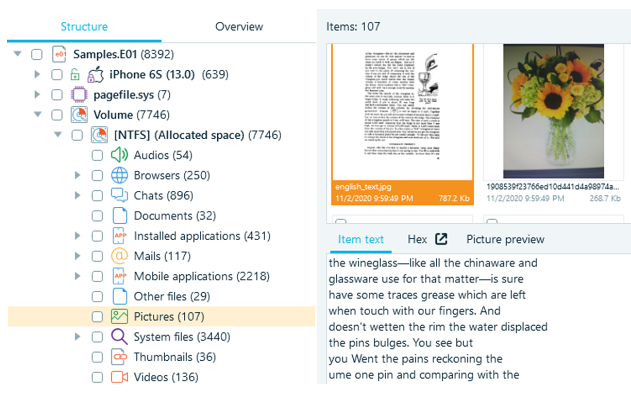
Figure 6. Recognized text in Belkasoft X
This feature can save an examiner a lot of time as company documents may originate from a scanner. Though such documents are typically stored as a PDF file, the text inside is often not indexed or searchable due to the file format. Opening thousands of documents and reviewing them manually would likely take an overwhelming amount of time. Belkasoft X can detect such documents, automatically recognize the embedded text and extract it making it searchable (much like a regular Word document).
Connection graph
Belkasoft X supports a high-level visualization capability called a Connection Graph. This graph displays a high-level visualization of interactions between different people involved in a case. You may see individuals represented as dots (or avatars), which are linked together by lines— this means the individuals interacted with each other (i.e. communicated) through calls, SMS messages, instant messenger chats, file transfer sessions, emails, and other means.
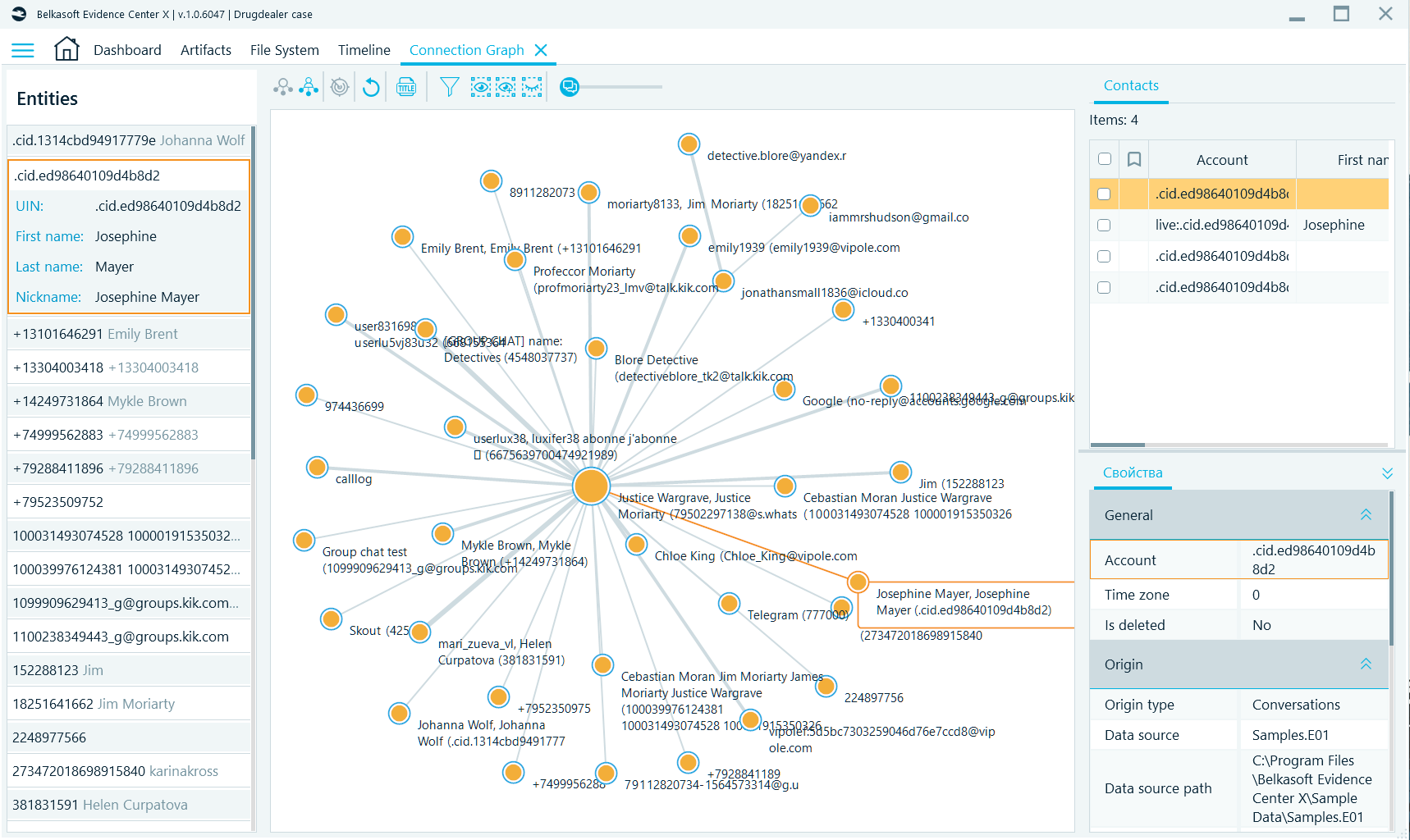
Figure 7. Visualization of interactions on the Connection Graph
Stage 7: Analysis
