Belkasoft was extremely lucky to work on this article with Kevin Stenger, a digital forensic examiner who investigated the case of Casey Anthony.
BROWSER FORENSICS AND THE CASE OF CASEY ANTHONY
The case of Casey Anthony occurred back in 2008. Her 2-year-old daughter Caylee was first reported missing, and then half a year later, found dead.
The mother's behavior was suspicious from the very beginning and she was arrested the day after her child was reported missing.
What followed was called 'the social media trial of the century' by TIME magazine. The trial did not start for the case until almost two and half years later.
The trial lasted approximately six weeks and there were multiple items of physical evidence, but something was standing apart. It was electronic evidence: some browser searches, in which Casey allegedly made prior to the child's death.
Browser history analysis
The search terms were quite disturbing and included search terms used in Google for 'how to make chloroform' and 'neck breaking' among others. The prosecution supposed that Anthony used chloroform to make her daughter unconscious. The software, which was used for the computer analysis, also listed84 visits to a website which referenced making 'chloroform'.
Though Wikipedia states, with the reference to a TV channel that "police never investigated Firefox browser evidence on Casey's computer", Mr. Stenger witnesses that in fact it did.
The Firefox history data which this evidence was recovered from was located in unallocated space and could not be attributed to a specific user. The recovered history utilized a Mork database format which had not been used by Firefox for some time.The Mork format is considered to be inefficient and difficult to parse as the database gets larger.
Further complicating the examination of the computer was the fact that all the users in the household appeared to access the computer and user accounts. In addition the CMOS battery had been dead for an extended period of time. Users shutting down the computer and power failures from common Central Florida thunderstorms resulted in the date and time constantly being reset to the default. It also did not appear that the users made an effort to correctly set the date and time after it came back up.
Four separate forensic examination tools were used to try and examine the Firefox artifact. All four produced differing results. Among the software used for the analysis was a tool called 'CacheBack', and its author was an ex-law enforcement officer. CacheBack analyzed Internet Explorer history of the desktop computer, which was seized from Anthony's home and gave the result described above.
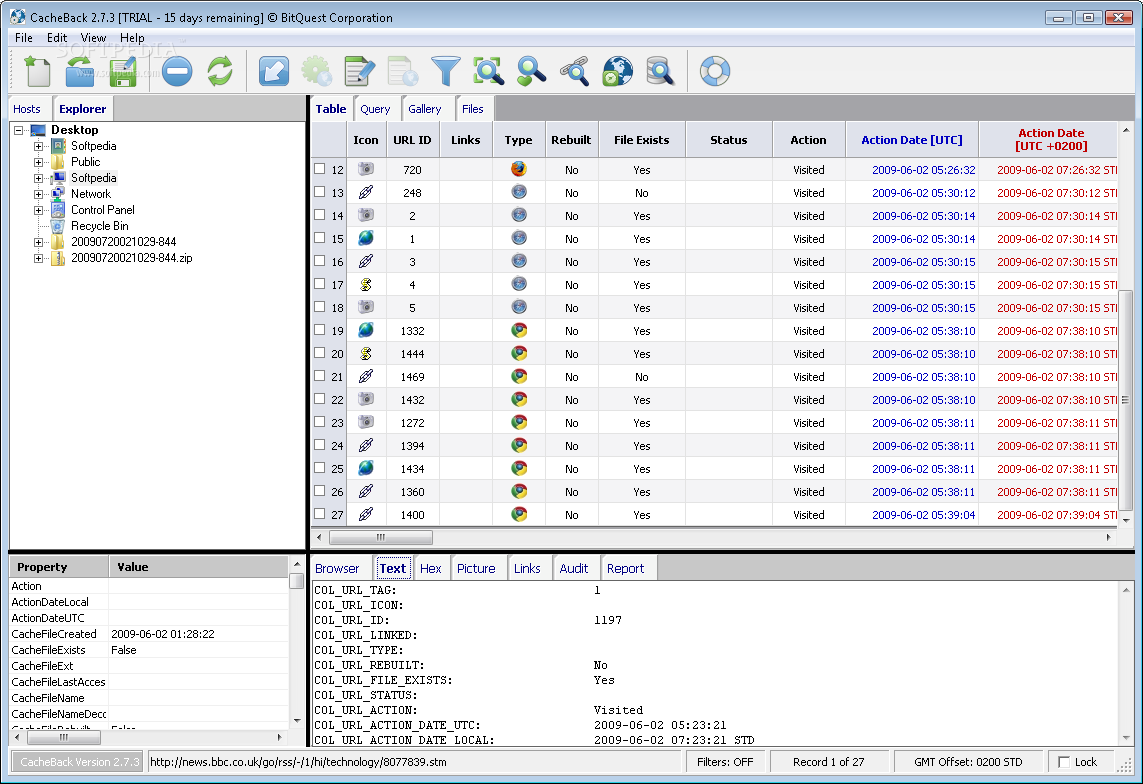
CacheBack user interface
A spreadsheet was generated with the results of the analysis of the Firefox artifact and provided to the Prosecution and Defense. The examiner after consulting with the Prosecution recommended not presenting the evidence of the 84 visits to the website since the analysis differed between all the applications on this point.It was decided to just present the search terms used in Google which did cross check with the other tools.
Examiners and the Prosecution agreed that the best course of action was to present the digital evidence which could be cross checked and verified and also was corroborated by physical evidence. In this case the air sample taken from the suspects vehicle which had a high concentration of chloroform.
During direct examination by the Prosecution the portion of the spreadsheet containing the Google searches was shown to the jury, judge and attorneys via display. This information was not visible to the visitors or media. The witness was questioned on the information presented. During cross examination by the Defense however the Defense attorney accidently presented to the jury the part of the spreadsheet containing the 84 visits to the website on making chloroform. The Prosecution on redirect then brought to the attention of the jury the 84 visit results that the Defense had accidently entered into evidence. At this point neither the Defense nor the Prosecution was aware that the number of visits to the site was in error.
Was Casey Anthony guilty?
After the conclusion of the case, News Media interviewed several of the jurors. They indicated that they could not come to a conclusion on a guilty verdict. While the digital and physical evidence that was presented suggested a number of different methods of possible homicide no actual cause of death was determined making all of the possibilities just theories without evidence.
The presiding judge was interviewed after his retirement and he concluded that the evidence presented indicated that the suspect had utilized chloroform on the victim but there was no evidence that the death was the result of a deliberate overdose or simple negligence/abuse.
Conclusions
Cross checking results is a vital part of any digital forensics exam. This case presents an interesting problem in what an examiner should do in the event that none of the forensic applications have results that cross-check each other.
Even if you have a preferred digital forensic tool and often rely on it, double check its results by using another digital forensic tool, or manually.
P.S.
Belkasoft is grateful to Mr. Stenger for his comments and contribution to fixing inaccuracies in the original version of this article.