iOS Telegram Forensics. Part II: Artifacts, Secret Chats, Cache, Deleted Messages
Manual decoding of the iOS Telegram database is undeniably a tedious task, and with a large number of records, it can take a very long time. For this kind of application, a digital forensic tool becomes indispensable.
In this article, we will explore how Belkasoft X can help you streamline iOS Telegram forensic analysis and look into the pitfalls to avoid when interpreting Telegram data. Here is what we will cover:
- Analyzing iOS Telegram artifacts
- Working with Telegram secret chats
- Dealing with cached data
- Recovering deleted and edited messages from the iOS Telegram database
Analyzing iOS Telegram with Belkasoft X
When you add an iOS device image as a data source to a case in Belkasoft X, you can set up the analysis options to only examine Telegram data:
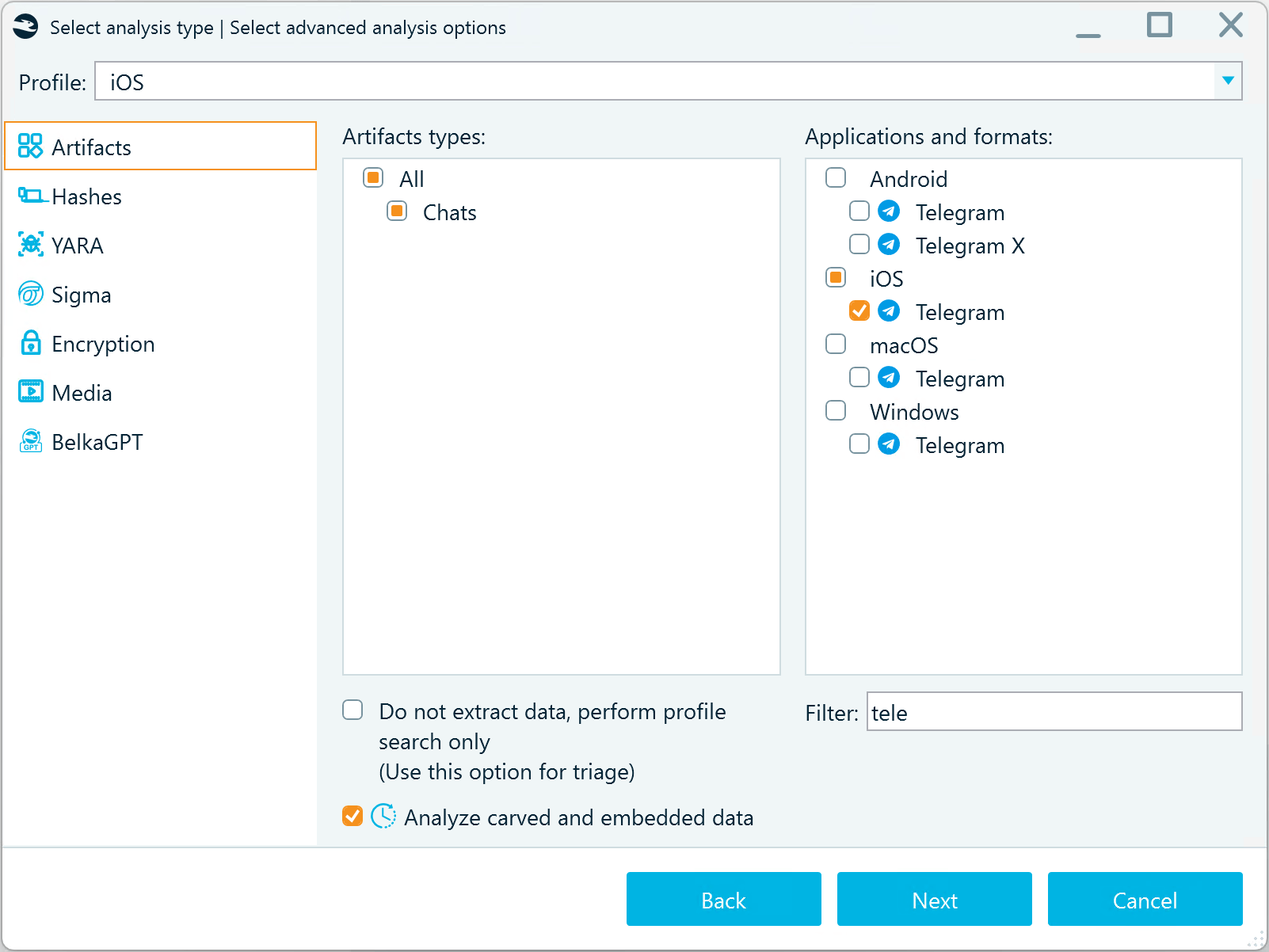
Figure 1: iOS Telegram profile selected for analysis in Belkasoft X
After the tool analyzes the files in Telegram folders, it presents extracted findings in the Artifacts window. In the Structure tab, the Chats → Telegram profile displays the account owner’s name and numeric ID in the database. The middle pane reveals the user’s sent and received messages in the bubble chat view:
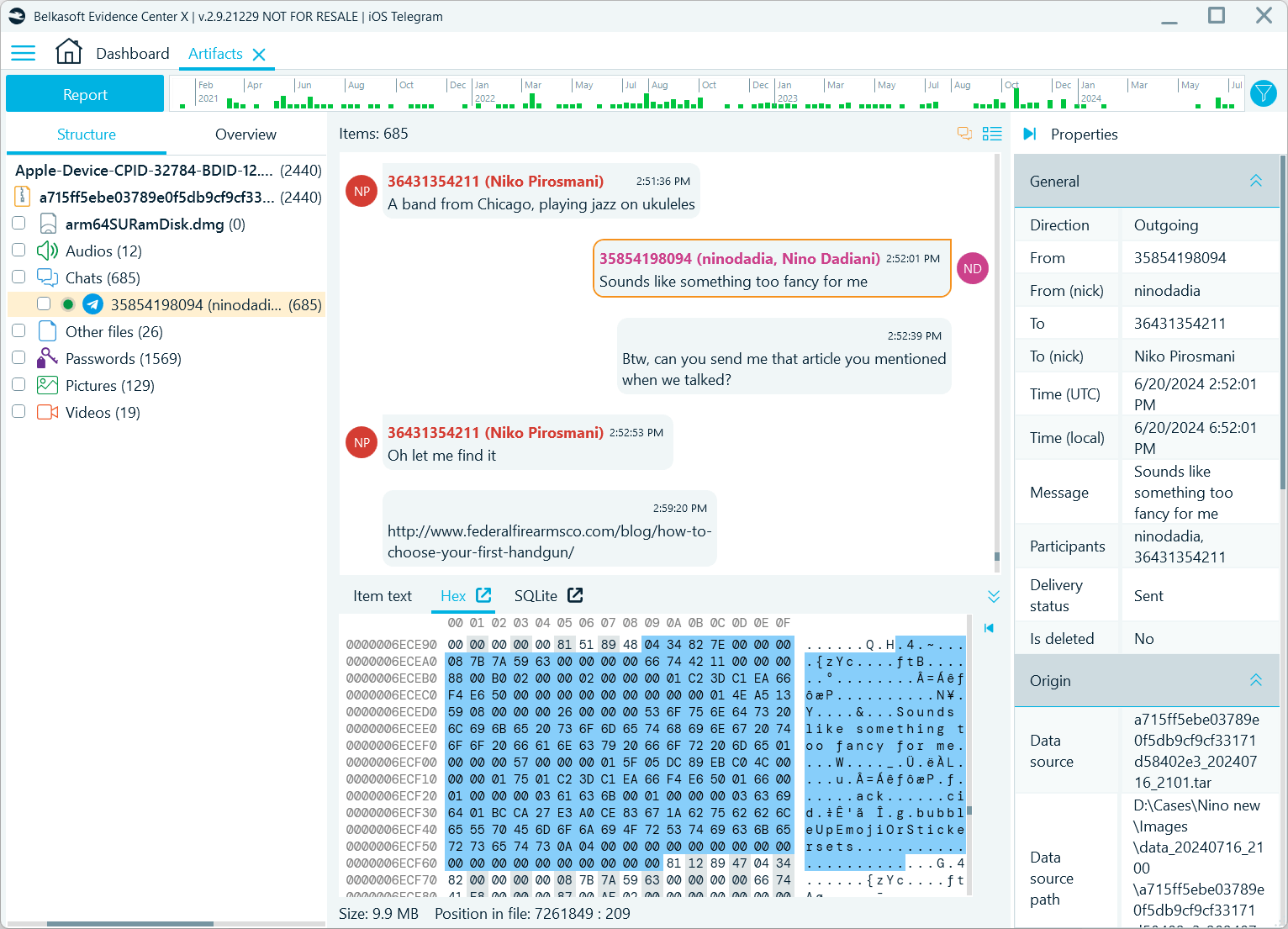
Figure 2: The Artifacts window displaying Telegram messages in the bubble chat view
You can select a message and then inspect its details in the Properties pane. If you want to view the source binary data record from which the message originates, you can find it highlighted in the Tools pane → Hex viewer tab.
Filters