The analysis stage may be considered a variation of stage six. This is where you initiate deeper, more targeted searches for useful content and relevant context in the analyzed information and artifacts. Here, you may utilize search templates, key topics, known data about people, and knowledge from discussions relating to the results.
Belkasoft X provides a wide range of functions for performing the tasks in this stage. You can use Belkasoft to filter data based on given criteria or apply certain search functions for keywords.
Timeline
With Timeline, Belkasoft X displays all artifacts in your case according to their timestamps—chats, emails, documents, pictures, and others—and presents them in chronological order. Timeline allows you to review all activities or events that occurred around specific periods of time on one or more devices. You can also use two synchronized views: graphical and grid views.
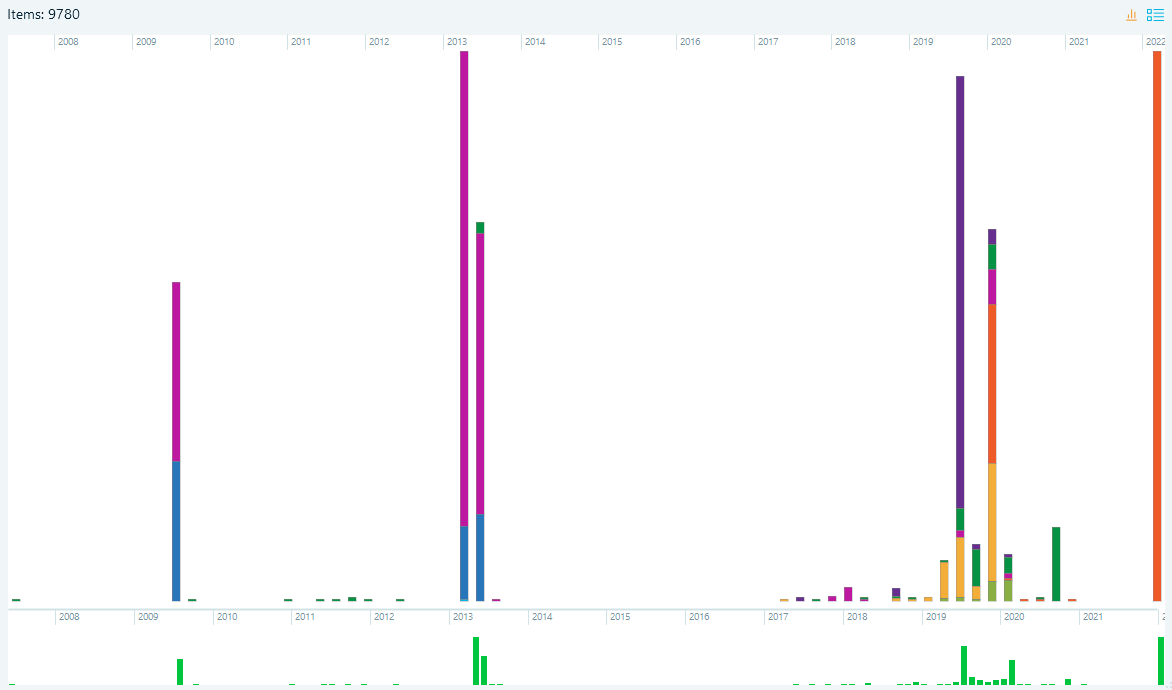
Figure 8. Graphical Timeline
Advanced filters
Advanced filters allow for complex filtering of files using various criteria and their conjunctions. With Belkasoft X you can utilize any number of simple criteria, join them using AND or OR conjunctions, use NOT clauses and named filters, and combine these capabilities to build even more complex and powerful filters for improved productivity.
