Photo Forensics: Analyzing the Full Picture
Digital photographs often carry layers of embedded metadata, including timestamps, location data, camera details, and the name of editing software. This information can reveal a picture's origin, history, and potential manipulation.
Forensic photo analysis is not limited to identifying individual images but also extends to reconstructing sequences of events. In corporate investigations and criminal inquiries, such techniques can help DFIR experts analyze an individual's activity or track the movement of sensitive information. Belkasoft X enables investigators to extract, analyze, and interpret this information, whether the picture is a standalone file, embedded in another document, or recovered from deleted space.
This article explores the artifacts that occur in photos and demonstrates how Belkasoft X supports forensic workflows involving photo metadata. We will cover:
- What photo forensics can reveal
- EXIF: Metadata in forensic photo analysis
- Example: EXIF analysis of a real photo
- Finding embedded pictures
- Photo analysis techniques
- AI-powered photo forensics
What photo forensics can reveal
The structure of a digital photo, coupled with the processes involved in its creation, storage, and transmission, embeds a large amount of data. The key attributes and data points that forensic photo analysis can uncover are:
- EXIF metadata: Technical details recorded by the capturing device. This includes camera model, timestamps, lens, and exposure settings, and sometimes GPS data.
- Software indicators: Certain photo editing programs leave detectable fingerprints. These can help determine if a photo was altered or composited.
- File system metadata: You can uncover file creation, access, and modification dates, even after renaming or copying.
- Embedded pictures: Photos may be hidden inside documents, emails, or cached browser data. Photo forensic analysis techniques can extract these embedded pictures, which might contain useful information.
- Deleted or residual data: Even when the picture is "deleted," it is often not fully erased from a storage device. Forensic data carving techniques can recover fragments or entire deleted files, as well as residual data from overwritten files.
These attributes make digital photos incredibly valuable in forensic investigations as they can corroborate other evidence, attribute photos to suspects' devices, establish timelines, and more. A corporate investigator can leverage these artifacts for internal investigations in cases involving sensitive data exfiltration or corporate espionage.
EXIF: Metadata in forensic photo analysis
Exchangeable Image File Format (EXIF) metadata provides essential forensic context. It records capture conditions, device identity, location, and post-processing details.
The table below lists the common EXIF tags that can be extracted from photos along with their forensic utility.
|
Tag Name |
Description |
Forensic Significance |
|
Make |
Manufacturer of the recording equipment (camera, phone, drone) |
Identifies the specific brand of the device used to capture the photo, aiding in device attribution |
|
Model |
Model name or number of the recording equipment |
Pinpoints the exact model of the device, offering specific attribution and insight into device capabilities |
|
DateTimeOriginal |
Date and time the picture was originally captured |
Establishes the precise moment an event occurred, useful for timeline reconstruction |
|
DateTimeDigitized |
Date and time the picture was converted to digital data |
Can show when an analog picture was digitized, or a copy was created |
|
GPSLatitude, GPSLongitude, GPSAltitude |
Coordinates and altitude where the photo was taken |
Pinpoints exact location, useful for linking individuals to places |
|
GPSTimeStamp |
Time and date of the GPS reading at capture |
Provides an accurate, synchronized timestamp tied to the GPS data |
|
Software or ProcessingSoftware |
Name of the software used to process the picture |
Indicates whether and how an photo may have been edited |
|
Orientation |
Picture orientation (e.g., rotated) |
Can reveal changes to photo layout or post-capture edits |
|
ImageDescription |
Free text description of the picture |
May contain user-added context or original file naming |
|
Artist |
Creator or owner metadata |
May identify who captured or processed the photo |
|
Copyright |
Rights information embedded in the file |
Useful in copyright or intellectual property disputes |
If a photo contains GPS coordinates, it can help you verify travel routes, link users to locations, or corroborate alibis. When correlated with other artifacts, geolocation provides a spatial context for user activity.
