Belkasoft CTF 6: Write-up
The sixth BelkaCTF was held from Apr 5 to 7, 2024. The competition commenced at 3 PM CEST on the 5th and spanned 48 hours. The CTF page was https://belkasoft.com/belkactf6/ with tasks prepared by the Belkasoft and TODO: security teams.
This official write-up explains how the tasks were
intended to be solved using Belkasoft X.
While there are various methods
to tackle these challenges,
we encourage reading the contestants' own write-ups.
Importantly, every task could
be solved without the Belkasoft X product, so
lack of access or issues with the trial version should not have stopped
anyone from finding correct answers.
In this write-up we will focus solely on solutions utilizing the Belkasoft
X tool, wherever possible. Contrary to previous CTFs' write-ups, we will not
discuss solutions using third-party
tools, as many participants will likely share their insights on those.
Did you like this CTF? Share your feedback on your social networks using the tag #BelkaCTF.
The Plot
The CTF plot develops around a seemingly dull and insignificant incident. A cashier at a corner shop received a fake $50 bill and reported it to the police. Given the absence of other intriguing cases (it seems like you are working in a happy community!) your boss wants you to uncover what happened. Quite unexpectedly, your investigation leads to some significant findings.
Will you be able—using digital forensics only—to expose a well-organized gang involved in counterfeit currency crimes?

Let's begin taking flags!
1. Ident (Baby)
Question
What is the Apple ID used on the imaged iPhone?
Solution
- Open your Belkasoft X v.2.4
- Create a new case and add the first CTF image as a data source (at this point you do not have the password for the second image, so just disregard it for now)
- Analyze the image, selecting all artifacts for extraction
- Navigate to Artifacts → Overview → iOS Accounts
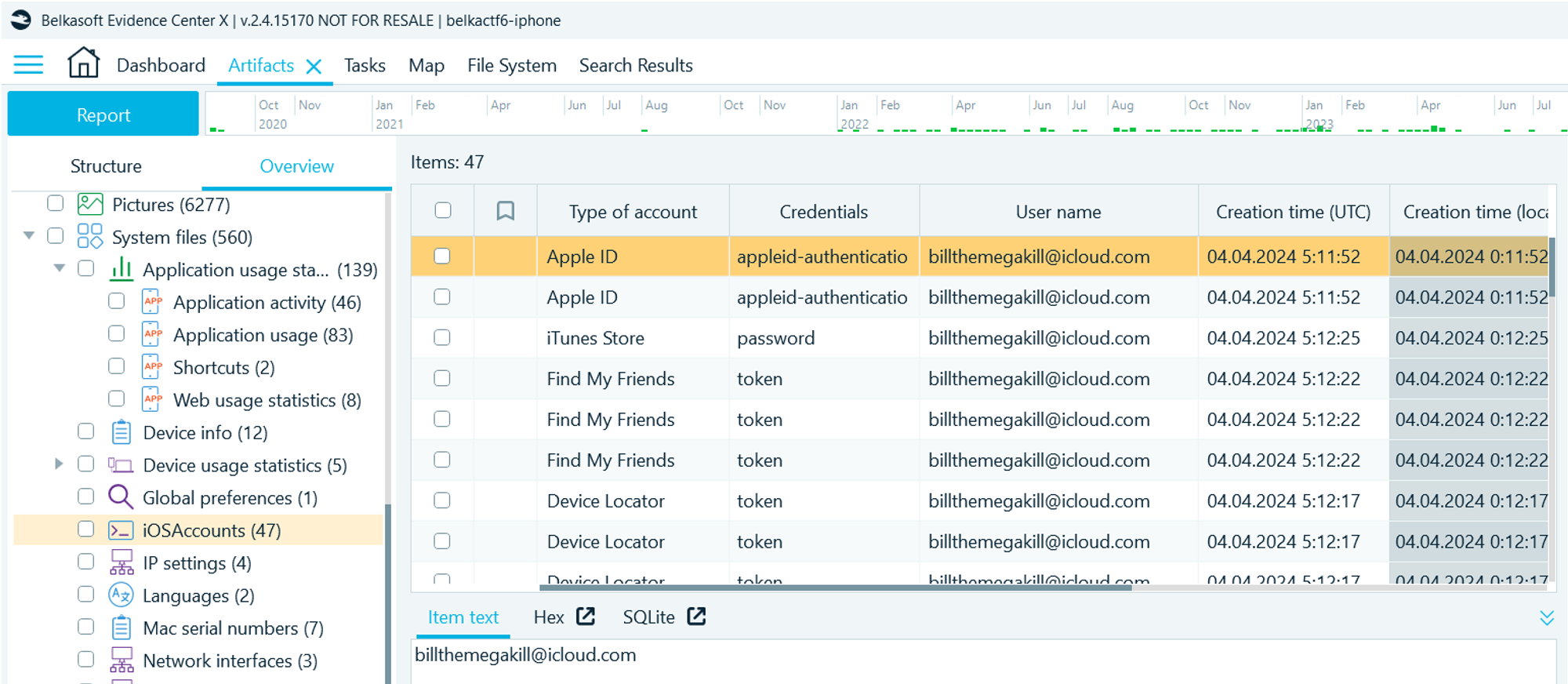
Flag
billthemegakill@icloud.com (the task was solved XX times)
2. Namedrop (Baby)
Question
What is the iPhone owner's full name? Flag format: First name Last name
Solution
- Navigate to Artifacts → Overview → Contacts
- Find the email from the previous question
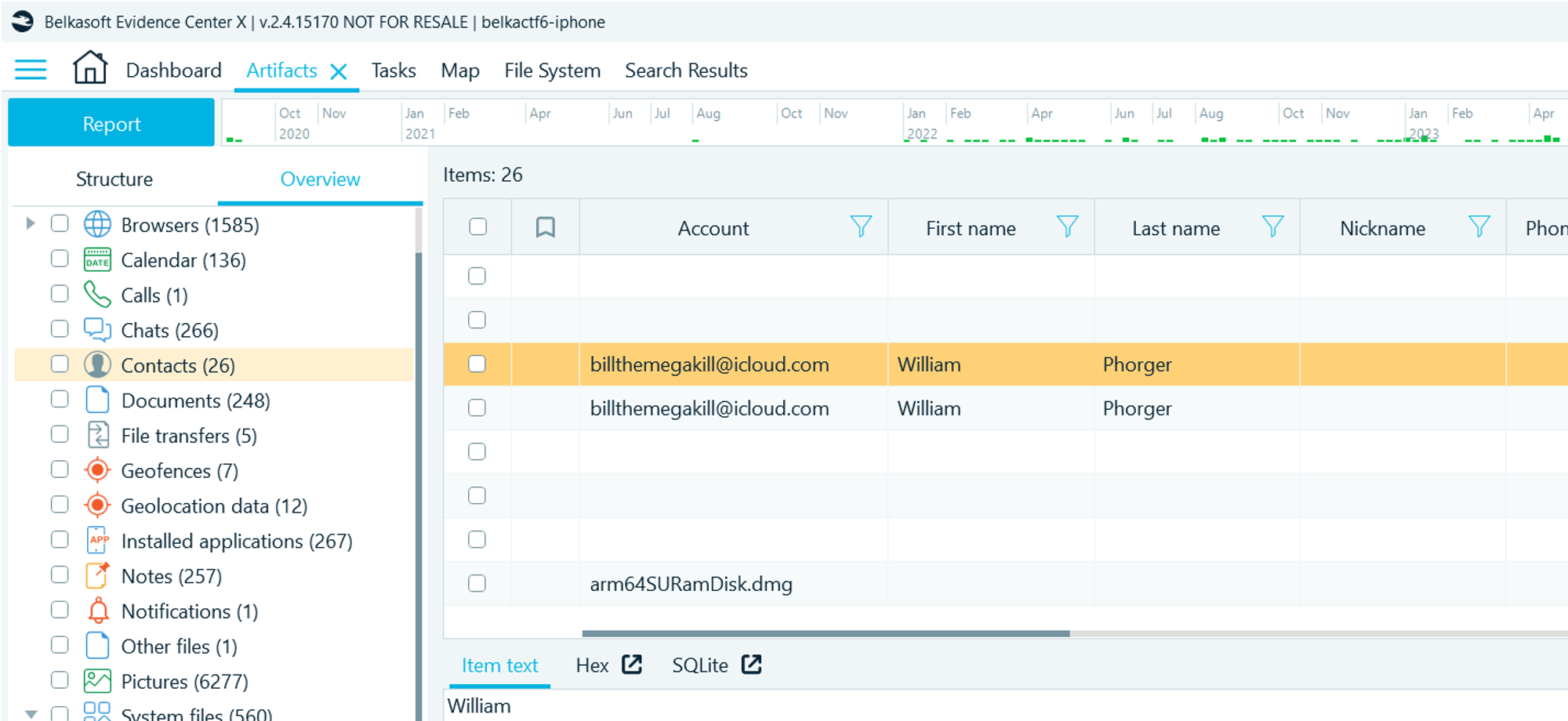
Flag
William Phorger (the task was solved XX times)
3. Conspirators (Warmup)
Question
Which Telegram accounts did the owner discuss shady stuff with? Flag format: @username, @username, @username, ...
