Belkasoft CTF 6: Interview with the Winner
The first weekend of April was a bustling time for over 600 digital forensics specialists worldwide. These enthusiastic professionals and students took part in Belkasoft's sixth Capture the Flag (CTF) contest, dubbed "Bogus Bill," featuring 18 challenges within a 48-hour timeframe. The first winner emerged in under 24 hours, and it was quite an impressive result considering the second winner was able to complete all CTF challenges just before the deadline.
We interviewed its5Q, the winner of the sixth BelkaCTF, to find out how he beat the other contestants by such a large margin.

What are you currently studying?
I'm currently finishing my local college in the field of programming/computer science. Honestly, it didn't give me much in terms of knowledge, and all the stuff I do now is basically self-taught, but it doesn't hurt having some sort of a degree.
Do you prefer digital forensics (DF) or incident response (IR)?
I am not sure yet, but I think I prefer digital forensics to incident response. As I understand, digital forensics is more about analyzing and extracting information, and incident response is more about threat isolation and mitigation, and it often involves quick decisions on the amount of stealth when working on data extraction and more stuff like that. Most often DF and IR work in tandem, and I think I want to be on the side that works on collecting and analyzing evidence.
How often do you participate in Capture The Flag (CTF) competitions? We were amazed at how you managed to overtake other participants by an entire day! Typically, we see only a few hours' difference.
Quite often, in fact, at the same time BelkaCTF was taking place, I was participating in the quals stage for a local CTF that took place on the 6th of April with a team of my friends, and we qualified too. It was difficult juggling two CTFs at the same time, but I mostly focused on Belka. I've got some CTFs I participated in on my GitHub readme, but that list is far from complete, those are just the ones that feel more important to me because I had more involvement in solving them. I'm currently part of an academic team BinaryBears and I occasionally participate in CTFs with them too. So, my guesstimate would be about once a month, but I've been more active in the past several months.
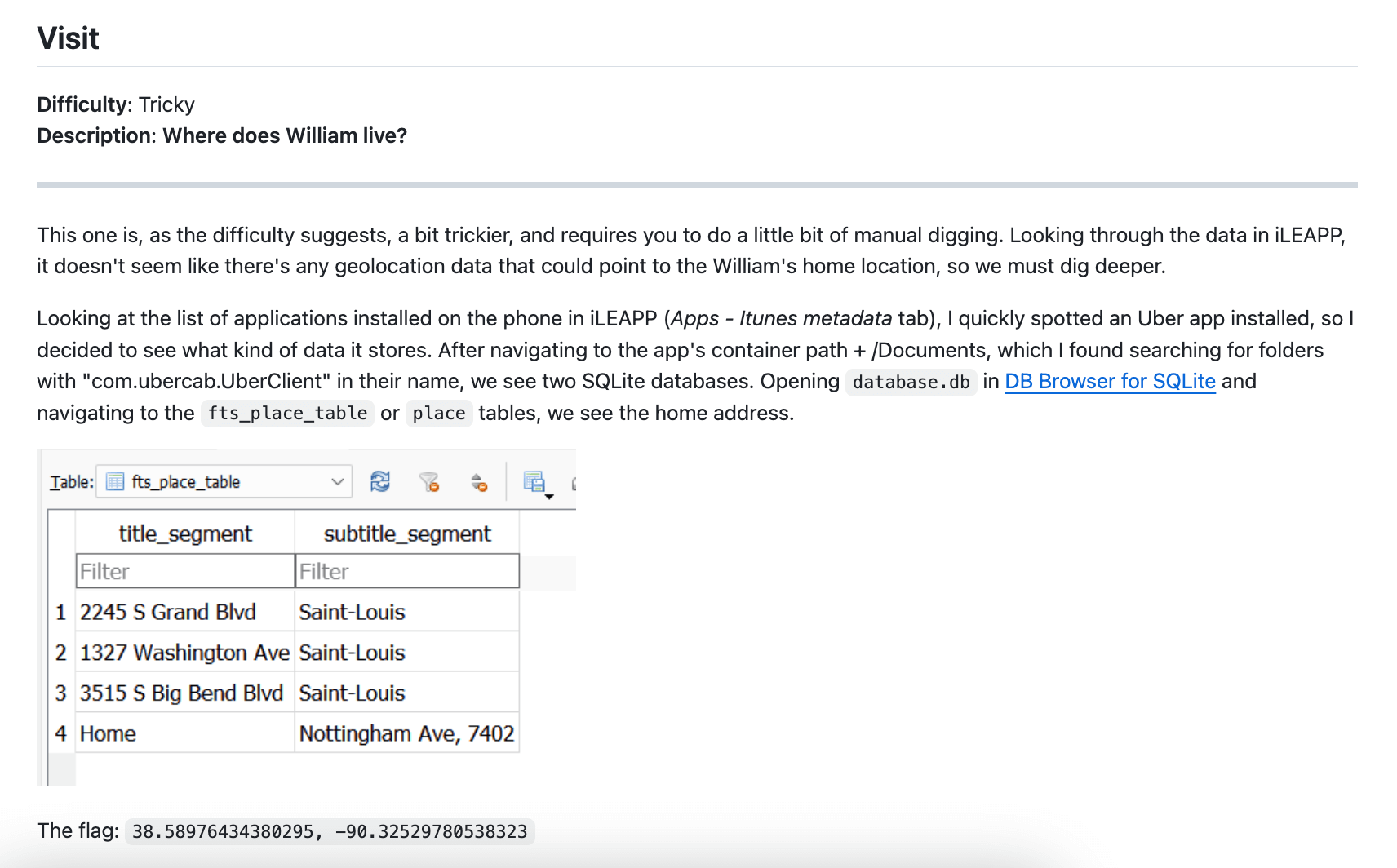
A variant solution to one of the tasks from its5Q. See the
full version of the write-up by the winner
on
GitHub.
Can you share your thought process while solving the CTF challenges?
For me, when starting to work on a challenge, the path to a solution is often obvious the moment I look at the description, or, in the case of web challs, the web pages. When I work on challenges, I try not to spend much time on a single challenge, and if I feel like I'm stuck, I just switch to another one while it sits in the back of my mind, and when I eventually come back to it I have come up with some theories on what the solution might be.
How did you feel after solving all the tasks?