Other types of EXIF data can also provide valuable insights:
- Camera settings (for example, aperture, shutter speed) can indicate ambient light or movement
- Device details, such as serial numbers, can support device attribution
- Editing traces (software-related fields) may indicate tampering or re-encoding
You should always correlate EXIF data with file system metadata to confirm authenticity and detect inconsistencies.
Example: EXIF analysis of a real photo
Now, let us examine a real photo with Belkasoft X.

A photograph of the Chalaadi glacier in Svaneti, Georgia
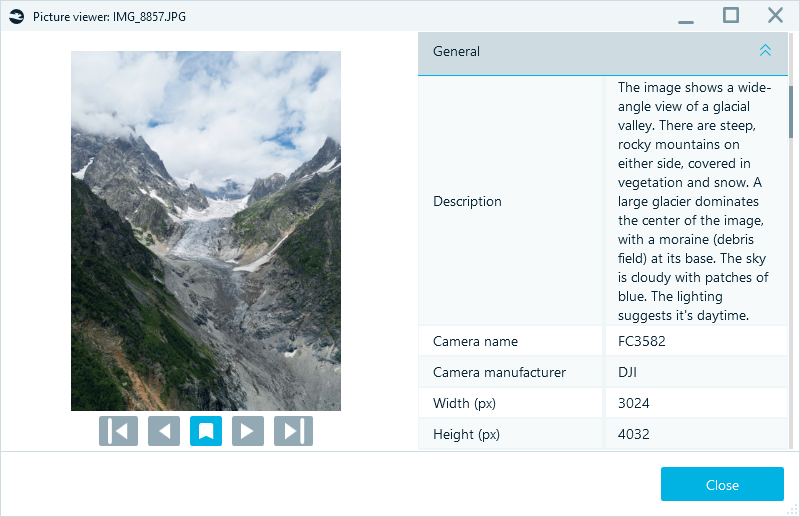
First, you can view extracted EXIF metadata displayed in the Properties pane of the Artifacts window. You can also find it in the embedded Picture viewer, which opens files directly within the software:
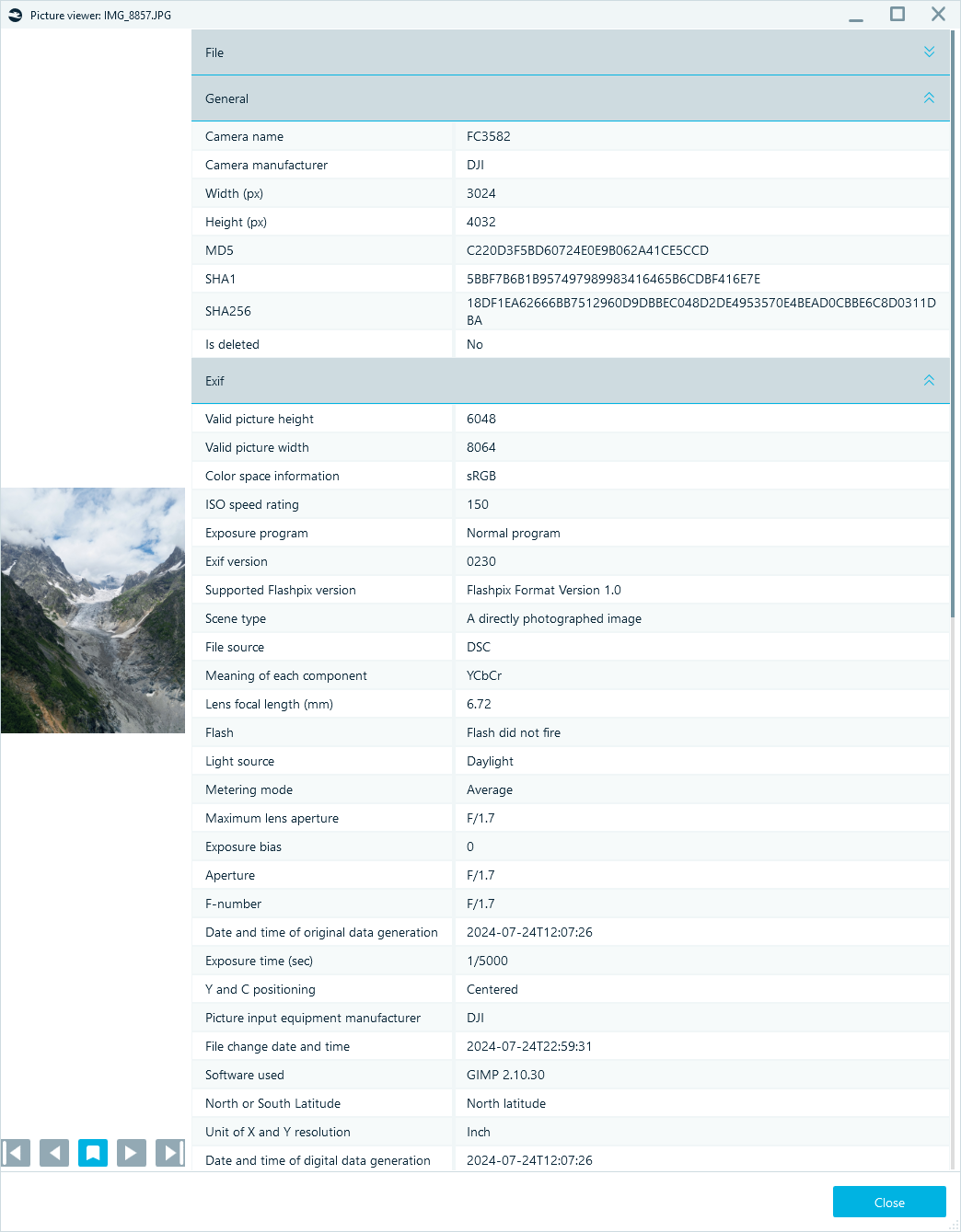
Picture viewer with EXIF data in Belkasoft X
EXIF records reveal the following details:
- Device and software info show the photo was captured by a DJI drone model FC3582 and later edited with GIMP
- GPS coordinates place the photo in the Caucasus Mountains at over 2,300 meters
