BelkaCTF “Kidnapper Case” write-up
The fourth BelkaCTF was conducted on March 11th & 12th, 2022. The CTF started at 11:00 AM UTC on the 11th and lasted for 24 hours. The CTF page was https://belkasoft.extremeroot.com/ and the tasks were prepared for you by Belkasoft and ExtremeRoot teams with the tool sponsorship by Passware.
This is an official write-up on how the tasks were supposed to be solved. There are naturally more ways to solve these tasks, and we encourage you to read contestants' own write-ups.
Note that every task could be solved without Belkasoft X product, so even if one missed our trial or had any issues with it, it should not have stopped them from giving correct answers.
Did you like this CTF?
This time the plot was a bit mysterious. From the CTF name and the dialogue between the main hero (you) and the Chief, you might have guessed, that a son of a high-profile person was kidnapped, and that the son was fond of computers. His laptop was seized and had to be analyzed by the protagonist.
Let's begin taking flags!
1. Users (Baby—100 pts)
Question
List all users of the laptop. (Format: username1, username2, username3)
This task had a little misleading hint hidden in the flag format. Some of players thought there must be 3 users. However, please have in mind that the flag format relates to the format only (commas, spaces, time type, etc.), not to things like number of answers.
Solution without Belkasoft X
- Load the image file into a forensic viewer of your choice, browse the file system to the main partition.
- Navigate to the home directory.
- The users of this machine will be listed.
Solution with Belkasoft X
- Create a new case and add the E01 file as an image data source.
- Analyze the image, selecting all artifacts to be extracted.
- Navigate to File System → Partition Allocated space, Ext4 → /home. There you will find the two users of the system... OR
- Navigate to File System → Partition Allocated space, Ext4 → /etc/passwd → open passwd file in Hex Viewer and scroll to bottom to see the added users:
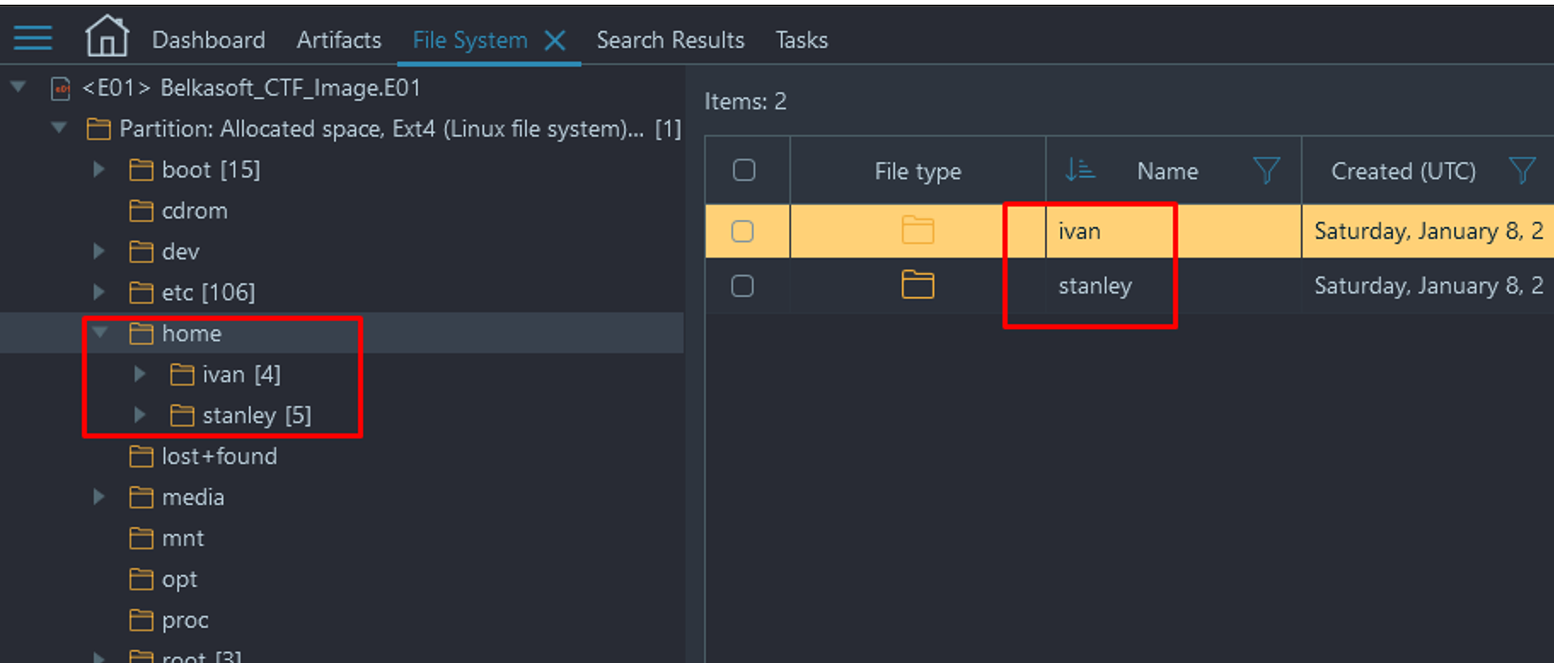
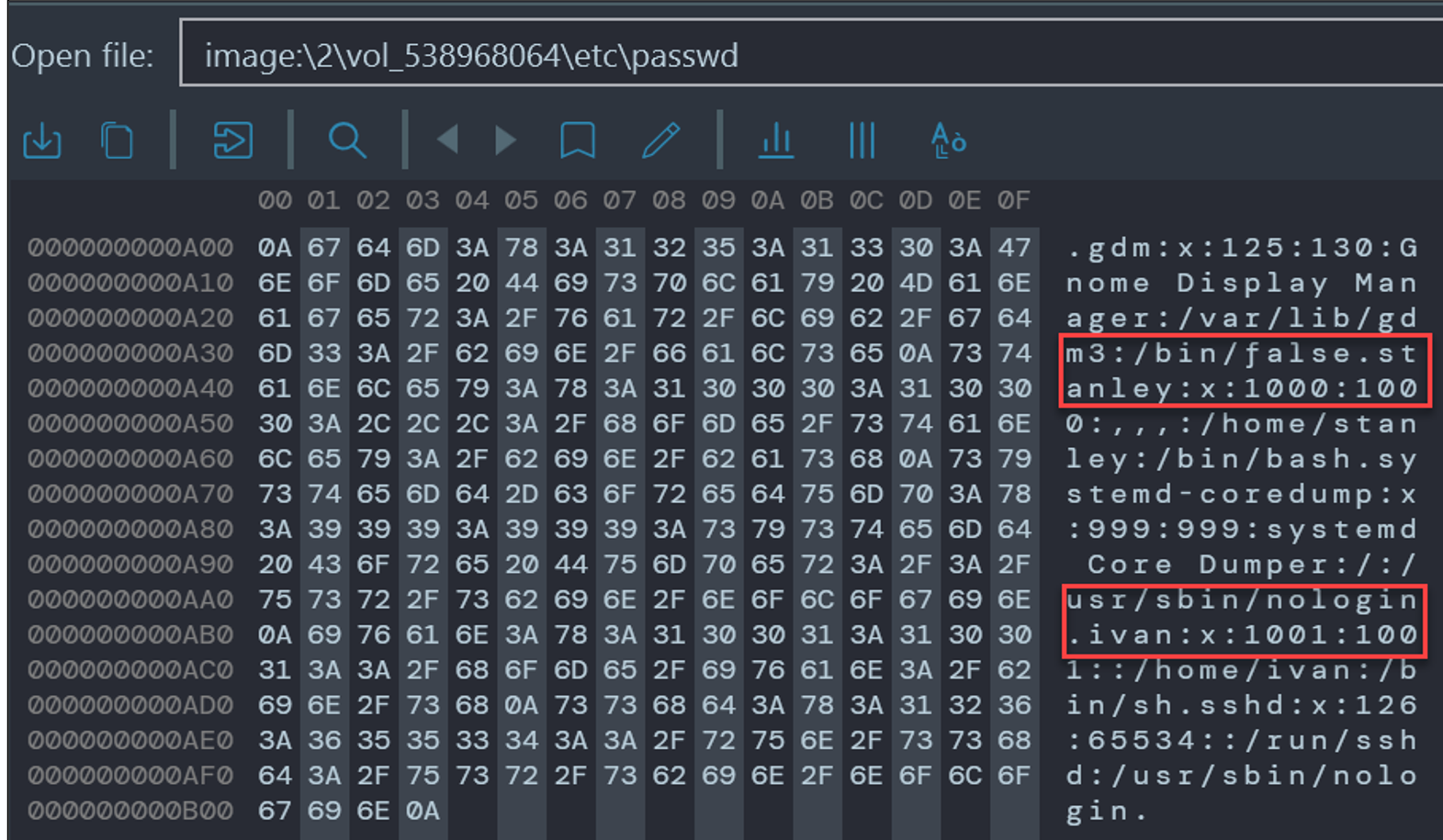
Flag
ivan, stanley (this task was solved 191 times)
2. Special Website (Baby—100 pts)
Question
What web application was used by the boy to earn his pocket money?
Solution without Belkasoft X
- Load the image file into a forensic viewer of your choice and look for browser data. In this instance it will be from: (\home\ivan\.mozilla\firefox\yyxsdegu.default-release\places.sqlite).
- Navigate to the above database and search for a website that looks like it may be hosting products for the victim's side job.
- The https://x-tux-0.web.app URL can be found under moz_places in the places.sqlite database.
Solution with Belkasoft X
- Navigate to Artifacts → Browsers → URLs → Search for any sort of website that may be hosting products for our victim's side job.
- You can either filter for a product name or simply scroll the list looking for a website that fits the description. As there are only 229 URLs to look through this second option may be more feasible.
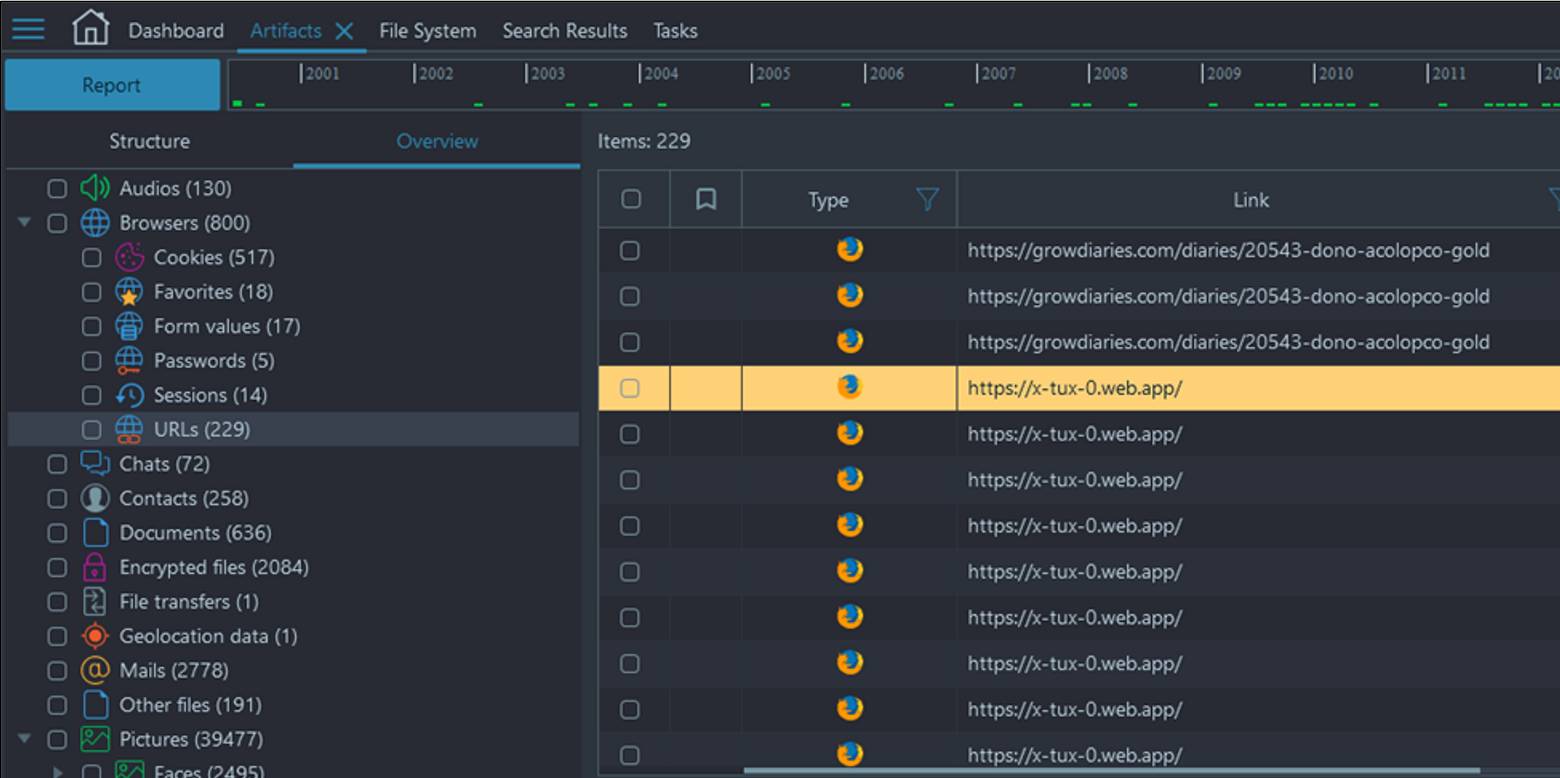
Flag
https://x-tux-0.web.app (this task was solved 166 times)
3. Wallet (Baby—100pts)
Question
Which BTC wallet did the boy use to sell drugs?
