iCloud Advanced Data Protection: Implications for Forensic Extraction
Introduction
Apple's iCloud service has long been a go-to platform for users to store their photos, documents, application backups, and more, which has also made it a valuable source of data for criminal and cybersecurity investigations. One big advantage it gives is the possibility to access user data even if the device is not available. At the same time, Apple is continually enhancing the security of iCloud data storage, which often poses challenges for data acquisition.
One significant development in this regard is the introduction of Advanced Data Protection (ADP) for iCloud in iOS 16.2. In this article, we are going to explore how it works and what it means for digital forensics examiners.
iCloud security in a nutshell
iCloud security starts with two-factor authentication (2FA), which Apple devices require to enable synchronization with iCloud. Once the user configures 2FA, iCloud, by default, enables standard data protection. What does it mean?
- The sensitive part of user data, including the keychain, health data, payment information, and so on, is end-to-end encrypted and can only be decrypted on trusted devices
- Other types of data like contacts, iCloud mail, calendars, and device backup data are only encrypted in transit and on the Apple server. However, Apple stores its encryption key as well, so it can be downloaded along with data and used to decrypt it.
When Advanced Data Protection comes into play, things get more complicated. To enable ADP, users need to take an additional step—generate a recovery key or assign a trusted contact that can assist in regaining access to iCloud data.
Now, when it comes to obtaining and decrypting iCloud data protected with ADP, a higher level of security is in place. Besides the user's Apple ID credentials and the 2FA verification code, the recovery key becomes a crucial requirement. In addition to that, with ADP, iCloud extends the number of protected types of data leaving out only iCloud mail, contacts, and calendars (as of iOS 16.6.1).
iCloud data acquisition in Belkasoft X
After checking the ADP specifications on Apple's website, we decided to test this feature to verify if there is a chance of extracting any information at all when it is enabled.
We began with updating our test iPhone 12 to the latest version (a requirement for ADP) and synchronizing it with iCloud. Our next step was to acquire a control sample of data with Belkasoft X.
The product provides the ability to acquire two parts of iCloud data:
- iCloud app data, including iCloud mail, calendars, media files, and other data accessible when logging in to Apple account on icloud.com
- iCloud backup, containing the data required to restore an Apple device: system files, settings, iMessage chats, data from iOS and other applications using iCloud for backup storage (e.g., WhatsApp and Viber), and more.
We acquired both of these parts and then proceeded to enable ADP on the phone, choosing to use a recovery key for securing data.
Next, we initiated the iCloud part acquisition. After we selected the necessary options and provided the Apple ID credentials in Belkasoft X, the device displayed a notification to confirm the login into the iCloud account— a good sign. We entered the 2FA code, and Belkasoft X began downloading iCloud data. After analyzing it, we compared the number of artifacts to the non-ADP control sample:
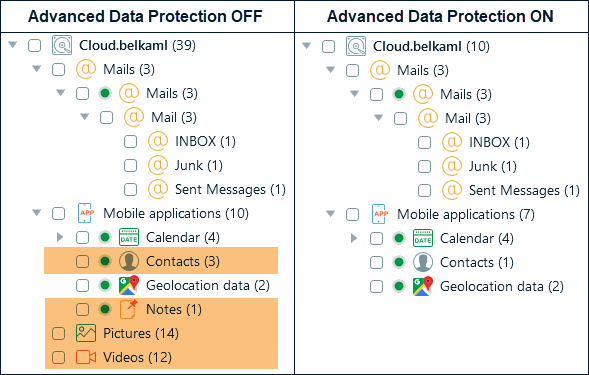
We observed that, indeed, notes and media files were no longer present. However, the iCloud mail account, calendar, and geolocation data remained accessible. As for contacts, only the device owner's contact was acquired.
But what about the iCloud backup data? Unfortunately, no good news here. Belkasoft X currently cannot handle this part of iCloud storage acquisition when ADP is on.
What can you do about Advanced Data Protection?
As you see, even with ADP enabled, you can still extract a few artifacts from iCloud, however, most valuable data is inaccessible. It seems like, at this point, the only way to deal with iCloud ADP is to disable it within the device settings. This process does not require providing the recovery key—only the device passcode.
As long as you have the device and its passcode, you can also acquire its data through iTunes backups, which ADP does not impact in any way—we have verified this as well, just in case.