- Timestamps from DateTimeOriginal and DateTimeDigitized specify that the photo was taken on 2024-07-24 at 12:07 and are consistent, indicating no re-encoding
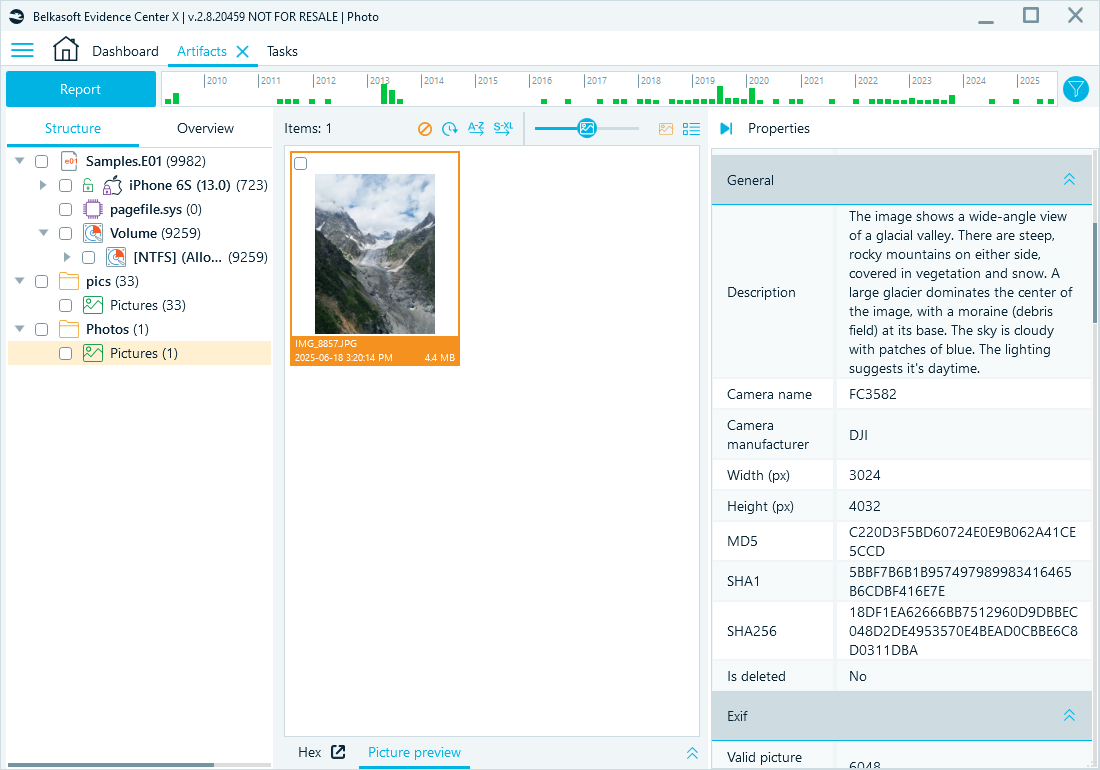
Reviewing photos in the Artifacts window
- In the Map window, the exact location appears visually:
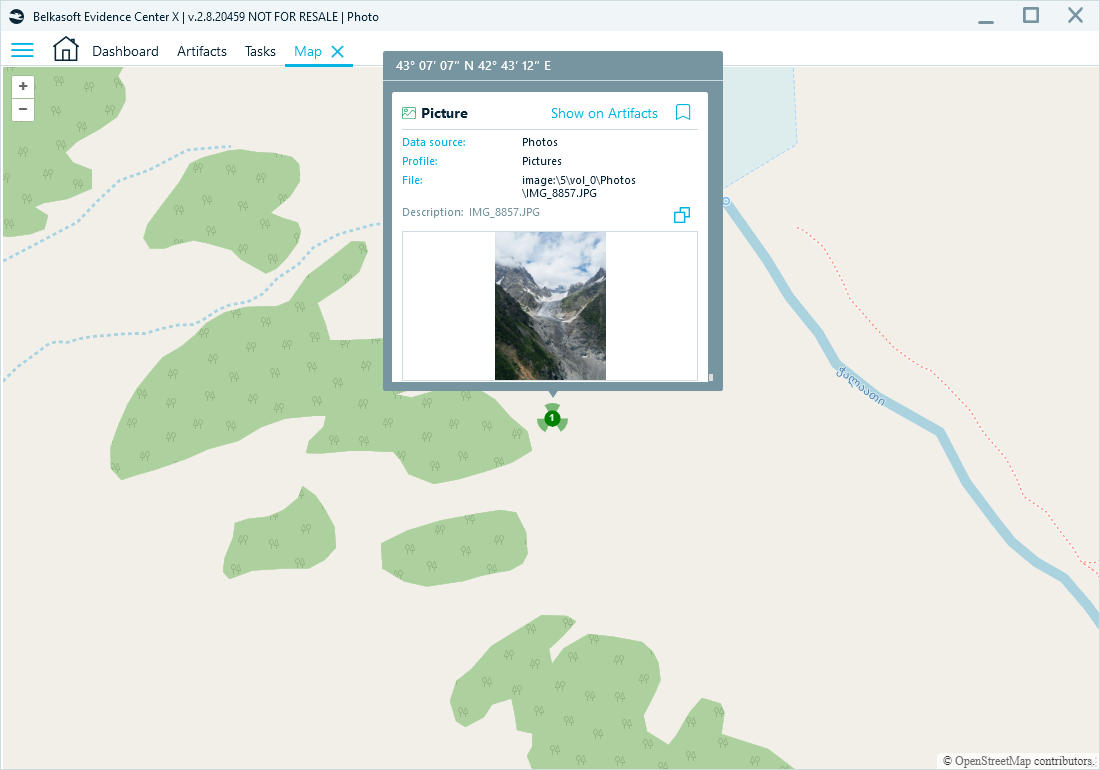
Photo geolocation shown in the Map window
- In the Timeline window, the photo displays under the Media category. Other timeline events that appear near the photo's file system timestamps indicate that it was downloaded with a browser on 18 July, 2025.