Solution without Belkasoft X
- From the last question, we have identified that website that was being used to host these illegal products, let's try to browse the URL to see if it is a live site.
- The link is still alive, now we can browse to one of the products. Upon inspection of the page, we can see that the seller of the products has posted a Bitcoin wallet so that buyers can pay him directly. This is your flag.
Solution with Belkasoft X
- Same solution as above, now that we have identified the web application that is being used under Artifacts → Browsers → URLs, we can browse to this website.
- Now that we are on the website, we can select a product and see that the sellers Bitcoin wallet is hosted at the bottom of the webpage.
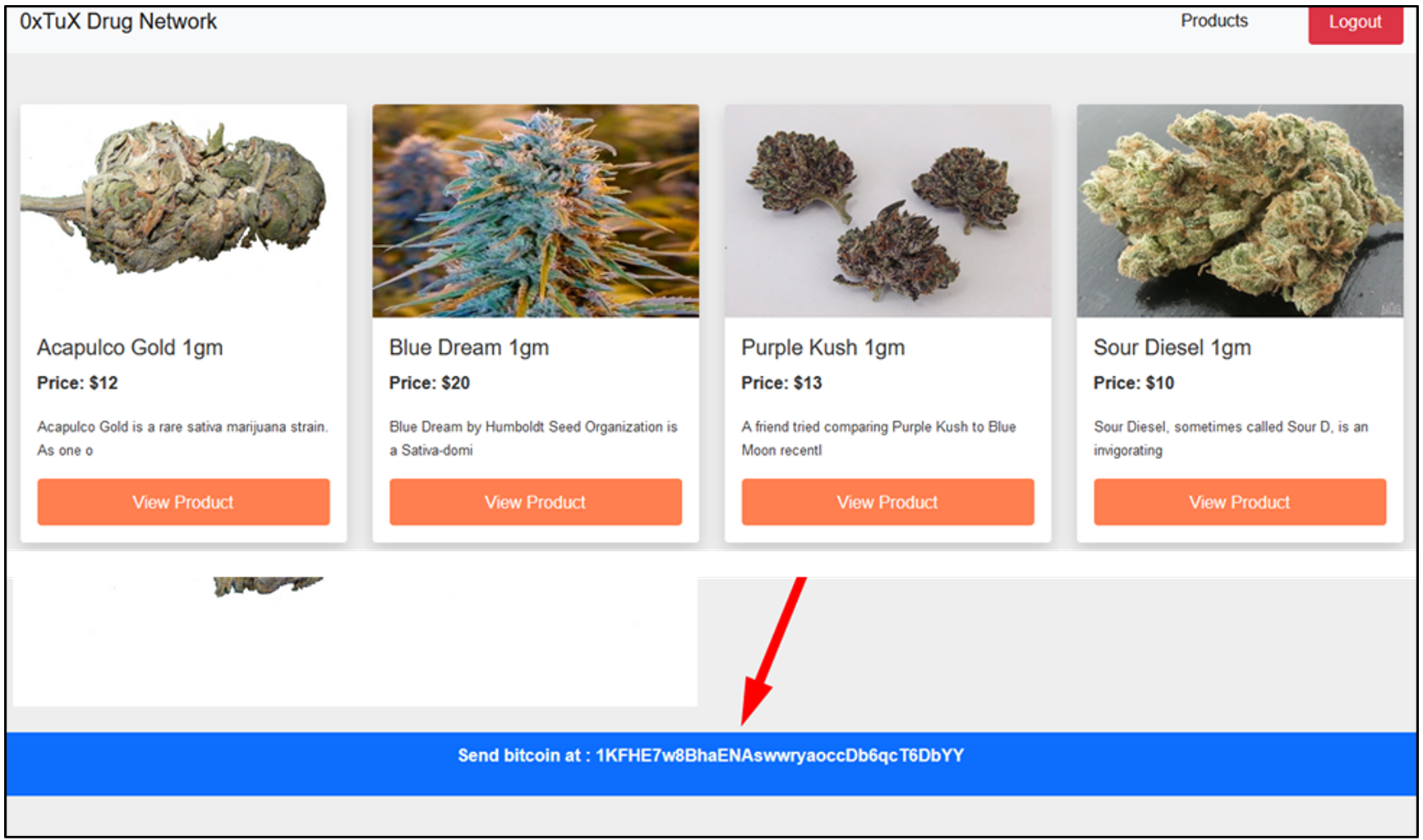
Flag
1KFHE7w8BhaENAswwryaoccDb6qcT6DbYY (this task was solved 105 times)
4. Passme (Moderate—500pts)
Question
On which date does the kid's database show the most sales for "Acapulco Gold"? (Format: YYYY-MM-DD)
Solution without Belkasoft X
- In a forensic viewer of your choice, navigate to the home/Stanley/.db/Dec.
- Export the Monthly_DB.zip file.
- Utilize a password cracking tool to crack the password for the database
(e.g. John The Ripper).
- Run "sudo apt install john" once it has completed its download to install the package.
- Then utilize zip2john against the Monthly_DB.zip file and push the output to a hash.txt file
- Next, we will utilize "john" and point the wordlist to the hash.txt file:
- Utilize a searching function to narrow down the most sales from all of the .CSV files, which will give you your answer (2021-05-12)
Solution with Belkasoft X
The solution for this task varies a bit between the trial and fully featured version of Belkasoft.
- Navigate to Artifacts → Overview → Mails and search for an attachment that references "Sell Database".
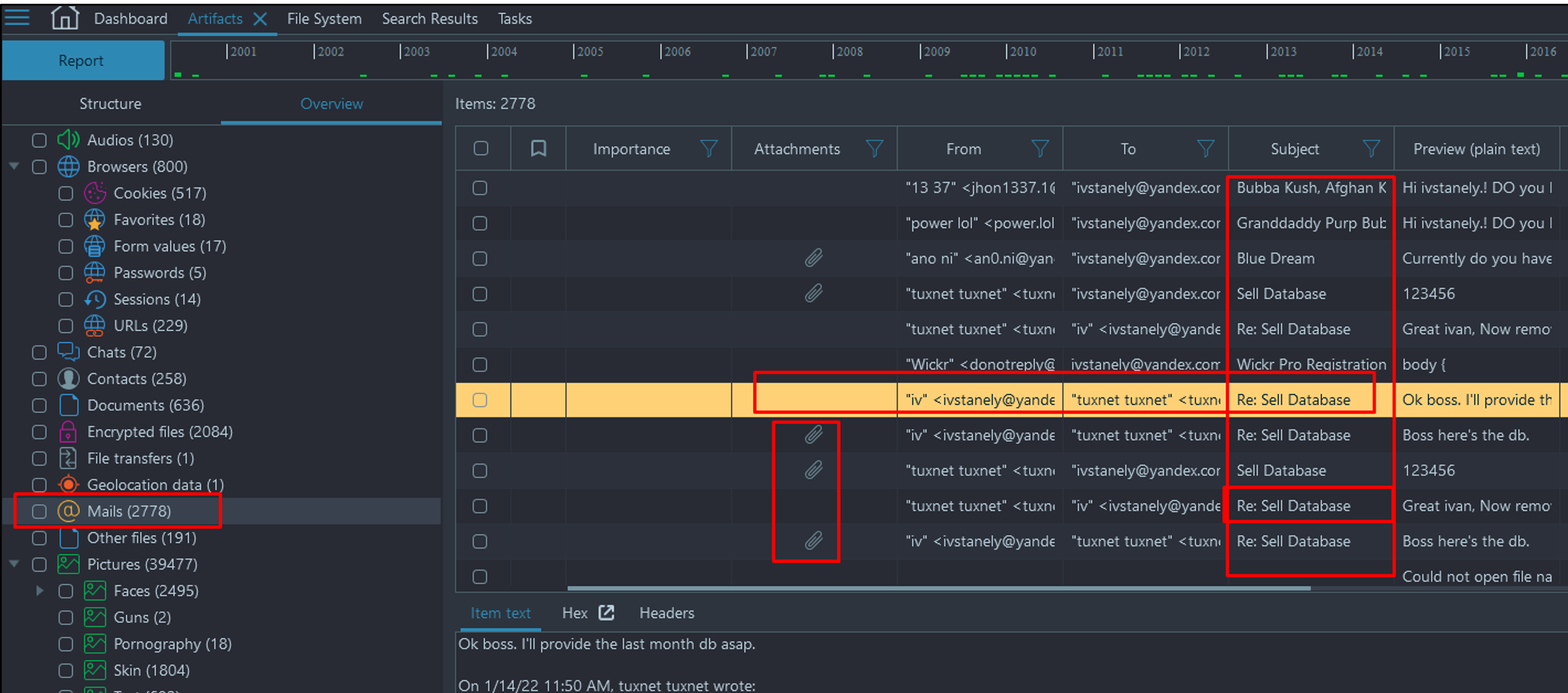
- One of these attachments is labeled "Monthly_DB.zip", but it appears to be encrypted.