To narrow your search, you can switch to the grid view and apply various filters. For example, you can select a date range of the messages to display:
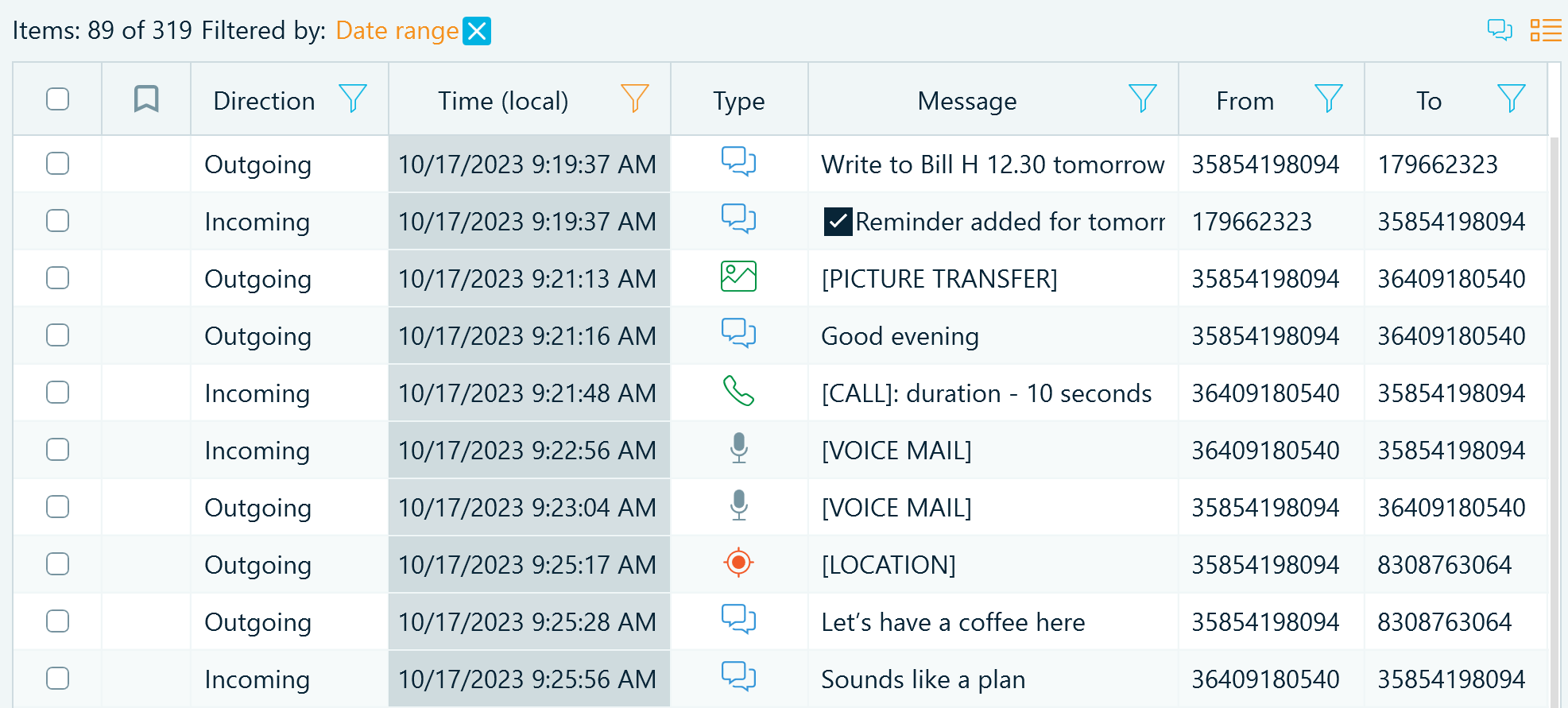
Figure 3: Telegram messages filtered by a date range in the grid view
Attachments
While analyzing a Telegram database, Belkasoft X identifies the types of data exchanged in the messages and marks the records accordingly. Messages with attachments may include pictures, audio and video files, and other types of documents. You can view their details in the Properties pane and access shared files in the Tools pane → Attachments tab.
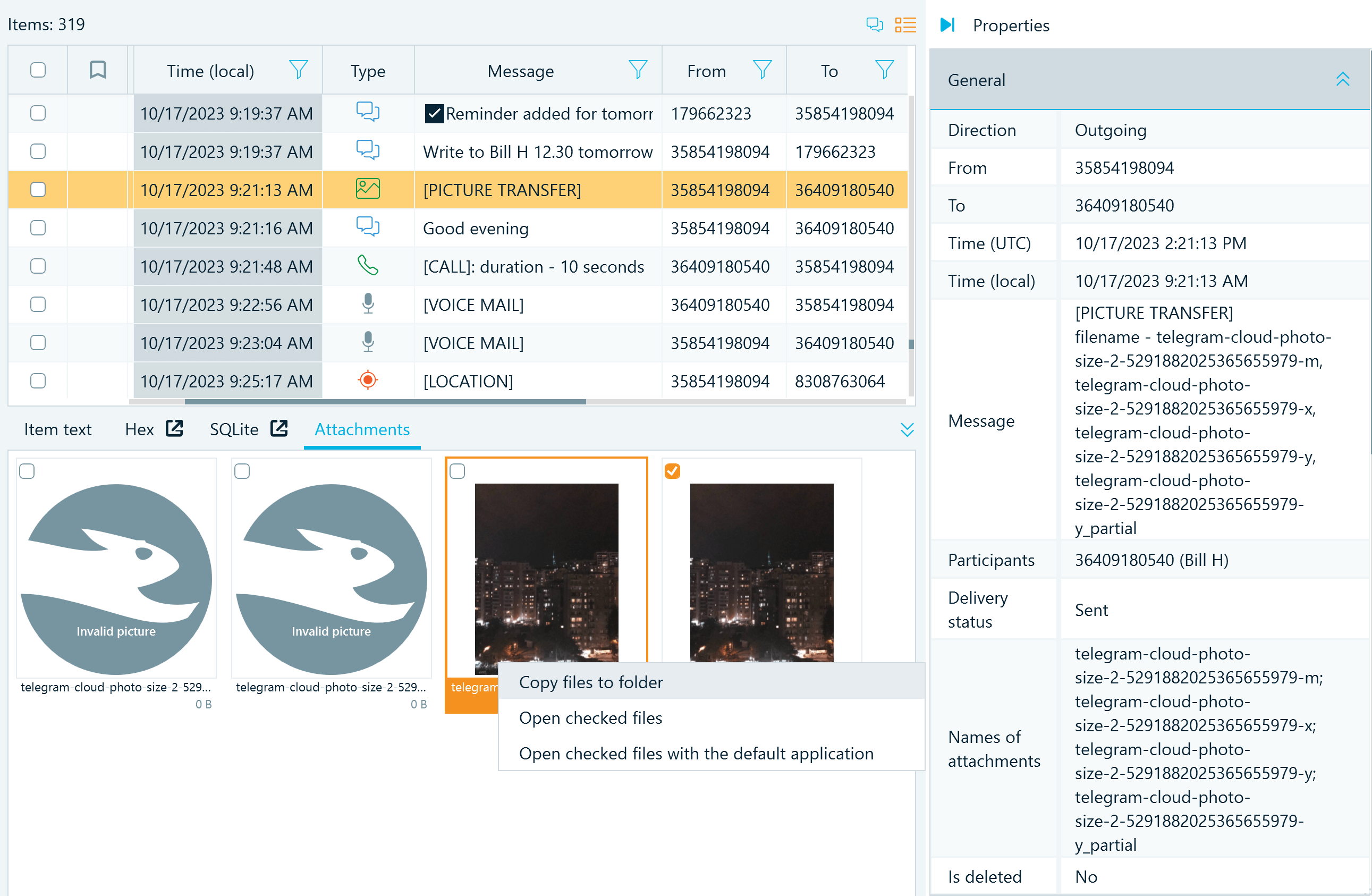
Figure 4: Telegram message attachments displayed in the Artifacts window
Note that some attachment files may not be available if they had been cleared from the application cache before you acquired the device image.