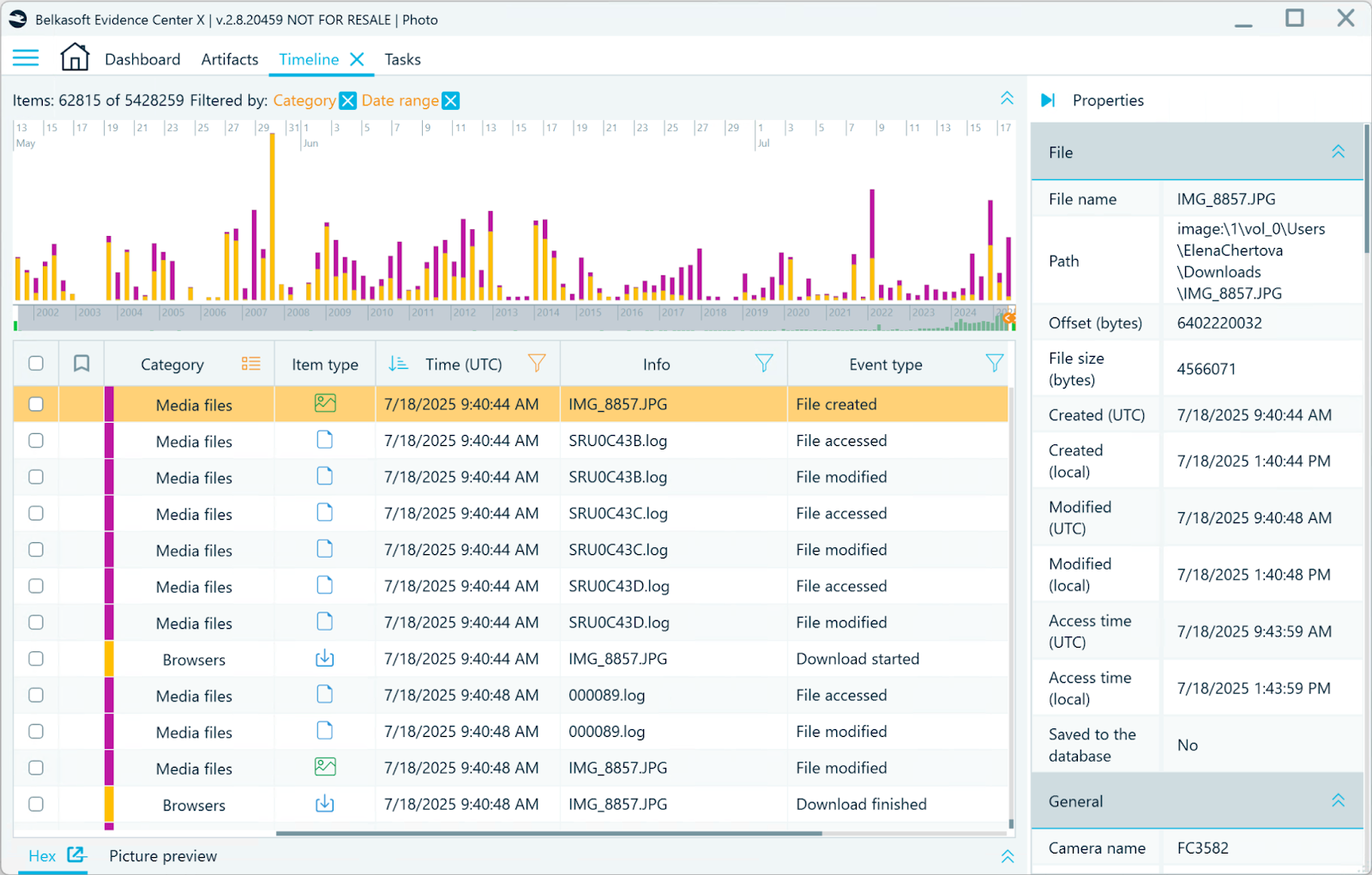
The target photo found in the Timeline window
- The File System window provides additional information on the photo, such as its location in the data source and MFT timestamps. In this example, you can also find an Alternative Data Stream (ADS) Zone Identifier record which reveals that the photo was downloaded from Google Drive.