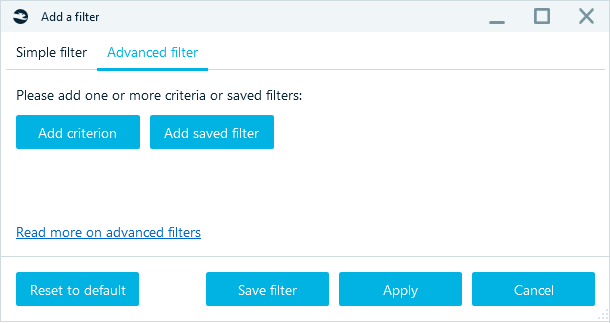
Figure 9. Creating an advanced filter
There are also a number of text-based filters such as "contains", "starts with", "ends with", as well as date range filters that can be employed to improve findings.
Hashset analysis
You can filter files by whitelist and blacklist hash sets. The whitelist filter will hide all files with matching hash values, while the blacklist filter will show only matching files.
You can add one or multiple hashset databases against which you can evaluate matches. The following types of hash databases are supported:
- NSRL (National Software Reference Library)
- ProjectVic versions 1.3 and 2.0
- Plain files in text and CSV formats. This option is most handy if you would like to provide the product with your own hashset
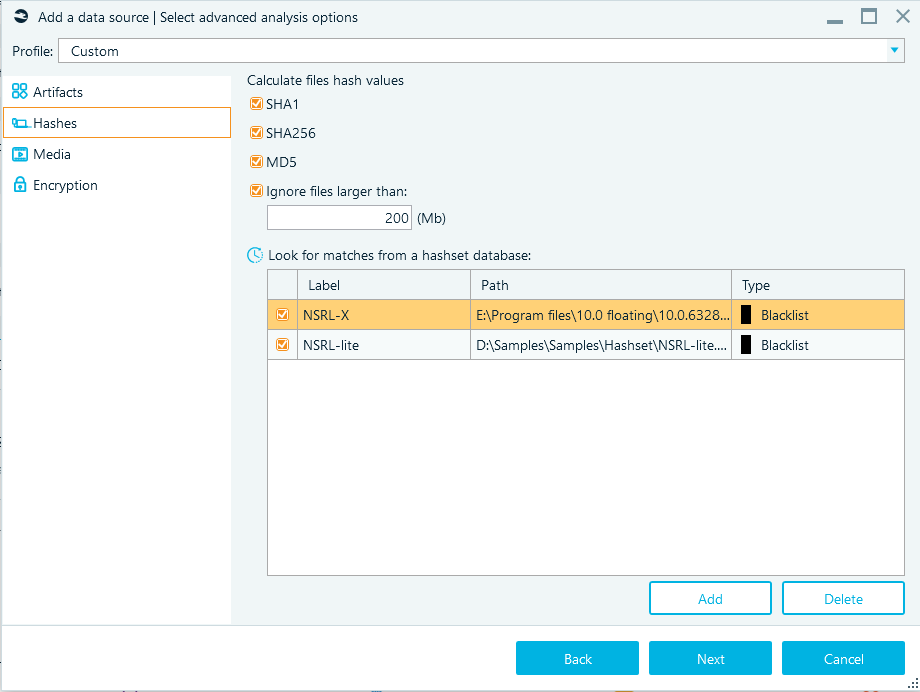
Figure 10. Adding one or multiple hashset databases
Stage 8: Production
In this stage, you identify documents and information that a client and/or their lawyers can use as evidence. You may also have to prepare documents for the parties relevant to a case.