Solution
- Navigate to the Artifacts → Overview → Chats
- Read the Telegram chat history, list all usernames discussed for shady dealings
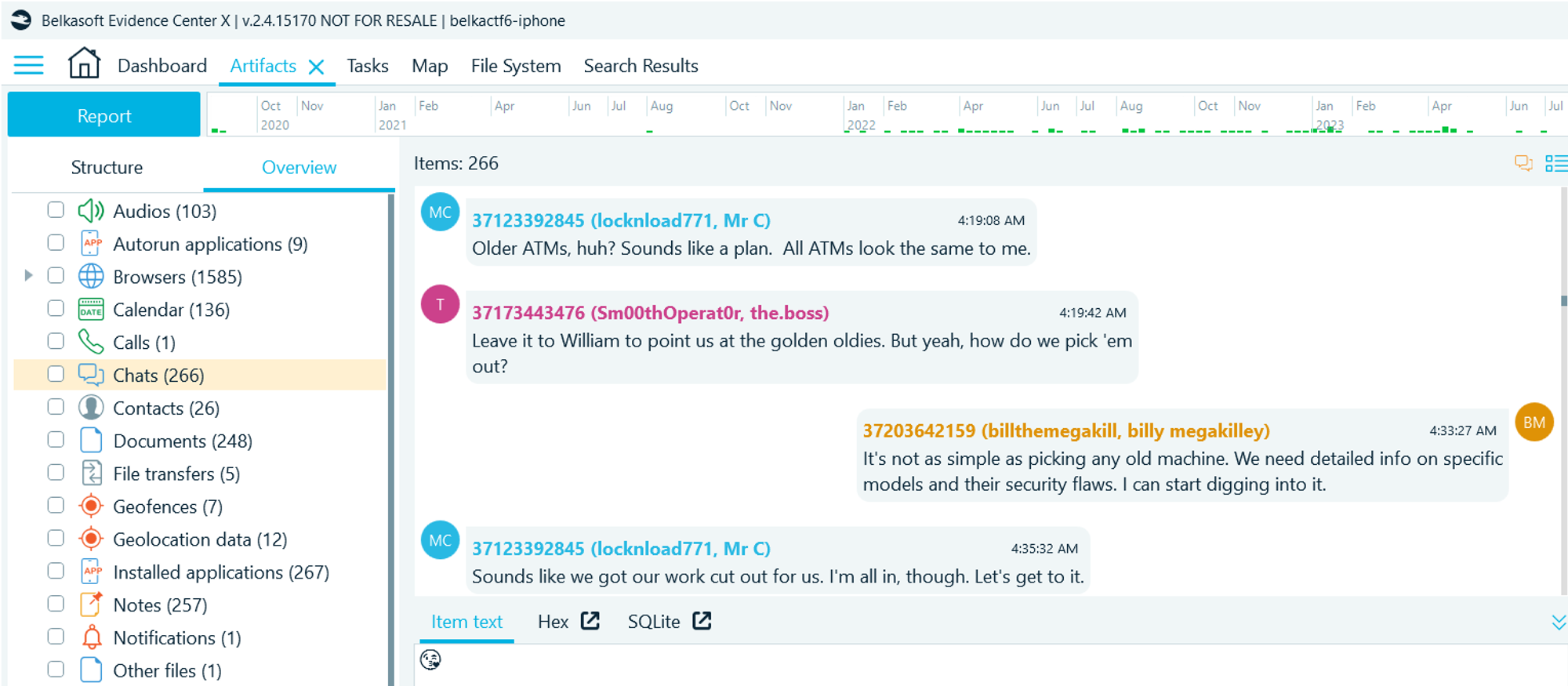
Flag
@Sm00thOperat0r, @locknload771, @JesusStreeton1999, @diddyflowers (this task was solved XX times)
4. Visit (Tricky)
Question
Where does William live? Flag format: latitude, longitude—or just click the map
Solution
- Navigate to Artifacts → Overview → Geolocation data
- Extract important locations from Uber, one of them is home
- Viewing raw in SQLite, you can see a "home" label:
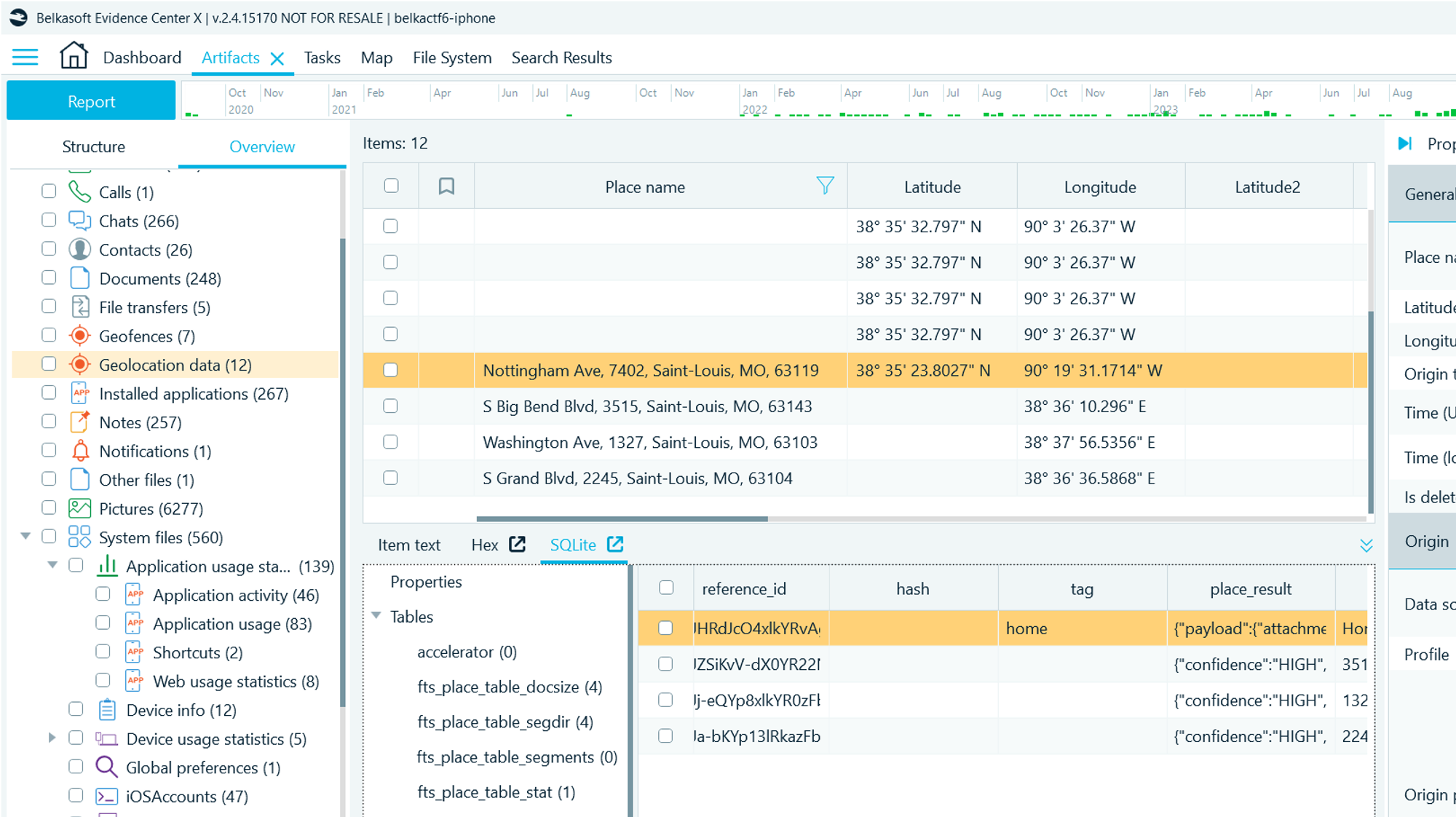
Flag
Nottingham Ave, 7402, Saint-Louis, MO, 63119 (this task was solved XX times)
5. Username (Baby)
Question
What is the username of the laptop user?
At this point you are given the password for the second file and can now unpack it.
Solution
- Add the new image to your case and analyze it with all available Belkasoft X options
- Navigate to Artifacts → Overview → Windows → User name and Sid list
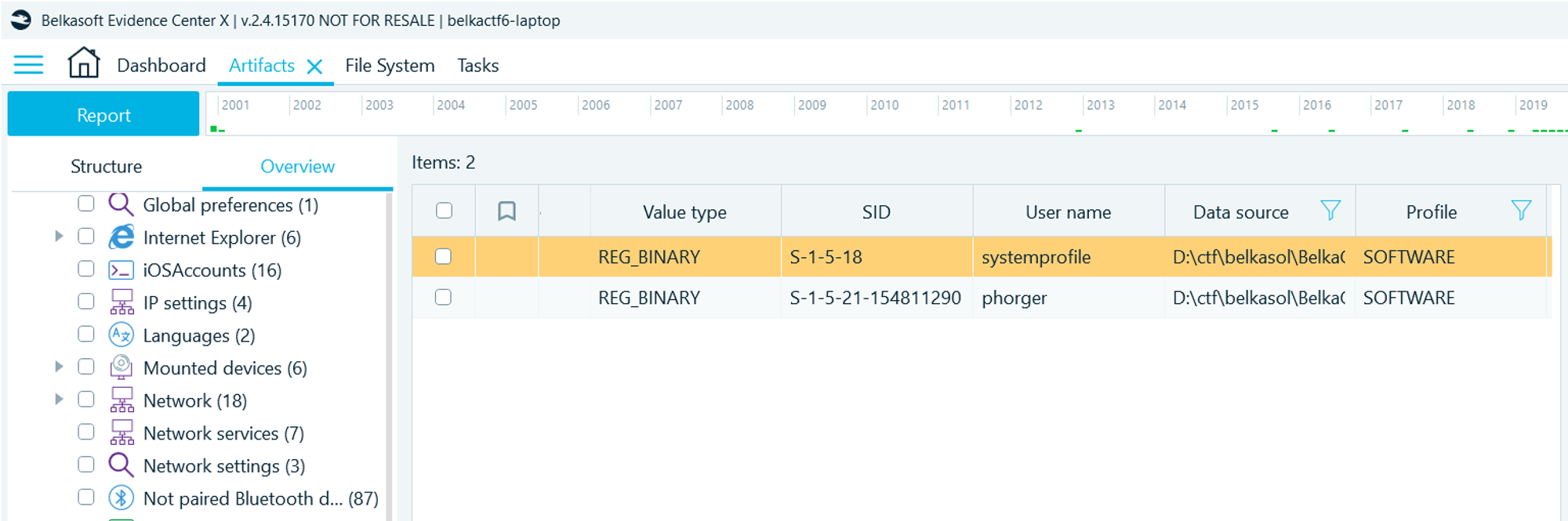
Flag
phorger (this task was solved XX times)
6. April Paycheck (Warmup)
- Navigate to Artifacts → Overview → Notifications
- There's a notification from the chat application called "Element":
"sm00thoperat0r (Friends) | Yo William, gotta talk cash. That mess we made? Yeah, we're sorry, bro. Upping your take this month by 15%. You're landing at 7012USD total this round."
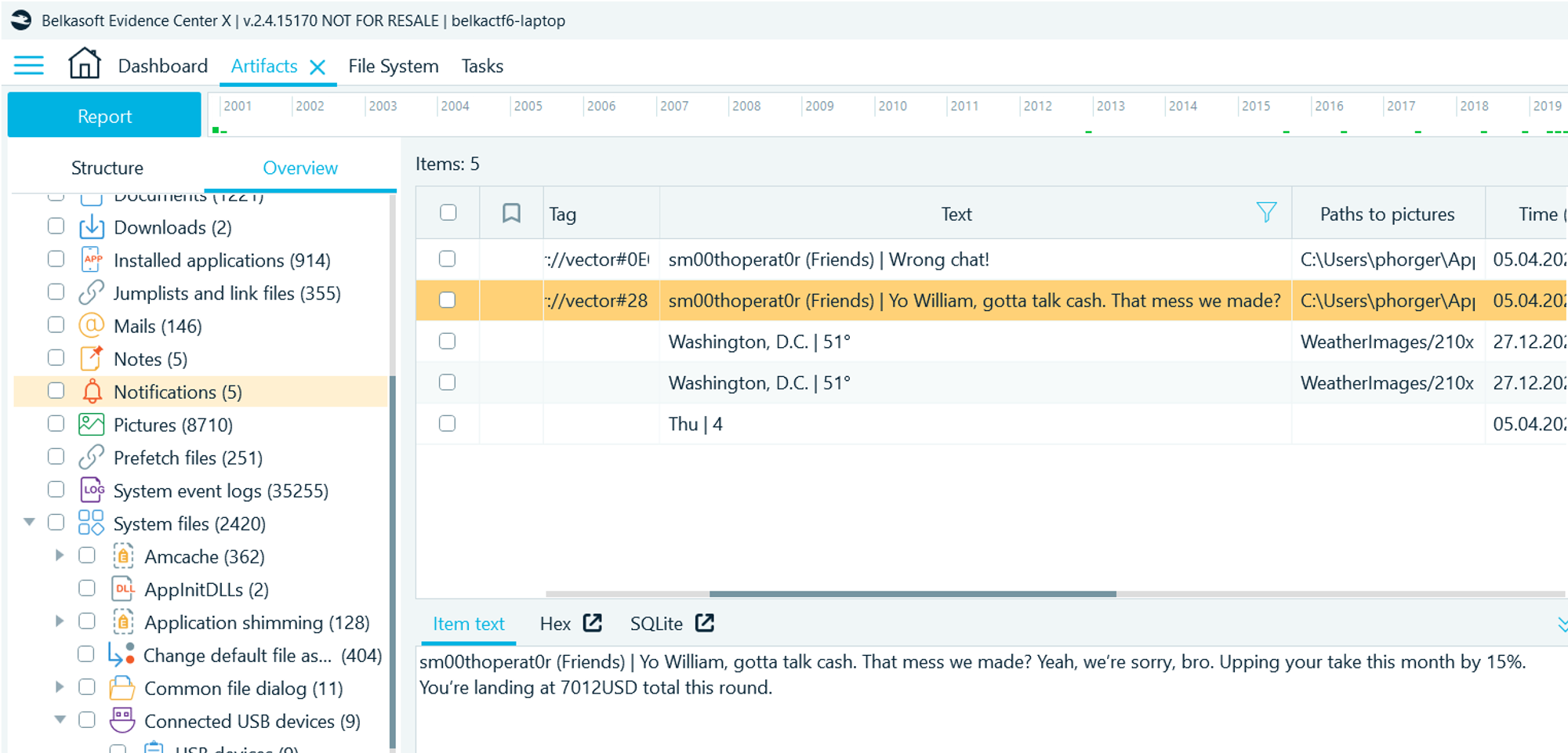
Flag
7012 (this task was solved XX times)
7. Party (Tricky)
Question
Where did the gang go to celebrate their success together in March? Flag format: latitude, longitude—or just click the map
Solution
-
Navigate to Artifacts → Overview → Chats
-
Read the chat history. Firstly, on March 19th, the boss suggests hanging out somewhere:
Yo, crew! We've been grindin' like crazy. How's 'bout we crash that bar downtown tomorrow night? Time to throw down some celebration for us bustin' our butts. 🍻 on me! Eh? -
Secondly, a bit earlier, it's mentioned they use Splitwise:
Now that's what I call a great meal! Added it to our Splitwise -
Search for the Splitwise database. For this, unpack .tar for file name search, search for "splitwise"
A Splitwise settings file is found:
/private/var/mobile/Containers/Data/Application/E951DC58-CF30-4518-9482-3E076D89A20B/Library/Preferences/com.Splitwise.SplitwiseMobile.plist -
Nearby in the same container lies the database:
/private/var/mobile/Containers/Data/Application/E951DC58-CF30-4518-9482-3E076D89A20B/Library/Application Support/database.sqlite -
Open in Belkasoft's SQLite Viewer. In the SWExpense table, there is a record with description "Get-together at Cunetto"
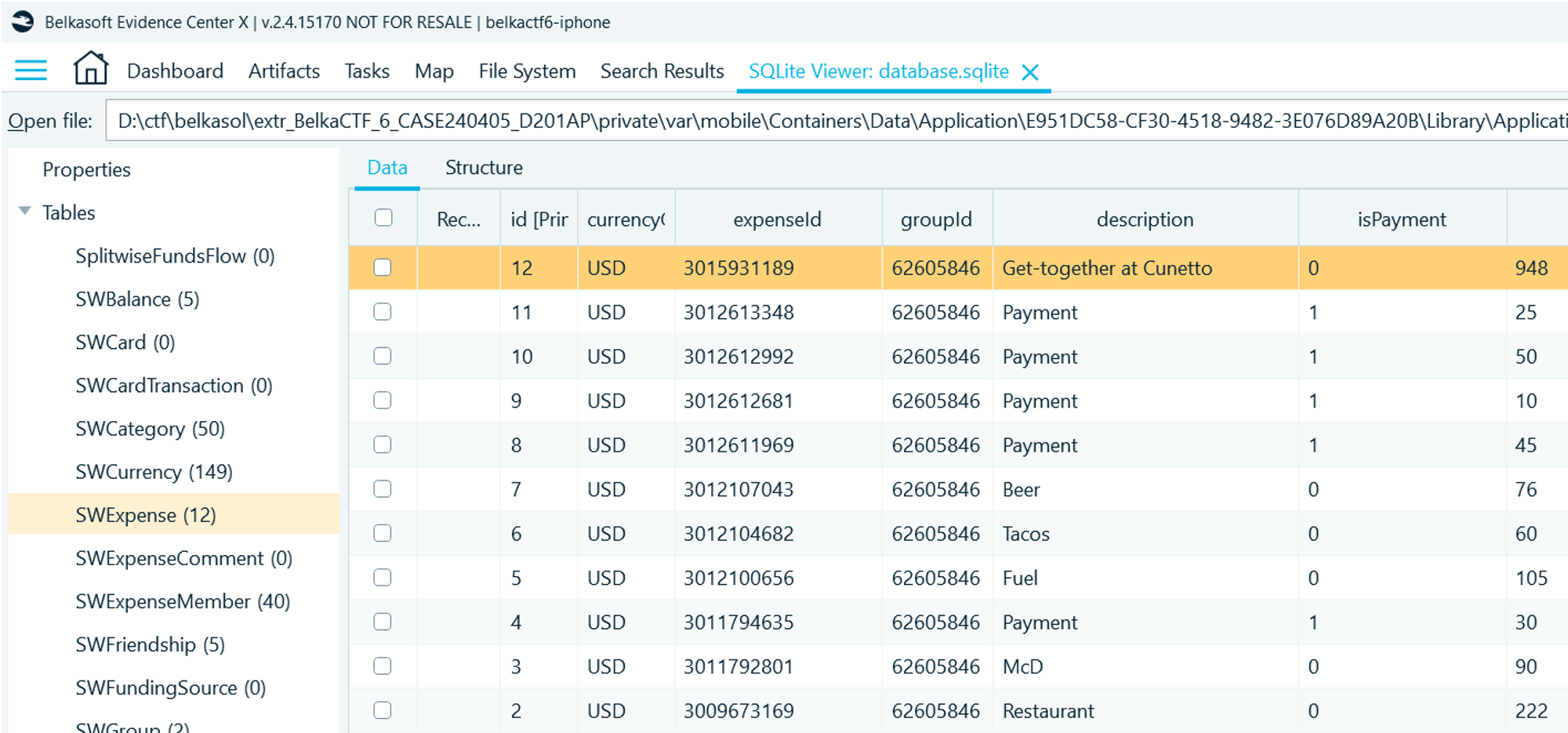
-
Search for Cunetto— it is Cunetto House of Pasta