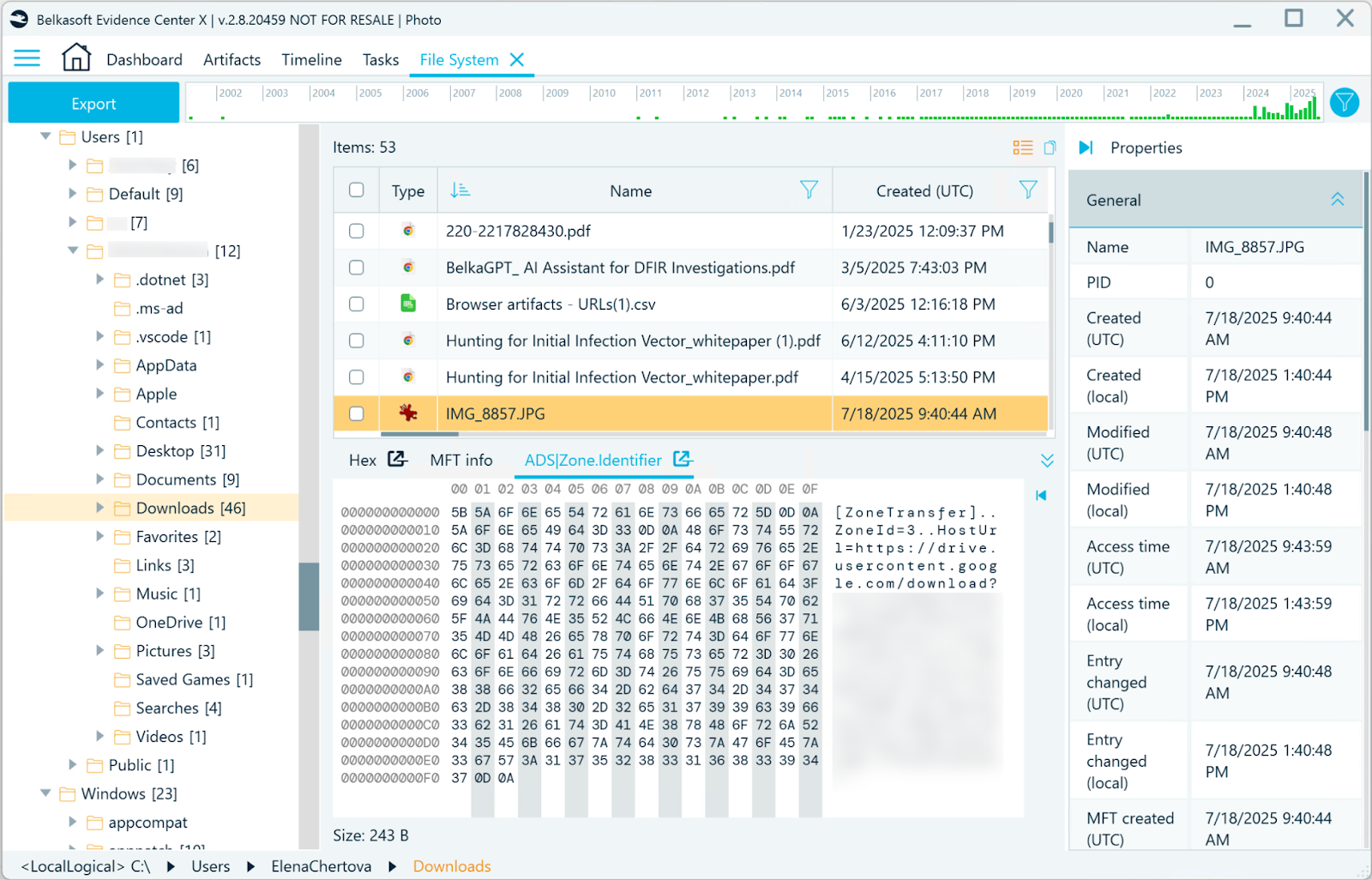
The target photo found in the File System window
This single photo demonstrates the depth of information available through EXIF analysis alone. However, Belkasoft X supports a much broader set of techniques for analyzing and recovering picture-based evidence.