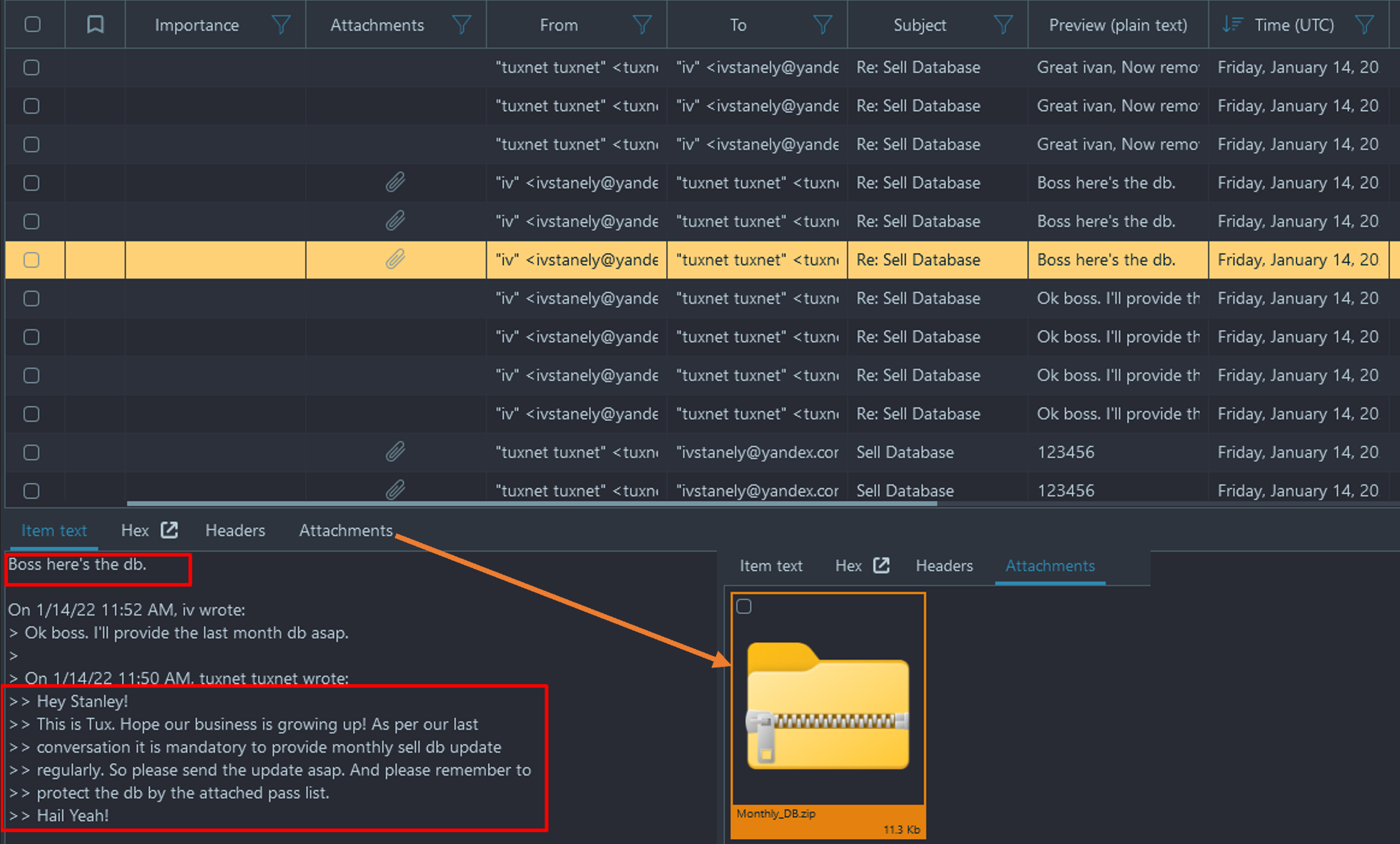
If you have the trial version of Belkasoft X:
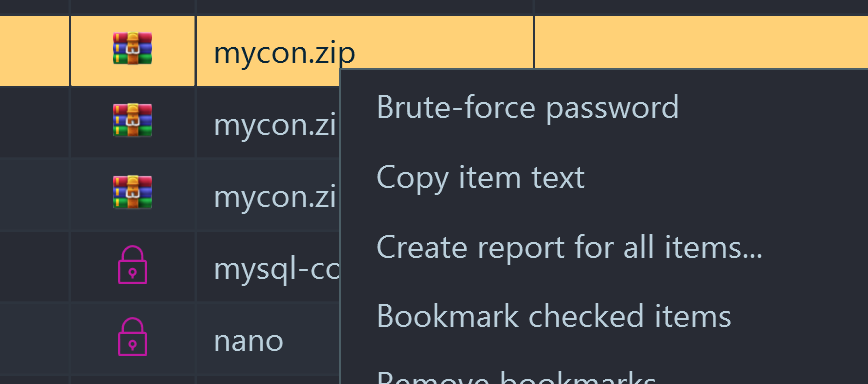
- Right-click and choose "Copy files to folder".
- Within the Mails tab, we can see there is also another file that seems to be a password list titled "10-million-password-list-top-1000000.txt". This file is actually truncated so you have to first download the original one from the corresponding GitHub and use against the zip folder found in step 2.
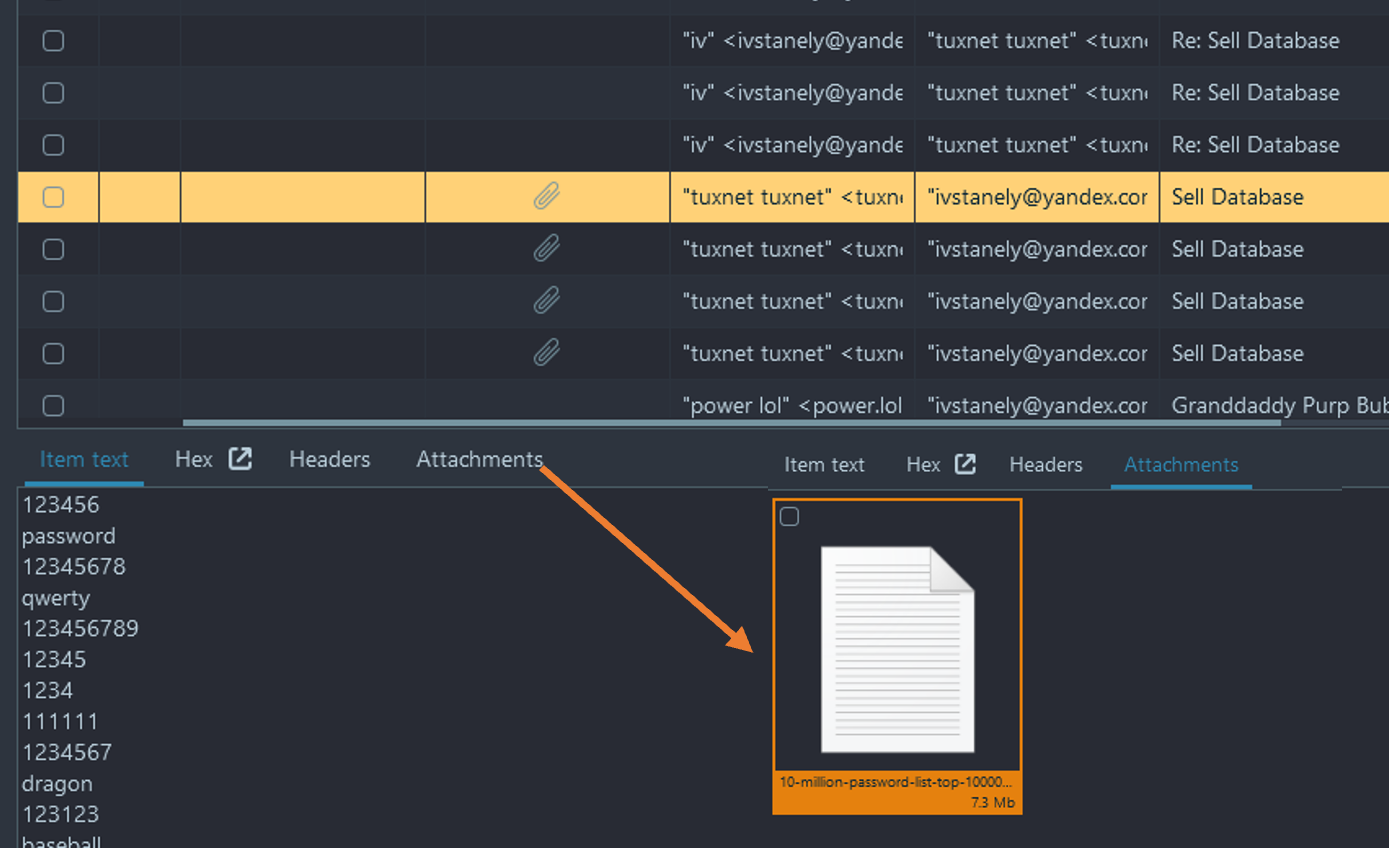
- Use Passware Kit Forensic, provided you along with the Belkasoft trial. Passware can decrypt an encrypted file using a dictionary provided. Use 10 million passwords file to find the password almost instantly.
If you have the full version of Belkasoft X:
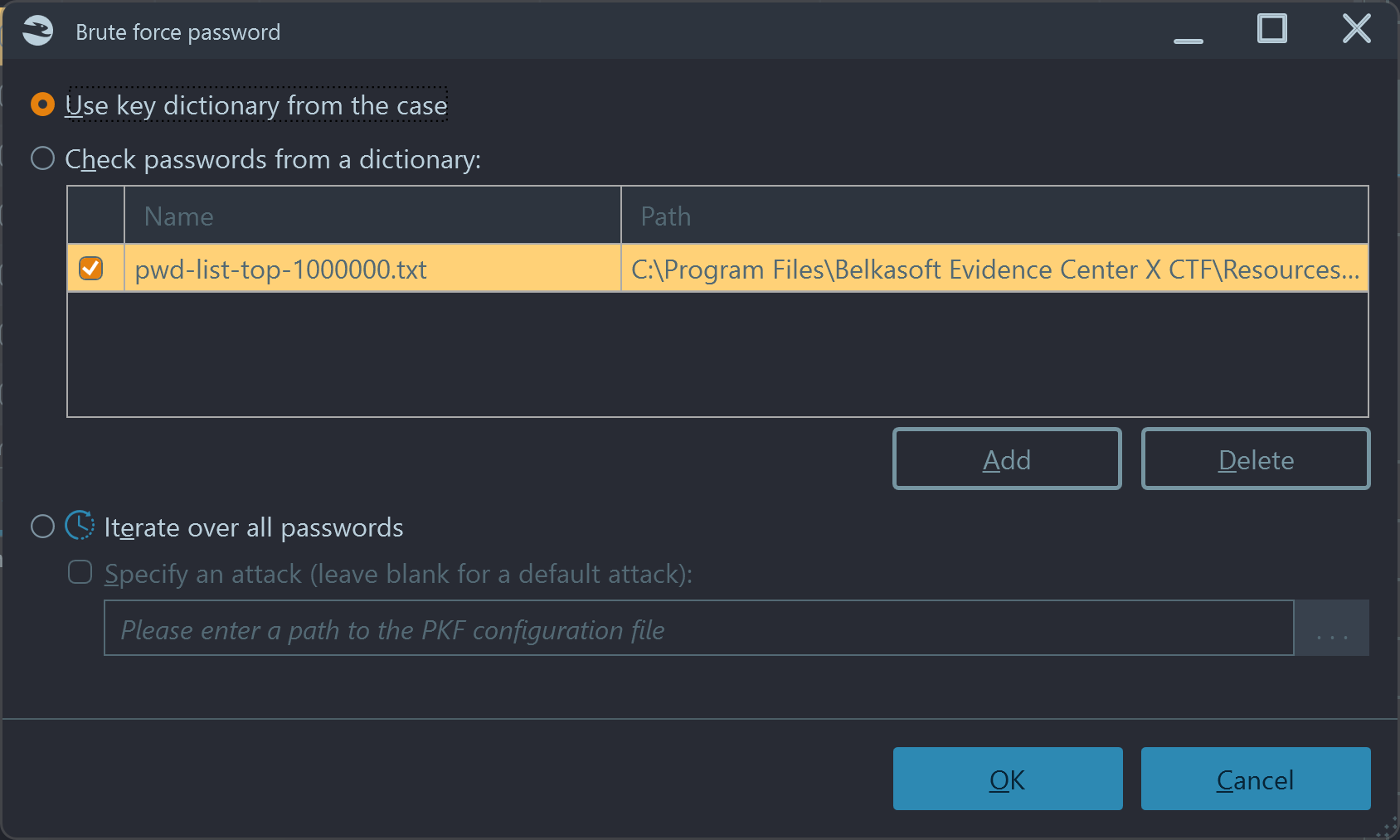
- Belkasoft has a nice option of an encrypted file brute-force based on key dictionary. This option will test all terms found in the case and since the password is stored somewhere in the case, you do not even have to look for it.
- Alternatively, if you found a hint about 10 million password file, you can also use the built-in option of decryption based on a dictionary.
Now that we have the password, we can use it to open the Monthly_DB.zip and search for what day had the most sales. Analysis of the files inside reveals that May 12th, 2021 was the date with the highest sales.
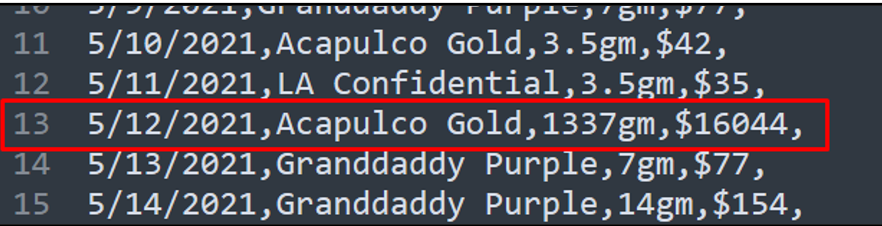
Flag
2021-05-12 (this task was solved 86 times)
5. Cryptlet (Tricky—750pts)
Question
What was the other BTC wallet of the victim, which he used to hide his "under the counter" sales from his superior?