Flag
5453 Magnolia Ave, St. Louis (this task was solved XX times)
8. Crypto (Warmup)
Question
Which file does the guy keep his encrypted container in? Flag format: full path, e.g. C:\VeraCrypt\MyContainer.vc
Solution
- Navigate to Artifacts → Overview → Chats
- Read the chat, at the end, the bad guy tries to send a panic command to
the bot, but the bot throws an exception:
Exception has happened:
Traceback (most recent call last):
File "Y:\baker[bot.py](http://bot.py/)", line 98, in destroy_encrypted_container
os.remove(cryptocontainer)
PermissionError: [WinError 32] The process cannot access the file because it is being used by another process: 'C:/Users/phorger/Documents/de... - Review the Windows' image in the File System viewer. What can match that "de..." file in that C:\Users\phorger\Documents? Looks like desktop.ini
- Hm... ini file. Now, pay attention to the dialog between your hero and his Chief. Typically almost meaningless, this time they have a good hint! Your hero says "The file might be drifting in an undercurrent, hidden from plain sight."
- Undercurrent, current, stream... he gives a hint about alternate data stream!
- Click on the desktop.ini and notice that Belkasoft shows an Alternate Data Stream called vault.vhdx
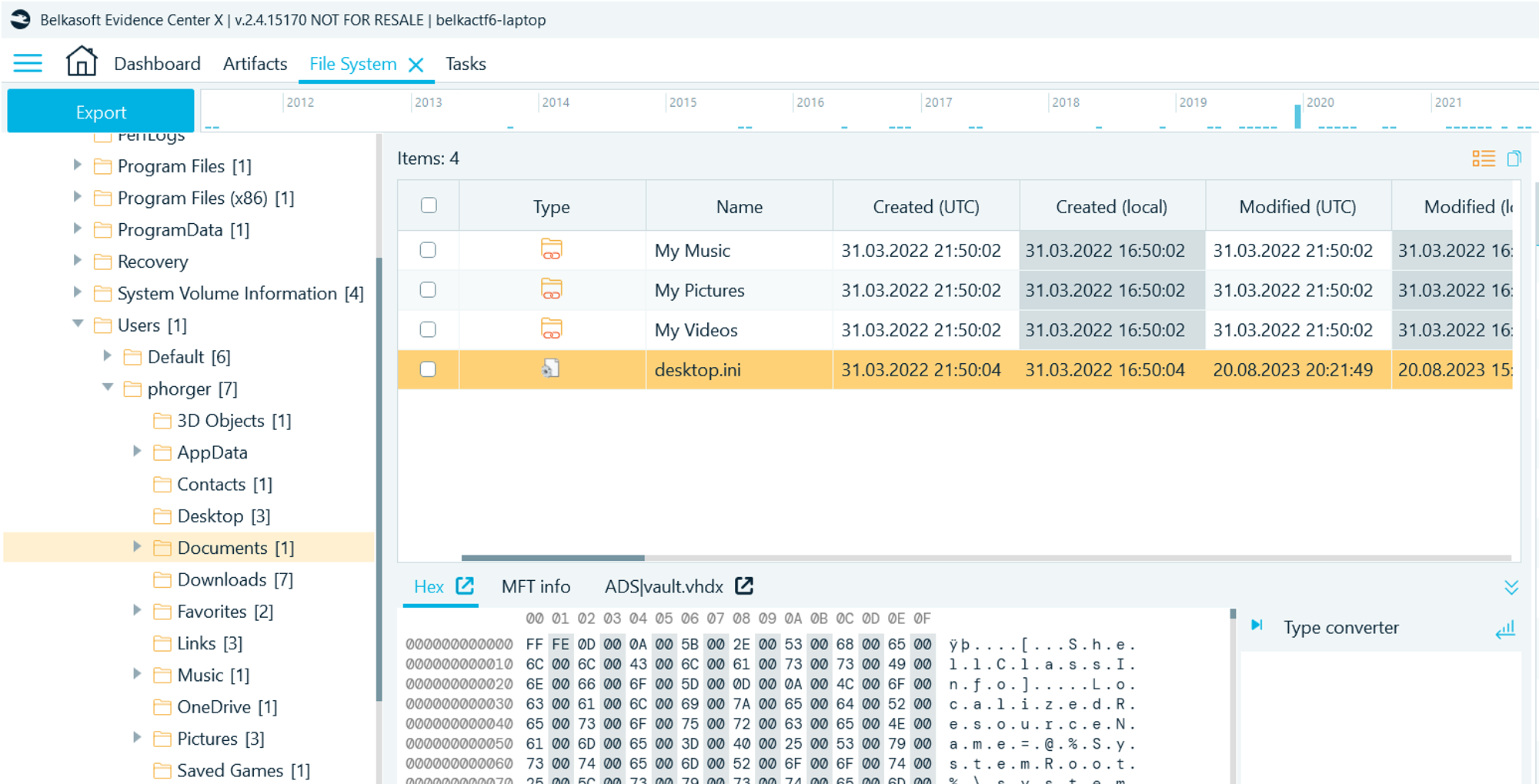
Flag
C:\Users\phorger\Documents\desktop.ini:vault.vhdx (accepted also without ":vault.vhdx"; this task was solved XX times)
9. Luxury (Warmup)
Question
Which luxurious item did Phorger put his laundered money into? Flag format: full name incl. any codes, e.g. Bugatti Chiron BG744
Solution
- First, decrypt the crypto container. Extract it from the alternate data stream (using Belkasoft, you can do this by opening its Hex Viewer full screen, select all, and click "Save selection")
- Navigate to the Artifacts → Overview → Notes. Inside the notes, you will
find the BitLocker recovery key:
BitLocker recovery
Identifier:
929983CA-5012-49E9-A194-4550C08C6127
Recovery key:
590238-514580-359986-088242-029766-319495-410509-636911
- Mount the extracted vault.vhdx in Windows, choose to unlock BitLocker with the recovery key
- Inside the crypto container, find an Excel file called Spending.xlsx
- Find a line with the biggest expense inside:
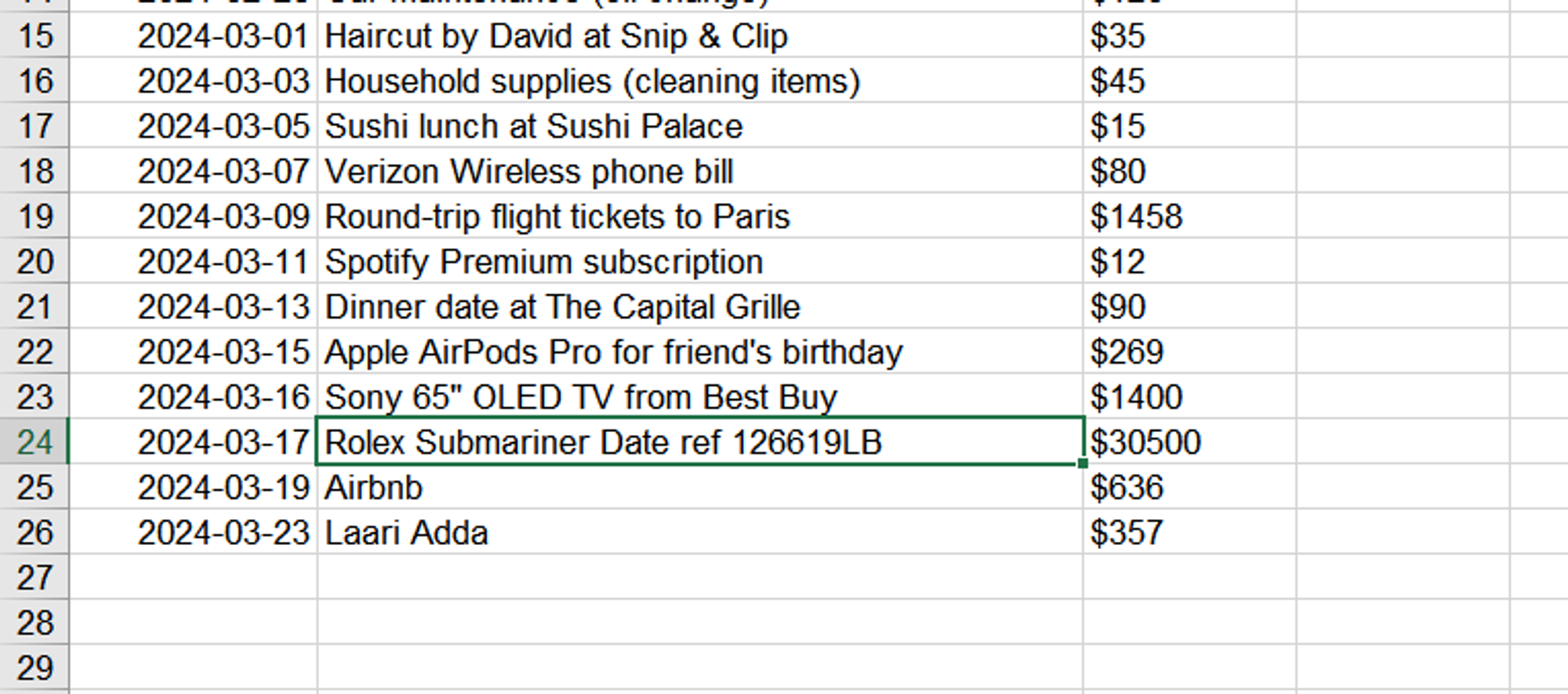
Flag
Rolex Submariner Date ref 126619LB (this task was solved XX times)
10. Vacation (Tricky)
Question
Which concert were Phorger and his girlfriend planning to attend in May? Format: artist, venue, city, e.g. Taylor Swift, Friends Arena, Stockholm
Solution
- Navigate to Artifacts → Overview → Chats. In the Telegram chat on December 24th, it's mentioned that Drew and William discussed the planned May trip, but then Drew deleted everything.