Finding embedded pictures
When analyzing a data source, Belkasoft X automatically searches and extracts pictures that are part of the following file types:
- PDF documents
- Microsoft Office files
- Email attachments
- Instant messenger databases
- Web browser cache and more
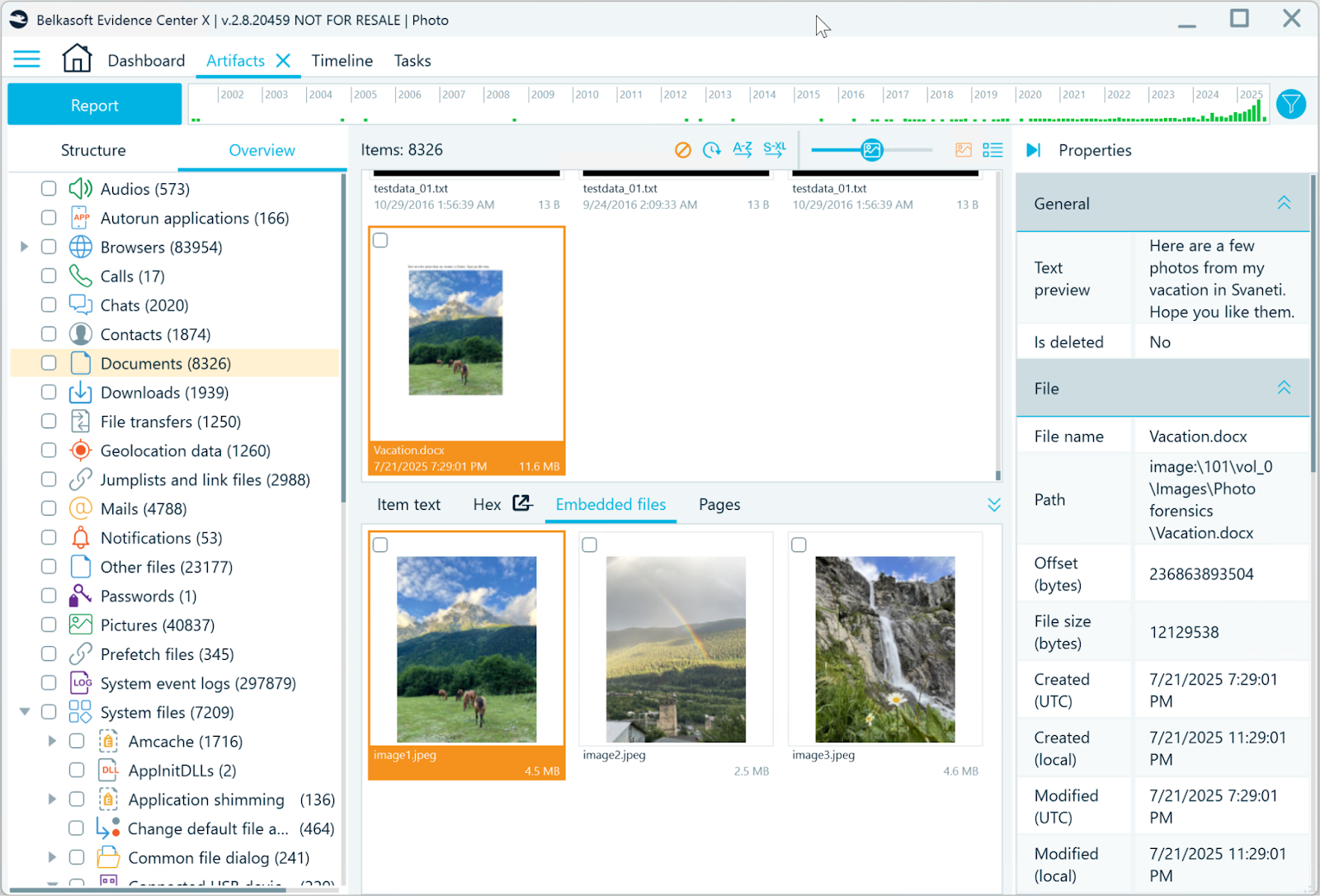
Photos extracted from a .docx file
By enabling Analyze carved and embedded data in analysis settings, you can extract additional data from embedded photos and apply picture-specific analysis techniques. This capability is especially valuable in corporate investigations that often involve large volumes of PDFs, Office documents, and emails, many of which may contain images. Manually reviewing each file in such cases is typically impractical.