The task name has a hint: this must be something about a wallet, which is somehow hidden.
Solution without Belkasoft X
- In a forensic viewer of your choice, navigate to the home/ivan/Documents/.custom (a hidden directory).
- Notice all files have mismatched extensions, try to change all extensions to PDF, only two will not change. Let's add a PDF header to the file 101.bin
- Replace the first 4 bytes on the file titled "101.bin" to a PDF header "25 50 44 46" and the document will show up as an invoice.
- Your flag is at the bottom of the invoice.
Solution with Belkasoft X
- Navigate to Artifacts → Overview → Pictures → Text.
- You will notice that the victim has invoices of his sales that Belkasoft was able to pull text out of. Unfortunately, the text is blurry and unreadable.
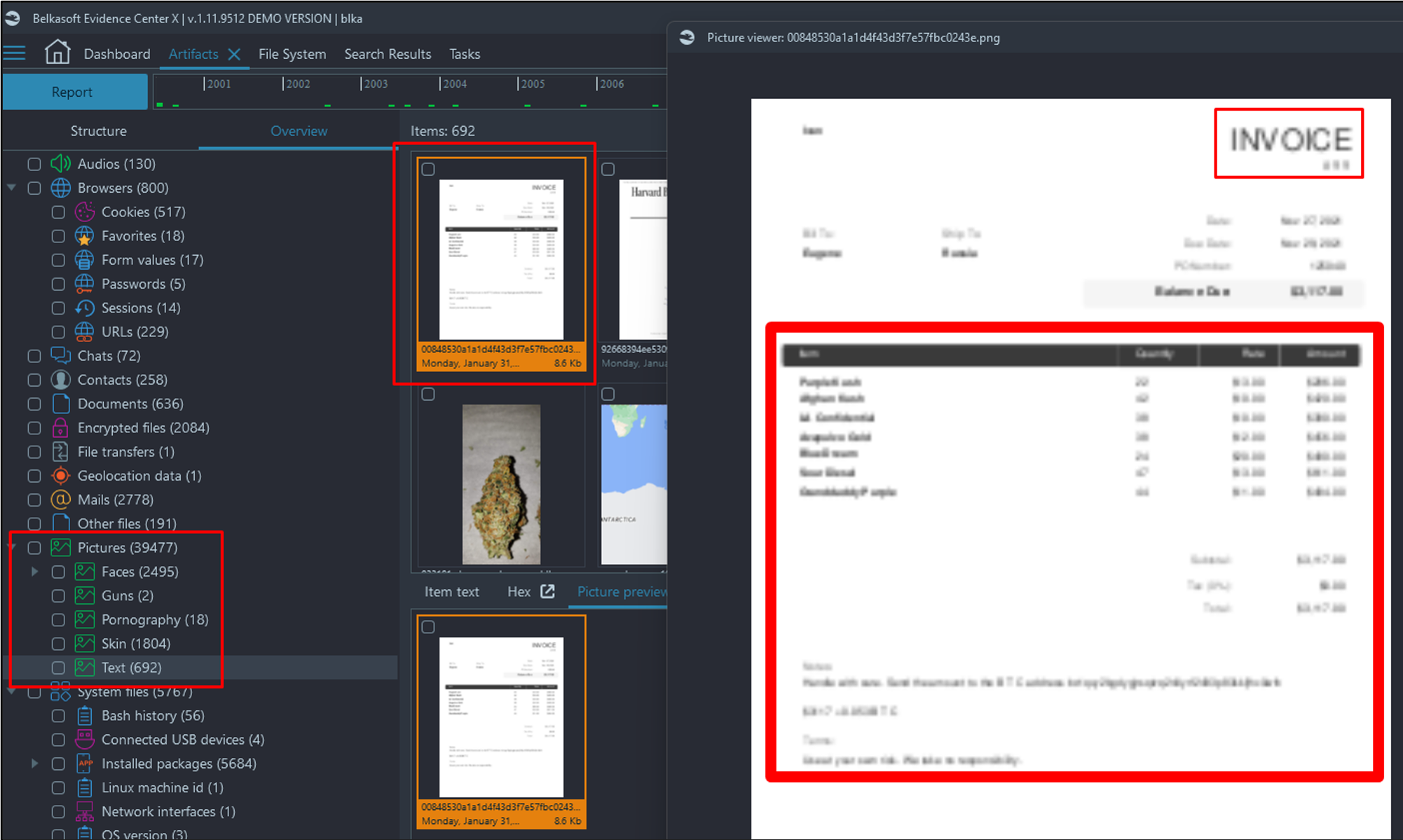
- Next, lets navigate to the bash history file to see what the victim was up to last. Artifacts → Overview → System files → Bash history.
- The victim has recently used Hexdump as well as a Hexedit tool, a commonly used tool for modifying file signatures. Further analysis shows that the file name that was used with Hexedit was "inv".
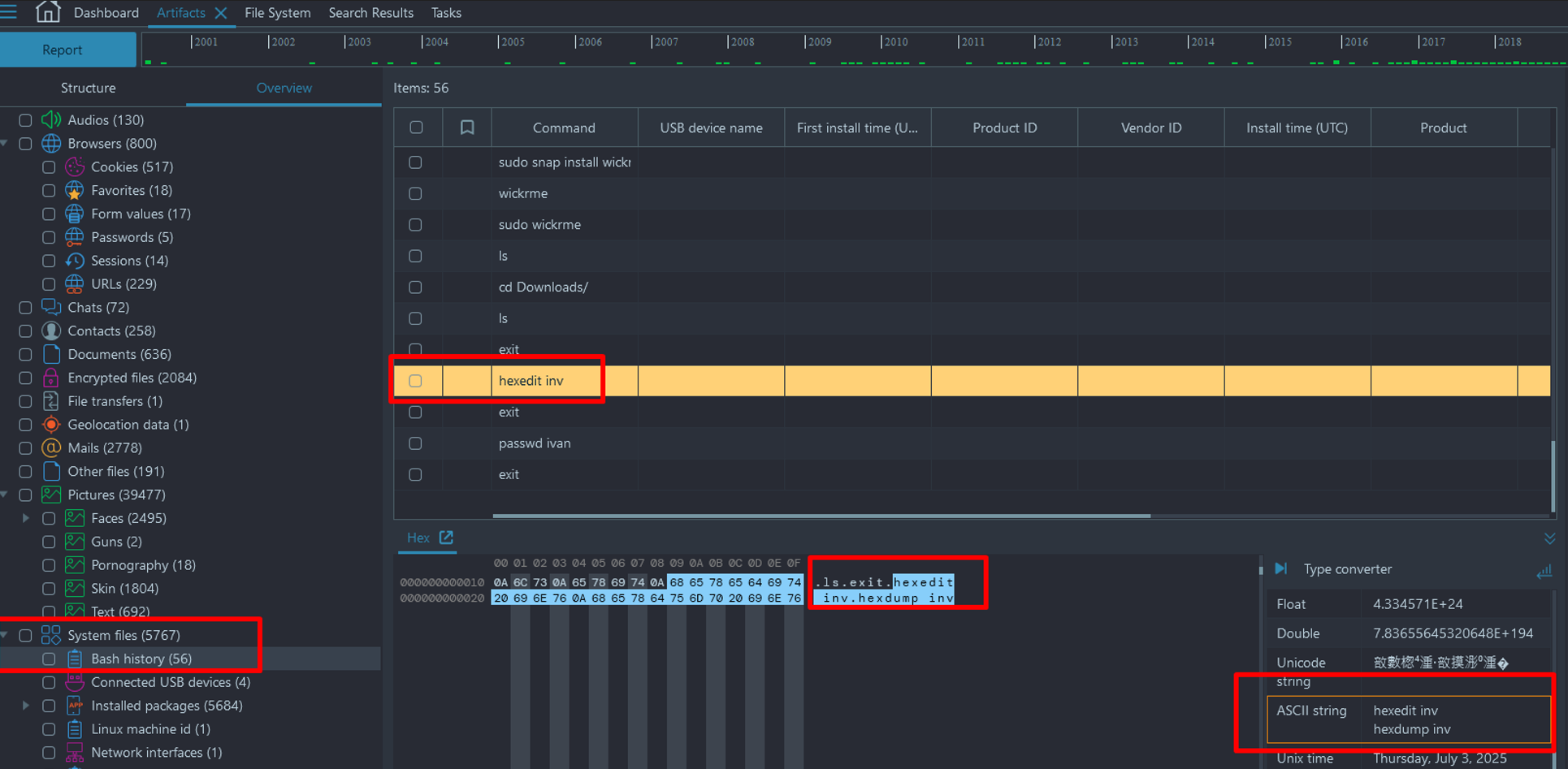
- Searching through the rest of the image we can find a few files titled "Inv". They can be found by navigating to File System → Ext4 → home → ivan → Documents → .custom (hidden directory).
- A quick glance at these files show that they are mostly PDFs with renamed extensions.
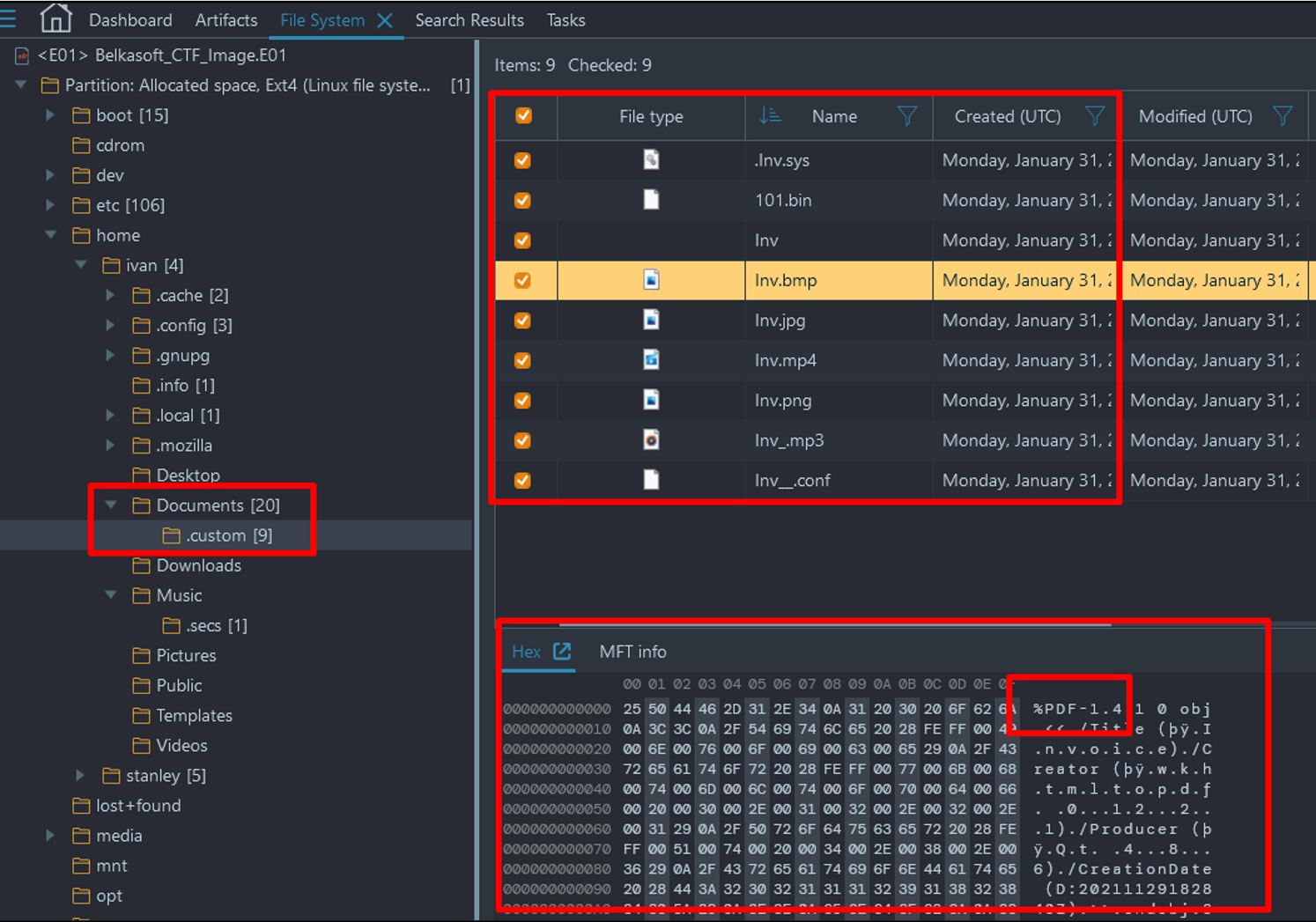
- Copy the all files in this directory to a folder and change extension on them. Of these files, only two are corrupt after changing the extension. Open a hexeditor tool or use an online tool such as https://hexed.it to replace the file header of 101.bin with "25 50 44 46". The document can now be opened as a PDF which displays a bitcoin wallet at the bottom of the invoice.