Belkasoft X allows you to create bookmarks for almost all artifacts or objects—such as an email, chat, contact, geolocation, or even a registry setting. Belkasoft X highlights bookmarked artifacts with colors to help you find and recognize them easily.
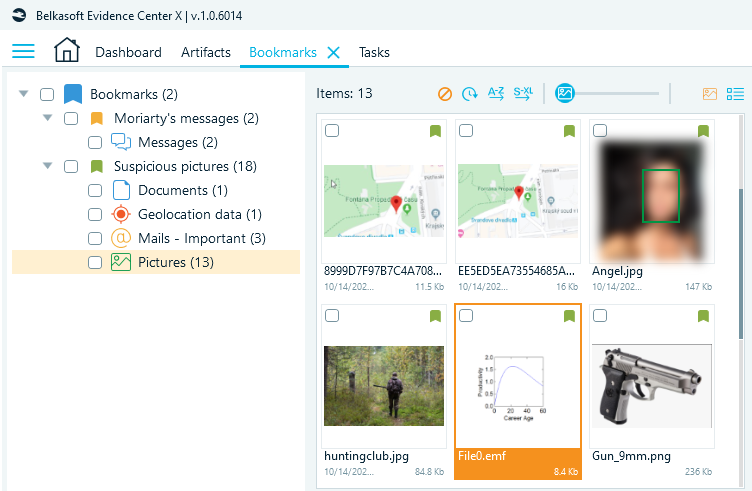
Figure 11. Bookmarks window
Stage 9: Presentation
Now it is time for all that hard, detailed work to pay off - the presentation stage. This stage encompasses the processes for the presentation of the analyzed results to the relevant parties (i.e. clients, their lawyers, and/or courts).
Belkasoft X provides a standard interface for the presentation of all results. With this interface, all parties can conveniently view results. It is important to note that with the Belkasoft DFIR Software suite the results of any analysis work can be viewed by anyone using a free viewer—Belkasoft Evidence Reader. This tool is a free utility embedded in the delivery package. You can use it to present the results of your research or work to the appropriate parties.