- Navigate to Artifacts → Overview → Browsers → Cache. Search for cached images (image/jpeg) from Telegram web. Among them, there is a poster you are looking for:
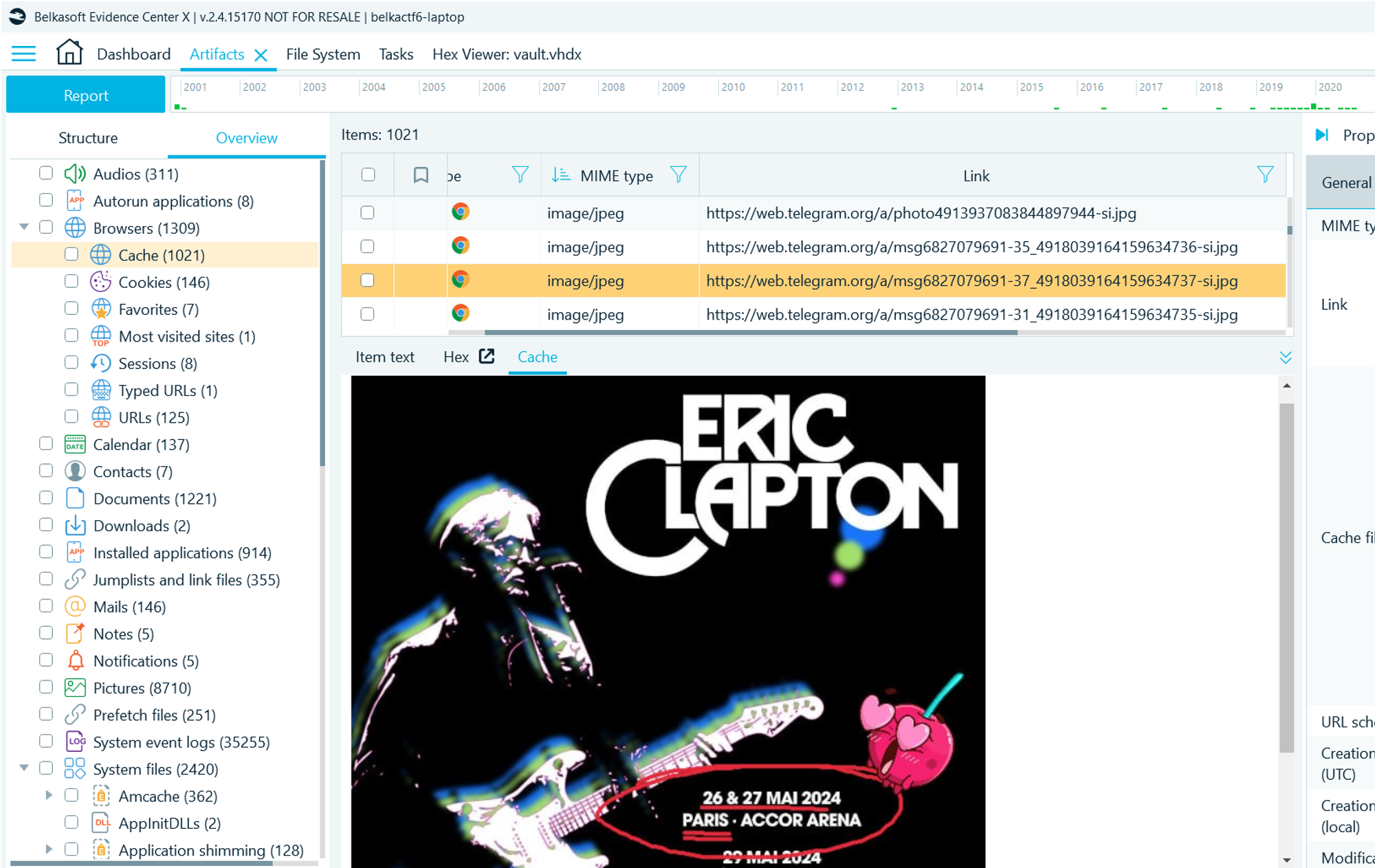
Flag
Eric Clapton, Accor Arena, Paris (this task was solved XX times)
11. Illustrator (Warmup)
Question
What's the name of the person who designed the print template for the bills? Flag format: First name Last name
Solution
- On the crypto container in \baker\presets\ there is a PSD file with a print
template for the bill. In its metadata, the edits of this file are logged, metadata
is visible in the Hex Viewer:
…
File 50_USD_Series_2004_Note_Front.psd opened
Open false
true
C:\Users\DrewLinesworth\Documents\work\50_USD_Series_2004_Note_Front.psd
64
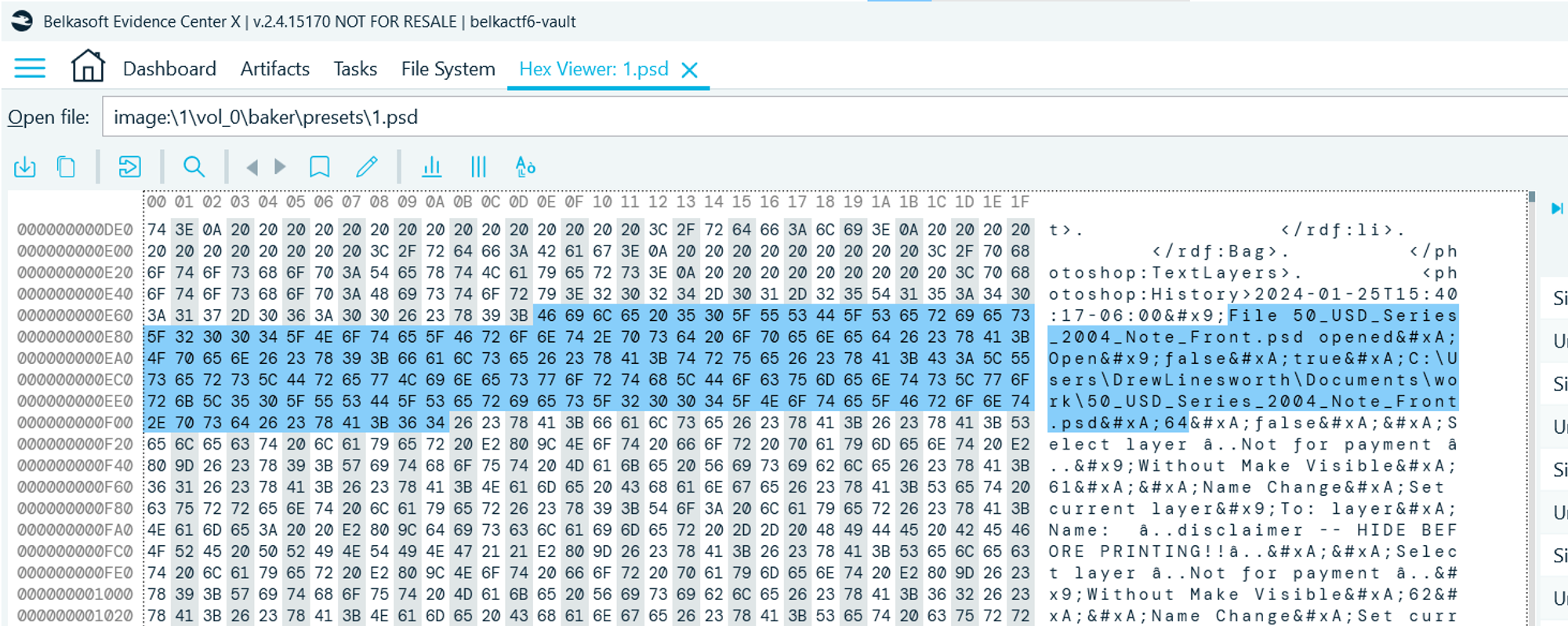
Flag
Drew Linesworth (this task was solved XX times)
12. Homebrew Lab (Tricky)
Question
Where is the makeshift lab where they printed the cash located? Flag format: full address, e.g. 314 S Main St, Kirksville, MO
Solution
- Navigate to Artifacts → Overview → Geofences
- A geofence is set upon leaving the point 38° 35' 32.797" N, 90° 3' 26.37" W (actually, it is a geo-reminder with the text “Turn off the fume hood!”)