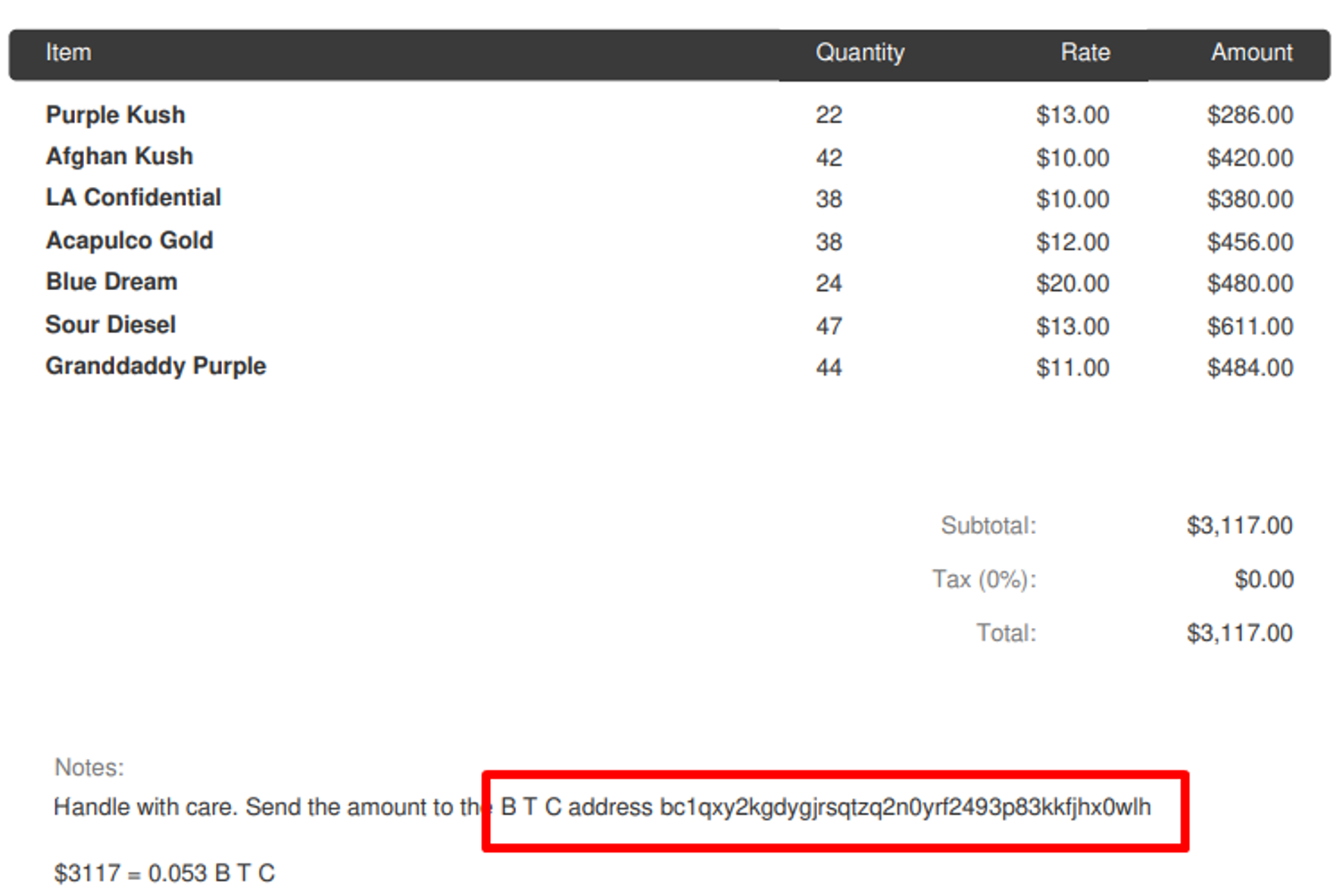
Flag
bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh (this task was solved 51 times)
6. Notipass (Tricky—750pts)
Question
What is the password to the boy's notes?
Again, the hint was hidden in the task name, which was a combination of "notes" and "password".
Solution without Belkasoft X
- In a forensic viewer of your choice, start by searching for "note" you should be brought to the root/home/Stanley/Documents/mynote directory.
- One of the files "notes" does not have an extension, but based off of the other note in the directory, we can try to change the extension to .odt.
- While trying to open the file, you are prompted for a password.
- The plot (and the picture) threw out a hint talking about containers, meaning the password is probably hidden inside another document. Browsing the file system you may have stumbled across a PDF titled "NOTHING_IMPORTANT_INFO.pdf". This was important—*Cough, cough*.
- Throwing the file into a online tool such as Cyberchef and decrypting it with "from Base32" and "Rot13" (another hint, the password for the system image was Base32) will display all passwords—see the one labeled as "note".
Solution with Belkasoft X
- Navigate to Artifacts → Overview → Documents and perform a search for "note" in the "File name" column.

- Only one file is labeled note. If we right-click this file and choose "Show on Structure" we can see where this file is located on the system.
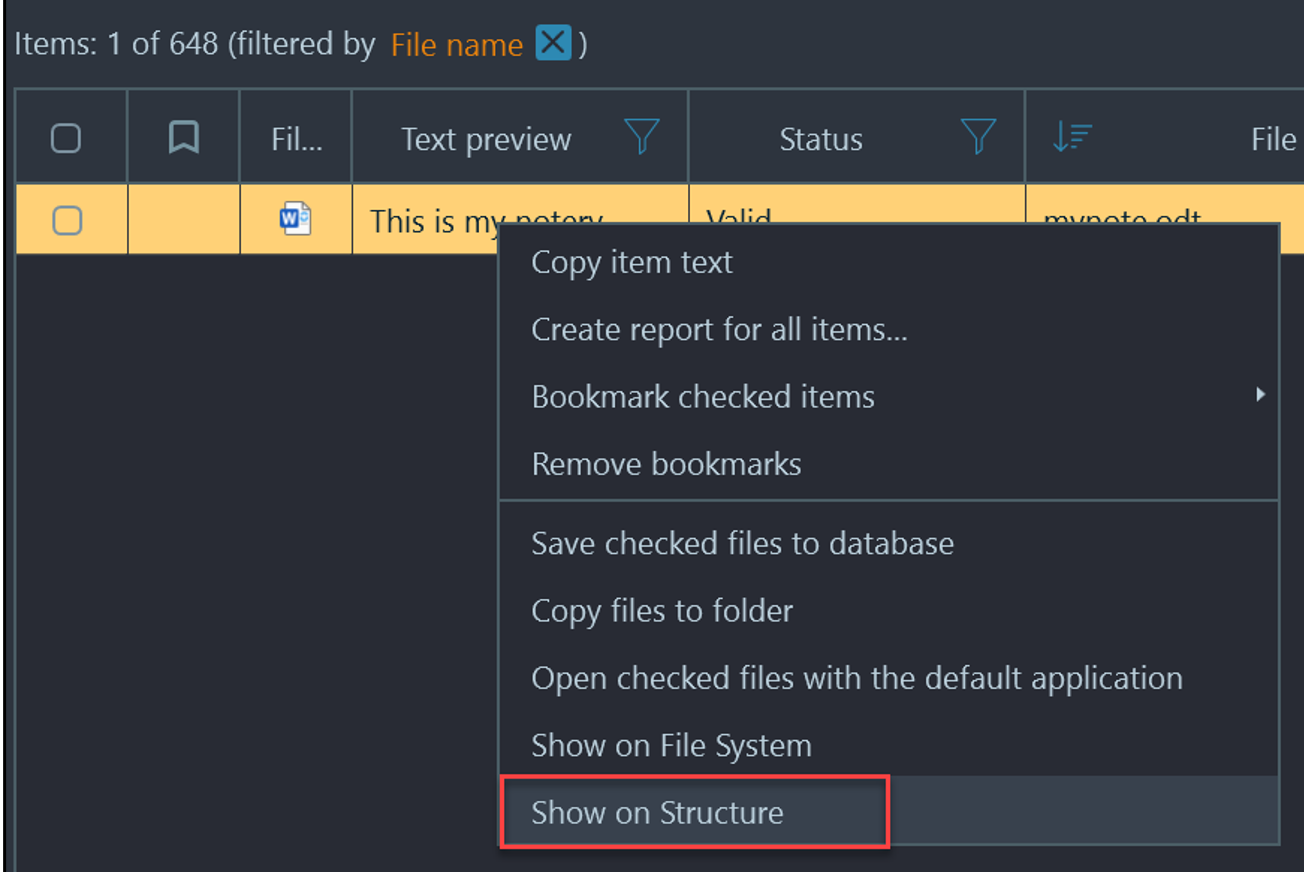
- Now that we are on structure, right-click the file again and choose "Show on File System"—this will take us to where the file is located on the file system.
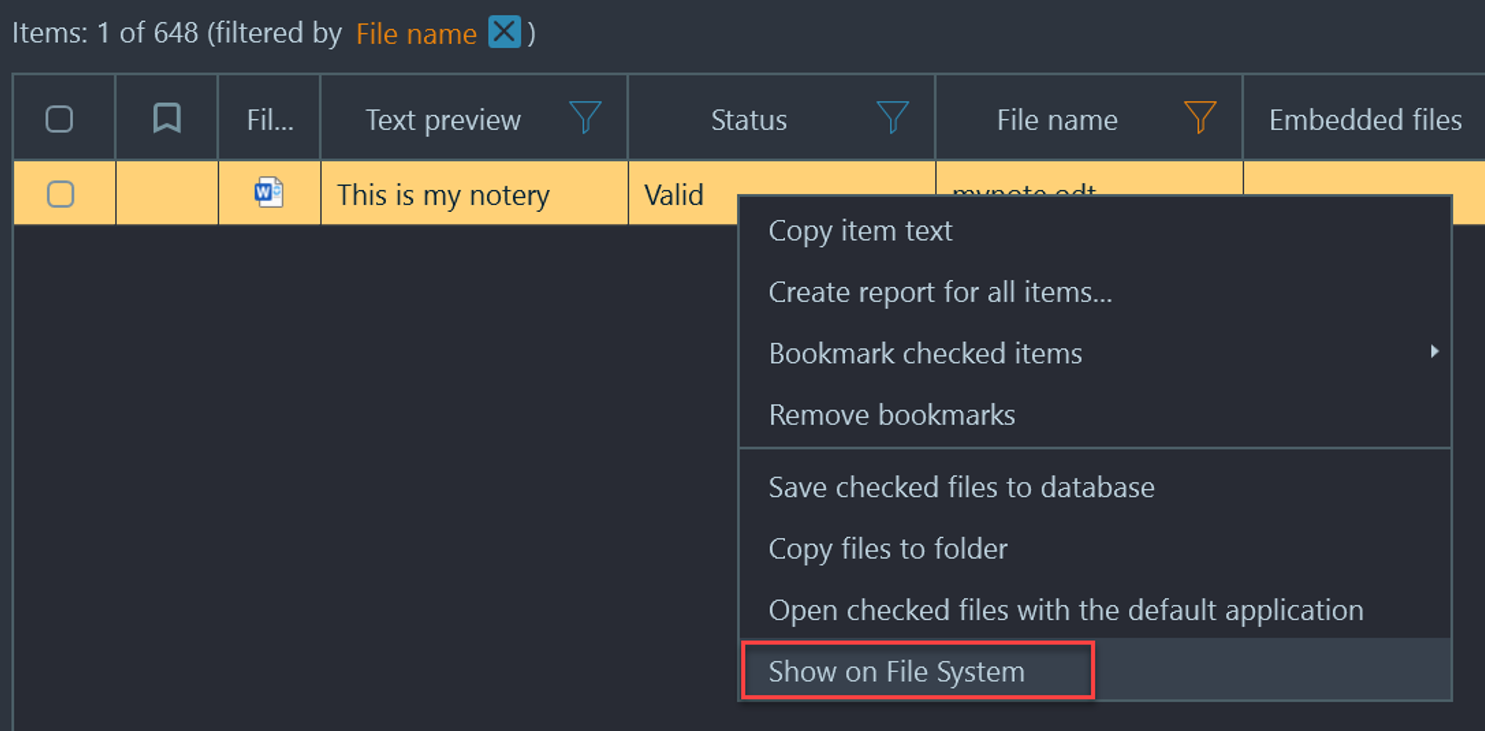
- Once we are in the file system viewer we are brought to /home/Stanley/Documents/.mynote (hidden directory) we notice a file without a file extension, and it appears to be encrypted.