I felt awesome knowing I came out on top with hundreds of people competing. And a bit of relief, as I had put in a lot of hours, and I had a good rest after the CTF. I would say it was the most fun I had in a CTF.
Why do you think you were so much ahead of the other players? Which of your skills or strategies helped you the most?
I think generally, not focusing too much on a single challenge helps tremendously in CTFs, and that was especially true for Belka, as all the challenges are mostly interconnected, so it's often you stumble across a solution to a different task than the one you were working on. So, my approach was not to focus on the single tasks but rather to extract as much information as I can from what I have, and then figure out how I can use that information at hand to get to solutions. And, of course, hyper-focusing on the CTF helped a lot too, I don't think many people put in the amount of hours that I did into this CTF. It was probably about 12-14 hours in total actively digging into the images if I had to guess, but I'm not sure, I get lost in time a lot :)

Many of your competitors were seasoned digital forensics professionals. How did it feel to outperform them?
I felt very proud of myself. It was my first forensics-only CTF, and my previous experiences with forensics were from generic CTFs, which don't feature forensics challenges as much, and many of them lack quality and polish. But despite that, it was still the category I went into first, before any other, if it was featured in a CTF, and I had great success solving them. I was still not sure how I'd do in BelkaCTF, but I've tried my best and I had learned that I'm very good in forensics.
Could you share a funny story from your life?
Not many specific stories come to mind, so let's go with this one. Once, we gathered with a bunch of friends to try to bake a cake. None of us knew how to cook, but we just went with a random recipe we found online that looked good. The cake ended up being almost as hard as a rock, when, in fact, it was supposed to be quite soft. It was extremely hard to even get a spoon in it, and we've got a funny picture of a spoon standing upright stuck in the cake just one or two centimeters deep. But regardless, it tasted good, and we all had a very good time together playing some board games while it was cooking.
Are you open to job opportunities? We're confident that many cybersecurity companies would love to have a specialist like you on board.
Yeah, I'd be happy to review any remote job opportunities available. I'm currently a bit busy with my final year of college, so I will be completely free around late August/early September.
The sixth BelkaCTF was held from April 5 to April 7, 2024. Participants had only 48 hours to solve the challenges, but now you can download the images and tackle the problems at your own pace. If you need help finding solutions, do not hesitate to consult the official write-up.
If you are a student interested in digital forensics and cybersecurity, join our academic education program.
We look forward to collaborating and advancing the field of forensics together. Stay tuned for our next CTF!