Chats
By default, the Artifacts window displays messages from all user’s Telegram chats in one window. If you want to look into each available chat individually, in the Structure tab, right-click the Telegram profile and select Show contacts:
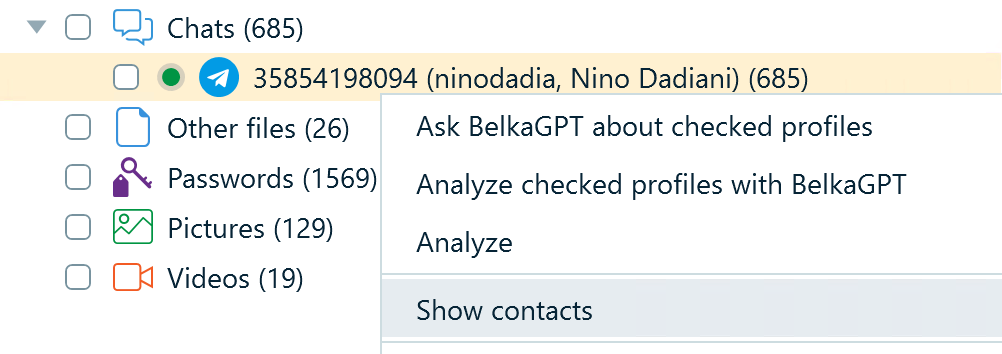
Figure 5: Configuring the Telegram profile to show individual chats
The tool then displays the conversations available in the database. Channels and group chats are marked by the corresponding tags, while one-to-one chats and bots are displayed together with associated names if they are available:

Figure 6: Viewing Telegram user’s chats individually
The chat nodes that do not include user details are typically either secret chats or chats with deleted accounts.
One notable chat to explore when analyzing Telegram data is the user’s chat with themselves (typically marked in the iOS Telegram app as “Saved Messages”). In Belkasoft X, you can spot it by the same number as the numeric ID of the Telegram profile:
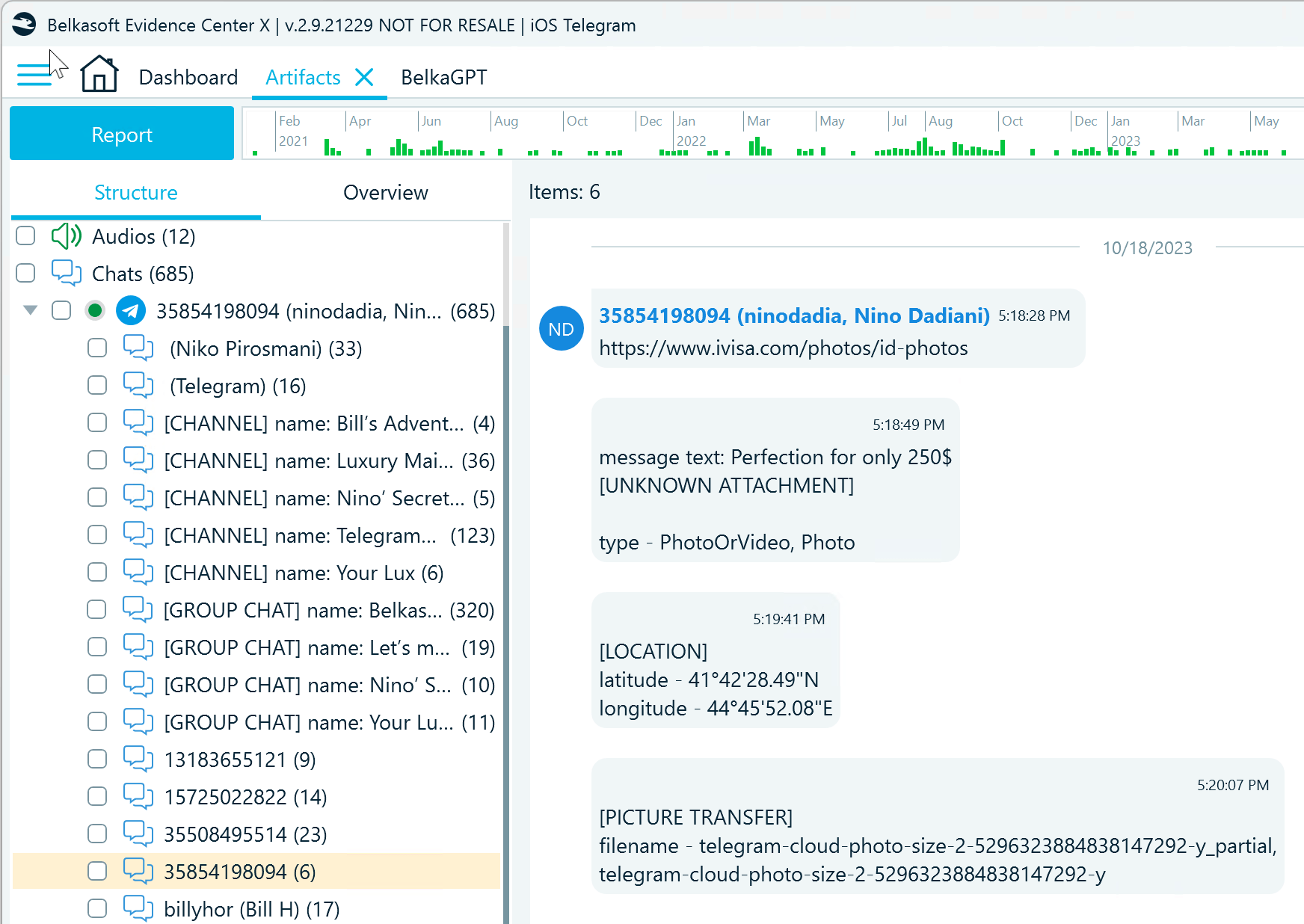
Figure 7: A Telegram user’s “Saved Messages” chat presented in Belkasoft X
For Telegram users, this chat often serves as a storage for important messages, files, links, and more, so it may contain valuable information for the investigation.