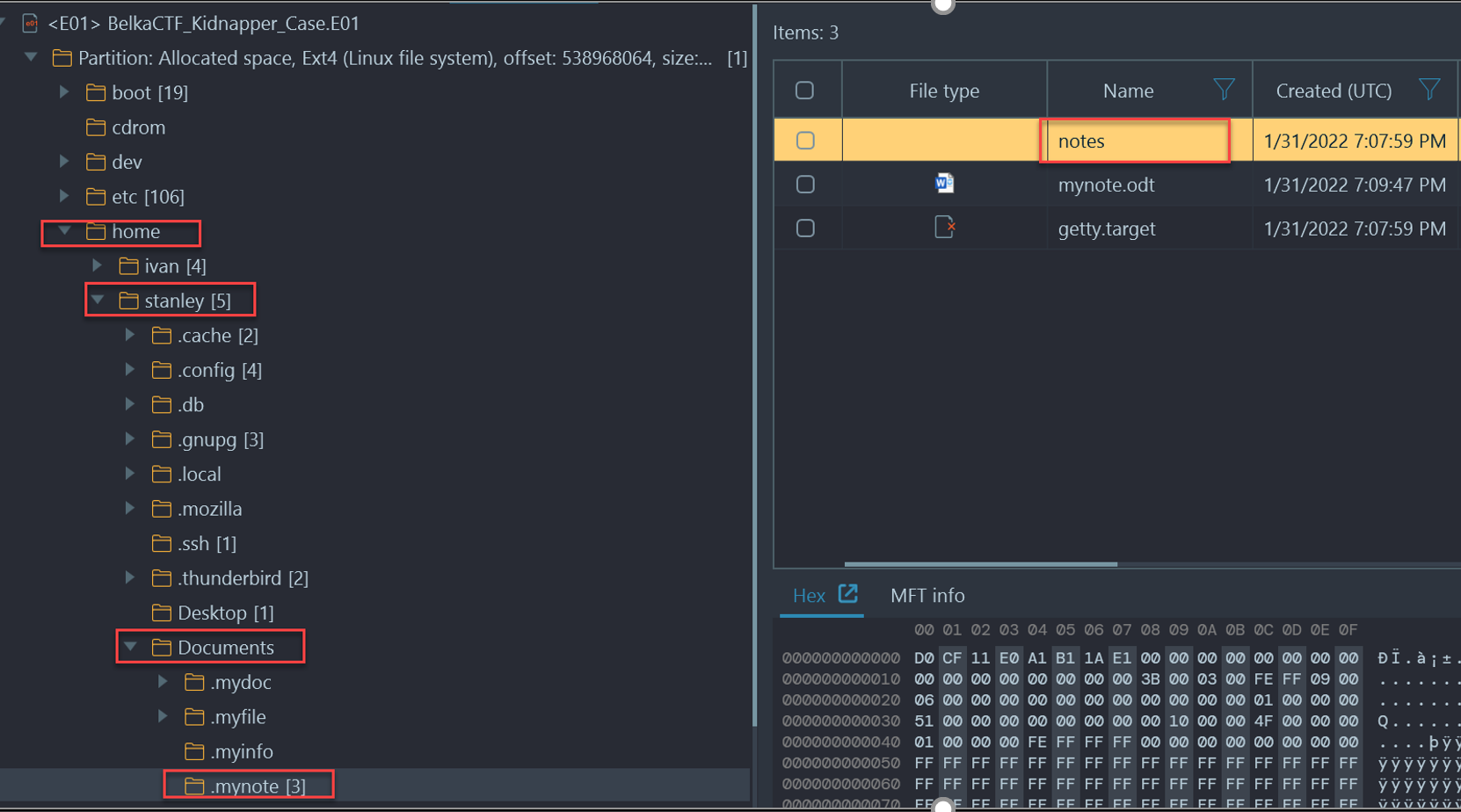
- Copy the "notes" file out of Belkasoft X and change its extension to ".odt" like the other note file present in the hidden directory. You will be prompted for a password to read the contents of the file.

- The plot (and the picture) threw out a hint talking about containers, meaning the password is probably hidden inside another document. Browsing the file system you may have stumbled across a PDF titled "NOTHING_IMPORTANT_INFO.pdf". This was important—*Cough, cough*.
- Throwing the file into a online tool such as Cyberchef and decrypting it with "from Base32" and "Rot13" (another hint, the password for the system image was Base32) will display all passwords—see the one labeled as "note".
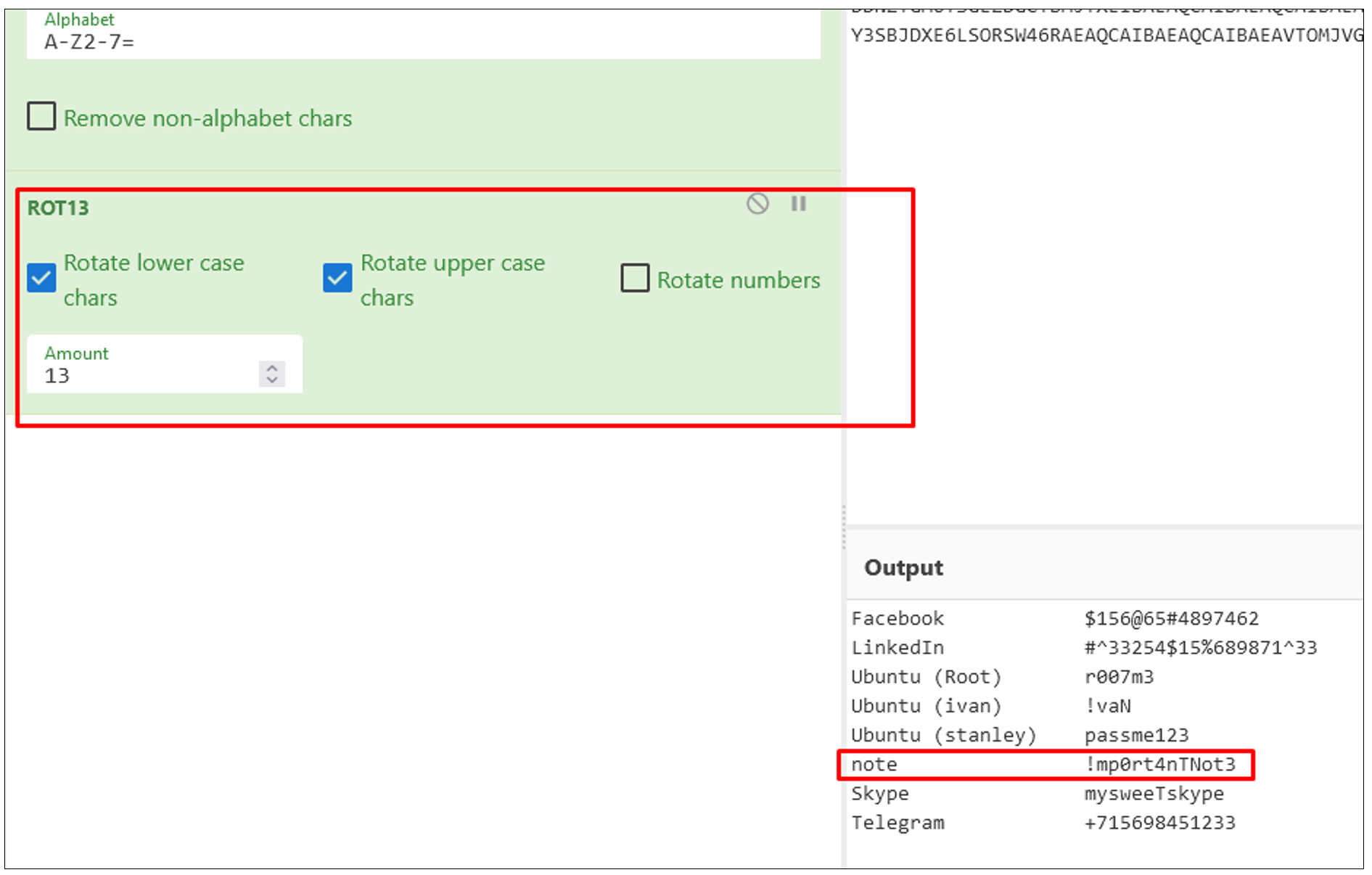
Flag
!mp0rt4nTNot3 (this task was solved 37 times)
7. Specudio (Hard—1000pts)
Question
What is the "secret pin" mentioned in the notes?
This task had a nice hint hidden in its name ("specudio"), which gave player a clue that a secret audio must be looked for.
Solution without Belkasoft X
- With the password to the notes file, we can analyze the notes.docx. While browsing the file, we see a reference to a "shark" file—this could only be a wireshark file (well known for analyzing PCAP or Packet Capture).
- Searching the image for "pcap" in a forensic viewer of your choice, you should see a pcap file called "secret.pcapng". This file can be found at home/ivan/Music/.secs (a hidden directory).
- Export this file and open it with Wireshark.
- Inside Wireshark choose File → Export Objects → HTTP.
- Notice the audio/wav file that was found inside the PCAP file. Export this file and try to play it with a standard audio/mp3 player. You will notice, it is simply an audio file without any meaningful sound inside, which will require some sort of spectrum analyzer.
- A free online tool, which can be used is https://www.dcode.fr/spectral-analysis. Load the file into this player for your flag.
Solution with Belkasoft X
- With the password to the notes file, we can analyze the notes.docx. While browsing the file, we see a reference to a "shark" file—this could only be a Wireshark file (well known for analyzing PCAP or Packet Capture).
- As hidden directories have been common in this CTF, manually digging through the home directory for ivan, you will stumble upon a .pcapng file labeled ".secret.pcapng".