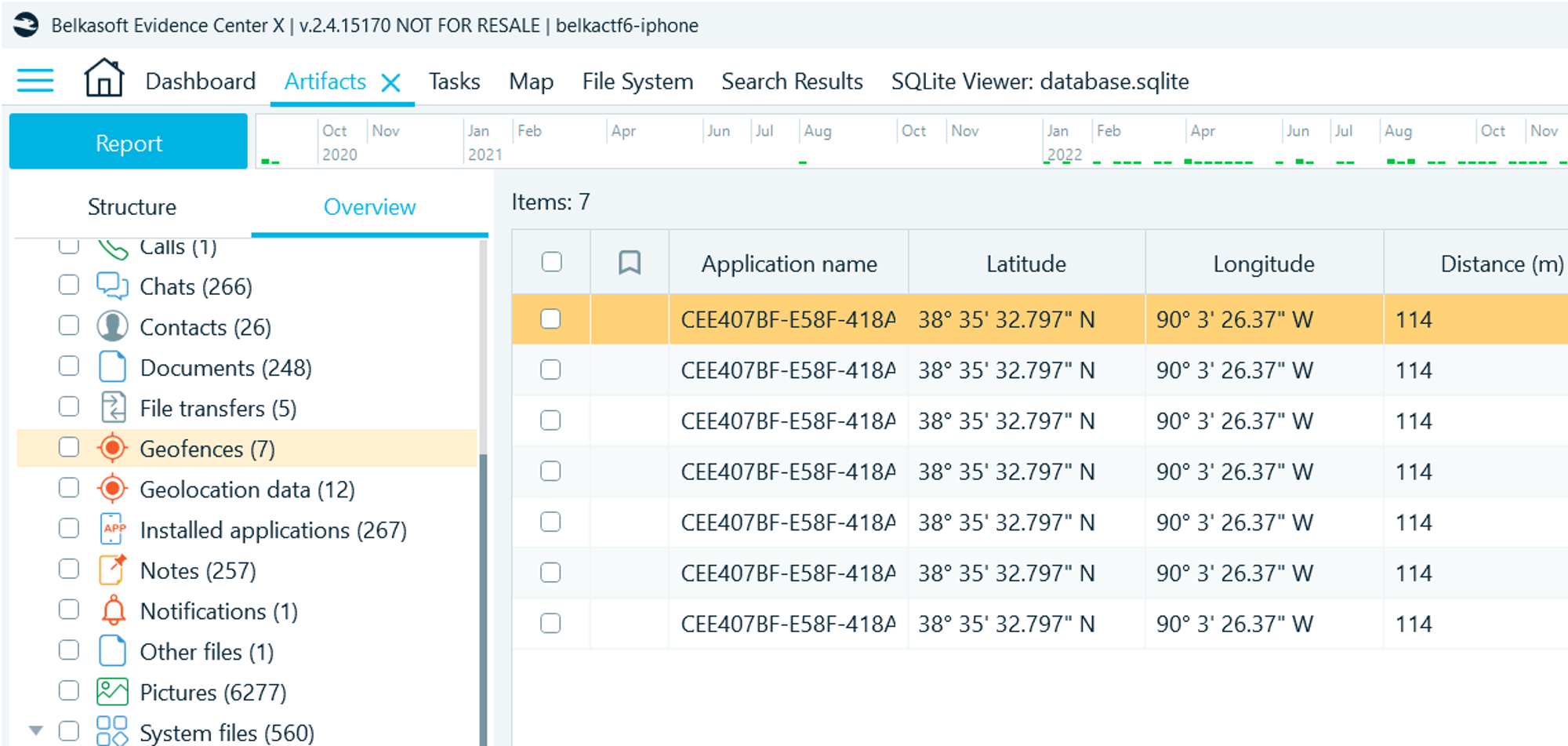
- Search this location on Google Maps
Flag
900 N 88th St, East St Louis, IL (this task was solved XX times)
13. Largest Batch (Warmup)
Question
What is the precise moment their largest printing batch was completed? Provide exact timestamp in a common format, e.g. 2023-07-17 17:07:07 UTC
Solution
- As you know, printing was initiated through a Telegram bot. Navigate to Artifacts → Overview → Chats
- Search for the largest printing batch (of 160 sheets)
- Check the timestamp of the message from the bot about the end of work
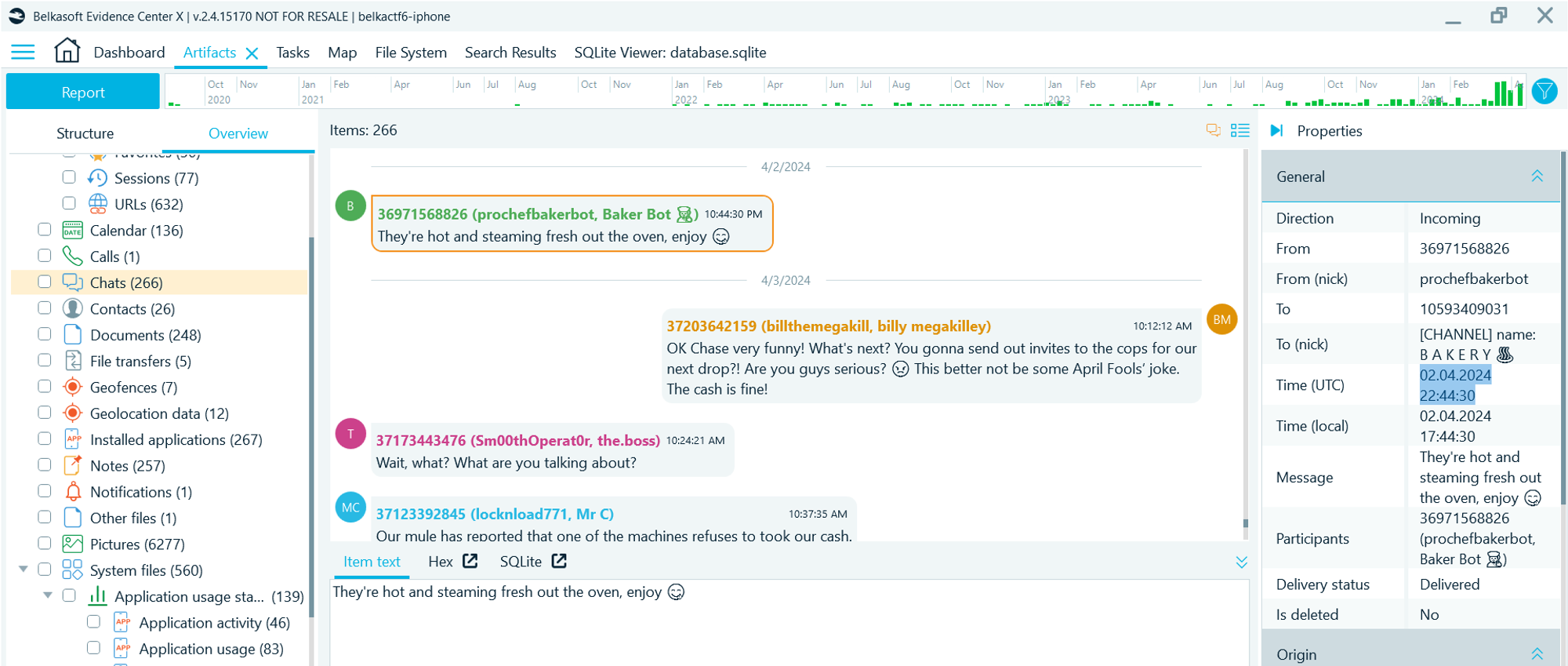
Flag
02.04.2024 22:44:30 UTC (this task was solved XX times)
14. Device (Tricky)
Question
What's the printer model they used to print money? For example, Canon Color imageCLASS MF656Cdw
Solution
- Navigate to Artifacts → Overview → System files → Connected USB devices → USB devices
- In the device connection history you will find an HP device with VID_03F0&PID_042A
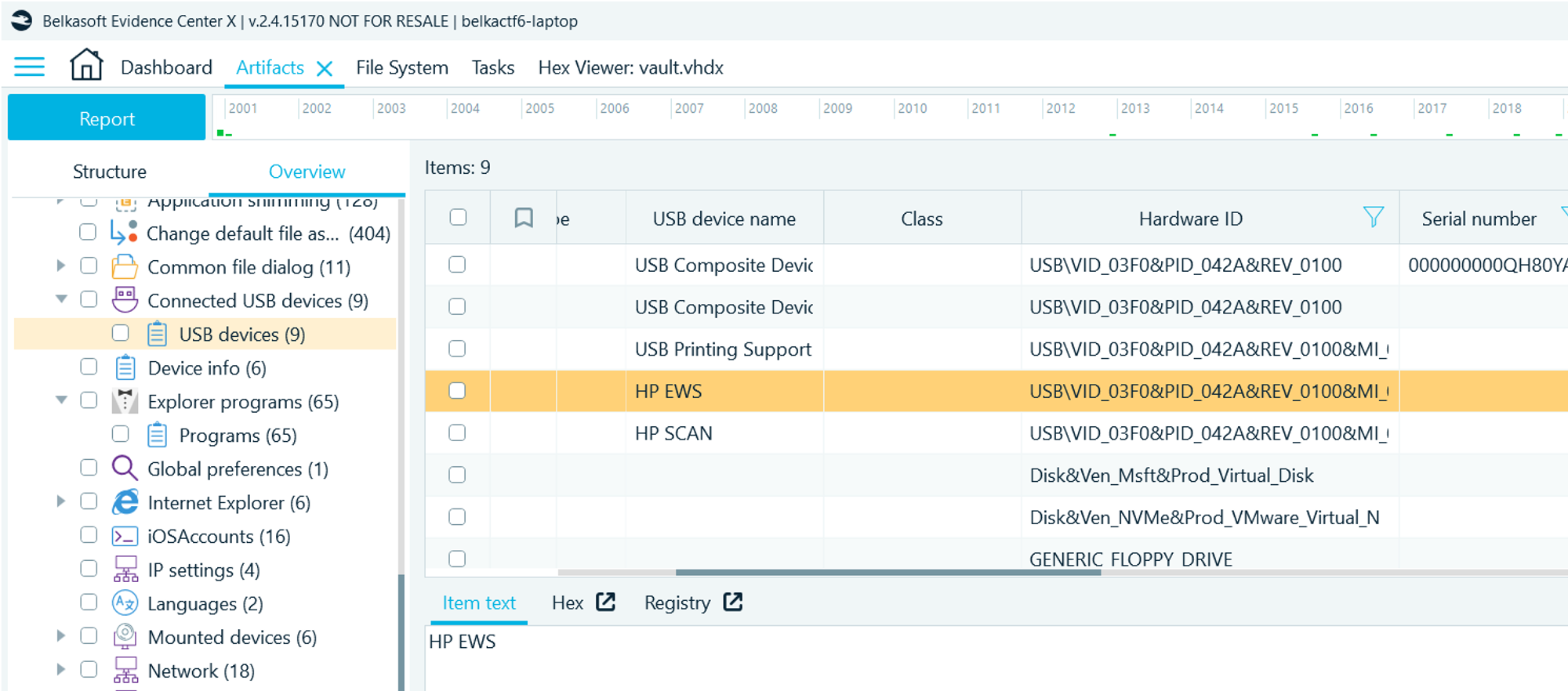
- Google for this VID
Flag
HP LaserJet Professional M1132 MFP (this task was solved XX times)
15. Night Shift (Tricky)
Question
Which ATM did Phorger test his bills on recently? Flag format: bank and street name, e.g. Chase ATM on S Main St
Solution
- Navigate to Artifacts → Overview → Chats
- In the chat, it is mentioned that on April 1st, the guy was reported that the ATM did not accept the fakes, and he would go to check them.