Working with Telegram secret chats
Telegram secret chats are only available on the devices where they were initiated. Such chats are end-to-end encrypted while in transit between devices; however, devices store them in an unencrypted form.
Telegram database keeps each secret chat under a separate ID number. In Belkasoft X, they look essentially the same as other one-to-one chats, with the only difference being that the details of the sender do not display in the tree view. When analyzing such secret chats, Belkasoft X identifies the name of the sender and displays it in the chat view:
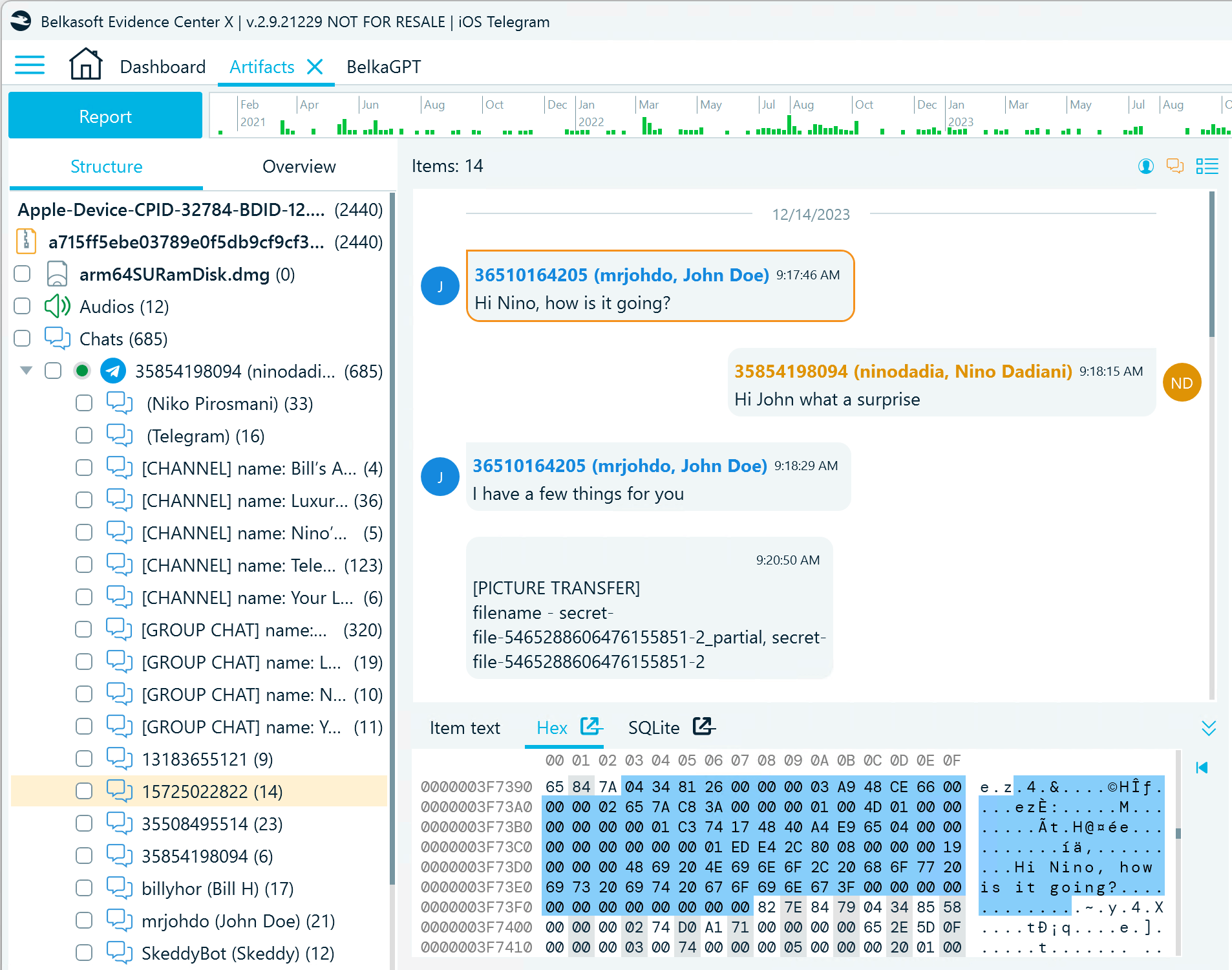
Figure 8: A message in a Telegram secret chat
Dealing with cached Telegram data
Telegram has a "global search" function that enables users to discover other users or groups and channels within the platform.