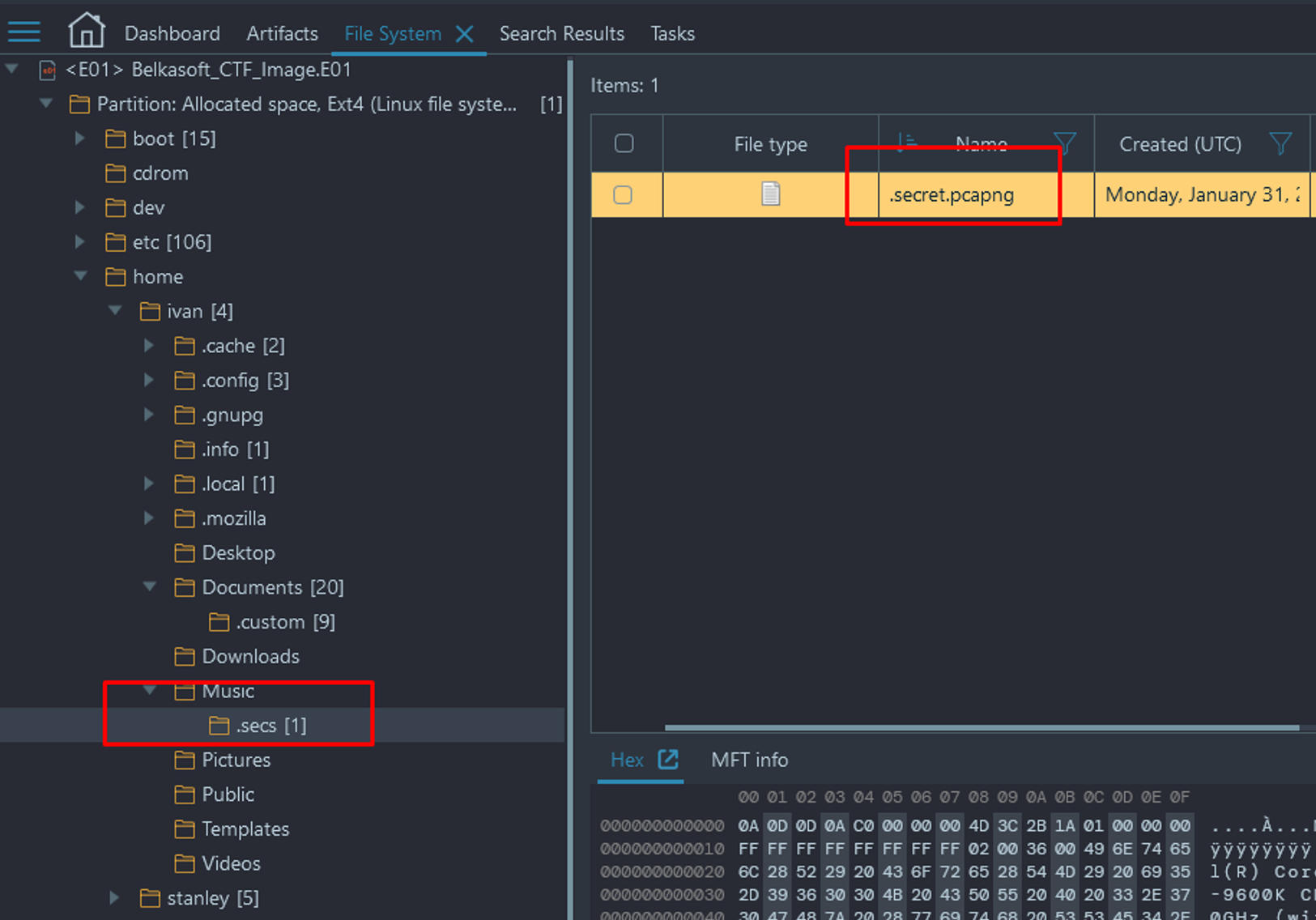
- Export this PCAP file and load it into Wireshark.
- Inside Wireshark choose File → Export Objects → HTTP.
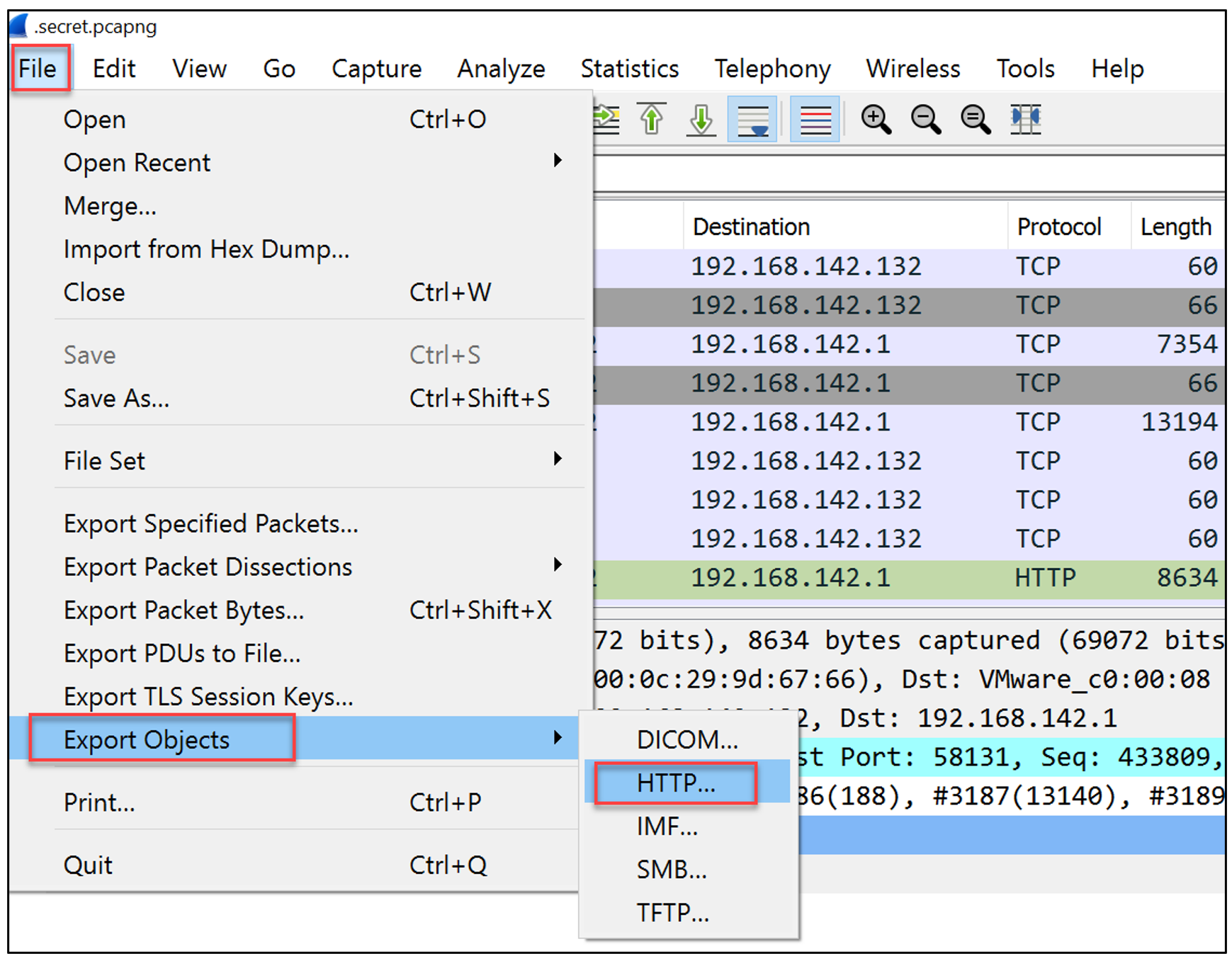
- Notice the audio/wav file that was found inside the PCAP file. Export this file and try to play it with a standard audio/mp3 player. You will notice, it is simply an audio file without any meaningful sound inside, which will require some sort of spectrum analyzer.
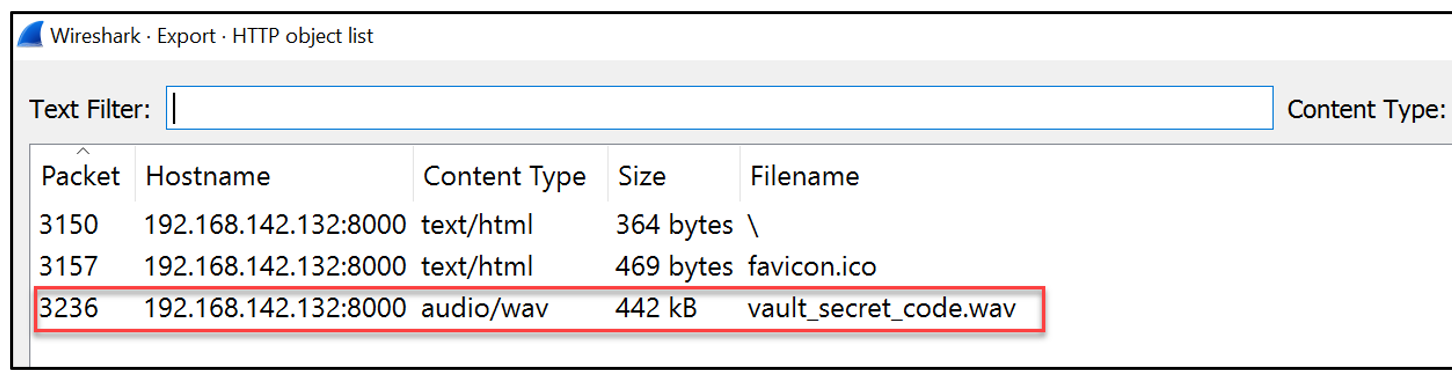
- A free online tool, which can be used is https://www.dcode.fr/spectral-analysis. Load the file into this player for your flag.
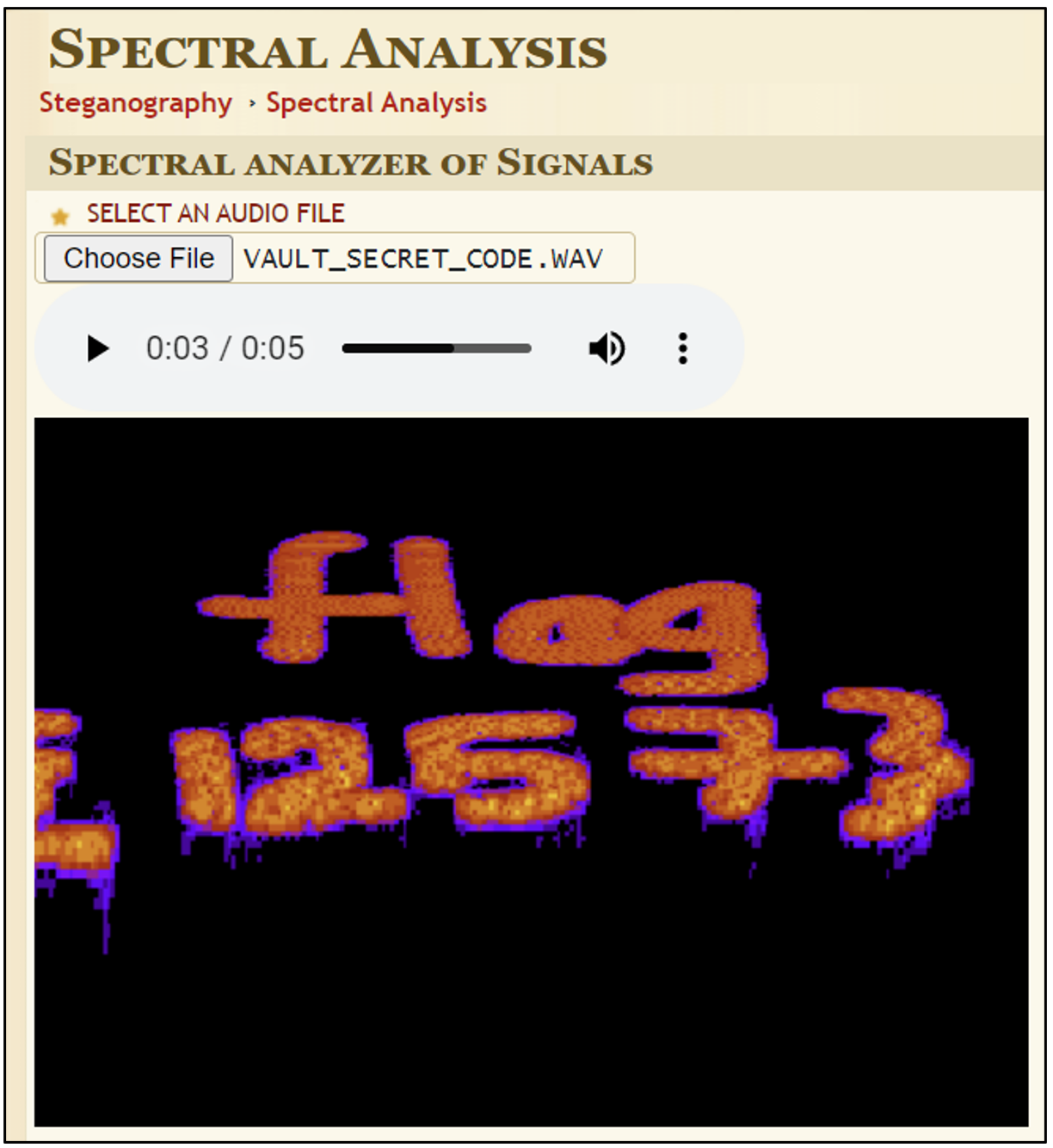
Flag
flag{1257} (this task was solved 38 times)
8. Ultimatum (Baby—100pts)
Question
When did the boy receive a threat? (Format: Epoch Time)
This task had a screw-up initially, the flag format was "UTC time" (had to be "Unix time" or "Epoch time"). However, players guessed the correct format based on the time from the note. The flag format was fixed during the competition.