- Navigate to Artifacts → Overview → Wi-Fi connections
- On April 3rd at 2 am, there's a connection to the Wi-Fi network UCPLPublicWireless
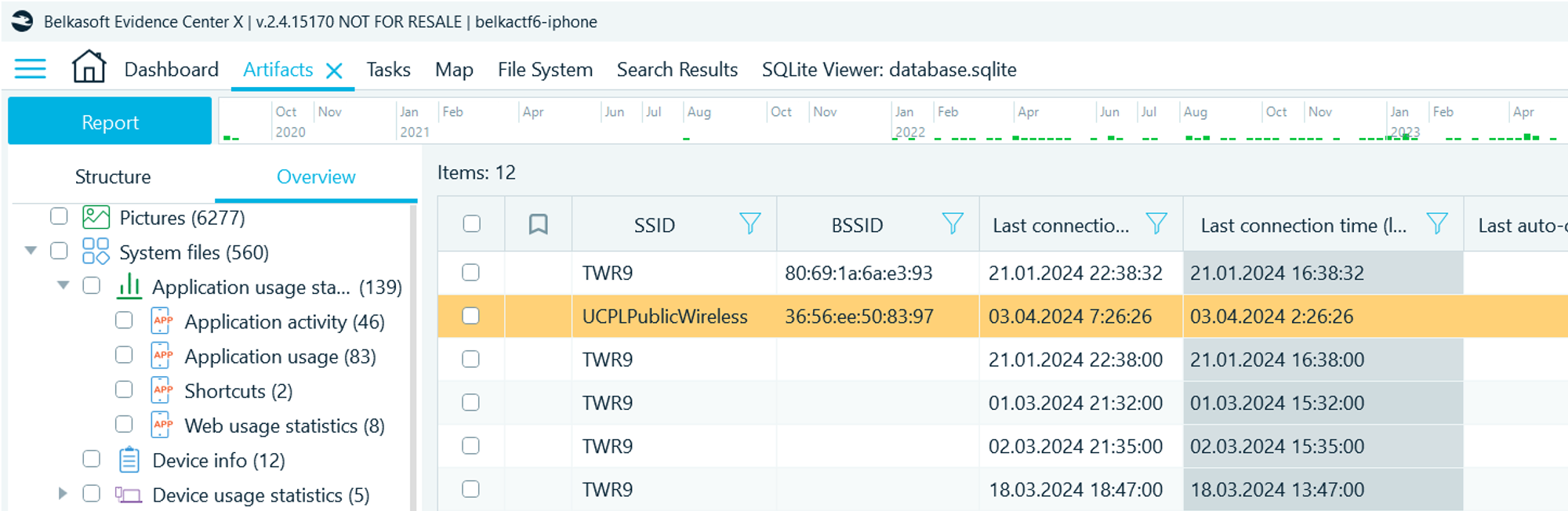
- Use wigle.net to find this Wi-FI location by MAC address or by searching name. You will figure that this is the network of University City Public Library:
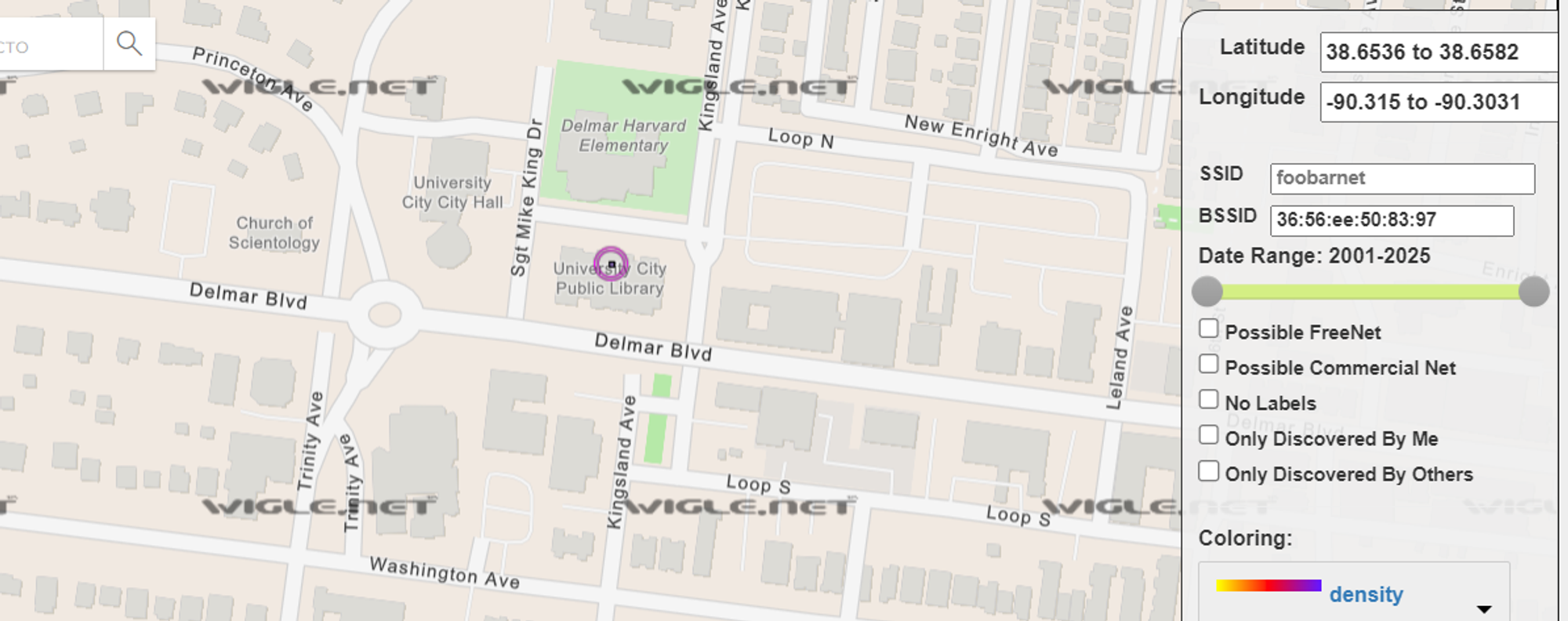
- Google for ATMs nearby
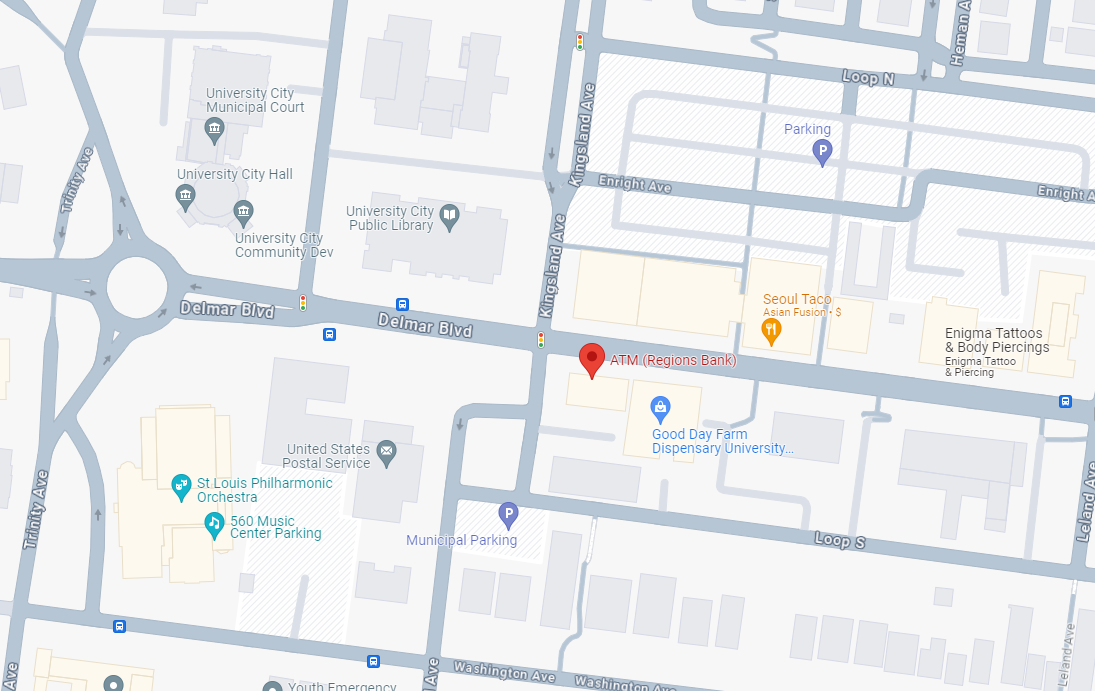
Flag
Regions Bank ATM on Delmar Blvd (this task was solved XX times)
16. Mole (Hard)
Question
Who leaked the technical data on the bill validator to the gang? Flag format: First name Last name
Solution
- Unlock the crypto container in Windows and mount it as a logical drive
- Add it as a data source to Belkasoft X (Add data source → Add existing → Disk drive → Logical drive)
- Carve the entire data source with all artifacts selected (use "Carve all space option")
- A deleted PDF with the label CONFIDENTIAL is found (the file name will be "document_00000D45D000.pdf", where the number represents an offset on the disk):

- Open the file in any PDF viewer. The file turns out to be digitally signed by the insider:

Flag
Kenneth Leek (this task was solved XX times)
17. Financial institution (Hard)
Question
Which offshore financial institution did the gang bank with? Provide its SWIFT code.
Solution
Well, this is by far the toughest task in the entire CTF! Kudos to the 4 players who were so persistent that they solved this incredibly difficult task.
- Navigate to Artifacts → Overview → Chats. In the chat, the boss says on
March 1st, that he opened a Panamanian bank account. Some time later, Chase
start communicating using cryptic hex messages:
>> 2fce2a77262293ce51775dfc9322937afc115177c2e7e7ce11e377f822e77a93223b773bce9393cebd779c51
<< a9a62f0081ed12650012caed12650012ca
- Trace back when the hex communication started—it is January 16th:
>> No messaging apps can be trusted, believe me.
>> Have you got the Shortcut I sent to you?
<< Yes, Chase, but no idea how to approach its use.
>> Just press Share on any text. And punch in the secret key we agreed on in the box that pops up.
<< addaf04dc94ddaf04ddfc980661fc91e7caac9f0dadac94df1664d0c
- Looks like an external third-party encryption is used, implemented as an iOS Shortcut
- Navigate to Artifacts → Structure → iPhone → Mobile applications → Biome notifications
- There, you can find several notifications with titles SecuEncrypt and SecuDecrypt that originated from com.apple.shortcuts
- Search where shortcuts are stored—/private/var/mobile/Library/Shortcuts/Shortcuts.sqlite
- The database structure is quite complicated, but if you extract strings (UTF-16, for example with the strings2 utility), you will see JavaScript code executed by the shortcut to encrypt data:
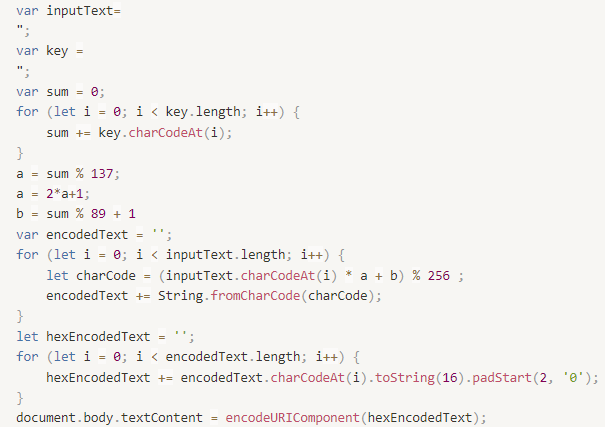
In a nutshell, the code turns the key given to it into two numbers—"a" and "b", and then transforms each text character, multiplying it by a and adding b
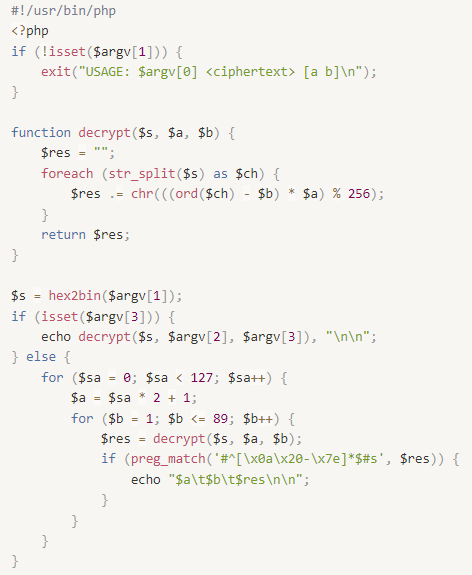
- Since there are not so many variations of a and b, you can decrypt the encryption by brute force, leaving only the results made up entirely of printable characters. Here is a sample code for brute-forcing:
- Try this code for the very first message to test. You will see the following:
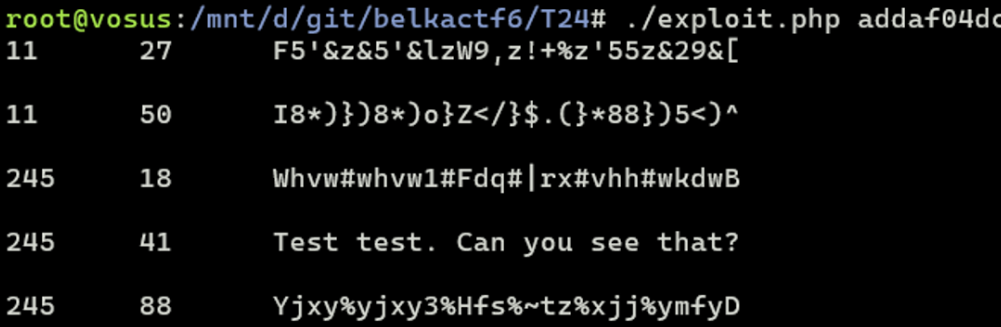
It works!