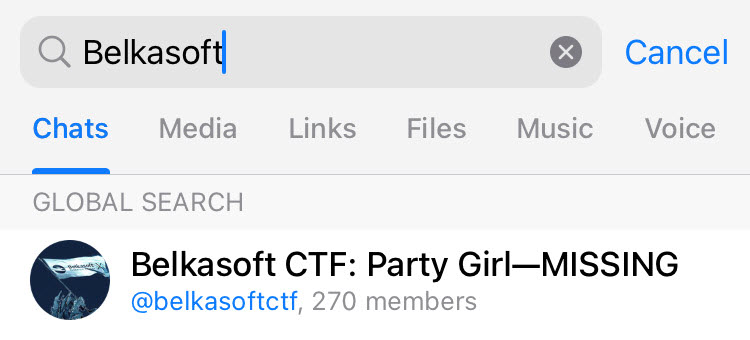
Figure 9: Global search in iOS Telegram
When a user enters keywords in Telegram’s Search field, the application displays related results and caches them to the t2 database table even if the user does not interact with the displayed accounts. This way, when you analyze a database, it may reveal names of accounts, groups, and channels that have nothing to do with the user and are not visible on their device.
For example, when examining the contact list below, you can find a number of accounts that are not part of the user’s chats on the device. Many accounts cached from the search results have no messages within the database, which is indicated by the (0) next to them. However, if the user has opened channels or groups, their messages and media files are cached and end up on the device, as it happened with the BestLuxury_bags channel in the below example.
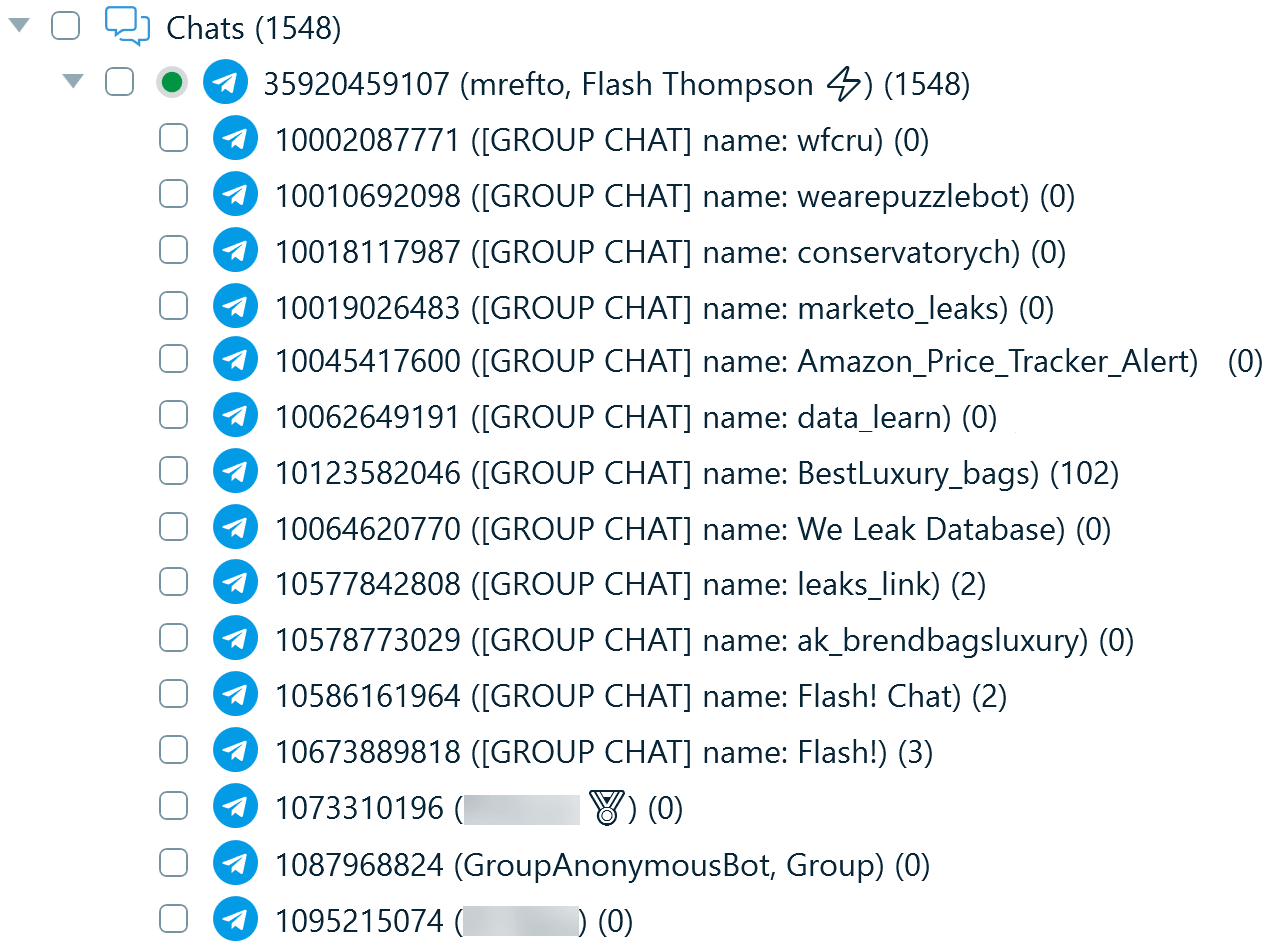
Figure 10: Cached accounts parsed from an iOS Telegram database
Cached accounts and messages in a Telegram database may cause confusion about the device user’s interaction with users, channels, and groups. You should be careful when making conclusions based on data from the device image only, and if possible, check the application within the device or the account data acquired from the cloud to corroborate your findings.