Solution without Belkasoft X
- Again, referencing the decrypted note, we see that the victim was threatened by his friend (0xTux) 10 minutes before he went to school, which included a timestamp.
- Utilizing a free online tool such as Cyberchef we can input the timestamp from the note file and change it From UNIX timestamp.
- We now need to subtract 10 minutes from this time and push it back through "To UNIX timestamp" to obtain the flag.
Solution with Belkasoft X
- Again, referencing the decrypted note, we see that the victim was threatened by his friend (0xTux) 10 minutes before he went to school, which included a timestamp.

- Utilizing a free online tool such as Cyberchef we can input the timestamp given from the note file and change it to human readable format by using "From UNIX timestamp".
- We now need to subtract 10 minutes from this converted timestamp and push it back into UNIX epoch time to obtain the flag. (1637948867 minus 600 seconds (10 min) is 1637948257). This will be your flag.
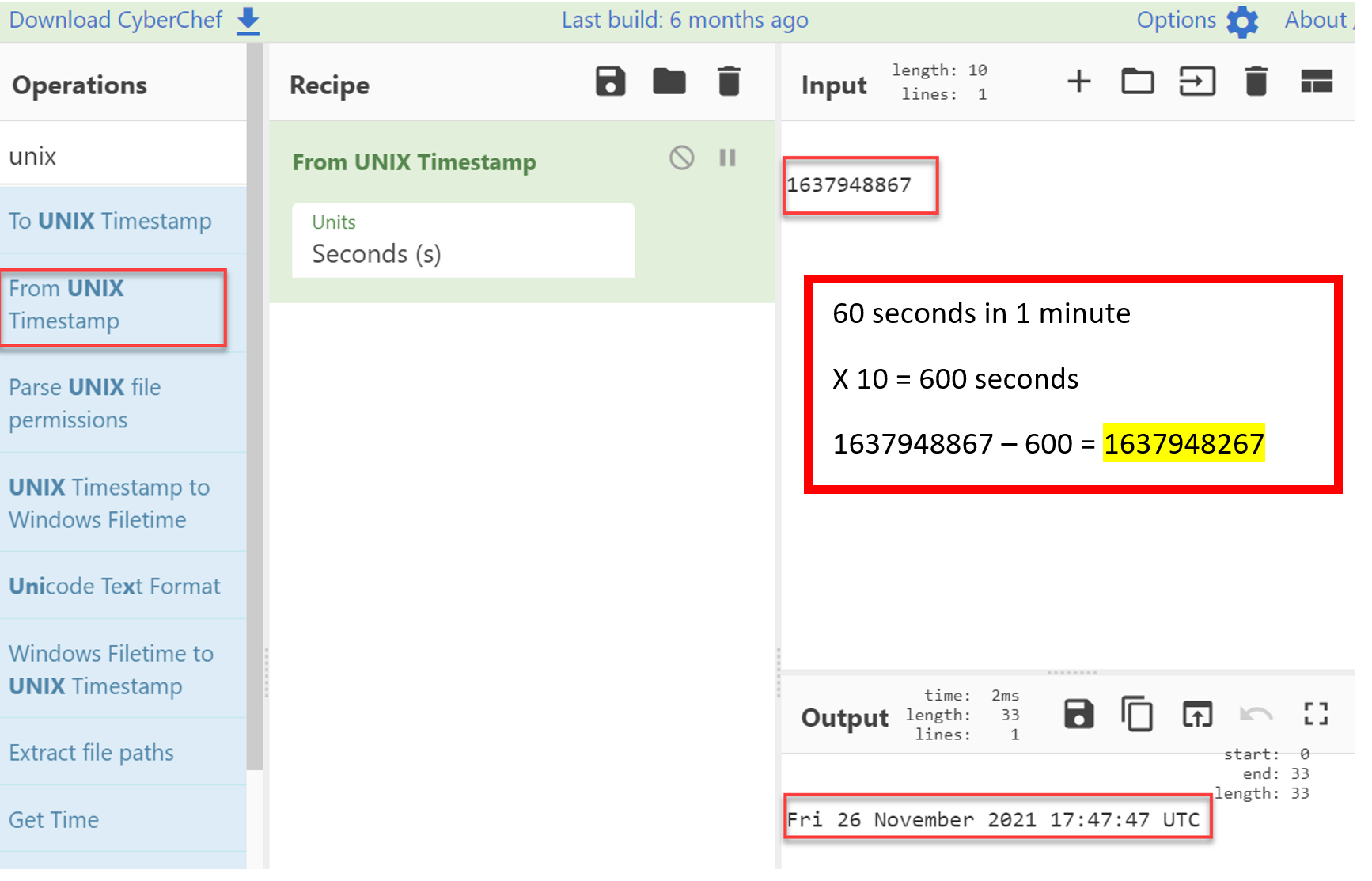
Flag
1637948267 (this task was solved 30 times)
9. Whois (Warmup—200pts)
Question
Who was the kidnapper? (Format: Nickname, email)
The image had a pity mistake regarding this task: there was a leftover (a copy) of a database with a crackable password. It was supposed that you first decrypt a Wickr chat and then find the password to the mycon.zip file, which was actually the flag from the task 7. However, the simpler way was to just crack one of mycon.zip copies, which had a simple password.
Solution without Belkasoft X
- From the note, we know who the kidnapper is (0xTux), but now we need the email address.
- In a forensic viewer of your choice navigate to home/ivan/.local (hidden directory) and find the mycon.zip file.
- This file is also password protected. Load the file into a Linux VM and use any password cracking software (e.g. John the Ripper) to crack the password.
- The password will be found 1257 (note the similar password that cracked in question 7).
- The email for 0xTux can be found in the decrypted file: wixelig493@keagenan.com
Solution with Belkasoft X
- From the note, we know who the kidnapper is (0xTux), but now we need the email address. Lets begin by looking for misplaced or encrypted files.
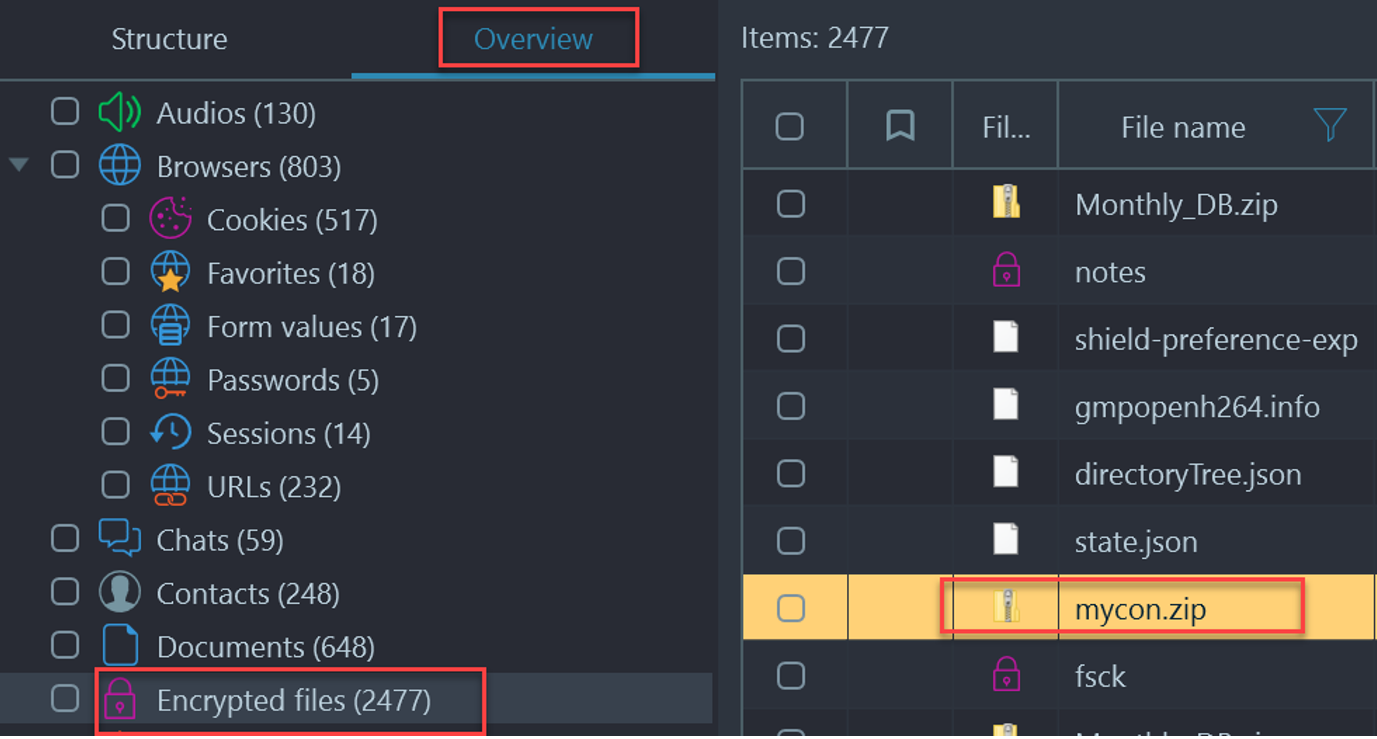
- The only other encrypted zip file that we have not utilized in this CTF was the mycon.zip file located under Artifacts → Overview → Encrypted Files
- Decrypt Wickr chat with the password found inside the file on the desktop.
- Wickr chat gives you a hint that the database password is the flag from the task 7, so you can just use it to decrypt the file.
- Next open up the Sheet1.html file from the extracted archive with a browser of your choice. Once it loads utilize Ctrl+F to search for our username (0x Tux), you will find the second part of the flag.
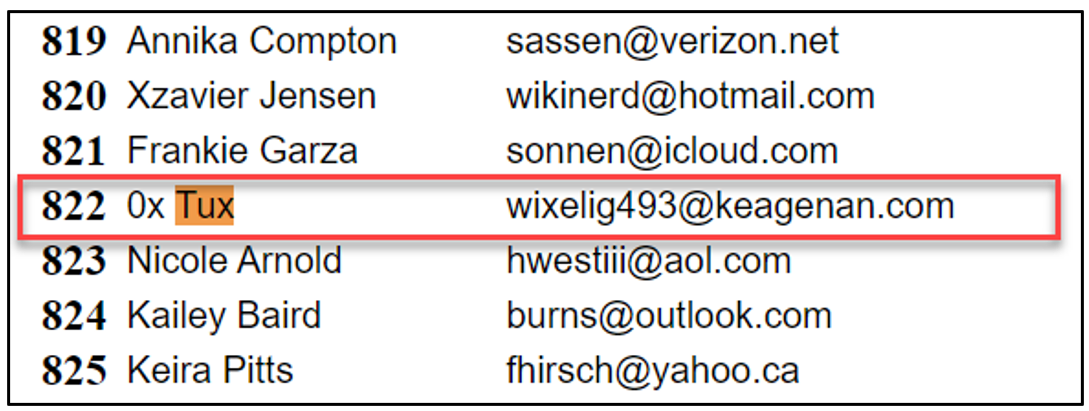
Flag
0xTux, wixelig493@keagenan.com (this task was solved 32 times)
10. Pride (Final—250pts)
This was a bonus task, which allowed you to get 250 extra point for a social post on your success with this BelkaCTF. Every player could submit a URL to their post. There was no standard flag; every URL was manually checked to avoid cheating.
A great example of a correct flag is this post by Emma Sousa.