- So, now try it on the biggest message from the chat, near the discussion of the offshore account:
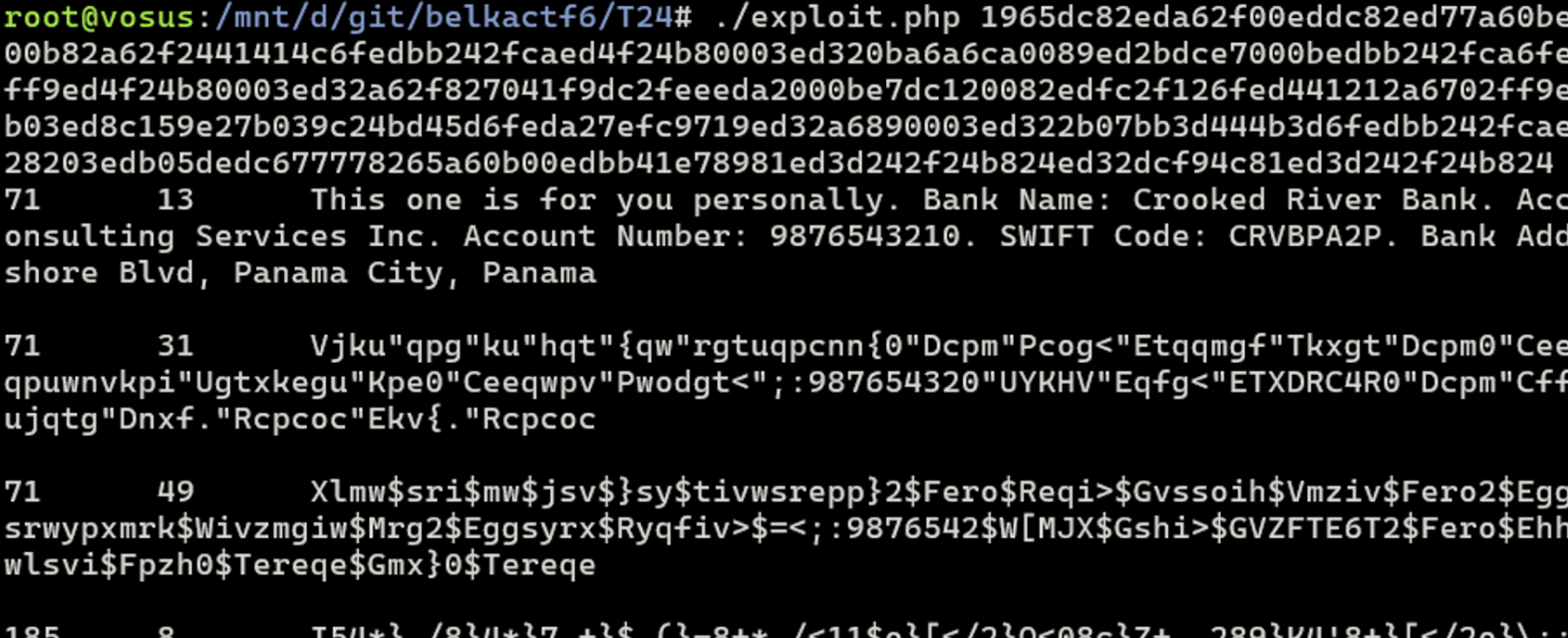
Flag
CRVBPA2P (this task was solved XX times)
18. Statement (Hard)
Question
Paste Phorger's entire bank statement here, containing all his offshore transactions.
Solution
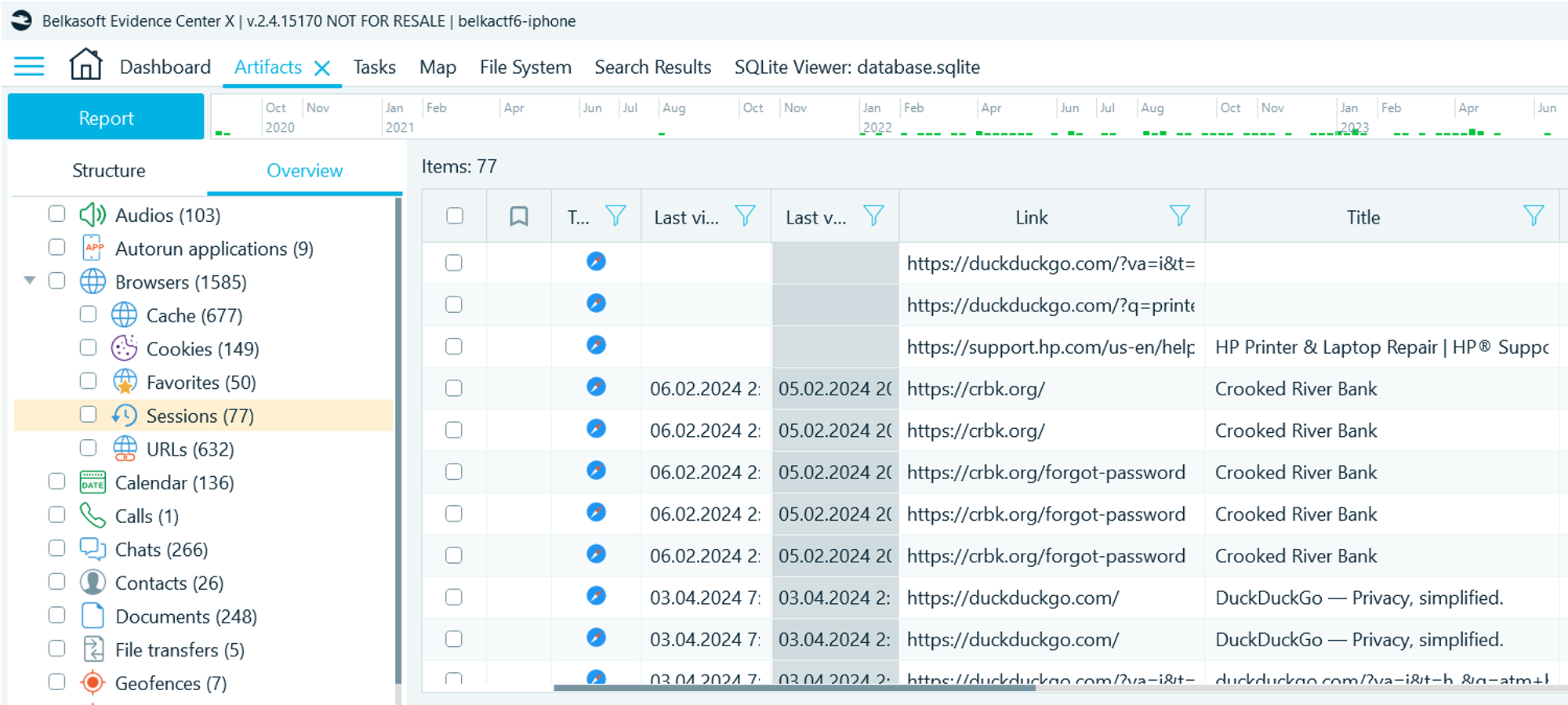
- Navigate to the Artifacts → Overview → Browsers → Sessions
- There, you will see visits to Crooked River Bank at crbk.org
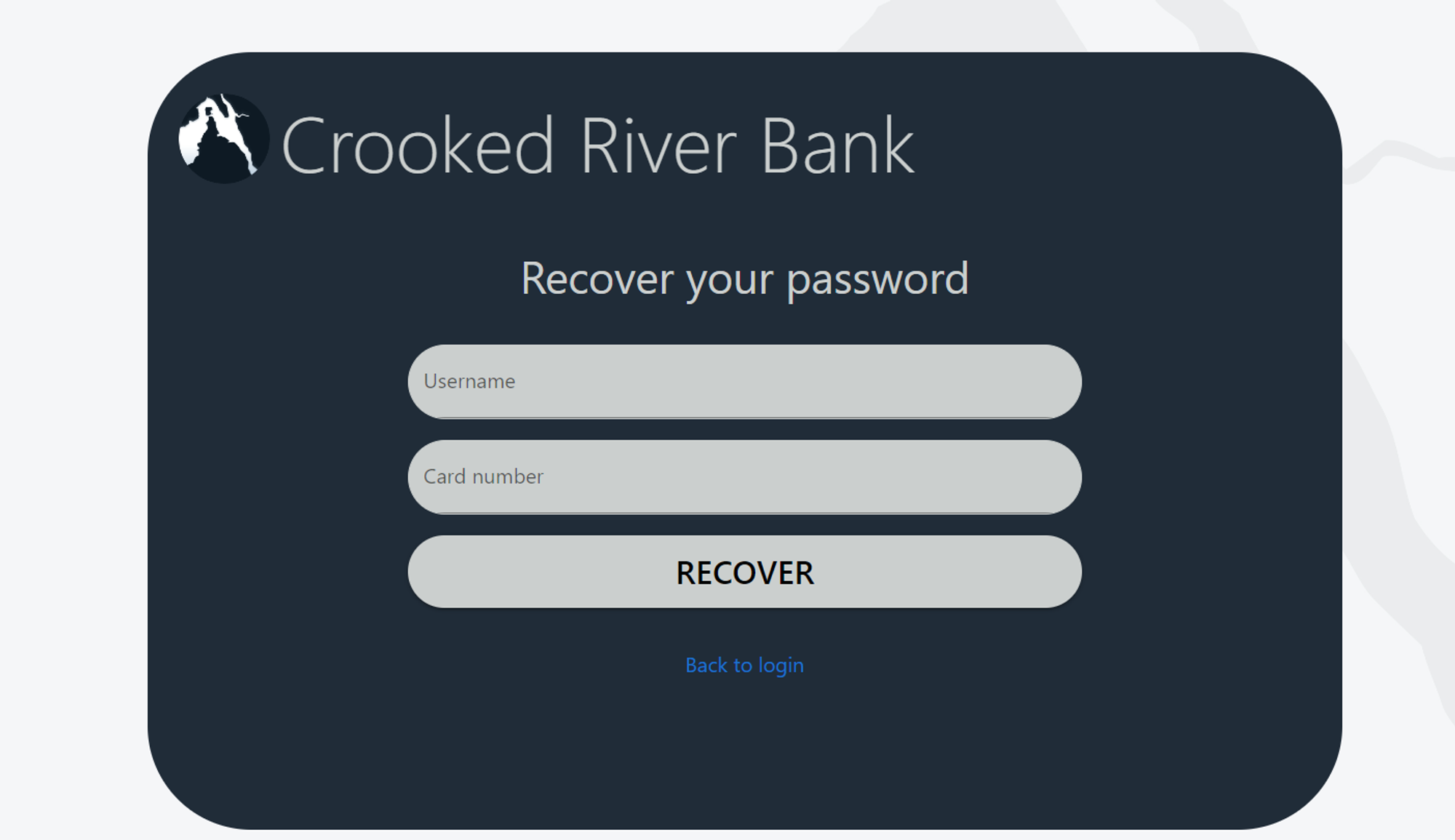
- The bank's site has a login form (requires login and password) and a password recovery option (requires login and card number):
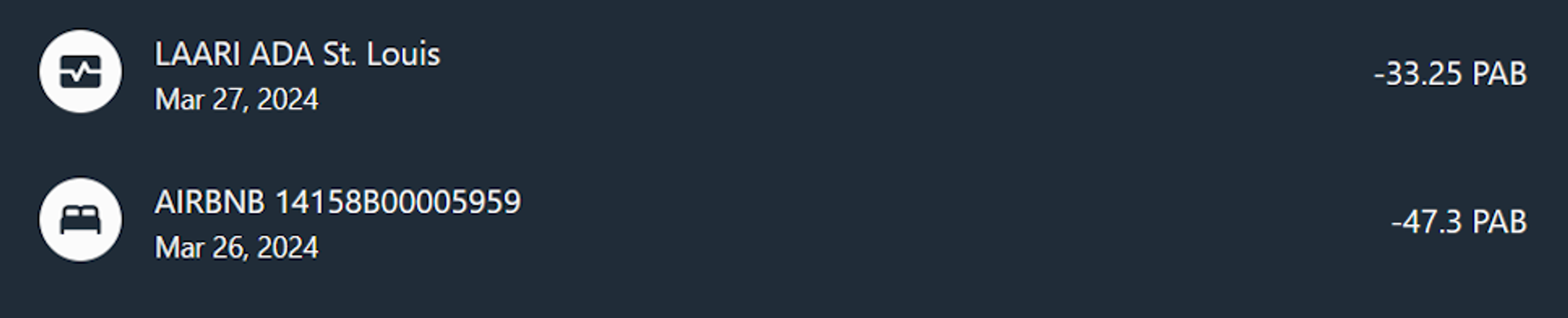
- On the Windows image, there is a file C:\Users\phorger\Pictures\Capture2.png, which has a photo of several transactions in Panamanian balboas
- If you look at this file in the Hex Viewer, you can see that the PNG marker of IEND is located approximately at 15% from the beginning of the file, and after it, there's a lot of data, which also ends with IEND
- This is a sign of the Acropalypse bug—the screenshot app first takes a full-screen screenshot and writes it to a file as PNG, and when cropping, it overwrites the file content with the new cropped PNG, but does not truncate the file to the new length—so the tail of the full-screen PNG remains in the file
- From this tail, you can recover the image, for example, with the Acropalypse-Multi-Tool
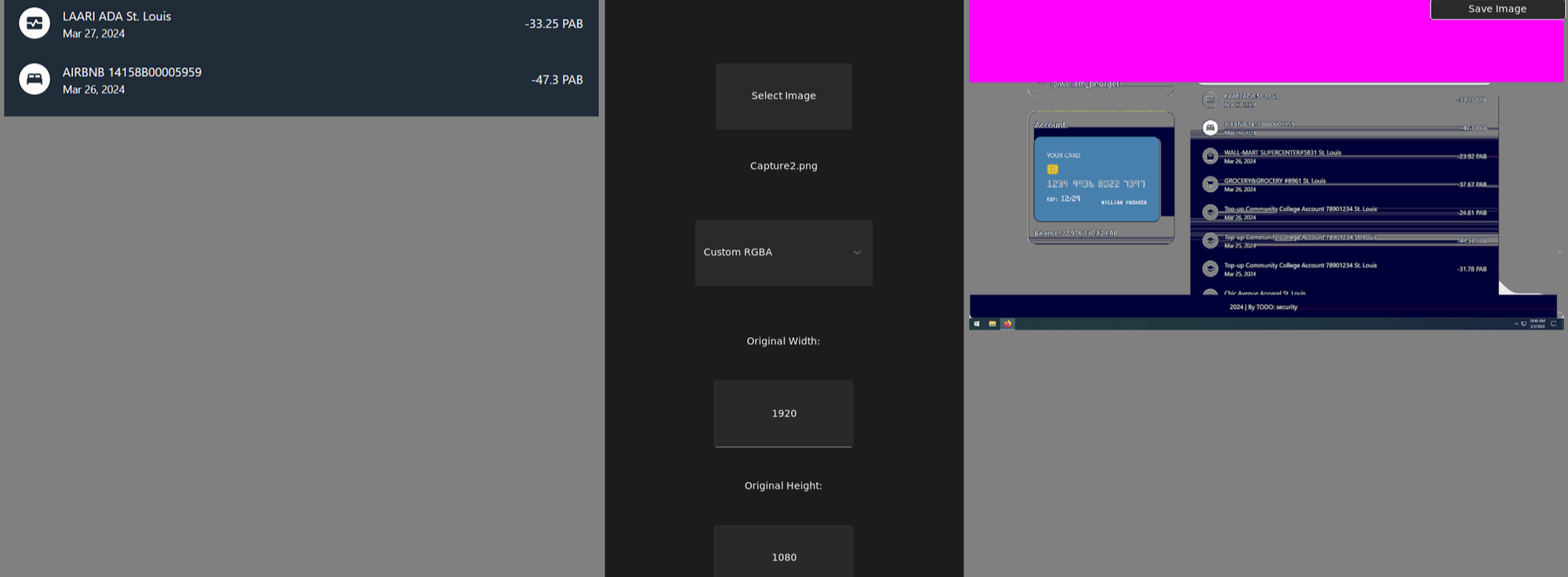
- On the uncropped image, you can see the login "william_phorger" and the card number "1234 9936 8022 7397"
- Using these details, you can reset the password for the account on crbk.org