Recovering deleted and edited messages from the iOS Telegram database
A research on how well DFIR tools support various communication applications revealed that none of the tools could recover a deleted Telegram message from an iOS 15 image. Based on our observations, the possibility to recover deleted data in Telegram exists, but it depends on the iOS version of the device and on how soon after deletion you can acquire the application database.
iOS Telegram uses the SQLite database format to store and process its records. This format has several features that manage record deletion, and we can spot three of them in the iOS Telegram database: freelists, write-ahead logs (WAL), and unallocated space.
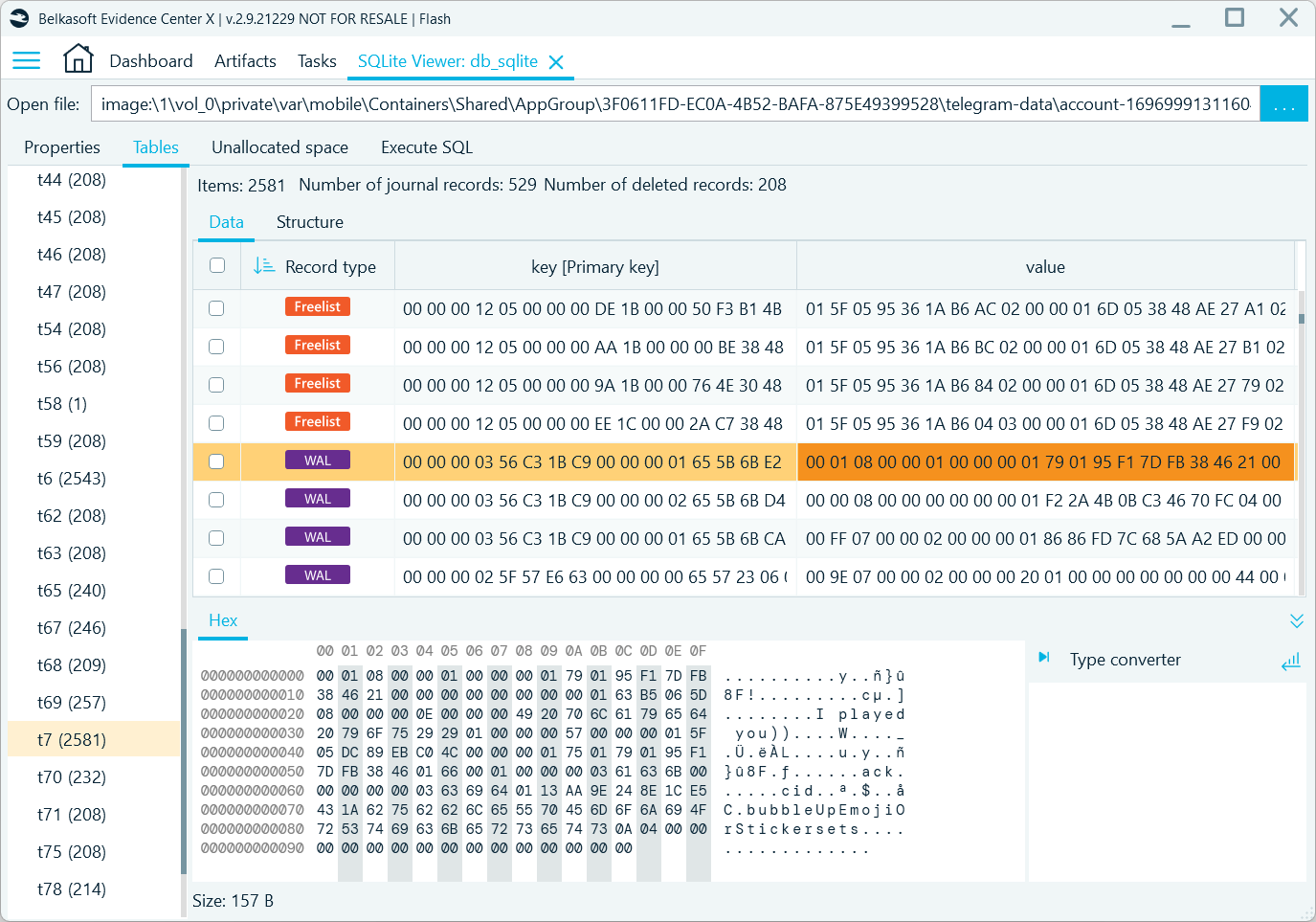
Figure 11: Freelist and WAL records in db_sqlite
We have covered how these features allow you to recover deleted data in the article "SQLite Forensics with Belkasoft X." In a nutshell:
- Freelists and unallocated space store recently deleted records within a database until a system event wipes them
- Write-ahead log is a transactional file that captures all changes that happen to records in a database; at a certain point, the system commits the latest state of the records to the main database and deletes this transactional file
You can typically find Telegram’s deleted and edited messages in WAL records if you can obtain the database before the system wipes them. Let us explore an example conversation with deleted and edited messages:
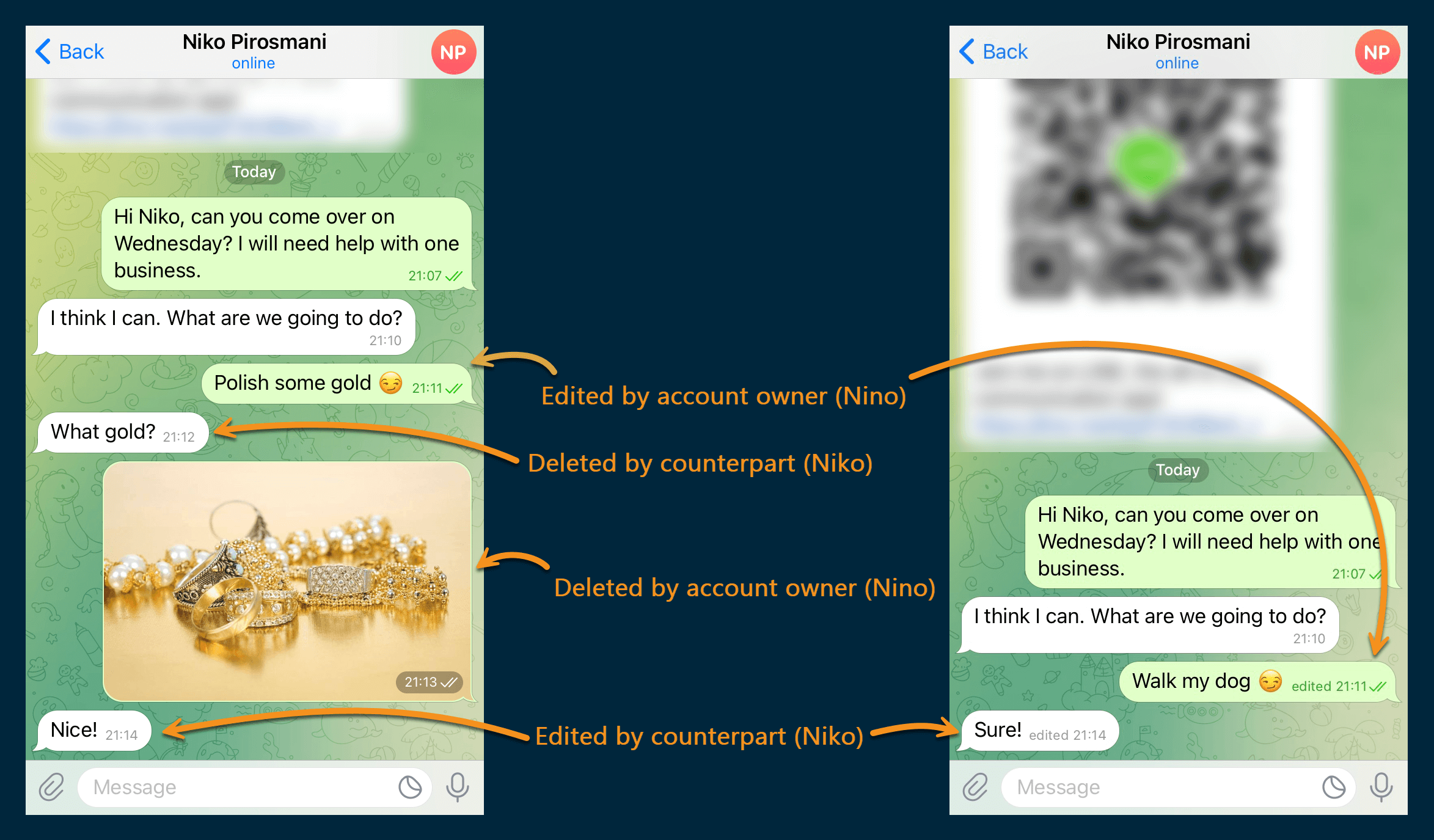
Figure 12: A test Telegram chat with deleted and edited messages
When inspecting this chat in Belkasoft X, you can find all the original, edited, and deleted messages:

Figure 13: Deleted and edited Telegram messages recovered by Belkasoft X
The possibility of recovering deleted iOS Telegram messages is based on how the database is set up. Its settings may depend on the application configuration and iOS version on the device where it is installed. Based on our observations, deleted records from one-to-one and group chats stay within the application database from about one hour to a couple of days, while those deleted from secret chats cannot be recovered at all.
Conclusion
The complex storage structure of the Telegram app makes analyzing its data from iOS devices a challenging task. That is why using a powerful DFIR tool like Belkasoft X is essential for both acquiring and thoroughly examining Telegram data.
Data extracted from an iOS device can reveal much more than what is available in Telegram’s cloud storage. This includes sensitive information such as encrypted or “secret” chats and traces of deleted messages. However, investigators should handle residual cached data carefully, as it may not always reflect the app data on the device accurately. To achieve a complete and reliable analysis, it is best to use a multi-source approach to data acquisition and examination.

