Belkasoft Evidence Center X v.1.11 was tested for its ability to recover data stored in SQLite databases, under the CFTT (Computer Forensics Tool Testing) program by DHS and NIST.
The report has recently been published on the Department of Homeland Security website.
The general conclusion of the test was positive. The report states that "All test cases were successful" with a small number of exceptions. These exceptions include:
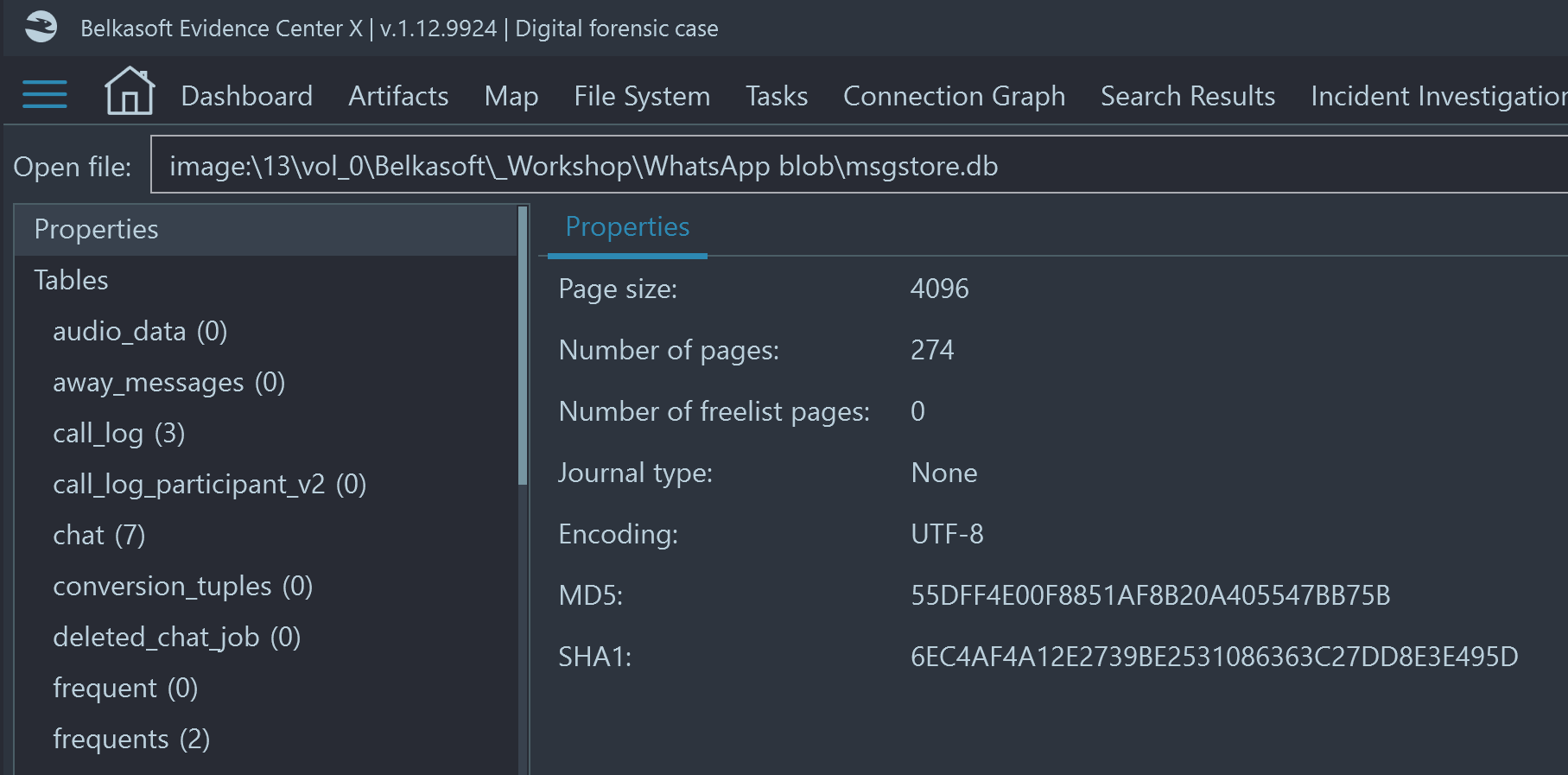
- Header related information (i.e., page size, journal mode information, number of pages, and encoding) are not presented in the SQLite viewer
- The status of records that have been deleted or modified are not specified by the tool as "deleted" or "modified" records
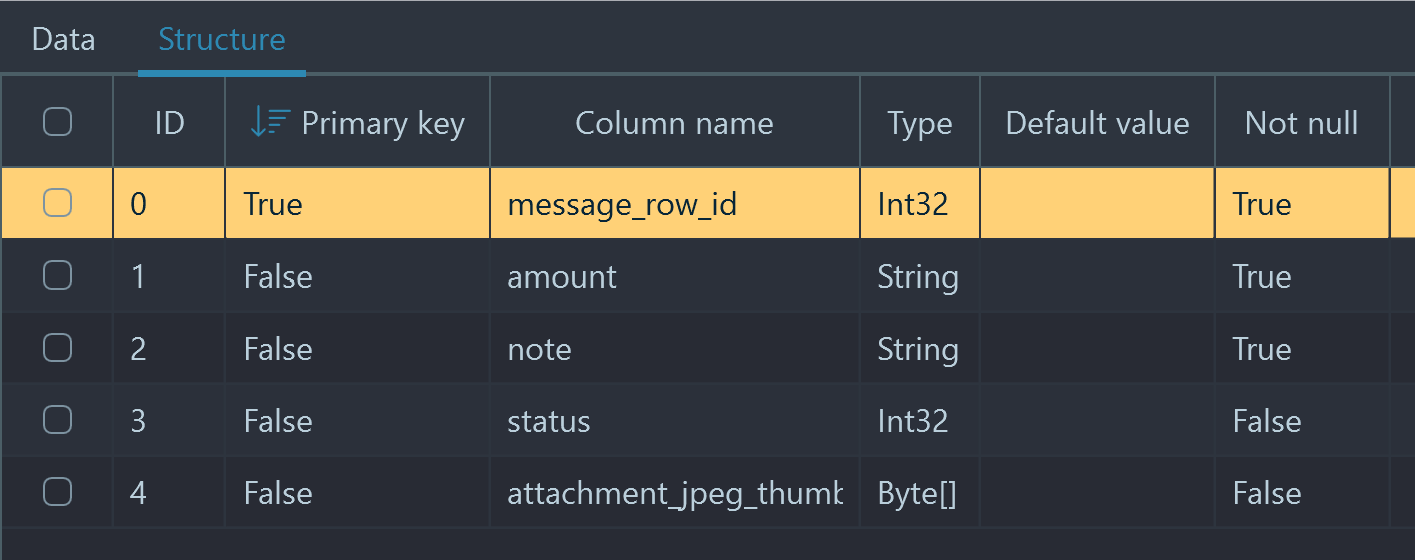
- The type (i.e., Primary Key, Int, Float, Text, BLOB) of individual items within a record are not reported
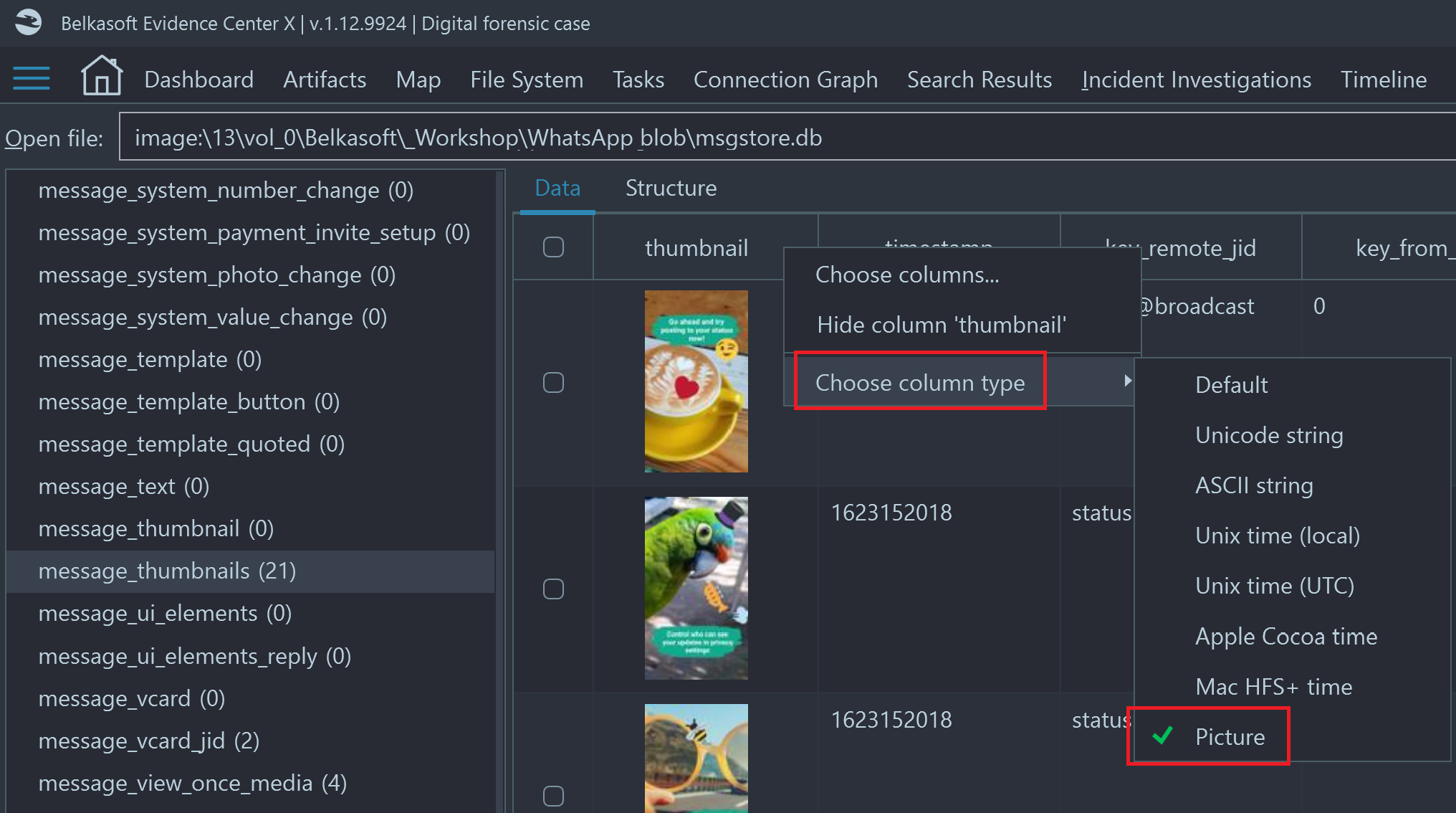
- Binary Large Object (BLOB) data containing graphic files are not displayed
- The recovered row and table name are not reported for deleted records that have been recovered
Belkasoft worked intensively to address the issues pointed out by the reviewer. In the versions of Belkasoft X, following v.1.11, we fixed the above-mentioned issues and added new features to cover lacking functionality. Updates include:
- The built-in SQLite Viewer now contains Properties element, that displays page size, journaling type, page number and encoding:
- The inability to show Column types was an unfortunate bug in the tested version. This feature was supported in the very first version of the product and was fixed in the v.1.12:
- We added support for BLOB data types containing images. You can now review such images by using "Picture" in the "Column type" menu. On the screenshot below, there is an example of a BLOB stored in a WhatsApp database:
- We added the "Row id" for convenience and easier navigation. However, the table name was actually available for the recovered deleted record. The product shows recovered records under the table, which a record was recovered for
The only issue, that has not yet been addressed is showing whether a record was deleted or modified. This applies to journal records only (freelist items are always "deleted").
Belkasoft was happy to work with NIST to improve our digital forensic software for the DFIR community.
About Belkasoft X Platform
The Belkasoft X Platform helps customers to analyze mobile and computer devices and acquire cloud data in the course of a digital forensic investigation or a cyber incident response case. You can effectively triage a running computer or a desktop to quickly locate data of interest under the pressure of time. Malicious code trails and intrusion attempt traces can be easily discovered in the case that your Windows-based network is compromised. With the Belkasoft X Platform, you can acquire remote computers and even mobile devices—without painful re-configuration of your network.
About Belkasoft
Belkasoft is a US-based company with headquarters in California. Belkasoft is a global leader in digital forensics and incident response software. Our products helps customers in over 130 countries to solve digital forensic cases, respond to cyber incidents, conduct eDiscovery investigations and protect precious business assets from cyber threats.
About CFTT
The Computer Forensics Tool Testing (CFTT) program is a joint project of:
- The Department of Homeland Security (DHS) Science and Technology Directorate (S&T)
- The National Institute of Justice
- The National Institute of Standards and Technology (NIST) Special Programs Office and Information Technology Laboratory
CFTT is supported by other organizations including:
- The Federal Bureau of Investigation
- The U.S. Department of Defense's Cyber Crime Center
- The U.S. Internal Revenue Service's Criminal Investigation Division Electronic Crimes Program
- The DHS Bureau of Immigration and Customs Enforcement
- The U.S. Customs and Border Protection
- The U.S. Secret Service
The objective of the CFTT program is to provide measurable assurance to practitioners, researchers, and other applicable users that the tools used in computer forensics investigations provide accurate results. Accomplishing this requires the development of specifications and test methods for computer forensics tools and subsequent testing of specific tools against those specifications.