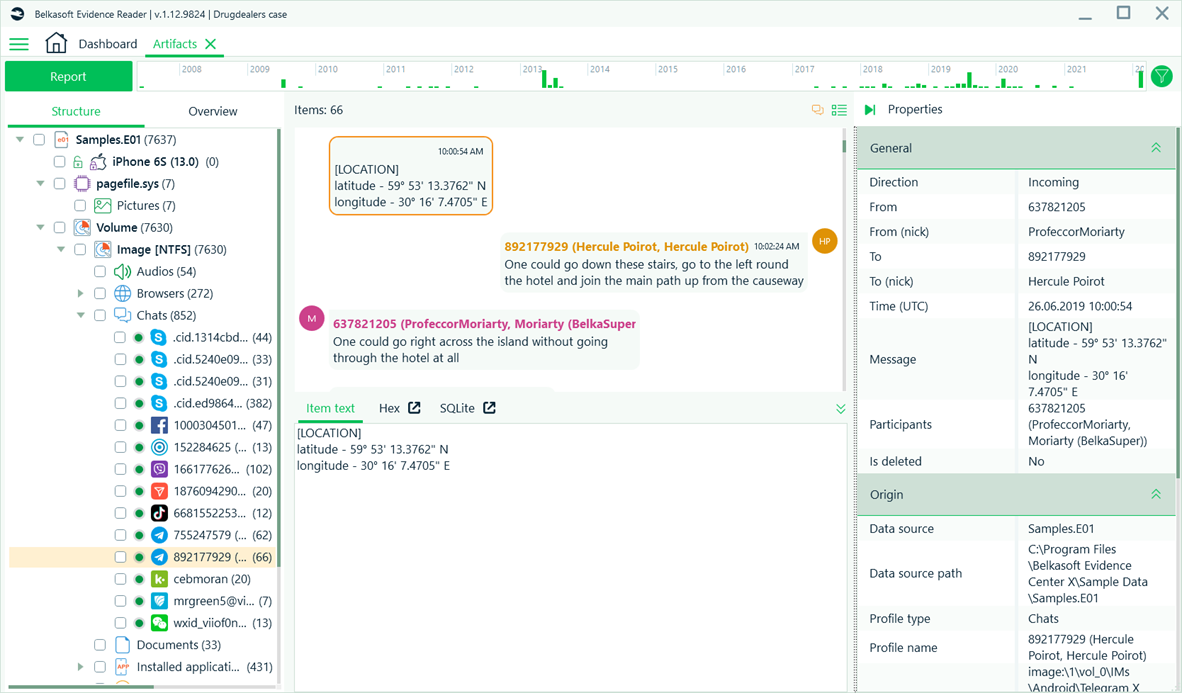
Figure 12. Research results presented in Belkasoft Evidence Reader's interface
Formats for the presentation of results
In the world of eDiscovery, technical experts typically present the results of their investigation in these formats:
- Native format files: Copies of these files are saved in the format in which they originally existed. For example, a document originally in the .docx format gets saved as a file in the same .docx format; an email originally in the .eml format is saved as a file in the same .eml format; and so on.
- Similar format files: These files are converted (or extracted and then saved) to another format that displays the data in ways very similar to the native format. The new format, however, does not require people to use specialized software to view them. This approach also provides the means for convenient search tasks (through keywords or based on specific queries).
For example, information from emails—especially those originally in .htm, .mht, or .rtf formats—and databases are saved as text files or in the .csv file format.
- Graphic format: All graphic files are converted to image files, which typically exist in the .tiff format.
- Paper format: All the extracted electronic evidence is printed on paper.
Belkasoft X allows you to create reports in several formats accepted in courts and used by clients' lawyers.
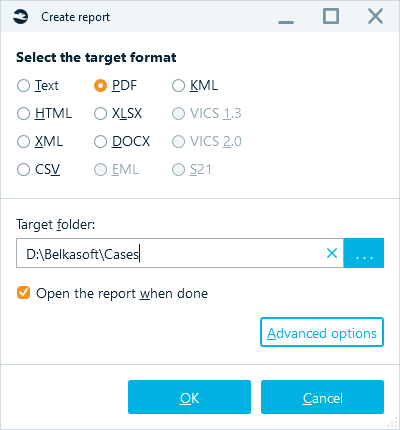
Figure 13. Choosing the appropriate format for a report in Belkasoft
With Belkasoft X the results of your work can also be exported to the standard Concordance load file format as well as Relativity Short Message Format (RSMF). You can then load the resulting file into any eDiscovery tool of your choice, including Relativity—and Belkasoft X, of course!
Typical use cases
The projected procedures and processes are often used in these scenarios:
- Certifying the contents of private chats.
- Establishing whether an email was actually received or sent.
- Establishing whether a document was modified on a specific computer and showing its editing history.
- Establishing whether a user performed a sequence of tasks on a computer.
- Establishing the fact that a user performed a sequence of tasks on a computer.