- To download the full transaction history, the bank asks to confirm the operation with a one-time code from a 2FA app
- Find the iTunes backup inside the Windows image and navigate to pictures inside on the Artifacts → Structure → iPhone → Pictures
- Among the pictures, there is a deleted screenshot of an export from the Google Authenticator app:

- You can import it into the Google Authenticator app or decode it with the tool https://github.com/dim13/otpauth, and generate a 6-digit code with the authenticator
- After entering the code, the bank gives out a CSV with the transaction history:
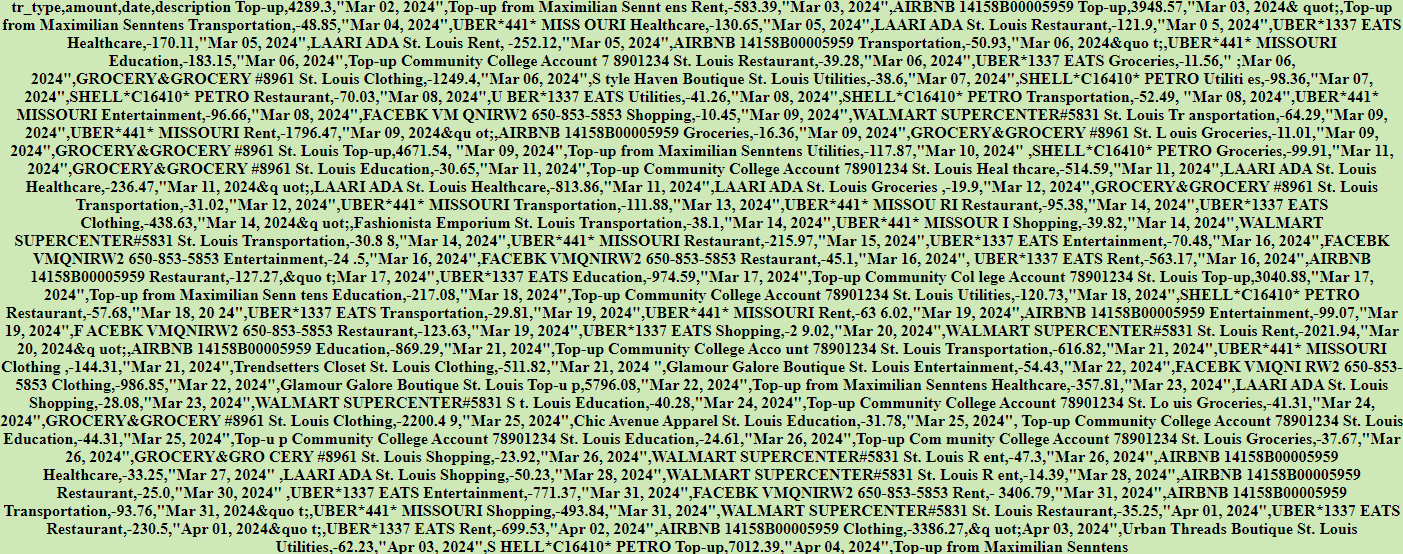
Wait, what? Seriously?
Raise your hand whoever knows about that "Acropalypse bug"? Anyone?
If you have Belkasoft X, there is the way simpler solution:
- What is we can find the full version of this screenshot? Navigate to Artifacts → Overview → Pictures, right click and run Analyze pictures → Detect text
- Once the OCR (text recognition) is completed, search for "LAARI ADA". You will get two more results that are located under the Windows temp folder:
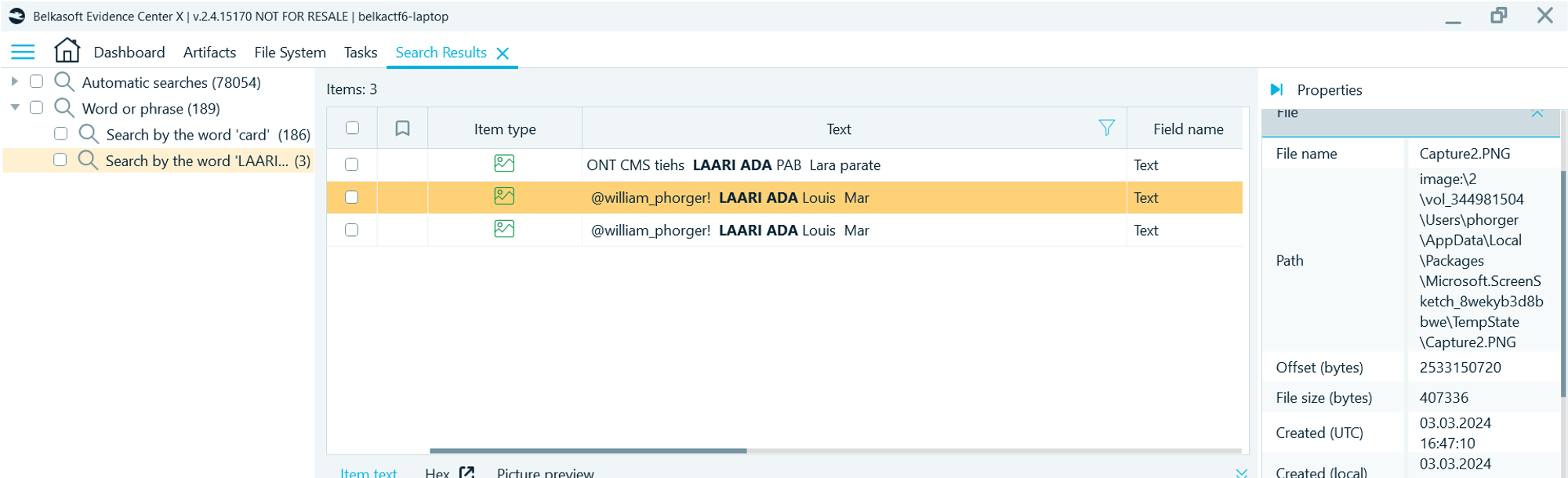
- One of these pictures is the full screenshot:
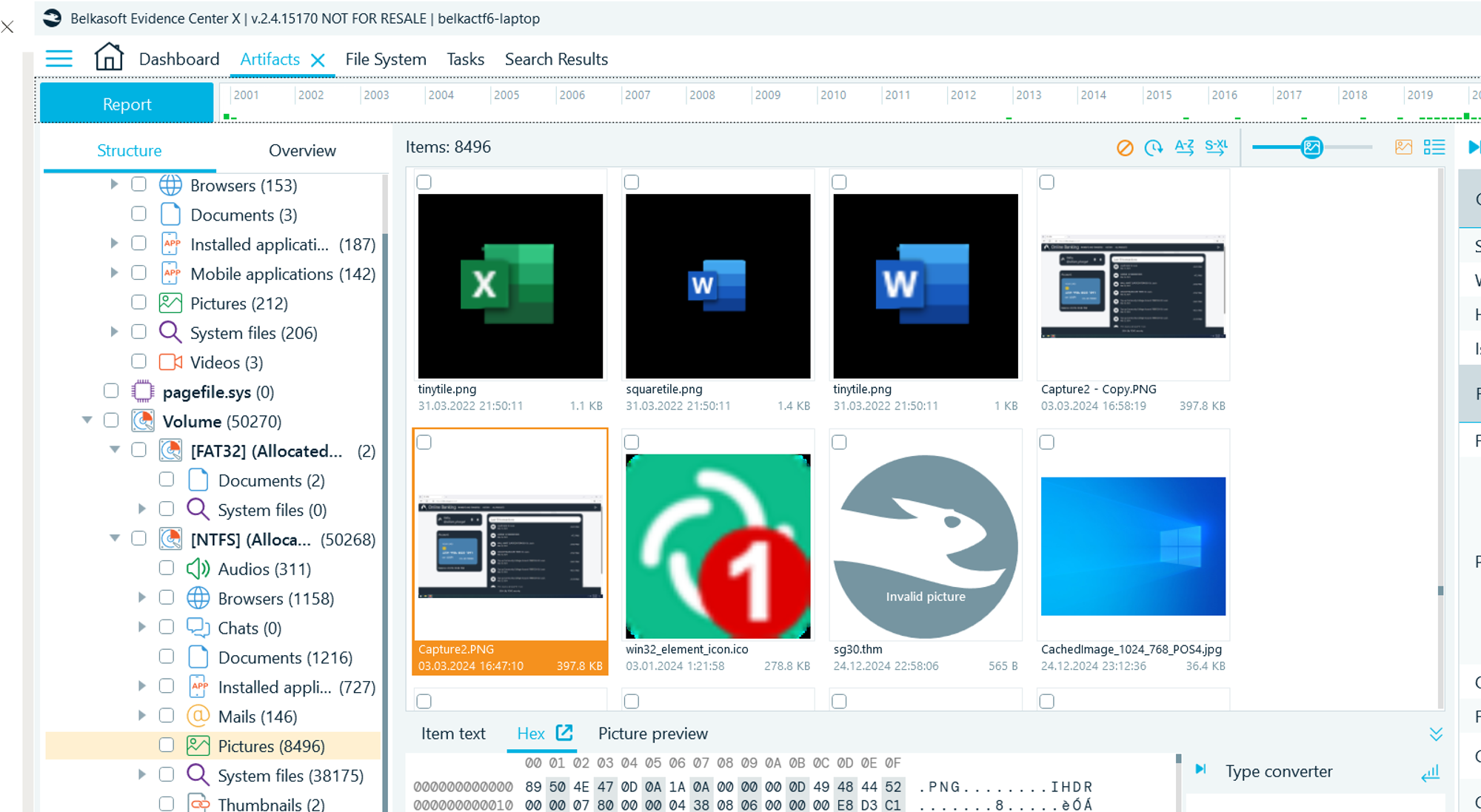
Now you can continue with the p.8 above.
We hope you enjoyed the CTF "Bogus Bill". If so, please share your feedback in your social accounts using #BelkaCTF tag. See you next time!
See also
- Enjoy past Belkasoft CTFs
- Learn more on the Belkasoft X product used for this write-up
- See Belkasoft's webinars on digital forensics and cyber incident response
- A Uni student or a professor? Check out our academic page!