You can learn more about embedded media analysis techniques in our articles about media file forensics, document forensics, and email forensics.
Belkasoft X also supports carving and recovery of deleted pictures from free and unallocated disk space, application caches, SQLite databases, and backups.
Photo analysis techniques
After extracting all metadata and embedded pictures, you can use various techniques to automate the discovery of the photos of interest:
- Content classification to detect faces, nudity, weapons, or skin exposure
- OCR to extract searchable text from screenshots and scanned documents in over 50 languages
- Video keyframe extraction for efficient visual review
- Hashset analysis using known datasets such as NSRL and Project VIC
AI-powered photo forensics
Beyond basic classification, you can use picture analysis with BelkaGPT—a multi-modal AI assistant that generates text descriptions of scenes and objects occurring in the photos. This feature facilitates the search for case-relevant photos and helps discover evidence faster.
Belkasoft X's picture viewer window with a detailed description of the target photo
With such analysis capabilities, investigators can:
- Look for pictures using keywords for objects or appearance and clothing of individuals
- Identify connections between photos and other artifacts, such as chat messages and emails
- Ask BelkaGPT to find and reference artifacts using natural language queries:
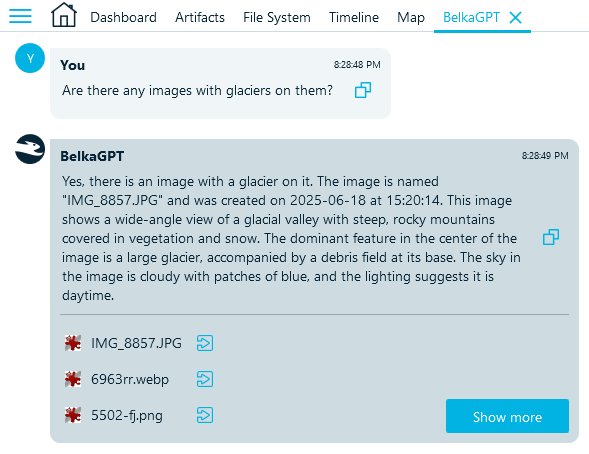
BelkaGPT window referencing all photos with glaciers it found
Conclusion: Reveal more with every picture
A single photo can offer far more than just visual content—it may contain timestamped, geolocated, and device-linked data that is critical to any investigation. With the right digital forensic tools, this hidden information can be extracted and turned into a meaningful narrative.
Belkasoft X equips investigators to perform in-depth forensic analysis of photos while streamlining evidence review. This all-in-one solution supports a wide range of photo forensics tasks, including:
- Extracting EXIF, geolocation, and file system metadata
- Analyzing embedded photos and their metadata
- Recovering deleted and hidden images
- Visualizing photo data on timelines and maps
- Identifying case-relevant images with advanced analysis techniques
From corporate investigations into employee misconduct or insider threats to criminal cases involving CSAM or drug trafficking, Belkasoft X helps transform ordinary pictures into structured, verified digital evidence—making every pixel part of your case story.