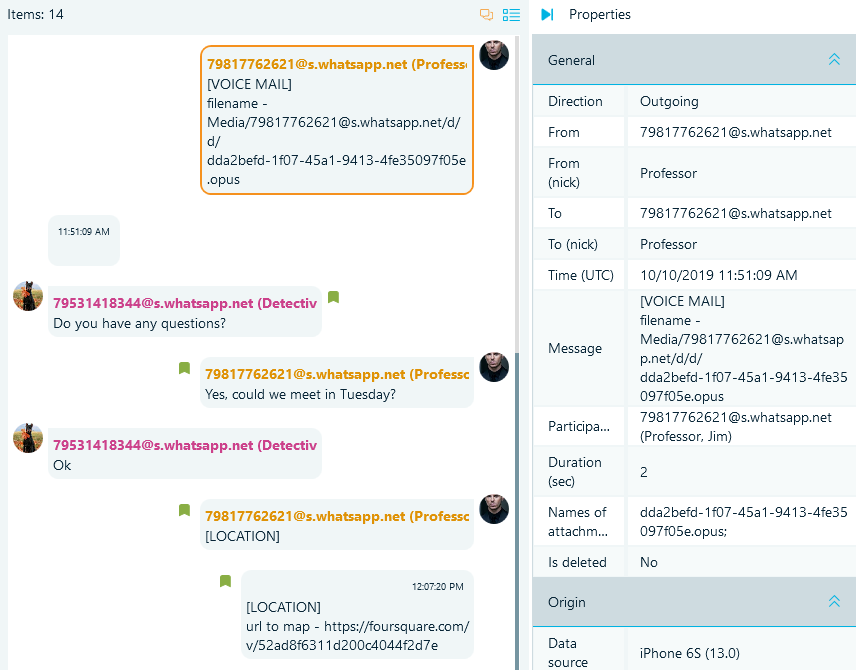
Figure 14. Using Belkasoft X to certify chats
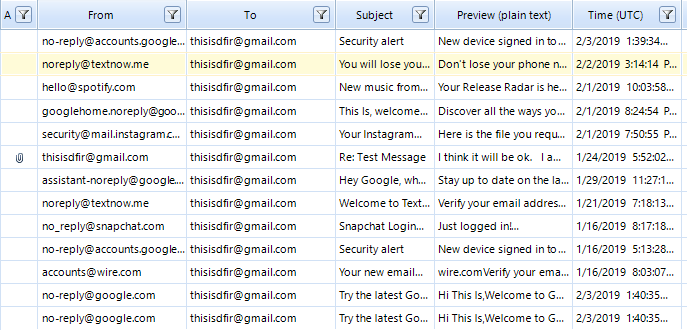
Figure 15. Emails presented in Belkasoft X
With Belkasoft, you can not only extract email data from various sources, but you can also instruct the tool to present the results of its analysis in a convenient layout.
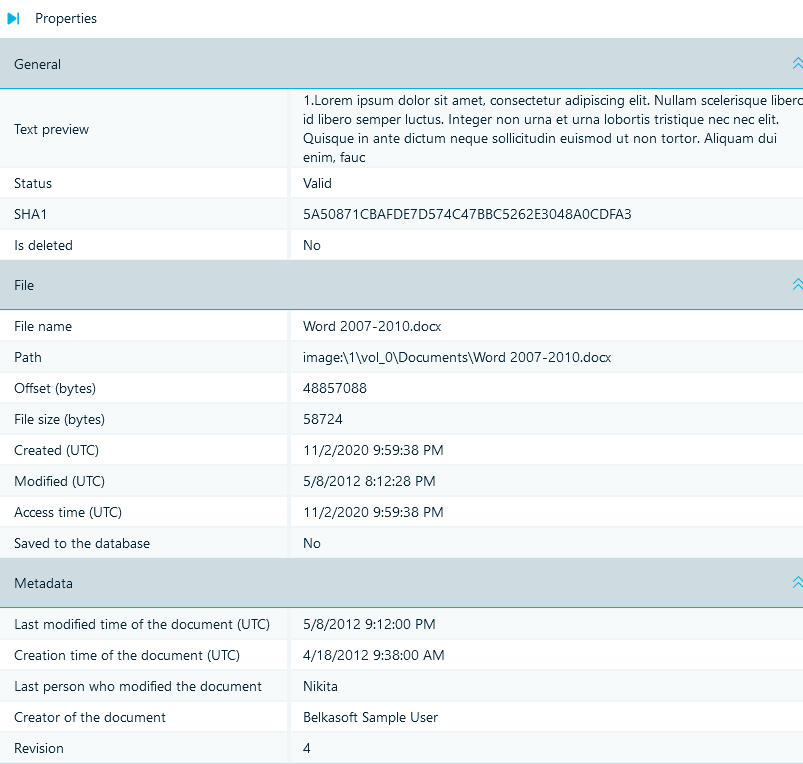
Figure 16. Analyzing a document's properties in Belkasoft
Belkasoft X provides comprehensive information on a document's metadata (data that lies within the file itself) and details on the metadata from the file system. With the file recovery function, a researcher can reconstruct events to events showing changes made to a file.
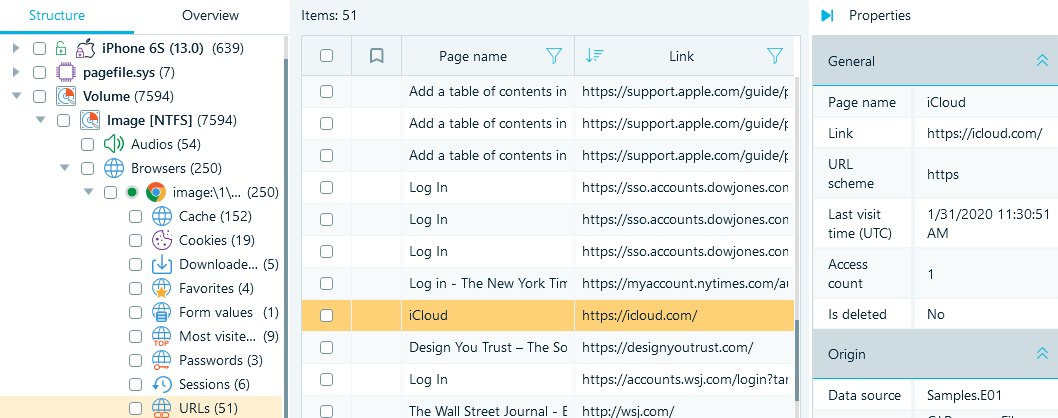
Figure 17. A user's browsing history presented in Belkasoft
Besides finding and presenting the users' browsing histories, Belkasoft X provides recovered web data, search queries, and clogged or broken items.

Figure 18. A user's timeline displayed in Belkasoft X
You can use the Timeline function to view a user history. This way, information corresponding to a user's activity can be presented as a graph or in a tabular format.
Conclusion
Advancements in technology have definitely created new challenges in terms of larger data volumes, increases in the complexity of information, and a wider range of evidentiary sources. Fortunately, computer forensics—through eDiscovery—can help researchers and investigators deal with the difficulties.
eDiscovery corresponds to a collection of tools, methods, and technologies that must be used in the correct manner to obtain optimal results. The identification, collection, processing, and production stages are the most important phases in any eDiscovery procedure.
It is imperative that technical specialists acquire sufficient knowledge and skills in eDiscovery. This way, they can effectively help clients and interested parties through the discovery process while arming them with necessary information, data and analysis points. The higher the level of understanding the better your chances to win cases and achieve the best legal outcomes.
With regards to the methods, processes, and events described in this paper, Belkasoft Evidence Center X is equipped with all the functionality a technical expert needs to conduct comprehensive research, like: collecting digital evidence, analyzing information, and then presenting the results in a court (or to a client).
Different organizations—especially law enforcement agencies, military and security bodies, and private firms—trust and use Belkasoft products. The results of research and forensics tasks conducted in Belkasoft X have repeatedly been accepted and used in courts as evidence.
